Unit - 1
Data Communication Components
Representation of Data
Computer does not understand human language. Any data, viz., letters, symbols, pictures, audio, videos, etc., fed to computer should be converted to machine language first. Computers represent data in the following three forms –
Number System
We are introduced to concept of numbers from a very early age. To a computer, everything is a number, i.e., alphabets, pictures, sounds, etc., are numbers. Number system is categorized into four types −
- Binary number system consists of only two values, either 0 or 1
- Octal number system represents values in 8 digits.
- Decimal number system represents values in 10 digits.
- Hexadecimal number system represents values in 16 digits.
Number System | ||
System | Base | Digits |
Binary | 2 | 0 1 |
Octal | 8 | 0 1 2 3 4 5 6 7 |
Decimal | 10 | 0 1 2 3 4 5 6 7 8 9 |
Hexadecimal | 16 | 0 1 2 3 4 5 6 7 8 9 A B C D E F |
Bits and Bytes
Bits − A bit is a smallest possible unit of data that a computer can recognize or use. Computer usually uses bits in groups.
Bytes − group of eight bits is called a byte. Half a byte is called a nibble.
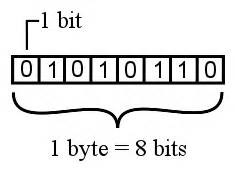
The following table shows conversion of Bits and Bytes –
Byte Value | Bit Value |
1 Byte | 8 Bits |
1024 Bytes | 1 Kilobyte |
1024 Kilobytes | 1 Megabyte |
1024 Megabytes | 1 Gigabyte |
1024 Gigabytes | 1 Terabyte |
1024 Terabytes | 1 Petabyte |
1024 Petabytes | 1 Exabyte |
1024 Exabytes | 1 Zettabyte |
1024 Zettabytes | 1 Yottabyte |
1024 Yottabytes | 1 Brontobyte |
1024 Brontobytes | 1 Geopbytes |
Text Code
Text code is format used commonly to represent alphabets, punctuation marks and other symbols. Four most popular text code systems are −
- EBCDIC
- ASCII
- Extended ASCII
- Unicode
EBCDIC
Extended Binary Coded Decimal Interchange Code is an 8-bit code that defines 256 symbols. Given below is the EBCDIC Tabular column
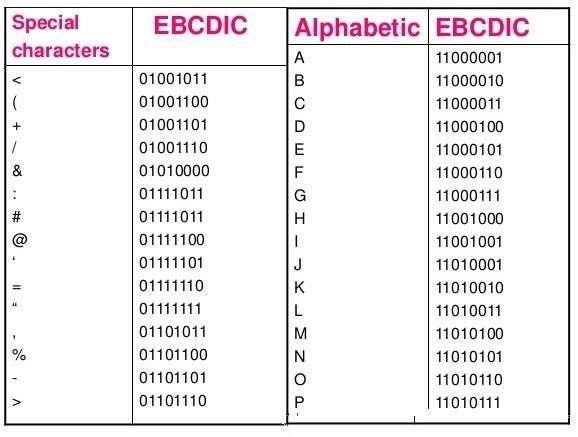
Fig 1 - EBCDIC Tabular column
ASCII
American Standard Code for Information Interchange is an 8-bit code that specifies character values from 0 to 127.
ASCII Tabular column
ASCII Code | Decimal Value | Character |
0000 0000 | 0 | Null prompt |
0000 0001 | 1 | Start of heading |
0000 0010 | 2 | Start of text |
0000 0011 | 3 | End of text |
0000 0100 | 4 | End of transmit |
0000 0101 | 5 | Enquiry |
0000 0110 | 6 | Acknowledge |
0000 0111 | 7 | Audible bell |
0000 1000 | 8 | Backspace |
0000 1001 | 9 | Horizontal tab |
0000 1010 | 10 | Line Feed |
Extended ASCII
Extended American Standard Code for Information Interchange is an 8-bit code that specifies character values from 128 to 255.
Extended ASCII Tabular column
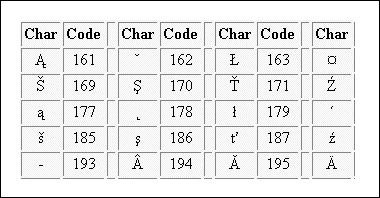
Fig 2 - Extended ASCII Tabular column
Unicode
Unicode Worldwide Character Standard uses 4 to 32 bits to represent letters, numbers and symbol.
Unicode Tabular Column
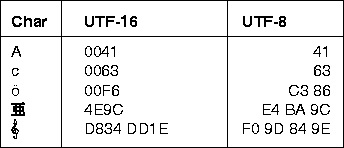
Fig 3 - Unicode Tabular Column
Transmission mode
- The way in which data is transmitted from one device to another device is known as transmission mode.
- The transmission mode is also known as the communication mode.
- Each communication channel has a direction associated with it, and transmission media provide the direction. Therefore, the transmission mode is also known as a directional mode.
- The transmission mode is defined in the physical layer.
The Transmission mode is divided into three categories:
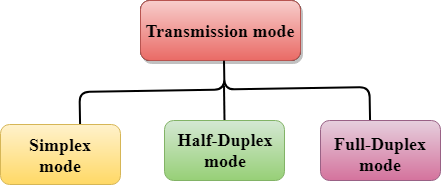
Fig 4 – Transmission mode types
- Simplex mode
- Half-duplex mode
- Full-duplex mode
Simplex mode
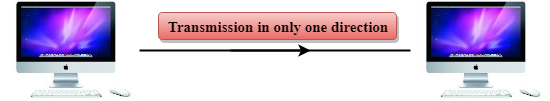
Fig 5 – Simplex mode
- In Simplex mode, the communication is unidirectional, i.e., the data flow in one direction.
- A device can only send the data but cannot receive it or it can receive the data but cannot send the data.
- This transmission mode is not very popular as mainly communications require the two-way exchange of data. The simplex mode is used in the business field as in sales that do not require any corresponding reply.
- The radio station is a simplex channel as it transmits the signal to the listeners but never allows them to transmit back.
- Keyboard and Monitor are the examples of the simplex mode as a keyboard can only accept the data from the user and monitor can only be used to display the data on the screen.
- The main advantage of the simplex mode is that the full capacity of the communication channel can be utilized during transmission.
Advantage of Simplex mode:
- In simplex mode, the station can utilize the entire bandwidth of the communication channel, so that more data can be transmitted at a time.
Disadvantage of Simplex mode:
- Communication is unidirectional, so it has no inter-communication between devices.
Half-Duplex mode
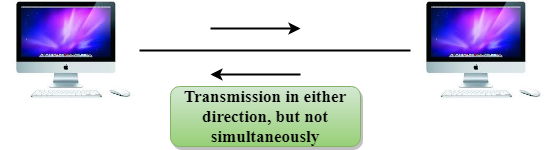
Fig 6 – Half Duplex mode
- In a Half-duplex channel, direction can be reversed, i.e., the station can transmit and receive the data as well.
- Messages flow in both the directions, but not at the same time.
- The entire bandwidth of the communication channel is utilized in one direction at a time.
- In half-duplex mode, it is possible to perform the error detection, and if any error occurs, then the receiver requests the sender to retransmit the data.
- A Walkie-talkie is an example of the Half-duplex mode. In Walkie-talkie, one party speaks, and another party listens. After a pause, the other speaks and first party listens. Speaking simultaneously will create the distorted sound which cannot be understood.
Advantage of Half-duplex mode:
- In half-duplex mode, both the devices can send and receive the data and also can utilize the entire bandwidth of the communication channel during the transmission of data.
Disadvantage of Half-Duplex mode:
- In half-duplex mode, when one device is sending the data, then another has to wait, this causes the delay in sending the data at the right time.
Full-duplex mode
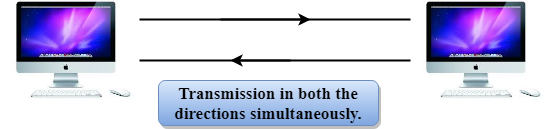
Fig 7 – Full duplex mode
- In Full duplex mode, the communication is bi-directional, i.e., the data flow in both the directions.
- Both the stations can send and receive the message simultaneously.
- Full-duplex mode has two simplex channels. One channel has traffic moving in one direction, and another channel has traffic flowing in the opposite direction.
- The Full-duplex mode is the fastest mode of communication between devices.
- The most common example of the full-duplex mode is a telephone network. When two people are communicating with each other by a telephone line, both can talk and listen at the same time.
Advantage of Full-duplex mode:
- Both the stations can send and receive the data at the same time.
Disadvantage of Full-duplex mode:
- If there is no dedicated path exists between the devices, then the capacity of the communication channel is divided into two parts.
Differences b/w Simplex, Half-duplex and Full-duplex mode
Basis for comparison | Simplex mode | Half-duplex mode | Full-duplex mode |
Direction of communication | In simplex mode, the communication is unidirectional. | In half-duplex mode, the communication is bidirectional, but one at a time. | In full-duplex mode, the communication is bidirectional. |
Send/Receive | A device can only send the data but cannot receive it or it can only receive the data but cannot send it. | Both the devices can send and receive the data, but one at a time. | Both the devices can send and receive the data simultaneously. |
Performance | The performance of half-duplex mode is better than the simplex mode. | The performance of full-duplex mode is better than the half-duplex mode. | The Full-duplex mode has better performance among simplex and half-duplex mode as it doubles the utilization of the capacity of the communication channel. |
Example | Examples of Simplex mode are radio, keyboard, and monitor. | Example of half-duplex is Walkie-Talkies. | Example of the Full-duplex mode is a telephone network. |
Key takeaways
- Representation of Data
Computer does not understand human language. Any data, viz., letters, symbols, pictures, audio, videos, etc., fed to computer should be converted to machine language first. Computers represent data in the following three forms –
2. Number System
We are introduced to concept of numbers from a very early age. To a computer, everything is a number, i.e., alphabets, pictures, sounds, etc., are numbers. Number system is categorized into four types –
- Binary number system consists of only two values, either 0 or 1
- Octal number system represents values in 8 digits.
- Decimal number system represents values in 10 digits.
- Hexadecimal number system represents values in 16 digits.
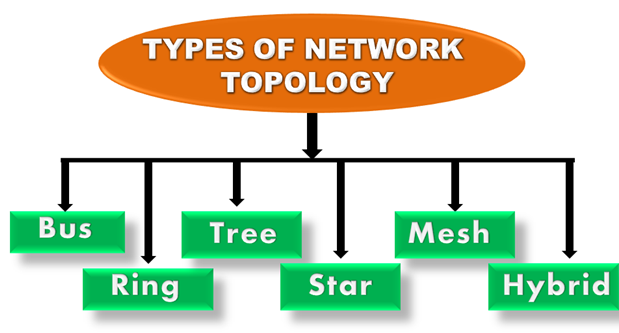
What is Topology?
Topology defines the structure of the network of how all the components are interconnected to each other. There are two types of topology: physical and logical topology.
Physical topology is the geometric representation of all the nodes in a network.
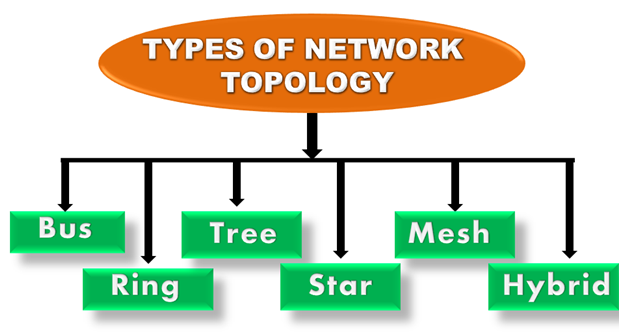
Fig 8 – Types of network topology
Bus Topology
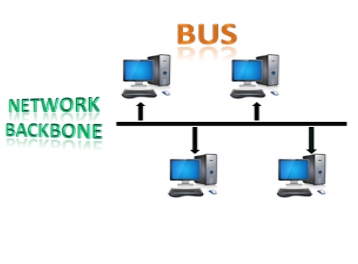
Fig 9 – Bus topology
- The bus topology is designed in such a way that all the stations are connected through a single cable known as a backbone cable.
- Each node is either connected to the backbone cable by drop cable or directly connected to the backbone cable.
- When a node wants to send a message over the network, it puts a message over the network. All the stations available in the network will receive the message whether it has been addressed or not.
- The bus topology is mainly used in 802.3 (ethernet) and 802.4 standard networks.
- The configuration of a bus topology is quite simpler as compared to other topologies.
- The backbone cable is considered as a "single lane" through which the message is broadcast to all the stations.
- The most common access method of the bus topologies is CSMA (Carrier Sense Multiple Access).
CSMA: It is a media access control used to control the data flow so that data integrity is maintained, i.e., the packets do not get lost. There are two alternative ways of handling the problems that occur when two nodes send the messages simultaneously.
- CSMA CD: CSMA CD (Collision detection) is an access method used to detect the collision. Once the collision is detected, the sender will stop transmitting the data. Therefore, it works on "recovery after the collision".
- CSMA CA: CSMA CA (Collision Avoidance) is an access method used to avoid the collision by checking whether the transmission media is busy or not. If busy, then the sender waits until the media becomes idle. This technique effectively reduces the possibility of the collision. It does not work on "recovery after the collision".
Advantages of Bus topology:
- Low-cost cable: In bus topology, nodes are directly connected to the cable without passing through a hub. Therefore, the initial cost of installation is low.
- Moderate data speeds: Coaxial or twisted pair cables are mainly used in bus-based networks that support upto 10 Mbps.
- Familiar technology: Bus topology is a familiar technology as the installation and troubleshooting techniques are well known, and hardware components are easily available.
- Limited failure: A failure in one node will not have any effect on other nodes.
Disadvantages of Bus topology:
- Extensive cabling: A bus topology is quite simpler, but still it requires a lot of cabling.
- Difficult troubleshooting: It requires specialized test equipment to determine the cable faults. If any fault occurs in the cable, then it would disrupt the communication for all the nodes.
- Signal interference: If two nodes send the messages simultaneously, then the signals of both the nodes collide with each other.
- Reconfiguration difficult: Adding new devices to the network would slow down the network.
- Attenuation: Attenuation is a loss of signal leads to communication issues. Repeaters are used to regenerate the signal.
Ring Topology
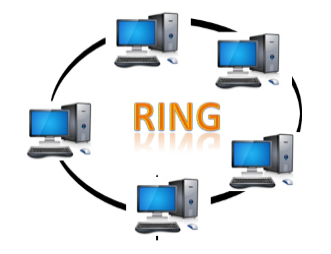
Fig 10 – Ring topology
- Ring topology is like a bus topology, but with connected ends.
- The node that receives the message from the previous computer will retransmit to the next node.
- The data flows in one direction, i.e., it is unidirectional.
- The data flows in a single loop continuously known as an endless loop.
- It has no terminated ends, i.e., each node is connected to other node and having no termination point.
- The data in a ring topology flow in a clockwise direction.
- The most common access method of the ring topology is token passing.
- Token passing: It is a network access method in which token is passed from one node to another node.
- Token: It is a frame that circulates around the network.
Working of Token passing
- A token moves around the network, and it is passed from computer to computer until it reaches the destination.
- The sender modifies the token by putting the address along with the data.
- The data is passed from one device to another device until the destination address matches. Once the token received by the destination device, then it sends the acknowledgment to the sender.
- In a ring topology, a token is used as a carrier.
Advantages of Ring topology:
- Network Management: Faulty devices can be removed from the network without bringing the network down.
- Product availability: Many hardware and software tools for network operation and monitoring are available.
- Cost: Twisted pair cabling is inexpensive and easily available. Therefore, the installation cost is very low.
- Reliable: It is a more reliable network because the communication system is not dependent on the single host computer.
Disadvantages of Ring topology:
- Difficult troubleshooting: It requires specialized test equipment to determine the cable faults. If any fault occurs in the cable, then it would disrupt the communication for all the nodes.
- Failure: The breakdown in one station leads to the failure of the overall network.
- Reconfiguration difficult: Adding new devices to the network would slow down the network.
- Delay: Communication delay is directly proportional to the number of nodes. Adding new devices increases the communication delay.
Star Topology
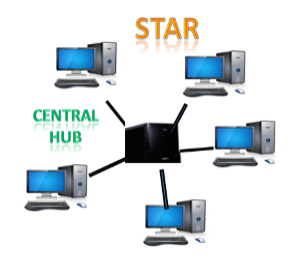
Fig 11 – Star topology
- Star topology is an arrangement of the network in which every node is connected to the central hub, switch or a central computer.
- The central computer is known as a server, and the peripheral devices attached to the server are known as clients.
- Coaxial cable or RJ-45 cables are used to connect the computers.
- Hubs or Switches are mainly used as connection devices in a physical star topology.
- Star topology is the most popular topology in network implementation.
Advantages of Star topology
- Efficient troubleshooting: Troubleshooting is quite efficient in a star topology as compared to bus topology. In a bus topology, the manager has to inspect the kilometers of cable. In a star topology, all the stations are connected to the centralized network. Therefore, the network administrator has to go to the single station to troubleshoot the problem.
- Network control: Complex network control features can be easily implemented in the star topology. Any changes made in the star topology are automatically accommodated.
- Limited failure: As each station is connected to the central hub with its own cable, therefore failure in one cable will not affect the entire network.
- Familiar technology: Star topology is a familiar technology as its tools are cost-effective.
- Easily expandable: It is easily expandable as new stations can be added to the open ports on the hub.
- Cost effective: Star topology networks are cost-effective as it uses inexpensive coaxial cable.
- High data speeds: It supports a bandwidth of approx 100Mbps. Ethernet 100BaseT is one of the most popular Star topology networks.
Disadvantages of Star topology
- A Central point of failure: If the central hub or switch goes down, then all the connected nodes will not be able to communicate with each other.
- Cable: Sometimes cable routing becomes difficult when a significant amount of routing is required.
Tree topology
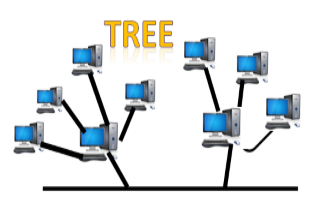
Fig 12 – Tree topology
- Tree topology combines the characteristics of bus topology and star topology.
- A tree topology is a type of structure in which all the computers are connected with each other in hierarchical fashion.
- The top-most node in tree topology is known as a root node, and all other nodes are the descendants of the root node.
- There is only one path exists between two nodes for the data transmission. Thus, it forms a parent-child hierarchy.
Advantages of Tree topology
- Support for broadband transmission: Tree topology is mainly used to provide broadband transmission, i.e., signals are sent over long distances without being attenuated.
- Easily expandable: We can add the new device to the existing network. Therefore, we can say that tree topology is easily expandable.
- Easily manageable: In tree topology, the whole network is divided into segments known as star networks which can be easily managed and maintained.
- Error detection: Error detection and error correction are very easy in a tree topology.
- Limited failure: The breakdown in one station does not affect the entire network.
- Point-to-point wiring: It has point-to-point wiring for individual segments.
Disadvantages of Tree topology
- Difficult troubleshooting: If any fault occurs in the node, then it becomes difficult to troubleshoot the problem.
- High cost: Devices required for broadband transmission are very costly.
- Failure: A tree topology mainly relies on main bus cable and failure in main bus cable will damage the overall network.
- Reconfiguration difficult: If new devices are added, then it becomes difficult to reconfigure.
Mesh topology
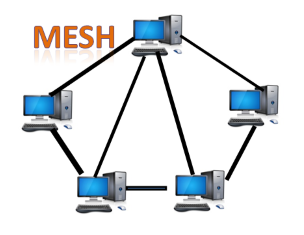
Fig 13 – Mesh topology
- Mesh technology is an arrangement of the network in which computers are interconnected with each other through various redundant connections.
- There are multiple paths from one computer to another computer.
- It does not contain the switch, hub or any central computer which acts as a central point of communication.
- The Internet is an example of the mesh topology.
- Mesh topology is mainly used for WAN implementations where communication failures are a critical concern.
- Mesh topology is mainly used for wireless networks.
- Mesh topology can be formed by using the formula:
Number of cables = (n*(n-1))/2;
Where n is the number of nodes that represents the network.
Mesh topology is divided into two categories:
- Fully connected mesh topology
- Partially connected mesh topology
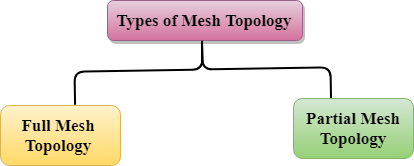
Fig 14 – Types of mesh topology
- Full Mesh Topology: In a full mesh topology, each computer is connected to all the computers available in the network.
- Partial Mesh Topology: In a partial mesh topology, not all but certain computers are connected to those computers with which they communicate frequently.
Advantages of Mesh topology:
Reliable: The mesh topology networks are very reliable as if any link breakdown will not affect the communication between connected computers.
Fast Communication: Communication is very fast between the nodes.
Easier Reconfiguration: Adding new devices would not disrupt the communication between other devices.
Disadvantages of Mesh topology
- Cost: A mesh topology contains a large number of connected devices such as a router and more transmission media than other topologies.
- Management: Mesh topology networks are very large and very difficult to maintain and manage. If the network is not monitored carefully, then the communication link failure goes undetected.
- Efficiency: In this topology, redundant connections are high that reduces the efficiency of the network.
Hybrid Topology
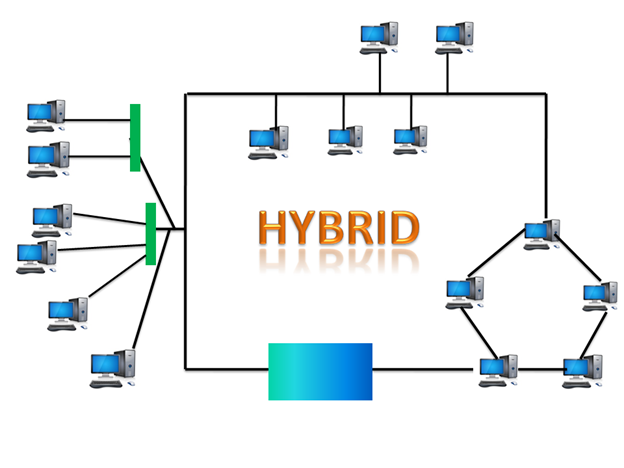
Fig 15 – Hybrid topology
- The combination of various different topologies is known as Hybrid topology.
- A Hybrid topology is a connection between different links and nodes to transfer the data.
- When two or more different topologies are combined together is termed as Hybrid topology and if similar topologies are connected with each other will not result in Hybrid topology. For example, if there exist a ring topology in one branch of ICICI bank and bus topology in another branch of ICICI bank, connecting these two topologies will result in Hybrid topology.
Advantages of Hybrid Topology
- Reliable: If a fault occurs in any part of the network will not affect the functioning of the rest of the network.
- Scalable: Size of the network can be easily expanded by adding new devices without affecting the functionality of the existing network.
- Flexible: This topology is very flexible as it can be designed according to the requirements of the organization.
- Effective: Hybrid topology is very effective as it can be designed in such a way that the strength of the network is maximized and weakness of the network is minimized.
Disadvantages of Hybrid topology
- Complex design: The major drawback of the Hybrid topology is the design of the Hybrid network. It is very difficult to design the architecture of the Hybrid network.
- Costly Hub: The Hubs used in the Hybrid topology are very expensive as these hubs are different from usual Hubs used in other topologies.
- Costly infrastructure: The infrastructure cost is very high as a hybrid network requires a lot of cabling, network devices, etc.
Key takeaways
- Topology defines the structure of the network of how all the components are interconnected to each other. There are two types of topology: physical and logical topology.
- Physical topology is the geometric representation of all the nodes in a network.
Network Protocols are a set of rules governing exchange of information in an easy, reliable and secure way. Before we discuss the most common protocols used to transmit and receive data over a network, we need to understand how a network is logically organized or designed. The most popular model used to establish open communication between two systems is the Open Systems Interface (OSI) model proposed by ISO.
OSI Model
OSI model is not a network architecture because it does not specify the exact services and protocols for each layer. It simply tells what each layer should do by defining its input and output data. It is up to network architects to implement the layers according to their needs and resources available.
These are the seven layers of the OSI model −
- Physical layer −It is the first layer that physically connects the two systems that need to communicate. It transmits data in bits and manages simplex or duplex transmission by modem. It also manages Network Interface Card’s hardware interface to the network, like cabling, cable terminators, topography, voltage levels, etc.
- Data link layer − It is the firmware layer of Network Interface Card. It assembles datagrams into frames and adds start and stop flags to each frame. It also resolves problems caused by damaged, lost or duplicate frames.
- Network layer − It is concerned with routing, switching and controlling flow of information between the workstations. It also breaks down transport layer datagrams into smaller datagrams.
- Transport layer − Till the session layer, file is in its own form. Transport layer breaks it down into data frames, provides error checking at network segment level and prevents a fast host from overrunning a slower one. Transport layer isolates the upper layers from network hardware.
- Session layer − This layer is responsible for establishing a session between two workstations that want to exchange data.
- Presentation layer − This layer is concerned with correct representation of data, i.e. syntax and semantics of information. It controls file level security and is also responsible for converting data to network standards.
- Application layer − It is the topmost layer of the network that is responsible for sending application requests by the user to the lower levels. Typical applications include file transfer, E-mail, remote logon, data entry, etc.
Fig 16 – Client server machine
It is not necessary for every network to have all the layers. For example, network layer is not there in broadcast networks.
When a system wants to share data with another workstation or send a request over the network, it is received by the application layer. Data then proceeds to lower layers after processing till it reaches the physical layer.
At the physical layer, the data is actually transferred and received by the physical layer of the destination workstation. There, the data proceeds to upper layers after processing till it reaches application layer.
At the application layer, data or request is shared with the workstation. So each layer has opposite functions for source and destination workstations. For example, data link layer of the source workstation adds start and stop flags to the frames but the same layer of the destination workstation will remove the start and stop flags from the frames.
Let us now see some of the protocols used by different layers to accomplish user requests.
TCP/IP
TCP/IP stands for Transmission Control Protocol/Internet Protocol. TCP/IP is a set of layered protocols used for communication over the Internet. The communication model of this suite is client-server model. A computer that sends a request is the client and a computer to which the request is sent is the server.
Fig 17 – Media for data transfer
TCP/IP has four layers −
- Application layer − Application layer protocols like HTTP and FTP are used.
- Transport layer − Data is transmitted in form of datagrams using the Transmission Control Protocol (TCP). TCP is responsible for breaking up data at the client side and then reassembling it on the server side.
- Network layer − Network layer connection is established using Internet Protocol (IP) at the network layer. Every machine connected to the Internet is assigned an address called IP address by the protocol to easily identify source and destination machines.
- Data link layer − Actual data transmission in bits occurs at the data link layer using the destination address provided by network layer.
TCP/IP is widely used in many communication networks other than the Internet.
FTP
As we have seen, the need for network came up primarily to facilitate sharing of files between researchers. And to this day, file transfer remains one of the most used facilities. The protocol that handles these requests is File Transfer Protocol or FTP.

Fig 18 – FTP
Using FTP to transfer files is helpful in these ways −
- Easily transfers files between two different networks
- Can resume file transfer sessions even if connection is dropped, if protocol is configure appropriately
- Enables collaboration between geographically separated teams
PPP
Point to Point Protocol or PPP is a data link layer protocol that enables transmission of TCP/IP traffic over serial connection, like telephone line.

Fig 19 – PPP
To do this, PPP defines these three things −
- A framing method to clearly define end of one frame and start of another, incorporating errors detection as well.
- Link control protocol (LCP) for bringing communication lines up, authenticating and bringing them down when no longer needed.
- Network control protocol (NCP) for each network layer protocol supported by other networks.
Using PPP, home users can avail Internet connection over telephone lines.
Key takeaways
- Network Protocols are a set of rules governing exchange of information in an easy, reliable and secure way. Before we discuss the most common protocols used to transmit and receive data over a network, we need to understand how a network is logically organized or designed. The most popular model used to establish open communication between two systems is the Open Systems Interface (OSI) model proposed by ISO.
- OSI model is not a network architecture because it does not specify the exact services and protocols for each layer. It simply tells what each layer should do by defining its input and output data. It is up to network architects to implement the layers according to their needs and resources available.
- OSI stands for Open System Interconnection is a reference model that describes how information from a software application in one computer moves through a physical medium to the software application in another computer.
- OSI consists of seven layers, and each layer performs a particular network function.
- OSI model was developed by the International Organization for Standardization (ISO) in 1984, and it is now considered as an architectural model for the inter-computer communications.
- OSI model divides the whole task into seven smaller and manageable tasks. Each layer is assigned a particular task.
- Each layer is self-contained, so that task assigned to each layer can be performed independently.
Characteristics of OSI Model:
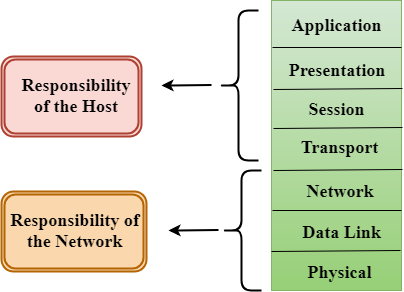
Fig 20 - Characteristics of OSI Model
- The OSI model is divided into two layers: upper layers and lower layers.
- The upper layer of the OSI model mainly deals with the application related issues, and they are implemented only in the software. The application layer is closest to the end user. Both the end user and the application layer interact with the software applications. An upper layer refers to the layer just above another layer.
- The lower layer of the OSI model deals with the data transport issues. The data link layer and the physical layer are implemented in hardware and software. The physical layer is the lowest layer of the OSI model and is closest to the physical medium. The physical layer is mainly responsible for placing the information on the physical medium.
Functions of the OSI Layers
There are the seven OSI layers. Each layer has different functions. A list of seven layers are given below:
- Physical Layer
- Data-Link Layer
- Network Layer
- Transport Layer
- Session Layer
- Presentation Layer
- Application Layer
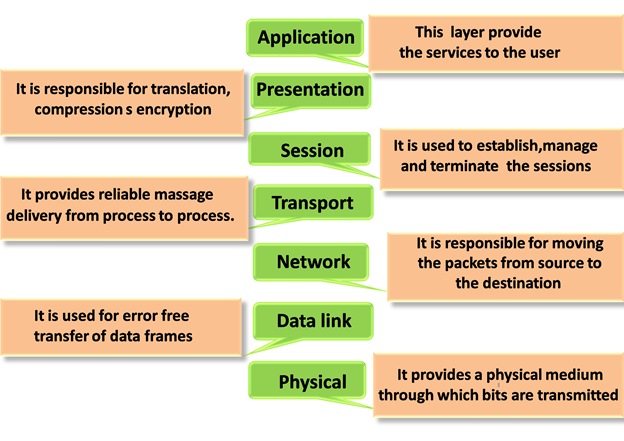
Fig 21 – Layers of OSI model
Physical layer
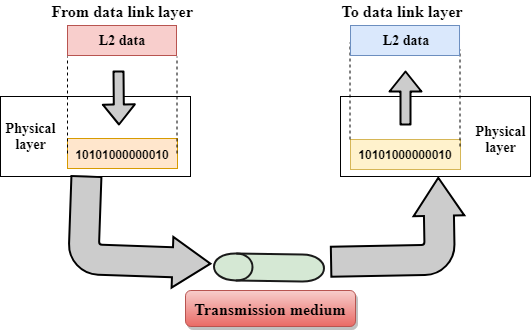
Fig 22 – Transmission medium
- The main functionality of the physical layer is to transmit the individual bits from one node to another node.
- It is the lowest layer of the OSI model.
- It establishes, maintains and deactivates the physical connection.
- It specifies the mechanical, electrical and procedural network interface specifications.
Functions of a Physical layer:
- Line Configuration: It defines the way how two or more devices can be connected physically.
- Data transmission: It defines the transmission mode whether it is simplex, half-duplex or full-duplex mode between the two devices on the network.
- Topology: It defines the way how network devices are arranged.
- Signals: It determines the type of the signal used for transmitting the information.
Data-Link Layer
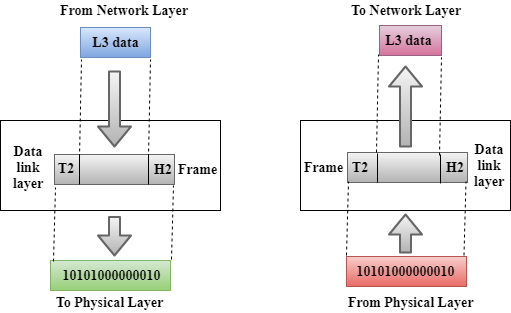
Fig 23 – Data link layer
- This layer is responsible for the error-free transfer of data frames.
- It defines the format of the data on the network.
- It provides a reliable and efficient communication between two or more devices.
- It is mainly responsible for the unique identification of each device that resides on a local network.
- It contains two sub-layers:
- Logical Link Control Layer
- It is responsible for transferring the packets to the Network layer of the receiver that is receiving.
- It identifies the address of the network layer protocol from the header.
- It also provides flow control.
- Media Access Control Layer
- A Media access control layer is a link between the Logical Link Control layer and the network's physical layer.
- It is used for transferring the packets over the network.
- Logical Link Control Layer
Functions of the Data-link layer
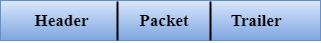
- Framing: The data link layer translates the physical's raw bit stream into packets known as Frames. The Data link layer adds the header and trailer to the frame. The header which is added to the frame contains the hardware destination and source address.
- Physical Addressing: The Data link layer adds a header to the frame that contains a destination address. The frame is transmitted to the destination address mentioned in the header.
- Flow Control: Flow control is the main functionality of the Data-link layer. It is the technique through which the constant data rate is maintained on both the sides so that no data get corrupted. It ensures that the transmitting station such as a server with higher processing speed does not exceed the receiving station, with lower processing speed.
- Error Control: Error control is achieved by adding a calculated value CRC (Cyclic Redundancy Check) that is placed to the Data link layer's trailer which is added to the message frame before it is sent to the physical layer. If any error seems to occurr, then the receiver sends the acknowledgment for the retransmission of the corrupted frames.
- Access Control: When two or more devices are connected to the same communication channel, then the data link layer protocols are used to determine which device has control over the link at a given time.
Network Layer
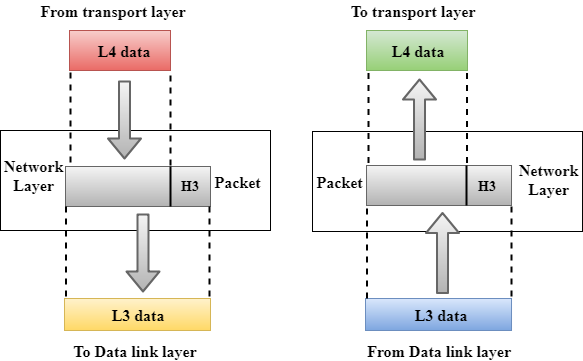
Fig 24 – Network layer
- It is a layer 3 that manages device addressing, tracks the location of devices on the network.
- It determines the best path to move data from source to the destination based on the network conditions, the priority of service, and other factors.
- The Data link layer is responsible for routing and forwarding the packets.
- Routers are the layer 3 devices, they are specified in this layer and used to provide the routing services within an internetwork.
- The protocols used to route the network traffic are known as Network layer protocols. Examples of protocols are IP and Ipv6.
Functions of Network Layer:
- Internetworking: An internetworking is the main responsibility of the network layer. It provides a logical connection between different devices.
- Addressing: A Network layer adds the source and destination address to the header of the frame. Addressing is used to identify the device on the internet.
- Routing: Routing is the major component of the network layer, and it determines the best optimal path out of the multiple paths from source to the destination.
- Packetizing: A Network Layer receives the packets from the upper layer and converts them into packets. This process is known as Packetizing. It is achieved by internet protocol (IP).
Transport Layer
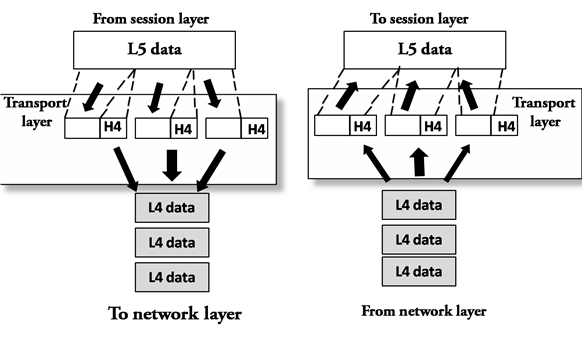
Fig 25 – Transport layer
- The Transport layer is a Layer 4 ensures that messages are transmitted in the order in which they are sent and there is no duplication of data.
- The main responsibility of the transport layer is to transfer the data completely.
- It receives the data from the upper layer and converts them into smaller units known as segments.
- This layer can be termed as an end-to-end layer as it provides a point-to-point connection between source and destination to deliver the data reliably.
The two protocols used in this layer are:
- Transmission Control Protocol
- It is a standard protocol that allows the systems to communicate over the internet.
- It establishes and maintains a connection between hosts.
- When data is sent over the TCP connection, then the TCP protocol divides the data into smaller units known as segments. Each segment travels over the internet using multiple routes, and they arrive in different orders at the destination. The transmission control protocol reorders the packets in the correct order at the receiving end.
- User Datagram Protocol
- User Datagram Protocol is a transport layer protocol.
- It is an unreliable transport protocol as in this case receiver does not send any acknowledgment when the packet is received, the sender does not wait for any acknowledgment. Therefore, this makes a protocol unreliable.
Functions of Transport Layer:
- Service-point addressing: Computers run several programs simultaneously due to this reason, the transmission of data from source to the destination not only from one computer to another computer but also from one process to another process. The transport layer adds the header that contains the address known as a service-point address or port address. The responsibility of the network layer is to transmit the data from one computer to another computer and the responsibility of the transport layer is to transmit the message to the correct process.
- Segmentation and reassembly: When the transport layer receives the message from the upper layer, it divides the message into multiple segments, and each segment is assigned with a sequence number that uniquely identifies each segment. When the message has arrived at the destination, then the transport layer reassembles the message based on their sequence numbers.
- Connection control: Transport layer provides two services Connection-oriented service and connectionless service. A connectionless service treats each segment as an individual packet, and they all travel in different routes to reach the destination. A connection-oriented service makes a connection with the transport layer at the destination machine before delivering the packets. In connection-oriented service, all the packets travel in the single route.
- Flow control: The transport layer also responsible for flow control but it is performed end-to-end rather than across a single link.
- Error control: The transport layer is also responsible for Error control. Error control is performed end-to-end rather than across the single link. The sender transport layer ensures that message reach at the destination without any error.
Session Layer
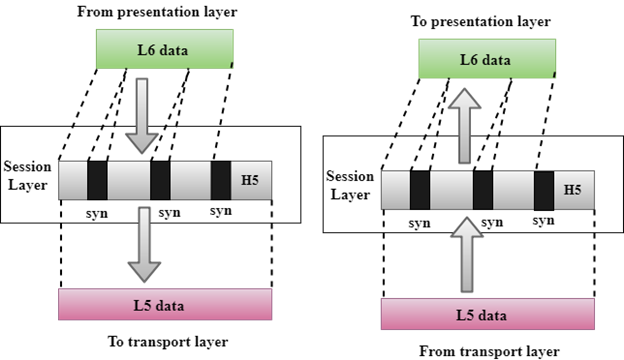
Fig 26 – Session layer
- It is a layer 3 in the OSI model.
- The Session layer is used to establish, maintain and synchronizes the interaction between communicating devices.
Functions of Session layer:
- Dialog control: Session layer acts as a dialog controller that creates a dialog between two processes or we can say that it allows the communication between two processes which can be either half-duplex or full-duplex.
- Synchronization: Session layer adds some checkpoints when transmitting the data in a sequence. If some error occurs in the middle of the transmission of data, then the transmission will take place again from the checkpoint. This process is known as Synchronization and recovery.
Presentation Layer
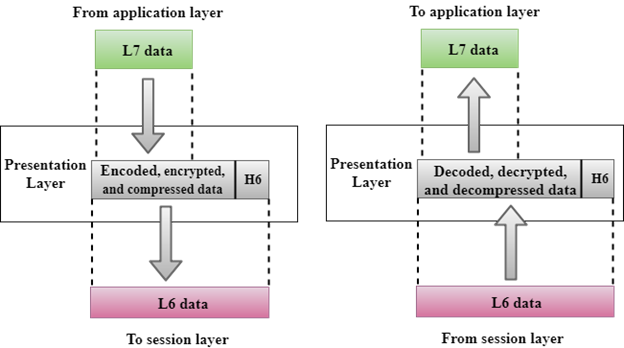
Fig 27 – Presentation layer
- A Presentation layer is mainly concerned with the syntax and semantics of the information exchanged between the two systems.
- It acts as a data translator for a network.
- This layer is a part of the operating system that converts the data from one presentation format to another format.
- The Presentation layer is also known as the syntax layer.
Functions of Presentation layer:
- Translation: The processes in two systems exchange the information in the form of character strings, numbers and so on. Different computers use different encoding methods, the presentation layer handles the interoperability between the different encoding methods. It converts the data from sender-dependent format into a common format and changes the common format into receiver-dependent format at the receiving end.
- Encryption: Encryption is needed to maintain privacy. Encryption is a process of converting the sender-transmitted information into another form and sends the resulting message over the network.
- Compression: Data compression is a process of compressing the data, i.e., it reduces the number of bits to be transmitted. Data compression is very important in multimedia such as text, audio, video.
Application Layer
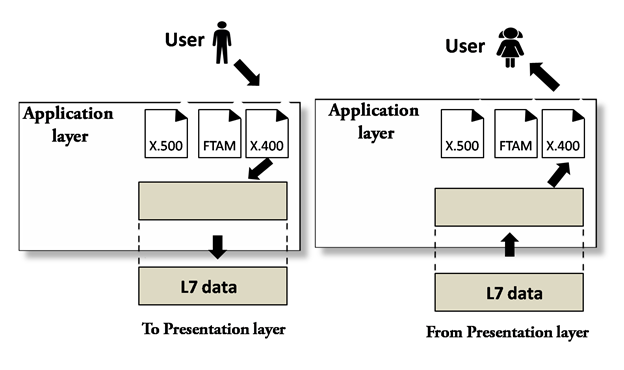
Fig 28 – Application layer
- An application layer serves as a window for users and application processes to access network service.
- It handles issues such as network transparency, resource allocation, etc.
- An application layer is not an application, but it performs the application layer functions.
- This layer provides the network services to the end-users.
Functions of Application layer:
- File transfer, access, and management (FTAM): An application layer allows a user to access the files in a remote computer, to retrieve the files from a computer and to manage the files in a remote computer.
- Mail services: An application layer provides the facility for email forwarding and storage.
- Directory services: An application provides the distributed database sources and is used to provide that global information about various objects.
Key takeaways
- OSI stands for Open System Interconnection is a reference model that describes how information from a software application in one computer moves through a physical medium to the software application in another computer.
- OSI consists of seven layers, and each layer performs a particular network function.
- OSI model was developed by the International Organization for Standardization (ISO) in 1984, and it is now considered as an architectural model for the inter-computer communications.
- OSI model divides the whole task into seven smaller and manageable tasks. Each layer is assigned a particular task.
- Each layer is self-contained, so that task assigned to each layer can be performed independently.
What is Transmission media?
- Transmission media is a communication channel that carries the information from the sender to the receiver. Data is transmitted through the electromagnetic signals.
- The main functionality of the transmission media is to carry the information in the form of bits through LAN(Local Area Network).
- It is a physical path between transmitter and receiver in data communication.
- In a copper-based network, the bits in the form of electrical signals.
- In a fibre based network, the bits in the form of light pulses.
- In OSI(Open System Interconnection) phase, transmission media supports the Layer 1. Therefore, it is considered to be as a Layer 1 component.
- The electrical signals can be sent through the copper wire, fibre optics, atmosphere, water, and vacuum.
- The characteristics and quality of data transmission are determined by the characteristics of medium and signal.
- Transmission media is of two types are wired media and wireless media. In wired media, medium characteristics are more important whereas, in wireless media, signal characteristics are more important.
- Different transmission media have different properties such as bandwidth, delay, cost and ease of installation and maintenance.
- The transmission media is available in the lowest layer of the OSI reference model, i.e., Physical layer.
Some factors need to be considered for designing the transmission media:
- Bandwidth: All the factors are remaining constant, the greater the bandwidth of a medium, the higher the data transmission rate of a signal.
- Transmission impairment: When the received signal is not identical to the transmitted one due to the transmission impairment. The quality of the signals will get destroyed due to transmission impairment.
- Interference: An interference is defined as the process of disrupting a signal when it travels over a communication medium on the addition of some unwanted signal.
Causes Of Transmission Impairment:
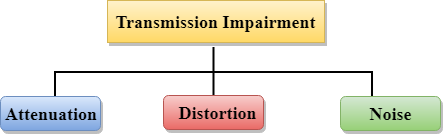
Fig 29 – Transmission Impairment
- Attenuation: Attenuation means the loss of energy, i.e., the strength of the signal decreases with increasing the distance which causes the loss of energy.
- Distortion: Distortion occurs when there is a change in the shape of the signal. This type of distortion is examined from different signals having different frequencies. Each frequency component has its own propagation speed, so they reach at a different time which leads to the delay distortion.
- Noise: When data is travelled over a transmission medium, some unwanted signal is added to it which creates the noise.
Classification Of Transmission Media:
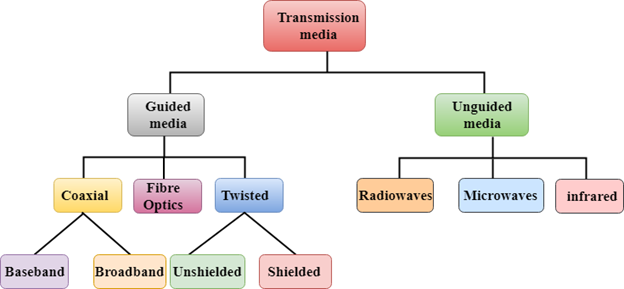
Fig 30 – Classification of transmission media
- Guided Transmission Media
- Unguided Transmission Media
Guided Media
It is defined as the physical medium through which the signals are transmitted. It is also known as Bounded media.
Types Of Guided media:
Twisted pair:
Twisted pair is a physical media made up of a pair of cables twisted with each other. A twisted pair cable is cheap as compared to other transmission media. Installation of the twisted pair cable is easy, and it is a lightweight cable. The frequency range for twisted pair cable is from 0 to 3.5KHz.
A twisted pair consists of two insulated copper wires arranged in a regular spiral pattern.
The degree of reduction in noise interference is determined by the number of turns per foot. Increasing the number of turns per foot decreases noise interference.
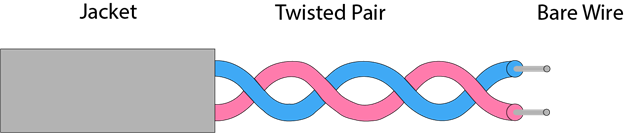
Fig 31 – Twisted pair
Types of Twisted pair:
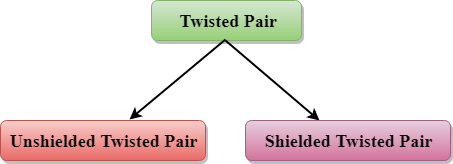
Fig 32 – Types of twisted pair
Unshielded Twisted Pair:
An unshielded twisted pair is widely used in telecommunication. Following are the categories of the unshielded twisted pair cable:
- Category 1: Category 1 is used for telephone lines that have low-speed data.
- Category 2: It can support upto 4Mbps.
- Category 3: It can support upto 16Mbps.
- Category 4: It can support upto 20Mbps. Therefore, it can be used for long-distance communication.
- Category 5: It can support upto 200Mbps.
Advantages Of Unshielded Twisted Pair:
- It is cheap.
- Installation of the unshielded twisted pair is easy.
- It can be used for high-speed LAN.
Disadvantage:
- This cable can only be used for shorter distances because of attenuation.
Shielded Twisted Pair
A shielded twisted pair is a cable that contains the mesh surrounding the wire that allows the higher transmission rate.
Characteristics Of Shielded Twisted Pair:
- The cost of the shielded twisted pair cable is not very high and not very low.
- An installation of STP is easy.
- It has higher capacity as compared to unshielded twisted pair cable.
- It has a higher attenuation.
- It is shielded that provides the higher data transmission rate.
Disadvantages
- It is more expensive as compared to UTP and coaxial cable.
- It has a higher attenuation rate.
Coaxial Cable
- Coaxial cable is very commonly used transmission media, for example, TV wire is usually a coaxial cable.
- The name of the cable is coaxial as it contains two conductors parallel to each other.
- It has a higher frequency as compared to Twisted pair cable.
- The inner conductor of the coaxial cable is made up of copper, and the outer conductor is made up of copper mesh. The middle core is made up of non-conductive cover that separates the inner conductor from the outer conductor.
- The middle core is responsible for the data transferring whereas the copper mesh prevents from the EMI(Electromagnetic interference).
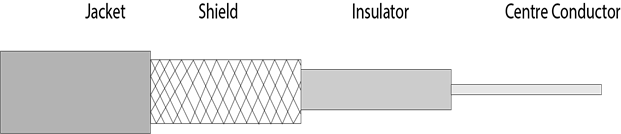
Fig 33 – Coaxial cable
Coaxial cable is of two types:
- Baseband transmission: It is defined as the process of transmitting a single signal at high speed.
- Broadband transmission: It is defined as the process of transmitting multiple signals simultaneously.
Advantages Of Coaxial cable:
- The data can be transmitted at high speed.
- It has better shielding as compared to twisted pair cable.
- It provides higher bandwidth.
Disadvantages Of Coaxial cable:
- It is more expensive as compared to twisted pair cable.
- If any fault occurs in the cable causes the failure in the entire network.
Fibre Optic
- Fibre optic cable is a cable that uses electrical signals for communication.
- Fibre optic is a cable that holds the optical fibres coated in plastic that are used to send the data by pulses of light.
- The plastic coating protects the optical fibres from heat, cold, electromagnetic interference from other types of wiring.
- Fibre optics provide faster data transmission than copper wires.
Diagrammatic representation of fibre optic cable:
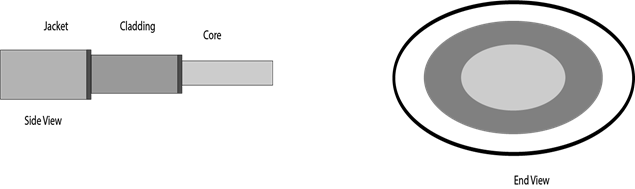
Fig 34 – Fibre optic cable
Basic elements of Fibre optic cable:
- Core: The optical fibre consists of a narrow strand of glass or plastic known as a core. A core is a light transmission area of the fibre. The more the area of the core, the more light will be transmitted into the fibre.
- Cladding: The concentric layer of glass is known as cladding. The main functionality of the cladding is to provide the lower refractive index at the core interface as to cause the reflection within the core so that the light waves are transmitted through the fibre.
- Jacket: The protective coating consisting of plastic is known as a jacket. The main purpose of a jacket is to preserve the fibre strength, absorb shock and extra fibre protection.
Following are the advantages of fibre optic cable over copper:
- Greater Bandwidth: The fibre optic cable provides more bandwidth as compared copper. Therefore, the fibre optic carries more data as compared to copper cable.
- Faster speed: Fibre optic cable carries the data in the form of light. This allows the fibre optic cable to carry the signals at a higher speed.
- Longer distances: The fibre optic cable carries the data at a longer distance as compared to copper cable.
- Better reliability: The fibre optic cable is more reliable than the copper cable as it is immune to any temperature changes while it can cause obstruct in the connectivity of copper cable.
- Thinner and Sturdier: Fibre optic cable is thinner and lighter in weight so it can withstand more pull pressure than copper cable.
Unguided Transmission
- An unguided transmission transmits the electromagnetic waves without using any physical medium. Therefore it is also known as wireless transmission.
- In unguided media, air is the media through which the electromagnetic energy can flow easily.
Unguided transmission is broadly classified into three categories:
Radio waves
- Radio waves are the electromagnetic waves that are transmitted in all the directions of free space.
- Radio waves are omnidirectional, i.e., the signals are propagated in all the directions.
- The range in frequencies of radio waves is from 3Khz to 1 khz.
- In the case of radio waves, the sending and receiving antenna are not aligned, i.e., the wave sent by the sending antenna can be received by any receiving antenna.
- An example of the radio wave is FM radio.
Fig 35 – FM radio
Applications Of Radio waves:
- A Radio wave is useful for multicasting when there is one sender and many receivers.
- An FM radio, television, cordless phones are examples of a radio wave.
Advantages Of Radio transmission:
- Radio transmission is mainly used for wide area networks and mobile cellular phones.
- Radio waves cover a large area, and they can penetrate the walls.
- Radio transmission provides a higher transmission rate.
Microwaves
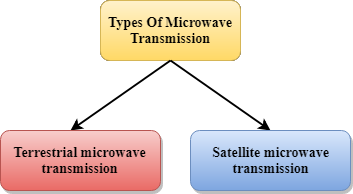
Fig 36 – Types of microwave transmission
Microwaves are of two types:
- Terrestrial microwave
- Satellite microwave communication.
Terrestrial Microwave Transmission
- Terrestrial Microwave transmission is a technology that transmits the focused beam of a radio signal from one ground-based microwave transmission antenna to another.
- Microwaves are the electromagnetic waves having the frequency in the range from 1GHz to 1000 GHz.
- Microwaves are unidirectional as the sending and receiving antenna is to be aligned, i.e., the waves sent by the sending antenna are narrowly focussed.
- In this case, antennas are mounted on the towers to send a beam to another antenna which is km away.
- It works on the line of sight transmission, i.e., the antennas mounted on the towers are the direct sight of each other.
Characteristics of Microwave:
- Frequency range: The frequency range of terrestrial microwave is from 4-6 GHz to 21-23 GHz.
- Bandwidth: It supports the bandwidth from 1 to 10 Mbps.
- Short distance: It is inexpensive for short distance.
- Long distance: It is expensive as it requires a higher tower for a longer distance.
- Attenuation: Attenuation means loss of signal. It is affected by environmental conditions and antenna size.
Advantages Of Microwave:
- Microwave transmission is cheaper than using cables.
- It is free from land acquisition as it does not require any land for the installation of cables.
- Microwave transmission provides an easy communication in terrains as the installation of cable in terrain is quite a difficult task.
- Communication over oceans can be achieved by using microwave transmission.
Disadvantages of Microwave transmission:
- Eavesdropping: An eavesdropping creates insecure communication. Any malicious user can catch the signal in the air by using its own antenna.
- Out of phase signal: A signal can be moved out of phase by using microwave transmission.
- Susceptible to weather condition: A microwave transmission is susceptible to weather condition. This means that any environmental change such as rain, wind can distort the signal.
- Bandwidth limited: Allocation of bandwidth is limited in the case of microwave transmission.
Satellite Microwave Communication
- A satellite is a physical object that revolves around the earth at a known height.
- Satellite communication is more reliable nowadays as it offers more flexibility than cable and fibre optic systems.
- We can communicate with any point on the globe by using satellite communication.
How Does Satellite work?
The satellite accepts the signal that is transmitted from the earth station, and it amplifies the signal. The amplified signal is retransmitted to another earth station.
Advantages Of Satellite Microwave Communication:
- The coverage area of a satellite microwave is more than the terrestrial microwave.
- The transmission cost of the satellite is independent of the distance from the centre of the coverage area.
- Satellite communication is used in mobile and wireless communication applications.
- It is easy to install.
- It is used in a wide variety of applications such as weather forecasting, radio/TV signal broadcasting, mobile communication, etc.
Disadvantages Of Satellite Microwave Communication:
- Satellite designing and development requires more time and higher cost.
- The Satellite needs to be monitored and controlled on regular periods so that it remains in orbit.
- The life of the satellite is about 12-15 years. Due to this reason, another launch of the satellite has to be planned before it becomes non-functional.
Infrared
- An infrared transmission is a wireless technology used for communication over short ranges.
- The frequency of the infrared in the range from 300 GHz to 400 THz.
- It is used for short-range communication such as data transfer between two cell phones, TV remote operation, data transfer between a computer and cell phone resides in the same closed area.
Characteristics Of Infrared:
- It supports high bandwidth, and hence the data rate will be very high.
- Infrared waves cannot penetrate the walls. Therefore, the infrared communication in one room cannot be interrupted by the nearby rooms.
- An infrared communication provides better security with minimum interference.
- Infrared communication is unreliable outside the building because the sun rays will interfere with the infrared waves.
Key takeaways
- Transmission media is a communication channel that carries the information from the sender to the receiver. Data is transmitted through the electromagnetic signals.
- The main functionality of the transmission media is to carry the information in the form of bits through LAN(Local Area Network).
- It is a physical path between transmitter and receiver in data communication.
- In a copper-based network, the bits in the form of electrical signals.
- In a fibre based network, the bits in the form of light pulses.
- In OSI(Open System Interconnection) phase, transmission media supports the Layer 1. Therefore, it is considered to be as a Layer 1 component.
- The electrical signals can be sent through the copper wire, fibre optics, atmosphere, water, and vacuum.
- The characteristics and quality of data transmission are determined by the characteristics of medium and signal.
- Transmission media is of two types are wired media and wireless media. In wired media, medium characteristics are more important whereas, in wireless media, signal characteristics are more important.
- Different transmission media have different properties such as bandwidth, delay, cost and ease of installation and maintenance.
- The transmission media is available in the lowest layer of the OSI reference model, i.e., Physical layer.
Computer Network Types
A computer network is a group of computers linked to each other that enables the computer to communicate with another computer and share their resources, data, and applications.
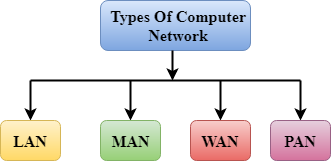
A computer network can be categorized by their size. A computer network is mainly of four types:
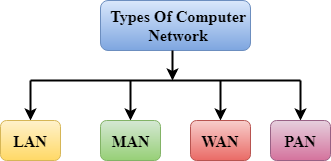
Fig 37 – Types of computer network
- LAN(Local Area Network)
- PAN(Personal Area Network)
- MAN(Metropolitan Area Network)
- WAN(Wide Area Network)
LAN(Local Area Network)
- Local Area Network is a group of computers connected to each other in a small area such as building, office.
- LAN is used for connecting two or more personal computers through a communication medium such as twisted pair, coaxial cable, etc.
- It is less costly as it is built with inexpensive hardware such as hubs, network adapters, and ethernet cables.
- The data is transferred at an extremely faster rate in Local Area Network.
- Local Area Network provides higher security.
Fig 38 – LAN
PAN(Personal Area Network)
- Personal Area Network is a network arranged within an individual person, typically within a range of 10 meters.
- Personal Area Network is used for connecting the computer devices of personal use is known as Personal Area Network.
- Thomas Zimmerman was the first research scientist to bring the idea of the Personal Area Network.
- Personal Area Network covers an area of 30 feet.
- Personal computer devices that are used to develop the personal area network are the laptop, mobile phones, media player and play stations.
Fig 39 – PAN
There are two types of Personal Area Network:
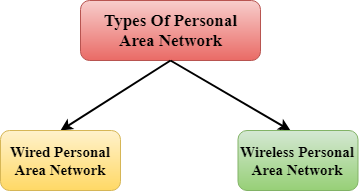
Fig 40 – Types of PAN
- Wired Personal Area Network
- Wireless Personal Area Network
Wireless Personal Area Network: Wireless Personal Area Network is developed by simply using wireless technologies such as WiFi, Bluetooth. It is a low range network.
Wired Personal Area Network: Wired Personal Area Network is created by using the USB.
Examples Of Personal Area Network:
- Body Area Network: Body Area Network is a network that moves with a person. For example, a mobile network moves with a person. Suppose a person establishes a network connection and then creates a connection with another device to share the information.
- Offline Network: An offline network can be created inside the home, so it is also known as a home network. A home network is designed to integrate the devices such as printers, computer, television but they are not connected to the internet.
- Small Home Office: It is used to connect a variety of devices to the internet and to a corporate network using a VPN
MAN(Metropolitan Area Network)
- A metropolitan area network is a network that covers a larger geographic area by interconnecting a different LAN to form a larger network.
- Government agencies use MAN to connect to the citizens and private industries.
- In MAN, various LANs are connected to each other through a telephone exchange line.
- The most widely used protocols in MAN are RS-232, Frame Relay, ATM, ISDN, OC-3, ADSL, etc.
- It has a higher range than Local Area Network(LAN).
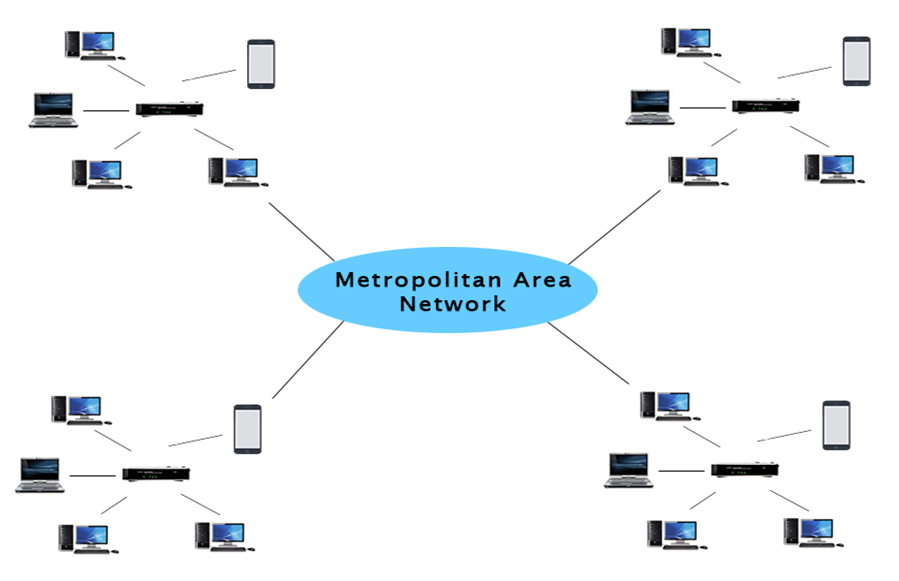
Fig 41 – MAN
Uses Of Metropolitan Area Network:
- MAN is used in communication between the banks in a city.
- It can be used in an Airline Reservation.
- It can be used in a college within a city.
- It can also be used for communication in the military.
WAN(Wide Area Network)
- A Wide Area Network is a network that extends over a large geographical area such as states or countries.
- A Wide Area Network is quite bigger network than the LAN.
- A Wide Area Network is not limited to a single location, but it spans over a large geographical area through a telephone line, fibre optic cable or satellite links.
- The internet is one of the biggest WAN in the world.
- A Wide Area Network is widely used in the field of Business, government, and education.
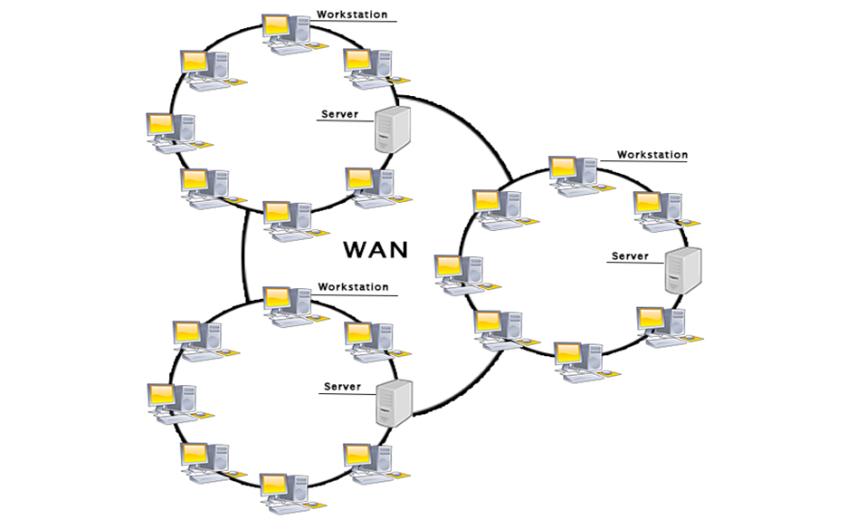
Fig 42 – WAN
Examples Of Wide Area Network:
- Mobile Broadband: A 4G network is widely used across a region or country.
- Last mile: A telecom company is used to provide the internet services to the customers in hundreds of cities by connecting their home with fiber.
- Private network: A bank provides a private network that connects the 44 offices. This network is made by using the telephone leased line provided by the telecom company.
Advantages Of Wide Area Network:
Following are the advantages of the Wide Area Network:
- Geographical area: A Wide Area Network provides a large geographical area. Suppose if the branch of our office is in a different city then we can connect with them through WAN. The internet provides a leased line through which we can connect with another branch.
- Centralized data: In case of WAN network, data is centralized. Therefore, we do not need to buy the emails, files or back up servers.
- Get updated files: Software companies work on the live server. Therefore, the programmers get the updated files within seconds.
- Exchange messages: In a WAN network, messages are transmitted fast. The web application like Facebook, Whatsapp, Skype allows you to communicate with friends.
- Sharing of software and resources: In WAN network, we can share the software and other resources like a hard drive, RAM.
- Global business: We can do the business over the internet globally.
- High bandwidth: If we use the leased lines for our company then this gives the high bandwidth. The high bandwidth increases the data transfer rate which in turn increases the productivity of our company.
Disadvantages of Wide Area Network:
The following are the disadvantages of the Wide Area Network:
- Security issue: A WAN network has more security issues as compared to LAN and MAN network as all the technologies are combined together that creates the security problem.
- Needs Firewall & antivirus software: The data is transferred on the internet which can be changed or hacked by the hackers, so the firewall needs to be used. Some people can inject the virus in our system so antivirus is needed to protect from such a virus.
- High Setup cost: An installation cost of the WAN network is high as it involves the purchasing of routers, switches.
- Troubleshooting problems: It covers a large area so fixing the problem is difficult.
Internetwork
- An internetwork is defined as two or more computer network LANs or WAN or computer network segments are connected using devices, and they are configured by a local addressing scheme. This process is known as internetworking.
- An interconnection between public, private, commercial, industrial, or government computer networks can also be defined as internetworking.
- An internetworking uses the internet protocol.
- The reference model used for internetworking is Open System Interconnection(OSI).
Types Of Internetwork:
1. Extranet: An extranet is a communication network based on the internet protocol such as Transmission Control protocol and internet protocol. It is used for information sharing. The access to the extranet is restricted to only those users who have login credentials. An extranet is the lowest level of internetworking. It can be categorized as MAN, WAN or other computer networks. An extranet cannot have a single LAN, atleast it must have one connection to the external network.
2. Intranet: An intranet is a private network based on the internet protocol such as Transmission Control protocol and internet protocol. An intranet belongs to an organization which is only accessible by the organization's employee or members. The main aim of the intranet is to share the information and resources among the organization employees. An intranet provides the facility to work in groups and for teleconferences.
Intranet advantages:
- Communication: It provides a cheap and easy communication. An employee of the organization can communicate with another employee through email, chat.
- Time-saving: Information on the intranet is shared in real time, so it is time-saving.
- Collaboration: Collaboration is one of the most important advantage of the intranet. The information is distributed among the employees of the organization and can only be accessed by the authorized user.
- Platform independency: It is a neutral architecture as the computer can be connected to another device with different architecture.
- Cost effective: People can see the data and documents by using the browser and distributes the duplicate copies over the intranet. This leads to a reduction in the cost.
Introduction to Wireless LAN
Wireless LAN stands for Wireless Local Area Network. It is also called LAWN (Local Area Wireless Network). WLAN is one in which a mobile user can connect to a Local Area Network (LAN) through a wireless connection.
The IEEE 802.11 group of standards defines the technologies for wireless LANs. For path sharing, 802.11 standard uses the Ethernet protocol and CSMA/CA (carrier sense multiple access with collision avoidance). It also uses an encryption method i.e. wired equivalent privacy algorithm.
Wireless LANs provide high speed data communication in small areas such as building or an office. WLANs allow users to move around in a confined area while they are still connected to the network.
In some instance wireless LAN technology is used to save costs and avoid laying cable, while in other cases, it is the only option for providing high-speed internet access to the public. Whatever the reason, wireless solutions are popping up everywhere.
Examples of WLANs that are available today are NCR's waveLAN and Motorola's ALTAIR.
Advantages of WLANs
- Flexibility: Within radio coverage, nodes can communicate without further restriction. Radio waves can penetrate walls, senders and receivers can be placed anywhere (also non-visible, e.g., within devices, in walls etc.).
- Planning: Only wireless ad-hoc networks allow for communication without previous planning, any wired network needs wiring plans.
- Design: Wireless networks allow for the design of independent, small devices which can for example be put into a pocket. Cables not only restrict users but also designers of small notepads, PDAs, etc.
- Robustness: Wireless networks can handle disasters, e.g., earthquakes, flood etc. whereas, networks requiring a wired infrastructure will usually break down completely in disasters.
- Cost: The cost of installing and maintaining a wireless LAN is on average lower than the cost of installing and maintaining a traditional wired LAN, for two reasons. First, after providing wireless access to the wireless network via an access point for the first user, adding additional users to a network will not increase the cost. And second, wireless LAN eliminates the direct costs of cabling and the labor associated with installing and repairing it.
- Ease of Use: Wireless LAN is easy to use and the users need very little new information to take advantage of WLANs.
Disadvantages of WLANs
- Quality of Services: Quality of wireless LAN is typically lower than wired networks. The main reason for this is the lower bandwidth due to limitations is radio transmission, higher error rates due to interference and higher delay/delay variation due to extensive error correction and detection mechanisms.
- Proprietary Solutions: Due to slow standardization procedures, many companies have come up with proprietary solutions offering standardization functionality plus many enhanced features. Most components today adhere to the basic standards IEEE 802.11a or 802.11b.
- Restrictions: Several govt. And non-govt. Institutions world-wide regulate the operation and restrict frequencies to minimize interference.
- Global operation: Wireless LAN products are sold in all countries so, national and international frequency regulations have to be considered.
- Low Power: Devices communicating via a wireless LAN are typically power consuming, also wireless devices running on battery power. Whereas the LAN design should take this into account and implement special power saving modes and power management functions.
- License free operation: LAN operators don't want to apply for a special license to be able to use the product. The equipment must operate in a license free band, such as the 2.4 GHz ISM band.
- Robust transmission technology: If wireless LAN uses radio transmission, many other electrical devices can interfere with them (such as vacuum cleaner, train engines, hair dryers, etc.).Wireless LAN transceivers cannot be adjusted for perfect transmission is a standard office or production environment.
Wired
In computing terminology, the term "wired" is used to differentiate between wireless connections and those that involve cables. While wireless devices communicate over the air, a wired setup uses physical cables to transfer data between different devices and computer systems.
A wired network is a common type of wired configuration. Most wired networks use Ethernet cables to transfer data between connected PCs. In a small wired network, a single router may be used to connect all the computers. Larger networks often involve multiple routers or switches that connect to each other. One of these devices typically connects to a cable modem, T1 line, or other type of Internet connection that provides Internet access to all devices connected to the network.
Wired may refer to peripheral devices as well. Since many keyboards and mice are now wireless, "wired" is often used to describe input devices that connect to a USB port. Peripherals such as monitors and external hard drives also use cables, but they are rarely called wired devices since wireless options are generally not available.
While many peripherals are now wireless, some users still prefer wired devices, since they have a few benefits over their wireless counterparts. For example, an Ethernet connection is not prone to signal interference that can slow down Wi-Fi connections. Additionally, wired network connections are often faster than wireless ones, which allows for faster data transfer rates. Some users also prefer wired peripherals since their is no need to replace batteries on a regular basis. Gamers especially prefer wired keyboards and mice since they have lower latency and can be backlit, thanks to the power provided by the USB connection.
What is Virtual LAN?
Virtual Local Area Networks or Virtual LANs (VLANs) are a logical group of computers that appear to be on the same LAN irrespective of the configuration of the underlying physical network. Network administrators partition the networks to match the functional requirements of the VLANs so that each VLAN comprise of a subset of ports on a single or multiple switches or bridges. This allows computers and devices in a VLAN to communicate in the simulated environment as if it is a separate LAN.
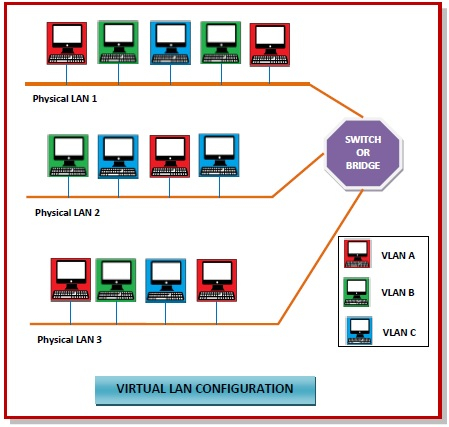
Fig 43 – VLAN
Features of VLANs
- A VLAN forms sub-network grouping together devices on separate physical LANs.
- VLAN's help the network manager to segment LANs logically into different broadcast domains.
- VLANs function at layer 2, i.e. Data Link Layer of the OSI model.
- There may be one or more network bridges or switches to form multiple, independent VLANs.
- Using VLANs, network administrators can easily partition a single switched network into multiple networks depending upon the functional and security requirements of their systems.
- VLANs eliminate the requirement to run new cables or reconfiguring physical connections in the present network infrastructure.
- VLANs help large organizations to re-partition devices aiming improved traffic management.
- VLANs also provide better security management allowing partitioning of devices according to their security criteria and also by ensuring a higher degree of control connected devices.
- VLANs are more flexible than physical LANs since they are formed by logical connections. This aids is quicker and cheaper reconfiguration of devices when the logical partitioning needs to be changed.
Types of VLANs
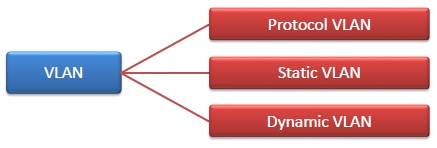
Fig 44 – Types of VLAN
- Protocol VLAN − Here, the traffic is handled based on the protocol used. A switch or bridge segregates, forwards or discards frames the come to it based upon the traffics protocol.
- Port-based VLAN − This is also called static VLAN. Here, the network administrator assigns the ports on the switch / bridge to form a virtual network.
- Dynamic VLAN − Here, the network administrator simply defines network membership according to device characteristics
Key takeaways
- A computer network is a group of computers linked to each other that enables the computer to communicate with another computer and share their resources, data, and applications.
- A computer network can be categorized by their size. A computer network is mainly of four types:
- LAN(Local Area Network)
- PAN(Personal Area Network)
- MAN(Metropolitan Area Network)
- WAN(Wide Area Network)
What is Multiplexing?
Multiplexing is a technique used to combine and send the multiple data streams over a single medium. The process of combining the data streams is known as multiplexing and hardware used for multiplexing is known as a multiplexer.
Multiplexing is achieved by using a device called Multiplexer (MUX) that combines n input lines to generate a single output line. Multiplexing follows many-to-one, i.e., n input lines and one output line.
Demultiplexing is achieved by using a device called Demultiplexer (DEMUX) available at the receiving end. DEMUX separates a signal into its component signals (one input and n outputs). Therefore, we can say that demultiplexing follows the one-to-many approach.
Why Multiplexing?
- The transmission medium is used to send the signal from sender to receiver. The medium can only have one signal at a time.
- If there are multiple signals to share one medium, then the medium must be divided in such a way that each signal is given some portion of the available bandwidth. For example: If there are 10 signals and bandwidth of medium is100 units, then the 10 unit is shared by each signal.
- When multiple signals share the common medium, there is a possibility of collision. Multiplexing concept is used to avoid such collision.
- Transmission services are very expensive.
History of Multiplexing
- Multiplexing technique is widely used in telecommunications in which several telephone calls are carried through a single wire.
- Multiplexing originated in telegraphy in the early 1870s and is now widely used in communication.
- George Owen Squier developed the telephone carrier multiplexing in 1910.
Concept of Multiplexing
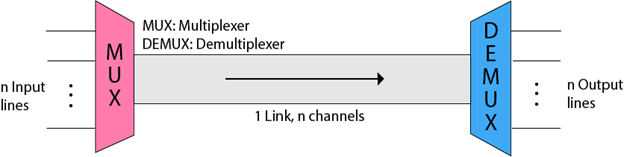
Fig 45 – Multiplexing
- The 'n' input lines are transmitted through a multiplexer and multiplexer combines the signals to form a composite signal.
- The composite signal is passed through a Demultiplexer and demultiplexer separates a signal to component signals and transfers them to their respective destinations.
Advantages of Multiplexing:
- More than one signal can be sent over a single medium.
- The bandwidth of a medium can be utilized effectively.
Multiplexing Techniques
Multiplexing techniques can be classified as:
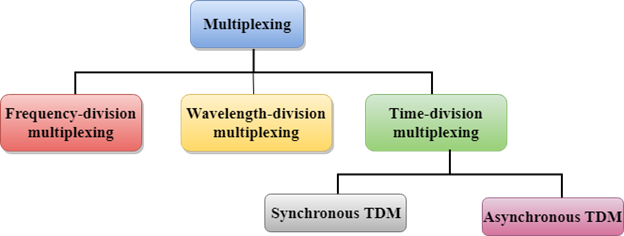
Fig 46 - Multiplexing techniques
Frequency-division Multiplexing (FDM)
- It is an analog technique.
- Frequency Division Multiplexing is a technique in which the available bandwidth of a single transmission medium is subdivided into several channels.
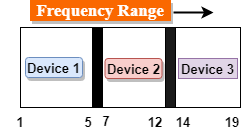
Fig 47 – Frequency range
- In the above diagram, a single transmission medium is subdivided into several frequency channels, and each frequency channel is given to different devices. Device 1 has a frequency channel of range from 1 to 5.
- The input signals are translated into frequency bands by using modulation techniques, and they are combined by a multiplexer to form a composite signal.
- The main aim of the FDM is to subdivide the available bandwidth into different frequency channels and allocate them to different devices.
- Using the modulation technique, the input signals are transmitted into frequency bands and then combined to form a composite signal.
- The carriers which are used for modulating the signals are known as sub-carriers. They are represented as f1,f2..fn.
- FDM is mainly used in radio broadcasts and TV networks.
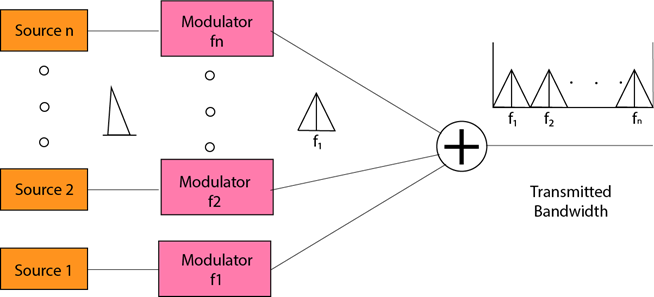
Fig 48 – FDM
Advantages Of FDM:
- FDM is used for analog signals.
- FDM process is very simple and easy modulation.
- A Large number of signals can be sent through an FDM simultaneously.
- It does not require any synchronization between sender and receiver.
Disadvantages Of FDM:
- FDM technique is used only when low-speed channels are required.
- It suffers the problem of crosstalk.
- A Large number of modulators are required.
- It requires a high bandwidth channel.
Applications Of FDM:
- FDM is commonly used in TV networks.
- It is used in FM and AM broadcasting. Each FM radio station has different frequencies, and they are multiplexed to form a composite signal. The multiplexed signal is transmitted in the air.
Wavelength Division Multiplexing (WDM)
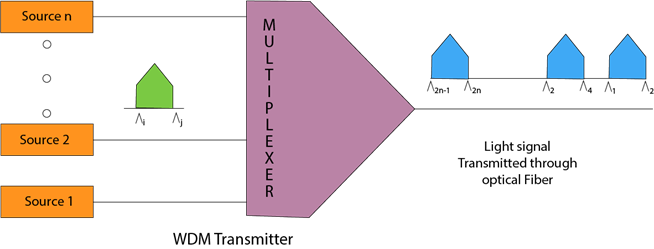
Fig 49 – WDM
- Wavelength Division Multiplexing is same as FDM except that the optical signals are transmitted through the fibre optic cable.
- WDM is used on fibre optics to increase the capacity of a single fibre.
- It is used to utilize the high data rate capability of fibre optic cable.
- It is an analog multiplexing technique.
- Optical signals from different source are combined to form a wider band of light with the help of multiplexer.
- At the receiving end, demultiplexer separates the signals to transmit them to their respective destinations.
- Multiplexing and Demultiplexing can be achieved by using a prism.
- Prism can perform a role of multiplexer by combining the various optical signals to form a composite signal, and the composite signal is transmitted through a fibre optical cable.
- Prism also performs a reverse operation, i.e., demultiplexing the signal.
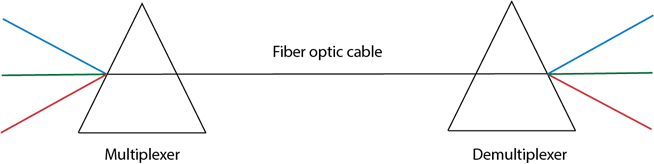
Fig 50 – Fiber optic cable
Time Division Multiplexing
- It is a digital technique.
- In Frequency Division Multiplexing Technique, all signals operate at the same time with different frequency, but in case of Time Division Multiplexing technique, all signals operate at the same frequency with different time.
- In Time Division Multiplexing technique, the total time available in the channel is distributed among different users. Therefore, each user is allocated with different time interval known as a Time slot at which data is to be transmitted by the sender.
- A user takes control of the channel for a fixed amount of time.
- In Time Division Multiplexing technique, data is not transmitted simultaneously rather the data is transmitted one-by-one.
- In TDM, the signal is transmitted in the form of frames. Frames contain a cycle of time slots in which each frame contains one or more slots dedicated to each user.
- It can be used to multiplex both digital and analog signals but mainly used to multiplex digital signals.
There are two types of TDM:
- Synchronous TDM
- Asynchronous TDM
Synchronous TDM
- A Synchronous TDM is a technique in which time slot is preassigned to every device.
- In Synchronous TDM, each device is given some time slot irrespective of the fact that the device contains the data or not.
- If the device does not have any data, then the slot will remain empty.
- In Synchronous TDM, signals are sent in the form of frames. Time slots are organized in the form of frames. If a device does not have data for a particular time slot, then the empty slot will be transmitted.
- The most popular Synchronous TDM are T-1 multiplexing, ISDN multiplexing, and SONET multiplexing.
- If there are n devices, then there are n slots.
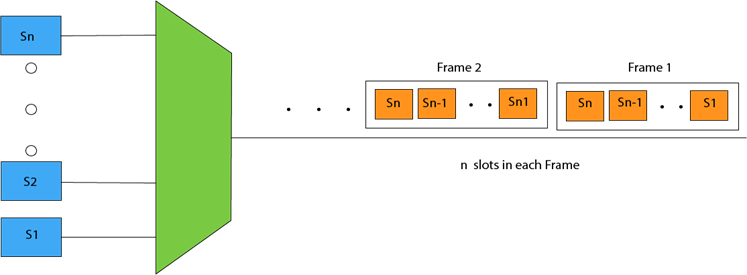
Fig 51 - Synchronous TDM
Concept Of Synchronous TDM
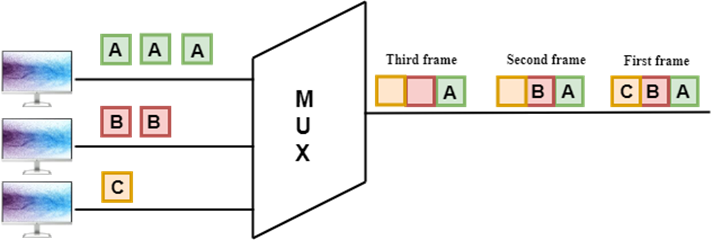
Fig 52 – MUX
In the above figure, the Synchronous TDM technique is implemented. Each device is allocated with some time slot. The time slots are transmitted irrespective of whether the sender has data to send or not.
Disadvantages Of Synchronous TDM:
- The capacity of the channel is not fully utilized as the empty slots are also transmitted which is having no data. In the above figure, the first frame is completely filled, but in the last two frames, some slots are empty. Therefore, we can say that the capacity of the channel is not utilized efficiently.
- The speed of the transmission medium should be greater than the total speed of the input lines. An alternative approach to the Synchronous TDM is Asynchronous Time Division Multiplexing.
Asynchronous TDM
- An asynchronous TDM is also known as Statistical TDM.
- An asynchronous TDM is a technique in which time slots are not fixed as in the case of Synchronous TDM. Time slots are allocated to only those devices which have the data to send. Therefore, we can say that Asynchronous Time Division multiplexor transmits only the data from active workstations.
- An asynchronous TDM technique dynamically allocates the time slots to the devices.
- In Asynchronous TDM, total speed of the input lines can be greater than the capacity of the channel.
- Asynchronous Time Division multiplexor accepts the incoming data streams and creates a frame that contains only data with no empty slots.
- In Asynchronous TDM, each slot contains an address part that identifies the source of the data.
- The difference between Asynchronous TDM and Synchronous TDM is that many slots in Synchronous TDM are unutilized, but in Asynchronous TDM, slots are fully utilized. This leads to the smaller transmission time and efficient utilization of the capacity of the channel.
- In Synchronous TDM, if there are n sending devices, then there are n time slots. In Asynchronous TDM, if there are n sending devices, then there are m time slots where m is less than n (m<n).
- The number of slots in a frame depends on the statistical analysis of the number of input lines.
Concept Of Asynchronous TDM
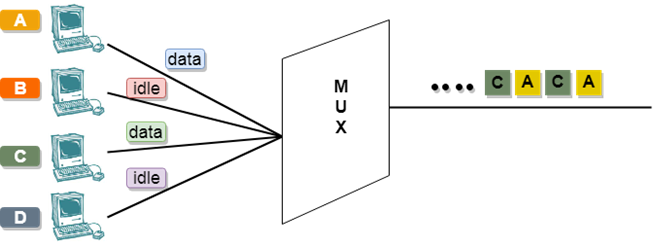
Fig 53 - Asynchronous TDM
In the above diagram, there are 4 devices, but only two devices are sending the data, i.e., A and C. Therefore, the data of A and C are only transmitted through the transmission line.
Frame of above diagram can be represented as:
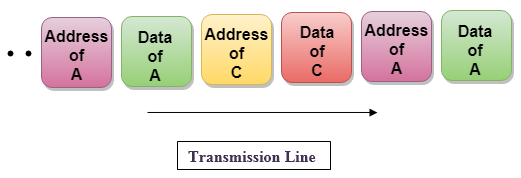
The above figure shows that the data part contains the address to determine the source of the data.
Key takeaways
- Multiplexing is a technique used to combine and send the multiple data streams over a single medium. The process of combining the data streams is known as multiplexing and hardware used for multiplexing is known as a multiplexer.
- Multiplexing is achieved by using a device called Multiplexer (MUX) that combines n input lines to generate a single output line. Multiplexing follows many-to-one, i.e., n input lines and one output line.
- Demultiplexing is achieved by using a device called Demultiplexer (DEMUX) available at the receiving end. DEMUX separates a signal into its component signals (one input and n outputs). Therefore, we can say that demultiplexing follows the one-to-many approach.
Spread spectrum is a technique used for wireless communications in telecommunication and radio communication. In this technique, the frequency of the transmitted signal, i.e., an electrical signal, electromagnetic signal, or acoustic signal, is deliberately varied and generates a much greater bandwidth than the signal would have if its frequency were not varied.
In other words, "Spread Spectrum is a technique in which the transmitted signals of specific frequencies are varied slightly to obtain greater bandwidth as compared to initial bandwidth."
Now, spread spectrum technology is widely used in radio signals transmission because it can easily reduce noise and other signal issues.
Example of Spread Spectrum
Let's see an example to understand the concept of spread spectrum in wireless communication:
We know that a conventional wireless signal frequency is usually specified in megahertz (MHz) or gigahertz (GHz). It does not change with time (Sometimes it is exceptionally changed in the form of small, rapid fluctuations that generally occur due to modulation). Suppose you want to listen to FM stereo at frequency 104.8 MHz on your radio, and then once you set the frequency, the signal stays at 104.8 MHz. It does not go up to 105.1 MHz or down to 101.1 MHz. You see that your set digits on the radio's frequency dial stay the same at all times. The frequency of a conventional wireless signal is kept as constant to keep bandwidth within certain limits, and the signal can be easily located by someone who wants to retrieve the information.
In this conventional wireless communication model, you can face at least two problems:
- A signal whose frequency is constant is subject to catastrophic interference. This interference occurs when another signal is transmitted on or near the frequency of a specified signal.
- A constant-frequency signal can easily be intercepted. So, it is not suitable for the applications in which information must be kept confidential between the source (transmitting party) and the receiver.
The spread spectrum model is used to overcome with this conventional communication model. Here, the transmitted signal frequency is deliberately varied over a comparatively large segment of the electromagnetic radiation spectrum. This variation is done according to a specific but complicated mathematical function. If the receiver wants to intercept the signal, it must be tuned to frequencies that vary precisely according to this function.
Reasons to use Spread Spectrum
- Spread spectrum signals are distributed over a wide range of frequencies and then collected and received back to the receiver. On the other hand, wide-band signals are noise-like and challenging to detect.
- Initially, the spread spectrum was adopted in military applications because of its resistance to jamming and difficulty intercepting.
- Now, this is also used in commercial wireless communication.
- It is most preferred because of its useful bandwidth utilization ability.
Usage of Spread Spectrum
There are many reasons to use this spread spectrum technique for wireless communications. The following are some reasons:
- It can successfully establish a secure medium of communication.
- It can increase the resistance to natural interference, such as noise and jamming, to prevent detection.
- It can limit the power flux density (e.g., in satellite down links).
- It can enable multiple-access communications.
Types of Spread Spectrum
Spread Spectrum can be categorized into two types:
- Frequency Hopping Spread Spectrum (FHSS)
- Direct Sequence Spread Spectrum(DSSS)
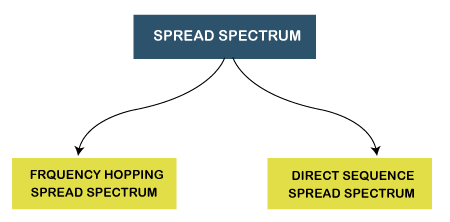
Fig 54 – Spread spectrum
Frequency Hopping Spread Spectrum (FHSS)
- The Frequency Hopping Spread Spectrum or FHSS allows us to utilize bandwidth properly and maximum. In this technique, the whole available bandwidth is divided into many channels and spread between channels, arranged continuously.
- The frequency slots are selected randomly, and frequency signals are transmitted according to their occupancy.
- The transmitters and receivers keep on hopping on channels available for a particular amount of time in milliseconds.
- So, you can see that it implements the frequency division multiplexing and time-division multiplexing simultaneously in FHSS.
The Frequency Hopping Spread Spectrum or FHSS can also be classified into two types:
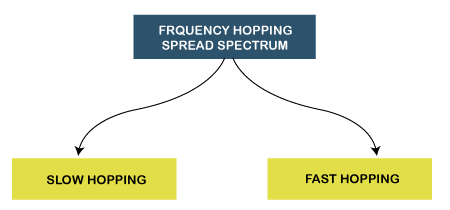
Fig 55 - Frequency Hopping Spread Spectrum
- Slow Hopping: In slow hopping, multiple bits are transmitted on a specific frequency or same frequency.
- Fast Hopping: In fast hopping, individual bits are split and then transmitted on different frequencies.
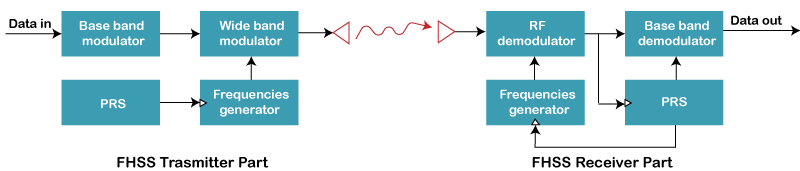
Advantages of Frequency Hopping Spread Spectrum (FHSS)
The following are some advantages of frequency hopping spread spectrum (FHSS):
- The biggest advantage of Frequency Hopping Spread Spectrum or FHSS is its high efficiency.
- The Frequency Hopping Spread Spectrum or FHSS signals are highly resistant to narrowband interference because the signal hops to a different frequency band.
- It requires a shorter time for acquisition.
- It is highly secure. Its signals are very difficult to intercept if the frequency-hopping pattern is not known; that's why it is preferred to use in Military services.
- We can easily program it to avoid some portions of the spectrum.
- Frequency Hopping Spread Spectrum or FHSS transmissions can share a frequency band with many types of conventional transmissions with minimal mutual interference. FHSS signals add minimal interference to narrowband communications, and vice versa.
- It provides a very large bandwidth.
- It can be simply implemented as compared to DsSS.
Disadvantages of Frequency Hopping Spread Spectrum (FHSS)
The following are some disadvantages of Frequency Hopping Spread Spectrum (FHSS):
- FHSS is less Robust, so sometimes it requires error correction.
- FHSS needs complex frequency synthesizers.
- FHSS supports a lower data rate of 3 Mbps as compared to the 11 Mbps data rate supported by DSSS.
- It is not very useful for range and range rate measurements.
- It supports the lower coverage range due to the high SNR requirement at the receiver.
- Nowadays, it is not very popular due to the emerging of new wireless technologies in wireless products.
Applications of Frequency Hopping Spread Spectrum (FHSS)
Following is the list of most used applications of Frequency Hopping Spread Spectrum or FHSS:
- The Frequency Hopping Spread Spectrum or FHSS is used in wireless local area networks (WLAN) standard for Wi-Fi.
- FHSS is also used in the wireless personal area networks (WPAN) standard for Bluetooth.
Direct Sequence Spread Spectrum (DSSS)
The Direct Sequence Spread Spectrum (DSSS) is a spread-spectrum modulation technique primarily used to reduce overall signal interference in telecommunication. The Direct Sequence Spread Spectrum modulation makes the transmitted signal wider in bandwidth than the information bandwidth. In DSSS, the message bits are modulated by a bit sequencing process known as a spreading sequence. This spreading-sequence bit is known as a chip. It has a much shorter duration (larger bandwidth) than the original message bits. Following are the features of Direct Sequence Spread Spectrum or DSSS.
- In Direct Sequence Spread Spectrum or DSSS technique, the data that needs to be transmitted is split into smaller blocks.
- After that, each data block is attached with a high data rate bit sequence and is transmitted from the sender end to
- The receiver end.
- Data blocks are recombined again to generate the original data at the receiver's end, which was sent by the sender, with the help of the data rate bit sequence.
- If somehow data is lost, then data blocks can also be recovered with those data rate bits.
- The main advantage of splitting the data into smaller blocks is that it reduces the noise and unintentional inference.
The Direct Sequence Spread Spectrum or DSSS can also be classified into two types:
- Wide Band Spread Spectrum
- Narrow Band Spread Spectrum
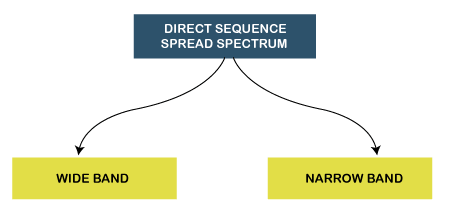
Advantages of Direct Sequence Spread Spectrum (DSSS)
The following are some advantages of Direct Sequence Spread Spectrum or DSSS:
- Direct Sequence Spread Spectrum or DSSS is less reluctant to noise; that's why the DSSS system's performance in the presence of noise is better than the FHSS system.
- In Direct Sequence Spread Spectrum or DSSS, signals are challenging to detect.
- It provides the best discrimination against multipath signals.
- In Direct Sequence Spread Spectrum, there are very few chances of jamming because it avoids intentional interference such as jamming effectively.
Disadvantages of Direct Sequence Spread Spectrum (DSSS)
The following are some disadvantages of Direct Sequence Spread Spectrum or DSSS:
- The Direct Sequence Spread Spectrum or DSSS system takes large acquisition time; that's why its performance is slow.
- It requires wide-band channels with small phase distortion.
- In DSSS, the pseudo-noise generator generates a sequence at high rates.
Applications of Direct Sequence Spread Spectrum (DSSS)
Following is the list of most used applications of Direct Sequence Spread Spectrum or DSSS:
- Direct Sequence Spread Spectrum or DSSS is used in LAN technology.
- Direct Sequence Spread Spectrum or DSSS is also used in Satellite communication technology.
- DSSS is used in the military and many other commercial applications.
- It is used in the low probability of the intercept signal.
- It supports Code division multiple access.
Key takeaways
- Spread spectrum is a technique used for wireless communications in telecommunication and radio communication. In this technique, the frequency of the transmitted signal, i.e., an electrical signal, electromagnetic signal, or acoustic signal, is deliberately varied and generates a much greater bandwidth than the signal would have if its frequency were not varied.
- In other words, "Spread Spectrum is a technique in which the transmitted signals of specific frequencies are varied slightly to obtain greater bandwidth as compared to initial bandwidth."
- Now, spread spectrum technology is widely used in radio signals transmission because it can easily reduce noise and other signal issues.
References:
1. Computer Networks, 8th Edition, Andrew S. Tanenbaum, Pearson New International Edition.
2. Internetworking with TCP/IP, Volume 1, 6th Edition Douglas Comer, Prentice Hall of India.
3. TCP/IP Illustrated, Volume 1, W. Richard Stevens, Addison-Wesley, United States of America.