UNIT 4
Security and IDS Management
It is a way to understand the relationship between multiple variables and attributes in your dataset. Here:
- One or multiple attributes depend on another attribute or a cause for another attribute.
- One or multiple attributes are associated with other attributes.
- It helps in predicting one attribute from another.
- It indicates the presence of a causal relationship.
- It is used as a basic quantity for many modeling techniques
TYPES:
Positive Correlation:
- Here, if feature A increases then feature B also increases or if feature A decreases then feature B also decreases.
- Both features move in tandem and they have a linear relationship.
Negative Correlation:
Here, if feature A increases then feature B decreases and vice versa.
No Correlation:
No relationship between those two attributes.
Multicollinearity :
- If positive or negative attributes of your dataset is perfect then there is a high chance that the performance of the model will be impacted by a problem called — “Multicollinearity”.
- It happens when one predictor variable in a multiple regression model can be linearly predicted from the others with a high degree of accuracy.
- This can lead to skewed or misleading results.
The incident-response process consists of several steps. The first is to do a proper risk analysis, design a proper methodology, and create a response team that will follow the methodology.
Risk Analysis
Risk analysis involves identifying risks within your organization and the potential loss resulting from those risks. It is imperative that this is done so that a proper response can be put in place, based on the amount of risk.
Risk can be looked at from either a quantitative or qualitative point of view.
Quantitative risk analysis attempts to assign an objective numeric value, usually monetary, to components of the risk assessment and to potential loss.
The formula would look like this:
(Attack Success + Criticality) – (Countermeasures) = Risk
Methodology
There are several methodologies that are used, and many organizations use variations on different models, but the model presented here is the most thorough. The model consists of six stages:
- Preparation
- Detection
- Containment
- Eradication
- Recovery
- Follow-up
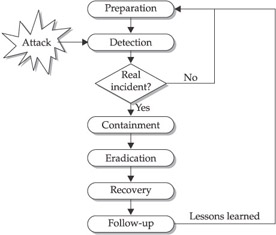
Six-stage incident-response model
The preparation stage is when information is gathered on how you would respond to various incidents.
The detection stage happens when a possible incident has occurred—it is the first reactive stage in the process.
Once the detection has occurred, it is imperative that the incident be recorded. This includes the date and time, who is involved, any direction from management, the nature of the attack, and what is being attacked.
In the containment stage, decisions and actions need to be made about how the incident can be prevented from causing more damage, and how it can eventually be eradicated.
Once the event has been contained, it must be eradicated. Eradication is the process of eliminating the root cause of the incident, whether it was a back door, virus, or operating system vulnerability.
The recovery stage is when you get all systems back up and online as they would normally be. This process assumes that the eradication has taken place and that processes and procedures are followed to bring the systems back up.
The follow-up stage is very important, as it reviews the previous steps and analyzes what was done correctly and what could be improved upon.
Other things that should be developed:
- Guidelines on system outages Be sure to log how long a system can be disconnected from the network without disrupting critical business function.
- Backup and restoration plans Identify tools that are likely to be needed in an incident. It is recommended that you have a tool kit with the software and utilities needed to respond appropriately to attacks.
- Incident-reporting and contact forms Create forms on which you can record the people contacted, the systems and networks targeted by the attack, purpose of the attack, and evidence of the attack. Figure 13-3 shows a sample incidentreporting form.

Incident identification form
|
Creating an Incident Response Team
Each organization will define the roles differently, but these are some common roles:
- Incident Coordinator (IC)
- Incident Manager (IM)
- Incident Analyst (IA)
- Constituency
Responding to an IDS or IPS Incident
One of the most important aspects of incident response and intrusion detection and prevention is being able to handle the alerts that are generated. An IDS can generate large numbers of alerts. Being able to identify which ones are legitimate and which are false is crucial. The most common attacks detected by both IDSs and IPSs are scanning attacks, penetration attacks, and denial-of-service attacks, which were covered in Chapters 2 and 3.
IDS and IPS Incident Response Phases
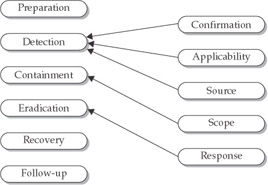
There are five phases to dealing with a possible attack:
- Confirmation
- Applicability
- Source
- Scope
- Response
A procedure outlines the specific steps of how the policy, supporting standards, and guidelines will be implemented. A procedure is a description of tasks that must be executed in a specific order. Procedures are sometimes referred to as “practices.”
A baseline is a method of implementing security mechanisms and products. Baselines are platform unique and should be employed throughout an organization. They detect differences between various operating systems (OSs) to ensure uniform security implementation.
IDS IPS Policy
An IDS policy is a stand-alone policy, but it integrates with other policies, such as the firewall, routers, and incident response. When creating a policy, it’s important to include enough detail to be able to determine the strategies for standards, guidelines, procedures, and baselines.
Creating an IDS IPS Policy
When you create a policy, having input from the organization as to what they want to achieve is critical. The policy wants to cover the why and the how. One effective way to do this is to cover the following seven steps:
- Introduction
- Purpose
- Scope
- Policy
- Enforcement
- Definitions
- Revisions
The following is an example policy using this seven-step process:
Sectionx | Mm/dd/yy: Effective |
| Mm/dd/yy: Revised |
Policy x.xx Intrusion Detection Policy | Security Analyst Author |
Step 1: Introduction
Intrusion detection is a critical piece of the organization’s security policy. Effective security systems must evolve to handle the vast amount of vulnerabilities introduced by the use of distributed systems. Having some type of reassurance that the systems and network are secure is important, and intrusion detection systems can help provide part of that assurance.
Step 2: Purpose
The purpose of this policy is to provide guidance for the use of intrusion detection at <Your Organization Here>. This document is to be followed for intrusion-detection monitoring using intrusion detection tools and system audit logs for the system servers, software, database, networks, and firewalls under its control.
Step 3: Scope
This policy applies to all constituents at <Your Organization Here>. More specifically, this policy applies to all individuals who are responsible for the installation of new information resources, the operations of existing information resources, and individuals charged with information resource security.
Step 4: Policy
247 intrusion-detection monitoring will be conducted by using intrusion-detection tools and system audit logs for the system servers, software, database, networks, and firewalls under its control. Reports will be submitted daily for assessment and possible corrective action. Immediate corrective action will be taken to help eliminate system vulnerabilities or to prevent future intrusion attempts. This can also be seen as a contract with the rest of the organization regarding the expected quality of service (that is, 247 or maximum response time).
Procedures for system break-ins:
- Immediately notify management via a predefined emergency notification list and notify the affected network manager.
- Follow up with a system security report to management in the System Security Template, as shown in the following example. The report will include an assessment on compromised systems or information, system risks, and corrective actions.
- Security management will determine the appropriate corrective action and direct the corrective action based on priority.
System Security Template |
Date: |
Time: |
Security Incident Report—Number ______________ |
Incident Details: |
Information Resource Effect: |
Incident Identified By: |
Source of Attempt: |
Analyses and Recommendation(s): |
Reporting Manager: |
Step 5: Enforcement
Any employee found to have violated this policy could be subject to disciplinary action, up to and including termination of employment. Additionally, individuals are subject to loss of information resources, access privileges, and the possibility of civil and criminal prosecution.
Step 6: Definitions
- Constituent Any employee, contracted employee, or affiliate of the company.
- Information Resources Any computer-related or computer-generated material. Including, but not limited to, printouts, online display devices, magnetic storage media, and any computer-related activities involving any device with e-mail receiving capabilities, browsing web sites, or otherwise capable of receiving, storing, managing, or transmitting electronic data including, but not limited to, mainframes, servers, personal computers, notebook computers, hand-held computers, personal digital assistants (PDA), and pagers.
- Security Incident Any attempt or action of unauthorized access to a information resource.
Step 7: Revision History
- Policy: Version 1.0 April 2000
- Revised: Version 1.1 June 2002
- Revised: Version 1.2 May 2003
Procedure for Implementation of Your Policy
Just having a policy written isn’t nearly enough. Proper implementation of the policy is key. At this stage, the staff needs to be educated on the policy and what needs to be done for the policy to succeed. Therefore, all staff who have access to, or are responsible for, the IDS or the IPS program must have the policy made available to them. The policy should be easily accessible, but also secured. This can be done via an intranet site or on a server on the internal network.
Keeping Your Policy Current
Keeping your policy current is critical for a successful policy. If your policy is outdated, it won’t do anyone any good when it’s needed. Make certain you review your policy at least annually. Things that might need to be updated include the following:
- Any new software added
- New legislation
- Changes in procedures
- Changes in critical assets
- Roles and responsibilities
- Contact information
- New detection methods
Also important is to look at what happened during an incident and revise your policy to reflect these issues. You might find your policy lacks certain steps or actions that should have been addressed.
The National Institute of Standards and Technology (NIST) developed this document in furtherance of its statutory responsibilities under the Federal Information Security Management Act (FISMA) of 2002, Public Law 107-347. This publication seeks to assist organizations in understanding intrusion detection system (IDS) and intrusion prevention system (IPS) technologies and in designing, implementing, configuring, securing, monitoring, and maintaining intrusion detection and prevention systems (IDPS). It provides practical, real-world guidance for each of four classes of IDPS: network-based, wireless, network behavior analysis software, and host-based. The publication also provides an overview of complementary technologies that can detect intrusions, such as security information and event management software. It focuses on enterprise IDPS, but most of the information in the publication is also applicable to standalone and small-scale IDPS deployments.
Legal Review
Creation of any security policy needs to be reviewed by your organization’s legal representation, so the policy can be legally reinforced and defensible. Your legal department can help determine if the policy reflects best practices and due care on the part of your organization. When investigations of an incident occur, it’s critical that your organization does everything in its power to protect the information and preserve evidence for legal proceedings. In addition, making sure that your organization adheres to all local, state, and federal regulations can help.
Another key issue is to make sure the policy is in touch with legislation that affects your organization. Your policy should include a clause regarding compliance with any legislation. Because much legislation is required, it’s wise to incorporate your policies with this legislation. Your legal department is in the best position to do this.
The standard was published in 2015, “revising and canceling” (i.e. replacing) ISO/IEC 18043:2006.
A technical corrigendum in 2016 corrected the title of the published standard, reintroducing the conspicuously absent words “and prevention” that somehow got lost along the way.
Attack Metrics
One of the most powerful aspects of implementing an intrusion detection and prevention program is that you can obtain measurable metrics of actual attacks against your organization’s network. Following are examples of some quantitative data that can be useful:
- Attack type It is important that you are able to collect data on the amount and type of attacks that threaten your organization. While this is a dynamic number, at any time it can be helpful to determine what areas of your security program can be bolstered and what areas have sufficient controls in place.
- Probability of detection This will allow an organization to create a metric that identifies the amount of correctly detected attacks during a specific time frame. This is an effective measurement of your IDS capabilities and the fine tuning that may be needed.
- Correlation abilities This will help you determine your ability to correlate information from other systems, such as firewalls, with the current IDS and IPS data to detect attacks. This can be very effective, especially when detecting “low-and-slow” attacks.
Proactive vs Reactive Technology
Much of the technology deployed on a network is reactive in nature. For example, firewalls will react and block a port after an unauthorized attempt, but with intrusion prevention and some intrusion detection capabilities, you are able to be proactive in attack situations.
IDS Deployment Costs
When considering costs, it is important that you evaluate three areas: the infrastructure cost, the residual costs, and the support costs
Acquisition
Most organizations have their own process in place to acquire new products. Thus, discussing the detailed acquisition processes of writing a request for information (RFI), request for proposal (RFP), and request for quotes (RFQ) won’t add value to this book. The steps are
- Define your organization’s requirements.
- Research the IDS/IPS products.
- Select a vendor’s product to test.
- Test the product.
- Select the product.
Requirements
When defining the requirements for your organization, consider the cost and purpose. In a perfect world, money would not be an issue and you would just implement the “best of breed”—but this is not a perfect world.
Research
When researching an IDS/IPS product, you can collect data from three main sources: peer-reviews, third-party analysis, and testing materials. Testing will be covered in detail a little later in the chapter. Peer review would entail gathering information from other companies about the product and getting their input on what has and has not worked for them.
Vendor Selection
Vendor selection is the evaluation of the vendor after you have decided that the vendor’s product is worthy of testing.
Testing
Testing allows you to evaluate the product’s performance on your network. This process can help you to
- Verify vendor’s claims
- Provide insight into the implementation
- Test performance
Selection
The final step is to make a selection based on the requirements, research, and testing that has occurred. This information can be put into a matrix similar to the requirements matrix discussed earlier.
Evasion Tools
The number of methods for evading signature-based IDSs has been increasing dramatically over the last few years. For example, powerful tools that can defeat signature-based IDSs are available.
Neural Networks
Neural networks are sets of mathematical models that imitate how neurons learn, assigning different weights to connections between elements within the neural network similarly to how electrical potentials for neurons are built up at synaptic junctions based on their frequency of firing.
Protocol Analysis
Protocol analysis means analyzing the behavior of protocols to determine whether one host is communicating normally with another. For example, the TCP handshake
Target Detection
We're also likely to see more widespread use of target detection in the future. As mentioned previously, target detection has proven to be one of the most robust and reliable methods of intrusion detection. Attackers almost invariably make changes in systems, often to create back doors, but sometimes (especially in the case of novice attackers) changes occur simply by accident. Attackers may be able to evade signature-based IDSs, and they may also be able to delete system logs to hide evidence of their activity, but they are less likely to escape the notice of a target detection tool that uses a variety of strong cryptographic algorithms and requires strong authentication for access to the target detection functions.
References:
- Intrusion Detection & Prevention by Carl Endorf, Eugene Schultz and Jim Mellander, TMH.
2. Implementing Intrusion Detection systems by Tim Crothers, Wiley.