UNIT 4
Computer Networking & Computer Security Basics
What is a Computer Network?
- Computer Network is a group of computers connected with each other through wires, optical fibres or optical links so that various devices can interact with each other through a network.
- The aim of the computer network is the sharing of resources among various devices.
- In the case of computer network technology, there are several types of networks that vary from simple to complex level.
Components Of Computer Network:
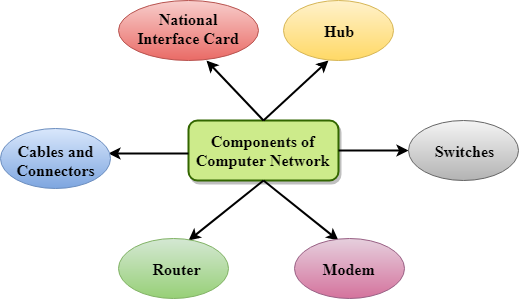
Major components of a computer network are:
NIC(National interface card)
NIC is a device that helps the computer to communicate with another device. The network interface card contains the hardware addresses, the data-link layer protocol use this address to identify the system on the network so that it transfers the data to the correct destination.
There are two types of NIC: wireless NIC and wired NIC.
- Wireless NIC: All the modern laptops use the wireless NIC. In Wireless NIC, a connection is made using the antenna that employs the radio wave technology.
- Wired NIC: Cables use the wired NIC to transfer the data over the medium.
Hub
Hub is a central device that splits the network connection into multiple devices. When computer requests for information from a computer, it sends the request to the Hub. Hub distributes this request to all the interconnected computers.
Switches
Switch is a networking device that groups all the devices over the network to transfer the data to another device. A switch is better than Hub as it does not broadcast the message over the network, i.e., it sends the message to the device for which it belongs to. Therefore, we can say that switch sends the message directly from source to the destination.
Cables and connectors
Cable is a transmission media that transmits the communication signals. There are three types of cables:
- Twisted pair cable: It is a high-speed cable that transmits the data over 1Gbps or more.
- Coaxial cable: Coaxial cable resembles like a TV installation cable. Coaxial cable is more expensive than twisted pair cable, but it provides the high data transmission speed.
- Fibre optic cable: Fibre optic cable is a high-speed cable that transmits the data using light beams. It provides high data transmission speed as compared to other cables. It is more expensive as compared to other cables, so it is installed at the government level.
Router
Router is a device that connects the LAN to the internet. The router is mainly used to connect the distinct networks or connect the internet to multiple computers.
Modem
Modem connects the computer to the internet over the existing telephone line. A modem is not integrated with the computer motherboard. A modem is a separate part on the PC slot found on the motherboard.
Uses of Computer Network
- Resource sharing: Resource sharing is the sharing of resources such as programs, printers, and data among the users on the network without the requirement of the physical location of the resource and user.
- Server-Client model: Computer networking is used in the server-client model. A server is a central computer used to store the information and maintained by the system administrator. Clients are the machines used to access the information stored in the server remotely.
- Communication medium: Computer network behaves as a communication medium among the users. For example, a company contains more than one computer has an email system which the employees use for daily communication.
- E-commerce: Computer network is also important in businesses. We can do the business over the internet. For example, amazon.com is doing their business over the internet, i.e., they are doing their business over the internet.
Features of Computer network
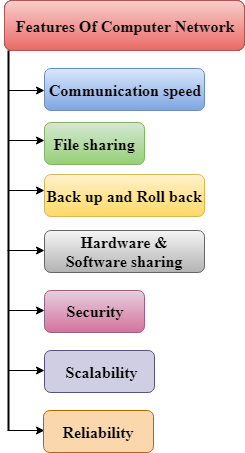
A list Of Computer network features is given below.
- Communication speed
- File sharing
- Back up and Roll back is easy
- Software and Hardware sharing
- Security
- Scalability
- Reliability
Communication speed
Network provides us to communicate over the network in a fast and efficient manner. For example, we can do video conferencing, email messaging, etc. over the internet. Therefore, the computer network is a great way to share our knowledge and ideas.
File sharing
File sharing is one of the major advantage of the computer network. Computer network provides us to share the files with each other.
Back up and Roll back is easy
Since the files are stored in the main server which is centrally located. Therefore, it is easy to take the back up from the main server.
Software and Hardware sharing
We can install the applications on the main server, therefore, the user can access the applications centrally. So, we do not need to install the software on every machine. Similarly, hardware can also be shared.
Security
Network allows the security by ensuring that the user has the right to access the certain files and applications.
Scalability
Scalability means that we can add the new components on the network. Network must be scalable so that we can extend the network by adding new devices. But, it decreases the speed of the connection and data of the transmission speed also decreases, this increases the chances of error occurring. This problem can be overcome by using the routing or switching devices.
Reliability
Computer network can use the alternative source for the data communication in case of any hardware failure.
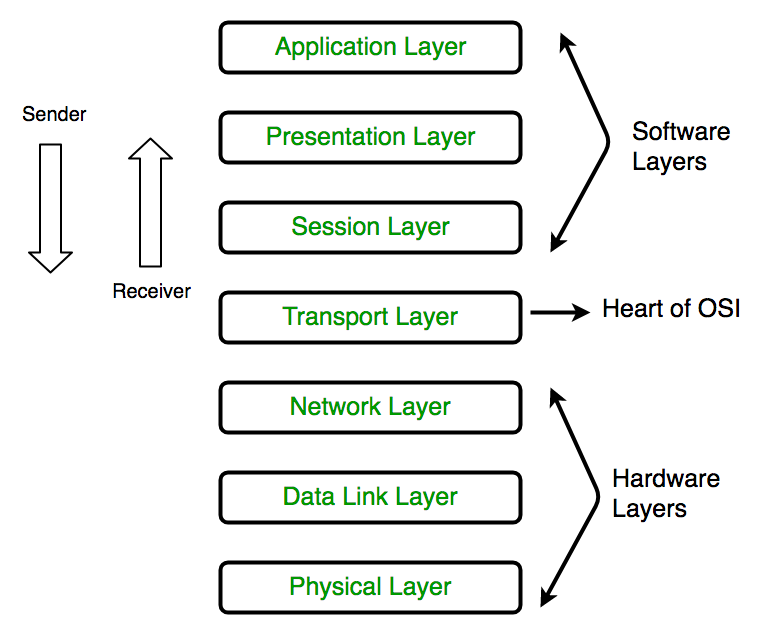
Full form of OSI is Open Systems Interconnection. OSI is developed by ISO – ‘International Organization of Standardization in the year 1974. OSI is seven layer architecture with every layer is having specific functionality to perform. All these seven layers work together to transmit the data from one person to another.
Physical Layer (Layer 1):
The very lowest layer of the OSI model is the physical layer. It is responsible for actual physical connection between devices. The physical layer has information in the form of bits. When receiving the data, this layer will get signal received and then convert it into 0s and 1s and send them to the next layer which is Data Link layer, which will put the frame back together again.
The functions of the physical layer are as follows:
- Bit synchronization: The physical layer provides synchronization of the bits by providing a clock. This clock controls both the sender and the receiver thus providing the synchronization at bit level.
- Bit rate control:The Physical layer defines the transmission rate which is the number of bits sent per second.
- Physical topologies: Physical layer specifies the way in which the different, devices are arranged in a network which is bus, star or mesh topology.
- Transmission mode: It also defines the way in which the data flows between the two connected devices. Various transmission modes possible are: Simplex, half-duplex and full-duplex.
Data Link Layer (DLL) (Layer 2):
The data link layer is responsible for node to node delivery of message. The main function of this layer is to make sure that data transfer is error free from one node to another node, over the physical layer. When the packet arrives in a network, it is the responsibility of DLL to transmit it to the Host using its MAC address.
Data Link Layer is divided into two sub layers:
- Logical Link Control (LLC)
- Media Access Control (MAC)
The packet which is received from the Network layer is again divided into frames depending on the frame size of NIC (Network Interface Card). DLL also encapsulates the Sender and the Receiver’s MAC address in the header.
The Receiver’s MAC address is obtained by placing an ARP(Address Resolution Protocol) request onto the wire asking “Who has that IP address?” and the destination host will reply with its MAC address.
The functions of the data Link layer are as follows:
- Framing: Framing is a function of the data link layer. It provides a way for a sender to transmit the set of bits that are very meaningful to the receiver. This can be accomplished by attaching the special bit patterns to the beginning and end of the frame.
- Physical addressing: After creating frames, Data link layer adds physical addresses (MAC address) of the sender and/or receiver in the header of each of the frame.
- Error control: Data link layer provides the mechanism of error which control in which it detects and then retransmits damaged or lost frames.
- Flow Control: The data rate must be constant on both of the sides else the data may get corrupted thus; flow of control coordinates that amount of data that can be sent before receiving the acknowledgement.
- Access control: When a single communication channel is shared by the multiple devices, MAC sub-layer of data link layer helps to determine that which of the device has control over the channel at a given time.
Network Layer (Layer 3):
Network layer works for the transmission of data from one host to another host which located in different networks. It also takes care of packet routing that is selection of the shortest path to transmit packet, from the number of routes which is available. The sender & the receiver’s IP address are placed in the header by the network layer.
The functions of the Network layer are as follows:
- Routing: The network layer protocols determine which of the route is suitable from source to destination. This function of network layer is called routing.
- Logical Addressing: In order to identify each device on internet uniquely, network layer defines the addressing scheme. The sender & the receiver’s IP address are placed in the header by the network layer. Such an address distinguishes each of the devices uniquely and universally.
Transport Layer (Layer 4):
Transport layer provides the services to the application layer and then takes services from network layer. The data in the transport layer is known as Segments. It is responsible for the End to End delivery of the complete message. Transport layer also provides the acknowledgment of the successful data transmission and then re-transmits the data if an error occurred.
• At sender’s side:
Transport layer receives formatted data from the upper layers, which performs Segmentation and also implements Flow & Error control to ensure that proper data transmission occurs. It also adds Source and Destination port number in its header and then forwards the segmented data into the Network Layer.
• At receiver’s side:
Transport Layer reads the port number from its header and then forwards the Data which it has received to respective application. It also performs the sequencing and the reassembling of the segmented data.
The functions of the transport layer are as follows:
- Segmentation and Reassembly: This layer which accepts the message from the (session) layer then breaks the message into smaller units. Each of the segments produced has the header associated with it. The transport layer at the destination station then reassembles the message.
- Service Point Addressing: In order to deliver message to correct process, transport layer header includes the type of address which is known as service point address or port address. Thus by specifying this address, transport layer makes sure that the message is delivered to a correct process.
The services provided by transport layer as follows:
- Connection Oriented Service: It is a three-phase processes which includes
– Connection Establishment
– Data Transfer
– Termination / disconnection
In this type of transmission, the receiving device sends an acknowledgment, back to the source after a packet or group of packet is received. This type of transmission is reliable and secure. - Connection less service: It is a one phase process and includes Data Transfer. In this type of transmission, the receiver does not acknowledge receipt of a packet. This approach allows for much faster communication between devices. Connection oriented Service is more reliable than connection less Service.
Session Layer (Layer 5):
The session layer is responsible for establishment of the connection and the maintenance of sessions, authentication and also it ensures security.
The functions of the session layer are as follows:
- Session establishment, maintenance and termination: This layer allows the two processes to establish the use and then terminate a connection.
- Synchronization: The session layer allows a process to add checkpoints which are considered as a synchronization points into data. These synchronization point help to identify the error so that the data can be re-synchronized properly, and ends of the messages are not cut prematurely and then data loss is avoided.
- Dialog Controller: The session layer allows the two systems to start communication with each other in half-duplex or in full-duplex.
Presentation Layer (Layer 6):
Presentation layer is also known as Translation layer. The data which is from the application layer is extracted here and then manipulated as per the required format to transmit over the network.
The functions of the presentation layer are as follows:
- Translation: For instance ASCII to EBCDIC.
- Encryption/ Decryption: Data encryption which translates the data into another form or code. The encrypted data is called the cipher text and the decrypted data is called plain text. A key value which is used for encrypting as well as decrypting the data.
- Compression: Reduces the number of bits which need to be transmitted on the network.
Application Layer (Layer 7):
The very top layer of the OSI Reference Model is Application layer which is implemented by the network applications. The applications produce the data, which has to be transferred over the network. The application layer also serves as a window for the application services to access network and for displaying received information to the user.
Example - Application – Browsers, Skype Messenger etc.
The functions of the Application layer are as follows:
- Network Virtual Terminal
- FTAM-File transfer access and management
- Mail Services
- Directory Services
Internetworking is the technique of interconnecting myriad networks together, using connecting devices like routers and gateways. The different networks are owned by different entities that widely vary in terms of network technologies. These networks may be public, private, government, business or academic in nature, whose sizes may vary from small LANs to large WANs. The resulting network of networks is generally termed as internetwork or simply internet.
To enable efficient data communication among multiple networks, the connected networks decide upon a common protocol stack or communication methodology. The two architectural models that define the protocols used for communication are −
- Open System Interconnections model (OSI model)
- TCP/IP model or the Internet Protocol Suite.
Examples of internetworking
- The most widely used internetwork is the Internet (capitalization implies one specific internet), that uses the TCP/IP suite for interconnections. Its biggest service is the World Wide Web. The modern Internet in its present form came in the early 1990s. Since then it has been growing and is presently used by a few billion people all over the world.
- The predecessor of the Internet was ARPANET that was developed in the late 1960s and early 1970s. It was a packet switched network that developed protocols for internetworking.
Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter)
1. Repeater – A repeater operates at the physical layer. Its job is to regenerate the signal over the same network before the signal becomes too weak or corrupted so as to extend the length to which the signal can be transmitted over the same network. An important point to be noted about repeaters is that they do not amplify the signal. When the signal becomes weak, they copy the signal bit by bit and regenerate it at the original strength. It is a 2 port device.
2. Hub – A hub is basically a multiport repeater. A hub connects multiple wires coming from different branches, for example, the connector in star topology which connects different stations. Hubs cannot filter data, so data packets are sent to all connected devices. In other words, collision domain of all hosts connected through Hub remains one. Also, they do not have intelligence to find out best path for data packets which leads to inefficiencies and wastage.
Types of Hub
- Active Hub:- These are the hubs which have their own power supply and can clean, boost and relay the signal along with the network. It serves both as a repeater as well as wiring centre. These are used to extend the maximum distance between nodes.
- Passive Hub :- These are the hubs which collect wiring from nodes and power supply from active hub. These hubs relay signals onto the network without cleaning and boosting them and can’t be used to extend the distance between nodes.
3. Bridge – A bridge operates at data link layer. A bridge is a repeater, with add on the functionality of filtering content by reading the MAC addresses of source and destination. It is also used for interconnecting two LANs working on the same protocol. It has a single input and single output port, thus making it a 2 port device.
Types of Bridges
- Transparent Bridges:- These are the bridge in which the stations are completely unaware of the
bridge’s existence i.e. whether or not a bridge is added or deleted from the network, reconfiguration of
the stations is unnecessary. These bridges make use of two processes i.e. bridge forwarding and bridge learning. - Source Routing Bridges:- In these bridges, routing operation is performed by source station and the frame specifies which route to follow. The hot can discover frame by sending a special frame called discovery frame, which spreads through the entire network using all possible paths to destination.
4. Switch – A switch is a multiport bridge with a buffer and a design that can boost its efficiency(a large number of ports imply less traffic) and performance. A switch is a data link layer device. The switch can perform error checking before forwarding data, that makes it very efficient as it does not forward packets that have errors and forward good packets selectively to correct port only. In other words, switch divides collision domain of hosts, but broadcast domain remains same.
5. Routers – A router is a device like a switch that routes data packets based on their IP addresses. Router is mainly a Network Layer device. Routers normally connect LANs and WANs together and have a dynamically updating routing table based on which they make decisions on routing the data packets. Router divide broadcast domains of hosts connected through it.
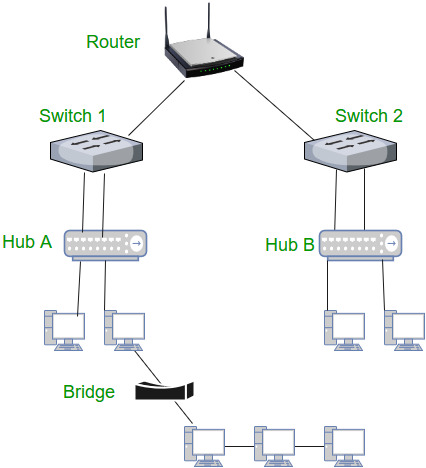
6. Gateway – A gateway, as the name suggests, is a passage to connect two networks together that may work upon different networking models. They basically work as the messenger agents that take data from one system, interpret it, and transfer it to another system. Gateways are also called protocol converters and can operate at any network layer. Gateways are generally more complex than switch or router.
7. Brouter – It is also known as bridging router is a device which combines features of both bridge and router. It can work either at data link layer or at network layer. Working as router, it is capable of routing packets across networks and working as bridge, it is capable of filtering local area network traffic.
- The TCP/IP model was developed prior to the OSI model.
- The TCP/IP model is not exactly similar to the OSI model.
- The TCP/IP model consists of five layers: the application layer, transport layer, network layer, data link layer and physical layer.
- The first four layers provide physical standards, network interface, internetworking, and transport functions that correspond to the first four layers of the OSI model and these four layers are represented in TCP/IP model by a single layer called the application layer.
- TCP/IP is a hierarchical protocol made up of interactive modules, and each of them provides specific functionality.
Here, hierarchical means that each upper-layer protocol is supported by two or more lower-level protocols.
Functions of TCP/IP layers:
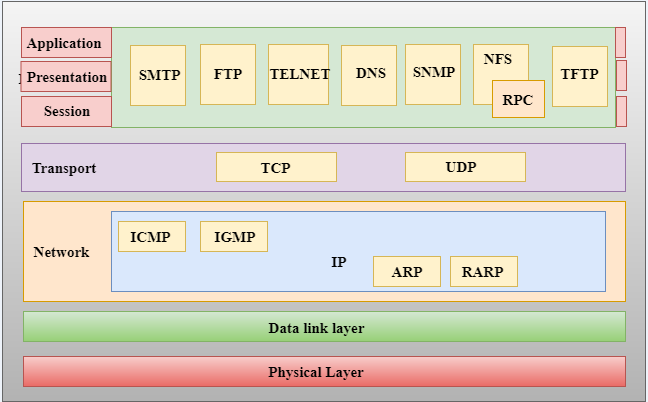
Network Access Layer
- A network layer is the lowest layer of the TCP/IP model.
- A network layer is the combination of the Physical layer and Data Link layer defined in the OSI reference model.
- It defines how the data should be sent physically through the network.
- This layer is mainly responsible for the transmission of the data between two devices on the same network.
- The functions carried out by this layer are encapsulating the IP datagram into frames transmitted by the network and mapping of IP addresses into physical addresses.
- The protocols used by this layer are Ethernet, token ring, FDDI, X.25, frame relay.
Internet Layer
- An internet layer is the second layer of the TCP/IP model.
- An internet layer is also known as the network layer.
- The main responsibility of the internet layer is to send the packets from any network, and they arrive at the destination irrespective of the route they take.
Following are the protocols used in this layer are:
IP Protocol:
IP protocol is used in this layer, and it is the most significant part of the entire TCP/IP suite.
ARP Protocol
Following are the responsibilities of this protocol:
- IP Addressing: This protocol implements logical host addresses known as IP addresses. The IP addresses are used by the internet and higher layers to identify the device and to provide internetwork routing.
- Host-to-host communication: It determines the path through which the data is to be transmitted.
- Data Encapsulation and Formatting: An IP protocol accepts the data from the transport layer protocol. An IP protocol ensures that the data is sent and received securely; it encapsulates the data into message known as IP datagram.
- Fragmentation and Reassembly: The limit imposed on the size of the IP datagram by data link layer protocol is known as Maximum Transmission unit (MTU). If the size of IP datagram is greater than the MTU unit, then the IP protocol splits the datagram into smaller units so that they can travel over the local network. Fragmentation can be done by the sender or intermediate router. At the receiver side, all the fragments are reassembled to form an original message.
- Routing: When IP datagram is sent over the same local network such as LAN, MAN, WAN, it is known as direct delivery. When source and destination are on the distant network, then the IP datagram is sent indirectly. This can be accomplished by routing the IP datagram through various devices such as routers.
- ARP stands for Address Resolution Protocol.
- ARP is a network layer protocol which is used to find the physical address from the IP address.
- The two terms are mainly associated with the ARP Protocol:
- ARP request: When a sender wants to know the physical address of the device, it broadcasts the ARP request to the network.
- ARP reply: Every device attached to the network will accept the ARP request and process the request, but only recipient recognize the IP address and sends back its physical address in the form of ARP reply. The recipient adds the physical address both to its cache memory and to the datagram header
ICMP Protocol
- ICMP stands for Internet Control Message Protocol.
- It is a mechanism used by the hosts or routers to send notifications regarding datagram problems back to the sender.
- A datagram travels from router-to-router until it reaches its destination. If a router is unable to route the data because of some unusual conditions such as disabled links, a device is on fire or network congestion, then the ICMP protocol is used to inform the sender that the datagram is undeliverable.
- An ICMP protocol mainly uses two terms:
- ICMP Test: ICMP Test is used to test whether the destination is reachable or not.
- ICMP Reply: ICMP Reply is used to check whether the destination device is responding or not.
- The core responsibility of the ICMP protocol is to report the problems, not correct them. The responsibility of the correction lies with the sender.
- ICMP can send the messages only to the source, but not to the intermediate routers because the IP datagram carries the addresses of the source and destination but not of the router that it is passed to.
Internet is a global communication system that links together thousands of individual networks. It allows exchange of information between two or more computers on a network. Thus internet helps in transfer of messages through mail, chat, video & audio conference, etc. It has become mandatory for day-to-day activities: bills payment, online shopping and surfing, tutoring, working, communicating with peers, etc.
In this topic, we are going to discuss in detail about concepts like basics of computer networks, Local Area Network (LAN), Wide Area Network (WAN), concept of internet, basics of internet architecture, services on internet, World Wide Web and websites, communication on internet, internet services, preparing computer for internet access, ISPs and examples (Broadband/Dialup/Wi-Fi), internet access techniques, web browsing software, popular web browsing software, configuring web browser, search engines, popular search engines/search for content, accessing web browser, using favorites folder, downloading web pages and printing web pages.
Sr.No. | Internet, WWW, Web Browsers Concepts & Description |
1 | Basics of Computer Networks Computer network is an interconnection between two or more hosts/computers. Different types of networks include LAN, WAN, MAN, etc. |
2 | Internet Architecture Internet is called the network of networks. It is a global communication system that links together thousands of individual networks. Internet architecture is a meta-network, which refers to a congregation of thousands of distinct networks interacting with a common protocol |
3 | Services on Internet Internet acts as a carrier for numerous diverse services, each with its own distinctive features and purposes. |
4 | Communication on Internet Communication can happens through the the Internet by using Email, Internet Relay Chat, Video Conference etc. |
5 | Preparing Computer for Internet Access We shall learn how to use functions and charts in Microsoft Excel Using Formulas like Addition, Subtraction, Multiplication, Division |
6 | Internet Access Techniques A chart is a graphical representation of worksheet data. Charts can make data interesting, attractive and easy to read and evaluate. They can also help you to analyze and compare data. |
7 | Web Browsing Software "World Wide Web" or simple "Web" is the name given to all the resources of internet. The special software or application program with which you can access web is called "Web Browser". |
8 | Configuring Web Browser Search Engine is an application that allows you to search for content on the web. It displays multiple web pages based on the content or a word you have typed. |
9 | Search Engines Search Engine is an application that allows you to search for content on the web. It displays multiple web pages based on the content or a word you have typed. |
10 | Search for the content Search Engine helps to search for content on web using the different stages |
11 | Accessing Web Browser There are several ways to access a web page like using URLs, hyperlinks, using navigating tools, search engine, etc. |
Summary
This topic summarized the concepts of internet like LAN, WAN, internet architecture, internet services, WWW, communications on the internet, internet service providers, internet access techniques, web browsers, search engines, favourite’s folder, configuration of web browsers, and downloading & printing web pages.
E-Commerce
E-commerce means using the Internet and the web for business transactions and/or commercial transactions, which typically involve the exchange of value (e.g., money) across organizational or individual boundaries in return for products and services. Here we focus on digitally enabled commercial transactions among organizations and individuals.
E-business applications turn into e-commerce precisely, when an exchange of value occurs. Digitally enabled transactions include all transactions mediated by digital technology and platform; that is, transactions that occur over the Internet and the web.
Hence, e-tailing is a subset of e-commerce, which encapsulates all “commerce” conducted via the Internet. It refers to that part of e-commerce that entails the sale of product merchandise and does not include sale of services, namely railway tickets, airlines tickets and job portals.
There are three types of destinations that cater to retail sales:
i. Traditional retail- brick-and-mortar
Ii. Corporatized retail- brick-and-mortar
Iii. Corporatized retail- e-tailing
The various objectives of the e-commerce can be laid down as follows:
1. Development of Business-Relationship:
The business development can be done through the e-commerce being the primary and the basic object. As their direct contact in between the company and the consumer, their business relationship will be enhanced. Hence the area of the market can be increased.
2. Better-Customer Service:
As it is done round the clock, the customer will always have online help regarding the products. As all the information is furnished to the customer, it becomes easy to him to choose the best product among all other alternatives. As even the service can also be done through the net immediately, the customer service will be ballooned. By highlighting the customer service, the companies are trying to subjugate a lion-share in the market.
3. Getting more Customers:
In these days it becomes the mandate of the companies to double its customers, and this can be done by rendering the value add service and maintaining the quality. Hence, it is also one of the primary objectives of the companies which supply impetus for the robust growth in sales and overall profit.
Why Security?
Cyberspace (internet, work environment, intranet) is becoming a dangerous place for all organizations and individuals to protect their sensitive data or reputation. This is because of the numerous people and machines accessing it. It is important to mention that the recent studies have shown a big danger is coming from internal threats or from disappointed employees like the Edward Snowden case, another internal threat is that information material can be easy accessible over the intranet.
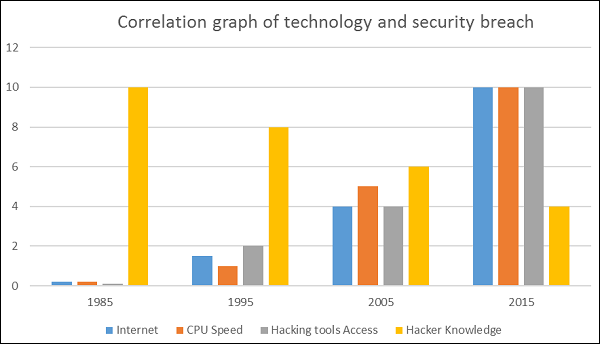
One important indicator is the IT skills of a person that wants to hack or to breach your security has decreased but the success rate of it has increased, this is because of three main factors −
- Hacking tools that can be found very easily by everyone just by googling and they are endless.
- Technology with the end-users has increased rapidly within these years, like internet bandwidth and computer processing speeds.
- Access to hacking information manuals.
All this can make even a school boy with the curiosity, a potential hacker for your organization.
Since locking down all networks is not an available option, the only response the security managers can give is to harden their networks, applications and operating systems to a reasonable level of safety, and conducting a business disaster recovery plan.
The following graph gives us a basic idea.
What to Secure?
Let’s see this case, you are an IT administrator in a small company having two small servers staying in a corner and you are very good at your job. You are doing updates regularly, setting up firewalls, antiviruses, etc. One day, you see that the organization employees are not accessing the systems anymore. When you go and check, you see the cleaning lady doing her job and by mistake, she had removed the power cable and unplugged the server.
What I mean by this case is that even physical security is important in computer security, as most of us think it is the last thing to take care of.
Now let’s go directly to the point of what all to secure in a computer environment −
- First of all, is to check the physical security by setting control systems like motion alarms, door accessing systems, humidity sensors, temperature sensors. All these components decrease the possibility of a computer to be stolen or damaged by humans and environment itself.
- People having access to computer systems should have their own user id with password protection.
- Monitors should be screen saver protected to hide the information from being displayed when the user is away or inactive.
- Secure your network especially wireless, passwords should be used.
- Internet equipment as routers to be protected with password.
- Data that you use to store information which can be financial, or non-financial by encryption.
- Information should be protected in all types of its representation in transmission by encrypting it.
Benefits of Computer Security Awareness
Do you know in all this digital world, what is the biggest hole or the weakest point of the security?
Answer. It is us, humans.
Most of the security breaches come from uninformed and untrained persons which give information to a third party or publish data in Internet without knowing the consequences.
See the following scenario which tells us what employees might end up doing without computer security awareness −
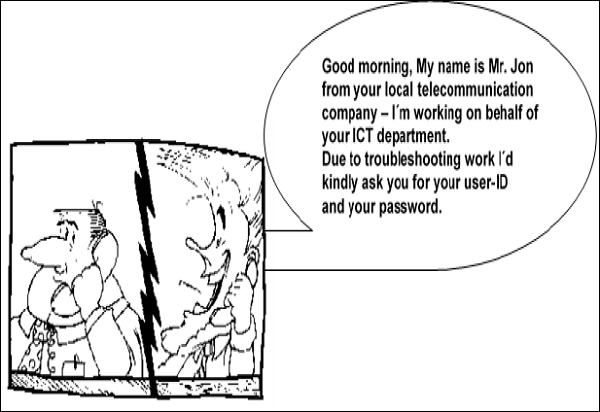
So the benefits of computer security awareness are obvious as it directly minimizes the potential of you being hacked off your identity, your computer, your organization.
Potential Losses due to Security Attacks
The potential loses in this cyberspace are many even if you are using a single computer in your room. Here, I will be listing some examples that have a direct impact on you and on others −
- Losing you data − If your computer has been hacked or infected, there is a big chance that all your stored data might be taken by the attacker.
- Bad usage of your computer resources − This means that your network or computer can go in overload so you cannot access your genuine services or in a worst case scenario, it can be used by the hacker to attack another machine or network.
- Reputation loss − Just think if your Facebook account or business email has been owned by a social engineering attack and it sends fake information to your friends, business partners. You will need time to gain back your reputation.
- Identity theft − This is a case where your identity is stolen (photo, name surname, address, and credit card) and can be used for a crime like making false identity documents.
Basic Computer Security Checklist
There are some basic things that everyone of us in every operating system need to do −
- Check if the user is password protected.
- Check if the operating system is being updated. In my case, I did a screenshot of my laptop which is a Windows 7.
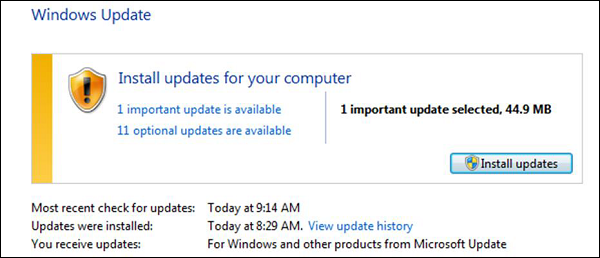
- Check if the antivirus or antimalware is installed and updated. In my case, I have a Kaspersky antivirus being updated.
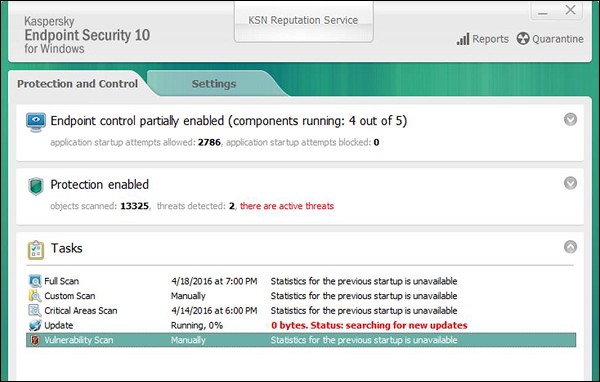
- Check for the unusual services running that consumes resources.
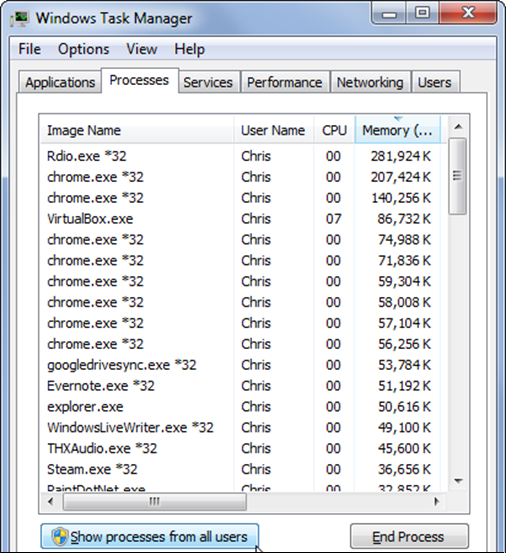
- Check if your monitor is using a screen saver.
- Check if the computer firewall is on or not.
- Check if you are doing backups regularly.
- Check if there are shares that are not useful.
- Check if your account has full rights or is restricted.
- Update other third party software’s.
Virus
A virus is a computer code or program, which is capable of affecting your computer data badly by corrupting or destroying them.
Computer virus has the tendency to make its duplicate copies at a swift pace, and also spread it across every folder and damage the data of your computer system.
A computer virus is actually a malicious software program or "malware" that, when infecting your system, replicates itself by modifying other computer programs and inserting its own code.

Infected computer programs may include data files, or even the "boot" sector of the hard drive.
Types of Virus
Following are the major types of computer virus −
Worms
This is a computer program that replicates itself at a swift pace. Unlike a computer virus, it is self-contained and hence does not need to be part of another program to propagate itself.
Trojan Horse
A Trojan Horse is also a sort of destructive program that remains disguised in a normal software program. It is not exactly a virus, as it cannot replicate itself. However, there is possibility that virus program may remain concealed in the Trojan Horse.
Bombs
It is similar to Trojan Horse, but Logic bombs have some specialty; these include a timing device and hence it will go off only at a particular date and time.
How Does Virus Affect?
Let us discuss in what ways a virus can affect your computer system. The ways are mentioned below −
- By downloading files from the Internet.
- During the removable of media or drives.
- Through pen drive.
- Through e-mail attachments.
- Through unpatched software & services.
- Through unprotected or poor administrator passwords.
Impact of Virus
Let us now see the impact of virus on your computer system −
- Disrupts the normal functionality of respective computer system.
- Disrupts system network use.
- Modifies configuration setting of the system.
- Destructs data.
- Disrupts computer network resources.
- Destructs of confidential data.
Virus Detection
The most fundamental method of detection of virus is to check the functionality of your computer system; a virus affected computer does not take command properly.
However, if there is antivirus software in your computer system, then it can easily check programs and files on a system for virus signatures.
Virus Preventive Measures
Let us now see the different virus preventive measures. A computer system can be protected from virus through the following −
- Installation of an effective antivirus software.
- Patching up the operating system.
- Patching up the client software.
- Putting highly secured Passwords.
- Use of Firewalls.
Most Effective Antivirus
Following are the most popular and effective antivirus from which you can choose one for your personal computer −
- McAfee Antivirus Plus
- Symantec Norton Antivirus
- Avast Pro Antivirus
- Bitdefender Antivirus Plus
- Kaspersky Anti-Virus
- Avira Antivirus
- Webroot Secure Anywhere Antivirus
- Emsisoft Anti-Malware
- Quick Heal Antivirus
- ESET NOD32 Antivirus
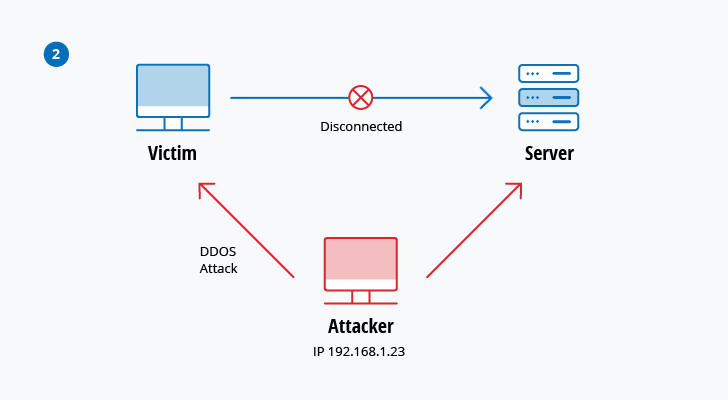
1. Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks
A denial-of-service attack overwhelms a system’s resources so that it cannot respond to service requests. A DDoS attack is also an attack on system’s resources, but it is launched from a large number of other host machines that are infected by malicious software controlled by the attacker.
Unlike attacks that are designed to enable the attacker to gain or increase access, denial-of-service doesn’t provide direct benefits for attackers. For some of them, it’s enough to have the satisfaction of service denial. However, if the attacked resource belongs to a business competitor, then the benefit to the attacker may be real enough. Another purpose of a DoS attack can be to take a system offline so that a different kind of attack can be launched. One common example is session hijacking, which I’ll describe later.
There are different types of DoS and DDoS attacks; the most common are TCP SYN flood attack, teardrop attack, smurf attack, ping-of-death attack and botnets.
TCP SYN flood attack
In this attack, an attacker exploits the use of the buffer space during a Transmission Control Protocol (TCP) session initialization handshake. The attacker’s device floods the target system’s small in-process queue with connection requests, but it does not respond when the target system replies to those requests. This causes the target system to time out while waiting for the response from the attacker’s device, which makes the system crash or become unusable when the connection queue fills up.
There are a few countermeasures to a TCP SYN flood attack:
- Place servers behind a firewall configured to stop inbound SYN packets.
- Increase the size of the connection queue and decrease the timeout on open connections.
Teardrop attack
This attack causes the length and fragmentation offset fields in sequential Internet Protocol (IP) packets to overlap one another on the attacked host; the attacked system attempts to reconstruct packets during the process but fails. The target system then becomes confused and crashes.
If users don’t have patches to protect against this DoS attack, disable SMBv2 and block ports 139 and 445.
Smurf attack
This attack involves using IP spoofing and the ICMP to saturate a target network with traffic. This attack method uses ICMP echo requests targeted at broadcast IP addresses. These ICMP requests originate from a spoofed “victim” address. For instance, if the intended victim address is 10.0.0.10, the attacker would spoof an ICMP echo request from 10.0.0.10 to the broadcast address 10.255.255.255. This request would go to all IPs in the range, with all the responses going back to 10.0.0.10, overwhelming the network. This process is repeatable, and can be automated to generate huge amounts of network congestion.
To protect your devices from this attack, you need to disable IP-directed broadcasts at the routers. This will prevent the ICMP echo broadcast request at the network devices. Another option would be to configure the end systems to keep them from responding to ICMP packets from broadcast addresses.
Ping of death attack
This type of attack uses IP packets to ‘ping a target system with an IP size over the maximum of 65,535 bytes. IP packets of this size are not allowed, so attacker fragments the IP packet. Once the target system reassembles the packet, it can experience buffer overflows and other crashes.
Ping of death attacks can be blocked by using a firewall that will check fragmented IP packets for maximum size.
Botnets
Botnets are the millions of systems infected with malware under hacker control in order to carry out DDoS attacks. These bots or zombie systems are used to carry out attacks against the target systems, often overwhelming the target system’s bandwidth and processing capabilities. These DDoS attacks are difficult to trace because botnets are located in differing geographic locations.
Botnets can be mitigated by:
- RFC3704 filtering, which will deny traffic from spoofed addresses and help ensure that traffic is traceable to its correct source network. For example, RFC3704 filtering will drop packets from bogon list addresses.
- Black hole filtering, which drops undesirable traffic before it enters a protected network. When a DDoS attack is detected, the BGP (Border Gateway Protocol) host should send routing updates to ISP routers so that they route all traffic heading to victim servers to a null0 interface at the next hop.
2. Man-in-the-middle (MitM) attack
A MitM attack occurs when a hacker inserts itself between the communications of a client and a server. Here are some common types of man-in-the-middle attacks:
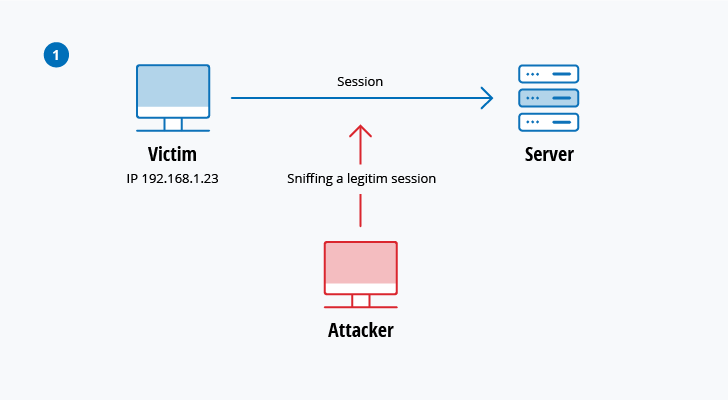
Session hijacking
In this type of MitM attack, an attacker hijacks a session between a trusted client and network server. The attacking computer substitutes its IP address for the trusted client while the server continues the session, believing it is communicating with the client. For instance, the attack might unfold like this:
- A client connects to a server.
- The attacker’s computer gains control of the client.
- The attacker’s computer disconnects the client from the server.
- The attacker’s computer replaces the client’s IP address with its own IP address and
spoofs the client’s sequence numbers. - The attacker’s computer continues dialog with the server and the server believes it is still communicating with the client.
IP Spoofing
IP spoofing is used by an attacker to convince a system that it is communicating with a known, trusted entity and provide the attacker with access to the system. The attacker sends a packet with the IP source address of a known, trusted host instead of its own IP source address to a target host. The target host might accept the packet and act upon it.
Replay
A replay attack occurs when an attacker intercepts and saves old messages and then tries to send them later, impersonating one of the participants. This type can be easily countered with session timestamps or nonce (a random number or a string that changes with time).
Currently, there is no single technology or configuration to prevent all MitM attacks. Generally, encryption and digital certificates provide an effective safeguard against MitM attacks, assuring both the confidentiality and integrity of communications. But a man-in-the-middle attack can be injected into the middle of communications in such a way that encryption will not help — for example, attacker “A” intercepts public key of person “P” and substitute it with his own public key. Then, anyone wanting to send an encrypted message to P using P’s public key is unknowingly using A’s public key. Therefore, A can read the message intended for P and then send the message to P, encrypted in P’s real public key, and P will never notice that the message was compromised. In addition, A could also modify the message before resending it to P. As you can see, P is using encryption and thinks that his information is protected but it is not, because of the MitM attack.
So, how can you make sure that P’s public key belongs to P and not to A? Certificate authorities and hash functions were created to solve this problem. When person 2 (P2) wants to send a message to P, and P wants to be sure that A will not read or modify the message and that the message actually came from P2, the following method must be used:
- P2 creates a symmetric key and encrypts it with P’s public key.
- P2 sends the encrypted symmetric key to P.
- P2 computes a hash function of the message and digitally signs it.
- P2 encrypts his message and the message’s signed hash using the symmetric key and sends the entire thing to P.
- P is able to receive the symmetric key from P2 because only he has the private key to decrypt the encryption.
- P, and only P, can decrypt the symmetrically encrypted message and signed hash because he has the symmetric key.
- He is able to verify that the message has not been altered because he can compute the hash of received message and compare it with digitally signed one.
- P is also able to prove to himself that P2 was the sender because only P2 can sign the hash so that it is verified with P2 public key.
3. Phishing and spear phishing attacks
Phishing attack is the practice of sending emails that appear to be from trusted sources with the goal of gaining personal information or influencing users to do something. It combines social engineering and technical trickery. It could involve an attachment to an email that loads malware onto your computer. It could also be a link to an illegitimate website that can trick you into downloading malware or handing over your personal information.
Spear phishing is a very targeted type of phishing activity. Attackers take the time to conduct research into targets and create messages that are personal and relevant. Because of this, spear phishing can be very hard to identify and even harder to defend against. One of the simplest ways that a hacker can conduct a spear phishing attack is email spoofing, which is when the information in the “From” section of the email is falsified, making it appear as if it is coming from someone you know, such as your management or your partner company. Another technique that scammers use to add credibility to their story is website cloning — they copy legitimate websites to fool you into entering personally identifiable information (PII) or login credentials.
To reduce the risk of being phished, you can use these techniques:
- Critical thinking — Do not accept that an email is the real deal just because you’re busy or stressed or you have 150 other unread messages in your inbox. Stop for a minute and analyze the email.
- Hovering over the links — Move your mouse over the link, but do not click it! Just let your mouse cursor h over over the link and see where would actually take you. Apply critical thinking to decipher the URL.
- Analyzing email headers — Email headers define how an email got to your address. The “Reply-to” and “Return-Path” parameters should lead to the same domain as is stated in the email.
- Sandboxing — You can test email content in a sandbox environment, logging activity from opening the attachment or clicking the links inside the email.
4. Drive-by attack
Drive-by download attacks are a common method of spreading malware. Hackers look for insecure websites and plant a malicious script into HTTP or PHP code on one of the pages. This script might install malware directly onto the computer of someone who visits the site, or it might re-direct the victim to a site controlled by the hackers. Drive-by downloads can happen when visiting a website or viewing an email message or a pop-up window. Unlike many other types of cyber security attacks, a drive-by doesn’t rely on a user to do anything to actively enable the attack — you don’t have to click a download button or open a malicious email attachment to become infected. A drive-by download can take advantage of an app, operating system or web browser that contains security flaws due to unsuccessful updates or lack of updates.
To protect yourself from drive-by attacks, you need to keep your browsers and operating systems up to date and avoid websites that might contain malicious code. Stick to the sites you normally use — although keep in mind that even these sites can be hacked. Don’t keep too many unnecessary programs and apps on your device. The more plug-ins you have, the more vulnerabilities there are that can be exploited by drive-by attacks.
5. Password attack
Because passwords are the most commonly used mechanism to authenticate users to an information system, obtaining passwords is a common and effective attack approach. Access to a person’s password can be obtained by looking around the person’s desk, ‘‘sniffing’’ the connection to the network to acquire unencrypted passwords, using social engineering, gaining access to a password database or outright guessing. The last approach can be done in either a random or systematic manner:
- Brute-force password guessing means using a random approach by trying different passwords and hoping that one work Some logic can be applied by trying passwords related to the person’s name, job title, hobbies or similar items.
- In a dictionary attack, a dictionary of common passwords is used to attempt to gain access to a user’s computer and network. One approach is to copy an encrypted file that contains the passwords, apply the same encryption to a dictionary of commonly used passwords, and compare the results.
In order to protect yourself from dictionary or brute-force attacks, you need to implement an account lockout policy that will lock the account after a few invalid password attempts. You can follow these account lockout best practices in order to set it up correctly.
- Password Policy Best Practices
6. SQL injection attack
SQL injection has become a common issue with database-driven websites. It occurs when a malefactor executes a SQL query to the database via the input data from the client to server. SQL commands are inserted into data-plane input (for example, instead of the login or password) in order to run predefined SQL commands. A successful SQL injection exploit can read sensitive data from the database, modify (insert, update or delete) database data, execute administration operations (such as shutdown) on the database, recover the content of a given file, and, in some cases, issue commands to the operating system.
For example, a web form on a website might request a user’s account name and then send it to the database in order to pull up the associated account information using dynamic SQL like this:
“SELECT * FROM users WHERE account = ‘“ + userProvidedAccountNumber +”’;”
While this works for users who are properly entering their account number, it leaves a hole for attackers. For example, if someone decided to provide an account number of “‘ or ‘1’ = ‘1’”, that would result in a query string of:
“SELECT * FROM users WHERE account = ‘’ or ‘1’ = ‘1’;”
Because ‘1’ = ‘1’ always evaluates to TRUE, the database will return the data for all users instead of just a single user.
The vulnerability to this type of cyber security attack depends on the fact that SQL makes no real distinction between the control and data planes. Therefore, SQL injections work mostly if a website uses dynamic SQL. Additionally, SQL injection is very common with PHP and ASP applications due to the prevalence of older functional interfaces. J2EE and ASP.NET applications are less likely to have easily exploited SQL injections because of the nature of the programmatic interfaces available.
In order to protect yourself from a SQL injection attacks, apply least0privilege model of permissions in your databases. Stick to stored procedures (make sure that these procedures don’t include any dynamic SQL) and prepared statements (parameterized queries). The code that is executed against the database must be strong enough to prevent injection attacks. In addition, validate input data against a white list at the application level.
7. Cross-site scripting (XSS) attack
XSS attacks use third-party web resources to run scripts in the victim’s web browser or scriptable application. Specifically, the attacker injects a payload with malicious JavaScript into a website’s database. When the victim requests a page from the website, the website transmits the page, with the attacker’s payload as part of the HTML body, to the victim’s browser, which executes the malicious script. For example, it might send the victim’s cookie to the attacker’s server, and the attacker can extract it and use it for session hijacking. The most dangerous consequences occur when XSS is used to exploit additional vulnerabilities. These vulnerabilities can enable an attacker to not only steal cookies, but also log key strokes, capture screenshots, discover and collect network information, and remotely access and control the victim’s machine.
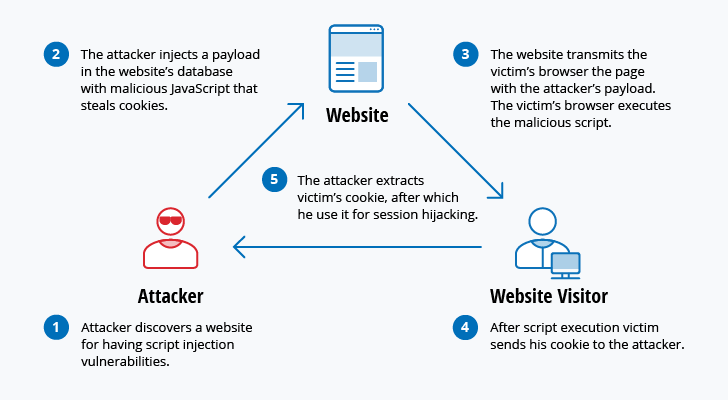
While XSS can be taken advantage of within VBScript, ActiveX and Flash, the most widely abused is JavaScript — primarily because JavaScript is supported widely on the web.
To defend against XSS attacks, developers can sanitize data input by users in an HTTP request before reflecting it back. Make sure all data is validated, filtered or escaped before echoing anything back to the user, such as the values of query parameters during searches. Convert special characters such as ?, &, /, <, > and spaces to their respective HTML or URL encoded equivalents. Give users the option to disable client-side scripts.
8. Eavesdropping attack
Eavesdropping attacks occur through the interception of network traffic. By eavesdropping, an attacker can obtain passwords, credit card numbers and other confidential information that a user might be sending over the network. Eavesdropping can be passive or active:
- Passive eavesdropping — A hacker detects the information by listening to the message transmission in the network.
- Active eavesdropping — A hacker actively grabs the information by disguising himself as friendly unit and by sending queries to transmitters. This is called probing, scanning or tampering.
Detecting passive eavesdropping attacks is often more important than spotting active ones, since active attacks requires the attacker to gain knowledge of the friendly units by conducting passive eavesdropping before.
Data encryption is the best countermeasure for eavesdropping.
9. Birthday attack
Birthday attacks are made against hash algorithms that are used to verify the integrity of a message, software or digital signature. A message processed by a hash function produces a message digest (MD) of fixed length, independent of the length of the input message; this MD uniquely characterizes the message. The birthday attack refers to the probability of finding two random messages that generate the same MD when processed by a hash function. If an attacker calculates same MD for his message as the user has, he can safely replace the user’s message with his, and the receiver will not be able to detect the replacement even if he compares MDs.
10. Malware attack
Malicious software can be described as unwanted software that is installed in your system without your consent. It can attach itself to legitimate code and propagate; it can lurk in useful applications or replicate itself across the Internet. Here are some of the most common types of malware:
- Macro viruses — These viruses infect applications such as Microsoft Word or Excel. Macro viruses attach to an application’s initialization sequence. When the application is opened, the virus executes instructions before transferring control to the application. The virus replicates itself and attaches to other code in the computer system.
- File infectors — File infector viruses usually attach themselves to executable code, such as .exe files. The virus is installed when the code is loaded. Another version of a file infector associates itself with a file by creating a virus file with the same name, but an .exe extension. Therefore, when the file is opened, the virus code will execute.
- System or boot-record infectors — A boot-record virus attaches to the master boot record on hard disks. When the system is started, it will look at the boot sector and load the virus into memory, where it can propagate to other disks and computers.
- Polymorphic viruses — These viruses conceal themselves through varying cycles of encryption and decryption. The encrypted virus and an associated mutation engine are initially decrypted by a decryption program. The virus proceeds to infect an area of code. The mutation engine then develops a new decryption routine and the virus encrypts the mutation engine and a copy of the virus with an algorithm corresponding to the new decryption routine. The encrypted package of mutation engine and virus is attached to new code, and the process repeats. Such viruses are difficult to detect but have a high level of entropy because of the many modifications of their source code. Anti-virus software or free tools like Process Hacker can use this feature to detect them.
- Stealth viruses — Stealth viruses take over system functions to conceal themselves. They do this by compromising malware detection software so that the software will report an infected area as being uninfected. These viruses conceal any increase in the size of an infected file or changes to the file’s date and time of last modification.
- Trojans — A Trojan or a Trojan horse is a program that hides in a useful program and usually has a malicious function. A major difference between viruses and Trojans is that Trojans do not self-replicate. In addition to launching attacks on a system, a Trojan can establish a back door that can be exploited by attackers. For example, a Trojan can be programmed to open a high-numbered port so the hacker can use it to listen and then perform an attack.
- Logic bombs — A logic bomb is a type of malicious software that is appended to an application and is triggered by a specific occurrence, such as a logical condition or a specific date and time.
- Worms — Worms differ from viruses in that they do not attach to a host file, but are self-contained programs that propagate across networks and computers. Worms are commonly spread through email attachments; opening the attachment activates the worm program. A typical worm exploit involves the worm sending a copy of itself to every contact in an infected computer’s email address In addition to conducting malicious activities, a worm spreading across the internet and overloading email servers can result in denial-of-service attacks against nodes on the network.
- Droppers — A dropper is a program used to install viruses on computers. In many instances, the dropper is not infected with malicious code and, therefore might not be detected by virus-scanning software. A dropper can also connect to the internet and download updates to virus software that is resident on a compromised system.
- Ransomware — Ransomware is a type of malware that blocks access to the victim’s data and threatens to publish or delete it unless a ransom is paid. While some simple computer ransomware can lock the system in a way that is not difficult for a knowledgeable person to reverse, more advanced malware uses a technique called cryptoviral extortion, which encrypts the victim’s files in a way that makes them nearly impossible to recover without the decryption key.
Handpicked related content:
- How to Prevent Ransomware Best Practices
- Ransomware Protection Using FSRM and PowerShell
- Ransomware Survivor: 6 Tips to Prevent Ransomware Attacks
- Adware — Adware is a software application used by companies for marketing purposes; advertising banners are displayed while any program is running. Adware can be automatically downloaded to your system while browsing any website and can be viewed through pop-up windows or through a bar that appears on the computer screen automatically.
- Spyware — Spyware is a type of program that is installed to collect information about users, their computers or their browsing habits. It tracks everything you do without your knowledge and sends the data to a remote user. It also can download and install other malicious programs from the internet. Spyware works like adware but is usually a separate program that is installed unknowingly when you install another freeware application.
Pharming, a portmanteau of the words "phishing" and "farming", is a type of cybercrime very similar to phishing, where a website's traffic is manipulated and confidential information is stolen. Pharming exploits the foundation of how Internet browsing works — namely, that the sequence of letters that form an Internet address, such as www.google.com, have to be converted into an IP address by a DNS server in order for the connection to proceed. This exploit attacks this process in one of two ways. First, a hacker may install a virus or Trojan on a user's computer that changes the computer's hosts file to direct traffic away from its intended target, and toward a fake website instead. Second, the hacker may instead poison a DNS server, causing multiple users to inadvertently visit the fake site. The fake websites can be used to install viruses or Trojans on the user's computer, or they could be an attempt to collect personal and financial information for use in identity theft.
Pharming is an especially worrisome form of cybercrime, because in cases of DNS server poisoning, the affected user can have a completely malware-free computer and still become a victim. Even taking precautions such as manually entering in the website address or always using trusted bookmarks isn't enough, because the misdirection happens after the computer sends a connection request.
Protecting yourself from these types of scams begins with the installation of a robust anti-malware and antivirus solution, to be used in conjunction with smart computing practices like avoiding suspicious websites and never clicking on links in suspicious email messages. These steps will prevent most malware from accessing your computer and changing your hosts file.
However, that's only part of the threat, so you also have to be smart about the websites that you visit — especially those that contain your personal or financial information. If the website looks strange, the address in the address bar looks off, or the site starts asking for information that it normally doesn't, check to ensure there is a lock icon in the address bar, denoting a secure website, and click on the lock to ensure that the website has a trusted, up-to-date certificate. Those running DNS servers have some pretty sophisticated anti-pharming techniques at their disposal, but the risk of being hacked is always there, so you can only mitigate the risks through a combination of personal protection and Internet awareness.
What are Ethics?
Ethics are a structure of standards and practices that influence how people lead their lives. It is not strictly implemented to follow these ethics, but it is basically for the benefit of everyone that we do.
Ethics are unlike laws that legally mandate what is right or wrong. Ethics illustrate society’s views about what is right and what is wrong.
Computer Ethics
Computer ethics are a set of moral standards that govern the use of computers. It is society’s views about the use of computers, both hardware and software. Privacy concerns, intellectual property rights and effects on the society are some of the common issues of computer ethics.
Privacy Concerns
- Hacking – is unlawful intrusion into a computer or a network. A hacker can intrude through the security levels of a computer system or network and can acquire unauthorised access to other computers.
- Malware – means malicious software which is created to impair a computer system. Common malware are viruses, spyware, worms and trojan horses. A virus can delete files from a hard drive while a spyware can collect data from a computer.
- Data Protection – also known as information privacy or data privacy is the process of safeguarding data which intends to influence a balance between individual privacy rights while still authorising data to be used for business purposes.
- Anonymity – is a way of keeping a user’s identity masked through various applications.
Intellectual Property Rights
- Copyright – is a form of intellectual property that gives proprietary publication, distribution and usage rights for the author. This means that whatever idea the author created cannot be employed or disseminated by anyone else without the permission of the author.
- Plagiarism – is an act of copying and publishing another person’s work without proper citation. It’s like stealing someone else’s work and releasing it as your own work.
- Cracking – is a way of breaking into a system by getting past the security features of the system. It’s a way of skipping the registration and authentication steps when installing a software.
- Software License – allows the use of digital material by following the license agreement. Ownership remains with the original copyright owner, users are just granted licenses to use the material based on the agreement.
Effects on Society
- Jobs – Some jobs have been abolished while some jobs have become simpler as computers have taken over companies and businesses. Things can now be done in just one click whereas before it takes multiple steps to perform a task. This change may be considered unethical as it limits the skills of the employees.
- There are also ethical concerns on health and safety of employees getting sick from constant sitting, staring at computer screens and typing on the keyboard or clicking on the mouse.
- Environmental Impact – Environment has been affected by computers and the internet since so much time spent using computers increases energy usage which in turn increases the emission of greenhouse gases.
- There are ways where we can save energy like limiting computer time and turning off the computer or putting on sleep mode when not in use. Buying energy efficient computers with Energy Star label can also help save the environment.
- Social Impact – Computers and the internet help people stay in touch with family and friends. Social media has been very popular nowadays.
- Computer gaming influenced society both positively and negatively. Positive effects are improved hand-eye coordination, stress relief and improved strategic thinking. Negative effects are addiction of gamers, isolation from the real world and exposure to violence.
- Computer technology helps the government in improving services to its citizens. Advanced database can hold huge data being collected and analysed by the government.
- Computer technology aids businesses by automating processes, reports and analysis.
Cyber Law also called IT Law is the law regarding Information-technology including computers and internet. It is related to legal informatics and supervises the digital circulation of information, software, information security and e-commerce.
IT law does not consist a separate area of law rather it encloses aspects of contract, intellectual property, privacy and data protection laws. Intellectual property is a key element of IT law. The area of software licence is controversial and still evolving in Europe and elsewhere.
According to Ministry of Electronic and Information Technology, Government of India :
Cyber Laws yields legal recognition to electronic documents and a structure to support e-filing and e-commerce transactions and also provides a legal structure to reduce, check cyber crime.
Importance of Cyber Law:
- It covers all transaction over internet.
- It keeps eyes on all activities over internet.
- It touches every action and every reaction in cyberspace.
Area of Cyber Law:
Cyber laws contain different types of purposes. Some laws create rules for how individuals and companies may use computers and the internet while some laws protect people from becoming the victims of crime through unscrupulous activities on the internet. The major areas of cyber law include:
- Fraud:
Consumers depend on cyber laws to protect them from online fraud. Laws are made to prevent identity theft, credit card theft and other financial crimes that happen online. A person who commits identity theft may face confederate or state criminal charges. They might also encounter a civil action brought by a victim. Cyber lawyers work to both defend and prosecute against allegations of fraud using the internet. - Copyright:
The internet has made copyright violations easier. In early days of online communication, copyright violations was too easy. Both companies and individuals need lawyers to bring actions to impose copyright protections. Copyright violation is an area of cyber law that protects the rights of individuals and companies to profit from their own creative works. - Defamation:
Several personnel use the internet to speak their mind. When people use the internet to say things that are not true, it can cross the line into defamation. Defamation laws are civil laws that save individuals from fake public statements that can harm a business or someone’s personal reputation. When people use the internet to make statements that violate civil laws, that is called Defamation law. - Harassment and Stalking:
Sometimes online statements can violate criminal laws that forbid harassment and stalking. When a person makes threatening statements again and again about someone else online, there is violation of both civil and criminal laws. Cyber lawyers both prosecute and defend people when stalking occurs using the internet and other forms of electronic communication. - Freedom of Speech:
Freedom of speech is an important area of cyber law. Even though cyber laws forbid certain behaviors online, freedom of speech laws also allow people to speak their minds. Cyber lawyers must advise their clients on the limits of free speech including laws that prohibit obscenity. Cyber lawyers may also defend their clients when there is a debate about whether their actions consist of permissible free speech. - Trade Secrets:
Companies doing businesses online often depend on cyber laws to protect their trade secrets. For example, Google and other online search engines spend lots of time developing the algorithms that produce search results. They also spend a great deal of time developing other features like maps, intelligent assistance and flight search services to name a few. Cyber laws help these companies to take legal action as necessary in order to protect their trade secrets. - Contracts and Employment Law:
Every time you click a button that says you agree to the terms and conditions of using a website, you have used cyber law. There are terms and conditions for every website that are somehow related to privacy concerns.
Advantages of Cyber Law:
- Organizations are now able to carry out e-commerce using the legal infrastructure provided by the Act.
- Digital signatures have been given legal validity and sanction in the Act.
- It has opened the doors for the entry of corporate companies for issuing Digital Signatures Certificates in the business of being Certifying Authorities.
- It allows Government to issue notification on the web thus heralding e-governance.
- It gives authority to the companies or organizations to file any form, application or any other document with any office, authority, body or agency owned or controlled by the suitable Government in e-form by means of such e-form as may be prescribed by the suitable Government.
- The IT Act also addresses the important issues of security, which are so critical to the success of electronic transactions.
#1st Tip
Lock your PC when you are away
This is a no-brainer; yet, most of us may conveniently forget to do so. And we don’t realize its importance until some miscreant gets their hands on our private stuff. So, lock it when you’re not at it!
#2nd Tip
Go offline
We may go without food and water for a few days or weeks, but not even a single day without the Internet! I may be a tad bit dramatic here, but this is true for most folks. Having said all that, there comes a time when we do have to go offline , and when we do that, it is a good habit to disconnect our computer too. It may sound unreal but your chances of being nicked by a hacker are way higher when you are connected to the Internet 24/7.
#3rd Tip
Change your passwords
May 5th was observed as the World Password Day and we shared a few tips with our readers. Here, let me share them with you:
- Create a strong password (use uppercase and lowercase letters, numbers, and special characters)
- Keep a unique password for every online account you use
- Change your passwords regularly, especially for your online banking account
#4th Tip
Keep your software up-to-date
Now, there are these things called ‘security vulnerabilities’ – defined as weaknesses/flaws present in the Operating System or any program of your computer, using which a hacker can jinx you to kingdom come. But you can avoid this. How? By applying the latest product and security updates (also known as patches) to your Operating System, Internet Browsers and other programs. These patches work like bandages on security weaknesses, healing them and making them less vulnerable to any exploit. Also, to make sure that your OS is always up-to-date, keep Automatic Updates ON.
#5th Tip
Have an antivirus installed on your computer
While our digital security depends a lot on what steps we follow to maintain it, there are some things that are out of our scope. For instance, visiting a genuine and popular website may install a malware on your computer – something that you would never expect. But, such bad surprises are common. This is where a reliable antivirus software can help you by blocking such compromised websites even before you are able to access them. ‘Proactive protection’ is the word in today’s world of digital security.
#6th Tip
Consider physical security too
In all the hullabaloo of protecting our digital security, let’s not forget that the physical safekeeping of our digital devices is also equally important. Given their compactness, laptops and tablets are more vulnerable to theft. So, be extra cautions against such risks while in public. Power surges can also be a problem, which you can mitigate by following basic safety instructions.
#7th Tip
Back up. Back up. Back up.
This should have been first on my list of computer security habits. Nevertheless, I hope you are reading it anyway. In the wake of the recent upsurge in ransomware attacks, regular data backup is ‘THE’ step that everyone of us ought to take, unless we are not concerned about our computer data. Ransomware, to give you a brief, is a malware that takes an infected computer or its data hostage and demands a ransom from the victim in exchange for the hostages. So, having a backup of all your important data, saves you from being a victim of extortion.
I hope you find all these computer security habits useful, start practicing them and share them with your friends and peers. Stay safe!
Reference Books:
1. Introduction of Computers: Peter Norton, TMH
2. Object Oriented Programming with C++:E. Balagurusamy, TMH
3. Object Oriented Programming in C++: Rajesh K.Shukla, Wiley India
4. Concepts in Computing: Kenneth Hoganson, Jones & Bartlett.
5. Operating Systems – Silberschatz and Galvin - Wiley India
6. Computer Networks: Andrew Tananbaum, PHI
7. Data Base Management Systems, Korth, TMH
8. Cloud Computing, Kumar, Wiley India