Unit - 1
Introduction to IoT
The Internet of Things (IoT) has not been around for very long. However, there have been visions of machines communicating with one another since the early 1800s. Machines have been providing direct communications since the telegraph (the first landline) was developed in the 1830s and 1840s. Described as “wireless telegraphy,” the first radio voice transmission took place on June 3, 1900, providing another necessary component for developing the Internet of Things. The development of computers began in the 1950s.
The Internet, itself a significant component of the IoT, started out as part of DARPA (Defense Advanced Research Projects Agency) in 1962, and evolved into ARPANET in 1969. In the 1980s, commercial service providers began supporting public use of ARPANET, allowing it to evolve into our modern Internet. Global Positioning Satellites (GPS) became a reality in early 1993, with the Department of Defense providing a stable, highly functional system of 24 satellites. This was quickly followed by privately owned, commercial satellites being placed in orbit. Satellites and landlines provide basic communications for much of the IoT.
About objects/things in the IoT
The Internet of Things (IoT) describes a vision in which everyday objects are connected to the Internet, be identified and communicate with other devices. These objects are typically referred to as "smart objects." The aim is to digitizing applications and processes to make them easier and more efficient. Smart Objects (also known as Intelligent Objects) are objects that are equipped with positioning and communication technologies and are integrated into a communication network, the so-called Internet of Things (IoT).
These intelligent objects can enter, store and process data and interact with other objects, systems or people. They can be embedded or fixed in other objects and capture data about position and sensors, as well as execute decision and control functions.
Overview and motivations
The internet of things (IoT) is a computing concept that describes a scenario where every day physical objects are connected to the internet and can identify themselves to other devices or processes, via an address. The IoT is significant because an object that can represent itself digitally becomes something greater than the object by itself. No longer does the object just relate to the process; it now connects to surrounding objects and database data, permitting “big data” analytics and insights. In particular, “things” might communicate autonomously with other things and other devices, such as sensors in manufacturing environments or an activity tracker with a smartphone. IoT has evolved from the convergence of wireless technologies, micro-electromechanical systems, microservices and the internet.
IoT Architecture
There is not such a unique or standard consensus on the Internet of Things (IoT) architecture which is universally defined. The IoT architecture differs from their functional area and their solutions. However, the IoT architecture technology mainly consists of four major components:
Components of IoT Architecture
Sensors/Devices
Gateways and Networks
Cloud/Management Service Layer
Application Layer
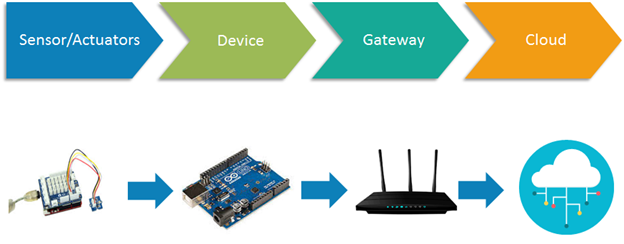
Fig 1: Source of IoT
Sources of IoT:
- Sensors/Actuators: Sensors or Actuators are the devices that are able to emit, accept and process data over the network. These sensors or actuators may be connected either through wired or wireless. This contains GPS, Electrochemical, Gyroscope, RFID, etc. Most of the sensors need connectivity through sensors gateways. The connection of sensors or actuators can be through a Local Area Network (LAN) or Personal Area Network.
- Gateways and Data Acquisition: As the large numbers of data are produced by these sensors and actuator need the high-speed Gateways and Networks to transfer the data. This network can be of type Local Area Network (LAN such as WiFi, Ethernet, etc.), Wide Area Network (WAN such as GSM, 5G, etc.).
- Edge IT: Edge in the IoT Architecture is the hardware and software gateways that analyze and pre-process the data before transferring it to the cloud. If the data read from the sensors and gateways are not changed from its previous reading value then it does not transfer over the cloud, this saves the data used.
- Data center/ Cloud: The Data Center or Cloud comes under the Management Services which process the information through analytics, management of device and security controls. Beside this security controls and device management the cloud transfers the data to the end user’s application such as Retail, Healthcare, Emergency, Environment, and Energy, etc.
Internet of Things (IoT): Vision, Definition
Vision:
A vision where things (wearable, watch, alarm clock, home devices, surrounding objects with) become smart and behave alive through sensing, computing and communicating systems
A vision where embedded devices interact with remote objects or persons through connectivity, for examples, using Internet or Near Field Communication or other technologies.
Definition:
The network of physical objects or "things" embedded with electronics, software, sensors, connected so as to enable achieving greater value and offer service by exchanging data with the manufacturer, operator and/or other connected devices each thing uniquely identifiable, things embedded with sensors and computing system, able to interoperate within the existing Internet infrastructure.
Internet of Things (IoT) extends the uses of Internet by providing the communication, and thus inter-network of the physical objects, devices, machines, vehicles; all referred as “things”.
Key Takeaways
- Internet of Things (IoT) extends the uses of Internet by providing the communication, and thus inter-network of the physical objects, devices, machines, vehicles; all referred as “things”.
2. Ease of designing with availability of sensors, actuators, controllers and IoT devices
3. Low in cost and hardware, and
4. Use preferably open-source software components and protocols
In the not-too-distant future, our daily lives will be increasingly populated by intelligent, linked items. They will exist in our homes, workplaces, and cities, as well as accompany us wherever we go in the form of wearables, smart clothes, and other things we can't even envision right now. The internet of things, or IoT, is the name given to this development.
Developing IoT solutions presents whole new design difficulties for designers who are used to designing SW services, screen-based interfaces, or physical goods. Multiple components make up IoT solutions: physical equipment such as sensors, actuators, and interactive devices, the network that connects these devices, the data collected from these devices and evaluated to create a meaningful experience, and, last but not least, the physical context in which the user interacts with the solution. From industrial product design to service and business design, you'll need to execute a variety of things.
All of these elements have an impact on the overall UX of the IoT system, and designing in this environment can be a daunting undertaking.
1. Focus on value
User research and service design are more important than ever in the IoT age. While early adopters are eager to try out new technology, many others are hesitant to use it and are wary about doing so because they are unfamiliar with it. In order for your IoT solution to be broadly adopted, you must delve deeply into consumers' needs to determine where an issue actually worth solving exists and what the solution's true end user value is. You should also be aware of any potential impediments to embracing new technology in general, and your solution in particular. You'll also require research to decide on your feature set. Features that are valuable and relevant to tech early adopters may be uninteresting to the majority of users, and vice versa, so you must carefully consider which features to include and in what order.
2. Take a holistic view
Multiple devices with varying capacities and both physical and digital touch points are common in IoT solutions. The solution could potentially be offered in collaboration with a variety of service providers. It is not enough to design one of the touch points correctly; instead, you must consider the entire system, the role of each device and service, and the conceptual model of how the user perceives and understands the system. The whole system needs to work seamlessly together in order to create a meaningful experience. The whole system needs to work seamlessly together in order to create a meaningful experience.
3. Put safety first
Because IoT solutions are used in a real-world setting, when something goes wrong, the implications can be severe. At the same time, customers of IoT solutions may be wary of new technologies, therefore one of your key design drivers should be to develop trust. Because confidence is earned slowly and easily betrayed, you must ensure that each engagement with the product/service develops rather than destroys it. What does this mean in practice? To begin with, it entails recognizing and attempting to prevent possible error situations relating to the context of use, HW, SW, and network, as well as user interactions.
Second, if the error situations persist, it necessitates properly alerting the user about them and assisting them in their recovery. Second, it involves making data security and privacy a priority in your design. It is critical for consumers to believe that their personal information is secure, that their homes, workplaces, and ordinary products cannot be hacked, and that their loved ones are not at risk. Third, quality assurance is crucial, and it should focus not just on testing the SW, but also on evaluating the entire system in a real-world setting.
4. Consider the context
At the intersection of the physical and digital worlds, IoT solutions exist. Real-world effects may be produced by commands supplied through digital interfaces, but unlike digital orders, real-world actions cannot always be undone. In the actual world, a lot of unexpected things might happen, yet the user should feel safe and in control at all times. Other kinds of requirements are imposed on the design by the setting. The purpose may be to minimize the user's distraction or, for example, to develop gadgets that can withstand changing weather conditions, depending on the physical setting.
IoT solutions in homes, offices, and public spaces are often multi-user systems, making them less personal than, say, screen-based solutions used in smartphones, which also considers the social context in which the solution is used and its design needs.
5. Build a strong brand
Because of the real-world context of IoT solutions, no matter how carefully you design things and strive to develop trust, something unexpected will occur at some point, and your solution will fail. In these kind of scenarios, having a strong brand that actually resonates with the end customers is critical.
They will be more forgiving of system errors and continue to use your solution if they feel linked to your brand. When creating your brand, keep in mind that trust should be a major component and one of the essential brand principles. This core value should be represented in the rest of the brand's elements, such as color, voice, imagery, and so on.
6. Prototype early and often
HW and SW typically have quite distinct lifespans, but because a successful IoT solution requires both HW and SW, the lifespans should be synchronized. At the same time, IoT solutions are difficult to upgrade because once a connected object is installed, it is difficult to replace it with a newer version, particularly if the user must pay for the upgrade, and the software within the connected object may be difficult to update for security and privacy reasons. Because of these considerations, and in order to avoid costly hardware iterations, it's critical to get the solution right from the start.
This means that prototyping and rapid iteration of both the HW and the entire solution are critical in the early stages of the project from a design standpoint. New and innovative approaches to prototyping and fake the answer are required.
7. Use data responsibly
IoT devices can easily generate a large amount of data. However, the goal is to discover the data points that are required to make the solution functional and valuable, not to collect as much data as possible. Nonetheless, because the amount of data may be enormous, the designer must be familiar with data science and how to make sense of it.
Data science offers numerous options to reduce user friction, such as saving time, energy, and attention, as well as lowering stress. It can be used to automate context-dependent judgments, interpret intent from partial or insufficient input, and filter significant signals from noise. Understanding what data is available and how it can be used to help the user is a key element in designing successful IoT services.
Needed capabilities
- Create an enterprise data strategy
Large volumes of data are already in the hands of today's businesses. However, much of it is compartmentalized and unusable, a problem that will only get worse as IoT and edge computing become more prevalent.
As a result, many businesses are putting together an enterprise data strategy and data practice. This discipline aids firms in determining what data they have and how it relates to business goals, identifying new data sources, ensuring overall data quality, and aligning all teams on a route ahead. Only correctly labeled, standardized, and deduplicated IoT data can be used in data models for artificial intelligence (AI) and machine learning.
Workplace data, which provides insights into how employees use spaces, technologies, and energy, is one type of data that firms have but rarely use. Companies spend a lot of money on buying or leasing real estate, furnishing spaces, and running structures. Understanding how spaces are used allows you to make more informed decisions about how to grow your organization, plan development, update infrastructure, and estimate workforce demands. Steelcase, a provider of office furniture, has taken advantage of this commercial potential. Steelcase has created technology to make greater use of IoT data in the workplace.
2.Balance structure and flexibility to exploit new opportunities
As businesses acquire experience with IoT pilots, they will come to a decision point: institutionalize IoT by making it a strategic program, or continue to experiment. The former entails considering the big picture of potential new services and revenue streams.
IoT can be used to improve existing business processes, but its actual worth is realized when teams take the time to figure out what's failing and why, fix the underlying issues, and align all associated processes and workflows to optimize new IoT value.
Steelcase made a long-term bet when it launched its Smart + Connected business line that its analytics capabilities would become a significant service offering that would open doors to new client relationships and strengthen existing ones. Steelcase converts what may be a one-time office furniture purchase into a chance to provide continuing value by serving as a consultant in helping organizations understand their spaces and arrange furniture and tools. Steelcase Workplace Advisor is also sold on a subscription basis, providing the organization with a steady stream of money.
3.Develop specialized talent
Companies will identify missing competencies required for success as they move forward with IoT. Cross-training existing talent is one option. Another approach is to hire new-skilled employees to fill the IoT bench. Many companies that are deploying IoT or plan to do so are having difficulty finding people with the necessary capabilities to move their initiatives ahead.
Staff who can blend business and technology visions and strategies, agile team leaders and practitioners, business process reengineering specialists, analytics pros, and cyber security experts, all of whom can work in an environment marked by constant change, uncertain outcomes, and a desire to create and optimize business value, are likely on the wish list for these companies.
Steelcase had to quickly evolve its IT capabilities as it started its IoT adventure. This most likely entailed hiring people with experience in IoT, analytics, mobile app development, and smart space design.
Furthermore, the company adopted new methods of working, embracing the agile methodology and scrum framework to increase business and IT cooperation, as well as utilizing its space use information to improve its own team workspaces. Agile sprint velocity increased by 40% as a result of the new agile culture, process, and workplace, providing a compelling case study to the company's customers.
4. Harden and evolve security
Companies must prepare for greater cyberattacks as they implement IoT programs. In fact, many people have most certainly previously encountered them.
The Internet of Things exacerbates enterprises' already-existing security issues. With more endpoints, hackers have a larger attack surface to deal with. The answer is to address security at a large scale.
Azure IoT Central combines enterprise-grade Azure managed services with Software as a Service (SaaS) to deliver a platform that allows businesses to connect, manage, and monitor their IoT assets, whether they have hundreds or millions of them. This implies that companies like Steelcase can design fully functional IoT solutions in a matter of hours, without having to worry about infrastructure or security.
5. Continually consider consumer expectations
Companies that use IoT devices and services are interacting with their customers in new and possibly intrusive ways. For example, IoT allows for comprehensive situational awareness, which may come as a surprise to customers and employees if they aren't given enough information. In view of shifting customer expectations surrounding privacy, the IoT team requires mechanisms for considering and revising data collection and usage practices.
Consumers are aware that they are handing over sensitive information, but they expect firms to secure it and use it in ways that benefit both parties. As firms move deeper into IoT, AI, and machine learning, many are creating ethical data usage policies to define how they utilize data. These policies vary, but they usually prioritize consumer privacy, clear governance, justice, shared benefit, and transparency.
In general, businesses follow a policy of least use, obtaining consumer consent to collect only the data they require and then asking for permission to collect more. Companies who fail to follow this policy risk losing business if they lose consumer trust as a result of privacy or security breaches. To preserve their focus on delivering value that consumers can see and enjoy, firms should perceive IoT as a shared journey with consumers.
The Internet of Things (IoT) provides the ability to interconnect computing devices, mechanical machines, objects, animals, or unique identifiers and people to transfer data across a network without the need for human-to-human or human-to-computer is a system of conversation. IoT applications bring a lot of value to our lives. The Internet of Things provides objects, computing devices, or unique identifiers and people's ability to transfer data across a network without the human-to-human or human-to-computer interaction.
Fig 2: Application
City Automation:
IoT-enabled smart city use cases span multiple areas: from contributing to a healthier environment and improving traffic to enhancing public safety and optimizing street lighting. Below, we provide an overview of the most popular use cases that are already implemented in smart cities across the globe.
Smart meters & billing
With a network of smart meters, municipalities can provide citizens with cost-effective connectivity to utility companies’ IT systems. Now, smart connected meters can send data directly to a public utility over a telecom network, providing it with reliable meter readings. Smart metering allows utility companies to bill accurately for the amount of water, energy, and gas consumed by each household.
Revealing consumption patterns
A network of smart meters enables utility companies to gain greater visibility and see how their customers consume energy and water. With a network of smart meters, utility companies can monitor demand in real-time and redirect resources as necessary or encourage consumers to use less energy or water at times of shortage.
Remote monitoring
IoT smart city solutions can also provide citizens with utility management services. These services allow citizens to use their smart meters to track and control their usage remotely. For instance, a householder can turn off their home central heating using a mobile phone. Additionally, if a problem (e.g., a water leakage) occurs, utility companies can notify householders and send specialists to fix it.
E- Health care:
The Internet of Things (IoT) devices can collect and share data directly with other devices through the cloud environment, providing a huge amount of information to be gathered, stored, and analyzed for data-analytics processes. The scenarios in which the IoT devices may be useful are amazing varying, from automotive to industrial automation or remote monitoring of the domestic environment. Furthermore, has been proved that healthcare applications represent an important field of interest for IoT devices, due to the capability of improving the access to care, reducing the cost of healthcare, and most importantly increasing the quality of life of the patients. In this paper, we analyze the state-of-art of IoT in a medical environment, illustrating an extended range of IoT-driven healthcare applications that, however, still need innovative and high technology-based solutions to be considered ready to market. In particular, problems regarding characteristics of response-time and precision will be examined. Furthermore, wearable and energy-saving properties will be investigated in this paper, and also the IT architectures able to ensure security and privacy during the all data-transmission process. Finally, considerations about data mining applications, such as risk prediction, classification, and clustering will be provided, that are considered fundamental issues to ensure the accuracy of the care processes.
Medical Information Distribution
One of the challenges of medical care is the distribution of accurate and current information to patients. Healthcare also struggles with the guidance given the complexity of the following guidance. IoT devices not only improve facilities and professional practice, but also health in the daily lives of individuals.
IoT devices give direct, 24/7 access to the patient in a less intrusive way than other options. They take healthcare out of facilities and into the home, office, or social space. They empower individuals in attending to their health and allow providers to deliver better and more granular care to patients. This results in fewer accidents from miscommunication, improved patient satisfaction, and better preventive care.
Emergency Care
The advanced automation and analytics of IoT allow more powerful emergency support services, which typically suffer from their limited resources and disconnect with the base facility. It provides a way to analyze an emergency more completely from miles away. It also gives more providers access to the patient before their arrival. IoT gives providers critical information for delivering essential care on arrival. It also raises the level of care available to a patient received by emergency professionals. This reduces the associated losses and improves emergency healthcare.
Research
Much of current medical research relies on resources lacking critical real-world information. It uses controlled environments, volunteers, and essentially leftovers for medical examination. IoT opens the door to a wealth of valuable information through real-time field data, analysis, and testing.
IoT can deliver relevant data superior to standard analytics through integrated instruments capable of performing viable research. It also integrates into actual practice to provide more key information. This aids in healthcare by providing more reliable and practical data, and better leads; which yields better solutions and discovery of previously unknown issues.
It also allows researchers to avoid risks by gathering data without manufactured scenarios and human testing.
Devices
Current devices are rapidly improving in precision, power, and availability; however, they still offer less of these qualities than an IoT system integrating the right system effectively. IoT unlocks the potential of existing technology and leads us toward new and better medical device solutions.
IoT closes gaps between the equipment and the way we deliver healthcare by creating a logical system rather than a collection of tools. It then reveals patterns and missing elements in healthcare such as obvious necessary improvements or huge flaws.
Automotive applications
At every layer of transportation, IoT provides improved communication, control, and data distribution. These applications include personal vehicles, commercial vehicles, trains, UAVs, and other equipment. It extends throughout the entire system of all transportation elements such as traffic control, parking, fuel consumption, and more.
Rails and Mass Transit
Current systems deliver sophisticated integration and performance, however, they employ older technology and approaches to MRT. The improvements brought by IoT deliver more complete control and monitoring. This results in better management of overall performance, maintenance issues, maintenance, and improvements.
Mass transit options beyond standard MRT suffer from a lack of the integration necessary to transform them from an option to a dedicated service. IoT provides an inexpensive and advanced way to optimize performance and bring qualities of MRT to other transportation options like buses. This improves services and service delivery in the areas of scheduling, optimizing transport times, reliability, managing equipment issues, and responding to customer needs.
Road
The primary concerns of traffic are managing congestion, reducing accidents, and parking. IoT allows us to better observe and analyze the flow of traffic through devices at all traffic observation points. It aids in parking by making storage flow transparent when current methods offer little if any data.
Accidents typically result from some factors, however, traffic management impacts their frequency. Construction sites, poor rerouting, and a lack of information about traffic status are all issues that lead to incidents. IoT provides solutions in the form of better information sharing with the public, and between various parties directly affecting road traffic.
Automobile
Many in the automotive industry envision a future for cars in which IoT technology makes cars “smart,” attractive options equal to MRT. IoT offers a few significant improvements to personal vehicles. Most benefits come from better control over related infrastructure and the inherent flaws in automobile transport; however, IoT does improve personal vehicles as personal spaces. IoT brings the same improvements and customization to a vehicle as those in the home.
Commercial Transportation
Transportation benefits extend to business and manufacturing by optimizing the transport arm of organizations. It reduces and eliminates problems related to poor fleet management through better analytics and control such as monitoring idling, fuel consumption, travel conditions, and travel time between points. This results in product transportation operating more like an aligned service and less like a collection of contracted services.
Home automation, smart cards
Consumers benefit personally and professionally from the optimization and data analysis of IoT. IoT technology behaves like a team of personal assistants, advisors, and security. It enhances the way we live, work, and play.
Home
IoT takes the place of a full staff −
Butler − IoT waits for you to return home, and ensures your home remains fully prepared. It monitors your supplies, family, and the state of your home. It takes action to resolve any issues that appear.
Chef − An IoT kitchen prepares meals or simply aids you in preparing them.
Nanny − IoT can somewhat act as a guardian by controlling access, providing supplies, and alerting the proper individuals in an emergency.
Gardner − The same IoT systems of a farm easily work for home landscaping.
Repairman − Smart systems perform key maintenance and repairs and also request them.
Security Guard − IoT watches over you 24/7. It can observe suspicious individuals miles away and recognize the potential of minor equipment problems to become disasters well before they do.
Work
A smart office or other workspace combines customization of the work environment with smart tools. IoT learns about you, your job, and the way you work to deliver an optimized environment. This results in practical accommodations like adjusting the room temperature, but also more advanced benefits like modifying your schedule and the tools you use to increase your output and reduce your work time. IoT acts as a manager and consultant capable of seeing what you cannot.
Play
IoT learns as much about you as it does professionally. This enables the technology to support leisure −
Culture and Night Life − IoT can analyze your real-world activities and response to guide you in finding more of the things and places you enjoy such as recommending restaurants and events based on your preferences and experiences.
Vacations − Planning and saving for vacations proves difficult for some, and many utilize agencies, which can be replaced by IoT.
Products and Services − IoT offers a better analysis of the products you like and need than current analytics based on its deeper access. It integrates with key information like your finances to recommend great solutions.
Communicating Data with H/W units
A communications device is any type of hardware capable of transmitting data, instructions, and information between a sending device and a receiving device. One type of communications device that connects a communications channel to a sending or receiving device such as a computer is a modem. Computers process data as digital signals. Data, instructions, and information travel along a communications channel in either analog or digital form depending on the communications channel. An analog signal consists of a continuous electrical wave. A digital signal consists of individual electrical pulses that represent bits grouped together into bytes. For communications channels that use digital signals (such as cable television lines), the modem transfers the digital signals between the computer and the communications channel. If a communications channel uses analog signals (such as some telephone lines), however, the modem first converts between analog and digital signals.
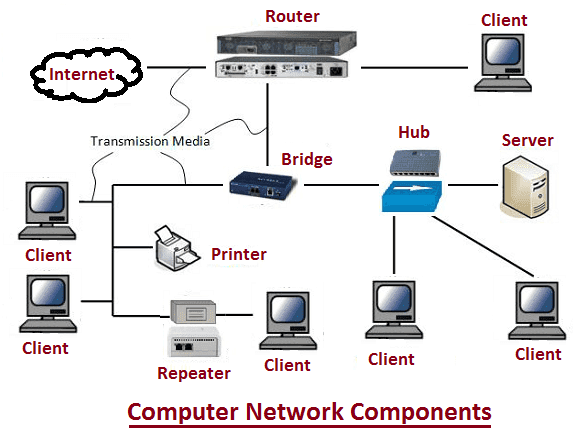
Fig 3: Computer network components
Dial-Up Modems
A modem usually is in the form of an adapter card that you insert in an expansion slot on a computer’s motherboard. One end of a standard telephone cord attaches to a port on the modem card and the other end plugs into a telephone outlet.
ISDN and DSL Modems
An ISDN modem sends digital data and information from a computer to an ISDN line and receives digital data and information from an ISDN line. A DSL modem sends digital data and information from a computer to a DSL line and receives digital data and information from a DSL line. ISDN and DSL modems usually are external devices, in which one end connects to the telephone line and the other end connects to a port on the system unit.
Cable Modems
A cable modem is a digital modem that sends and receives digital data over the cable television (CATV) network. With more than 110 million homes wired for cable television, cable modems provide a faster Internet access alternative to dial-up for the home user and have speeds similar to DSL. Cable modems currently can transmit data at speeds that are much faster than either a dial-up modem or ISDN.
Wireless Modems
Some mobile users have a wireless modem that uses the cell phone network to connect to the Internet wirelessly from a notebook computer, a smartphone, or another mobile device. Wireless modems, which have an external or built-in antenna, are available as PC Cards, Express Card modules, and flashcards.
Network Cards
A network card is an adapter card, PC Card, Express Card module, USB network adapter, or flashcard that enables a computer or device that does not have networking capability to access a network. The network card coordinates the transmission and receipt of data, instructions, and information to and from the computer or device containing the network card. Network cards are available in a variety of styles. A network card for a desktop computer is an adapter card that has a port to which a cable connects. A network card for mobile computers and devices is in the form of a PC Card, Express Card module, USB network adapter, or a flashcard. Network cards that provide wireless data transmission also are available. This type of card sometimes called a wireless network card, often has an antenna. A network card follows the guidelines of a particular network communications standard, such as Ethernet or token ring. An Ethernet card is the most common type of network card.
Wireless Access Points
A wireless access point is a central communications device that allows computers and devices to transfer data wirelessly among themselves or to transfer data wirelessly to a wired network. Wireless access points have high-quality antennas for optimal signals.
Routers
A router is a communications device that connects multiple computers or other routers together and transmits data to its correct destination on the network. A router can be used on any size of the network. On the largest scale, routers along the Internet backbone forward data packets to their destination using the fastest available path. For smaller business and home networks, a router allows multiple computers to share a single high-speed Internet connection such as a cable modem or DSL modem. These routers connect from 2 to 250 computers.
Mobiles, tablets, Designing of smart street lights in a smart city.
Today, smartphones or tablets are equipped with sensors of data from anything from location to the device orientation to light conditions. Altogether, these sensors produce a huge amount of data, both in an unstructured form (picture or videos) as well as structured, such as GPS or acceleration data. With the rise of wearables, smartphones increasingly have an additional role.
This new role can be considered as the "brain" of your Body Area Network (BAN), given the storage and communication capabilities of the smartphone. Last but not least with technologies such as Near Field Communications (NFC), smartphones can function not only as sensors but also as actuators. That is, trigger actions (such as payments) or control other things, including home, parking slots, cars, and many more.
Smart Devices
“A Smart Object is an object that can describe its possible interactions.”
Any device that not only has a state but also has certain data associated with that state and can also determine the nature of connectivity, duration of connectivity, and connectivity protocol are called smart objects. Some of the smart devices are smartphones, tablets, smartwatches, smart bands, and smart key chains. The term smart device can also refer to a ubiquitous computing device, a device that exhibits some properties of ubiquitous computing.
Characteristics of smart devices
A set of system hardware and software Information and Communication Technology (ICT) resources. This set is usually statically fixed at design time.
Dynamic component-oriented resource extensions and plug-ins (Plug and Play) of some hardware resources.
Remote external service access and execution.
Local, internal autonomous service execution.
Access to specific external environments: human interaction, physical world interaction, and distributed ICT / virtual computing interaction.
Ubiquitous computing properties.
Street lights:
Street lights are essential for proper navigation of traffic in the dark. They also make paths secure for humans to travel to during bad weather conditions such as a heavily cloudy day. And at the same time, connectivity with the help of digital devices such as a smartphone, tablet, or laptop is equally important in such situations. However, due to the space constraints of setting up a new telecommunication tower, one has to move to different places just to get a good connection, even if it requires straying away to a dimly lit area.
Smart Lighting Poles
Presenting a new smart lighting pole created by Signify (formerly known as Philips Lighting) that integrates a variety of IoT applications in it and features an uninterruptible 4G LTE wireless connectivity for the urban environment.
By replacing the standard street lights with these new poles (also known as Bright Sites smart poles), several wireless connectivity hubs can be created that provide telecommunication and advertising services for municipalities. While the smart pole can currently provide services for 4G and Wi-Fi, future versions could also include 5G services.
Other features
Sensors integrated into the smart pole can provide environment monitoring such as air quality, noise, and incident detection as well as collect data for overall liability in urban areas. Integrated cameras can observe road conditions to improve traffic flows while integrated screens can display emergency messaging as well as targeted advertising.
Provision for microphones that can record sounds such as breaking glass, car alarms, shouting, or even gunshots has also been made.
Key takeaway
IoT applications bring a lot of value in our lives. The Internet of Things provides objects, computing devices, or unique identifiers and people's ability to transfer data across a network without the human-to-human or human-to-computer interaction.
A set of system hardware and software Information and Communication Technology (ICT) resources. This set is usually statically fixed at design time.
IoT’s new role can be considered as the "brain" of your Body Area Network (BAN), given the storage and communication capabilities of the smart phone. Last but not least with technologies such as Near Field Communications (NFC), smart phones can function not only as sensors but also as actuators.
Sensors can be found all over the place. They can be found in our homes and businesses, as well as retail malls and hospitals. They're built into smartphones and play a key role in the Internet of Things (IoT). Sensors have existed for quite some time. Infrared sensors have been around since the late 1940s, while the first thermostat was launched in the late 1880s. The Internet of Things (IoT) and its industrial cousin, the Industrial Internet of Things (IIoT), are taking sensor usage to new heights.
Sensors, in general, are devices that detect and respond to changes in their surroundings. Light, temperature, motion, and pressure are all examples of possible inputs. Sensors produce useful data, which they can exchange with other connected devices and management systems if they are connected to a network.
Sensors are vital to the success of many modern organizations. They can alert you to possible issues before they turn into major issues, allowing firms to do preventative maintenance and avoid costly downtime.
A good sensor should have these three characteristics:
• It needs to be attentive to the phenomenon it's tracking.
• It shouldn't be affected by other bodily factors.
• During the measuring procedure, it should not change the phenomenon being measured.
We can use a variety of sensors to measure practically all of the physical properties around us. Thermometers, pressure sensors, light sensors, accelerometers, gyroscopes, motion sensors, gas sensors, and many other common sensors are widely used in everyday life. Several properties can be used to describe a sensor, the most essential of which is:
• Range - The sensor's range refers to the phenomenon's highest and minimum values.
• Sensitivity - Sensitivity is defined as the smallest change in the measured parameter that results in a noticeable change in the output signal.
• Resolution - The sensor's resolution is the smallest change in the phenomenon it can detect.
Sensor classification
Several criteria can be used to classify sensors:
• Passive or Active - Active sensors, on the other hand, require an external power source to monitor an environment, whereas passive sensors do not.
• Another classification is dependent on how the property was detected and measured (mechanical, chemical, etc.).
• Analog or Digital - Digital sensors produce a discrete signal, whereas analog sensors produce an analog, or continuous, signal.
Types of sensors
There are many different types of IoT sensors, as well as numerous applications and use cases. Here are ten of the most common types of IoT sensors, as well as some of their applications.
- Temperature sensors
Temperature sensors detect temperature changes and translate them to data by measuring the quantity of heat energy present in a source. Manufacturing machinery frequently necessitates specific environmental and device temperatures. Similarly, soil temperature is an important determinant in crop growth in agriculture.
2. Humidity sensors
These sensors determine how much water vapor is present in the environment of air or other gases. Humidity sensors are often found in both industrial and domestic heating, venting, and air conditioning systems. They can also be found in a variety of different places, such as hospitals and meteorology stations, where they record and forecast weather.
3. Pressure sensors
Changes in gases and liquids are detected by a pressure sensor. The sensor monitors changes in pressure and conveys them to connected systems when they occur. Leak testing, which might occur as a result of degradation, is a common application case. Pressure sensors are also important in the manufacture of water systems since they can easily detect pressure variations or dips.
4. Proximity sensors
Proximity sensors are used to detect objects that are close to the sensor without having to touch them. Electromagnetic fields or beams of radiation, such as infrared, are frequently emitted by these sensors. Proximity sensors have a variety of applications. A proximity sensor in retail can detect motion between a customer and a product that piques his or her attention. Any discounts or special offers on products near the sensor might be notified to the user. Mall parking lots, stadium parking lots, and airport parking lots all use proximity sensors to signal parking availability. They can also be employed in production lines in the chemical, food, and a variety of other industries.
5. Level sensors
The level of substances such as liquids, powders, and granular materials is detected using level sensors. Level sensors are used in a variety of industries, including oil production, water treatment, and beverage and food manufacturing. Level sensors can measure the amount of rubbish in a garbage can or dumpster, which is a frequent use case for waste management systems.
6. Gyroscope sensors
Gyroscope sensors measure the angular rate or velocity, which is commonly defined as the speed and rotation around an axis. Automobiles, such as automobile navigation and electronic stability control (anti-skid) systems, are examples of use cases. Motion sensing for video games and camera shake detection systems are two other applications.
7. Gas sensors
These sensors track and detect changes in air quality, such as the presence of toxic, flammable, or dangerous gases. Mining, oil and gas, chemical research, and manufacturing are all industries that use gas sensors. Carbon dioxide detectors, which are found in many homes, are a common consumer use case.
8. Infrared sensors
By producing or detecting infrared radiation, these sensors detect features in their surroundings. They can also detect the heat that objects emit. Infrared sensors are employed in a range of IoT projects, including healthcare, because they make blood flow and blood pressure monitoring easier. Infrared sensors are used by televisions to decipher the signals supplied by a remote control. Art historians utilizing infrared sensors to observe hidden layers in paintings to assist establish whether a work of art is real or fake, or has been altered by a restoration technique, is another intriguing application.
9. Optical sensors
Optical sensors are devices that transform light beams into electrical impulses. Optical sensors have a wide range of applications and use cases. Vehicles in the automotive industry utilize optical sensors to detect signs, obstructions, and other objects that a driver might see while driving or parking. Optical sensors are crucial in the development of self-driving cars. Optical sensors are widely used in mobile phones.
Key takeaway
Sensors can be found all over the place. They can be found in our homes and businesses, as well as retail malls and hospitals.
Sensors are vital to the success of many modern organizations.
Sensors, in general, are devices that detect and respond to changes in their surroundings.
A physical object (“thing”) + controller (“brain”) + sensors + actuators + networks make up an IoT device (Internet). A machine component or system that moves or regulates a mechanism or system is known as an actuator. The device's sensors detect the surroundings, and control signals are sent to the actuators based on the activities required.
An actuator is something like a servo motor. They can move to a defined angular or linear location and are either linear or rotatory actuators. For IoT applications, we can use servo motors and rotate them to 90 degrees, 180 degrees, and other angles as needed.
The controller instructs the actuator to conduct the task depending on the sensor data, as shown in the diagram below.
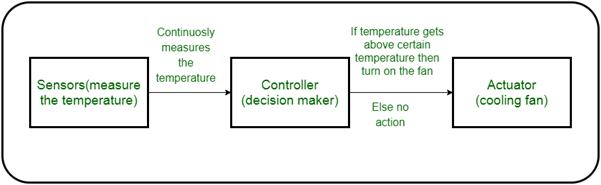
Fig 4: Use of actuations
Through the actuator, the control system affects the environment. It necessitates an energy supply as well as a control signal. It turns the source of energy into a mechanical operation when it gets a control signal. On this premise, on the form of energy it uses, it has different types given below.
Types of Actuators
- Hydraulic actuator
A hydraulic actuator is a mechanical device that employs hydraulic power to complete a task. A cylinder or a fluid motor drives them. According to the needs of the IoT device, mechanical motion is translated to rotary, linear, or oscillatory motion. Hydraulic actuators are used in construction equipment because they can create a considerable amount of force.
Advantages
• Hydraulic actuators have the ability to generate significant amounts of force at a high rate.
• Used in welding, clamping, and other applications.
• In car transport carriers, it's used to lower or raise the vehicles.
Disadvantages
• Leaks in hydraulic fluid can reduce performance and complicate cleanup.
• Noise reduction equipment, heat exchangers, and high-maintenance systems are all required.
• It is expensive.
2. Pneumatic Actuators
A pneumatic actuator converts energy created by vacuum or high-pressure compressed air into linear or rotary motion. For example, sensors that act like human fingers and are powered by compressed air are used in robotics.
Advantages
• They are a low-cost solution that is employed in extreme temperatures where employing air rather than chemicals is a safer option.
• They require little maintenance, are long-lasting, and have a lengthy service life.
• It is quite quick to initiate and stop the action.
Disadvantages
• It can become less efficient if there is a loss of pressure.
• The air compressor should be turned on all the time.
• It is possible for air to be polluted, and it must be maintained.
3. Electrical actuators
An electric actuator works by converting electrical energy into mechanical torque and is usually powered by a motor. A solenoid-based electric bell is an example of an electric actuator.
Advantages
• It can automate industrial valves, which makes it useful in a variety of sectors.
• It makes less noise and is completely safe to use because there are no fluid leaks.
• It has the ability to be reprogrammed and delivers the highest level of control and precision positioning.
Disadvantages
• It's not cheap.
• It is highly dependent on the surrounding environment.
Key takeaway
An actuator is something like a servo motor. They can move to a defined angular or linear location and are either linear or rotatory actuators.
A computer network is made up of two or more computers that are linked together by cables (wired) or WiFi (wireless) in order to transmit, exchange, or share data and resources. Hardware (such as routers, switches, access points, and cables) and software are used to create a computer network (e.g., operating systems or business applications).
A computer network's location is frequently defined by its geographical location. A LAN (local area network), for example, connects computers within a certain physical place, such as an office building, whereas a WAN (wide area network) connects computers across continents. The internet, which connects billions of computers around the world, is the most well-known example of a WAN.
Networking types and networking
Networks can be wired or wireless, with the majority of networks combining the two.
Wired vs Wireless Networks
Early networks (before to 2008) were mostly wired.
Most networks nowadays, however, will use a combination of wired and wireless networks.
Ethernet is the data link protocol used in wired networks. This is unlikely to alter with the Internet of Things, as most IoT devices will be wireless.
Wired advantages
The following are the benefits and drawbacks of wired networks:
• Almost all laptops/PCs and netbooks, even ones as old as eight years, include Ethernet connectors.
• Wireless networks are slower than wired networks. Data rates were boosted from 10 megabits per second to 1 gigabit per second on a regular basis. The majority of residential networks use speeds of 10 to 100 Mbps.
• Wireless is less secure.
Disadvantages
• Need to use cable, which is unattractive, difficult to install, and costly.
• It is difficult to utilize between buildings (planning etc.).
• Many of these drawbacks are overcome by a new technique that uses mains cable. On home and small office networks, powerline networking is common.
• Mobile phones and tablets are not supported.
Wireless network
Wi-Fi is the data communication protocol used by wireless networks. Other wireless options for the IoT, on the other hand, are being developed (Internet of things). Wireless networking technologies for IoT can be found here.
The following are the benefits and drawbacks of wireless networks:
Advantages
• In general, they are easier to set up.
• It operates on both private and public networks.
• There are no cables necessary.
• Mobile phones and tablets are supported.
Disadvantages
• Generally, Networks that are wireless are slower than those that are wired.
• Range is a limitation.
• Eavesdropping is possible.
• Depending on the setup, it may not be as secure.
Network topology
There are a variety of methods for connecting network nodes. This isn't usually a consideration in small networks, but it becomes increasingly significant as networks grow larger.
There are a variety of methods for connecting network nodes.
Wi-Fi, Bluetooth, and other common connection technologies are intended to work with a specific network layout.
Understanding these topologies is crucial for constructing networks and selecting connection protocols.
Common are:
• Bus
• Ring
• Mesh
• Star
• Hybrid
Each of these topologies has benefits and drawbacks. This page on network topologies gives a fair overview of each topology, as well as its benefits and drawbacks.
Early Ethernet networks, modern Ethernet networks, and Wi-Fi networks all used a bus structure. Use a hybrid (star bus) structure.
Wi-Fi and Bluetooth, on the other hand, are being improved to accommodate mesh networking.
Network size
The size of a network varies greatly. The following are some terms that are frequently used:
PAN - PAN (Personal Area Network) is a network that connects local devices, such as a computer to a printer.
LAN - The LAN (Local Area Network) connects devices in a single or multiple offices.
MAN - MAN (Metropolitan Area Network) is a network that connects devices across numerous buildings, such as a campus.
WAN - WAN stands for wide area network, and it connects devices across a country or countries.
Key takeaway
A computer network is made up of two or more computers that are linked together by cables (wired) or WiFi (wireless) in order to transmit, exchange, or share data and resources.
A computer network's location is frequently defined by its geographical location.
Machine-to-machine (M2M)
Machine-to-machine, or M2M, is a broad label that can be used to describe any technology that enables networked devices to exchange information and perform actions without the manual assistance of humans. Artificial intelligence (AI) and machine learning (ML) facilitate communication between systems, allowing them to make their own autonomous choices.
M2M technology was first adopted in manufacturing and industrial settings, where other technologies, such as SCADA and remote monitoring, helped remotely manage and control data from equipment. M2M has since found applications in other sectors, such as healthcare, business, and insurance. M2M is also the foundation for the internet of things (IoT).
M2M applications and examples:
Machine-to-machine communication is often used for remote monitoring. In product restocking, for example, a vending machine can message the distributor's network, or machine, when a particular item is running low to send a refill. An enabler of asset tracking and monitoring, M2M is vital in warehouse management systems (WMS) and supply chain management (SCM).
Utility companies often rely on M2M devices and applications to not only harvest energy, such as oil and gas but also to bill customers -- through the use of smart meters -- and to detect worksite factors, such as pressure, temperature, and equipment status.
M2M apps
In telemedicine, M2M devices can enable the real-time monitoring of patients' vital statistics, dispensing medicine when required, or tracking healthcare assets.
IoT and M2M:
The combination of the IoT, AI, and ML is transforming and improving mobile payment processes and creating new opportunities for different purchasing behaviors. Digital wallets, such as Google Wallet and Apple Pay, will most likely contribute to the widespread adoption of M2M financial activities.
Smart home systems have also incorporated M2M technology. The use of M2M in this embedded system enables home appliances and other technologies to have real-time control of operations as well as the ability to remotely communicate.
M2M is also an important aspect of remote-control software, robotics, traffic control, security, logistics and fleet management, and automotive.
Key features of M2M technology include:
Low power consumption, to improve the system's ability to effectively service M2M applications.
A network operator that provides packet-switched service
Monitoring abilities that provide the functionality to detect events.
Time tolerance, meaning data transfers can be delayed.
Time control, meaning data can only be sent or received at specific predetermined periods.
Location-specific triggers that alert or wake up devices when they enter particular areas.
The ability to continually send and receive small amounts of data.
Working of M2M Communication:
The main purpose of machine-to-machine technology is to tap into sensor data and transmit it to a network. Unlike SCADA or other remote monitoring tools, M2M systems often use public networks and access methods -- for example, cellular or Ethernet -- to make it more cost-effective.
The main components of an M2M system include sensors, RFID, a Wi-Fi or cellular communications link, and autonomic computing software programmed to help a network device interpret data and make decisions. These M2M applications translate the data, which can trigger preprogrammed, automated actions.
One of the most well-known types of machine-to-machine communication is telemetry, which has been used since the early part of the last century to transmit operational data. Pioneers in telemetric first used telephone lines, and later, radio waves, to transmit performance measurements gathered from monitoring instruments in remote locations.
The Internet and improved standards for wireless technology have expanded the role of telemetry from pure science, engineering, and manufacturing to everyday use in products such as heating units, electric meters, and internet-connected devices, such as appliances.
Beyond being able to remotely monitor equipment and systems, the top benefits of M2M include:
Reduced costs by minimizing equipment maintenance and downtime
Boosted revenue by revealing new business opportunities for servicing products in the field
Improved customer service by proactively monitoring and servicing equipment before it fails or only when it is needed.
M2M requirements:
According to the European Telecommunications Standards Institute (ETSI), requirements of an M2M system include:
Scalability - The M2M system should be able to continue to function efficiently as more connected objects are added.
Anonymity - The M2M system must be able to hide the identity of an M2M device when requested, subject to regulatory requirements.
Logging - M2M systems must support the recording of important events, such as failed installation attempts, service not operating, or the occurrence of faulty information. The logs should be available by request.
M2M application communication principles
M2M systems should enable communication between M2M applications in the network and the M2M device or gateway using communication techniques, such as short message service (SMS) and IP Connected devices should also be able to communicate with each other in a peer-to-peer (P2P) manner.
Delivery methods - The M2M system should support unicast, anycast, multicast, and broadcast communication modes, with the broadcast being replaced by multicast or anycast whenever possible to minimize the load on the communication network.
Message transmission scheduling - M2M systems must be able to control network access and messaging schedules and should be conscious of M2M applications' scheduling delay tolerance.
Message communication path selection - Optimization of the message communication paths within an M2M system must be possible and based on policies like transmission failures, delays when other paths exist, and network costs.
M2M standards
Machine-to-machine technology does not have a standardized device platform, and many M2M systems are built to be task- or device-specific. Several key M2M standards, many of which are also used in IoT settings, have emerged over the years, including:
OMA-DM (Open Mobile Alliance Device Management), a device management protocol
OMA LightweightM2M, a device management protocol
MQTT, a messaging protocol
TR-069 (Technical Report 069), an application layer protocol
HyperCat, a data discovery protocol
OneM2M, a communications protocol
Google Thread, a wireless mesh protocol
AllJoyn, an open-source software framework
IoT/M2M systems layers:
Layer 1: M2M Application Domain
• Integration, Collaboration, and M2M Application Services
• Application (Reporting, Analysis, control)
Layer 2: Network Domain
• M2M server, device identity, device and device-network management, Data Analysis, Abstraction, Accumulation, and Management
• Uni-cast and multicast message delivery
• Core functionalities for monitoring Connectivity (Communication and Processing Units)
Layer 3: M2M device communication domain
• M2M Devices Domain Communication
• Gateway
• Physical devices and Controllers (the things in IoT) [Sensors, machines, devices, Intelligent Edge nodes of Different Types
Key takeaway
Machine-to-machine, or M2M, is a broad label that can be used to describe any technology that enables networked devices to exchange information and perform actions without the manual assistance of humans.
M2M technology was first adopted in manufacturing and industrial settings, where other technologies, such as SCADA and remote monitoring, helped remotely manage and control data from equipment.
The main components of an M2M system include sensors, RFID, a Wi-Fi or cellular communications link, and autonomic computing software programmed to help a network device interpret data and make decisions.
Businesses are faced with the issue of integrating a plethora of devices and protocols, many of which have different power and connectivity requirements, as the Internet of Things (IoT) grows. It's possible that legacy technology will be included in this mix.
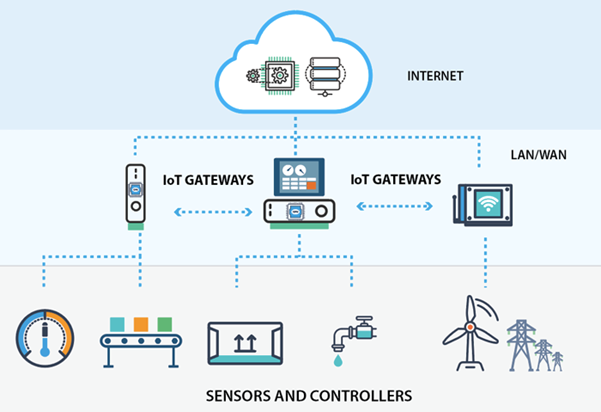
Fig 5: Device and gateway
IoT Gateways are quickly gaining traction as a critical component in establishing a stable IoT infrastructure and offering computational capacity in edge computing applications. Instead than depending on a single server for the bulk of the work, edge computing spreads the strain on a system by executing data processing at the data source, or "edge," rather than on a central server. This is where an IoT Gateway, such as the OAS Platform, comes in handy.
An IoT Gateway is a system for facilitating IoT communication, which is typically device-to-device or device-to-cloud. Typically, a gateway is a hardware device that houses application software that performs critical functions. The gateway, at its most basic level, permits the connections between various data sources and destinations.
Comparing an IoT Gateway to your home or business network router or gateway is a simple way to visualize it. This type of gateway allows you to communicate with your devices while still maintaining security and providing an admin interface where you can perform simple tasks. This is what an IoT Gateway does, plus much more.
IoT Gateways have evolved to fulfill a variety of functions, ranging from simple data filtering to visualization and advanced analytics. These intelligent devices are assisting in the current wave of IoT growth.
IoT Gateway feature set
Any of the following functions can be performed by a versatile IoT Gateway:
• Facilitating communication with legacy or non-internet connected devices
• Data caching, buffering and streaming
• Data pre-processing, cleansing, filtering and optimization
• Some data aggregation
• Device to Device communications/M2M
• Networking features and hosting live data
• Data visualization and basic data analytics via IoT Gateway applications
• Short term data historian features
• Security – manage user access and network security features
• Device configuration management
• System diagnostics
Data management is the process of reducing a large amount of data to the most relevant information. Various devices and applications send vast amounts of data in a variety of formats. Managing all of this IoT data necessitates the creation and implementation of architectures, rules, practices, and procedures capable of meeting the full data lifecycle requirements.
Smart devices are in charge of automating processes so that we can save time. Intelligent things can gather, transmit, and analyze data, but aggregating data and drawing inferences, trends, and patterns will require a tool.
Embedded system and device developers and manufacturers must create systems that meet the demands of data management. They must create a data management framework that is interoperable with all software and hardware involved in data collection, administration, and distribution. To reduce the end-time-to-market, product's the design must be efficient.
Analytical purposes are carried out using data from IoT devices. Dark data is information that corporations collect and retain but does not use for analytical purposes, therefore it remains largely stable. Customer demographics, purchase histories, and satisfaction levels, as well as generic product data, are all included.
Requirement for data management
Let's look at the most important data management requirements.
Scalability
Given the vast volumes of data generated by the Internet of Things, businesses must be able to scale up data volumes quickly and seamlessly. Current infrastructures must be able to scale up and down easily, and on a global scale. Dealing with challenges like shrinking storage size and costs should be a thing of the past—the pace of innovation and the speed with which IoT data is created make circumstances where storage and expenses are a worry difficult to afford. Rather, the data lifecycle must be reimagined in light of technological limitations.
Organizations should consider whether their current network and infrastructure can handle massive data volumes in the long run. They should also consider which storage solution is best for them: cloud, data center, data stored at the edge, or a hybrid model. Organizations must also define the levels of access to the data, as well as the data's retention obligations and legal implications. Existing infrastructures must be flexible enough to accommodate data processing activities in the next years, which requires foresight.
Data gravity
Value is created by volume. Data gravity develops when the volume of IoT data expands. As data volumes increase, other applications or services can extract value from it. As a result, these apps lead to the creation of even greater data volumes.
Massive amounts of data lead to more insight. As a result, the more data there is, the more value it has in terms of actionable intelligence. This is why businesses must be able to maintain robust infrastructures capable of safely harvesting, managing, and extracting insights from data.
Integration
The concept of interconnectedness pervades and characterizes everything that has to do with IoT. Wired and wireless devices, processors and storage, services, platforms, and apps are all available to help you turn your connection into value. To put it another way, the value of IoT is derived from its high connection, which implies communication and shareability on multiple levels.
As a result, every IoT data management system must integrate data sources at the edge and services. This includes real-time processing of operational data, secure integration of components and connections within an IoT environment, and security safeguards that enable enterprises to connect, harvest, share, and manage data across the whole IoT network.
A worldwide IoT platform with an integrated cloud data science studio for IoT analytics can effectively address the concerns of scalability, data gravity, and integration. This will allow you to connect, manage, grow, and deploy within an IoT infrastructure environment that is already in place.
Data management challenges
As the number of IoT devices grows, so will the issues of real-time processing and analysis in order to save storage time. To provide ample room for new information, metadata such as user IDs and passwords must be optimized.
Real-time data is used in functions including adaptive maintenance, predictive repair, security monitoring, and process optimization. Because integration between different sensors must be proved and compatibilities must be confirmed, choosing the proper tools is difficult. Devices must still obtain insights, make decisions, and prepare for data delivery even when there is no connection.
Interoperability, scalability, security, and standards supplied by software technologies to construct IoT devices are all significant reasons behind an IoT device data management platform. It's critical to keep data safe from unauthorized access and alteration. National data security norms and regulations must be followed by businesses.
Data from IoT devices must also be reviewed for quality. Having a large number of diverse devices linked directly to cloud services creates a large attack surface, which can be reduced by routing data through a secure gateway device.
Why IoT data management
Needs for data management
Product development
IoT data management can help you recognize and use patterns, which can then be used in the decision-making process to improve product design and development. Businesses can discover faults, monitor performance, and get quick access to measurements thanks to data management solutions. All of these provide information about how products are used, which may be used to identify areas that require improvement and to improve existing product versions. As a result of the insights pouring into product development, the user experience improves.
Facilitate resource and system efficiency
Streamlining and efficacy are the goals of data management. Data management allows you to have a better understanding of how customers interact with your products in a consumer IoT context. You will be better equipped to make the proper judgments as a result of these insights. You can assess favored features, keep track of engagement histories, and prevent deterioration by watching how users interact with your service.
Data management is useful in an industrial IoT scenario because it allows you to keep track of a large number of different devices. These devices may begin to depart from established behavior patterns when working as part of a system. Data management approaches encompass not just the collection of data from individual devices, but also the transmission, storage, and organization of (sometimes vast volumes of) IoT data.
Predict wear and tear of assets
Wear-and-tear projections for your linked infrastructure and assets are also covered by IoT data management. Finally, IoT data management aids in the analysis of equipment life cycles and the creation of maintenance schedules. You can utilize the data to see if devices and/or people are acting in unusual ways and create predictions based on that information. Using insights from both user and device behavior to conduct predictive analytics and discover places where your product needs to be rethought will help you conduct predictive analytics and identify areas where your product needs to be rethought.
When dealing with technology advancements, all company procedures must be future-proof and adaptable. The Internet of Things is already being used by many enterprises (IoT). Business processes, as well as the way they are handled, will have to adapt as technology becomes more and more embedded into our lives.
Industries all across the world are learning and experimenting with the Internet of Things. They can make better use of IoT solutions if they understand the technology and the business processes that surround it. Businesses must understand how to leverage the Internet of Things to collect sensor data intelligently from various users and process it in a cloud architecture.
Businesses must view the Internet of Things as a disruptive technology. In many businesses, this disruption is occurring at various levels. There is no turning back to old, non-smart technologies at the rate that businesses like Google, Samsung, NXP, ARM, Intel, and Apple are investing billions of dollars to create breakthrough IoT applications.
In India, only a small percentage of individuals still use Nokia feature phones, while the majority of people have switched to smartphones. Nokia paid a high price for failing to notice smartphone technologies: it lost consumers and, as a result, revenue. This shows that businesses and governments cannot afford to ignore the Internet of Things. Companies all around the world are looking for new technology to boost productivity, employee morale, and profits. In this field, the Internet of Things (IoT) is gaining traction.
Companies must learn how to identify IoT processes in order to optimize their business operations. A business process is a set of events, activities, and choices that all happen at the same time. It involves a variety of aspects and resources that, when combined, result in a valuable output for both the organization and the consumer.
Everything-as-a- The term "service" refers to the services and apps that users can request on the Internet.
The Everything-as-a-Service definition may appear ambiguous at first glance, yet it is not difficult to comprehend. It all began with the cloud computing terminology SaaS (Software-as-a-Service), PaaS (Platform-as-a-Service), and IaaS (Infrastructure-as-a-Service), which imply that ready-made software, a platform for its creation, or a comprehensive computer infrastructure can all be delivered over the internet. Other services gradually emerged, and currently the term as-a-Service is connected with a variety of digital components, such as data, security, and communication.
Example
Now that we've gone over the definition of XaaS, let's look at some of the most popular -aaS cases (aside from SaaS, PaaS, and IaaS).
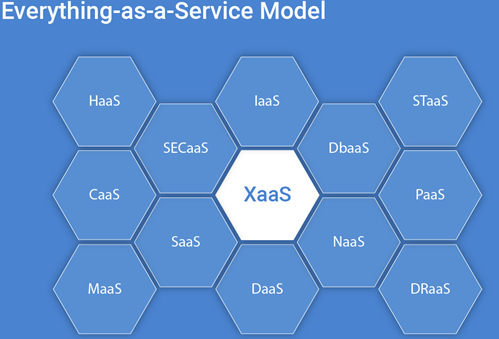
Fig 6: Xaas
Hardware-as-a-Service (HaaS)
MSPs (managed service providers) own certain hardware and can install it on customers' sites whenever they want. The hardware is used by customers in accordance with service level agreements. When computing resources are located at MSP's location and supplied to consumers as virtual equivalents of actual hardware, this pay-as-you-go approach is akin to leasing and can be likened to IaaS.
Communication-as-a-Service (CaaS)
This approach incorporates various communication options hosted in the vendor's cloud, such as VoIP (voice over IP or Internet telephony), IM (instant messaging), and video conference software. A corporation can deploy communication tools that best suit their present needs for a limited time and just pay for the time they use them.
This method is cost-effective and saves money on short-term communication needs.
Desktop-as-a-Service (DaaS)
Desktops are supplied as virtual services, complete with all necessary applications. As a result, a client can operate on a home computer while also tapping into the computing capacity of third-party servers (which can be much more powerful than those of a PC).
A DaaS provider is usually in charge of storing, safeguarding, and backing up user data, as well as providing updates for all supported desktop apps.
Security-as-a-Service (SECaaS)
Outsourced security management follows this concept. A security service provider integrates their services into your company's infrastructure and, in most cases, distributes them over the Internet. Anti-virus software, encryption, authentication, intrusion detection systems, and other services may be provided.
Healthcare-as-a-Service (HaaS)
The healthcare business is evolving into Healthcare-as-a-Service, thanks to electronic medical records (EMR) and hospital information systems (HIS). Medical care is becoming more data-driven and centered on the patient. The following services are now available thanks to the Internet of Things, wearables, and other new technologies:
• Online consultations with doctors
• Health monitoring 24/7
• Medicine delivery at your doorstep
• Lab samples collection even at home and delivery of results as soon as they are ready
• Access to your medical records 24/7
Transportation-as-a-Service (TaaS)
Mobility and flexibility of traveling over various distances are important trends in modern civilization. As a result of the proliferation of transportation-related apps, a portion of the business is shifting to a -aaS model. The following are some of the most vivid examples:
Carsharing - You can rent a car from any location using a special app and drive wherever you need to go, paying for the time you use the car or the distance you travel.
Uber taxi services - You hire a cab through an app that estimates the cost of the journey ahead of time). In the near future, Uber plans to test flying taxis and self-driving planes.
Benefits of XaaS
Due to a variety of benefits, they provide both for enterprises and end-users, the market for cloud computing and Internet-based services is rapidly growing. The following are the most significant advantages:
Scalability - (With outsourcing, a company has access to unlimited computer capacity, storage space, RAM, and other resources; it can scale its processes up and down fast and seamlessly based on demand without having to worry about new installations or downtimes.)
Cost and time effectiveness - (A corporation does not need to buy its own equipment and hence does not need to deploy it, saving time and money; a pay-as-you-go approach is also advantageous)
Focus on core competencies - (Employees can focus on their direct jobs and achieve higher performance because they don't have to set up apps and programs or go through training.)
The high quality of services - (Because specialists manage and maintain your infrastructure and systems, they can supply the most recent updates as well as all upcoming technologies, ensuring that your services are of the highest quality.)
Better customer services - (The above-mentioned benefits promote consumer happiness and loyalty.)
Key takeaway
The Everything-as-a-Service definition may appear ambiguous at first glance, yet it is not difficult to comprehend. It all began with the cloud computing terminology SaaS (Software-as-a-Service), PaaS (Platform-as-a-Service), and IaaS (Infrastructure-as-a-Service), which imply that ready-made software, a platform for its creation, or a comprehensive computer infrastructure can all be delivered over the internet.
The Internet of Things (IoT) generates a large amount of data, which is referred to as big data. For businesses, managing the flow and storage of this data is a difficult task. Cloud computing, with its various models and implementation platforms, assists businesses in managing and analyzing data, hence improving the overall efficiency and effectiveness of IoT systems. DLM, AEP, and Digital Twins are just a few of the solutions that cloud platforms like Amazon Web Services (AWS) and Microsoft Azure can help with.
Cloud computing enables businesses to store and manage data on cloud platforms, allowing for scalability in application and software as a service delivery. Cloud computing also allows data to be transferred and stored over the internet or via a direct link, allowing for continuous data flow between devices, apps, and the cloud.
The Internet of Things (sensors, machines, and devices) generate a massive quantity of data per second, as we all know. Cloud computing aids in the storing and analysis of this data, allowing businesses to get the most out of their IoT infrastructure. The Internet of Things (IoT) solution should link and allow communication between things, people, and processes, and cloud computing plays a key part in this collaboration in order to achieve high visibility.
The Internet of Things isn't simply about system connectivity, data collection, storage, and analytics. It aids in the modernization of operations by linking legacy and smart devices, as well as machines to the internet, and by removing barriers between IT and OT teams through a single view of systems and data. In IoT deployments, cloud computing eliminates the need to deploy large hardware, configure, and manage networks and infrastructure. Cloud computing also allows businesses to scale up or down their infrastructure based on their demands without having to invest in new gear or infrastructure.
This not only helps to speed up the development process, but it can also save money. Because businesses only pay for the resources they use, they won't have to spend money on purchasing and provisioning servers and other infrastructure.
Benefits
In the IoT ecosystem, there are numerous cloud services and platforms that perform distinct functions. To do complicated analytics, some platforms include built-in features such as machine learning, business intelligence tools, and SQL query engines. Let's look at how various cloud platforms and services might help an IoT ecosystem.
Cloud Platform for Device Lifecycle Management:
Cloud services (SaaS) enable businesses to create apps and software that link devices and enable device registration, onboarding, remote device upgrades, and remote device diagnosis in a fraction of the time while lowering operating and support expenses. Within the IoT ecosystem, cloud introduces DevOps, which enables enterprises automate various activities remotely. As more devices become connected, data protection, control, and management become increasingly important.
Cloud services enable IoT remote device lifecycle management, which is critical for obtaining a 360-degree picture of the device infrastructure. Several cloud providers provide IoT device lifecycle solutions that make updating and setting up firmware and software over the air simple (FOTA).
Application Enablement Cloud Platform:
The cloud allows for application portability and interoperability over a network of diverse cloud installations. To put it another way, these are the intercloud advantages that companies may take use of. SDKs (Software Development Kits) are available in Intercloud systems, allowing businesses to construct applications and software without having to worry about the backend procedures.
Cisco's application enablement platform for application hosting, update, and deployment through the cloud, for example, allows businesses to operate and update apps remotely. Enterprises can shift their apps between cloud and fog nodes to host them and study and monitor the data in close proximity to crucial systems.
Many cloud service providers are focusing on constructing cloud environments based on OCF standards so that they may seamlessly interoperate with the vast majority of apps, appliances, and platforms that support D-to-D (device-to-device) and M-to-M (machine-to-machine) communication. The standardization of the Open Connectivity Foundation (OCF) ensures that devices can safely connect and interact in any cloud environment, bringing interoperability to the connected world.
The standardization of the Open Connectivity Foundation (OCF) ensures that devices can safely connect and interact in any cloud environment, bringing interoperability to the connected world.
Key takeaway
The Internet of Things (sensors, machines, and devices) generate a massive quantity of data per second, as we all know. Cloud computing aids in the storing and analysis of this data, allowing businesses to get the most out of their IoT infrastructure.
The Internet of Things isn't simply about system connectivity, data collection, storage, and analytics. It aids in the modernization of operations by linking legacy and smart devices, as well as machines to the internet, and by removing barriers between IT and OT teams through a single view of systems and data.
It outlines the procedures that must be taken as part of IoT (Internet of Things) security to avoid potential hacking. It also includes links to the following Internet of Things sub-topics:
The Internet of Things (IoT) business is flourishing, and IoT gadgets have become a need in human life. IoT stands for Internet of Things, as we all know. This means that in order to use IoT network services, each device must be IP compliant, which means that all devices must have IP addresses in order to connect to the internet backbone and co-exist in the IoT system.
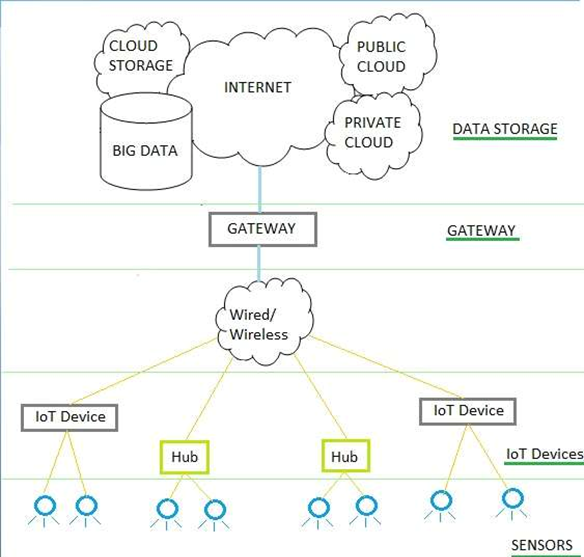
IoT devices are rapidly gaining popularity for a variety of purposes, and people have begun to use them without regard for security concerns. This has resulted in major security concerns, as the IoT system contains numerous loopholes that might be exploited by hackers.
The typical IoT topology is depicted in Figure 1. Data storage or acquisition, data processing, gateway, wired or wireless network, and IoT devices are all part of the IoT system, as indicated (e.g., sensors, hubs and user end devices). IoT users use both public and private cloud storage locations.
Important IoT security aspects
IoT systems can be hacked via wireless devices because most of them use existing wireless networks like wifi, zigbee, zwave, GSM, and so on. Precautions should be taken to ensure that IoT devices and networks are used safely and securely. These are extremely beneficial as IoT security features for both users and IoT network service providers.
• Do not put any sensitive business or personal information in the cloud.
• No passwords should be stored on your IoT device or in the cloud.
• Installing malware without first validating its legitimacy is a bad idea.
• Always get third-party software from reputable and trustworthy sources.
• Do not be in a hurry to start utilizing your IoT gadget; instead, protect it with anti-malware and anti-virus software.
• If feasible, change the password on your IoT device on a frequent basis to boost security.
• If your home network is less secure than your office network, don't bring any important business material home to rework. Do not keep sensitive information on readily hacked storage devices or in public storage facilities. Furthermore, avoid using a public WiFi network for such tasks.
• Turn down unneeded IoT devices in your home network since they are exposed to hackers. When not in use, for example, turn off IoT-enabled thermostats.
• When you don't need internet connectivity, turn off the wifi on your smartphone. This is because it has been discovered that passwords and location information from smartphone-based fitness apps can be easily leaked through public wifi networks.
• Companies in the business, finance, and banking sectors should keep and retain data until it is needed. To reduce the risk of hacking, they should be erased after they are no longer needed.
• House owners should exercise caution to ensure that no unclaimed IoT gadget is installed or placed on their property without their permission. Later on, hackers may be able to use these devices for malicious purposes.
• Regular software fixes for smart watches, IoT sensors, IoT gadgets, and healthcare apps on smartphones should be provided by IoT service providers. This improves the security of IoT devices. These fixes should be able to handle the most recent and contemporary malware and viruses.
Key takeaway
The Internet of Things (IoT) business is flourishing, and IoT gadgets have become a need in human life. IoT stands for Internet of Things, as we all know.
IoT devices are rapidly gaining popularity for a variety of purposes, and people have begun to use them without regard for security concerns.
References:
1. Olivier Hersent, David Boswarthick, Omar Elloumi “The Internet of Things key applications and protocols”, willey
2. Jeeva Jose, Internet of Things, Khanna Publications
3. Michael Miller “The Internet of Things” by Pearson
4. Raj Kamal “INTERNET OF THINGS”, McGraw-Hill, 1ST Edition, 2016
5. ArshdeepBahga, Vijay Madisetti “Internet of Things (A hands-on approach)” 1ST edition, VPI publications,2014
6. Adrian McEwen, Hakin Cassimally “Designing the Internet of Things” Wiley India