UNIT 6
Bridges and Layer-2 Switches
The need for bridging devices which arises with the need by communicating with computers located beyond a particular local area network (LAN). Although all the clients (computers) attached to a LAN need not be located in the same room, there are limitations on the distance between clients as well as on the number of clients that can be attached to a single network segment. Bridging devices are used to overcome these limitations and facilitate communication among machines on different floors, different buildings, different cities, and different countries.
Bridging devices are available in a variety of configurations to interconnect multiple local area network segments. The choice of bridging device depends on distance, traffic volume, and complexity of the communication pathways between sites. Commonly used bridging devices are repeaters, bridges, routers, and gateways
Bridge is a networking device which is use to divide a LAN into multiple segment. Bridge works under data link layer of OSI model. Bridge stores the MAC address of PC available in a network. Bridge is use to reduce the traffic.
A bridge provides interconnection with other bridge networks that use the same protocol. Bridge connecting two different networks together and providing communication between them.
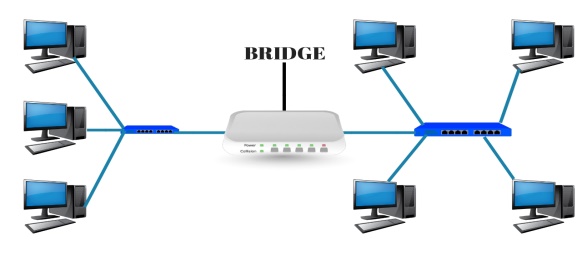
Types of Bridges
There are mainly there types of bridges
- Transparent Bridge – As the name itself tells us that it appears to be transparent for the other device on the network the other devices are ignorant of its existence. It only blocks or forwards the data as per MAC address
- Source Route Bridge – Source Route Bridge derives its name from the fact that the path which packet takes through the network is implanted within the packet it is mainly used in the token ring network.
- Translational bridge – This process of conversion takes place via translational bridge. Translational bridge converts the data format of one networking to another. For Example token ring to Ethernet and vice versa
Features of Bridge
- Network Expansion– It increases the number of attached workstations and network segments
- Frame Buffering–It enables to interconnect the different segments which use different MAC protocols as frames are buffered
- Transparency– It works at the MAC layer and hence are transparent to higher level protocols
- Reliability–It increases network reliability and it makes the network easier to maintain by subdividing LAN into smaller segments which reduces congestion
- Speed – It is slow as compared to a repeater as it introduces delays due to buffering of frames.
- Overload –Gates Overloaded during periods of high traffic
- Expensive– Expensive than repeaters
- No filtering–It provides no filtering of the broadcast frames
Spanning tree protocol (STP) which is a Layer 2 network protocol and is used to prevent looping within a network topology. It was created to avoid the problems that arise when the computers compete for the ability which is use to share the telecommunications path on a local area network (LAN). When many computers will try to send at the same time, the overall network performance is affected and it can bring all traffic to a near halt.
STP advantages/disadvantages
Advantages
- It is easy to use.
- Proven technology.
- It offers wide support for bridges and switches.
- It can provide link redundancy while simultaneously preventing undesirable loops.
- It offers various backups that become active if the main connection experiences hiccups.
Disadvantages
- As the data centres increase use of virtualization technology, STP may not be able to handle increased input/output (I/O) demands.
- The full network capacity is not realized when using STP. Even when there is equal-cost multiple paths on a network, all traffic flows along a single path and as defined by a spanning tree. This restriction of the traffic means alternative, and perhaps more direct, paths are blocked.
- It is developed as a bridge protocol for token ring LANS.
- Source Routing gain Popularity due to IBM support of it.
- Source route network is easy to install.
- Source route network into a large network is not easy to grow.
- Invented due to technical limitations of the source route chip set. Early source route chip set could not be set for promiscuous mode.
- Source routing was also invented which allows two non-routing protocols which are to be placed on a LAN: NETBIOS and SNA.
- It does not build forwarding tables which is based on MAC addresses.
Features of Source Routing Bridge
- Source routing will require split intelligence which is to be carried in the node and that of the bridge.
- All frames are containing routing information, which will produce more overhead.
- Uses STA to configure which bridges will forward single route broadcast frames.
- All paths are active which legally allows loops to be designed.
- Provided a routing solution for those protocols that could not be routed(NetBIOS)
- Source routing originated as an alternative to that of the transparent bridging.
Route discovery allows any of the host in the ad hoc network to dynamically discover the route to any of the other hosting to that of the ad hoc network, whether it is directly reachable within the wireless transmission range or can be reachable through one or more intermediate network hops through the other hosts. A host initiating a route discovery broadcasts for a route request packet which may be received by that of the hosts within the wireless transmission range of it. The route request packet will identifies the host which is referred to as thetargetof the route discovery, for which the routeis requested. If that of the route discovery is successful the initiating host will receives aroute replypacket listing to asequence of network hops through which it can reach the target. In addition to that of the address of the original initiator of that of the request and the target of that of the request, each routerequest packet will contain aroute record, in which it is accumulated and a record of the sequence of hops taken by that of theroute request packet as it is propagated through that of the ad hoc network during the route discovery. Each routerequest packet which also contains a uniquerequest id and is set by the initiator from that of the locally-maintained sequencenumber. In order to detect that the duplicate route requests are received, each host in the ad hoc network will maintains alist of theinitiator address, request idipairs which has recently received on any of the route request. When any of the host receives a route request packet, it then processes the request according to the steps as followed: 1. If the pairinitiator address, request idifor this route request is found in this host’s list of recentlyseen requests, then discard the route request packet and do not process it further.2. Otherwise, if this host’s address is already listed in the route record in the request, then it will discard theroute request packet and then do not process it further.3. Otherwise, if the target of the request matches this host’s own address, then the route record which is in thepacket contains the route by which to that of the request reached this host from that of the initiator of route request. Return a copy of that route in aroute replypacket to that of the initiator.4. Otherwise, append this host’s own address to the route record in the route request packet;andre-broadcast the request. The route request will thus propagates through that of the ad hoc network until it willreached the target host, which thenreplies to that of the initiator. The original route request packet is being received only by those hosts within wirelesstransmission range of that of the initiating host and each of these hosts again propagates the request and if it is not thetarget and if the request will not appear to this host to be redundant. Discarding the request becausethe host’s address is already listed in the route record guarantees that no single copy of the request canpropagate around a loop. Also discarding the request when the host has recently seen one with the sameinitiator address, request idiremoves later copies of the request that arrive at this host by a different route. IN order to return theroute replypacket to the initiator of the route discovery, the target host must have aroute to the initiator. If the target will have an entry for the destination in its route cache, then it can send the route reply packet using the route in the same way as is used in sending any other packet. Otherwise, the target will reverse the route in the route record from the route request packet, and use this type of route to sendthe route reply packet. This, however will require the wireless network to communicate between each of thesepairs of hosts which work equally well in both of the directions, which is not true in some of the environments or withsome MAC-level protocols. An alternative approach, and the one which we have currently adopted, is for thishost to piggyback to that of the route reply packet on a route request targeted at the initiator of that the route discovery towhich it is going to reply. This use of piggybacking.
Switch is a layer 2 device that works on the basis of the MAC address (physical address) of a device. Switch mainly performs the following functions:
- Learning – The switch that learns the MAC address of the device is on the switch port on which it receives frame.
- Forwarding –The switch works on 2 types of message forwarding:
(a) Unicast: The switch unicast the frame to that of the destination only when it has an allowed entry for destination MAC address in its MAC address table.
(b) Unknown Unicast: When a switch receives a unicast frame for that of a destination for which switch has no entry allowed in its MAC table then the switch simply broadcast the frame through all the ports. This is called flooding. - Filtering – The frame will be forwarded through that of the switch port only for which the switch has already learned the MAC address in its MAC table.
- Loop avoidance – For redundancy, two of the switches are connected to each other through two of the links which can also result in layer 2 loops. These loops are avoided by switch and then using STP (Spanning tree protocol) protocol.
References:
- Data Communication & Networking by Forouzan, Tata McGraw Hill.
- Computer Network, 4e, by Andrew S. Tenenbaum, Pearson Education/ PHI.
- Data Communication and Computer Networks, by Prakash C.Gupta, PHI.
- Networking Ali-in-one Desk Reference by Doug Lowe, Wiley Dreamtech
- Computer Networking: A Top-Down Approach featuring the Internet, 3e by James F.Kurose.
- Computer Network by Godbole, Tata McGraw Hill.
- Computer Networking, by Stanford H. Rowe, Marsha L. Schuh
UNIT 6
Bridges and Layer-2 Switches
The need for bridging devices which arises with the need by communicating with computers located beyond a particular local area network (LAN). Although all the clients (computers) attached to a LAN need not be located in the same room, there are limitations on the distance between clients as well as on the number of clients that can be attached to a single network segment. Bridging devices are used to overcome these limitations and facilitate communication among machines on different floors, different buildings, different cities, and different countries.
Bridging devices are available in a variety of configurations to interconnect multiple local area network segments. The choice of bridging device depends on distance, traffic volume, and complexity of the communication pathways between sites. Commonly used bridging devices are repeaters, bridges, routers, and gateways
Bridge is a networking device which is use to divide a LAN into multiple segment. Bridge works under data link layer of OSI model. Bridge stores the MAC address of PC available in a network. Bridge is use to reduce the traffic.
A bridge provides interconnection with other bridge networks that use the same protocol. Bridge connecting two different networks together and providing communication between them.
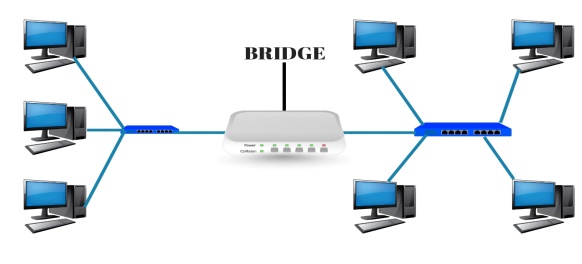
Types of Bridges
There are mainly there types of bridges
- Transparent Bridge – As the name itself tells us that it appears to be transparent for the other device on the network the other devices are ignorant of its existence. It only blocks or forwards the data as per MAC address
- Source Route Bridge – Source Route Bridge derives its name from the fact that the path which packet takes through the network is implanted within the packet it is mainly used in the token ring network.
- Translational bridge – This process of conversion takes place via translational bridge. Translational bridge converts the data format of one networking to another. For Example token ring to Ethernet and vice versa
Features of Bridge
- Network Expansion– It increases the number of attached workstations and network segments
- Frame Buffering–It enables to interconnect the different segments which use different MAC protocols as frames are buffered
- Transparency– It works at the MAC layer and hence are transparent to higher level protocols
- Reliability–It increases network reliability and it makes the network easier to maintain by subdividing LAN into smaller segments which reduces congestion
- Speed – It is slow as compared to a repeater as it introduces delays due to buffering of frames.
- Overload –Gates Overloaded during periods of high traffic
- Expensive– Expensive than repeaters
- No filtering–It provides no filtering of the broadcast frames
Spanning tree protocol (STP) which is a Layer 2 network protocol and is used to prevent looping within a network topology. It was created to avoid the problems that arise when the computers compete for the ability which is use to share the telecommunications path on a local area network (LAN). When many computers will try to send at the same time, the overall network performance is affected and it can bring all traffic to a near halt.
STP advantages/disadvantages
Advantages
- It is easy to use.
- Proven technology.
- It offers wide support for bridges and switches.
- It can provide link redundancy while simultaneously preventing undesirable loops.
- It offers various backups that become active if the main connection experiences hiccups.
Disadvantages
- As the data centres increase use of virtualization technology, STP may not be able to handle increased input/output (I/O) demands.
- The full network capacity is not realized when using STP. Even when there is equal-cost multiple paths on a network, all traffic flows along a single path and as defined by a spanning tree. This restriction of the traffic means alternative, and perhaps more direct, paths are blocked.
- It is developed as a bridge protocol for token ring LANS.
- Source Routing gain Popularity due to IBM support of it.
- Source route network is easy to install.
- Source route network into a large network is not easy to grow.
- Invented due to technical limitations of the source route chip set. Early source route chip set could not be set for promiscuous mode.
- Source routing was also invented which allows two non-routing protocols which are to be placed on a LAN: NETBIOS and SNA.
- It does not build forwarding tables which is based on MAC addresses.
Features of Source Routing Bridge
- Source routing will require split intelligence which is to be carried in the node and that of the bridge.
- All frames are containing routing information, which will produce more overhead.
- Uses STA to configure which bridges will forward single route broadcast frames.
- All paths are active which legally allows loops to be designed.
- Provided a routing solution for those protocols that could not be routed(NetBIOS)
- Source routing originated as an alternative to that of the transparent bridging.
Route discovery allows any of the host in the ad hoc network to dynamically discover the route to any of the other hosting to that of the ad hoc network, whether it is directly reachable within the wireless transmission range or can be reachable through one or more intermediate network hops through the other hosts. A host initiating a route discovery broadcasts for a route request packet which may be received by that of the hosts within the wireless transmission range of it. The route request packet will identifies the host which is referred to as thetargetof the route discovery, for which the routeis requested. If that of the route discovery is successful the initiating host will receives aroute replypacket listing to asequence of network hops through which it can reach the target. In addition to that of the address of the original initiator of that of the request and the target of that of the request, each routerequest packet will contain aroute record, in which it is accumulated and a record of the sequence of hops taken by that of theroute request packet as it is propagated through that of the ad hoc network during the route discovery. Each routerequest packet which also contains a uniquerequest id and is set by the initiator from that of the locally-maintained sequencenumber. In order to detect that the duplicate route requests are received, each host in the ad hoc network will maintains alist of theinitiator address, request idipairs which has recently received on any of the route request. When any of the host receives a route request packet, it then processes the request according to the steps as followed: 1. If the pairinitiator address, request idifor this route request is found in this host’s list of recentlyseen requests, then discard the route request packet and do not process it further.2. Otherwise, if this host’s address is already listed in the route record in the request, then it will discard theroute request packet and then do not process it further.3. Otherwise, if the target of the request matches this host’s own address, then the route record which is in thepacket contains the route by which to that of the request reached this host from that of the initiator of route request. Return a copy of that route in aroute replypacket to that of the initiator.4. Otherwise, append this host’s own address to the route record in the route request packet;andre-broadcast the request. The route request will thus propagates through that of the ad hoc network until it willreached the target host, which thenreplies to that of the initiator. The original route request packet is being received only by those hosts within wirelesstransmission range of that of the initiating host and each of these hosts again propagates the request and if it is not thetarget and if the request will not appear to this host to be redundant. Discarding the request becausethe host’s address is already listed in the route record guarantees that no single copy of the request canpropagate around a loop. Also discarding the request when the host has recently seen one with the sameinitiator address, request idiremoves later copies of the request that arrive at this host by a different route. IN order to return theroute replypacket to the initiator of the route discovery, the target host must have aroute to the initiator. If the target will have an entry for the destination in its route cache, then it can send the route reply packet using the route in the same way as is used in sending any other packet. Otherwise, the target will reverse the route in the route record from the route request packet, and use this type of route to sendthe route reply packet. This, however will require the wireless network to communicate between each of thesepairs of hosts which work equally well in both of the directions, which is not true in some of the environments or withsome MAC-level protocols. An alternative approach, and the one which we have currently adopted, is for thishost to piggyback to that of the route reply packet on a route request targeted at the initiator of that the route discovery towhich it is going to reply. This use of piggybacking.
Switch is a layer 2 device that works on the basis of the MAC address (physical address) of a device. Switch mainly performs the following functions:
- Learning – The switch that learns the MAC address of the device is on the switch port on which it receives frame.
- Forwarding –The switch works on 2 types of message forwarding:
(a) Unicast: The switch unicast the frame to that of the destination only when it has an allowed entry for destination MAC address in its MAC address table.
(b) Unknown Unicast: When a switch receives a unicast frame for that of a destination for which switch has no entry allowed in its MAC table then the switch simply broadcast the frame through all the ports. This is called flooding. - Filtering – The frame will be forwarded through that of the switch port only for which the switch has already learned the MAC address in its MAC table.
- Loop avoidance – For redundancy, two of the switches are connected to each other through two of the links which can also result in layer 2 loops. These loops are avoided by switch and then using STP (Spanning tree protocol) protocol.
References:
- Data Communication & Networking by Forouzan, Tata McGraw Hill.
- Computer Network, 4e, by Andrew S. Tenenbaum, Pearson Education/ PHI.
- Data Communication and Computer Networks, by Prakash C.Gupta, PHI.
- Networking Ali-in-one Desk Reference by Doug Lowe, Wiley Dreamtech
- Computer Networking: A Top-Down Approach featuring the Internet, 3e by James F.Kurose.
- Computer Network by Godbole, Tata McGraw Hill.
- Computer Networking, by Stanford H. Rowe, Marsha L. Schuh