UNIT 5
NETWORK SECURITY
Active and Passive Attacks are security attacks. In Active attack, an attacker tries to modify the content of the messages. Whereas in Passive attack, an attacker observes the messages, copy them and may use them for malicious purposes.
Two types of passive attacks are the release of message contents and traffic analysis. The release of message content is easily understood. A telephone conversation, an electronic mail message, and a transferred file may contain sensitive or confidential information.
Types of active attacks include:
- Denial of service (DoS)
- Distributed Denial of Service (DDoS)
- Session replay.
- Masquerade.
- Message modification.
- Trojans.
Symmetric encryption is a type of encryption where only one key (a secret key) is used to both encrypt and decrypt electronic information. The entities communicating via symmetric encryption must exchange the key so that it can be used in the decryption process.
There are five main components of a symmetric encryption system: plaintext, encryption algorithm, secret key, ciphertext, and the decryption algorithm.
Blowfish, AES, RC4, DES, RC5, and RC6 are examples of symmetric encryption. The most widely used symmetric algorithm is AES-128, AES-192, and AES-256. The main disadvantage of the symmetric key encryption is that all parties involved have to exchange the key used to encrypt the data before they can decrypt it.
An encryption algorithm along with a key is used in the encryption and decryption of data. There are several types of data encryptions which form the basis of network security.
The Advanced Encryption Standard (AES) is the algorithm trusted as the standard by the U.S. Government and numerous organizations. Although it is extremely efficient in 128-bit form, AES also uses keys of 192 and 256 bits for heavy duty encryption purposes.
A key distribution center is a form of symmetric encryption that allows the access of two or more systems in a network by generating a unique ticket type key for establishing a secure connection over which data is shared and transferred. KDC is the main server which is consulted before communication takes place.
A key distribution center (KDC) is a component in an access control system responsible for servicing user requests to access resources by supplying access tickets and session keys. ... Using the ticket-granting-ticket, the user can access to the TGS and request a ticket to access a specific resource/system.
A malicious user must obtain both the private key and the corresponding passphrase to pose as a legitimate user. Provides stronger identity checking through secret private keys.
Traffic padding is like having a salted hash digest. You are adding additional data in your network traffic to make it more difficult to identify the sender, receiver, and/or the data being transmitted. It's designed to make the traffic look more random, or at least less identifiable.
Message authentication or data origin authentication is a property that a message has not been modified while in transit (data integrity) and that the receiving party can verify the source of the message.
Message authentication is a procedure to verify that received messages come from the alleged source and have not been altered. Message authentication may also verify sequencing and timeliness.
A hash function is a function which when given a key, generates an address in the table. The example of a hash function is a book call number. Each book in the library has a unique call number. A call number is like an address: it tells us where the book is located in the library.
A hash function is a mathematical function that converts an input value into a compressed numerical value – a hash or hash value. Basically, it's a processing unit that takes in data of arbitrary length and gives you the output of a fixed length – the hash value.
Family of SHA comprise of four SHA algorithms; SHA-0, SHA-1, SHA-2, and SHA-3. Though from same family, there are structurally different.
- The original version is SHA-0, a 160-bit hash function, was published by the National Institute of Standards and Technology (NIST) in 1993. It had few weaknesses and did not become very popular. Later in 1995, SHA-1 was designed to correct alleged weaknesses of SHA-0.
- SHA-1 is the most widely used of the existing SHA hash functions. It is employed in several widely used applications and protocols including Secure Socket Layer (SSL) security.
- In 2005, a method was found for uncovering collisions for SHA-1 within practical time frame making long-term employability of SHA-1 doubtful.
- SHA-2 family has four further SHA variants, SHA-224, SHA-256, SHA-384, and SHA-512 depending up on number of bits in their hash value. No successful attacks have yet been reported on SHA-2 hash function.
- Though SHA-2 is a strong hash function. Though significantly different, its basic design is still follows design of SHA-1. Hence, NIST called for new competitive hash function designs.
- In October 2012, the NIST chose the Keccak algorithm as the new SHA-3 standard. Keccak offers many benefits, such as efficient performance and good resistance for attacks.
Public key cryptography uses a pair of keys to encrypt and decrypt data to protect it against unauthorized access or use. Network users receive a public and private key pair from certification authorities.
Public key encryption is a form that uses two keys. One is public, which everyone knows, and one is private, which only you know. ... The most common example of public key encryption is RSA.
Digital signatures employ asymmetric cryptography. ... Digitally signed messages may be anything represent able as a bit string: examples include electronic mail, contracts, or a message sent via some other cryptographic protocol.
The digital signature is used in many forms like digitally signing the document, certificates, signing an email or encrypting the document and message, or it can be the computer. This can be used with any kind of message.
RSA is based on the fact that it is difficult to factorize a large integer. The public key consists of two numbers where one number is multiplication of two large prime numbers. And private key is also derived from the same two prime numbers.
Key management
Key management refers to managing cryptographic keys within a cryptosystem. It deals with generating, exchanging, storing, using and replacing keys as needed at the user level. A key management system will also include key servers, user procedures and protocols, including cryptographic protocol design.
Secure Sockets Layer (SSL) is a protocol developed by Netscape for establishing an encrypted link between a web server and a browser. SSL is an industry standard which transmits private data securely over the Internet by encrypting it.
Secure Sockets Layer (SSL) technology protects transactions between your Web site and visitors. The protocol uses a third party, a Certificate Authority (CA), to identify one end or both end of the transactions. This is in short how it works. A browser requests a secure page (usually https://).
Secure Socket Layer Protocols:
- SSL record protocol
- Handshake protocol
- Change-cipher spec protocol
- Alert protocol
SSL Protocol Stack:
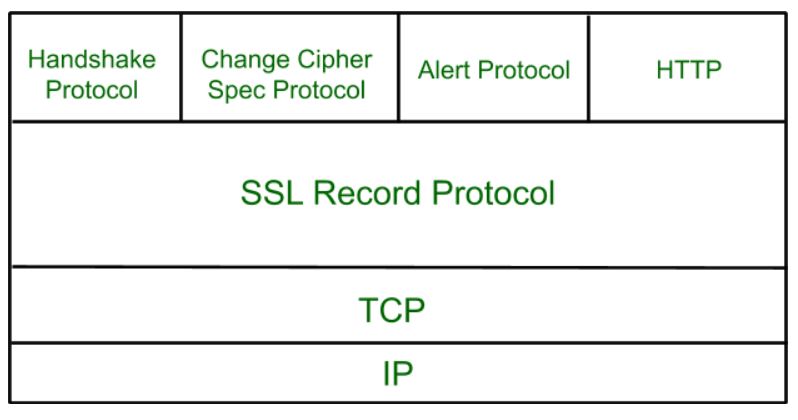
Handshake Protocol is used to establish sessions. This protocol allow client and server to authenticate each other by sending a series of messages to each other. Handshake protocol uses four phases to complete its cycle.
- Phase-1: In Phase-1 both Client and Server send hello-packets to each other. In this IP session, cipher suite and protocol version are exchanged for security purpose.
- Phase-2: Server send his certificate and Server-key-exchange. Server end the phase-2 by sending Server-hello-end packet.
- Phase-3: In this phase Client reply to the server by sending his certificate and Client-exchange-key.
- Phase-4: In Phase-4 Change-cipher suite occurred and after this Handshake Protocol ends.
Change-cipher Protocol:
This protocol uses SSL record protocol. Unless Handshake Protocol is completed, the SSL record Output will be in pending state. After handshake protocol the Pending state is converted into Current state.
Change-cipher protocol consists of single message which is 1 byte in length and can have only one value. This protocol purpose is to cause the pending state to be copied into current state.
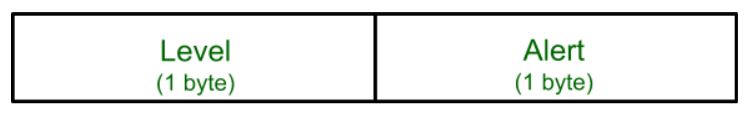
Alert Protocol:
This protocol is used to convey SSL-related alerts to the peer entity. Each message in this protocol contain 2 bytes.
IP security (IPSec)
The IP security (IPSec) is an Internet Engineering Task Force (IETF) standard suite of protocols between 2 communication points across the IP network that provide data authentication, integrity, and confidentiality. It also defines the encrypted, decrypted and authenticated packets. The protocols needed for secure key exchange and key management are defined in it.
Uses of IP Security –
IPsec can be used to do the following things:
- To encrypt application layer data.
- To provide security for routers sending routing data across the public internet.
- To provide authentication without encryption, like to authenticate that the data originates from a known sender.
- To protect network data by setting up circuits using IPsec tunneling in which all data is being sent between the two endpoints is encrypted, as with a Virtual Private Network(VPN) connection.
Components of IP Security –
It has the following components:
- Encapsulating Security Payload (ESP) –
It provides data integrity, encryption, authentication and anti replay. It also provides authentication for payload. - Authentication Header (AH) –
It also provides data integrity, authentication and anti replay and it does not provide encryption. The anti replay protection, protects against unauthorized transmission of packets. It does not protect data’s confidentiality.
Application security
Application security describes security measures at the application level that aim to prevent data or code within the app from being stolen or hijacked. ... Application security may include hardware, software, and procedures that identify or minimize security vulnerabilities.
An application layer is an abstraction layer that specifies the shared communications protocols and interface methods used by hosts in a communications network. The application layer abstraction is used in both of the standard models of computer networking: the Internet Protocol Suite (TCP/IP) and the OSI model.
FIREWALL
Firewall types can be divided into several different categories based on their general structure and method of operation. ... Packet-filtering firewalls. Circuit-level gateways. Stateful inspection firewalls. Application-level gateways (a.k.a. Proxy firewalls)
Three basic types of firewalls —packet filtering, application, and packet inspection—are designed to control traffic flows. The previous descriptions provide general functionality of the operation of these types of firewalls.
A virtual private network (VPN) gives you online privacy and anonymity by creating a private network from a public internet connection. ... Most important, VPN services establish secure and encrypted connections to provide greater privacy than even a secured Wi-Fi hotspot.
Some common disadvantages of VPN services
- A slower internet connection.
- Specific blockades of VPN services (for example by Netflix)
- Illegal use of VPNs themselves.
- Not knowing how strong the encryption provided by your VPN is.
- The logging and potential reselling of your internet habits to third parties.
- Connection breaks.