Unit - 5
Application Layer
An application layer protocol defines how the application processes running on different systems, pass the messages to each other.
- DNS stands for Domain Name System.
- DNS is a directory service that provides a mapping between the name of a host on the network and its numerical address.
- DNS is required for the functioning of the internet.
- Each node in a tree has a domain name, and a full domain name is a sequence of symbols specified by dots.
- DNS is a service that translates the domain name into IP addresses. This allows the users of networks to utilize user-friendly names when looking for other hosts instead of remembering the IP addresses.
- For example, suppose the FTP site at EduSoft had an IP address of 132.147.165.50, most people would reach this site by specifying ftp.EduSoft.com. Therefore, the domain name is more reliable than IP address.
DNS is a TCP/IP protocol used on different platforms. The domain name space is divided into three different sections: generic domains, country domains, and inverse domain.
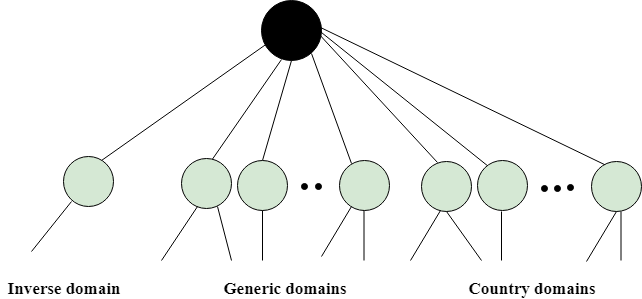
Fig 1 – DNS
Generic Domains
- It defines the registered hosts according to their generic behavior.
- Each node in a tree defines the domain name, which is an index to the DNS database.
- It uses three-character labels, and these labels describe the organization type.
Label | Description |
Aero | Airlines and aerospace companies |
Biz | Businesses or firms |
Com | Commercial Organizations |
Coop | Cooperative business Organizations |
Edu | Educational institutions |
Gov | Government institutions |
Info | Information service providers |
Int | International Organizations |
Mil | Military groups |
Museum | Museum & other nonprofit organizations |
Name | Personal names |
Net | Network Support centers |
Org | Nonprofit Organizations |
Pro | Professional individual Organizations |
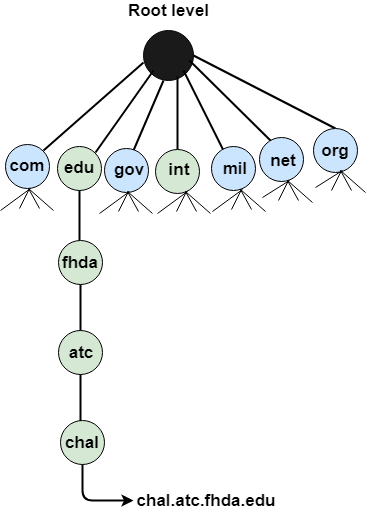
Country Domain
The format of country domain is same as a generic domain, but it uses two-character country abbreviations (e.g., us for the United States) in place of three character organizational abbreviations.
Inverse Domain
The inverse domain is used for mapping an address to a name. When the server has received a request from the client, and the server contains the files of only authorized clients. To determine whether the client is on the authorized list or not, it sends a query to the DNS server and ask for mapping an address to the name.
Working of DNS
- DNS is a client/server network communication protocol. DNS clients send requests to the. Server while DNS servers send responses to the client.
- Client requests contain a name which is converted into an IP address known as a forward DNS lookups while requests containing an IP address which is converted into a name known as reverse DNS lookups.
- DNS implements a distributed database to store the name of all the hosts available on the internet.
- If a client like a web browser sends a request containing a hostname, then a piece of software such as DNS resolver sends a request to the DNS server to obtain the IP address of a hostname. If DNS server does not contain the IP address associated with a hostname, then it forwards the request to another DNS server. If IP address has arrived at the resolver, which in turn completes the request over the internet protocol.
Key takeaways
- DNS stands for Domain Name System.
- DNS is a directory service that provides a mapping between the name of a host on the network and its numerical address.
- DNS is required for the functioning of the internet.
- Each node in a tree has a domain name, and a full domain name is a sequence of symbols specified by dots.
- DNS is a service that translates the domain name into IP addresses. This allows the users of networks to utilize user-friendly names when looking for other hosts instead of remembering the IP addresses.
- For example, suppose the FTP site at EduSoft had an IP address of 132.147.165.50, most people would reach this site by specifying ftp.EduSoft.com. Therefore, the domain name is more reliable than IP address.
5.2 SMTP
Simple Mail Transfer Protocol (SMTP)
E-mail system is implemented with the help of Message Transfer Agents (MTA). There are normally two MTAs in each mailing system. One for sending e-mails and another for receiving e-mails. The formal protocol that defines the MTA client and server in the internet is called Simple Mail Transfer Protocol (SMTP).
Fig shows the range of SMTP protocol.
By referring the above diagram, we can say that SMTP is used two times. That is between the sender and sender’s mail server and between the sender’s mail server and receiver’s mail server. Another protocol is used between the receiver’s mail server and receiver.
SMTP simply defines how commands and responses must be sent back and forth.

SMTP is a simple ASCII protocol
It establishes a TCP connection between a sender and port number 25 of the receiver. No checksums are generally required because TCP provides a reliable byte stream. After exchanging all the e-mail, the connection is released.
Commands and Responses
SMTP uses commands and responses to transfer messages between an MTA client and MTA server.
Each command or reply is terminated by a two-character (carriage return and line feed) end-of-line token.

Fig 2. Commands and Responses
Commands
Client sends commands to the server. SMTP defines 14 commands. Out of that first 5 commands are mandatory; every implementation must support these commands.
The next three commands are often used and are highly recommended. Last six commands are hardly used.
Following table shows FTP commands.
Table:
Keyword | Description |
HELO | Used by the client to identify itself. The argument is domain name of the client host. The format is: HELO: mail.viit.ac.in |
MAIL FROM | Used by the client to identify the sender of the message. The argument is email address of the sender. The format is MAIL FROM: amol.dhumane@gmail.com |
RCPT TO | Used by the client to identify the intended recipient of the message. The argument is the email address of the recipient. The format is: RCPT TO: ashwini.dhumane@yahoo.co.in |
DATA | This command is used to send the actual message. The lines following DATA command are treated as mail message. The format is: DATA There is an important meeting on this Sunday. So please be present for it. Regards; Nitin Sakhare |
QUIT | It terminates the message. The format is: QUIT |
RSET | It aborts the current email transaction. The stored information of the sender and receiver is deleted after executing the command. The connection gets reset. The format is: RSET |
VRFY | This command is used to verify the address of the recipient. In this sender asks the receiver to confirm that a name identifies a valid recipient. Its format is: VRFY: sai@puneatoz.net |
NOOP | By using this command, the client checks the status of the recipient. It requires an answer from recipient. Its format is: NOOP |
TURN | It reverses the role of sender and receiver. |
EXPN | It asks the receiving host to expand the mailing list. |
HELP | It sends system specific documentation. The format is: HELP: mail
|
SEND FROM | This command specifies that the mail is to be delivered to the terminal of the recipient, and not the mailbox. If the recipient is not logged in, the mail is bounced back. The argument is the address of the sender. The format is: SEND FROM: amol.dhumane@gmail.com |
SMOL FROM | This command specifies to send the mail to the terminal if possible, otherwise to the mailbox. |
SMAL FROM
FROM | It sends mail to the terminal and mail box. |
SMTP Working
SMTP works in the following three stages:
a) Connection Establishment
b) Message Transfer
c) Connection Termination
These are explained below:
Connection Establishment
Once the TCP connection is made on port no. 25, SMTP server starts the connection phase. This phase involves following three steps which are explained in the Fig.
The server tells the client that it is ready to receive mail by using the code 220. If the server is not ready, it sends code 421 which tells that service is not available.

Fig 3. Connection Establishment
Once the server becomes ready to receive the mails, client sends HELO message to identify itself using the domain name address. This is important step which informs the server of the domain name of the client. Remember that during TCP connection establishment, the sender and receiver know each other through their IP addresses.
Server responds with code 250 which tells that the request command is completed. Message Transfer Once the connection has been established, SMTP server sends messages to SMTP receiver.
The messages are transferred in three stages
A MAIL command identifies the message originator.
RCPT command identifies the receiver of the message.
DATA command transfers the message text.
Connection Closing
After the message is transferred successfully, the client terminates the connection. The connection is terminated in two steps The client sends the quit command.
The server responds with code 221 or some other appropriate code. After the connection termination phase, the TCP connection must be closed.
Post Office Protocol, version 3 (POP3) is simple and feature-limited. The POP3 client software is installed on the receiving machine; the POP3 server software is installed on the mail server.
If the user wants to download e-mails from the mailbox on the mail server, mail access begins with the client. On TCP port 110, the client opens a connection to the server. In order to reach the mailbox, it then sends the user name and password. The user will then, one by one, list and retrieve the mail messages.
There are two modes for POP3: the delete mode and the hold mode. In the delete mode, after each retrieval, the mail is removed from the mailbox. In keep mode, after retrieval, the mail stays in the mailbox. When the user is operating on their permanent device, the delete mode is usually used and after reading or replying, the received mail can be saved and sorted. Normally, the keep mode is used when the user accesses her mail away from her main computer (e.g., a laptop). For later retrieval and organisation, the mail is read but kept in the system.
In some aspects, POP3 is deficient. It does not allow the user to arrange his mail on the server; it is impossible for the user to have multiple folders on the server. (The user will build directories on their own computer, of course.)
Advantages of POP
- As they are already saved on our PC, it provides easy and simple access to the emails.
- The size of the email that we receive or send has no limit.
- When all emails are saved on the local computer, it takes less server storage space.
- The maximum size of a mailbox is available, but the size of the hard disc is limited.
- It is a straightforward protocol, so it is one of the most common protocols used today.
- Configuring and using it is simple.
Disadvantages of POP
- By default, if the emails are downloaded from the server, all the emails are deleted from the server. Mails will also not be accessed from other computers unless they are programmed to leave a mail copy on the server.
- It can be tough to move the mail folder from the local computer to another machine.
- As all of the attachments are placed on your local computer, if the virus scanner does not scan them, there is a high chance of a virus attack. Virus attacks can destroy your machine.
- There could also be corruption in the email folder that is downloaded from the mail server.
- Mails are saved on a local server, so the email folder can be accessed by someone who is sitting on your machine.
Key takeaway:
- Post Office Protocol, version 3 is simple and feature-limited.
- The POP3 client software is installed on the receiving machine; the POP3 server software is installed on the mail server.
- In order to reach the mailbox, it then sends the user name and password.
- FTP stands for File transfer protocol.
- FTP is a standard internet protocol provided by TCP/IP used for transmitting the files from one host to another.
- It is mainly used for transferring the web page files from their creator to the computer that acts as a server for other computers on the internet.
- It is also used for downloading the files to computer from other servers.
Objectives of FTP
- It provides the sharing of files.
- It is used to encourage the use of remote computers.
- It transfers the data more reliably and efficiently.
Why FTP?
Although transferring files from one system to another is very simple and straightforward, but sometimes it can cause problems. For example, two systems may have different file conventions. Two systems may have different ways to represent text and data. Two systems may have different directory structures. FTP protocol overcomes these problems by establishing two connections between hosts. One connection is used for data transfer, and another connection is used for the control connection.
Mechanism of FTP
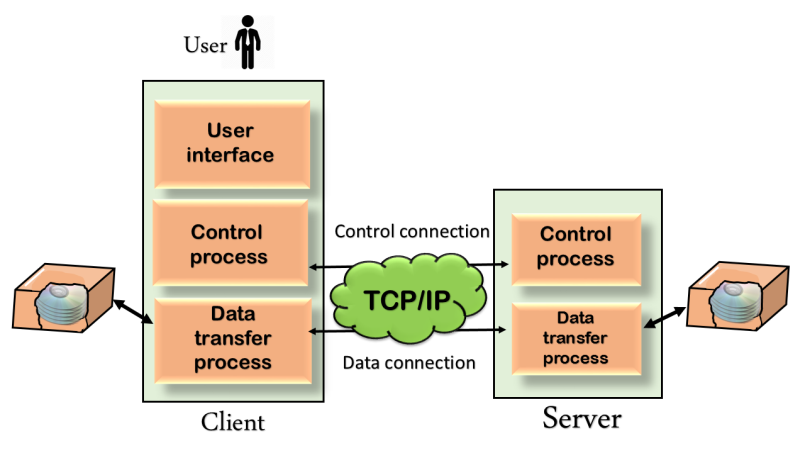
Fig 4 – Mechanism of FTP
The above figure shows the basic model of the FTP. The FTP client has three components: the user interface, control process, and data transfer process. The server has two components: the server control process and the server data transfer process.
There are two types of connections in FTP:
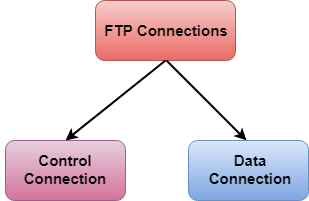
Fig 5 – FTP Connections
- Control Connection: The control connection uses very simple rules for communication. Through control connection, we can transfer a line of command or line of response at a time. The control connection is made between the control processes. The control connection remains connected during the entire interactive FTP session.
- Data Connection: The Data Connection uses very complex rules as data types may vary. The data connection is made between data transfer processes. The data connection opens when a command comes for transferring the files and closes when the file is transferred.
FTP Clients
- FTP client is a program that implements a file transfer protocol which allows you to transfer files between two hosts on the internet.
- It allows a user to connect to a remote host and upload or download the files.
- It has a set of commands that we can use to connect to a host, transfer the files between you and your host and close the connection.
- The FTP program is also available as a built-in component in a Web browser. This GUI based FTP client makes the file transfer very easy and also does not require to remember the FTP commands.
Advantages of FTP:
- Speed: One of the biggest advantages of FTP is speed. The FTP is one of the fastest way to transfer the files from one computer to another computer.
- Efficient: It is more efficient as we do not need to complete all the operations to get the entire file.
- Security: To access the FTP server, we need to login with the username and password. Therefore, we can say that FTP is more secure.
- Back & forth movement: FTP allows us to transfer the files back and forth. Suppose you are a manager of the company, you send some information to all the employees, and they all send information back on the same server.
Disadvantages of FTP:
- The standard requirement of the industry is that all the FTP transmissions should be encrypted. However, not all the FTP providers are equal and not all the providers offer encryption. So, we will have to look out for the FTP providers that provides encryption.
- FTP serves two operations, i.e., to send and receive large files on a network. However, the size limit of the file is 2GB that can be sent. It also doesn't allow you to run simultaneous transfers to multiple receivers.
- Passwords and file contents are sent in clear text that allows unwanted eavesdropping. So, it is quite possible that attackers can carry out the brute force attack by trying to guess the FTP password.
- It is not compatible with every system.
Hypertext Transfer Protocol (HTTP):
Hyper Text Transfer Protocol (HTTP) is an application layer protocol which enables WWW to work smoothly and effectively. It is based on a client-server model. The client is a web browser which communicates with the web server which hosts the website. This protocol defines how messages are formatted and transmitted and what actions the Web Server and browser should take in response to different commands. When you enter a URL in the browser, an HTTP command is sent to the Web server, and it transmits the requested Web Page.
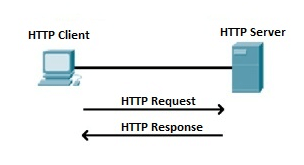
Fig 6 – HTTP Request and Response
When we open a website using a browser, a connection to the web server is opened, and the browser communicates with the server through HTTP and sends a request. HTTP is carried over TCP/IP to communicate with the server. The server processes the browser's request and sends a response, and then the connection is closed. Thus, the browser retrieves content from the server for the user.
HTTP
- HTTP stands for HyperText Transfer Protocol.
- It is a protocol used to access the data on the World Wide Web (www).
- The HTTP protocol can be used to transfer the data in the form of plain text, hypertext, audio, video, and so on.
- This protocol is known as HyperText Transfer Protocol because of its efficiency that allows us to use in a hypertext environment where there are rapid jumps from one document to another document.
- HTTP is similar to the FTP as it also transfers the files from one host to another host. But, HTTP is simpler than FTP as HTTP uses only one connection, i.e., no control connection to transfer the files.
- HTTP is used to carry the data in the form of MIME-like format.
- HTTP is similar to SMTP as the data is transferred between client and server. The HTTP differs from the SMTP in the way the messages are sent from the client to the server and from server to the client. SMTP messages are stored and forwarded while HTTP messages are delivered immediately.
Features of HTTP:
- Connectionless protocol: HTTP is a connectionless protocol. HTTP client initiates a request and waits for a response from the server. When the server receives the request, the server processes the request and sends back the response to the HTTP client after which the client disconnects the connection. The connection between client and server exist only during the current request and response time only.
- Media independent: HTTP protocol is a media independent as data can be sent as long as both the client and server know how to handle the data content. It is required for both the client and server to specify the content type in MIME-type header.
- Stateless: HTTP is a stateless protocol as both the client and server know each other only during the current request. Due to this nature of the protocol, both the client and server do not retain the information between various requests of the web pages.
HTTP Transactions
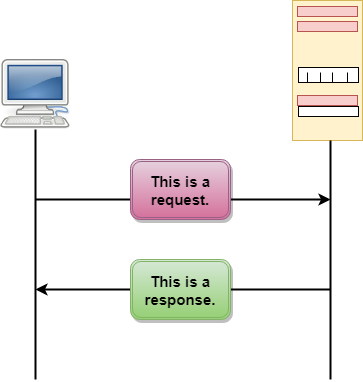
Fig 7 – HTTP Transaction
The above figure shows the HTTP transaction between client and server. The client initiates a transaction by sending a request message to the server. The server replies to the request message by sending a response message.
Messages
HTTP messages are of two types: request and response. Both the message types follow the same message format.
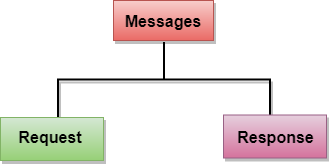
Fig 8 – Message
Request Message: The request message is sent by the client that consists of a request line, headers, and sometimes a body.
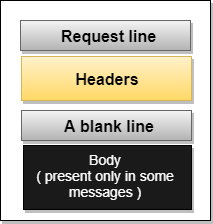
Fig 9 – Request Message
Response Message: The response message is sent by the server to the client that consists of a status line, headers, and sometimes a body.
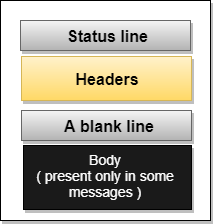
Fig 10 – Response Message
Uniform Resource Locator (URL)
- A client that wants to access the document in an internet needs an address and to facilitate the access of documents, the HTTP uses the concept of Uniform Resource Locator (URL).
- The Uniform Resource Locator (URL) is a standard way of specifying any kind of information on the internet.
- The URL defines four parts: method, host computer, port, and path.
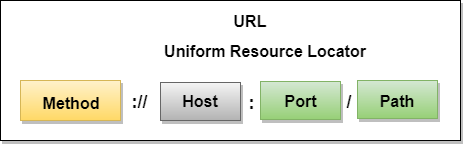
Fig 11 – URL
- Method: The method is the protocol used to retrieve the document from a server. For example, HTTP.
- Host: The host is the computer where the information is stored, and the computer is given an alias name. Web pages are mainly stored in the computers and the computers are given an alias name that begins with the characters "www". This field is not mandatory.
- Port: The URL can also contain the port number of the server, but it's an optional field. If the port number is included, then it must come between the host and path and it should be separated from the host by a colon.
- Path: Path is the pathname of the file where the information is stored. The path itself contain slashes that separate the directories from the subdirectories and files.
Wi-Fi is a popular wireless networking technology. Wi-Fi stands for “wireless fidelity”. Wi-Fi was invented by NCR Corporation/AT&T in the Netherlands in 1991. By using this technology, we can exchange information between two or more devices. Wi-Fi has been developed for mobile computing devices, such as laptops, but it is now extensively using for mobile applications and consumer electronics like televisions, DVD players, and digital cameras. There should be two possibilities in communicating with the Wi-Fi connection that may be through an access point to the client connection or client to client connection. Wi-Fi is one type of wireless technology. It is commonly called a wireless LAN (local area network). WiFi technology allows local area networks to operate without cable and wiring. It is making a popular choice for home and business networks. A computer’s wireless adaptor transfers the data into a radio signal and transfers the data into an antenna for users.
Principle:
Wi-Fi is a high-speed internet connection and network connection without the use of any cables or wires. The wireless network is operating three essential elements that are radio signals, antenna, and router. The radio waves are keys that make Wi-Fi networking possible. The computers and cell phones are ready with Wi-Fi cards. Wi-Fi compatibility has been using a new creation to constituent within the ground connected with community network.
The actual broadcast is connected in sequence in fact it is completed by way of stereo system surf as well as the worth of wires with the monitor to classification prone. Wi-Fi allows the person in order to get access to the web any place in the actually provided area. You can now generate a system within Resorts, library, schools, colleges, campus, personal institutes, as well as espresso stores as well as on the open public spot to help to make your company much more lucrative as well as interact with their own customer whenever.
Wi-Fi compatibility can make surf with stare to the company using their inspiring cable television much a smaller amount force down. The radio signals are transmitted from antennas and routers that signals are picked up by Wi-Fi receivers, such as computers and cell phones that are ready with Wi-Fi cards. Whenever the computer receives the signals within the range of 100-150 feet for the router it connects the device immediately.
The range of the Wi-Fi is depended upon the environment, indoor or outdoor ranges. The Wi-Fi cards will read the signals and create an internet connection between the user and the network. The speed of the device using Wi-Fi connection increases as the computer gets closer to the main source and the speed is decreased the computer gets further away.
Security
Security is an important element in Wi-Fi technology. Security is our personal decision but having a wireless connection we should pay attention to protect our private details. We can connect easily to unsecured wireless routers. The problem is anyone is connected to your wireless router using the data like download games, download apps and planning terrorist activities, shirring illegal music and movie files, etc. So it is necessary to provide security to the wireless technologies based devices.
References:
1. Computer Networks, 8th Edition, Andrew S. Tanenbaum, Pearson New International Edition.
2. Internetworking with TCP/IP, Volume 1, 6th Edition Douglas Comer, Prentice Hall of India.
3. TCP/IP Illustrated, Volume 1, W. Richard Stevens, Addison-Wesley, United States of America.