UNIT 8
Introduction to Internet Protocol
- IPv4 short form of Internet Protocol Version 4 is the fourth version of the Internet Protocol (IP).
- IP is responsible to deliver the data packets from source host to destination host.
- This delivery is solely based on the IP Addresses in the packet headers.
- The first major version of IP is IPv4.
- IPv4 is a connectionless protocol for use on that ofpacket-switched networks.
IPv4 Header-
Diagram of IPv4 header-
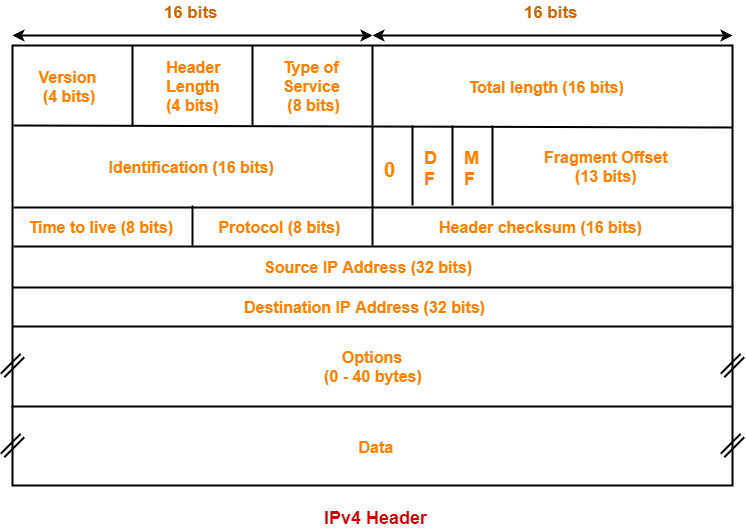
Each field of IPv4 header is explained one by one.
1. Version-
- Version is a 4 bit field that indicates the IP version used.
- The most popularly used IP versions are version-4 (IPv4) and version-6 (IPv6).
- The above header is used by only IPv4.
- So, this field always contains the decimal value 4.
NOTES It is important to note-
|
2. Header Length-
- Header length is a 4 bit field that contains the length of the IP header.
- It helps in knowing from where the actual data begins.
Minimum and Maximum Header Length-
IP header length always lies in the range- [20 bytes , 60 bytes] |
- The initial 5 rows are always used of the IP header.
- So, IP header minimum length is = 5 x 4 bytes = 20 bytes.
- The size of the 6th row representing the Options field varies.
- The size of Options field can go up to 40 bytes.
- So, IP header maximum length is = 20 bytes + 40 bytes = 60 bytes.
Concept of Scaling Factor-
- Header length bit field is 4.
- So, the range of decimal values that can be represented is [0, 15].
- But the header length range is [20, 60].
- So, scaling factor of 4 represent the header length.
In general,
Header length = Header length field value x 4 bytes |
Examples-
- If header length field contains decimal value 5 (represented as 0101), then-
Header length = 5 x 4 = 20 bytes
- If header length field contains decimal value 10 (represented as 1010), then-
Header length = 10 x 4 = 40 bytes
- If header length field contains decimal value of 15 (represented as 1111), then-
Header length = 15 x 4 = 60 bytes
NOTES It is important to note-
While solving questions-
|
3. Type of Service-
- Type of service is an 8 bit field that is used for Quality of Service (QoS).
- The datagram is marked for giving a certain treatment using this field.
4. Total Length-
- Total length bit field is 16 that contain the total length of the datagram (in bytes).
Total length = Header length + Payload length |
- Minimum total length of datagram = 20 bytes (20 bytes header + 0 bytes data)
- Maximum total length of datagram = Maximum value of 16 bit word = 65535 byte
5. Identification-
- 16 bit field is a identification.
- It is used for the identification of the fragments of an original IP datagram.
When an IP datagram is fragmented,
- Each fragmented datagram is assigned the same identification number.
- This number is useful during the re assembly of fragmented datagrams.
- It helps to identify to which IP datagram, the fragmented datagram belongs to.
6. DF Bit-
- The Do Not Fragment bit is a DF bit.
- Its value may be 0 or 1
When DF bit is set to 0,
- It grants the permission to the intermediate devices to fragment the datagram if required.
When DF bit is set to 1,
- It indicates the intermediate devices not to fragment the IP datagram at any cost.
- If network requires the datagram to be fragmented to travel further but settings does not allow its fragmentation, then it is discarded.
- An error message is sent to the sender saying that the datagram has been discarded due to its settings.
7. MF Bit-
- MF bit stands for More Fragments bit.
- Its value may be 0 or 1.
When MF bit is set to 0,
- It indicates to the receiver that the current datagram is either the last fragment in the set or that it is the only fragment.
When MF bit is set to 1,
- It indicates to the receiver that the current datagram is a fragment of some larger datagram.
- They are following more fragment bit.
- MF bit is set to 1 on all the fragments except the last one.
8. Fragment Offset-
- 13 bit field is a Fragment Offset.
- It indicates the position of a fragmented datagram in the original unfragmented IP datagram.
- The first fragmented datagram has a fragment offset of zero.
Fragment offset for a given fragmented datagram = Number of data bytes ahead of it in the original unregimented datagram |
Concept of Scaling Factor-
- We use a scaling factor of 8 for the fragment offset.
- Fragment offset field value is equal to Fragment Offset / 8
Scaling Factor for Fragment Offset need
(if no scaling factor is used)
|
9. Time to Live-
- 8 bit field is Time to live (TTL).
- It indicates the maximum number of hops a datagram can take to reach the destination.
- The main purpose of TTL is to prevent the IP datagrams from looping around forever in a routing loop.
TTL value is decremented by 1 when-
- Datagram takes a hop to any intermediate device having network layer.
- Datagram takes a hop to the destination.
If the value of TTL becomes zero before reaching the destination, then datagram is discarded.
NOTES It is important to note-
|
10. Protocol-
- Protocol is a 8 bit field.
- It tells the network layer at the destination host to which protocol the IP datagram belongs to.
- In other words, it tells the next level protocol to the network layer at the destination side.
- Protocol number of ICMP is 1, IGMP is 2, TCP is 6 and UDP is 17.
Why Protocol Number Is A Part Of IP Header?
Consider-
In such a case,
ICMP > IGMP > UDP > TCP
If protocol number would have been inside the datagram, then-
That is why; a part of IP header is made protocol number. |
11. Header Checksum-
- A 16 bit field is header checksum.
- The entire headercontains the checksum value.
- The checksum value is used for error checking of the header.
At each hop,
- The header checksum is compared with the value contained in this field.
- If header checksum is found to be mismatched, then the datagram is discarded.
- Router updates the checksum field whenever it modifies the datagram header.
The fields that may be modified are-
- TTL
- Options
- Datagram Length
- Header Length
- Fragment Offset
NOTE It is important to note-
|
Also Read-Checksum
12. Source IP Address-
- Source IP Address is a 32 bit field.
- It contains the logical address of the sender of the datagram.
13. Destination IP Address-
- Destination IP Address is a 32 bit field.
- It contains the logical address of the receiver of the datagram.
14. Options-
- A field whose size varies from 0 bytes to 40 bytes is an option.
- This field is used for several purposes such as-
- Record route
- Source routing
- Padding
1. Record Route-
- A record route option is used to record the IP Address of the routers through which the datagram passes on its way.
- When record route option is set in the options field, IP Address of the router gets recorded in the Options field.
NOTE
Explanation-
|
2. Source Routing-
- A source routing option is used to specify the route that the datagram must take to reach the destination.
- This option is generally used to check whether a certain path is working fine or not.
- It may be loose or strict.
3. Padding-
- Addition of dummy data to fill up unused space in the transmission unit and make it conform to the standard size is known as padding.
- Padding is used for options field.
Example-
- When header length is not a multiple of 4, extra zeroes are padded in the Options field.
- Header length becomes a multiple of 4 by doing this.
- If header length is 30 bytes, 2 bytes of dummy data is added to the header.
- This makes header length is 32 bytes.
- Then, the value 32 / 4 = 8 is put in the header length field.
- In worst case, 3 bytes of dummy data might have to be padded to make the header length a multiple of 4.
Since IP does not have an inbuilt mechanism for sending error and control messages. To provide an error control it depends on Internet Control Message Protocol (ICMP). ICMP is used for reporting errors and queries of management. It is a supporting protocol and it is used by network devices like routers for sending the messages of errors and operations information.
For Example: the requested service is not available or that a host or router could not be reached.
Source quench message:
Source quench message is a request to decrease the traffic rate for messages which are sending to the host (destination). Or we can say that when the receiving host detects that rate of sending packets (traffic rate) is too fast then it sends the source quench message to the source to slow down the pace so that no packet can be lost.
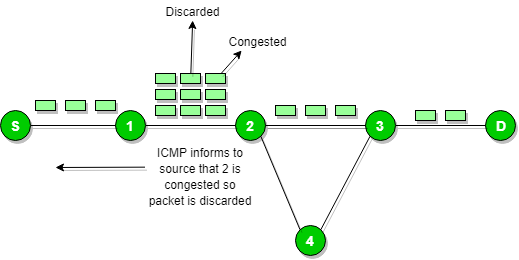
ICMP will take source IP address from the discarded packet and then informs to the source by sending source quench message.Then source will slow down the speed of transmission so that router will free for congestion.
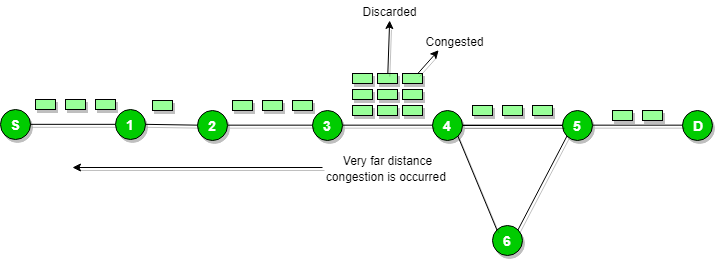
When the congestion router is far away from the source router then the ICMP will send hop by hop source quench message so that every router will slow down the speed of transmission.
Parameter problem:
Whenever packets come to the router end then the calculated header checksum should be equal to that of received header checksum then only packet is acceptable by the router.
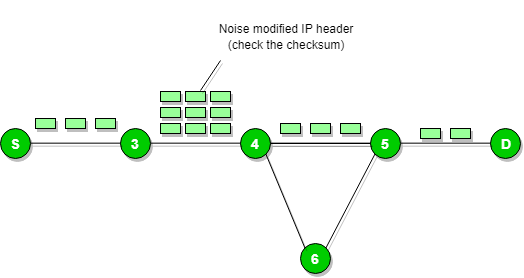
If there is any mismatch then packet will be dropped by the router.
ICMP will take the source IP address from the discarded packet and then it informs to source by sending the parameter problem message.
Time exceeded message:
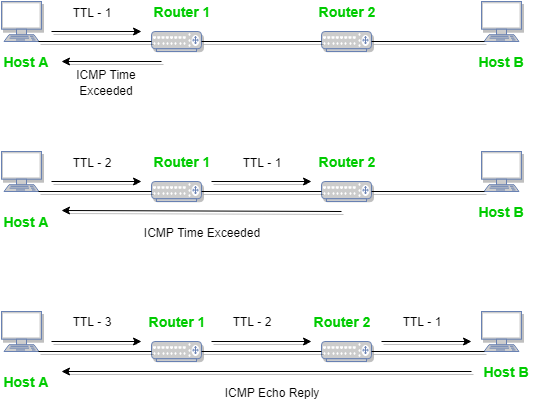
When some of the fragments are lost in a network then the holding fragment by that of the router will be dropped and then the ICMP will take source IP address from discarded packet and then it informs to the source, of discarded datagram due to time to live field reaches to by zero, by sending time exceeded message.
Destination un-reachable:
Destination unreachable will be generated by the host or its inbound gateway so that it informs to the client that the destination is unreachable for some reason.
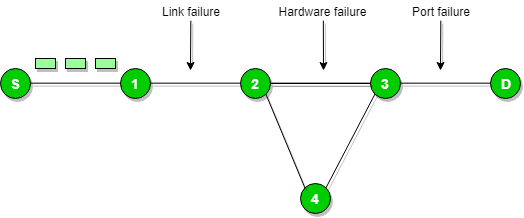
There is no necessary condition takes place that only router will give the ICMP error message some time the destination host send ICMP error message when any type of failure like (link failure or hardware failure or port failure etc.) happens in the network.
Redirection message:
Redirect requests data packets to be sent on an alternate route. The message informs to its host to update its routing information (to send packets on an alternate route).
Example: If host tries to send data through a R1 router and R1 sends data on a R2 router and there is a direct way from host to R2. Then R1 will send a redirect message to inform the host that there is a best way to the destination directly through R2 available. The host then sends data packets for the destination directly to R2.
The router R2 will send the original datagram to the intended destination.
But if datagram contains routing information then this message will not be sent even if better route is available as it redirects should only be sent by that of the gateways and should not be sent by Internet hosts.
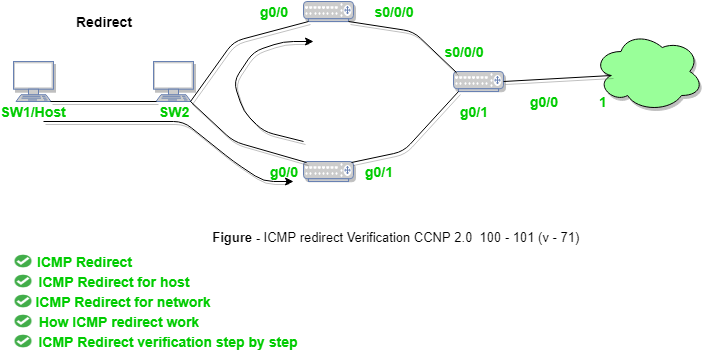
Whenever a packet is forwarded in a wrong direction then later on it is re-directed again in a current direction then ICMP will send re-directed message
References:
- Data Communication & Networking by Forouzan, Tata McGraw Hill.
- Computer Network, 4e, by Andrew S. Tenenbaum, Pearson Education/ PHI.
- Data Communication and Computer Networks, by Prakash C.Gupta, PHI.
- Networking Ali-in-one Desk Reference by Doug Lowe, Wiley Dreamtech
- Computer Networking: A Top-Down Approach featuring the Internet, 3e by James F.Kurose.
- Computer Network by Godbole, Tata McGraw Hill.
- Computer Networking, by Stanford H. Rowe, Marsha L. Schuh
UNIT 8
Introduction to Internet Protocol
- IPv4 short form of Internet Protocol Version 4 is the fourth version of the Internet Protocol (IP).
- IP is responsible to deliver the data packets from source host to destination host.
- This delivery is solely based on the IP Addresses in the packet headers.
- The first major version of IP is IPv4.
- IPv4 is a connectionless protocol for use on that ofpacket-switched networks.
IPv4 Header-
Diagram of IPv4 header-
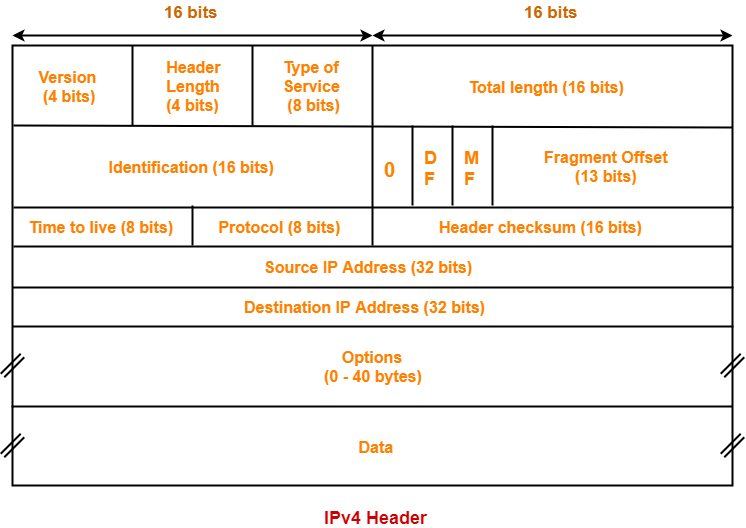
Each field of IPv4 header is explained one by one.
1. Version-
- Version is a 4 bit field that indicates the IP version used.
- The most popularly used IP versions are version-4 (IPv4) and version-6 (IPv6).
- The above header is used by only IPv4.
- So, this field always contains the decimal value 4.
NOTES It is important to note-
|
2. Header Length-
- Header length is a 4 bit field that contains the length of the IP header.
- It helps in knowing from where the actual data begins.
Minimum and Maximum Header Length-
IP header length always lies in the range- [20 bytes , 60 bytes] |
- The initial 5 rows are always used of the IP header.
- So, IP header minimum length is = 5 x 4 bytes = 20 bytes.
- The size of the 6th row representing the Options field varies.
- The size of Options field can go up to 40 bytes.
- So, IP header maximum length is = 20 bytes + 40 bytes = 60 bytes.
Concept of Scaling Factor-
- Header length bit field is 4.
- So, the range of decimal values that can be represented is [0, 15].
- But the header length range is [20, 60].
- So, scaling factor of 4 represent the header length.
In general,
Header length = Header length field value x 4 bytes |
Examples-
- If header length field contains decimal value 5 (represented as 0101), then-
Header length = 5 x 4 = 20 bytes
- If header length field contains decimal value 10 (represented as 1010), then-
Header length = 10 x 4 = 40 bytes
- If header length field contains decimal value of 15 (represented as 1111), then-
Header length = 15 x 4 = 60 bytes
NOTES It is important to note-
While solving questions-
|
3. Type of Service-
- Type of service is an 8 bit field that is used for Quality of Service (QoS).
- The datagram is marked for giving a certain treatment using this field.
4. Total Length-
- Total length bit field is 16 that contain the total length of the datagram (in bytes).
Total length = Header length + Payload length |
- Minimum total length of datagram = 20 bytes (20 bytes header + 0 bytes data)
- Maximum total length of datagram = Maximum value of 16 bit word = 65535 byte
5. Identification-
- 16 bit field is a identification.
- It is used for the identification of the fragments of an original IP datagram.
When an IP datagram is fragmented,
- Each fragmented datagram is assigned the same identification number.
- This number is useful during the re assembly of fragmented datagrams.
- It helps to identify to which IP datagram, the fragmented datagram belongs to.
6. DF Bit-
- The Do Not Fragment bit is a DF bit.
- Its value may be 0 or 1
When DF bit is set to 0,
- It grants the permission to the intermediate devices to fragment the datagram if required.
When DF bit is set to 1,
- It indicates the intermediate devices not to fragment the IP datagram at any cost.
- If network requires the datagram to be fragmented to travel further but settings does not allow its fragmentation, then it is discarded.
- An error message is sent to the sender saying that the datagram has been discarded due to its settings.
7. MF Bit-
- MF bit stands for More Fragments bit.
- Its value may be 0 or 1.
When MF bit is set to 0,
- It indicates to the receiver that the current datagram is either the last fragment in the set or that it is the only fragment.
When MF bit is set to 1,
- It indicates to the receiver that the current datagram is a fragment of some larger datagram.
- They are following more fragment bit.
- MF bit is set to 1 on all the fragments except the last one.
8. Fragment Offset-
- 13 bit field is a Fragment Offset.
- It indicates the position of a fragmented datagram in the original unfragmented IP datagram.
- The first fragmented datagram has a fragment offset of zero.
Fragment offset for a given fragmented datagram = Number of data bytes ahead of it in the original unregimented datagram |
Concept of Scaling Factor-
- We use a scaling factor of 8 for the fragment offset.
- Fragment offset field value is equal to Fragment Offset / 8
Scaling Factor for Fragment Offset need
(if no scaling factor is used)
|
9. Time to Live-
- 8 bit field is Time to live (TTL).
- It indicates the maximum number of hops a datagram can take to reach the destination.
- The main purpose of TTL is to prevent the IP datagrams from looping around forever in a routing loop.
TTL value is decremented by 1 when-
- Datagram takes a hop to any intermediate device having network layer.
- Datagram takes a hop to the destination.
If the value of TTL becomes zero before reaching the destination, then datagram is discarded.
NOTES It is important to note-
|
10. Protocol-
- Protocol is a 8 bit field.
- It tells the network layer at the destination host to which protocol the IP datagram belongs to.
- In other words, it tells the next level protocol to the network layer at the destination side.
- Protocol number of ICMP is 1, IGMP is 2, TCP is 6 and UDP is 17.
Why Protocol Number Is A Part Of IP Header?
Consider-
In such a case,
ICMP > IGMP > UDP > TCP
If protocol number would have been inside the datagram, then-
That is why; a part of IP header is made protocol number. |
11. Header Checksum-
- A 16 bit field is header checksum.
- The entire headercontains the checksum value.
- The checksum value is used for error checking of the header.
At each hop,
- The header checksum is compared with the value contained in this field.
- If header checksum is found to be mismatched, then the datagram is discarded.
- Router updates the checksum field whenever it modifies the datagram header.
The fields that may be modified are-
- TTL
- Options
- Datagram Length
- Header Length
- Fragment Offset
NOTE It is important to note-
|
Also Read-Checksum
12. Source IP Address-
- Source IP Address is a 32 bit field.
- It contains the logical address of the sender of the datagram.
13. Destination IP Address-
- Destination IP Address is a 32 bit field.
- It contains the logical address of the receiver of the datagram.
14. Options-
- A field whose size varies from 0 bytes to 40 bytes is an option.
- This field is used for several purposes such as-
- Record route
- Source routing
- Padding
1. Record Route-
- A record route option is used to record the IP Address of the routers through which the datagram passes on its way.
- When record route option is set in the options field, IP Address of the router gets recorded in the Options field.
NOTE
Explanation-
|
2. Source Routing-
- A source routing option is used to specify the route that the datagram must take to reach the destination.
- This option is generally used to check whether a certain path is working fine or not.
- It may be loose or strict.
3. Padding-
- Addition of dummy data to fill up unused space in the transmission unit and make it conform to the standard size is known as padding.
- Padding is used for options field.
Example-
- When header length is not a multiple of 4, extra zeroes are padded in the Options field.
- Header length becomes a multiple of 4 by doing this.
- If header length is 30 bytes, 2 bytes of dummy data is added to the header.
- This makes header length is 32 bytes.
- Then, the value 32 / 4 = 8 is put in the header length field.
- In worst case, 3 bytes of dummy data might have to be padded to make the header length a multiple of 4.
Since IP does not have an inbuilt mechanism for sending error and control messages. To provide an error control it depends on Internet Control Message Protocol (ICMP). ICMP is used for reporting errors and queries of management. It is a supporting protocol and it is used by network devices like routers for sending the messages of errors and operations information.
For Example: the requested service is not available or that a host or router could not be reached.
Source quench message:
Source quench message is a request to decrease the traffic rate for messages which are sending to the host (destination). Or we can say that when the receiving host detects that rate of sending packets (traffic rate) is too fast then it sends the source quench message to the source to slow down the pace so that no packet can be lost.
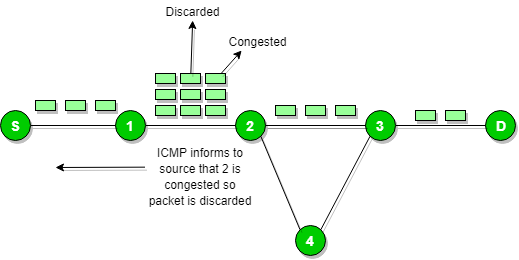
ICMP will take source IP address from the discarded packet and then informs to the source by sending source quench message.Then source will slow down the speed of transmission so that router will free for congestion.
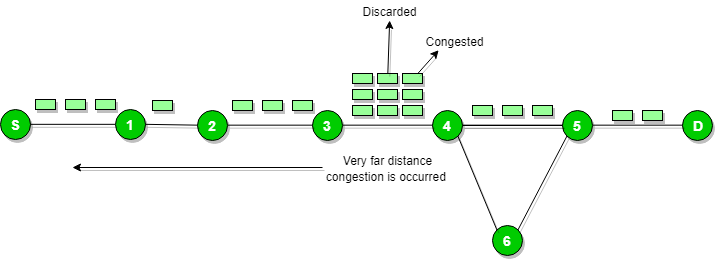
When the congestion router is far away from the source router then the ICMP will send hop by hop source quench message so that every router will slow down the speed of transmission.
Parameter problem:
Whenever packets come to the router end then the calculated header checksum should be equal to that of received header checksum then only packet is acceptable by the router.
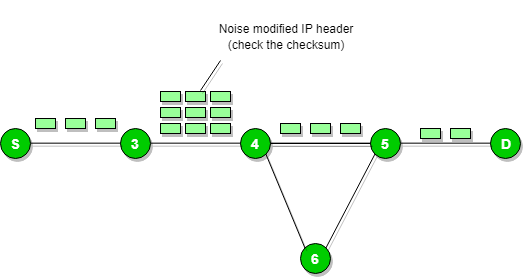
If there is any mismatch then packet will be dropped by the router.
ICMP will take the source IP address from the discarded packet and then it informs to source by sending the parameter problem message.
Time exceeded message:
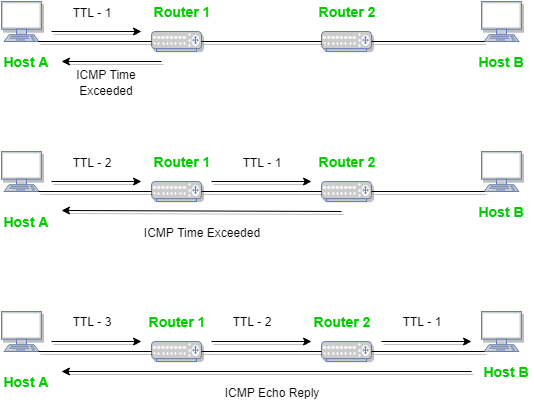
When some of the fragments are lost in a network then the holding fragment by that of the router will be dropped and then the ICMP will take source IP address from discarded packet and then it informs to the source, of discarded datagram due to time to live field reaches to by zero, by sending time exceeded message.
Destination un-reachable:
Destination unreachable will be generated by the host or its inbound gateway so that it informs to the client that the destination is unreachable for some reason.
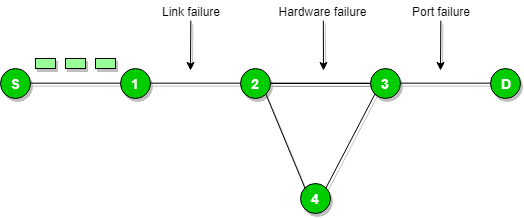
There is no necessary condition takes place that only router will give the ICMP error message some time the destination host send ICMP error message when any type of failure like (link failure or hardware failure or port failure etc.) happens in the network.
Redirection message:
Redirect requests data packets to be sent on an alternate route. The message informs to its host to update its routing information (to send packets on an alternate route).
Example: If host tries to send data through a R1 router and R1 sends data on a R2 router and there is a direct way from host to R2. Then R1 will send a redirect message to inform the host that there is a best way to the destination directly through R2 available. The host then sends data packets for the destination directly to R2.
The router R2 will send the original datagram to the intended destination.
But if datagram contains routing information then this message will not be sent even if better route is available as it redirects should only be sent by that of the gateways and should not be sent by Internet hosts.
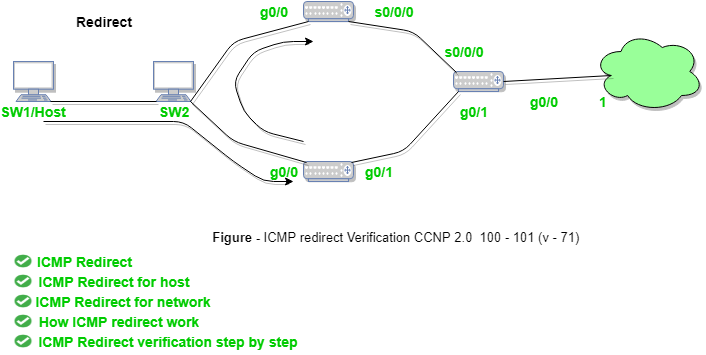
Whenever a packet is forwarded in a wrong direction then later on it is re-directed again in a current direction then ICMP will send re-directed message
References:
- Data Communication & Networking by Forouzan, Tata McGraw Hill.
- Computer Network, 4e, by Andrew S. Tenenbaum, Pearson Education/ PHI.
- Data Communication and Computer Networks, by Prakash C.Gupta, PHI.
- Networking Ali-in-one Desk Reference by Doug Lowe, Wiley Dreamtech
- Computer Networking: A Top-Down Approach featuring the Internet, 3e by James F.Kurose.
- Computer Network by Godbole, Tata McGraw Hill.
- Computer Networking, by Stanford H. Rowe, Marsha L. Schuh