UNIT 4
AUTHENTICATION
Different type’s authentication methods are used to identify the authenticator/ originator of the message.
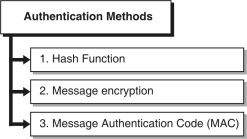
Fig. :Authentication Methods
1. Hash Function
The process of transforming input message m into a fixed size string (called as hash value h) is called as hash function and it is denoted by H. Fixed size hash value act as a authenticator.
2. Message encryption
The cipher text produced after encryption act a authenticator.
3. Message Authentication Code (MAC)
MAC ensures that only receiver can identify the original message. The MessageAuthentication Code (MAC) is a small fixed-size block of data that is generated based on a message M of variable length using secret key K. The fixed size block that serves as the authenticator. Following sections introduces the details on above three functions.
Password Key
Biometrics is the measurement and statistical analysis of people's unique physical and behavioral characteristics. The technology is mainly used for identification and access control, or for identifying individuals who are under surveillance. The basic premise of biometric authentication is that every person can be accurately identified by his or her intrinsic physical or behavioral traits. The term biometrics is derived from the Greek words bio meaning life and metric meaning to measure.
How biometrics work
Authentication by biometric verification is becoming increasingly common in corporate and public security systems, consumer electronics and point-of-sale applications. In addition to security, the driving force behind biometric verification has been convenience, as there are no passwords to remember or security tokens to carry. Some biometric methods, such as measuring a person's gait, can operate with no direct contact with the person being authenticated.
Components of biometric devices include:
- A reader or scanning device to record the biometric factor being authenticated.
- Software to convert the scanned biometric data into a standardized digital format and to compare match points of the observed data with stored data.
- A database to securely store biometric data for comparison.
Biometric data may be held in a centralized database, although modern biometric implementations often depend instead on gathering biometric data locally and then cryptographically hashing it so that authentication or identification can be accomplished without direct access to the biometric data itself.
Types of biometrics
The two main types of biometric identifiers depend on either physiological characteristics or behavioral characteristics.
Physiological identifiers relate to the composition of the user being authenticated and include:
- Facial recognition.
- Fingerprints.
- Finger geometry (the size and position of fingers).
- Iris recognition.
- Vein recognition.
- Retina scanning.
- Voice recognition.
- DNA matching.
Mutual authentication also called as two-factor authentication. Mutual Authentication is a security mechanism used to authenticate sender with the receiver. Sender must prove its identity to a receiver, and the receiver must prove its identity to the sender, before any unwanted threat sent between the sender and receiver.
For example :
If sender wants to communicate with the receiver over networks they must first mutually authenticate each other.
Meaning is that when sender A sends confidential message which is intended to receiver B. If Bcan decrypt the message using A’s public key, then B has verified that the message originated from A.
Both communicating users (sender and receiver) are verifying each other i.e. mutual authentication mechanisms helps to verify identity of the sender.
The most important application of mutual authentication is that communication between client machine and server machine over a network must be secure before performing any data sending and receiving process.
Why there is a Need of Mutual Authentication Protocol?
In order to achieve mutual authentication there must be certain provision of some protocols which suppose to verify identity of the sender over an insecure communication channel.
To achieve this goal most of the protocols depends on an authentication server also called Key Distribution Center (KDC).
If sender A wants to establish a secure communication with receiver B,then A can request for session key from Key Distribution Center for communicating with B.If group of people wants to securely communicate with Key Distribution Center then providing every group member a single key called a master key or secret key. Authentication servers are capable to delivers good quality session keys and distribute securely to client who requested it.
Authentication server also maintains a table containing a name and amaster key or secret key of each client.
The secret key is used to authenticate client to the authentication server and then for securely transmission of data between client and the authentication server. There are different protocols are used to perform this task but among this the well known protocol called as Needham-Schroeder Protocol.
References:
Text Book :
Information Security Principles & Practices by Mark Stamp, Wiley.
Reference Books :
Introduction to Computer Security by Bishop and Venkatramanayya, Pearson Education.
Cryptography and Network Security : Principles and Practice by Stallings, PHI.