UNIT 5
AUTHORIZATION
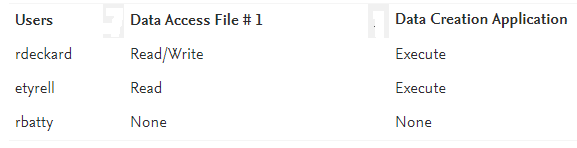
An access control matrix is a table that defines access permissions between specific subjects and objects. A matrix is a data structure that acts as a table lookup for the operating system. For example, Table is a matrix that has specific access permissions defined by user and detailing what actions they can enact. User rdeckard has read/write access to the data file as well as access to the data creation application. User etyrell can read the data file and still has access to the application. User rbatty has no access within this data access matrix.
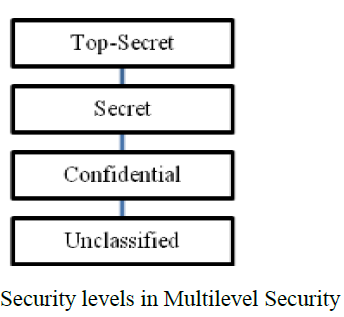
The multilevel security mechanism was originally designed to support military systems and to protect the security and confidentiality of a database. In this mechanism, information is divided into four different security levels according to the
Importance and sensitive degree of information. There are three famous security models based on multilevel security policy that are usually discussed — Bell-LaPadula model, Biba model and Clark-Wilson model .
Multilevel Security (MLS)
The MLS policy was originally designed to support the computer systems in the military sector and to protect the security and their database.
As shown in Figure, the information in MLS is divided into four different security levels based on the information importance and the degree of its sensitive. From low to high grade, the levels contain unclassified level, confidential level, secret level and top-secret level .
MLS systems are very important because:
1. A large amount of research has been done in it, because of military funding for computer science in the USA.
2. Originally multilevel concepts were developed to support confidentiality in military applications, however now multilevel integrity policies are using by
Many commercial systems.
3. Recently, some products like Red Hat Linux and Microsoft Vista have started to use mandatory access control mechanisms.
Analyzing of Multilevel Security Models
A security model is a symbolic representation of a policy. It delineate the require of the policy makers into a set of rules that are to be followed by a computer system. It takes the requirement of the policy and supply the requirement mathematical formulas, relationships, and structure to be go after to achieve the policy goal. There are three multilevel security models which are discussed and analyzed as follow:
The Bell-LaPadula Model
Bell-LaPadula Model (BLP) is the most common and frequently multilevel security model which is used computer . It is a type of computer operating model which used in military sector. The mainly using of this model is to solve the confidential problem of access control. The subjects and objects of this model can be classified by their
Security mark, corresponding to the military security levels. It can effectively prevent information from a high security level flowing to a low one. BLP model is describes a military security strategy for this reason it is executed in a multilevel
Security field with strict security hierarchies. It has already got the special attention from more of the researchers. As a hot research area in the multilevel security field, it has influenced the development of other security models a lot.
The Biba model
It can be define as a lattice-based access control security model dealing with multilevel sensitive information. The main idea of Biba model is to applying information flow policy by using mandatory access control to strengthen discretionary access control. According to mandatory access control policies it
Checks flows of system information to find and to prevent the possible destruction in the system. The subject and object in Biba model has its own integrity level. The higher level data has higher accuracy and reliability than a lower one. Unlike
BLP model the Biba model is used in the commercial applications, the integrity of data is more important than the confidentiality. It based on the integrity level so it is used to solve the integrity problem of applications‘ data, and its access control. The significance of Biba model is to protect the integrity of information system.
The Clark-Wilson model
It focuses on the integrity of information and system. In this model, an agent program is applied to access objects in order to protect the integrity of objects. So the user cannot directly access and control objects. The main idea of Clark-Wilson model is to use benign transaction processing technique and task separation technique
To ensure the consistency of data and the integrity of the transaction. Benign transaction processing technique means that the processing of information has to be restricted in certain of privilege and range. Task separation technique divides a task
Into different task subsets. Every subset has to be done by at least two people. By this technique, personal bluffing can be prevented.
Firewall is called as barrier place between inside and outside network to protect organization from inside and outside hackers. It also filters all traffic between intranet and extranet which runs through it.
The main purpose of the firewall is to keep attackers outside the protected environment. For that policies are set in the firewall to decide what is allowed and what is not allowed. Moreover we can decide the allowed places, allowed users, allowed sites, can provide different access rights to different category of the users.
Ex. :Cyber am through which only educational sites are allowed through college internet and non-educational sites like facebook, twitter can be blocked using firewall.
Firewall Characteristics
Following lists the characteristics as well as design goals for a firewall:
1. All inside and outside traffic must pass through the firewall. This is possible only because of physically blocking of all access to the local network except via the firewall.
2. The traffic defined by the local security policy will only allowed to pass through the network. Different types of firewall are used to define the policies.
3. The firewall itself is immune to penetration. Different techniques are used to control access and enforce the site's security policy.
Service control:This policy helps to determine which type of Internet services that can be accessed inbound and outbound. Firewall can filter traffic on the basis of IP address and TCP port number; it also act as proxy server that receives and interprets each service request before passing it on;
Direction control:Direction control determines the direction in which particular service requests may be initiated and allowed to flow through the firewall.
User control: This technique is used to controls access to a service according to which user is attempting to access it.
Behaviorcontrol:Controls how particular services are used. For example, the firewallmay filter e-mail to eliminate spam. Limitations of Firewall
Limitations:
 Following are the limitations of firewall
Following are the limitations of firewall
1. Viruses
Not all firewalls have full protection against computer viruses because virus uses different encoding techniques to encode files and transfer them over Internet.
2. Attacks
Firewall cant attacks which doesn’t passes through it. There are many ways to bypass firewall.
3. Architecture
Firewall architecture depends upon single security mechanism failure. If that security mechanism has a single point of failure, affects on entire firewall programs which opens the loop falls for intruders.
4. Configuration
Firewall doesn’t have mechanism to tell administrator about incorrect configuration. Only trained professionals in the field of network security can configure firewall properly.
5. Monitoring
Firewall doesn’t give notification about hacking it will notify only about thread occurrences. The reason organization demands additional hardware, software and different networking tools.
6. Encryption
Firewall and Virtual Private Networks (VPNs) don’t encrypt confidential documents and E-mail messages sent within the organization or to outsiders. Dignified procedures and tools are needed to provide protection against confidential documents.
7. Masquerading
Firewalls can’t stop hacker those who steal login id and password of authentic user to gain access to a secure network. Once attacker gains full access of the entire network, attacker can delete or change the network policies of organization.
8. Vulnerabilities:
Firewall can’t tell other venerability that might allow a hacker access to your internal network
Before defining Intrusion Detection first understand what is an Intruder?
An Intruder is a person who intercepts system availability, confidentiality and data integrity. Intruder’s gains unauthorized access to a system with criminal intensions. Intruder may damage that system or disturbs data.
When an attacker or intruder attempts to break into an information system or performs an illegal action such as denial of service attacks, scanning a networks, ping scan, sending many request for connection setup using fake IP address, etc which is legally not allowed, that is called as an intrusion.
Intrusion detection is an important technology that monitors network traffic, events and identifies network intrusions such as abnormal network behaviours, unauthorized network access and malicious attacks to computer systems.
The general example of intrusion detection is when we suffer from some disease and asking doctor what happen to me. Doctor suggests for blood checking and sends blood sample to laboratory for detection.
The blood report given by pathologies is just detection of disease (number of platelets count, WBC, RBC, haemoglobin, etc) then after checking the entire history of blood report doctor suggests medicine to cure the disease.
Here blood report is intrusion detection where as medicine given by the doctor after checking blood report is called intrusion detection system. Finally how fast patient get relief depends upon the doctor’s education, experience and knowledge, joke apart let us move towards technical definition of IDS.
Intrusion Detection system has some policies or mechanisms to protect computer systems from many attacks. As the use of data transmission and receiving over the internet increases the need to protect the data of these connected systems also increases. Many scientists have different definition of IDS but as per our point of view IDS can be defined as below point.
“An Intrusion Detection System is software that monitors the events occur in a computer systems or networks, analyzing what happens during an execution and tries to find out indications that the computer has been misused in order to achieve confidentiality, integrity and availability of a resource or data”.
The IDS will continuously run on our system in the background, and only generate the alert when it detects something suspicious as per its own rules and regulation or attack signature present into it and taking some immediate action to prevent damage.
An Intrusion detection : System examines or monitors system or network activity to find possible attacks on the system or network. Signs of violation of system security policies, standard security practices are analyzed. Intrusion Prevention is the process of detecting intruders and preventing them from intrusive effort to system.
Challenges of intrusion Detection
In order to better understand intrusion detection systems, it is important to realize that threats to networked computer systems come in a number of forms. According to the source of threats, potential intruders can be roughly classified into two categories :
1. Outside Intruders :The attack is launched by an unauthorized computer user. The attacker will stole or broken passwords, using system vulnerabilities or improper configurations, human engineering techniques, to gain access to computers.
2. Inside Intruders :Internal intruders, who have permission to access the system with some restrictions, In this case, the intruder already has legitimate access to a computer system, but utilizes any of the previously mentioned techniques to gain additional privileges and misuse the computer system. Sometimes inside intruders are more harmful than outside intruders. It is observed that 80% of intrusions and attacks come from within organizations.
 Following are the possible type of attacks that intrusion detection need to face.
Following are the possible type of attacks that intrusion detection need to face.
Fig. Type of attacks
1. Denial of Service (DoS) attacks
These attacks attempt to “shut down a network, computer, or process; or otherwise deny the use of resources or services to authorized users”.
There are two types of DoSattacks:
(i) Operating system attacks, which target bugs in specific operating systems and can be fixed with patches;
(ii) Networking attacks, which exploit inherent limitations of networking protocols and infrastructures.
An example of operating system attack is teardrop, in which an attacker exploits a vulnerability of the TCP/IP fragmentation re-assembly code that do not properly handle overlapping IP fragments by sending a series of overlapping packets that are fragmented. Typical example of networking DoS attack is a “SYN flood” attack, which takes advantage of three-way handshake for establishing a connection. In this attack, attacker establishes a large number of “half-open” connections using IP spoofing. The attacker first sends SYN packets with the spoofed (faked) IP address to the victim in order to establish a connection. The victim creates a record in a data structure and responds with SYN/ACK message to the spoofed IP address, but it never receives the final acknowledgment message ACK for establishing the connection, since the spoofed IP addresses are unreachable or unable to respond to the SYN/ACK messages. Although the record from the data structure is freed after a time out period, the attacker attempts to generate sufficiently large number of “half-open” connections to overflow the data structure that may lead to a segmentation fault or locking up the computer.
2. Ping scan
The simplest form of scan, an attacker sends an ICMP echo request packet to every candidate machine (which is the same way the ping tool works). Any addresses that respond are noted as active.
(1) TCP Connect ( ) scan :Another simple scan, an attacker attempts to open a standard TCP connection to a typical port on the candidate machine (such as the HTTP port 80). Any machine where such a connection succeeds is noted as active. Since many systems log any connection attempts, this type of scan is relatively easy to recognize from standard audit data.
(2) UDP scans :This scan consists of sending UDP packets to likely ports on candidate machines at worst, scanning for any open UDP ports. Since UDP is connectionless, such attempts are harder to control using filtering firewalls, and may be capable of finding unprotected services and hosts. Many variations on these scanning techniques exists – including scans using fragmented packets, and scans spread across a long period or a number of source machines. In practice, completely blocking scans is probably infeasible – but may give an administrator early warning of an impending attack.
(3) Rlogin :The RLOGIN attack is characterized by a high rate of connections from one node to another, often within a small period of time. In this attack, the intruder is attempting to gain access to the system.
Need of IDS
Intrusion Detection has its primary goal the detection of abuses of computer systems also it performs a variety of functions like :
Monitoring and analyzing user and system activity.
Auditing system configurations and vulnerabilities.
Assessing the integrity of critical system and data files.
Recognition of activity patterns reflecting known attacks.
Statistical analysis for abnormal activity patterns.
Operating-system audit-trail management, with recognition of user activity reflecting policy violations.
IDS should offer reports of attacks in real time, ideally as the intrusion is in progress allowing security personnel to take corrective action.
IDS should cooperate with other security mechanisms, increasing the overall security of systems. Ideally, IDS should be capable of detecting failures or attacks on other security mechanisms, forming a second level of defense.
IDS should be capable of responding to intrusive behavior: by increasing its monitoring in the relevant sections, or by excluding or restricting intrusive behavior.
IDS should protect itself against attacks, ensuring that the integrity of the greater system, and audit information up to the point of compromise remains intact, and ensuring that a compromised or hostile component cannot adversely affect the functioning of the system as a whole.
Other than monitoring network intruder and policy violations, the IDS can be useful in many other ways.
To identify problem based on security policies.
To maintain the logs of all the threat those are detected by IDS.
As users are monitored continuously in network, making them analyze so that less violations cannot be committed.
Using some preventive measures so that violation cannot be occur like terminating the network connections ,user session or block access to the targets or the accounts that are likely to be violated.
The IDPS (Intrusion Detection and Prevention System) can acts like proxy, which helps in un-packaging the payload of the request and remove header. This helps to invalidate the intruder attacks.
The IDPS can sometimes change the security environment to prevent it from attacks.
References:
Text Book :
Information Security Principles & Practices by Mark Stamp, Wiley.
Reference Books :
Introduction to Computer Security by Bishop and Venkatramanayya, Pearson Education.
Cryptography and Network Security : Principles and Practice by Stallings, PHI.