UNIT 1
BASICS
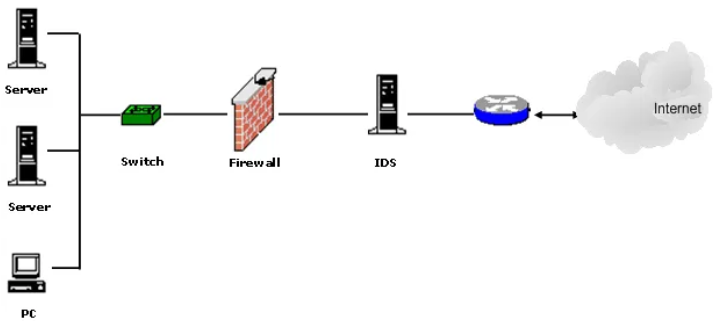
- An intrusion detection system (IDS) monitors network devices so that it can provide security to the administrators by identifying attacks in progress and take appropriate action to protect a network.
- The firewall must allow traffic on a network to access a web server on the internet.
- However, it is used as an attack vector for hackers and malware to gain access the network.
- Hence, IDS examines this traffic and compares it with known exploits; similar to how antivirus software uses known virus signatures to identify threats.
- When a match is detected to a known exploit, it sends an alert signal to the security or web server administrator so that action can be taken.
- Intrusion prevention systems (IPS) not only sends an alert, but these systems go one step further and automatically take action to prevent an intrusion.
- Network Intrusion refers to unauthorized activity within an IT infrastructure network.
- The purpose of unauthorized network activities range from data leaks to network downtime.
- The IDS is configured to detect traffic anomalies in reference to organizational policies of user access and privileges.
- In response to unauthorized network activities and incidents, the IDS system can alert appropriate personnel or technologies to act against the detected threats.
- It is the interface for the packet capture process.
- It starts with the libcap process to capture packets and then display their contents on the screen.
- The processing is then terminated by an interrupt signal (Control-C).
- The program is run at the command line and includes a number of options, which are indicated by flags.
- These flags alter the behavior of the program to get it to select packets that match a specified pattern, limit its running time, or get it to read stored packets from a file rather than from the network interface.
Tcp dump format
Tcpdump <-option_identifier> <option_name> <parameter> <parameter_value> <regular expressions>
Tcp dump options
The command tcp dump is followed by options, which are also known as flags. Each of these is denoted by a hyphen followed by a letter. Below is a list of each of these flags.
-A print packets in ASCII without the link-level headers
-b show the AS number is ASDOT format
-B buffer_size in units of KiB (1024 bytes
-c count – the limit of packets to capture
-C file_size – the process will create a new file once this file size limit is filled; Size is x 1 million bytes
-d Dump the compiled packet-matching code in ASCII
-dd Dump packet-matching code as a C program fragment
-ddd Dump packet-matching code as decimal numbers preceded with a count
-D List all accessible interfaces
-e Print the link-level header on each dump line
-E spi@ipaddr algo:secret – for decrypting IPsec ESP packets:
Spi is the Security Parameter Index
Ipaddr is the destination address on the packet
Algo is the algorithm, defaulted to des-cbc and the field is optional.
Possible values are:
- Des-cbc
- 3des-cbc
- Blowfish-cbc
- Rc3-cbc
- Cast128-cbc
Secret is the ASCII text for ESP secret key. If preceded by 0x, then it is a hex value
-f Print foreign’ IPv4 addresses numerically rather than symbolically
-F file – use file as input for the filter expression
-G rotate_seconds – period to rotate save file of -w option, will add timestamp to name
-h Print the tcpdump and libpcap version strings, print a usage message, and exit
-H Detect 802.11s draft mesh headers
-i interface – the interface on which to listen, defaults to lowest name alphabetically
-I monitor-mode | immediate-mode – removes buffering
-j tstamp_type – set the timestamp type for the capture to tstamp_type
-J tstamp_precision – set the time stamp precision (micro or nano) default is micro. If tstamp_precision is null, list timestamp types and exit
-K Don’t verify checksums
-l Stdout line buffered. E.g. tcpdump -l | tee dat or tcpdump -l > dat & tail -f dat
-L List the known data link types for the interface, in the specified mode, and exit
-m module – load SMI MIB module definitions from file module.
-M secret – shared secret value for validating with the TCP-MD5 option
-n Don’t convert addresses (i.e. host addresses, port numbers, etc.) to names
-N Don’t print domain name qualification of host names
-# Print an optional packet number at the beginning of the line
-O Don’t run the packet-matching code optimizer
-p Don’t put the interface into promiscuous mode
-Q direction – send/receive direction. Can be in, out, or inout
-q Print less protocol information
-r file – read packets from file. Specify – for standard input
-S Print absolute TCP sequence numbers
-s snaplen – snarf snaplen bytes from each packet, not the default 262144 bytes
-T type – interpret packets as the specified type. Options are:
- Aodv Ad-hoc On-demand Distance Vector Protocol
- Carp Common Address Redundancy Protocol
- Cnfp Cisco NetFlow Protocol
- Lmp Link Management Protocol
- Pgm Pragmatic General Multicast
- Pgm_zmtp1 ZMTP/1.0 inside PGM/EPGM)
- Resp REdis Serialization Protocol
- Radius RADIUS
- Rpc Remote Procedure Call
- Rtp Real-Time Applications protocol
- Rtcp Real-Time Applications control protocol
- Snmp Simple Network Management Protocol
- Tftp Trivial File Transfer Protocol
- Vat Visual Audio Tool
- Wb distributed White Board
- Zmtp1 ZeroMQ Message Transport Protocol 1.0
- Vxlan Virtual eXtensible Local Area Network
-t Don’t print a timestamp on each dump line
-tt Print the timestamp as offset since January 1, 1970 on each dump line
-ttt Print a delta (micro-second resolution) between current and previous line
-tttt Print a timestamp: date, hour, minute, second on each dump line
-ttttt Print a delta (micro-second resolution) between current and first line
-u Print undecoded NFS handles
-U Packet buffered
-v Slightly more verbose output
-vv More verbose output
-vvv Most verbose output
-V file – read a list of filenames from file. Standard input is used if file is –
-w file – write output to file
-W limit – the maximum number of files to be created by the -C and -G options
-x Print the data of each packet minus its link level header in hex
-xx Print the data of each packet, including its link level header, in hex
-X Print the data of each packet minus its link level header in hex and ASCII
-XX Print the data of each packet, including its link level header, in hex and ASCII.
-y Set the data link type to use while capturing packets to data link type
-z process save files usually with compression, eg -z gzip
-Z change the user ID to user and the group ID to the primary group of user
References:
- Intrusion Detection & Prevention by Carl Endorf, Eugene Schultz and Jim Mellander, TMH.
2. Implementing Intrusion Detection systems by Tim Crothers, Wiley.