UNIT 5
Data base Management System & Cloud computing
Database is a nothing but collection of related data. Data is a collection of facts and figures which is use to produce information.
For example, if we have data about examination. It contains marks and name of student. So using this data, we can then find the topper in the class, percentage wise result of each student and so on.
A Database Management System stores data in efficient way so that it becomes easier to retrieve, manipulate, and produce required result in terms of information. The design of DBMS depends on its architecture. The architecture of DBMS can be seen as either single tier or multi tier. A n tier architecture divides the whole system into related but independent n models, which can be independently modified, altered, changed, or replaced.
In 1-tier architecture, the database system is the only entity where the user directly interacts with the DBMS and uses it. Any changes made by user here will directly be done on the DBMS itself. Database designers and programmers normally prefer to use one-tier architecture as it is easy to access.
If the architecture of DBMS is 2-tier, Application layer lies on the top of the through which the DBMS can be accessed. Programmer design application and uses 2-tier architecture where they access the DBMS.
3-tier architecture separates each tier from each other based on the complexity of the users and how they use the data present in the database. It is the most widely used architecture to design a DBMS.
- Database (Data) Tier: This tier contains relations which contains data and the integrity constraints. At this tier, the database resides along with its query processing languages.
- Application (Middle) Tier: For a user, this application tier gives an abstract view of the database. They are just unaware about the database which exists beyond the application which they are using. Also, the database tier is unaware about the users beyond the application tier. Hence the application layer is in the middle and acts as a mediator between the end-user using application and the database behind it.
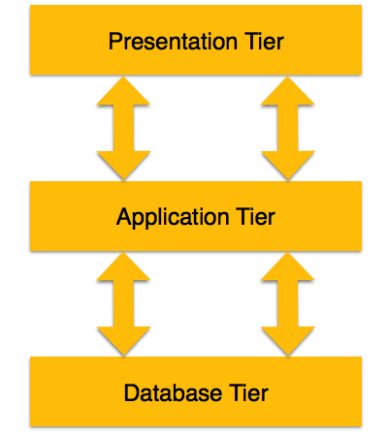
Fig.1.1. 3-tier Architecture of DBMS
- User (Presentation) Tier: End-users operate on this tier and they know nothing about any existence of the database beyond this layer. At this layer database can be viewed by many users. Each user has own perspective. All views as per user are generated at this layer.
File Oriented Approach:-
A traditional File Oriented Approach was based on the following:
- Information stored in files.
- An application program to access information stored in file.
Disadvantages of File Oriented Approach:
- Data Dependency:-
A traditional program is linked to:
- Structure of record.
- Size of each field inside a record.
- Type of each field.
- Position of field in the record.
A program writes to access the master file must be changed whenever new field is added, deleted/modified.
2. Data Redundancy:-
Same piece of information may be stored in different files.
Eg. Student name and one can appear in college file also and in department file also.
3. Data Inconsistency:-
Data duplication leads to inconsistency.
Eg. Name can be changed in department file but not in college file.
4. Lack of flexibility:-
- There is strong coupling between program and data. Every type of result to be generated should be programmed.
- Programming for a new record may require modification of existing record structure which may be difficult.
5. Data Isolation:-
- Data may be scattered in different files. Each file may have different format.
- It is difficult to combine because these files are created without any consideration of relation among data items.
6. Integrity Problems:-
- Data should be satisfy certain integrity constraints.
- Eg. Roll No. Must be unique.
- In traditional approach, code is added in application program to enforce integrity constraints.
- It is difficult to add new/modify existing constraints.
7. Atomicity Problem:-
- A computer system may fail at any time.
- Consider a transaction to x for 1000 Rs. From account A to B.
- System consistency require either both the credit and debit occur, and neither should occur.
- It is difficult to ensure atomicity in FOA.
8. Concurrent Access Problem:-
- In Client-Server, system allows multiple users to update data simultaneously.
- Concurrent programs are difficult to write. It requires knowledge of synchronization, semaphores etc.
9. Security Problems:-
- Every user cannot be allowed to have access to all the data.
- Access can be limited by login and password.
- In application programs it is difficult to enforce security constraint.
Database Approach:
- Insulation between programs and data:-
- Structure of data files is maintained by DBMS.
- Programs look at data at logical level without being concerned about its physical representation.
- Programs need not to be changed if new fields are added.
- This allows data independence. Also called as data abstraction.
2. Data Integrity:-
Integrity rules can be defined and its responsibility lies with DBMS.
3. Enforcing Standard:-
- It is easy to enforce standards in a centralized database environment.
- Required for every communication.
Eg. Display formats, report structure.
4. Reduced Application Development time:-
- DBMS provides many standard functions that the programmer will have to use.
- Program for data retrieval using SQL takes very little time to write.
- It is easy to design forms, report generation.
5. Flexibility:-
- DBMS allows changes to the structure of database without affecting existing data/existing application programs.
6. Self describing nature of database system:-
A database system contains Database, Database Structure, Constraints.
Structure of database is maintained in the system catalog which contains information about database structure. This catalog can be used by a program to extract information about database structure.
7. Sharing of data:-
- DBMS allows sharing of data by any number of users/programs.
- Multiple users can access data at the same time.
- New applications can be build on the existing data.
- Concurrency control mechanism is required for updates to be correct.
- DBMS ensures that concurrent processing operate correctly.
8. No data redundancy/inconsistency:-
- Database approach eliminates redundancy by integrating the files so that the multiple copies of same data are not stored.
- In DBMS, there is only copy of data item. Thus no problem of data inconsistency.
Data models are used to describe the design of a database at the logical level.
Some of the data models are:-
 Entity-Relationship Model Object Based Logical Model
Entity-Relationship Model Object Based Logical Model Relational Model
Relational Model- Hierarchical Model
 Network Model Record Based Logical Model
Network Model Record Based Logical Model- Object Relational Model
Entity-Relationship(E-R) Model:-
The logical structure of a database can be expressed by an E-R diagram. The mainComponents of ER Diagram are:-
a) Rectangles Entity Sets
b) Ellipses Attributes
c) Diamond Relation among entity sets
d) Lines Connects attributes to entity sets and entity sets to relationships.
Example:-
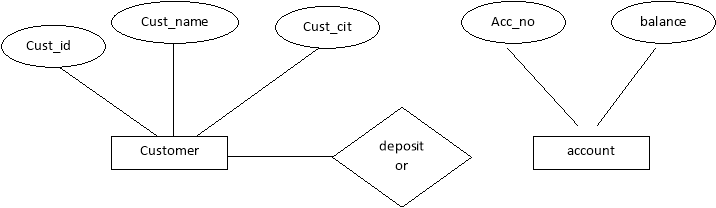

Fig. 1.1 ER diagram
The above E-R diagram has two entities: customer and account .
Customer entity has three attributes:
Cust_id
Cust_name
Cust_city
Account entity has two attributes:-
Acc_no
Balance
Relation depositor gives relationship between customers account.
Eg. Account A-101 is held by customer John.
Relationship can be of the type:
 1:1 One to one
1:1 One to one
 1:M One to many
1:M One to many
 M:1 Many to one
M:1 Many to one
 M:M Many to many
M:M Many to many
Database design in E-R model is converted to design in Relational model.
Relational Model:-
Relational model uses a collection of tables to represent both data and the relationships among those data.
Sample Relational Database:-
Cust-id | Cust_name | Cust_city |
19212 | John | Harrison |
19213 | Smith | Stamford |
20102 | Turner | Rye |
01234 | Jones | Pittsfield |
19212 | John | Harrison |
(a) Customer Table
Acc_no | Balance |
A-101 | 500 |
A-305 | 700 |
A-117 | 1000 |
A-102 | 100 |
A-219 | 1200 |
(b) Account table
Cust_id | Acc_no |
19212 | A-101 |
19213 | A-305 |
20102 | A-117 |
01234 | A-102 |
19212 | A-219 |
(c) Depositor table
Hierarchical Model:-
A Hierarchical model uses tree structure to represent relationship among entities. An Institute can offer many programs. Each program may have a number of courses. A number of students are registered in each course.



 1
1

 M
M
1
M
1
M
Network Model:-
Network model uses two different data structures:-
a) A record type is used to represent as entity set.
b) A set type is used to represent a directed relationship between two record type. It specifies 1:M relationship between owner record type and member record type.


Dept_employee Record type
Set type
Object Relational Model:-
There are two types of ORM:-
- Object-Oriented Data Model (OODM)
- Object-Relational Data Model (ORDM)
These models are used to handle objects:
1) To provide support for complex objects.
2) To provide user extensibility for data types operators and access methods.
3) There should be mechanism to support:
a) Abstract data type.
b) Data of type ‘procedure’.
c) Rules.
Advantages of ORDM:-
- Reuse of sharing standard functions can be implemented centrally, rather than coding it in each application.
- It preserves the existing relational applications.
Database System Architecture:
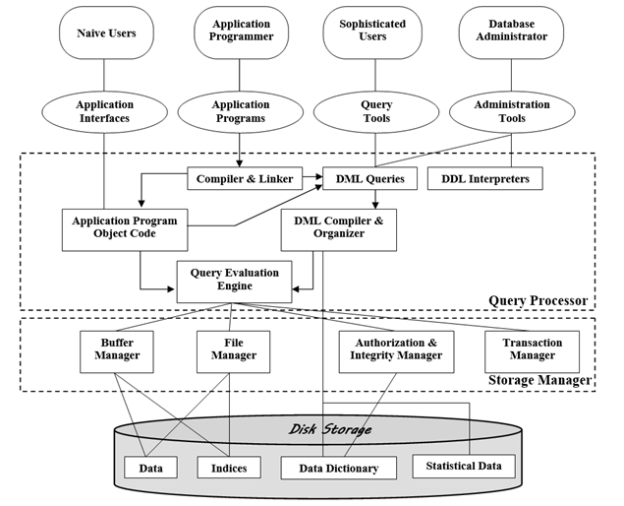
Fig Database System Architecture
Database system architecture is shown in above diagram. It contains functional components like storage manager and query processor. It also shows different database users.
Storage Manager:
A storage manager is a module which provides the interface between data stored in database, application programs used by user and the queries submitted to get the required results. Storage manager is responsible for the tasks like interaction with file manager, query processing which converts DML statements into low-level file system commands. It is also responsible for storing and updating data in the database.
The various components of storage manager are:
- Authorization and integrity manager: It checks different integrity constraints applied to database. It also checks authority of users accessing database.
- Transaction manager: It takes care of ACID properties of transaction. It means, transaction manager ensures that database will remain in consistent state irrespective of software or hardware failure. It also resolves conflictions in concurrent execution.
- File manager: It manages the space allocation on disk storage and different data structures used to represent information stored on disk.
- Buffer manager: It is responsible for fetching data from disk storage into main memory and detecting what data to cache in main memory.
- Data dictionary: It contains metadata. Metadata means data about data. The schema of a relation is an example of metadata.
Query Processor:
Query processor is an important component of the database system. Database system takes help of query processor to simplify and provide access to data. The Query processor components include:
- DDL Interpreter: It takes DDL statements as input. Then relation schema that is definition of relation is recorded in the data dictionary.
- DML Compiler: It translates DML statements like delete, update in a query language into an evaluation plan. Evaluation plan consists of low-level instructions which can be understood by the query evaluation engine. It also performs query optimization. Query optimization picks up the lowest cost evaluation plan among the alternatives.
- Query Evaluation Engine: it takes low-level instructions generated by the DML Compilers as a input and executes it.
Database users:-
Users are differentiated by the way they interact with the system.
- Application Programmers:- Interact with the system through DML system calls embedded with host language. RAD (Rapid Application Development) tools are tools that enable application programmer to construct forms and reports without writing a code.
- Sophisticated users:- Forms a request in a database by using Query Language. They interact with system without writing a program. They submit query to query processor; whose functions are to break down DML statements into instructions that storage manager understands. OLAP and data mining tools simplify their task by letting them view summaries of data.
- Specialized users:-Write Specialized database applications that do not fit into the traditional data processing framework.
- Naïve users:-Invoke one of the permanent applications programs that have been written previously.
Eg. People accessing database over the web, clerical staff etc.
Database Administrator (DBA):-
- Role of DBMS is to have control of both data and program accessing that data. The person having such control over the system is called DBA.
- DBA manages three levels of abstraction.
- DBA specifies the external view of the various users and applications.
- DBA is responsible for the definitions and implementation of the internal level including storage structure.
- Various mappings are defined by the DBA:-
- Mapping between internal and conceptual level.
- Mapping between conceptual and external level.
Vi. DBA ensures integrity of the database.
Vii. DBA stores profile of each user. It is used to stop database access by unauthorized user.
Viii. DBA is responsible for defining procedures to recover database from failures. It enables organization to continue to function without interruption.
Functions of DBA are summarized:-
- Schema definition.
- Storage structures and access method definition.
- Schema and physical organization modification.
- Granting of authorization for data access.
- Integrity constraint specification.
- Recovery of database on failures.
The functional components of database can be broadly classified into:- query processor components and storage manager components.
- DBA creates original database by execution of DDL statement.
- Carries out changes to schema. Alter the physical organization to improve the performance.
- Authorization information is kept in a special system structure that database consults whenever someone attempts to access database.
If a database system is not multi-layered, then it becomes difficult to make any changes in the database system. Database systems are designed in multi-layers as we learnt earlier.
Data Independence
A database system normally contains a lot of data in addition to users’ data. For example, it stores data about data, known as metadata, to locate and retrieve data easily. It is rather difficult to modify or update a set of metadata once it is stored in the database. But as a DBMS expands, it needs to change over time to satisfy the requirements of the users. If the entire data is dependent, it would become a tedious and highly complex job.
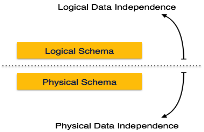
Metadata itself follows a layered architecture, so that when we change data at one layer, it does not affect the data at another level. This data is independent but mapped to each other.
Logical Data Independence
Logical data is data about database, that is, it stores information about how data is managed inside. For example, a table (relation) stored in the database and all its constraints, applied on that relation.
Logical data independence is a kind of mechanism, which liberalizes itself from actual data stored on the disk. If we do some changes on table format, it should not change the data residing on the disk.
Physical Data Independence
All the schemas are logical, and the actual data is stored in bit format on the disk. Physical data independence is the power to change the physical data without impacting the schema or logical data.
For example, in case we want to change or upgrade the storage system itself − suppose we want to replace hard-disks with SSD − it should not have any impact on the logical data or schemas.
Data Dictionary
A data dictionary contains metadata i.e data about the database. The data dictionary is very important as it contains information such as what is in the database, who is allowed to access it, where is the database physically stored etc. The users of the database normally don't interact with the data dictionary, it is only handled by the database administrators.
The data dictionary in general contains information about the following −
- Names of all the database tables and their schemas.
- Details about all the tables in the database, such as their owners, their security constraints, when they were created etc.
- Physical information about the tables such as where they are stored and how.
- Table constraints such as primary key attributes, foreign key information etc.
- Information about the database views that are visible.
This is a data dictionary describing a table that contains employee details.
Field Name | Data Type | Field Size for display | Description | Example |
Employee | Integer | 10 | Unique ID of each employee | 1645000001 |
Name | Text | 20 | Name of the employee | David Heston |
Date of Birth | Date/Time | 10 | DOB of Employee | 08/03/1995 |
Phone Number | Integer | 10 | Phone number of employee | 6583648648 |
The different types of data dictionary are −
Active Data Dictionary
If the structure of the database or its specifications change at any point of time, it should be reflected in the data dictionary. This is the responsibility of the database management system in which the data dictionary resides.
So, the data dictionary is automatically updated by the database management system when any changes are made in the database. This is known as an active data dictionary as it is self updating.
Passive Data Dictionary
This is not as useful or easy to handle as an active data dictionary. A passive data dictionary is maintained separately to the database whose contents are stored in the dictionary. That means that if the database is modified the database dictionary is not automatically updated as in the case of Active Data Dictionary.
So, the passive data dictionary has to be manually updated to match the database. This needs careful handling or else the database and data dictionary are out of sync.
Primary Key
A primary key is a field in a table which uniquely identifies each row/record in a database table. Primary keys must contain unique values. A primary key column cannot have NULL values.
A table can have only one primary key, which may consist of single or multiple fields. When multiple fields are used as a primary key, they are called a composite key.
If a table has a primary key defined on any field(s), then you cannot have two records having the same value of that field(s).
Note − You would use these concepts while creating database tables.
Create Primary Key
Here is the syntax to define the ID attribute as a primary key in a CUSTOMERS table.
CREATE TABLE CUSTOMERS(
ID INT NOT NULL,
NAME VARCHAR (20) NOT NULL,
AGE INT NOT NULL,
ADDRESS CHAR (25) ,
SALARY DECIMAL (18, 2),
PRIMARY KEY (ID)
);
To create a PRIMARY KEY constraint on the "ID" column when the CUSTOMERS table already exists, use the following SQL syntax −
ALTER TABLE CUSTOMER ADD PRIMARY KEY (ID);
NOTE − If you use the ALTER TABLE statement to add a primary key, the primary key column(s) should have already been declared to not contain NULL values (when the table was first created).
For defining a PRIMARY KEY constraint on multiple columns, use the SQL syntax given below.
CREATE TABLE CUSTOMERS(
ID INT NOT NULL,
NAME VARCHAR (20) NOT NULL,
AGE INT NOT NULL,
ADDRESS CHAR (25) ,
SALARY DECIMAL (18, 2),
PRIMARY KEY (ID, NAME)
);
To create a PRIMARY KEY constraint on the "ID" and "NAMES" columns when CUSTOMERS table already exists, use the following SQL syntax.
ALTER TABLE CUSTOMERS
ADD CONSTRAINT PK_CUSTID PRIMARY KEY (ID, NAME);
Delete Primary Key
You can clear the primary key constraints from the table with the syntax given below.
ALTER TABLE CUSTOMERS DROP PRIMARY KEY ;
DBA
A Database Administrator (DBA) in Database Management System (DBMS) is an IT professional who works on creating, maintaining, querying, and tuning the database of the organization. They are also responsible for maintaining data security and integrity. This role requires the professionals to have good knowledge and experience in the particular RDBMS that the company uses. Based on the requirements of the company, there are various types of DBAs including:
Administrative DBA: They maintain and run the databases and servers of the organization. They are mainly concerned with the security patches, replication, and backup of data.
Development DBA: They work on developing SQL queries and stored procedures to meet the requirements of the business. They specialize in database development.
Data Architect: They design schemas, build data structures, table indexes, and relationships. They are mainly responsible for building a structure the meets the business requirements in a specific area.
Data Warehouse DBA: They merge data from numerous data sources and store them in a data warehouse.
Database Language
- A DBMS has appropriate languages and interfaces to express database queries and updates.
- Database languages can be used to read, store and update the data in the database.
Types of Database Language
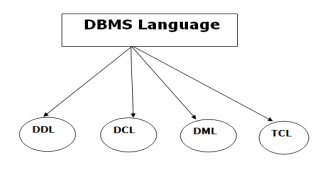
1. Data Definition Language
- DDL stands for Data Definition Language. It is used to define database structure or pattern.
- It is used to create schema, tables, indexes, constraints, etc. in the database.
- Using the DDL statements, you can create the skeleton of the database.
- Data definition language is used to store the information of metadata like the number of tables and schemas, their names, indexes, columns in each table, constraints, etc.
Here are some tasks that come under DDL:
- Create: It is used to create objects in the database.
- Alter: It is used to alter the structure of the database.
- Drop: It is used to delete objects from the database.
- Truncate: It is used to remove all records from a table.
- Rename: It is used to rename an object.
- Comment: It is used to comment on the data dictionary.
These commands are used to update the database schema that's why they come under Data definition language.
2. Data Manipulation Language
DML stands for Data Manipulation Language. It is used for accessing and manipulating data in a database. It handles user requests.
Here are some tasks that come under DML:
- Select: It is used to retrieve data from a database.
- Insert: It is used to insert data into a table.
- Update: It is used to update existing data within a table.
- Delete: It is used to delete all records from a table.
- Merge: It performs UPSERT operation, i.e., insert or update operations.
- Call: It is used to call a structured query language or a Java subprogram.
- Explain Plan: It has the parameter of explaining data.
- Lock Table: It controls concurrency.
3. Data Control Language
- DCL stands for Data Control Language. It is used to retrieve the stored or saved data.
- The DCL execution is transactional. It also has rollback parameters.
(But in Oracle database, the execution of data control language does not have the feature of rolling back.)
Here are some tasks that come under DCL:
- Grant: It is used to give user access privileges to a database.
- Revoke: It is used to take back permissions from the user.
There are the following operations which have the authorization of Revoke:
CONNECT, INSERT, USAGE, EXECUTE, DELETE, UPDATE and SELECT.
4. Transaction Control Language
TCL is used to run the changes made by the DML statement. TCL can be grouped into a logical transaction.
Here are some tasks that come under TCL:
- Commit: It is used to save the transaction on the database.
- Rollback: It is used to restore the database to original since the last Commit.
What is Cloud Computing?
Cloud Computing is defined as storing and accessing of data and computing services over the internet. It doesn't store any data on your personal computer. It is the on-demand availability of computer services like servers, data storage, networking, databases, etc. The main purpose of cloud computing is to give access to data centers to many users. Users can also access data from a remote server.
Example: AWS, Azure, Google Cloud
Benefits of Cloud Computing
The potential for cost saving is the major reason of cloud services adoption by many organizations. Cloud computing gives the freedom to use services as per the requirement and pay only for what you use. Due to cloud computing it has become possible to run IT operations as a outsourced unit without much in-house resources.
Following are the benefits of cloud computing:
- Lower IT infrastructure and computer costs for users
- Improved performance
- Fewer Maintenance issues
- Instant software updates
- Improved compatibility between Operating systems
- Backup and recovery
- Performance and Scalability
- Increased storage capacity
- Increase data safety
Types of Clouds
There are four different cloud models that you can subscribe according to business needs:
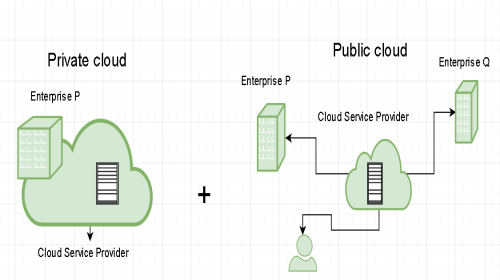
- Private Cloud: Here, computing resources are deployed for one particular organization. This method is more used for intra-business interactions. Where the computing resources can be governed, owned and operated by the same organization.
- Community Cloud: Here, computing resources are provided for a community and organizations.
- Public Cloud: This type of cloud is used usually for B2C (Business to Consumer) type interactions. Here the computing resource is owned, governed and operated by government, an academic or business organization.
- Hybrid Cloud: This type of cloud can be used for both type of interactions - B2B (Business to Business) or B2C ( Business to Consumer). This deployment method is called hybrid cloud as the computing resources are bound together by different clouds.
Cloud infrastructure consists of servers, storage devices, network, cloud management software, deployment software, and platform virtualization.
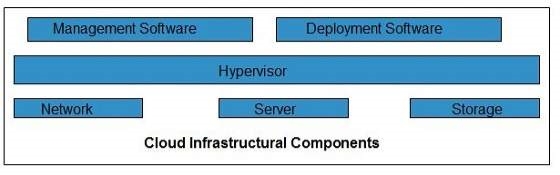
Hypervisor
Hypervisor is a firmware or low-level program that acts as a Virtual Machine Manager. It allows to share the single physical instance of cloud resources between several tenants.
Management Software
It helps to maintain and configure the infrastructure.
Deployment Software
It helps to deploy and integrate the application on the cloud.
Network
It is the key component of cloud infrastructure. It allows to connect cloud services over the Internet. It is also possible to deliver network as a utility over the Internet, which means, the customer can customize the network route and protocol.
Server
The server helps to compute the resource sharing and offers other services such as resource allocation and de-allocation, monitoring the resources, providing security etc.
Storage
Cloud keeps multiple replicas of storage. If one of the storage resources fails, then it can be extracted from another one, which makes cloud computing more reliable.
Infrastructural Constraints
Fundamental constraints that cloud infrastructure should implement are shown in the following diagram:
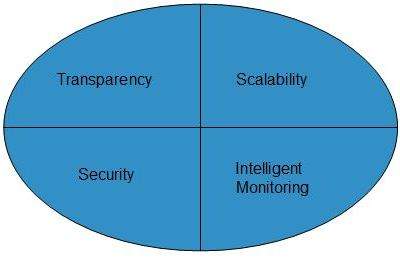
Transparency
Virtualization is the key to share resources in cloud environment. But it is not possible to satisfy the demand with single resource or server. Therefore, there must be transparency in resources, load balancing and application, so that we can scale them on demand.
Scalability
Scaling up an application delivery solution is not that easy as scaling up an application because it involves configuration overhead or even re-architecting the network. So, application delivery solution is need to be scalable which will require the virtual infrastructure such that resource can be provisioned and de-provisioned easily.
Intelligent Monitoring
To achieve transparency and scalability, application solution delivery will need to be capable of intelligent monitoring.
Security
The mega data center in the cloud should be securely architected. Also the control node, an entry point in mega data center, also needs to be secure.
Cloud Computing Services
The three major Cloud Computing Offerings are
- Software as a Service (SaaS)
- Platform as a Service (PaaS)
- Infrastructure as a Service (IaaS)
Different business use some or all of these components according to their requirement.
SaaS (Software as a Service)
SaaS or software as a service is a software distribution model in which applications are hosted by a vendor or service provider and made available to customers over a network (internet). SaaS is becoming an increasingly prevalent delivery model as underlying technologies that supports Service Oriented Architecture (SOA) or Web Services. Through internet this service is available to users anywhere in the world.
Traditionaly, software application needed to be purchased upfront &then installed it onto your computer. SaaS users on the other hand, instead of purchasing the software subscribes to it, usually on monthly basisvia internet.
Anyone who needs an access to a particular piece of software can be subscribe as a user, whether it is one or two people or every thousands of employees in a corporation. SaaS is compatible with all internet enabled devices.
Many important tasks like accounting, sales, invoicing and planning all can be performed using SaaS.
PaaS (Platform as a Service)
Platform as a service, is referred as PaaS, it provides a platform and environment to allow developers to build applications and services. This service is hosted in the cloud and accessed by the users via internet.
To understand in a simple terms, let compare this with painting a picture, where you are provided with paint colors, different paint brushes and paper by your school teacher and you just have to draw a beautiful picture using those tools.
PaaS services are constantly updated & new features added. Software developers, web developers and business can benefit from PaaS. It provides platform to support application development. It includes software support and management services, storage, networking, deploying, testing, collaborating, hosting and maintaining applications.
IaaS (Infrastructure as a Service)
IaaS (Infrastructure As A Service) is one of the fundamental service model of cloud computing alongside PaaS( Platform as a Service). It provides access to computing resources in a virtualized environment “the cloud” on internet. It provides computing infrastructure like virtual server space, network connections, bandwidth, load balancers and IP addresses. The pool of hardware resource is extracted from multiple servers and networks usually distributed across numerous data centers. This provides redundancy and reliability to IaaS.
IaaS(Infrastructure as a service) is a complete package for computing. For small scale businesses who are looking for cutting cost on IT infrastructure, IaaS is one of the solutions. Annually a lot of money is spent in maintenance and buying new components like hard-drives, network connections, external storage device etc. which a business owner could have saved for other expenses by using IaaS.
Cloud computing is an Internet-based computing in which shared the pool of resources are available over a broad network access, these resources can e provisioned or released with minimum management efforts and service provider interaction.
There are four types of cloud:
1. Public cloud
2. Private cloud
3. Hybrid cloud
4. Community cloud
Public cloud:
Public cloud are managed by third parties which provide cloud services over the internet to public, these services are available as pay-as-you-go billing mode.
They offer solutions for minimizing IT infrastructure costs and act as a good option for handling peak loads on the local infrastructure. They are a goto option for small enterprises, which are able to start their businesses without large upfront investments by completely relying on public infrastructure for their IT needs.
A fundamental characteristic of public clouds is multitenancy. A public cloud is meant to serve multiple users, not a single customer. A user requires a virtual computing environment that is separated, and most likely isolated, from other users.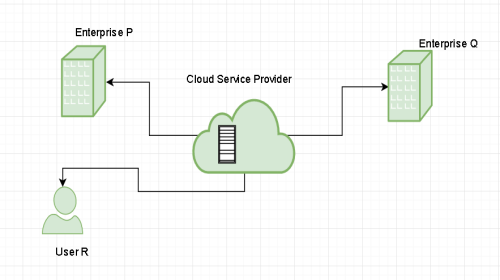
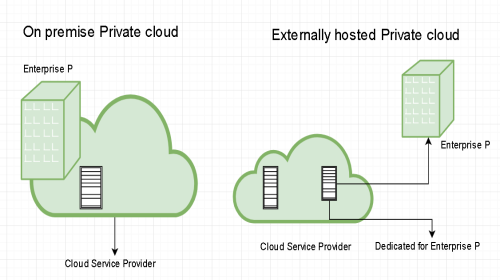
Private cloud :
Private clouds are distributed systems that work on a private infrastructure and providing the users with dynamic provisioning of computing resources. Instead of a pay-as-you-go model as in public clouds, there could be other schemes in that take into account the usage of the cloud and proportionally billing the different departments or sections of an enterprise.
The advantages of using a private cloud are:
- Customer information protection: In private cloud security concerns are less since customer data and other sensitive information does not flow out of a private infrastructure.
- Infrastructure ensuring SLAs: Private cloud provides specific operations such as appropriate clustering, data replication, system monitoring and maintenance, and disaster recovery, and other uptime services.
- Compliance with standard procedures and operations: Specific procedures have to be put in place when deploying and executing applications according to third-party compliance standards.This is not possible in case of public cloud.
Hybrid cloud:
Hybrid cloud is a heterogeneous distributed system resulted by combining facilities of public cloud and private cloud. For this reason they are also called heterogeneous clouds.
A major drawback of private deployments is the inability to scale on demand and to efficiently address peak loads. Here public clouds are needed. Hence, a hybrid cloud takes advantages of both public and private cloud.
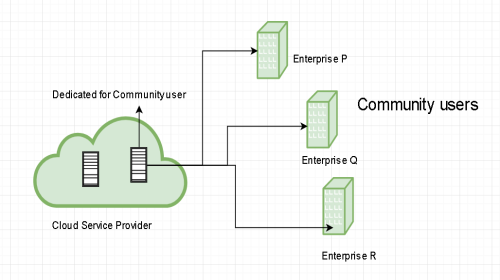
Community cloud:
Community clouds are distributed systems created by integrating the services of different clouds to address the specific needs of an industry, a community, or a business sector.
In community cloud, the infrastructure is shared between organization which have shared concerns or tasks. The cloud may be managed by an organization or a third party.
Sectors that use community clouds are:
- Media industry: Media companies are looking for quick, simple, low-cost way for increasing efficiency of content generation.Most media productions involve an extended ecosystem of partners. In particular, the creation of digital content is the outcome of a collaborative process that includes movement of large data, massive compute-intensive rendering tasks, and complex workflow executions.
- Healthcare industry: In healthcare industry community clouds are used to share information and knowledge on the global level with sensitive data in the private infrastructure.
- Energy and core industry: In these sectors, the community cloud is used to cluster set of solution which collectively addresses management, deployment, and orchestration of services and operations.
- Scientific research: In this organization with common interests of science share large distributed infrastructure for scientific computing.
Cloud computing technologies today has become something every business uses or plans to move to. The types of cloud have catered to every organization’s needs. Be it a public cloud, a private cloud or a hybrid cloud, all the three categories are enough to rock the world. Cloud computing is that one business solution that every enterprise uses. With a number of pros of cloud computing, there come corresponding cons as well.
Today, we will understand the pros and cons of cloud computing in business.
Come; let’s acknowledge the benefits of cloud computing first:
1. Say ‘Goodbye’ to costly systems: Cloud hosting enables the businesses to enjoy minimal expenditure. As everything can be done in the cloud, the local systems of the employees have very less to do with. It saves the dollars that are spent on costly devices.
2. Access from innumerable options: Another advantage of cloud computing is accessing the environment of cloud not only from the system but through other amazing options. These options are tablets, IPad, netbooks and even mobile phones. It not only increases efficiency but enhances the services provided to the consumers. The requested orders, documents, and valuable files are available via a single touch.
3. Software Expense: Cloud infrastructure eliminates the high software costs of the businesses. The numbers of software are already stored on the cloud servers. It removes the need for buying expensive software and paying for their licensing costs. The feature of time to time software upgrading retains your company’s time and money.
4. The cooked food: The expense of adding new employees is not affected by the applications’ setup, installation and arrangement of a new device. Cloud applications are right at the desk of employees that are ready to let them perform all the work. The cloud devices are like cooked food.
5. Lowers traditional servers’ cost: Cloud for business removes the huge costs at the front for the servers of the enterprise. The extra costs associated with increasing memory, hard drive space and processing power are all abolished.
6. Data Centralization: Another key benefit of cloud services is the centralized data. The information for multiple projects and different branch offices are stored in one location that can be accessed from remote places.
7. Data Recovery: Cloud computing providers enables automatic data backup on the cloud system. The recovery of data when a hard drive crash is either not possible or may cost a huge amount of dollars or wastage of valuable time.
8. Sharing Capabilities: We talked about documents accessibility, let’s hit sharing too. All your precious documents and files can be emailed, and shared whenever required. So, you can be present wherever you are not!
9. Cloud Security: Cloud service vendor chooses only the highest secure data centers for your information. Moreover, for sensitive information in the cloud there are proper auditing, passwords, and encryptions.
10. Free Cloud Storage: Cloud is the best platform to store all your valuable information. The storage is free, limitless and forever secure, unlike your system.
11. Instantly Test: Various tools employed in cloud computing permits you to test a new product, application, feature, upgrade or load instantly. The infrastructure is quickly available with flexibility and scalability of distributed testing environment.
So, these were the advantages, now let’s check out the disadvantages of cloud computing as well:
1. Net Connection: For cloud computing, an internet connection is a must to access your precious data.
2. Low Bandwidth: With a low bandwidth net, the benefits of Cloud computing cannot be utilized. Sometimes even a high bandwidth satellite connection can lead to poor quality performance due to high latency.
3. Affected Quality: The internet is used for various reasons such as listening to audios, watching videos online, downloading and uploading heavy files, printing from the cloud and the list goes on. The quality of Cloud computing connection can get affected when a lot of people utilize the net at the same time.
4. Security Issues: Of course, cloud computing keeps your data secure. But for maintaining complete security, an IT consulting firm’s assistance and advice is important. Else, the business can become vulnerable to hackers and threats.
5. Non-negotiable Agreements: Some cloud computing vendors have non-negotiable contracts for the companies. It can be disadvantageous for a lot of businesses.
6. Cost Comparison: Cloud software may look like an affordable option when compared to an in-house installation of software. But it is important to compare the features of the installed software and the cloud software. As some specific features in the cloud software can be missing that might be essential for your business. Sometimes you are charged extra for unrequired additional features.
7. No Hard Drive: As Steve jobs, the late chairman of Apple had exclaimed “I don’t need a hard disk on my computer if I can get to the server faster… carrying around these non-connected computers is byzantine by comparison.” But some people who use programs cannot do without an attached hard drive.
8. Lack of full support: Cloud-based services do not always provide proper support to the customers. The vendors are not available on e-mail or phones and want the consumers to depend on FAQ and online community for support. Due to this, complete transparency is never offered.
9. Incompatibility: Sometimes, there are problems of software incompatibility. As some applications, tools, and software connect particularly to a personal computer.
10. Lack of insight into your network: It’s true cloud computing companies provide you access to data like CPU, RAM, and disk utilization. But just think once how minimal your insight becomes into your network. So, if it’s a bug in your code, a hardware problem or anything, without recognizing the issue it is impossible to fix it.
11. Minimal flexibility: The application and services run on a remote server. Due to this, enterprises using cloud computing have minimal control over the functions of the software as well as hardware. The applications can never be run locally due to the remote software.
SaaS cloud computing applications offer lower total cost of ownership. SaaS applications do not need large capital investments for support infrastructure or licenses. The costs of cloud computing keep on varying, and it becomes important to check ongoing prices.
Reference Books:
1. Introduction of Computers: Peter Norton, TMH
2. Object Oriented Programming with C++:E. Balagurusamy, TMH
3. Object Oriented Programming in C++: Rajesh K.Shukla, Wiley India
4. Concepts in Computing: Kenneth Hoganson, Jones & Bartlett.
5. Operating Systems – Silberschatz and Galvin - Wiley India
6. Computer Networks: Andrew Tananbaum, PHI
7. Data Base Management Systems, Korth, TMH
8. Cloud Computing, Kumar, Wiley India