UNIT 4
APPLICATION LAYER
The Domain Name System (DNS) is the phonebook of the Internet. Humans access information online through domain names, like nytimes.com or espn.com. Web browsers interact through Internet Protocol (IP) addresses.
Domain names are alphabetic and therefore easy to remember, but the Internet is based on numeric IP addresses, so a DNS server is required for computers to communicate with one another. For example, the domain www.example.com might resolve (translate) to 198.105. 232.4.
Dynamic DNS keeps DNS records automatically up to date when an IP address changes.
Dynamic DNS is used in large networks that host internal services, and use their own internal DNS and DHCP servers.
Dynamic DNS Services are used by small companies and individuals when they want to publish a service on the Internet, and that service is hosted within an internal or home network.
Home networks typically uses a NAT router to connect to the internet which means that devices located on the internal network aren’t accessible from the Internet.
Telnet is a network protocol used to virtually access a computer and to provide a two-way, collaborative .
Telnet is a network protocol used to virtually access a computer and to provide a two-way, collaborative and text-based communication channel between two machines. It follows a user command Transmission Control Protocol/Internet Protocol (TCP/IP) networking protocol for creating remote sessions. By default, a telnet server listens on port 23 for incoming connections from clients
Email expedites the exchange of information, removes global barriers, keeps communication costs low and allows business people the flexibility to access their messages from anywhere in the world. As such, companies benefit from the many advantages that email offers.
FTP is short for File Transfer Protocol. A protocol is a set of rules that networked computers use to talk to one another. And FTP is the language that computers on a TCP/IP network (such as the internet) use to transfer files to and from each other.
- It provides the sharing of files.
- It is used to encourage the use of remote computers.
- It transfers the data more reliably and efficiently.
WWW stands for World Wide Web. A technical definition of the World Wide Web is : all the resources and users on the Internet that are using the Hypertext Transfer Protocol (HTTP).
A broader definition comes from the organization that Web inventor Tim Berners-Lee helped found, the World Wide Web Consortium (W3C).
SNMP works by sending messages, called protocol data units (PDUs), to devices within your network that “speak” SNMP. Using these requests, network administrators can track virtually any data values they specify. All of the information SNMP tracks can be provided to a product that asks for it.
SNMP is one of the widely accepted protocols to manage and monitor network elements. Most of the professional–grade network elements come with bundled SNMP agent. These agents have to be enabled and configured to communicate with the network monitoring tools or network management system (NMS).
A Bluetooth® device works by using radio waves instead of wires or cables to connect with your cell phone, smartphone or computer.So when Bluetooth-enabled products, such as a cell phone and headphones, are in close proximity to each other, they connect, or pair.
A firewall is a network security device that monitors incoming and outgoing network traffic and permits or blocks data packets based on a set of security rules. Its purpose is to establish a barrier between your internal network and incoming traffic from external sources (such as the internet) in order to block malicious traffic like viruses and hackers.
A firewall is a system designed to prevent unauthorized access to or from a private network. You can implement a firewall in either hardware or software form, or a combination of both. Firewalls prevent unauthorized internet users from accessing private networks connected to the internet, especially intranets
Cryptography is the study of secure communications techniques that allow only the sender and intended recipient of a message to view its contents. ... When transmitting electronic data, the most common use of cryptography is to encrypt and decrypt email and other plain-text messages.
Modern cryptography uses sophisticated mathematical equations (algorithms) and secret keys to encrypt and decrypt data. Today, cryptography is used to provide secrecy and integrity to our data, and both authentication and anonymity to our communications.
Three types of cryptography: secret-key, public key, and hash function.
'Cryptography in everyday life' contains a range of situations where the use of cryptography facilitates the provision of a secure service: cash withdrawal from an ATM, Pay TV, email and file storage using Pretty Good Privacy (PGP) freeware, secure web browsing, and use of a GSM mobile phone.
The Hypertext Transfer Protocol (HTTP) is an application-level protocol for distributed, collaborative, hypermedia information systems. This is the foundation for data communication for the World Wide Web (i.e. internet) since 1990. HTTP is a generic and stateless protocol which can be used for other purposes as well using extensions of its request methods, error codes, and headers.
Basically, HTTP is a TCP/IP based communication protocol, that is used to deliver data (HTML files, image files, query results, etc.) on the World Wide Web. The default port is TCP 80, but other ports can be used as well. It provides a standardized way for computers to communicate with each other. HTTP specification specifies how clients' request data will be constructed and sent to the server, and how the servers respond to these requests
Features
There are three basic features that make HTTP a simple but powerful protocol:
- HTTP is connectionless: The HTTP client, i.e., a browser initiates an HTTP request and after a request is made, the client waits for the response. The server processes the request and sends a response back after which client disconnect the connection. So client and server knows about each other during current request and response only. Further requests are made on new connection like client and server are new to each other.
- HTTP is media independent: It means, any type of data can be sent by HTTP as long as both the client and the server know how to handle the data content. It is required for the client as well as the server to specify the content type using appropriate MIME-type.
- HTTP is stateless: As mentioned above, HTTP is connectionless and it is a direct result of HTTP being a stateless protocol. The server and client are aware of each other only during a current request. Afterwards, both of them forget about each other. Due to this nature of the protocol, neither the client nor the browser can retain information between different requests across the web pages.
Basic Architecture
The following diagram shows a very basic architecture of a web application and depicts where HTTP sits:
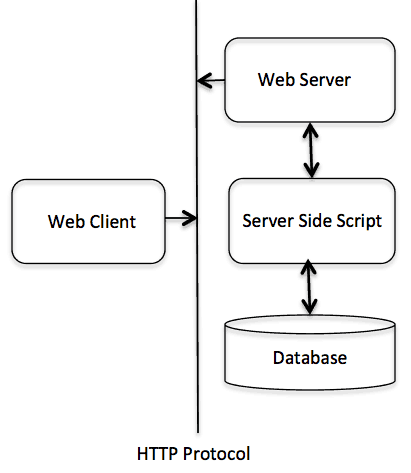
The HTTP protocol is a request/response protocol based on the client/server based architecture where web browsers, robots and search engines, etc. act like HTTP clients, and the Web server acts as a server.
Client
The HTTP client sends a request to the server in the form of a request method, URI, and protocol version, followed by a MIME-like message containing request modifiers, client information, and possible body content over a TCP/IP connection.
Server
The HTTP server responds with a status line, including the message's protocol version and a success or error code, followed by a MIME-like message containing server information, entity meta information, and possible entity-body content.