UNIT 1
Introduction
Computer network component comprises of both physical parts as well as the software required for installing computer network, both at organizations and at home. The hardware components are the server, the client, the peer, the transmission medium, and the connecting devices. The software components are operating system and protocols.
- Servers: Servers are the high-configuration computers that manage the resources of network. The network operating system is typically installed in server and so they give users accesses to the network resources. Servers can be of various kinds: file servers, database servers, print servers etc.
- Clients: Clients are computers that request and receive service from the servers to access and use the network resources.
- Peers: Peers are computers that provide as well as receive services from other peers in a workgroup network.
- Transmission Media: Transmission media is the channels through which data are transferred from one device to another device in a network. Transmission media may be guided media such as coaxial cable, fibre optic cables and many more or maybe unguided media such as microwaves, infra-red waves etc.
- Connecting Devices: Connecting devices act as a middleware between networks or computers, by binding network media together. Some of the common connecting devices are as follows:
Routers
Bridges
Hubs
Repeaters
Gateways
Switches
- Networking Operating System: Network Operating System is typically installed in server and facilitate workstations in network to share files, database, applications, printers and many more
- Protocol Suite: A protocol is a rule or a guideline followed by each computer to communicate data. Protocol suite is a set of related protocols that are laid down for computer network. The two protocol suites are:
OSI Model (Open System Interconnections)
TCP/IP Model
Full form of OSI is Open Systems Interconnection. OSI is developed by ISO – ‘International Organization of Standardization in the year 1974. OSI is seven layer architecture with every layer is having specific functionality to perform. All these seven layers work together to transmit the data from one person to another.
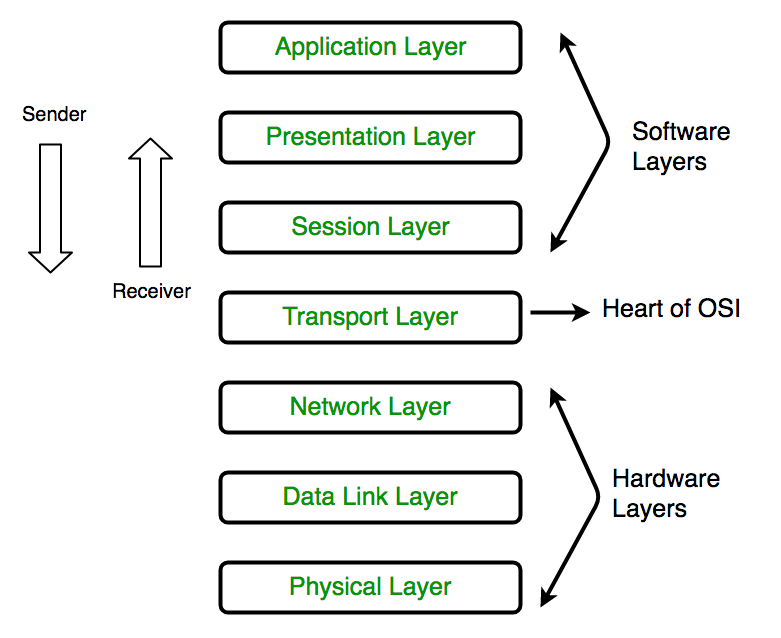
Physical Layer (Layer 1):
The very lowest layer of the OSI model is the physical layer. It is responsible for actual physical connection between devices. The physical layer has information in the form of bits. When receiving the data, this layer will get signal received and then convert it into 0s and 1s and send them to the next layer which is Data Link layer, which will put the frame back together again.
The functions of the physical layer are as follows:
- Bit synchronization: The physical layer provides synchronization of the bits by providing a clock. This clock controls both the sender and the receiver thus providing the synchronization at bit level.
- Bit rate control:The Physical layer defines the transmission rate which is the number of bits sent per second.
- Physical topologies: Physical layer specifies the way in which the different, devices are arranged in a network which is bus, star or mesh topology.
- Transmission mode: It also defines the way in which the data flows between the two connected devices. Various transmission modes possible are: Simplex, half-duplex and full-duplex.
Data Link Layer (DLL) (Layer 2):
The data link layer is responsible for node to node delivery of message. The main function of this layer is to make sure that data transfer is error free from one node to another node, over the physical layer. When the packet arrives in a network, it is the responsibility of DLL to transmit it to the Host using its MAC address.
Data Link Layer is divided into two sub layers:
- Logical Link Control (LLC)
- Media Access Control (MAC)
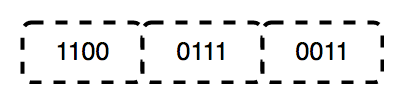
The packet which is received from the Network layer is again divided into frames depending on the frame size of NIC (Network Interface Card). DLL also encapsulates the Sender and the Receiver’s MAC address in the header.
The Receiver’s MAC address is obtained by placing an ARP(Address Resolution Protocol) request onto the wire asking “Who has that IP address?” and the destination host will reply with its MAC address.
The functions of the data Link layer are as follows:
- Framing: Framing is a function of the data link layer. It provides a way for a sender to transmit the set of bits that are very meaningful to the receiver. This can be accomplished by attaching the special bit patterns to the beginning and end of the frame.
- Physical addressing: After creating frames, Data link layer adds physical addresses (MAC address) of the sender and/or receiver in the header of each of the frame.
- Error control: Data link layer provides the mechanism of error which control in which it detects and then retransmits damaged or lost frames.
- Flow Control: The data rate must be constant on both of the sides else the data may get corrupted thus; flow of control coordinates that amount of data that can be sent before receiving the acknowledgement.
- Access control: When a single communication channel is shared by the multiple devices, MAC sub-layer of data link layer helps to determine that which of the device has control over the channel at a given time.
Network Layer (Layer 3):
Network layer works for the transmission of data from one host to another host which located in different networks. It also takes care of packet routing that is selection of the shortest path to transmit packet, from the number of routes which is available. The sender & the receiver’s IP address are placed in the header by the network layer.
The functions of the Network layer are as follows:
- Routing: The network layer protocols determine which of the route is suitable from source to destination. This function of network layer is called routing.
- Logical Addressing: In order to identify each device on internet uniquely, network layer defines the addressing scheme. The sender & the receiver’s IP address are placed in the header by the network layer. Such an address distinguishes each of the devices uniquely and universally.
Transport Layer (Layer 4):
Transport layer provides the services to the application layer and then takes services from network layer. The data in the transport layer is known as Segments. It is responsible for the End to End delivery of the complete message. Transport layer also provides the acknowledgment of the successful data transmission and then re-transmits the data if an error occurred.
• At sender’s side:
Transport layer receives formatted data from the upper layers, which performs Segmentation and also implements Flow & Error control to ensure that proper data transmission occurs. It also adds Source and Destination port number in its header and then forwards the segmented data into the Network Layer.
• At receiver’s side:
Transport Layer reads the port number from its header and then forwards the Data which it has received to respective application. It also performs the sequencing and the reassembling of the segmented data.
The functions of the transport layer are as follows:
- Segmentation and Reassembly: This layer which accepts the message from the (session) layer then breaks the message into smaller units. Each of the segments produced has the header associated with it. The transport layer at the destination station then reassembles the message.
- Service Point Addressing: In order to deliver message to correct process, transport layer header includes the type of address which is known as service point address or port address. Thus by specifying this address, transport layer makes sure that the message is delivered to a correct process.
The services provided by transport layer as follows:
- Connection Oriented Service: It is a three-phase processes which includes
– Connection Establishment
– Data Transfer
– Termination / disconnection
In this type of transmission, the receiving device sends an acknowledgment, back to the source after a packet or group of packet is received. This type of transmission is reliable and secure. - Connection less service: It is a one phase process and includes Data Transfer. In this type of transmission, the receiver does not acknowledge receipt of a packet. This approach allows for much faster communication between devices. Connection oriented Service is more reliable than connection less Service.
Session Layer (Layer 5):
The session layer is responsible for establishment of the connection and the maintenance of sessions, authentication and also it ensures security.
The functions of the session layer are as follows:
- Session establishment, maintenance and termination: This layer allows the two processes to establish the use and then terminate a connection.
- Synchronization: The session layer allows a process to add checkpoints which are considered as a synchronization points into data. These synchronization point help to identify the error so that the data can be re-synchronized properly, and ends of the messages are not cut prematurely and then data loss is avoided.
- Dialog Controller: The session layer allows the two systems to start communication with each other in half-duplex or in full-duplex.
Presentation Layer (Layer 6):
Presentation layer is also known as Translation layer. The data which is from the application layer is extracted here and then manipulated as per the required format to transmit over the network.
The functions of the presentation layer are as follows:
- Translation: For instance ASCII to EBCDIC.
- Encryption/ Decryption: Data encryption which translates the data into another form or code. The encrypted data is called the cipher text and the decrypted data is called plain text. A key value which is used for encrypting as well as decrypting the data.
- Compression: Reduces the number of bits which need to be transmitted on the network.
Application Layer (Layer 7):
The very top layer of the OSI Reference Model is Application layer which is implemented by the network applications. The applications produce the data, which has to be transferred over the network. The application layer also serves as a window for the application services to access network and for displaying received information to the user.
Example - Application – Browsers, Skype Messenger etc.
The functions of the Application layer are as follows:
- Network Virtual Terminal
- FTAM-File transfer access and management
- Mail Services
- Directory Services
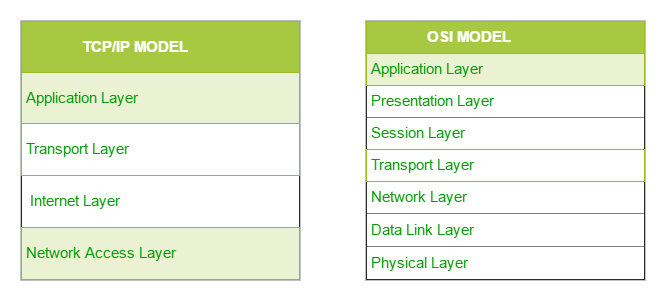
TCP/IP model was designed and developed by Department of Defence (DoD) in 1960s and is based on standard protocols. It is known as Transmission Control Protocol/Internet Protocol. The TCP/IP model is a concise version of the OSI model. It has four layers, unlike the seven layers of the OSI model. The layers are as follows:
- Process/Application Layer
- Host-to-Host/Transport Layer
- Internet Layer
- Network Access/Link Layer
The diagrammatic comparison of the TCP/IP and OSI model:
TCP/IP | OSI |
TCP stands for Transmission Control Protocol. | OSI stands for Open Systems Interconnection. |
Have 4 layers. | Have 7 layers. |
More reliable | Less reliable |
IT does not have very strict boundaries. | IT has strict boundaries |
IT follows a horizontal approach. | IT follows a vertical approach. |
IT uses both session and presentation layer in the application layer itself. | IT uses different session and presentation layers. |
IT developed protocols then model. | IT developed model then protocol. |
References:
- Data Communication & Networking by Forouzan, Tata McGraw Hill.
- Computer Network, 4e, by Andrew S. Tenenbaum, Pearson Education/ PHI.
- Data Communication and Computer Networks, by Prakash C.Gupta, PHI.
- Networking Ali-in-one Desk Reference by Doug Lowe, Wiley Dreamtech
- Computer Networking: A Top-Down Approach featuring the Internet, 3e by James F.Kurose.
- Computer Network by Godbole, Tata McGraw Hill.
- Computer Networking, by Stanford H. Rowe, Marsha L. Schuh