Unit - 3
Control Unit and Central Processing Unit
The Hardwired Control organization involves the control logic to be implemented with gates, flip-flops, decoders, and other digital circuits.
The following image shows the block diagram of a Hardwired Control organization.
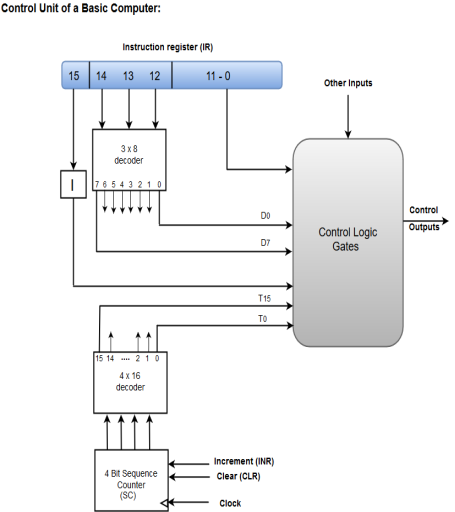
Fig – Control unit of a basic computer
A Hard-wired Control consists of two decoders, a sequence counter, and a number of logic gates.
An instruction fetched from the memory unit is placed in the instruction register (IR).
The component of an instruction register includes; I bit, the operation code, and bits 0 through 11.
The operation code in bits 12 through 14 are coded with a 3 x 8 decoder.
The outputs of the decoder are designated by the symbols D0 through D7.
The operation code at bit 15 is transferred to a flip-flop designated by the symbol I.
The operation codes from Bits 0 through 11 are applied to the control logic gates.
The Sequence counter (SC) can count in binary from 0 through 15.
Key takeaway
The Hardwired Control organization involves the control logic to be implemented with gates, flip-flops, decoders, and other digital circuits.
A sequence of microinstruction constitutes a microprogram.
The use of microprogram involves placing all control variables in words of ROM for use by the control unit through successive read operations.
The content of the word in ROM at a given address specifies a microinstruction.
The basic component of a microprogrammed control unit are the control memory and the circuits that select the next address. This address selection part is known as microprogram sequencer.
A microprogram sequencer can be constructed with digital functions to suit a particular application.
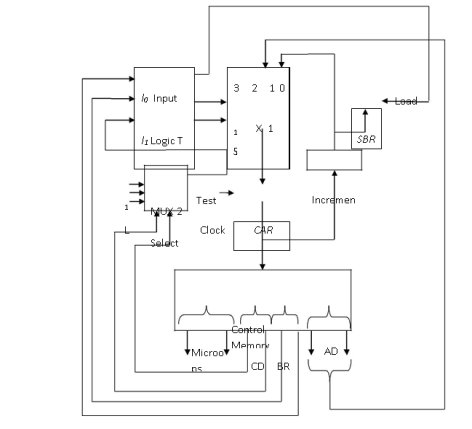
Figure: Micro program sequencer for a control memory
Above figure represents microprogram sequencer, which comprises of two multiplexers.
The first multiplexer selects an address from one of four sources and send it to CAR (Control address register) and the second multiplexer tests the value of a selected status bit and apply it to input logic circuit.
The content of CAR is incremented and applied to one of mux inputs and to the subroutine register SBR.
The other three inputs to multiplexer 1 come from the address field of the present microinstruction, output of SBR, an external source that maps the instruction.
The CD (Condition field) of the microinstruction selects one of the status bits in the second mux, if the bit is 1 variable is 1 else 0.
The T value with the two bits from BR goes to an input logic which will determine the type of operations available in the unit.
BR | Input | MUX 1 | Load SBR | |||
I1 | I0 | T | S1 | S0 | L | |
0 0 | 0 | 0 | 0 | 0 | 0 | 0 |
0 0 | 0 | 0 | 1 | 0 | 1 | 0 |
0 1 | 0 | 1 | 0 | 0 | 0 | 0 |
0 1 | 0 | 1 | 1 | 0 | 1 | 1 |
1 0 | 1 | 0 | X | 1 | 0 | 0 |
1 1 | 1 | 1 | X | 1 | 1 | 0 |
Table: Input logic truth table for microprogram sequencer
Key takeaway
A sequence of microinstruction constitutes a microprogram.
The use of microprogram involves placing all control variables in words of ROM for use by the control unit through successive read operations.
Computer instructions are always stored in sequential memory locations. For processing and execution, these instructions are fetched from different memory regions.
The program counter is advanced by one when an instruction is fetched from memory, pointing to the address of the next successive instruction in the memory. The program control, together with the program counter, which carries the location of the next instruction to be fetched, is returned to the fetch cycle once a data transfer and data manipulation instruction has been executed.
The program control instructions provide the criteria that can change the content of the program counter, whereas the data transfer and manipulation instructions specify the conditions for data processing operations.
An interrupt/break in the execution of instructions can be caused by a change in the content of the program counter. The program control instructions, on the other hand, control the flow of program execution and can branch to different program segments.
The table below lists some of the program control instructions.
Program Control Instructions
Name | Mnemonics |
Branch | BR |
Jump | JMP |
Skip | SKP |
Call | Call |
Return | RET |
Compare (by Subtraction) | CMP |
Test (by ANDing) | TST |
The instruction is a one-address branch. It's written as BR ADR, where ADR stands for address mnemonic. The value of ADR is transferred into the program counter by the branch instruction. The terms "branch" and "leap" are used interchangeably to describe the same thing. However, they can also refer to different addressing modes.
The condition to move the flow of execution is specified by conditional branch instructions such as 'branch if positive' or 'branch if zero.' The branch address is loaded into the program counter when the condition is met.
The conditional branch instructions are shown in the diagram.
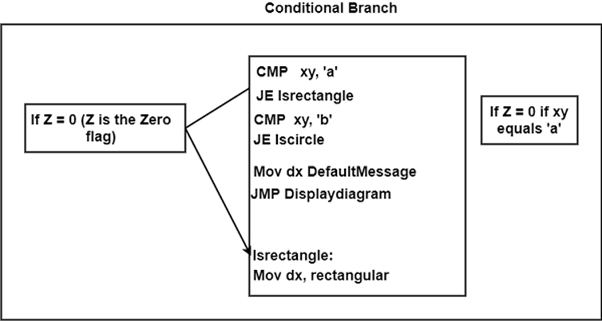
Fig: Conditional branch
Arithmetic subtraction is performed through the compare command. The operation's outcome is not recorded here; instead, the status bit conditions are set. The test instruction modifies the status bits by performing a logical AND operation on two operands.
Reduced Instruction Set Architecture
The main idea behind is to make hardware simpler by using an instruction set composed of a few basic steps for loading, evaluating, and storing operations just like a load command will load data, store command will store the data.
Characteristic of RISC –
- Simpler instruction, hence simple instruction decoding.
- Instruction comes undersize of one word.
- Instruction takes a single clock cycle to get executed.
- More number of general-purpose registers.
- Simple Addressing Modes.
- Less Data types.
- Pipeline can be achieved.
Note- RISC approach- Here programmer will write the first load command to load data in registers then it will use a suitable operator and then it will store the result in the desired location.
RISC processor has 5 stage instruction pipelines to execute all the instructions in the RISC instruction set. Following are the 5 stages of RISC pipeline with their respective operations.
- Stage 1 (Instruction Fetch)
In this stage the CPU reads instructions from the address in the memory whose value is present in the program counter.
- Stage 2 (Instruction Decode)
In this stage, instruction is decoded and the register file is accessed to get the values from the registers used in the instruction.
- Stage 3 (Instruction Execute)
In this stage, ALU operations are performed.
- Stage 4 (Memory Access)
In this stage, memory operands are read and written from/to the memory that is present in the instruction.
- Stage 5 (Write Back)
In this stage, computed/fetched value is written back to the register present in the instructions.
Computing using Complex Instruction Sets, This is a design for a microprocessor. The CISC architecture contains a significant number of computer instructions that range in complexity and specialization from simple to complicated and specialized. Though the design was meant to compute complicated instructions as quickly as possible, it was eventually discovered that numerous little, short instructions could do so more quickly. Reduced Instruction Set Computing (RISC) became the other major type of microprocessor architecture as a result of this. The Intel Pentium CPUs are mostly CISC-based with some RISC features, whereas the PowerPC processors are entirely RISC-based.
The CISC processor architecture's primary goal is to accomplish tasks with fewer assembly lines. The processor is designed to perform a sequence of operations for this goal. The MULT instruction is a complex instruction that operates a computer's memory banks directly without requiring the compiler to execute storing and loading operations.
Features of CISC
• Microprogramming is supported by CISC to simplify the computer architecture.
• Because CISC has a larger number of predefined instructions, it is easier to build and implement high-level languages.
• CISC has fewer registers and a greater number of addressing modes, usually 5 to 20.
• The execution of instructions in a CISC processor requires a variable amount of time – multi-clock cycles.
• The pipelining technique is extremely tough due to the CISC's complicated instruction set.
• CISC has a higher amount of instructions, usually between 100 and 250.
• Only very seldom are special instructions given.
• Instructions manipulate the operands in memory.
Advantages
• Microcode implementation is the process of grouping machine language instructions into microcode instructions, executing them, and then storing them permanently in the main processor's memory.
• Because the microcode memory is quicker than the main memory, the microcode instruction set can be implemented without a significant performance penalty as compared to hardwired implementation.
• Modifying the micro program design can handle an entirely new set of instructions.
• By developing rich instruction sets and making slow main memory more efficient, the number of instructions necessary to implement a program can be lowered in CISC.
• Micro coding is simple due to the superset of instructions that includes all previous instructions.
Disadvantages
• Varying instructions will take different amounts of time on the clock; as a result, the machine's performance will slow.
• Every subsequent generation of the CPU contains a subset of previous generations, increasing the complexity of the instruction set and chip hardware.
• Even though there are numerous specialized instructions that are not even utilized frequently, only 20% of the current instructions are used in a typical programming event.
• The conditional codes are set as a side effect of each CISC instruction, which takes time to complete — and, because the next instruction alters the condition code bits, the compiler must review the condition code bits before proceeding.
A computer is an electronic device that simplifies the completion of any work. In a computer, the CPU follows a set of steps to execute each instruction. This set of steps is known as a Machine Cycle, and it is repeated for each instruction. Fetching instructions, decoding instructions, transferring data, and executing instructions are all part of one machine cycle.
The following are the five basic units of a computer system that assist it in performing operations:
• Input Unit
• Output Unit
• Storage Unit
• Arithmetic Logic Unit
• Control Unit
Input unit
The input device connects the exterior environment to the computer system on the inside. It gives the computer system data and instructions. Keyboards, mice, magnetic tape, and other input devices are commonly utilized.
The input unit is responsible for the following tasks:
• Accept information and instructions from the outside world.
• Convert it to a machine-readable format.
• Provide the computer system with the transformed data.
Output unit
It is a device that connects a computer's internal system to the outside world. It communicates with the outside world the results of any computations or commands. Printers, monitors, and other output devices are examples.
Storage unit
The data and instructions are stored in this unit. Before sending the intermediate results to the output devices, it also saves them. It also saves the information for future use.
A computer system's storage unit can be classified into two types:
Primary storage - This memory is used to save the data that is currently being processed. It is used to store data temporarily. When the computer is turned off, the data is lost. The major storage memory is RAM.
Secondary storage - Secondary memory is less expensive and slower than primary memory. It is used to store data indefinitely. Hard disks, CDs, and other supplementary memory devices are commonly used.
Arithmetic logic unit
The computer system's ALU does all of the calculations. Basic operations like as addition, subtraction, division, and multiplication can be performed using the ALU. The control unit transmits data from the storage unit to the ALU whenever calculations are required. The result is returned to the storage unit once the processes are completed.
Control unit
It is in charge of the computer's other components. It regulates the flow of information and instructions from the storage unit to the ALU. As a result, it's also known as the computer's central nervous system.
Key takeaway
A computer is an electronic device that simplifies the completion of any work. In a computer, the CPU follows a set of steps to execute each instruction. This set of steps is known as a Machine Cycle, and it is repeated for each instruction. Fetching instructions, decoding instructions, transferring data, and executing instructions are all part of one machine cycle.
Data is transferred between memory and processor registers, processor registers and I/O devices, and from one processor register to another via data transfer instructions. There are eight different data transmission instructions that are routinely utilized. A mnemonic symbol is used to represent each instruction.
The eight data transfer instructions are listed in the table, together with their mnemonic symbols.
Data transfer instruction
Name | Mnemonic symbol |
Load | LD |
Store | ST |
Move | MOV |
Exchange | XCH |
Input | IN |
Output | OUT |
Push | PUSH |
Pop | POP |
The following is a description of the instructions:
• Load - Data is transferred from memory to a processor register, which is usually an accumulator, using the load instruction.
• Store - Data is transferred from processor registers to memory using the store instruction.
• Move - The move instruction moves data from one processor register to another, or from one processor register to another, or between processor registers.
• Exchange - The exchange instruction is used to transfer data between two registers or a register and a memory word.
• Input - Data is transferred between the CPU register and the input terminal using the input instruction.
• Output - Data is sent between the processor register and the output terminal using the output instruction.
• Push and pop - Data is transferred between a CPU register and the memory stack using the push and pop commands.
All of these instructions are linked to a number of different addressing modes. To distinguish between the various addressing modes, some assembly language instructions employ different mnemonic symbols.
LDI is an example of a mnemonic symbol for load immediate.
To build efficient assembly language programs for a computer, it is required to be conversant with various addressing modes and different types of instructions.
Key takeaway
Data is transferred between memory and processor registers, processor registers and I/O devices, and from one processor register to another via data transfer instructions. There are eight different data transmission instructions that are routinely utilized. A mnemonic symbol is used to represent each instruction.
Data manipulation instructions allow the computer to execute operations on data and give computational capabilities.
Instructions for data manipulation have computational capabilities. They manipulate data using arithmetic, logic, and shift operations.
The following are three types of data manipulation instructions:
Arithmetic instruction
Addition, subtraction, multiplication, and division are examples of arithmetic operations. Some computers simply supply instructions for addition and subtraction, and these two operations generate multiplication and division operations. A mnemonic symbol is used to represent each instruction.
The following is a description of these instructions:
Increment - The increment instruction increases the value in a register or memory word by one.
Decrement - The decrement instruction reduces the contents of the register or memory word by one.
Arithmetic instruction - For different forms of data, such as floating-point, binary, single-precision, or double-precision data, arithmetic instructions are provided.
The processor status flags or conditional codes are set during the execution of arithmetic instructions to denote the operation's outcome.
Logical and Bit Manipulation Instructions
Binary operations are performed on the bits stored in the registers via logical instructions. Each bit of the operand is handled as a Boolean variable in logical operations. Logical instructions can change the value of a bit, clear a group of bits, or even insert new bit values into operands in registers or memory words. Mnemonic symbols are used to represent each logical instruction.
Name | Mnemonics |
Clear | CLR |
Complement | COM |
AND | AND |
OR | OR |
Exclusive-OR | XOR |
Clear carry | CLRC |
Set carry | SETC |
Complement carry | COMC |
Enable interrupt | EI |
Disable interrupt | DI |
The clear instruction substitutes 0s for the specific operand. The complement instruction produces 1's complement by inverting all of the operand's bits. The AND, OR, and XOR instructions execute logical operations on the operand's bits or groups of bits.
The AND instruction can clear a single operand bit or a group of operand bits. The relationship 'ab0 = 0' and 'ab1 = a' for the Boolean variable a indicates that the binary variable turns to 0 when ANDed with 0.
The OR instruction can be used to set a single operand bit or a group of operand bits. The relationship 'a + 1 =1' and 'a + 0 = a' for the Boolean variable a states that the binary variable changes to 1 when ORed with 1.
An operand's bits can be supplemented using the XOR instruction. The relationship 'a + 1 = a' and 'a + 0 = a' for the Boolean variable a demonstrates that the binary variable is complemented when XORed with 1. When XORed with 0, however, the variable does not change its value.
Clearing, setting, or supplementing the carry bits with relevant instructions is possible. The interrupt facility, which is controlled by flip-flops, can also be enabled or disabled using bit manipulation instructions.
Shift Instructions
The shift instruction allows the bits of an operand to be shifted to the right or left. The shift's orientation is determined by particular instructions. After loading the operand into the accumulator, the shift operation is carried out bit by bit.
The zero is shifted left into low-order empty locations via the shift-left procedure. Zeros are shifted into high-order empty places in shift-right operations. The bits that are moved can be the sign bit's initial value, as in arithmetic right shift, or the bits that are shifted out of a low-order position of the accumulator-extension, as in Rotate Right Accumulator and Extension (RRAE).
Key takeaway
Data manipulation instructions allow the computer to execute operations on data and give computational capabilities.
Instructions for data manipulation have computational capabilities. They manipulate data using arithmetic, logic, and shift operations.
REGISTER ORGANISATION A computer system employs a memory hierarchy. At higher levels of the hierarchy, memory is faster, smaller, and more expensive (per bit). Within the processor, there is a set of registers that function as a level of memory above main memory and cache in the hierarchy.
The registers in the processor perform two roles:
- User-visible registers: Enable the machine- or assembly language programmer to minimize main memory references by optimizing use of registers.
- Control and status registers: Used by the control unit to control the operation of the processor and by privileged, operating system programs to control the execution of programs. User-Visible Registers A user-visible register is one that may be referenced by means of the machine language that the processor executes.
We can characterize these in the following categories:
• General purpose
• Data
• Address
• Condition codes
General-purpose registers can be assigned to a variety of functions by the programmer. Sometimes their use within the instruction set is orthogonal to the operation. That is, any general-purpose register can contain the operand for any opcode. This provides true general-purpose register use. There may be dedicated registers for floating-point and stack operations.
In some cases, general-purpose registers can be used for addressing functions (e.g., register indirect, displacement).
Data registers may be used only to hold data and cannot be employed in the calculation of an operand address.
Address registers may themselves be somewhat general purpose, or they may be devoted to a particular addressing mode.
Examples include the following:
- Segment pointers: In a machine with segmented addressing, a segment register holds the address of the base of the segment.
- Index registers: These are used for indexed addressing and may be auto indexed.
- Stack pointer: If there is user-visible stack addressing, then typically there is a dedicated register that points to the top of the stack. There are several design issues to be addressed here.
An important issue is whether to use completely general-purpose registers or to specialize their use.
Another design issue is the number of registers, general purpose or data plus address, to be provided.
Again, this affects instruction set design because more registers require more operand specifier bits.
Finally, there is the issue of register length. Registers that must hold addresses obviously must be at least long enough to hold the largest address.
Data registers should be able to hold values of most data types. Some machines allow two contiguous registers to be used as one for holding double-length values.
Stack is a storage structure that stores information in such a way that the last item stored is the first item retrieved. It is based on the principle of LIFO (Last-in-first-out). The stack in digital computers is a group of memory locations with a register that holds the address of top of element. This register that holds the address of top of element of the stack is called Stack Pointer.
Stack Operations:
The two operations of a stack are:
- Push: Inserts an item on top of stack.
- Pop: Deletes an item from top of stack.
Implementation of Stack:
In digital computers, stack can be implemented in two ways:
- Register Stack
- Memory Stack
Register Stack
A stack can be organized as a collection of finite number of registers that are used to store temporary information during the execution of a program. The stack pointer (SP) is a register that holds the address of top of element of the stack.
Memory Stack
A stack can be implemented in a random access memory (RAM) attached to a CPU. The implementation of a stack in the CPU is done by assigning a portion of memory to a stack operation and using a processor register as a stack pointer. The starting memory location of the stack is specified by the processor register as stack pointer.
Addressing Modes– The term addressing modes refers to the way in which the operand of an instruction is specified. The addressing mode specifies a rule for interpreting or modifying the address field of the instruction before the operand is actually executed.
Addressing modes for 8086 instructions are divided into two categories:
1) Addressing modes for data
2) Addressing modes for branch
The 8086 memory addressing modes provide flexible access to memory, allowing you to easily access variables, arrays, records, pointers, and other complex data types. The key to good assembly language programming is the proper use of memory addressing modes.
An assembly language program instruction consists of two parts

Fig - Assembly language program instruction
The memory address of an operand consists of two components:
IMPORTANT TERMS
- Starting address of memory segment.
- Effective address or Offset: An offset is determined by adding any combination of three address elements: displacement, base and index.
- Displacement: It is an 8 bit or 16 bit immediate value given in the instruction.
- Base: Contents of base register, BX or BP.
- Index: Content of index register SI or DI.
According to different ways of specifying an operand by 8086 microprocessor, different addressing modes are used by 8086.
Addressing modes used by 8086 microprocessors are discussed below:
- Implied mode: In implied addressing the operand is specified in the instruction itself. In this mode the data is 8 bits or 16 bits long and data is the part of instruction. Zero address instruction are designed with implied addressing mode.

Example: CLC (used to reset Carry flag to 0)
- Immediate addressing mode (symbol #):In this mode data is present in address field of instruction .Designed like one address instruction format.
Note: Limitation in the immediate mode is that the range of constants are restricted by size of address field.
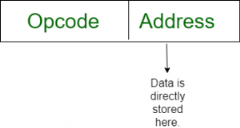
Example: MOV AL, 35H (move the data 35H into AL register)
- Register mode: In register addressing the operand is placed in one of 8 bit or 16-bit general purpose registers. The data is in the register that is specified by the instruction.
Here one register reference is required to access the data.

Example: MOV AX, CX (move the contents of CX register to AX register)
- Register Indirect mode: In this addressing the operand’s offset is placed in any one of the registers BX,BP,SI,DI as specified in the instruction. The effective address of the data is in the base register or an index register that is specified by the instruction.
Here two register reference is required to access the data.
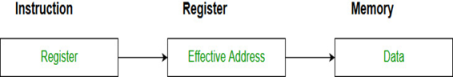
Fig – Register Indirect mode
The 8086 CPUs let you access memory indirectly through a register using the register indirect addressing modes.
- MOV AX, [BX](move the contents of memory location
Addressed by the register BX to the register AX)
- Auto Indexed (increment mode): Effective address of the operand is the contents of a register specified in the instruction. After accessing the operand, the contents of this register are automatically incremented to point to the next consecutive memory location.(R1)+.
Here one register reference, one memory reference and one ALU operation is required to access the data.
Example:
Add R1, (R2)+ // OR
R1 = R1 +M[R2]
R2 = R2 + d
Useful for stepping through arrays in a loop. R2 – start of array d – size of an element
- Auto indexed (decrement mode): Effective address of the operand is the contents of a register specified in the instruction. Before accessing the operand, the contents of this register are automatically decremented to point to the previous consecutive memory location. –(R1)
Here one register reference, one memory reference and one ALU operation is required to access the data.
Example:
Add R1, -(R2) //OR
R2 = R2-d
R1 = R1 + M[R2]
Auto decrement mode is same as auto increment mode. Both can also be used to implement a stack as push and pop. Auto increment and Auto decrement modes are useful for implementing “Last-In-First-Out” data structures.
- Direct addressing/ Absolute addressing Mode (symbol [ ]): The operand’s offset is given in the instruction as an 8 bit or 16 bit displacement element. In this addressing mode the 16-bit effective address of the data is the part of the instruction.
Here only one memory reference operation is required to access the data.
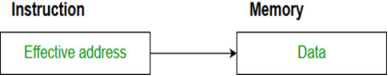
Example: ADD AL, [0301] //add the contents of offset address 0301 to AL
- Indirect addressing Mode (symbol @ or ()): In this mode address field of instruction contains the address of effective address. Here two references are required.
1st reference to get effective address.
2nd reference to access the data.
Based on the availability of Effective address, Indirect mode is of two kind:
- Register Indirect: In this mode effective address is in the register, and corresponding register name will be maintained in the address field of an instruction.
Here one register reference, one memory reference is required to access the data. - Memory Indirect: In this mode effective address is in the memory, and corresponding memory address will be maintained in the address field of an instruction.
Here two memory reference is required to access the data.
- Indexed addressing mode: The operand’s offset is the sum of the content of an index register SI or DI and an 8 bit or 16-bit displacement.
Example AX, [SI +05]
- Based Indexed Addressing: The operand’s offset is sum of the content of a base register BX or BP and an index register SI or DI.
Example: ADD AX, [BX+SI]
Based on Transfer of control, addressing modes are:
- PC relative addressing mode: PC relative addressing mode is used to implement intra segment transfer of control, In this mode effective address is obtained by adding displacement to PC.
- EA= PC + Address field value
PC= PC + Relative value.
3. Base register addressing mode: Base register addressing mode is used to implement inter segment transfer of control. In this mode effective address is obtained by adding base register value to address field value.
4. EA= Base register + Address field value.
5. PC= Base register + Relative value.
Note:
PC relative nad based register both addressing modes are suitable for program relocation at runtime.
Based register addressing mode is best suitable to write position independent codes.
Advantages of Addressing Modes
To give programmers to facilities such as Pointers, counters for loop controls, indexing of data and program relocation.
To reduce the number bits in the addressing field of the Instruction.
Key takeaway
Addressing Modes– The term addressing modes refers to the way in which the operand of an instruction is specified. The addressing mode specifies a rule for interpreting or modifying the address field of the instruction before the operand is actually executed.
References:
- Computer System Architecture by Morris Mano, Prenticehall, 3rd Edition, (2007)
- Computer Organization by Carl Hamacher, ZvonkoVranesic, SafwatZaky, Tata Mcgraw Hill, 5th Edition, (2011)
- Computer Architecture: A Quantitative Approach by Hennessy, J. L, David A Patterson, and Goldberg, Pearson Education, 4th Edition, (2006)