UNIT 7
OPERATING SYSTEM AND SECURITY
Security is providing a protection system to computer system resources such as CPU, memory, disk, software programs and most importantly data/information stored in the computer system. If a computer program is run by an unauthorized user, then he/she may cause severe damage to computer or data stored in it. So a computer system must be protected against unauthorized access, malicious access to system memory, viruses, worms etc.
- Authentication
- One Time passwords
- Program Threats
- System Threats
- Computer Security Classifications
Authentication
It refers to identifying each user of the system and associating the executing programs with those users. It is the responsibility of the Operating System to create a protection system which ensures that a user who is running a particular program is authentic. Operating Systems generally identifies/authenticates users using following three ways −
- Username / Password − User need to enter a registered username and password with Operating system to login into the system.
- User card/key − User need to punch card in card slot, or enter key generated by key generator in option provided by operating system to login into the system.
- User attribute - fingerprint/ eye retina pattern/ signature − User need to pass his/her attribute via designated input device used by operating system to login into the system.
One Time passwords
One-time passwords provide additional security along with normal authentication. In One-Time Password system, a unique password is required every time user tries to login into the system. Once a one-time password is used, then it cannot be used again. One-time password are implemented in various ways.
- Random numbers − Users are provided cards having numbers printed along with corresponding alphabets. System asks for numbers corresponding to few alphabets randomly chosen.
- Secret key − User are provided a hardware device which can create a secret id mapped with user id. System asks for such secret id which is to be generated every time prior to login.
- Network password − Some commercial applications send one-time passwords to user on registered mobile/ email which is required to be entered prior to login.
Program Threats
Operating system's processes and kernel do the designated task as instructed. If a user program made these process do malicious tasks, then it is known as Program Threats. One of the common example of program threat is a program installed in a computer which can store and send user credentials via network to some hacker. Following is the list of some well-known program threats.
- Trojan Horse − Such program traps user login credentials and stores them to send to malicious user who can later on login to computer and can access system resources.
- Trap Door − If a program which is designed to work as required, have a security hole in its code and perform illegal action without knowledge of user then it is called to have a trap door.
- Logic Bomb − Logic bomb is a situation when a program misbehaves only when certain conditions met otherwise it works as a genuine program. It is harder to detect.
- Virus − Virus as name suggest can replicate themselves on computer system. They are highly dangerous and can modify/delete user files, crash systems. A virus is generatlly a small code embedded in a program. As user accesses the program, the virus starts getting embedded in other files/ programs and can make system unusable for user
System Threats
System threats refers to misuse of system services and network connections to put user in trouble. System threats can be used to launch program threats on a complete network called as program attack. System threats creates such an environment that operating system resources/ user files are misused. Following is the list of some well-known system threats.
- Worm − Worm is a process which can choked down a system performance by using system resources to extreme levels. A Worm process generates its multiple copies where each copy uses system resources, prevents all other processes to get required resources. Worms processes can even shut down an entire network.
- Port Scanning − Port scanning is a mechanism or means by which a hacker can detects system vulnerabilities to make an attack on the system.
- Denial of Service − Denial of service attacks normally prevents user to make legitimate use of the system. For example, a user may not be able to use internet if denial of service attacks browser's content settings.
Computer Security Classifications
As per the U.S. Department of Defense Trusted Computer System's Evaluation Criteria there are four security classifications in computer systems: A, B, C, and D. This is widely used specifications to determine and model the security of systems and of security solutions. Following is the brief description of each classification.
S.N. | Classification Type & Description |
1 | Type A Highest Level. Uses formal design specifications and verification techniques. Grants a high degree of assurance of process security. |
2 | Type B Provides mandatory protection system. Have all the properties of a class C2 system. Attaches a sensitivity label to each object. It is of three types.
|
3 | Type C Provides protection and user accountability using audit capabilities. It is of two types.
|
4 | Type D Lowest level. Minimum protection. MS-DOS, Window 3.1 fall in this category. |
An operating system in which there exists a level of confidence on the basis of rigorous analysis and testing that the security principals and mechanisms are correctly implemented and operate as intended even in the presence of adversarial activity.
Here, the clients have trust in the people and in the organization operating a trusted system. Technically, a trusted or secure operating system refers to one labeled as “hardened OS” or “trusted OS.” Although the primary objective of both of these is to provide a secure operating environment.
Whereas a hardened operating system has been locked down to prevent attacks, a trusted operating system manages data to make sure that it cannot be altered or moved and that it can be viewed only by persons having appropriate and authorized access rights.
Good design principles are always good for security, These principles are:
- Least privilege. Each user and each program should operate by using the fewest privileges possible. In this way, the damage from an inadvertent or malicious attack is minimized.
- Economy of mechanism. The design of the protection system should be small, simple, and straightforward. Such a protection system can be carefully analyzed, exhaustively tested, perhaps verified, and relied on.
- Open design. The protection mechanism must not depend on the ignorance of potential attackers; the mechanism should be public, depending on secrecy of relatively few key items, such as a password table. An open design is also available for extensive public scrutiny, thereby providing independent confirmation of the design security.
- Complete mediation. Every access attempt must be checked. Both direct access attempts (requests) and attempts to circumvent the access checking mechanism should be considered, and the mechanism should be positioned so that it cannot be circumvented.
- Permission based. The default condition should be denial of access. A conservative designer identifies the items that should be accessible, rather than those that should not.
- Separation of privilege. Ideally, access to objects should depend on more than one condition, such as user authentication plus a cryptographic key. In this way, someone who defeats one protection system will not have complete access.
- Least common mechanism. Shared objects provide potential channels for information flow. Systems employing physical or logical separation reduce the risk from sharing.
- Ease of use. If a protection mechanism is easy to use, it is unlikely to be avoided.
Security Features of Ordinary Operating Systems
A multiprogramming operating system performs several functions that relate to security.
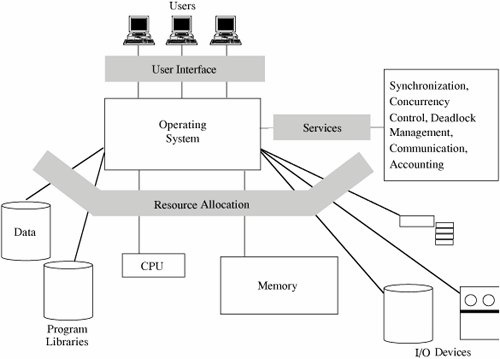
We can see that the system addresses several particular functions that involve computer security:
- User authentication. The operating system must identify each user who requests access and must ascertain that the user is actually who he or she purports to be. The most common authentication mechanism is password comparison.
- Memory protection. Each user's program must run in a portion of memory protected against unauthorized accesses. The protection will certainly prevent outsiders' accesses, and it may also control a user's own access to restricted parts of the program space. Differential security, such as read, write, and execute, may be applied to parts of a user's memory space. Memory protection is usually performed by hardware mechanisms, such as paging or segmentation.
- File and I/O device access control. The operating system must protect user and system files from access by unauthorized users. Similarly, I/O device use must be protected. Data protection is usually achieved by table lookup, as with an access control matrix.
- Allocation and access control to general objects. Users need general objects, such as constructs to permit concurrency and allow synchronization. However, access to these objects must be controlled so that one user does not have a negative effect on other users. Again, table lookup is the common means by which this protection is provided.
- Enforced sharing. Resources should be made available to users as appropriate. Sharing brings about the need to guarantee integrity and consistency. Table lookup, combined with integrity controls such as monitors or transaction processors, is often used to support controlled sharing.
- Guaranteed fair service. All users expect CPU usage and other service to be provided so that no user is indefinitely starved from receiving service. Hardware clocks combine with scheduling disciplines to provide fairness. Hardware facilities and data tables combine to provide control.
- Interprocess communication and synchronization. Executing processes sometimes need to communicate with other processes or to synchronize their accesses to shared resources. Operating systems provide these services by acting as a bridge between processes, responding to process requests for asynchronous communication with other processes or synchronization. Interprocess communication is mediated by access control tables.
- Protected operating system protection data. The operating system must maintain data by which it can enforce security. Obviously if these data are not protected against unauthorized access (read, modify, and delete), the operating system cannot provide enforcement. Various techniques, including encryption, hardware control, and isolation, support isolation of operating system protection data.
Security Features of Trusted Operating Systems
Trusted systems incorporate technology to address both features and assurance. The design of a trusted system is delicate, involving selection of an appropriate and consistent set of features together with an appropriate degree of assurance that the features have been assembled and implemented correctly.
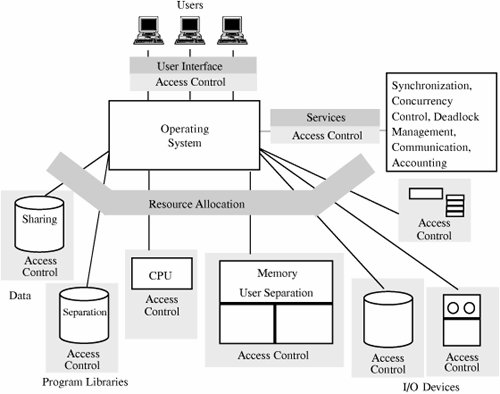
The key features of a trusted operating system, includes
- User identification and authentication
- Mandatory access control
- Discretionary access control
- Object reuse protection
- Complete mediation
- Trusted path
- Audit
- Audit log reduction
- Intrusion detection
Identification and Authentication
It is at the root of much of computer security. It requests access to an object, and verifies the subject's identity. It is based on accurate identification.
It was formerly known as Palladium. It is a software architecture designed by Microsoft which is expected to implement "Trusted Computing" concept on future versions of the Microsoft Windows operating system2. Microsoft's aim for palladium is to increase the security and privacy of computer users. Palladium involves a new breed of hardware and applications in along with the architecture of the Windows operating system. Designed to work side-by-side with the current functionality of Windows, this significant evolution of the personal computer platform will introduce a level of security that meets the rising customer requirements for data protection, integrity and distributed collaboration. It's designed to give people greater security, personal privacy and system integrity. Internet security is also provided by palladium such as protecting data from virus and hacking of data.
In addition to new core components in Windows that will move the Palladium effort forward, Microsoft is working with hardware partners to build Palladium components and features into their products. The new hardware architecture involves changes to CPUs which are significant from a functional perspective. There will also be a new piece of hardware called for by Palladium that you might refer to as a security chip. It will provide a set of keys and cryptographic functions that are central to what we're doing.
There are also some associated changes under the chipset, and the graphics and I/O system through the USB port—all designed to create a comprehensive security environment.
"Palladium" is the code name for an evolutionary set of features for the Microsoft Windows operating system. When combined with a new breed of hardware and applications, "Palladium" gives individuals and groups of user’s greater data security, personal privacy and system integrity. Designed to work side-by-side with the existing functionality of Windows, this significant evolution of the personal computer platform will introduce a level of security that meets the rising customer requirements for data protection, integrity and distributed collaboration.
The Four Fundamentals
A. Strong Process Isolation
The protected operating environment isolates a secure area of memory which is used to process data with higher security requirements. Windows provides separation by using ring 3 and ring 0 processor mode isolation. Windows and any other operating systems also make use of virtual memory segmentation to separate processes from the operating system and from each other. Virtual memory which is used to be considered hard process isolation but Microsoft makes a remarkable admission that “Using the current memory scheme, only virtual memory protection is achievable, and it is relatively easy for an attacker to add malicious programs to both the operating system and user space memory”. An interesting thought is to
Explore here is that under NGSCB even if Windows is completely
Compromised, the NGSCB components can still provide privacy and
Integrity.
B. Sealed Storage
This storage method uses encryption to help ensure the privacy of NGSCB data that persists on the hard disk of NGSCB-capable computers. Sealed storage is secure information storage on the hard disk. Sealed storage is provided through the use of a security support component (SSC) which is implemented directly in hardware. This feature provides the notion of a longlived confidential binding between an application and its data. A primary threat addressed is that even if any another operating system is booted or if any hard drive is moved to another computer the data should stay confidential.
C. Attestation
This occurs when a code digitally signs and attests to a piece of data which help to confirm to the recipient that the data was constructed by a cryptographically identifiable software stack. Attestation allows an application to both identify a remote partner application and satisfy a requirement that the remote application has
Integrity. This integrity is provided by a “cryptographically identifiable software stack”.
D. Secure Paths to the User
By encrypting I/O, the system creates a secure path from the mouse and
Keyboard to trusted applications and from those applications to a region of
The computer screen. These secure paths ensure that valuable information
Remains unaltered and private.
Secure path specifically means that keyboard input is protected from key press until consumed by a secure mode application .
Microsoft emphasizes the difference between the terms secure path and secure channel. Means secure path is a protected path between the computer and the user and secure channel is a protected channel between two computer applications.
References:
Text Book :
Information Security Principles & Practices by Mark Stamp, Wiley.
Reference Books :
Introduction to Computer Security by Bishop and Venkatramanayya, Pearson Education.
Cryptography and Network Security : Principles and Practice by Stallings, PHI.