UNIT 2
ARCHITECTURE
An effective architecture is one in which each machine, device, component, and process performs its role in an effective and (often) coordinated manner, resulting in efficient information processing and output, and also appropriate preventive responses that meet the business and operational needs of an organization.
TYPES:
Single Tiered Architecture
- The components in an IDS or IPS collect and process data themselves, rather than passing the output they collect to another set of components.
- Example: A host-based intrusion-detection tool that takes the output of system logs (such as the utmp and wtmp files on Unix systems) and compares it to known patterns of attack.
- It offers advantages like simplicity, low cost and independence from other components.
- It usually possesses components that are not known of each other, hence reducing efficiency and sophisticated functionality.
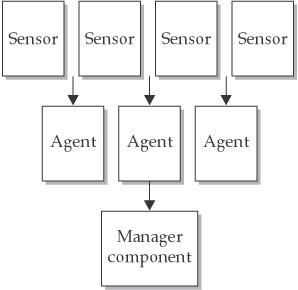
Multi Tiered Architecture
- It involves multiple components that pass information to each other.
- Many of today’s IDSs, for example, consist of three primary components: sensors, analyzers or agents, and a manager.
- Sensors perform data collection. They are often programs that capture data from network interfaces or system logs and other sources, such as personal firewalls and TCP wrappers.
- A central collection point allows for greater ease in analyzing logs because all the log information is available at one location.
- Additionally, writing log data to a different system from the one that produced them is advisable; if an attacker tampers with or destroys log data on the original system, the data will still be available on the central server—the manager component.
- The management consoles can enable intrusion-detection and intrusion-prevention staff to remotely by changing policies and parameters, erasing log files after they are archived, and performing other important functions without having to individually authenticate to sensors, agents, and remote systems.
Peer to Peer Architecture
- It involves exchanging intrusion-detection and intrusion-prevention information between peer components, each of which performs the same kinds of functions.
- It is often used by cooperating firewalls. As one firewall obtains information about events that are occurring, it passes this information to another, which may cause a change in an access control list or addition of restrictions on proxy connections. The second firewall can also send information that causes changes in the first. Neither firewall acts as the central server or master repository of information.
- Advantage: simplicity.
- Any peer can participate in what is effectively a group of peer machines, each of which can benefit from the information the others glean.
- The main downside is a lack of sophisticated functionality due to the absence of specialized components.
IDSs and IPSs can be as simple or as complex as you want them to be. At the simplest level, a packet-capturing program to dump packets to files, and then use commands such as egrep and fgrep within scripts to search for strings of interest within the files is used.
In a more complex IDS or IPS, additional operations, like filtering out undesirable input, applying firewall rules, getting certain kinds of incoming data in a format that can be more easily processed, running detection routines on the data, and executing routines occur.
Information Flow in IDS and IPS
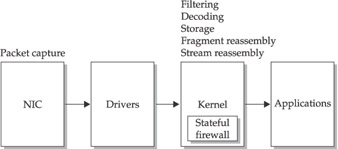
Here, the NIC collects packets and sends them to drivers that interface with the kernel. The kernel decodes, filters, and reassembles fragmented packets, and then reassembles streams. The output is passed on to applications.
Raw Packet Capture
- In this, information flow starts with raw packet capture.
- This involves passing the data to the next component of the system.
- It saves the raw packets that are captured, so they can be processed and analyzed at some later point.
- Mostly, the packets are held in memory long enough so initial processing activities can occur and then written to a file or a data structure to make room in memory for subsequent input.
Solving Problems
- Here, the most-common problem is packet loss.
- Solution: to deploy higher-ended hardware.
Filtering
- It is limiting the packets that are captured according to a certain logic based on type of packet, IP source address range etc.
- Filtering raw packet data can be done in several ways.
- The NIC itself may be able to filter incoming packets.
- The filtering rules are specified in the configuration of the driver itself.
- This kind of filtering is not likely to be as sophisticated.
Packet Decoding
- Packets are subsequently sent to a series of decoder routines that define the packet structure that are collected through promiscuous monitoring.
- The packets are then further decoded to determine whether the packet is an IPv4 packet, an IP header with no options or IPv6.
- It examines each packet to determine whether it is consistent with applicable RFCs.
- Packets are normally dropped because the IDS/IPS will not be able to process them properly.
Storage
- Once decoding is done, each packet is stored either by saving its data to a file or by assimilating it into a data structure on the other hand, at the same time, the data are cleared from memory.
- Storing data to a file is rather simple and intuitive because “what you see is what you get.”
- New data can simply be appended to an existing file or a new file can be opened, and then written to.
Fragment Reassembly
- Packet fragmentation poses yet another problem for IDSs and IPSs.
- Firewalls, routers, switches, and IDSs/IPSs must deal with a reasonable percentage of network traffic consists of packet fragments.
- Hostile fragmentation, packet fragmentation are used to attack other systems or to evade detection mechanisms.
Evading Intrusions
- Evasion focuses on fooling signature-based attack detection by changing the form of an attack.
- Fragroute is a tool that breaks packets into tiny fragments in extremely unusual ways before transmitting them across the network.
- These fragments are collected by network-based IDS or IPS and then decodes and reassemble them before detection routines analyze their data.
Stream Reassembly
- It takes the data from each TCP stream, reorder it so that it remains the same as when it was sent by the host that transmitted it and also the host that received it.
- This requires determining when each stream starts and stops.
Inspection of TCP Sessions
- Here network traffic is a virtual necessity whenever the need to analyze the legitimacy of packets that traverse networks presents itself.
- Attackers often try to slip packets they create through firewalls, screening routers, IDSs, and IPSs by making the fabricated packets look like part of an ongoing session or like one being negotiated via the three-way TCP handshake sequence, even though such a session was never established.
Firewalling
- Filtering is essentially a type of firewalling, even through it is relatively rudimentary.
- But, after stateful inspections of traffic are performed, more sophisticated firewalling based on the results of the inspections can be performed.
References:
- Intrusion Detection & Prevention by Carl Endorf, Eugene Schultz and Jim Mellander, TMH.
2. Implementing Intrusion Detection systems by Tim Crothers, Wiley.