Unit-3
Operational Amplifiers
Block Diagram of op-amp
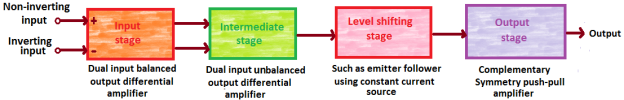
Fig 1: block diagram (Ref: 1)
The block diagram of op-amp consists of :
Non-inverting input
Inverting input
It has a dual input.
It is a differential amplifier which provides balanced output.
It provides voltage gain.
Establishes input resistance of op-amp.
It also has a dual input.
It is a differential amplifier which provides unbalanced output.
The output of the input stage becomes input for the intermediate stage.
Due to direct coupling, the dc voltage is well above 0V.
The output of the intermediate stage becomes input for the level shifting stage.
It is an emitter follower with constant current source.
It is used to shift dc level at the output to 0V wrto ground.
This is the final stage.
It’s a push pull amplifier.
It raises swing in output voltage as well as increases current supply capability of op-amp.
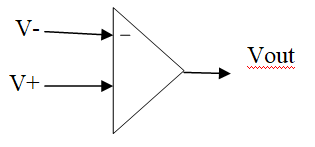
Schematic Symbol
V+ : voltage at inverting input
V- : voltage at non-inverting input
A : voltage gain of op-amp
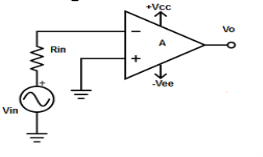
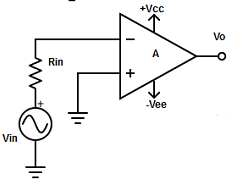
Fig 2: inverting op-amp (Ref: 1)
V1 = 0V and V2 = Vin
Vout = A( - Vin )
where, A is the voltage gain of op-amp.
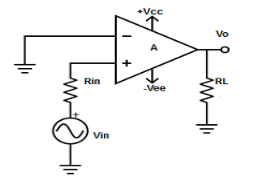
Fig 3: Non inverting amplifier (Ref: 1)
V1 = Vin and V2 = 0V
Vout = AVin
where, A is the voltage gain of op-amp.
A voltage follower also called a unity-gain amplifier, a buffer amplifier, and an isolation amplifier is a op-amp circuit which has a voltage gain of 1.
This means that the op amp does not provide any amplification to the signal. The reason it is called a voltage follower is because the output voltage directly follows the input voltage, meaning the output voltage is the same as the input voltage.
Thus, for example, if 10V goes into the op amp as input, 10V comes out as output. A voltage follower acts as a buffer, providing no amplification or attenuation to the signal.
This high input impedance is the reason voltage followers are used. When a circuit has high input impedance, small current is drawn from the circuit.
In ohm's law, current, I=V/R. Thus, the greater the resistance, the less current is drawn from a power source. Thus, the power of the circuit does not affect when current is feeding a high impedance load.
The below circuit is a circuit in which a power source feeds a low-impedance load.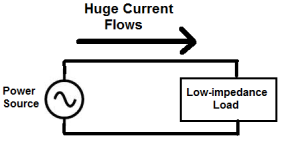
In this circuit above, the load demands and draws a huge amount of current, because the load is low impedance. According to ohm's law, again, current, I=V/R. If a load has too low resistance, it draws huge amounts of current. This causes huge amounts of power to be drawn from the power source and, because of this, causes high disturbances and use of the power source powering the load.
Now let's look at the circuit below, connected to an op-amp voltage follower:
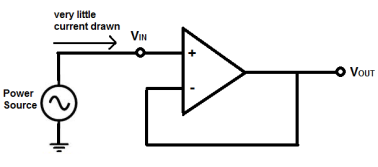
This circuit above now draws less current from the power source above. Because the op amp has such high impedance, it draws less current. And because op amp has no feedback resistors it gives the same output, the circuit outputs the same signal that is fed in.
This is one of the reasons voltage followers are used. They draw little current, not disturbing the original circuit, and give the same voltage signal as output. They act as isolation buffers, isolating a circuit so that the power of the circuit is disturbed too little.
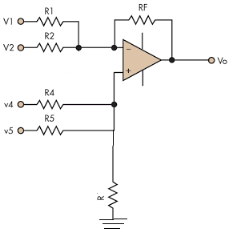
Fig. 4: Summing amplifier (Ref: 1)


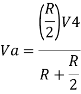
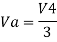
Hence,
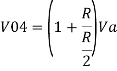
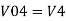
Similarly,
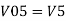
So, the resultant output voltage by all the 4 input voltages is given by,
Vo = V01 + V02 + V04 +V05
Vo = -V1 – V2 +V4 + V5
The output voltage Vo is equivalent to the sum all input voltages applied at both the terminals.
Numerical 1:
In a summing amplifier, if R = 1kΩ, Va = +3V, Vb = +8V, Vc = +9V, Vd = +5V and supply voltage is ±15V. Find the output voltage Vo.
Solution:
Vo = Sum of all input voltages applied at both the terminals
Vo = Va + Vb + Vc +Vd
Vo = -3 -8 +9 +5
Vo = +3V
Numerical 2:
Find the output voltage for the given circuit diagram if Rf = 5kΩ.
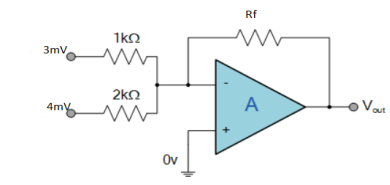
Solution :
We know,
Gain (Av) =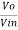 =
= 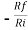
Hence,
Av1 = 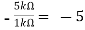
Av2 = 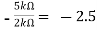
Now, Output voltage Vo = Sum of the two amplified input signals
Vo = Av1 x V1 + Av2 x V2
Vo =(-5 x 3) + ( -2.5x 4) mV
Vo = -25mV
As the above output voltage is negative hence it is an inverting amplifier.
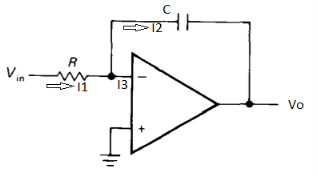
Fig 6 : Integrator
It is a circuit which provides output voltage Vo as an integral form of input voltage Vin.
It is obtained by using an inverting amplifier and replacing its feedback resistor Rf with a capacitor C.
Hence,
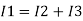
Ignoring I3 we have, I3 ≈ 0
So, I1 ≈ I2.
We know current across the capacitor is given by,
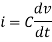
Now by applying Kirchoffs current law,
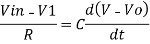
However, V = 0 because gain A is very large
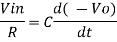
Integrating both sides we get
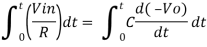
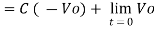
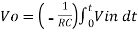 + Q
+ Q
Where Q is the integration constant and is proportional to Vo at t = 0 sec .
Therefore, voltage Vo is directly proportional to Vin and inversely proportional to constant RC.
Frequency response of basic integrator circuit is given by,
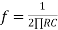 ( for 0 db gain)
( for 0 db gain)
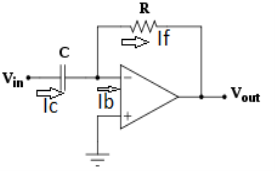
Fig. 7 : Differentiator
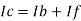
Since Ib = 0 then,
Ic ≈ If
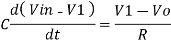
Since Gain A is very large hence, V1 = 0
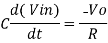
Or 
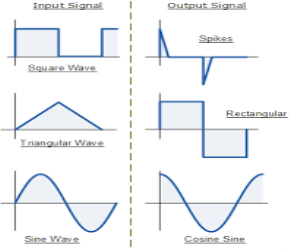
Fig.9: Input and output waveform of differentiator (Ref. 1)
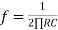 (for 0 db gain)
(for 0 db gain)
IoT (Internet of Things) is an advanced automation and analytics system which exploits networking, sensing, big data, and artificial intelligence technology to deliver complete systems for a product or service. These systems allow greater transparency, control, and performance when applied to any industry or system.
IoT systems have applications across industries through their unique flexibility and ability to be suitable in any environment. They enhance data collection, automation, operations, and much more through smart devices and powerful enabling technology.
IoT systems allow users to achieve deeper automation, analysis, and integration within a system. They improve the reach of these areas and their accuracy. IoT utilizes existing and emerging technology for sensing, networking, and robotics.
IoT exploits recent advances in software, falling hardware prices, and modern attitudes towards technology. Its new and advanced elements bring major changes in the delivery of products, goods, and services; and the social, economic, and political impact of those changes.
IoT − Key Features
The most important features of IoT include artificial intelligence, connectivity, sensors, active engagement, and small device use. A brief review of these features is given below −
1. Smart devices and sensors – Device connectivity
Devices and sensors are the components of the device connectivity layer. These smart sensors are continuously collecting data from the environment and transmit the information to the next layer.
Latest techniques in the semiconductor technology is capable of producing micro smart sensors for various applications.
Common sensors are:
2. Gateway
IoT Gateway manages the bidirectional data traffic between different networks and protocols. Another function of gateway is to translate different network protocols and make sure interoperability of the connected devices and sensors.
Gateways can be configured to perform pre-processing of the collected data from thousands of sensors locally before transmitting it to the next stage. In some scenarios, it would be necessary due to compatibility of TCP/IP protocol.
3. Cloud
Internet of things creates massive data from devices, applications and users which has to be managed in an efficient way. IoT cloud offers tools to collect, process, manage and store huge amount of data in real time. Industries and services can easily access these data remotely and make critical decisions when necessary.
Basically, IoT cloud is a sophisticated high-performance network of servers optimized to perform high speed data processing of billions of devices, traffic management and deliver accurate analytics. Distributed database management systems are one of the most important components of IoT cloud.
4. Analytics
Analytics is the process of converting analog data from billions of smart devices and sensors into useful insights which can be interpreted and used for detailed analysis. Smart analytics solutions are inevitable for IoT system for management and improvement of the entire system.
One of the major advantages of an efficient IoT system is real time smart analytics which helps engineers to find out irregularities in the collected data and act fast to prevent an undesired scenario. Service providers can prepare for further steps if the information is collected accurately at the right time.
5. User interface
User interfaces are the visible, tangible part of the IoT system which can be accessible by users. Designers will have to make sure a well-designed user interface for minimum effort for users and encourage more interactions.
Modern technology offers much interactive design to ease complex tasks into simple touch panels controls. Multicolour touch panels have replaced hard switches in our household appliances and the trend is increasing for almost every smart home device.
Microprocessor | Microcontroller |
Microprocessor is the heart of Computer system. | Micro Controller is the heart of an embedded system. |
It is only a processor, so memory and I/O components need to be connected externally | Micro Controller has a processor along with internal memory and I/O components. |
Memory and I/O has to be connected externally, so the circuit becomes large. | Memory and I/O are already present, and the internal circuit is small. |
You can't use it in compact systems | You can use it in compact systems. |
Cost of the entire system is high | Cost of the entire system is low |
Due to external components, the total power consumption is high. Therefore, it is not ideal for the devices running on stored power like batteries. | As external components are low, total power consumption is less. So it can be used with devices running on stored power like batteries. |
Most of the microprocessors do not have power saving features. | Most of the microcontrollers offer power-saving mode. |
It is mainly used in personal computers. | It is used mainly in a washing machine, MP3 players, and embedded systems. |
Microprocessor has a smaller number of registers, so more operations are memory-based. | Microcontroller has more register. Hence the programs are easier to write. |
Microprocessors are based on Von Neumann model | Micro controllers arc based on Harvard architecture |
It is a central processing unit on a single silicon-based integrated chip. | It is a byproduct of the development of microprocessors with a CPU along with other peripherals. |
It has no RAM, ROM, Input-Output units, timers, and other peripherals on the chip. | It has a CPU along with RAM, ROM, and other peripherals embedded on a single chip. |
It uses an external bus to interface to RAM, ROM, and other peripherals. | It uses an internal controlling bus. |
Microprocessor-based systems can run at a very high speed because of the technology involved. | Microcontroller based systems run up to 200MHz or more depending on the architecture. |
It's used for general purpose applications that allow you to handle loads of data. | It's used for application-specific systems. |
It's complex and expensive, with a large number of instructions to process. | It's simple and inexpensive with less number of instructions to process. |
Bluetooth technology is a high-speed low powered wireless technology link that is designed to connect phones or other portable equipment together. It is a specification (IEEE 802.15.1) for the use of low-power radio communications to link phones, computers, and other network devices over short distances without wires. Wireless signals transmitted with Bluetooth cover short distances, typically up to 30 feet (10 meters).
It is achieved by embedded low-cost transceivers into the devices. It supports the frequency band of 2.45GHz and can support upto 721KBps along with three voice channels. This frequency band has been set aside by international agreement for the use of industrial, scientific, and medical devices (ISM).rd-compatible with 1.0 devices.
It can connect up to “eight devices” simultaneously and each device offers a unique 48-bit address from the IEEE 802 standard with the connections being made a point to point or multipoint.
Working:
Bluetooth Network consists of a Personal Area Network or a piconet which contains a minimum of 2 to a maximum of 8 BlueTooth peer devices- Usually a single master and upto 7 slaves. A master is a device that initiates communication with other devices. The master device governs the communications link and traffic between itself and the slave devices associated with it. A slave device is a device that responds to the master device. Slave devices are required to synchronize they’re transmit/receive timing with that of the masters.
In addition, transmissions by slave devices are governed by the master device (i.e., the master device dictates when a slave device may transmit). Specifically, a slave may only begin its transmissions in a time slot immediately following the time slot in which it was addressed by the master, or in a time slot explicitly reserved for use by the slave device.
The frequency hopping sequence is defined by the Bluetooth device address (BD_ADDR) of the master device. The master device first sends a radio signal asking for a response from the particular slave devices within the range of addresses. The slaves respond and synchronize their hop frequency as well as a clock with that of the master device.
Scatternets are created when a device becomes an active member of more than one piconet. Essentially, the adjoining device shares its time slots among the different piconets.
Wi-Fi is a popular wireless networking technology. Wi-Fi stands for “wireless fidelity”. Wi-Fi was invented by NCR Corporation/AT&T in the Netherlands in 1991. By using this technology, we can exchange information between two or more devices. Wi-Fi has been developed for mobile computing devices, such as laptops, but it is now extensively using for mobile applications and consumer electronics like televisions, DVD players, and digital cameras. There should be two possibilities in communicating with the Wi-Fi connection that may be through an access point to the client connection or client to client connection. Wi-Fi is one type of wireless technology. It is commonly called a wireless LAN (local area network). WiFi technology allows local area networks to operate without cable and wiring. It is making a popular choice for home and business networks. A computer’s wireless adaptor transfers the data into a radio signal and transfers the data into an antenna for users.
Principle:
Wi-Fi is a high-speed internet connection and network connection without the use of any cables or wires. The wireless network is operating three essential elements that are radio signals, antenna, and router. The radio waves are keys that make Wi-Fi networking possible. The computers and cell phones are ready with Wi-Fi cards. Wi-Fi compatibility has been using a new creation to constituent within the ground connected with community network.
The actual broadcast is connected in sequence in fact it is completed by way of stereo system surf as well as the worth of wires with the monitor to classification prone. Wi-Fi allows the person in order to get access to the web any place in the actually provided area. You can now generate a system within Resorts, library, schools, colleges, campus, personal institutes, as well as espresso stores as well as on the open public spot to help to make your company much more lucrative as well as interact with their own customer whenever.
Wi-Fi compatibility can make surf with stare to the company using their inspiring cable television much a smaller amount force down. The radio signals are transmitted from antennas and routers that signals are picked up by Wi-Fi receivers, such as computers and cell phones that are ready with Wi-Fi cards. Whenever the computer receives the signals within the range of 100-150 feet for the router it connects the device immediately.
The range of the Wi-Fi is depended upon the environment, indoor or outdoor ranges. The Wi-Fi cards will read the signals and create an internet connection between the user and the network. The speed of the device using Wi-Fi connection increases as the computer gets closer to the main source and the speed is decreased the computer gets further away.
SecuritySecurity is an important element in Wi-Fi technology. Security is our personal decision but having a wireless connection we should pay attention to protect our private details. We can connect easily to unsecured wireless routers. The problem is anyone is connected to your wireless router using the data like download games, download apps and planning terrorist activities, shirring illegal music and movie files, etc. So it is necessary to provide security to the wireless technologies based devices.
A network is any interconnected group of people or things capable of sharing meaningful information with one another. In a technology context, network is usually short for "computer network" or "data network" and implies that computers are the things sharing the meaningful information.
At a conceptual level, all data networks consist of nodes, which refers to any computer or digital device using the network and links, the physical connections (either wired or wireless) that carry messages between nodes.
Data networks are important to all contemporary organizations because they provide faster, easier access to any message or data that can be represented and stored in digital format.
For example, when your colleagues and predecessors research an issue relevant to your organization and share their data and conclusions with you in a data format your computer recognizes, you can copy key information from their report into your own, saving yourself significant amounts of time (of course, you're always sure to give credit where it's due). If the colleague whose work you're relying on works in the same cubicle as you and they remember where they've stored the relevant report, a network may not offer significant advantages since you can turn to him or her and ask for the file on a CD or USB flash drive. However, in many organizations, large distances separate co-workers, and data sharing becomes a significant logistical problem in the absence of a network.
In addition to data sharing, computer networks also enable resource sharing, an important consideration in all budget-conscious charities and organizations. Rather than buying one printer for every employee and replacing them when they wear out, an organization with a network can buy a single printer, connect it to the network, and configure it in such a way that every computer user in the organization can print to it. The initial cost of a networked printer is usually more than the cost of a single desktop printer, but when considering costs on a per-user basis, the average cost of the networked printer is often much less than the cost of buying a printer for every employee. While some networked devices such as printers, scanners, and fax machines have predetermined, specialized functions, you can also network and share generic, unspecialized computing power in the form of servers. Servers are large, powerful computers that can handle resource-intensive tasks more efficiently than desktop computers. As with the networked printer, the initial outlay for a server is more than that for a desktop computer, but across the organization, it's often cheaper to run the server-based version of a program since individual users won't need expensive, high-performance desktop and laptop computers. Servers can also deploy software to other networked machines at a lower cost.
A sensor node, also known as a mote , is a node in a sensor network that is capable of performing some processing, gathering sensory information and communicating with other connected nodes in the network. A mote is a node but a node is not always a mote.
The main components of a sensor node are a microcontroller, transceiver, external memory, power source and one or more sensors.
"The cloud" refers to servers that are accessed over the Internet, and the software and databases that run on those servers. Cloud servers are located in data centers all over the world. By using cloud computing, users and companies don't have to manage physical servers themselves or run software applications on their own machines.
The cloud enables users to access the same files and applications from almost any device, because the computing and storage takes place on servers in a data center, instead of locally on the user device. This is why a user can log into their Instagram account on a new phone after their old phone breaks and still find their old account in place, with all their photos, videos, and conversation history. It works the same way with cloud email providers like Gmail or Microsoft Office 365, and with cloud storage providers like Dropbox or Google Drive.
For businesses, switching to cloud computing removes some IT costs and overhead: for instance, they no longer need to update and maintain their own servers, as the cloud vendor they are using will do that. This especially makes an impact for small businesses that may not have been able to afford their own internal infrastructure but can outsource their infrastructure needs affordably via the cloud. The cloud can also make it easier for companies to operate internationally, because employees and customers can access the same files and applications from any location.
References:
1 “Electronic devices and circuit theory” by Boylestead and Nashelsky, Pearson
2 “Electronic principle” by Albert Malvino and Davis J Bates, TMH
3 “Integrated Electronics”, By Jacob Millman and Christos Halkias