Unit - 1
Introduction to computer Networks
A computer network is a collection of devices linked together by a transmission media such as wires or cables. Computers, printers, scanners, and fax machines are examples of these gadgets.
The goal of having a computer network is to send and receive data from other devices through it. Nodes are a term used to describe these devices.
A computer network is a collection of computers linked together by cables, optical fibers, or optical connections so that different devices can communicate with one another.
The purpose of a computer network is to allow different devices to share resources.
There are many different types of networks in computer network technology, ranging from simple to complicated.
Uses Of Computer Network
● Resource sharing: Resource sharing is the sharing of resources like as programmes, printers, and data across network users without regard for the resource's or user's geographical location.
● Server-Client model: The server-client model makes advantage of computer networking. A server is a computer that is used to store data and is managed by the system administrator. Clients are the machines that connect to the server remotely to access data.
● Communication medium: A computer network serves as a means of communication between users. For example, a corporation with multiple computers may have an email system that employees utilise on a daily basis.
● E-commerce: In enterprises, computer networks are equally crucial. We'll be able to conduct business on the internet. For example, amazon.com is doing their business over the internet, i.e., they are doing their business over the internet.
Key takeaway
A computer network is a collection of devices linked together by a transmission media such as wires or cables. Computers, printers, scanners, and fax machines are examples of these gadgets.
● The way in which data is transmitted from one device to another device is known as transmission mode.
● The transmission mode is also known as the communication mode.
● Each communication channel has a direction associated with it, and transmission media provide the direction. Therefore, the transmission mode is also known as a directional mode.
● The transmission mode is defined in the physical layer.
The Transmission mode is divided into three categories:
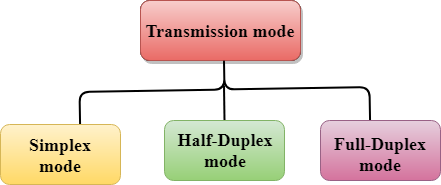
Fig 1: Data flow
● Simplex mode
● Half-duplex mode
● Full-duplex mode
Simplex mode
● In Simplex mode, the communication is unidirectional, i.e., the data flow in one direction.
● A device can only send the data but cannot receive it or it can receive the data but cannot send the data.
● This transmission mode is not very popular as mainly communications require the two-way exchange of data. The simplex mode is used in the business field as in sales that do not require any corresponding reply.
● The radio station is a simplex channel as it transmits the signal to the listeners but never allows them to transmit back.
● Keyboard and Monitor are the examples of the simplex mode as a keyboard can only accept the data from the user and monitor can only be used to display the data on the screen.
● The main advantage of the simplex mode is that the full capacity of the communication channel can be utilized during transmission.
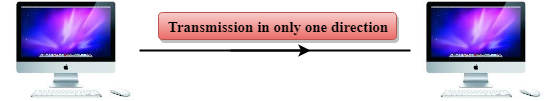
Fig 2: Simplex mode
Advantage of Simplex mode:
● In simplex mode, the station can utilize the entire bandwidth of the communication channel, so that more data can be transmitted at a time.
Disadvantage of Simplex mode:
● Communication is unidirectional, so it has no inter-communication between devices.
Half-Duplex mode
● In a Half-duplex channel, direction can be reversed, i.e., the station can transmit and receive the data as well.
● Messages flow in both the directions, but not at the same time.
● The entire bandwidth of the communication channel is utilized in one direction at a time.
● In half-duplex mode, it is possible to perform the error detection, and if any error occurs, then the receiver requests the sender to retransmit the data.
● A Walkie-talkie is an example of the Half-duplex mode. In Walkie-talkie, one party speaks, and another party listens. After a pause, the other speaks and first party listens. Speaking simultaneously will create the distorted sound which cannot be understood.
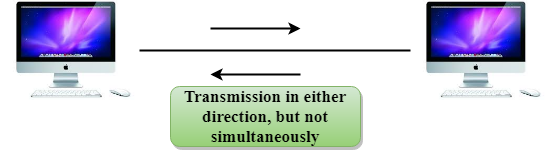
Fig 3: Half duplex mode
Advantage of Half-duplex mode:
● In half-duplex mode, both the devices can send and receive the data and also can utilize the entire bandwidth of the communication channel during the transmission of data.
Disadvantage of Half-Duplex mode:
● In half-duplex mode, when one device is sending the data, then another has to wait, this causes the delay in sending the data at the right time.
Full-duplex mode
● In Full duplex mode, the communication is bi-directional, i.e., the data flow in both the directions.
● Both the stations can send and receive the message simultaneously.
● Full-duplex mode has two simplex channels. One channel has traffic moving in one direction, and another channel has traffic flowing in the opposite direction.
● The Full-duplex mode is the fastest mode of communication between devices.
● The most common example of the full-duplex mode is a telephone network. When two people are communicating with each other by a telephone line, both can talk and listen at the same time.
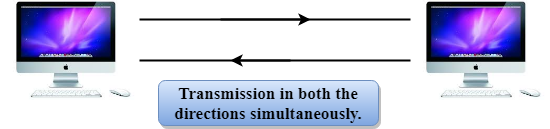
Fig 4: Full duplex mode
Advantage of Full-duplex mode:
● Both the stations can send and receive the data at the same time.
Disadvantage of Full-duplex mode:
● If no dedicated path exists between the devices, then the capacity of the communication channel is divided into two parts.
Differences b/w Simplex, Half-duplex and Full-duplex mode
Basis for comparison | Simplex mode | Half-duplex mode | Full-duplex mode |
Direction of communication | In simplex mode, the communication is unidirectional. | In half-duplex mode, the communication is bidirectional, but one at a time. | In full-duplex mode, the communication is bidirectional. |
Send/Receive | A device can only send the data but cannot receive it or it can only receive the data but cannot send it. | Both the devices can send and receive the data, but one at a time. | Both the devices can send and receive the data simultaneously. |
Performance | The performance of half-duplex mode is better than the simplex mode. | The performance of full-duplex mode is better than the half-duplex mode. | The Full-duplex mode has better performance among simplex and half-duplex mode as it doubles the utilization of the capacity of the communication channel. |
Example | Examples of Simplex mode are radio, keyboard, and monitor. | Example of half-duplex is Walkie-Talkies. | Example of the Full-duplex mode is a telephone network. |
Key takeaway
Each communication channel has a direction associated with it, and transmission media provide the direction. Therefore, the transmission mode is also known as a directional mode.
Distributed Processing is a method of disseminating data over a number of devices, which could be computers or data terminals with some intelligence. The devices are linked by communication systems. A distributed system is one in which components on networked computers communicate and coordinate their operations solely through the transmission of messages.
Originally, traditional microprocessors had only one CPU on a single chip. Manufacturers realized that many processors could be combined on a single unit to speed up procedures as microprocessor engineering progressed. Many modern processors use a multi-core design, such as Intel's quad-core design, which uses four distinct processors to provide incredibly fast programme execution and logic processing.
Parallel processing, in which programmes are made to execute faster with several processors, is an approximate synonym for distributed processing. Hardware users can also tie many computers together to accomplish parallel processing with applications known as distributed processing software, thanks to the approach of putting more than one processor on a microprocessor chip.
Moore's law states that the number of transistors on an each integrated circuit (IC) doubles every two years, which is consistent with the distributed processing paradigm. Engineering tactics like distributed processing have added to the speed of logical devices enabling some astounding gains in the ability of computers to accomplish functional tasks, as this hypothesis has generally proven right over the last four decades.
Examples
● The internet
● An intranet which is a portion of the internet managed by an organization
Key takeaway
Distributed processing is a setup in which multiple individual central processing units (CPU) work on the same programs, functions or systems to provide more capability for a computer or other device.
A computer network must meet the following criteria:
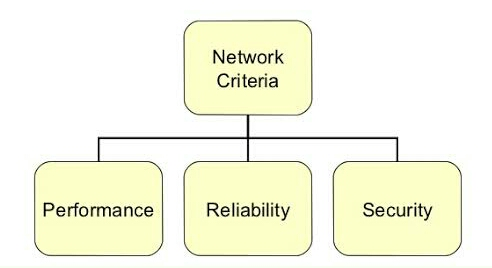
Fig 5: Network criteria
1. Performance – It's calculated in terms of transit and reaction times.
● The time it takes for a message to go from one device to another is known as transit time.
● The period between an enquiry and a response is known as response time.
The following elements influence performance:
● The number of users
● Type of transmission medium
● Capability of connected network
● Efficiency of software
2. Reliability – It's calculated in terms of
● Failure frequency.
● Failures can be overcome.
● Robustness in the face of a disaster.
Network dependability is assessed by the frequency of failure, the time it takes a link to recover from a failure, and the network's resiliency in a disaster, in addition to delivery accuracy.
"Catastrophe" - The network must be secured from disasters like fire, earthquakes, and theft.
3. Security – It entails preventing unwanted access to data.
● Protecting data from unauthorised access and viruses is one of the most important network security concerns.
● Protection can be done on a variety of levels. User identification numbers and passwords are at the most basic level. Encryption techniques are used at a higher level.
● Because a network can be accessed from a variety of locations, it is vulnerable to computer viruses.
There are several different forms of networking connections between two endpoints. One of the most popular examples is home networks and the Internet. Many different types of devices and approaches are used to bind to these types of network architectures.
Connecting computers to these types of networks necessitates the use of a networking system to do so. Point-to-Point Connection and Multipoint Connection are the two types of computer network connections discussed on this page.
Point-to-point connection:
A direct link between two devices, such as a computer and a printer, is known as a point-to-point connection. The devices are connected through a dedicated connection. The transmission between those two devices consumes the entire link's power. Modems and PSTN (Public Switched Telephone Network) communications are responsible for the majority of today's point-to-point connections. There are numerous links between individual pairs of machines in point-to-point networks.
A packet (short message) will take a variety of routes to get from point A to point B. PPP (Point-to-Point Protocol) is a data link protocol that is widely used in networking to create a direct connection between two networking nodes. It has the ability to authenticate connections, encrypt transmissions, and compress data. Serial cable, phone line, trunk line, cellular telephone, advanced radio communications, and fiber optic links such as SONET are all examples of physical networks where PPP is used. PPP is often used to link to the Internet.
Multipoint connection:
A multipoint connection is a connection that connects three or more devices together. Multi-drop configuration is another name for it. Broadcast Networks are networks that have a multipoint architecture.
A message or packet transmitted by any machine in a broadcast network is received by all other machines in the network. The address field in the packet determines the recipient. Any computer checks the packet's address field when it receives it. It processes the transmitted packet if it is for that specific machine; otherwise, it ignores it.
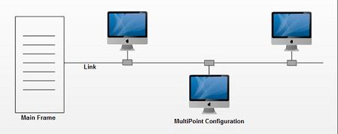
Fig 6: Multipoint connection
Key takeaway:
- A direct link between two devices, such as a computer and a printer, is known as a point-to-point connection.
- The devices are connected through a dedicated connection.
- A multipoint connection is a connection that connects three or more devices together.
Physical topology
Topology refers to the network's structure and how all of the elements are linked to one another. Physical and logical topology are the two forms of topology.
The geometric representation of all the nodes in a network is known as physical topology.
Bus topology:
The bus topology is set up in such a way that all of the stations are linked together by a single backbone cable. Each node is either connected to the backbone cable through a drop cable or is directly connected to it.
When a node wishes to send a message across the network, it does so by sending a message across the network. Regardless of whether the message has been answered, it will be received by all available stations in the network.
The bus topology is commonly used in regular networks such as 802.3 (ethernet) and 802.4 (wireless). In comparison to other topologies, the configuration of a bus topology is very straightforward. The backbone cable is thought of as a "single path" from which the message is sent to all of the stations.
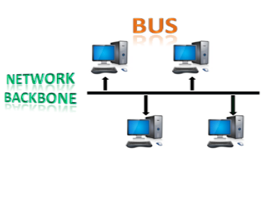
Fig 7: Bus topology
Advantages of Bus topology:
- Low-cost cable: In bus topology, nodes are directly connected to the cable without passing through a hub. Therefore, the initial cost of installation is low.
- Moderate data speeds: Coaxial or twisted pair cables are mainly used in bus-based networks that support upto 10 Mbps.
- Familiar technology: Bus topology is a familiar technology as the installation and troubleshooting techniques are well known, and hardware components are easily available.
- Limited failure: A failure in one node will not have any effect on other nodes.
Ring topology:
The topology of a ring is similar to that of a bus, but with connected ends. The node that receives the previous computer's message will retransmit to the next node. The data is unidirectional, meaning it only moves in one direction.
The data is continually flowed in a single loop, which is referred to as an infinite loop. It has no terminated ends, which means that each node is connected to the next and has no point of termination.
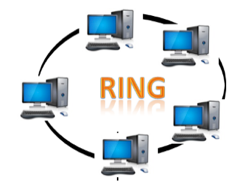
Fig 8: Ring topology
Advantages of Ring topology:
- Network Management: Faulty devices can be removed from the network without bringing the network down.
- Product availability: Many hardware and software tools for network operation and monitoring are available.
- Cost: Twisted pair cabling is inexpensive and easily available. Therefore, the installation cost is very low.
- Reliable: It is a more reliable network because the communication system is not dependent on the single host computer.
Star topology:
The star topology is a network configuration in which each node is connected to a central hub, switch, or device. The central computer is referred to as a server, and the peripheral devices connected to it as clients.
The computers are connected via coaxial cable or RJ-45 cables. In a physical star topology, hubs or switches are primarily used as connection devices. The star topology is the most widely used network topology.
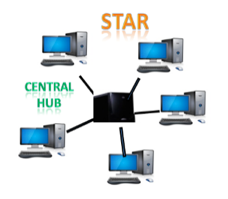
Fig 9: Star topology
Advantages of Star topology
- Efficient troubleshooting: Troubleshooting is quite efficient in a star topology as compared to bus topology. In a bus topology, the manager has to inspect the kilometers of cable. In a star topology, all the stations are connected to the centralized network. Therefore, the network administrator has to go to the single station to troubleshoot the problem.
- Network control: Complex network control features can be easily implemented in the star topology. Any changes made in the star topology are automatically accommodated.
- Limited failure: As each station is connected to the central hub with its own cable, therefore failure in one cable will not affect the entire network.
- Familiar technology: Star topology is a familiar technology as its tools are cost-effective.
- Easily expandable: It is easily expandable as new stations can be added to the open ports on the hub.
- Cost effective: Star topology networks are cost-effective as it uses inexpensive coaxial cable.
- High data speeds: It supports a bandwidth of approx 100Mbps. Ethernet 100BaseT is one of the most popular Star topology networks.
Tree topology:
Tree topology incorporates the advantages of both bus and star topologies. A tree topology is a system in which all computers are related to one another in a hierarchical manner.
A root node is the top-most node in a tree topology, and all other nodes are descendants of the root node. For data transmission, there is only one path between two nodes. As a result, it creates a parent-child hierarchy.
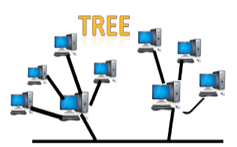
Fig 10: Tree topology
Advantages of Tree topology
- Support for broadband transmission: Tree topology is mainly used to provide broadband transmission, i.e., signals are sent over long distances without being attenuated.
- Easily expandable: We can add the new device to the existing network. Therefore, we can say that tree topology is easily expandable.
- Easily manageable: In tree topology, the whole network is divided into segments known as star networks which can be easily managed and maintained.
- Error detection: Error detection and error correction are very easy in a tree topology.
- Limited failure: The breakdown in one station does not affect the entire network.
- Point-to-point wiring: It has point-to-point wiring for individual segments.
Mesh topology:
Mesh technology is a network configuration in which computers are connected to one another through multiple redundant connections. There are many ways to get from one device to another. It is devoid of the turn, hub, or any central device that serves as a communication hub.
The mesh topology is exemplified by the Internet. Mesh topology is most commonly used in WAN deployments where communication failures are a major concern. Wireless networks commonly use the mesh topology.
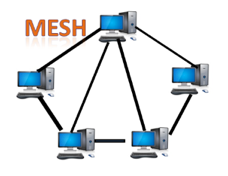
Fig 11: Mesh topology
Advantages of Mesh topology:
- Reliable: The mesh topology networks are very reliable as if any link breakdown will not affect the communication between connected computers.
- Fast Communication: Communication is very fast between the nodes.
- Easier Reconfiguration: Adding new devices would not disrupt the communication between other devices.
Hybrid topology:
Hybrid topology is the synthesis of many different topologies. A hybrid topology connects various links and nodes in order to transfer data. Hybrid topology is described as the combination of two or more different topologies, while similar topologies connecting to each other do not result in Hybrid topology.
For example, if a ring topology exists in one SBI bank branch and a bus topology exists in another SBI bank branch, connecting these two topologies would result in a Hybrid topology.
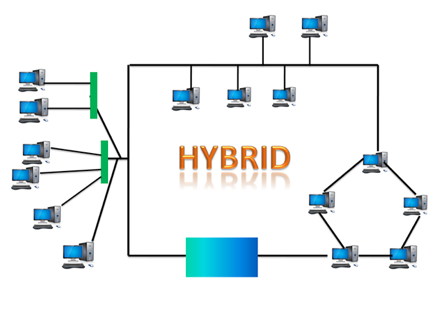
Fig 12: Hybrid topology
Advantages of Hybrid Topology
- Reliable: If a fault occurs in any part of the network will not affect the functioning of the rest of the network.
- Scalable: Size of the network can be easily expanded by adding new devices without affecting the functionality of the existing network.
- Flexible: This topology is very flexible as it can be designed according to the requirements of the organization.
- Effective: Hybrid topology is very effective as it can be designed in such a way that the strength of the network is maximized and weakness of the network is minimized.
Key takeaway:
- Topology refers to the network's structure and how all of the elements are linked to one another.
- The bus topology is set up in such a way that all of the stations are linked together by a single backbone cable.
- The star topology is a network configuration in which each node is connected to a central hub, switch, or device.
- A tree topology is a system in which all computers are related to one another in a hierarchical manner.
- A hybrid topology connects various links and nodes in order to transfer data.
A computer network is a set of computers linked together by a communication medium such as cable or wire.
The geographic area and number of computers that make up a network can be used to determine the scale of the network. It can range from a single computer in a single room to millions of devices distributed across the globe.
Based on their complexity, computer networks are divided into four categories:
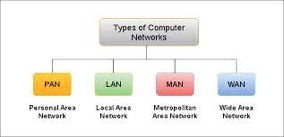
Fig 13: Types of network
PAN:
A personal area network (PAN) is a computer network that is formed around an individual. A computer, a cell phone, or a personal digital assistant are the most common components. PAN can be used to link these personal devices to a digital network and the internet by establishing contact between them.
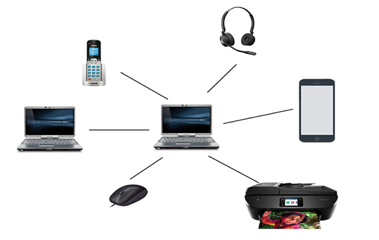
Fig 14: PAN
Characteristics
PAN's primary qualities are listed below:
● It is largely personal gadgets that are networked in a small region.
● Allows you to manage the interconnection of IT devices in a single user's environment.
● Mobile phones, tablets, and laptops are all included in PAN.
● WPAN allows it to connect to the internet wirelessly.
● Cordless mice, keyboards, and Bluetooth systems are examples of PAN appliances.
Advantages
The following are some of the major advantages and benefits of the PAN network:
● PAN networks are considered to be relatively safe and secure.
● It only provides a ten-meter short-range solution.
● Only a tiny space is available.
Disadvantages
The following are the disadvantages of using the PAN network:
● It's possible that it'll make a shaky connection to other networks using the same radio channels.
● There are some distance restrictions.
LAN:
A Local Area Network (LAN) is a set of computers and peripheral devices linked in a small area, such as a classroom, laboratory, home, or office building. It's a popular network for sharing resources such as files, printers, games, and other software. Connecting computers and a printer in someone's home or office is the most basic form of LAN network. LAN will be used as one form of transmission medium in general.
It's a network of less than 5000 interconnected devices spread over several buildings.
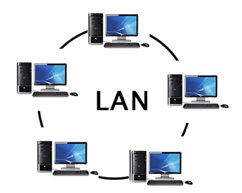
Fig 15: LAN
Characteristics
The following are some of the most important aspects of a LAN network:
● Because it is a private network, it is never regulated by a third party.
● When compared to other WAN technologies, LAN runs at a faster rate.
● Token ring and ethernet are two examples of media access control technologies.
Advantages
The following are the advantages and disadvantages of LAN:
● Local area networks can share computer resources such as hard discs, DVD-ROMs, and printers. This lowers the cost of hardware purchases greatly.
● Instead than acquiring licenced software for each client in the network, you can utilise the same software across the network.
● All network users' data can be saved on the server computer's single hard disc.
● Data and messages can be easily transferred across networked computers.
● It will be simple to handle data in a single location, making data more secure.
● The ability to share a single internet connection among all LAN users is provided by a local area network.
Disadvantages
The following are some of the disadvantages of LAN:
● Because of shared computer resources, LANs will save money, but the initial cost of setting up a LAN is fairly significant.
● Because the LAN administrator has access to every LAN user's personal data files, it does not provide adequate privacy.
● Unauthorized users can gain access to an organization's essential data if the LAN administrator fails to secure the centralised data repository.
● Because there are issues with software setup and hardware failures, a constant LAN administration is required.
MAN:
A Metropolitan Area Network, or MAN, is a computer network that spans a city, a college campus, or a small area. This network is far larger than a LAN, which is usually restricted to a single building or location. This form of network can cover a range of distances from a few miles to tens of miles, depending on the configuration.
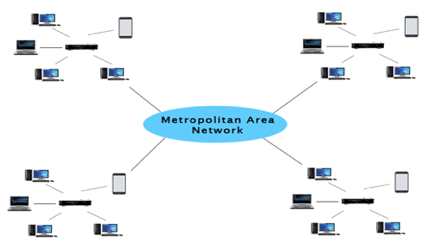
Fig 16: MAN
Characteristics
The following are some of the most important aspects of a LAN network:
● Because it is a private network, it is never regulated by a third party.
● When compared to other WAN technologies, LAN runs at a faster rate.
● Token ring and ethernet are two examples of media access control technologies.
Advantages
The following are the advantages and disadvantages of the MAN network:
● It provides high-speed communication over high-speed carriers such as fibre optic cables.
● It offers good support for a large network and increased WAN connectivity.
● The MAN network's dual bus allows data to be transmitted in both directions at the same time.
● A MAN network usually covers a portion of a city or the entire city.
Disadvantages
The following are some disadvantages and disadvantages of using the MAN network:
● To construct a MAN connection from one location to another, you'll need more cable.
● It's difficult to keep a MAN network secure from hackers.
WAN:
Another significant computer network that spans a vast geographical area is the WAN (Wide Area Network). A WAN network system may be a LAN link that uses telephone lines and radio waves to connect to other LANs. It is usually restricted to a single company or organization.
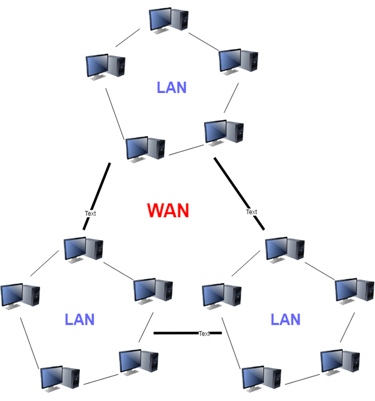
Fig 17: WAN
Characteristics
The following are some of the properties of WAN:
● The software files will be shared among all users, ensuring that everyone has access to the most recent versions.
● WAN can be used by any firm to create a global integrated network.
Advantages
The following are the advantages and disadvantages of WAN:
● The Wide Area Network (WAN) allows you to cover a broader geographical area. As a result, corporate offices located at a greater distance can connect effortlessly.
● Mobile phones, laptops, tablets, desktops, game consoles, and other electronic gadgets are included.
● The radio transmitters and receivers embedded into client devices are used to establish WLAN connections.
Disadvantages
The following are the disadvantages and disadvantages of a WAN network:
● The initial investment setup cost is really significant.
● The WAN network is difficult to maintain. You'll need technicians and network administrators who are well-versed in their fields.
● Because of the vast coverage and use of many technologies, there are more faults and issues.
● Because many wired and wireless technologies are involved, it takes longer to fix issues.
● When compared to other forms of computer networks, it provides less protection.
Key takeaway:
- A computer network is a set of computers linked together by a communication medium such as cable or wire.
- A personal area network is a computer network that is formed around an individual.
- A LAN is a set of computers and peripheral devices linked in a small area, such as a classroom, laboratory, home, or office building.
- A MAN, is a computer network that spans a city, a college campus, or a small area.
- A WAN network system may be a LAN link that uses telephone lines and radio waves to connect to other LANs.
It is an interconnected computer network system that spans the globe. It makes use of the TCP/IP protocol, which is widely used on the internet. A unique IP address is assigned to every machine on the Internet. An IP Address (for example, 110.22.33.114) is a series of integers that identify the location of a computer.
A DNS (Domain Name Server) computer is used to give an IP Address a name so that a user can find a computer by name.
ARPANET was expanded to connect the Department of Defense with US colleges conducting defense-related research. It included most of the country's major universities. When University College London (UK) and Royal Radar Network (Norway) joined the ARPANET and formed a network of networks, the concept of networking received a boost.
Stanford University's Vinton Cerf, Yogen Dalal, and Carl Sunshine invented the name "internet" to characterize this network of networks. They also collaborated on protocols to make information sharing via the Internet easier. The Transmission Control Protocol (TCP) is still the networking's backbone.
In the 1960s, the Internet was created as a means for government researchers to communicate information. In the 1960s, computers were enormous and stationary, and in order to access information stored on them, one had to either travel to the computer's location or have magnetic computer tapes transported through the mail system.
The escalation of the Cold War was another factor in the development of the Internet. The launch of the Sputnik satellite by the Soviet Union prompted the United States Defense Department to examine how information may be distributed even after a nuclear attack. This eventually led to the creation of the ARPANET (Advanced Research Projects Agency Network), which eventually evolved into the Internet we know today. ARPANET was a huge success, but it was only open to a few academic and research institutions with Defense Department contracts. As a result, new networks were formed to facilitate information sharing.
The Internet celebrates its formal birthday on January 1, 1983. Prior to this, there was no standard means for computer networks to communicate with one another. Transfer Control Protocol/Internetwork Protocol (TCP/IP) was created as a new communication protocol.
This allowed various types of computers on various networks to "speak" to one another. On January 1, 1983, ARPANET and the Defense Data Network switched to the TCP/IP standard, resulting in the birth of the Internet. A universal language could now connect all networks.
Key takeaway
In the 1960s, the Internet was created as a means for government researchers to communicate information.
In the 1960s, computers were enormous and stationary, and in order to access information stored on them, one had to either travel to the computer's location or have magnetic computer tapes transported through the mail system.
The Internet today comprises hundreds of thousands of local area networks (LANs) worldwide, interconnected by a backbone wide area network (WAN). LANs commonly operate at speeds ranging from 10 to 100 megabits per second. WAN networks supported lower bit rates until 1995, but the enormous rise in traffic paired with the cheaper cost of optical communications has raised backbone link rates to as high as 10 Gbps. Some network service providers use IP routers connected by ATM switched networks to deal with these high link speeds.
When compared to LAN speeds, corporate data networks often have a substantially slower connection to the Internet backbone. Because LANs provide high-bandwidth traffic between workstations and file servers within a single business, this is appropriate. The WAN, on the other hand, can handle electronic mail and rare file transfers across slow connections. In 1995, 40,000 students, instructors, and staff at the University of California, Berkeley used 20,000 workstations and PCs to access the Internet.
These computers were connected by 10-Mbps Ethernets and 100-Mbps FDDI rings on the university campus. Two 1.5-Mbps lines carried Internet traffic between the university and the rest of the globe, with a 30 percent utilization rate. The telephone links between the campus and the rest of the globe, on the other hand, have a capacity of 200 Mbps.
Users can use one of two methods to access the Internet. The user's PC or workstation is connected to a LAN that is connected to the Internet within a major enterprise, government organization, or university. ISPs are used by users at home and in small businesses. Subscribers link their PCs to ISP hosts using low-speed modems, which then provide Internet access. Some consumers are switching to cable TV or ADSL for faster access.
We look at some of the various variables that have contributed to the Internet's phenomenal success, which had connected 300 million people worldwide by 1999, when it was just 25 years old. The incremental cost of Internet access for users connected to LANs is a small fraction of the cost of the LANs. The network externalities of services like e-mail, Web access, and the establishment of special interest groups, along with the minimal extra cost, resulted in exponential expansion. Second, an increasing number of individuals possess PCs, and newer PCs include networking hardware, such as a built-in modem, as well as software. The cost of Internet access for these consumers is solely determined by their ISP provider's fees.
Protocol
A procedure is essentially the same as a rule. Communication takes place between entities in different systems in computer networks. Anything that can transmit or receive data is considered an entity. Any two entities can't just transmit each other bitstreams and expect to be understood.
In order for the communication to occur, the entities must agree on a protocol.
A protocol is a set of rules that control the transmission of data. What is communicated, how it is communicated, and when it is communicated are all defined by the protocol.
Key elements of a Protocol
The following are the essential components of a protocol:
● Syntax - This phrase mostly refers to the data's structure or format, which essentially refers to the order in which information is displayed. A simple protocol, for example, would anticipate the first 8 bits of data to be the sender's address, the second 8 bits to be the receiver's address, and the rest of the stream to be the message itself.
● Semantics - The meaning of each section of bits is referred to by this phrase. How is a specific pattern should be read, and what action should be made based on that interpretation? Does an address, for example, indicate the route to be traveled or the final destination of the vehicle?
● Timing - This word primarily refers to two aspects: when data should be transmitted and how quickly data can be sent. If a sender sends data at 100 Mbps but the receiver can only handle data at 1 Mbps, the transmission will overload the receiver and some data will be lost.
Standards
Standards are necessary for building and maintaining an open and creative market for equipment manufacturers, as well as ensuring national and international data, telecommunication technology, and process interoperability.
Standards are primarily utilised to offer rules to manufacturers, vendors, government organizations, and other service providers in order to assure the interconnectivity required in today's marketplace and worldwide communications.
There are two types of data communication standards:-
● de facto (which means "by fact"/ "by convention") - Those standards have been adopted as standards despite the fact that they were not approved by an organized body. These kinds of standards are frequently produced by producers who are just trying to outline the functionality of a new product or technology.
● de jure (which means "by law" /"by regulation") - Standards that have been enacted by an officially recognised organization are known as de jure standards.
Standard Organizations
The majority of standards are established through collaboration between standard-setting groups, government regulatory agencies, and forums.
Some Standard Creation committees are:
● International Organization of Standardization(ISO)
● American National Standards Institute(ANSI)
● Electronic Industries Association(EIA)
● Institute of Electrical and Electronics Engineers(IEEE)
OSI stands for Open System Interconnection is a reference model that describes how information from a software application in one computer moves through a physical medium to the software application in another computer’s consists of seven layers, and each layer performs a particular network function’s model was developed by the International Organization for Standardization (ISO) in 1984, and it is now considered as an architectural model for the inter-computer communications.
The OSI model divides the whole task into seven smaller and manageable tasks. Each layer is assigned a particular task. Each layer is self-contained, so that tasks assigned to each layer can be performed independently.
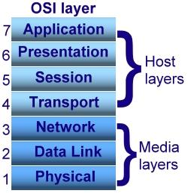
Fig 18: OSI model
The OSI model is divided into two layers: upper layers and lower layers. The upper layer of the OSI model mainly deals with the application related issues, and they are implemented only in the software. The application layer is closest to the end user. Both the end user and the application layer interact with the software applications. An upper layer refers to the layer just above another layer. The lower layer of the OSI model deals with the data transport issues.
The data link layer and the physical layer are implemented in hardware and software. The physical layer is the lowest layer of the OSI model and is closest to the physical medium. The physical layer is mainly responsible for placing the information on the physical medium. There are seven OSI layers.
Each layer has different functions. A list of seven layers are given below:
- Physical Layer: The physical layer is the lowest layer in the OSI reference model. It is in charge of establishing a physical link between the devices. Bits of information are stored in the physical layer. It is in charge of sending individual bits from one node to another. As this layer receives data, it converts the signal received into 0s and 1s and sends them to the Data Link layer, which reassembles the frame.
- Data-Link Layer: The data link layer is in charge of message transmission from node to node. The main purpose of this layer is to ensure that data transfers from one node to another over the physical layer are error-free. It is DLL's duty to send a packet to the Host using its MAC address when it arrives in a network.
- Network Layer: The network layer is responsible for data transmission between hosts on different networks. It also handles packet routing, which is the selection of the shortest path to transmit a packet from a large number of options. The network layer places the IP addresses of the sender and receiver in the header.
- Transport Layer: The application layer receives services from the transport layer, and the network layer receives services from the transport layer. Segments are the units of data in the transport layer. It is in charge of the full message's delivery from beginning to end.
- Session Layer: This layer is in charge of establishing connections, maintaining sessions, authenticating users, and ensuring security.
- Presentation Layer: The Translation layer is also known as the Presentation layer. The data from the application layer is extracted and manipulated here so that it can be transmitted over the network in the appropriate format.
- Application Layer: The Application layer, which is implemented by network applications, is at the very top of the OSI Reference Model stack of layers. These applications generate the data that must be sent over the network. This layer also acts as a window for application services to connect to the network and present the information they receive to the user.
Key takeaway:
- In the present day scenario security of the system is the sole priority of any organization.
- The main aim of any organization is to protect their data from attackers.
TCP/IP Reference Model is a four-layered suite of communication protocols. It was developed by the DoD (Department of Defense) in the 1960s. It is named after the two main protocols that are used in the model, namely, TCP and IP. TCP stands for Transmission Control Protocol and IP stands for Internet Protocol.
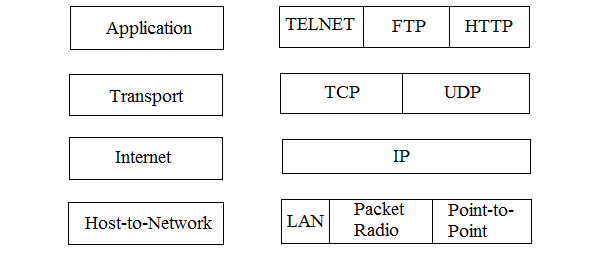
Fig 19: TCP/IP protocol suit
The four layers in the TCP/IP protocol suite are −
Host-to- Network Layer −It is the lowest layer that is concerned with the physical transmission of data. TCP/IP does not specifically define any protocol here but supports all the standard protocols.
Internet Layer −It defines the protocols for logical transmission of data over the network. The main protocol in this layer is Internet Protocol (IP) and it is supported by the protocols ICMP, IGMP, RARP, and ARP.
Transport Layer − It is responsible for error-free end-to-end delivery of data. The protocols defined here are Transmission Control Protocol (TCP) and User Datagram Protocol (UDP).
Application Layer − This is the topmost layer and defines the interface of host programs with the transport layer services. This layer includes all high-level protocols like Telnet, DNS, HTTP, FTP, SMTP, etc.
The advantages of TCP/IP protocol suite are
- It is an industry–standard model that can be effectively deployed in practical networking problems. It is interoperable, i.e., it allows cross-platform communications among heterogeneous networks.
- It is an open protocol suite. It is not owned by any particular institute and so can be used by any individual or organization.
- It is a scalable, client-server architecture. This allows networks to be added without disrupting the current services.
- It assigns an IP address to each computer on the network, thus making each device to be identifiable over the network. It assigns each site a domain name. It provides name and address resolution services.
The disadvantages of the TCP/IP model are
- It is not generic in nature. So, it fails to represent any protocol stack other than the TCP/IP suite. For example, it cannot describe the Bluetooth connection. It does not clearly separate the concepts of services, interfaces, and protocols. So, it is not suitable to describe new technologies in new networks.
- It does not distinguish between the data link and the physical layers, which have very different functionalities. The data link layer should concern with the transmission of frames. On the other hand, the physical layer should lay down the physical characteristics of transmission. A proper model should segregate the two layers.
- It was originally designed and implemented for wide area networks. It is not optimized for small networks like LAN (local area network) and PAN (personal area network). Among its suite of protocols, TCP and IP were carefully designed and well implemented. Some of the other protocols were developed ad hoc and so proved to be unsuitable in the long run. However, due to the popularity of the model, these protocols are being used even 30–40 years after their introduction.
Key takeaway:
- TCP/IP Reference Model is a four-layered suite of communication protocols.
- It is named after the two main protocols that are used in the model, namely, TCP and IP.
- TCP stands for Transmission Control Protocol and IP stands for Internet Protocol.
Difference between OSI and TCP/IP Model
OSI Model | TCP/IP |
It stands for Open System Interconnection. | It stands for Transmission Control Protocol. |
The transport layer offers a guarantee for packet delivery in the OSI model.
| The distribution of packets is not guaranteed by the transport layer. Nonetheless, we may assume that it is a trustworthy model. |
The vertical method is used in this model. | The horizontal method is used in this model. |
It consists of 7 layers. | It consists of 4 layers. |
The OSI model was created by ISO (International Standard Organization). | ARPANET was the company that produced it (Advanced Research Project Agency Network). |
The network layer in this model offers both connection-oriented and connectionless services. | Only connectionless services are provided by the network layer.
|
This model isn't seen very much. | This model is quite popular. |
It allows devices such as routers, motherboards, switches, and other hardware to be standardized. | It does not provide devices with standardization. It allows computers to communicate with one another. |
References:
- Forouzan, "Data Communication and Networking", TMH
- A.S. Tanenbaum, Computer Networks, Pearson Education
- W. Stallings, Data and Computer Communication, Macmillan Press
- Bhavneet Sidhu, An Integrated approach to Computer Networks, Khanna Publishing House
Unit - 1
Introduction to computer Networks
A computer network is a collection of devices linked together by a transmission media such as wires or cables. Computers, printers, scanners, and fax machines are examples of these gadgets.
The goal of having a computer network is to send and receive data from other devices through it. Nodes are a term used to describe these devices.
A computer network is a collection of computers linked together by cables, optical fibers, or optical connections so that different devices can communicate with one another.
The purpose of a computer network is to allow different devices to share resources.
There are many different types of networks in computer network technology, ranging from simple to complicated.
Uses Of Computer Network
● Resource sharing: Resource sharing is the sharing of resources like as programmes, printers, and data across network users without regard for the resource's or user's geographical location.
● Server-Client model: The server-client model makes advantage of computer networking. A server is a computer that is used to store data and is managed by the system administrator. Clients are the machines that connect to the server remotely to access data.
● Communication medium: A computer network serves as a means of communication between users. For example, a corporation with multiple computers may have an email system that employees utilise on a daily basis.
● E-commerce: In enterprises, computer networks are equally crucial. We'll be able to conduct business on the internet. For example, amazon.com is doing their business over the internet, i.e., they are doing their business over the internet.
Key takeaway
A computer network is a collection of devices linked together by a transmission media such as wires or cables. Computers, printers, scanners, and fax machines are examples of these gadgets.
● The way in which data is transmitted from one device to another device is known as transmission mode.
● The transmission mode is also known as the communication mode.
● Each communication channel has a direction associated with it, and transmission media provide the direction. Therefore, the transmission mode is also known as a directional mode.
● The transmission mode is defined in the physical layer.
The Transmission mode is divided into three categories:
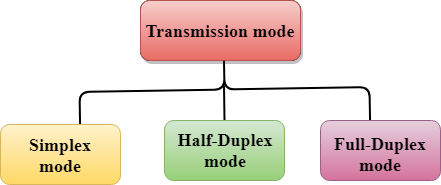
Fig 1: Data flow
● Simplex mode
● Half-duplex mode
● Full-duplex mode
Simplex mode
● In Simplex mode, the communication is unidirectional, i.e., the data flow in one direction.
● A device can only send the data but cannot receive it or it can receive the data but cannot send the data.
● This transmission mode is not very popular as mainly communications require the two-way exchange of data. The simplex mode is used in the business field as in sales that do not require any corresponding reply.
● The radio station is a simplex channel as it transmits the signal to the listeners but never allows them to transmit back.
● Keyboard and Monitor are the examples of the simplex mode as a keyboard can only accept the data from the user and monitor can only be used to display the data on the screen.
● The main advantage of the simplex mode is that the full capacity of the communication channel can be utilized during transmission.
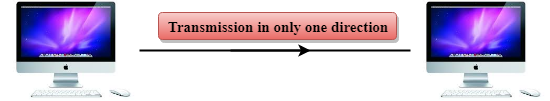
Fig 2: Simplex mode
Advantage of Simplex mode:
● In simplex mode, the station can utilize the entire bandwidth of the communication channel, so that more data can be transmitted at a time.
Disadvantage of Simplex mode:
● Communication is unidirectional, so it has no inter-communication between devices.
Half-Duplex mode
● In a Half-duplex channel, direction can be reversed, i.e., the station can transmit and receive the data as well.
● Messages flow in both the directions, but not at the same time.
● The entire bandwidth of the communication channel is utilized in one direction at a time.
● In half-duplex mode, it is possible to perform the error detection, and if any error occurs, then the receiver requests the sender to retransmit the data.
● A Walkie-talkie is an example of the Half-duplex mode. In Walkie-talkie, one party speaks, and another party listens. After a pause, the other speaks and first party listens. Speaking simultaneously will create the distorted sound which cannot be understood.
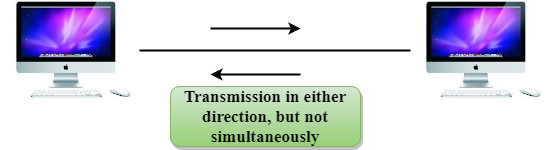
Fig 3: Half duplex mode
Advantage of Half-duplex mode:
● In half-duplex mode, both the devices can send and receive the data and also can utilize the entire bandwidth of the communication channel during the transmission of data.
Disadvantage of Half-Duplex mode:
● In half-duplex mode, when one device is sending the data, then another has to wait, this causes the delay in sending the data at the right time.
Full-duplex mode
● In Full duplex mode, the communication is bi-directional, i.e., the data flow in both the directions.
● Both the stations can send and receive the message simultaneously.
● Full-duplex mode has two simplex channels. One channel has traffic moving in one direction, and another channel has traffic flowing in the opposite direction.
● The Full-duplex mode is the fastest mode of communication between devices.
● The most common example of the full-duplex mode is a telephone network. When two people are communicating with each other by a telephone line, both can talk and listen at the same time.
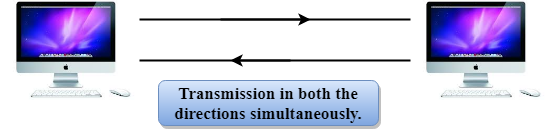
Fig 4: Full duplex mode
Advantage of Full-duplex mode:
● Both the stations can send and receive the data at the same time.
Disadvantage of Full-duplex mode:
● If no dedicated path exists between the devices, then the capacity of the communication channel is divided into two parts.
Differences b/w Simplex, Half-duplex and Full-duplex mode
Basis for comparison | Simplex mode | Half-duplex mode | Full-duplex mode |
Direction of communication | In simplex mode, the communication is unidirectional. | In half-duplex mode, the communication is bidirectional, but one at a time. | In full-duplex mode, the communication is bidirectional. |
Send/Receive | A device can only send the data but cannot receive it or it can only receive the data but cannot send it. | Both the devices can send and receive the data, but one at a time. | Both the devices can send and receive the data simultaneously. |
Performance | The performance of half-duplex mode is better than the simplex mode. | The performance of full-duplex mode is better than the half-duplex mode. | The Full-duplex mode has better performance among simplex and half-duplex mode as it doubles the utilization of the capacity of the communication channel. |
Example | Examples of Simplex mode are radio, keyboard, and monitor. | Example of half-duplex is Walkie-Talkies. | Example of the Full-duplex mode is a telephone network. |
Key takeaway
Each communication channel has a direction associated with it, and transmission media provide the direction. Therefore, the transmission mode is also known as a directional mode.
Distributed Processing is a method of disseminating data over a number of devices, which could be computers or data terminals with some intelligence. The devices are linked by communication systems. A distributed system is one in which components on networked computers communicate and coordinate their operations solely through the transmission of messages.
Originally, traditional microprocessors had only one CPU on a single chip. Manufacturers realized that many processors could be combined on a single unit to speed up procedures as microprocessor engineering progressed. Many modern processors use a multi-core design, such as Intel's quad-core design, which uses four distinct processors to provide incredibly fast programme execution and logic processing.
Parallel processing, in which programmes are made to execute faster with several processors, is an approximate synonym for distributed processing. Hardware users can also tie many computers together to accomplish parallel processing with applications known as distributed processing software, thanks to the approach of putting more than one processor on a microprocessor chip.
Moore's law states that the number of transistors on an each integrated circuit (IC) doubles every two years, which is consistent with the distributed processing paradigm. Engineering tactics like distributed processing have added to the speed of logical devices enabling some astounding gains in the ability of computers to accomplish functional tasks, as this hypothesis has generally proven right over the last four decades.
Examples
● The internet
● An intranet which is a portion of the internet managed by an organization
Key takeaway
Distributed processing is a setup in which multiple individual central processing units (CPU) work on the same programs, functions or systems to provide more capability for a computer or other device.
A computer network must meet the following criteria:
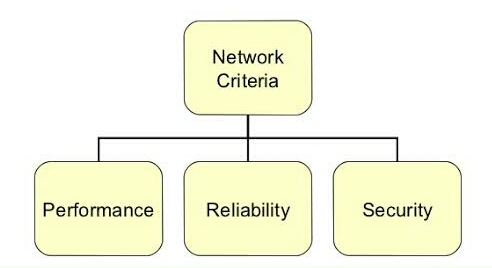
Fig 5: Network criteria
1. Performance – It's calculated in terms of transit and reaction times.
● The time it takes for a message to go from one device to another is known as transit time.
● The period between an enquiry and a response is known as response time.
The following elements influence performance:
● The number of users
● Type of transmission medium
● Capability of connected network
● Efficiency of software
2. Reliability – It's calculated in terms of
● Failure frequency.
● Failures can be overcome.
● Robustness in the face of a disaster.
Network dependability is assessed by the frequency of failure, the time it takes a link to recover from a failure, and the network's resiliency in a disaster, in addition to delivery accuracy.
"Catastrophe" - The network must be secured from disasters like fire, earthquakes, and theft.
3. Security – It entails preventing unwanted access to data.
● Protecting data from unauthorised access and viruses is one of the most important network security concerns.
● Protection can be done on a variety of levels. User identification numbers and passwords are at the most basic level. Encryption techniques are used at a higher level.
● Because a network can be accessed from a variety of locations, it is vulnerable to computer viruses.
There are several different forms of networking connections between two endpoints. One of the most popular examples is home networks and the Internet. Many different types of devices and approaches are used to bind to these types of network architectures.
Connecting computers to these types of networks necessitates the use of a networking system to do so. Point-to-Point Connection and Multipoint Connection are the two types of computer network connections discussed on this page.
Point-to-point connection:
A direct link between two devices, such as a computer and a printer, is known as a point-to-point connection. The devices are connected through a dedicated connection. The transmission between those two devices consumes the entire link's power. Modems and PSTN (Public Switched Telephone Network) communications are responsible for the majority of today's point-to-point connections. There are numerous links between individual pairs of machines in point-to-point networks.
A packet (short message) will take a variety of routes to get from point A to point B. PPP (Point-to-Point Protocol) is a data link protocol that is widely used in networking to create a direct connection between two networking nodes. It has the ability to authenticate connections, encrypt transmissions, and compress data. Serial cable, phone line, trunk line, cellular telephone, advanced radio communications, and fiber optic links such as SONET are all examples of physical networks where PPP is used. PPP is often used to link to the Internet.
Multipoint connection:
A multipoint connection is a connection that connects three or more devices together. Multi-drop configuration is another name for it. Broadcast Networks are networks that have a multipoint architecture.
A message or packet transmitted by any machine in a broadcast network is received by all other machines in the network. The address field in the packet determines the recipient. Any computer checks the packet's address field when it receives it. It processes the transmitted packet if it is for that specific machine; otherwise, it ignores it.
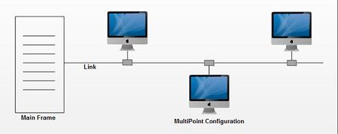
Fig 6: Multipoint connection
Key takeaway:
- A direct link between two devices, such as a computer and a printer, is known as a point-to-point connection.
- The devices are connected through a dedicated connection.
- A multipoint connection is a connection that connects three or more devices together.
Physical topology
Topology refers to the network's structure and how all of the elements are linked to one another. Physical and logical topology are the two forms of topology.
The geometric representation of all the nodes in a network is known as physical topology.
Bus topology:
The bus topology is set up in such a way that all of the stations are linked together by a single backbone cable. Each node is either connected to the backbone cable through a drop cable or is directly connected to it.
When a node wishes to send a message across the network, it does so by sending a message across the network. Regardless of whether the message has been answered, it will be received by all available stations in the network.
The bus topology is commonly used in regular networks such as 802.3 (ethernet) and 802.4 (wireless). In comparison to other topologies, the configuration of a bus topology is very straightforward. The backbone cable is thought of as a "single path" from which the message is sent to all of the stations.
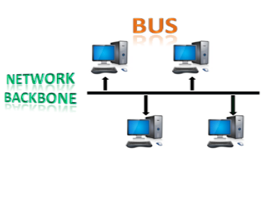
Fig 7: Bus topology
Advantages of Bus topology:
- Low-cost cable: In bus topology, nodes are directly connected to the cable without passing through a hub. Therefore, the initial cost of installation is low.
- Moderate data speeds: Coaxial or twisted pair cables are mainly used in bus-based networks that support upto 10 Mbps.
- Familiar technology: Bus topology is a familiar technology as the installation and troubleshooting techniques are well known, and hardware components are easily available.
- Limited failure: A failure in one node will not have any effect on other nodes.
Ring topology:
The topology of a ring is similar to that of a bus, but with connected ends. The node that receives the previous computer's message will retransmit to the next node. The data is unidirectional, meaning it only moves in one direction.
The data is continually flowed in a single loop, which is referred to as an infinite loop. It has no terminated ends, which means that each node is connected to the next and has no point of termination.
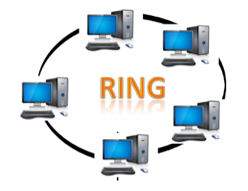
Fig 8: Ring topology
Advantages of Ring topology:
- Network Management: Faulty devices can be removed from the network without bringing the network down.
- Product availability: Many hardware and software tools for network operation and monitoring are available.
- Cost: Twisted pair cabling is inexpensive and easily available. Therefore, the installation cost is very low.
- Reliable: It is a more reliable network because the communication system is not dependent on the single host computer.
Star topology:
The star topology is a network configuration in which each node is connected to a central hub, switch, or device. The central computer is referred to as a server, and the peripheral devices connected to it as clients.
The computers are connected via coaxial cable or RJ-45 cables. In a physical star topology, hubs or switches are primarily used as connection devices. The star topology is the most widely used network topology.
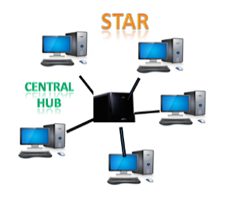
Fig 9: Star topology
Advantages of Star topology
- Efficient troubleshooting: Troubleshooting is quite efficient in a star topology as compared to bus topology. In a bus topology, the manager has to inspect the kilometers of cable. In a star topology, all the stations are connected to the centralized network. Therefore, the network administrator has to go to the single station to troubleshoot the problem.
- Network control: Complex network control features can be easily implemented in the star topology. Any changes made in the star topology are automatically accommodated.
- Limited failure: As each station is connected to the central hub with its own cable, therefore failure in one cable will not affect the entire network.
- Familiar technology: Star topology is a familiar technology as its tools are cost-effective.
- Easily expandable: It is easily expandable as new stations can be added to the open ports on the hub.
- Cost effective: Star topology networks are cost-effective as it uses inexpensive coaxial cable.
- High data speeds: It supports a bandwidth of approx 100Mbps. Ethernet 100BaseT is one of the most popular Star topology networks.
Tree topology:
Tree topology incorporates the advantages of both bus and star topologies. A tree topology is a system in which all computers are related to one another in a hierarchical manner.
A root node is the top-most node in a tree topology, and all other nodes are descendants of the root node. For data transmission, there is only one path between two nodes. As a result, it creates a parent-child hierarchy.
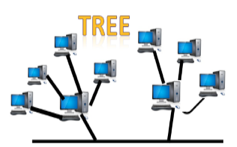
Fig 10: Tree topology
Advantages of Tree topology
- Support for broadband transmission: Tree topology is mainly used to provide broadband transmission, i.e., signals are sent over long distances without being attenuated.
- Easily expandable: We can add the new device to the existing network. Therefore, we can say that tree topology is easily expandable.
- Easily manageable: In tree topology, the whole network is divided into segments known as star networks which can be easily managed and maintained.
- Error detection: Error detection and error correction are very easy in a tree topology.
- Limited failure: The breakdown in one station does not affect the entire network.
- Point-to-point wiring: It has point-to-point wiring for individual segments.
Mesh topology:
Mesh technology is a network configuration in which computers are connected to one another through multiple redundant connections. There are many ways to get from one device to another. It is devoid of the turn, hub, or any central device that serves as a communication hub.
The mesh topology is exemplified by the Internet. Mesh topology is most commonly used in WAN deployments where communication failures are a major concern. Wireless networks commonly use the mesh topology.
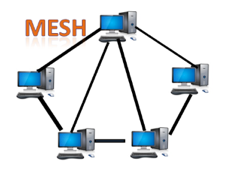
Fig 11: Mesh topology
Advantages of Mesh topology:
- Reliable: The mesh topology networks are very reliable as if any link breakdown will not affect the communication between connected computers.
- Fast Communication: Communication is very fast between the nodes.
- Easier Reconfiguration: Adding new devices would not disrupt the communication between other devices.
Hybrid topology:
Hybrid topology is the synthesis of many different topologies. A hybrid topology connects various links and nodes in order to transfer data. Hybrid topology is described as the combination of two or more different topologies, while similar topologies connecting to each other do not result in Hybrid topology.
For example, if a ring topology exists in one SBI bank branch and a bus topology exists in another SBI bank branch, connecting these two topologies would result in a Hybrid topology.
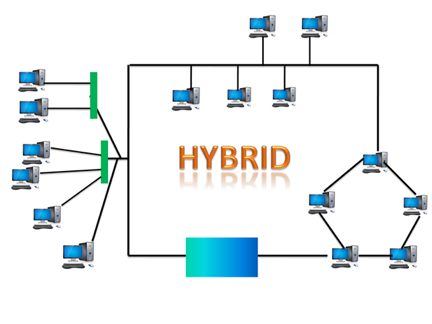
Fig 12: Hybrid topology
Advantages of Hybrid Topology
- Reliable: If a fault occurs in any part of the network will not affect the functioning of the rest of the network.
- Scalable: Size of the network can be easily expanded by adding new devices without affecting the functionality of the existing network.
- Flexible: This topology is very flexible as it can be designed according to the requirements of the organization.
- Effective: Hybrid topology is very effective as it can be designed in such a way that the strength of the network is maximized and weakness of the network is minimized.
Key takeaway:
- Topology refers to the network's structure and how all of the elements are linked to one another.
- The bus topology is set up in such a way that all of the stations are linked together by a single backbone cable.
- The star topology is a network configuration in which each node is connected to a central hub, switch, or device.
- A tree topology is a system in which all computers are related to one another in a hierarchical manner.
- A hybrid topology connects various links and nodes in order to transfer data.
A computer network is a set of computers linked together by a communication medium such as cable or wire.
The geographic area and number of computers that make up a network can be used to determine the scale of the network. It can range from a single computer in a single room to millions of devices distributed across the globe.
Based on their complexity, computer networks are divided into four categories:
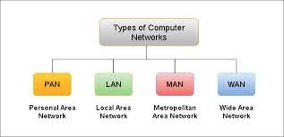
Fig 13: Types of network
PAN:
A personal area network (PAN) is a computer network that is formed around an individual. A computer, a cell phone, or a personal digital assistant are the most common components. PAN can be used to link these personal devices to a digital network and the internet by establishing contact between them.
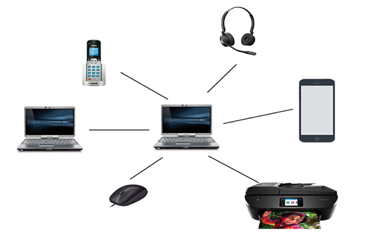
Fig 14: PAN
Characteristics
PAN's primary qualities are listed below:
● It is largely personal gadgets that are networked in a small region.
● Allows you to manage the interconnection of IT devices in a single user's environment.
● Mobile phones, tablets, and laptops are all included in PAN.
● WPAN allows it to connect to the internet wirelessly.
● Cordless mice, keyboards, and Bluetooth systems are examples of PAN appliances.
Advantages
The following are some of the major advantages and benefits of the PAN network:
● PAN networks are considered to be relatively safe and secure.
● It only provides a ten-meter short-range solution.
● Only a tiny space is available.
Disadvantages
The following are the disadvantages of using the PAN network:
● It's possible that it'll make a shaky connection to other networks using the same radio channels.
● There are some distance restrictions.
LAN:
A Local Area Network (LAN) is a set of computers and peripheral devices linked in a small area, such as a classroom, laboratory, home, or office building. It's a popular network for sharing resources such as files, printers, games, and other software. Connecting computers and a printer in someone's home or office is the most basic form of LAN network. LAN will be used as one form of transmission medium in general.
It's a network of less than 5000 interconnected devices spread over several buildings.
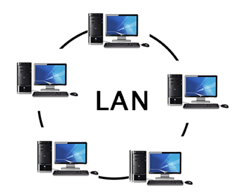
Fig 15: LAN
Characteristics
The following are some of the most important aspects of a LAN network:
● Because it is a private network, it is never regulated by a third party.
● When compared to other WAN technologies, LAN runs at a faster rate.
● Token ring and ethernet are two examples of media access control technologies.
Advantages
The following are the advantages and disadvantages of LAN:
● Local area networks can share computer resources such as hard discs, DVD-ROMs, and printers. This lowers the cost of hardware purchases greatly.
● Instead than acquiring licenced software for each client in the network, you can utilise the same software across the network.
● All network users' data can be saved on the server computer's single hard disc.
● Data and messages can be easily transferred across networked computers.
● It will be simple to handle data in a single location, making data more secure.
● The ability to share a single internet connection among all LAN users is provided by a local area network.
Disadvantages
The following are some of the disadvantages of LAN:
● Because of shared computer resources, LANs will save money, but the initial cost of setting up a LAN is fairly significant.
● Because the LAN administrator has access to every LAN user's personal data files, it does not provide adequate privacy.
● Unauthorized users can gain access to an organization's essential data if the LAN administrator fails to secure the centralised data repository.
● Because there are issues with software setup and hardware failures, a constant LAN administration is required.
MAN:
A Metropolitan Area Network, or MAN, is a computer network that spans a city, a college campus, or a small area. This network is far larger than a LAN, which is usually restricted to a single building or location. This form of network can cover a range of distances from a few miles to tens of miles, depending on the configuration.
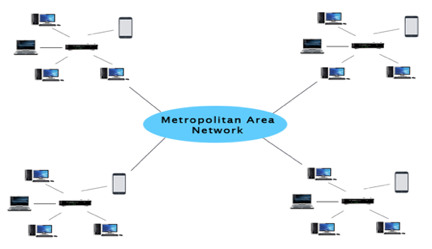
Fig 16: MAN
Characteristics
The following are some of the most important aspects of a LAN network:
● Because it is a private network, it is never regulated by a third party.
● When compared to other WAN technologies, LAN runs at a faster rate.
● Token ring and ethernet are two examples of media access control technologies.
Advantages
The following are the advantages and disadvantages of the MAN network:
● It provides high-speed communication over high-speed carriers such as fibre optic cables.
● It offers good support for a large network and increased WAN connectivity.
● The MAN network's dual bus allows data to be transmitted in both directions at the same time.
● A MAN network usually covers a portion of a city or the entire city.
Disadvantages
The following are some disadvantages and disadvantages of using the MAN network:
● To construct a MAN connection from one location to another, you'll need more cable.
● It's difficult to keep a MAN network secure from hackers.
WAN:
Another significant computer network that spans a vast geographical area is the WAN (Wide Area Network). A WAN network system may be a LAN link that uses telephone lines and radio waves to connect to other LANs. It is usually restricted to a single company or organization.
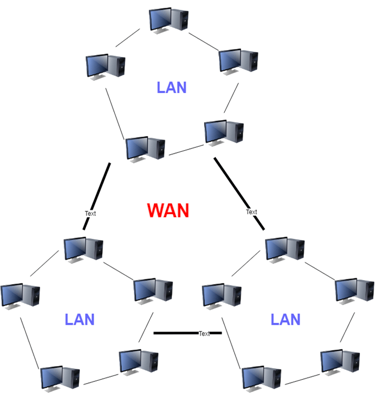
Fig 17: WAN
Characteristics
The following are some of the properties of WAN:
● The software files will be shared among all users, ensuring that everyone has access to the most recent versions.
● WAN can be used by any firm to create a global integrated network.
Advantages
The following are the advantages and disadvantages of WAN:
● The Wide Area Network (WAN) allows you to cover a broader geographical area. As a result, corporate offices located at a greater distance can connect effortlessly.
● Mobile phones, laptops, tablets, desktops, game consoles, and other electronic gadgets are included.
● The radio transmitters and receivers embedded into client devices are used to establish WLAN connections.
Disadvantages
The following are the disadvantages and disadvantages of a WAN network:
● The initial investment setup cost is really significant.
● The WAN network is difficult to maintain. You'll need technicians and network administrators who are well-versed in their fields.
● Because of the vast coverage and use of many technologies, there are more faults and issues.
● Because many wired and wireless technologies are involved, it takes longer to fix issues.
● When compared to other forms of computer networks, it provides less protection.
Key takeaway:
- A computer network is a set of computers linked together by a communication medium such as cable or wire.
- A personal area network is a computer network that is formed around an individual.
- A LAN is a set of computers and peripheral devices linked in a small area, such as a classroom, laboratory, home, or office building.
- A MAN, is a computer network that spans a city, a college campus, or a small area.
- A WAN network system may be a LAN link that uses telephone lines and radio waves to connect to other LANs.
It is an interconnected computer network system that spans the globe. It makes use of the TCP/IP protocol, which is widely used on the internet. A unique IP address is assigned to every machine on the Internet. An IP Address (for example, 110.22.33.114) is a series of integers that identify the location of a computer.
A DNS (Domain Name Server) computer is used to give an IP Address a name so that a user can find a computer by name.
ARPANET was expanded to connect the Department of Defense with US colleges conducting defense-related research. It included most of the country's major universities. When University College London (UK) and Royal Radar Network (Norway) joined the ARPANET and formed a network of networks, the concept of networking received a boost.
Stanford University's Vinton Cerf, Yogen Dalal, and Carl Sunshine invented the name "internet" to characterize this network of networks. They also collaborated on protocols to make information sharing via the Internet easier. The Transmission Control Protocol (TCP) is still the networking's backbone.
In the 1960s, the Internet was created as a means for government researchers to communicate information. In the 1960s, computers were enormous and stationary, and in order to access information stored on them, one had to either travel to the computer's location or have magnetic computer tapes transported through the mail system.
The escalation of the Cold War was another factor in the development of the Internet. The launch of the Sputnik satellite by the Soviet Union prompted the United States Defense Department to examine how information may be distributed even after a nuclear attack. This eventually led to the creation of the ARPANET (Advanced Research Projects Agency Network), which eventually evolved into the Internet we know today. ARPANET was a huge success, but it was only open to a few academic and research institutions with Defense Department contracts. As a result, new networks were formed to facilitate information sharing.
The Internet celebrates its formal birthday on January 1, 1983. Prior to this, there was no standard means for computer networks to communicate with one another. Transfer Control Protocol/Internetwork Protocol (TCP/IP) was created as a new communication protocol.
This allowed various types of computers on various networks to "speak" to one another. On January 1, 1983, ARPANET and the Defense Data Network switched to the TCP/IP standard, resulting in the birth of the Internet. A universal language could now connect all networks.
Key takeaway
In the 1960s, the Internet was created as a means for government researchers to communicate information.
In the 1960s, computers were enormous and stationary, and in order to access information stored on them, one had to either travel to the computer's location or have magnetic computer tapes transported through the mail system.
The Internet today comprises hundreds of thousands of local area networks (LANs) worldwide, interconnected by a backbone wide area network (WAN). LANs commonly operate at speeds ranging from 10 to 100 megabits per second. WAN networks supported lower bit rates until 1995, but the enormous rise in traffic paired with the cheaper cost of optical communications has raised backbone link rates to as high as 10 Gbps. Some network service providers use IP routers connected by ATM switched networks to deal with these high link speeds.
When compared to LAN speeds, corporate data networks often have a substantially slower connection to the Internet backbone. Because LANs provide high-bandwidth traffic between workstations and file servers within a single business, this is appropriate. The WAN, on the other hand, can handle electronic mail and rare file transfers across slow connections. In 1995, 40,000 students, instructors, and staff at the University of California, Berkeley used 20,000 workstations and PCs to access the Internet.
These computers were connected by 10-Mbps Ethernets and 100-Mbps FDDI rings on the university campus. Two 1.5-Mbps lines carried Internet traffic between the university and the rest of the globe, with a 30 percent utilization rate. The telephone links between the campus and the rest of the globe, on the other hand, have a capacity of 200 Mbps.
Users can use one of two methods to access the Internet. The user's PC or workstation is connected to a LAN that is connected to the Internet within a major enterprise, government organization, or university. ISPs are used by users at home and in small businesses. Subscribers link their PCs to ISP hosts using low-speed modems, which then provide Internet access. Some consumers are switching to cable TV or ADSL for faster access.
We look at some of the various variables that have contributed to the Internet's phenomenal success, which had connected 300 million people worldwide by 1999, when it was just 25 years old. The incremental cost of Internet access for users connected to LANs is a small fraction of the cost of the LANs. The network externalities of services like e-mail, Web access, and the establishment of special interest groups, along with the minimal extra cost, resulted in exponential expansion. Second, an increasing number of individuals possess PCs, and newer PCs include networking hardware, such as a built-in modem, as well as software. The cost of Internet access for these consumers is solely determined by their ISP provider's fees.
Protocol
A procedure is essentially the same as a rule. Communication takes place between entities in different systems in computer networks. Anything that can transmit or receive data is considered an entity. Any two entities can't just transmit each other bitstreams and expect to be understood.
In order for the communication to occur, the entities must agree on a protocol.
A protocol is a set of rules that control the transmission of data. What is communicated, how it is communicated, and when it is communicated are all defined by the protocol.
Key elements of a Protocol
The following are the essential components of a protocol:
● Syntax - This phrase mostly refers to the data's structure or format, which essentially refers to the order in which information is displayed. A simple protocol, for example, would anticipate the first 8 bits of data to be the sender's address, the second 8 bits to be the receiver's address, and the rest of the stream to be the message itself.
● Semantics - The meaning of each section of bits is referred to by this phrase. How is a specific pattern should be read, and what action should be made based on that interpretation? Does an address, for example, indicate the route to be traveled or the final destination of the vehicle?
● Timing - This word primarily refers to two aspects: when data should be transmitted and how quickly data can be sent. If a sender sends data at 100 Mbps but the receiver can only handle data at 1 Mbps, the transmission will overload the receiver and some data will be lost.
Standards
Standards are necessary for building and maintaining an open and creative market for equipment manufacturers, as well as ensuring national and international data, telecommunication technology, and process interoperability.
Standards are primarily utilised to offer rules to manufacturers, vendors, government organizations, and other service providers in order to assure the interconnectivity required in today's marketplace and worldwide communications.
There are two types of data communication standards:-
● de facto (which means "by fact"/ "by convention") - Those standards have been adopted as standards despite the fact that they were not approved by an organized body. These kinds of standards are frequently produced by producers who are just trying to outline the functionality of a new product or technology.
● de jure (which means "by law" /"by regulation") - Standards that have been enacted by an officially recognised organization are known as de jure standards.
Standard Organizations
The majority of standards are established through collaboration between standard-setting groups, government regulatory agencies, and forums.
Some Standard Creation committees are:
● International Organization of Standardization(ISO)
● American National Standards Institute(ANSI)
● Electronic Industries Association(EIA)
● Institute of Electrical and Electronics Engineers(IEEE)
OSI stands for Open System Interconnection is a reference model that describes how information from a software application in one computer moves through a physical medium to the software application in another computer’s consists of seven layers, and each layer performs a particular network function’s model was developed by the International Organization for Standardization (ISO) in 1984, and it is now considered as an architectural model for the inter-computer communications.
The OSI model divides the whole task into seven smaller and manageable tasks. Each layer is assigned a particular task. Each layer is self-contained, so that tasks assigned to each layer can be performed independently.
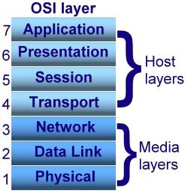
Fig 18: OSI model
The OSI model is divided into two layers: upper layers and lower layers. The upper layer of the OSI model mainly deals with the application related issues, and they are implemented only in the software. The application layer is closest to the end user. Both the end user and the application layer interact with the software applications. An upper layer refers to the layer just above another layer. The lower layer of the OSI model deals with the data transport issues.
The data link layer and the physical layer are implemented in hardware and software. The physical layer is the lowest layer of the OSI model and is closest to the physical medium. The physical layer is mainly responsible for placing the information on the physical medium. There are seven OSI layers.
Each layer has different functions. A list of seven layers are given below:
- Physical Layer: The physical layer is the lowest layer in the OSI reference model. It is in charge of establishing a physical link between the devices. Bits of information are stored in the physical layer. It is in charge of sending individual bits from one node to another. As this layer receives data, it converts the signal received into 0s and 1s and sends them to the Data Link layer, which reassembles the frame.
- Data-Link Layer: The data link layer is in charge of message transmission from node to node. The main purpose of this layer is to ensure that data transfers from one node to another over the physical layer are error-free. It is DLL's duty to send a packet to the Host using its MAC address when it arrives in a network.
- Network Layer: The network layer is responsible for data transmission between hosts on different networks. It also handles packet routing, which is the selection of the shortest path to transmit a packet from a large number of options. The network layer places the IP addresses of the sender and receiver in the header.
- Transport Layer: The application layer receives services from the transport layer, and the network layer receives services from the transport layer. Segments are the units of data in the transport layer. It is in charge of the full message's delivery from beginning to end.
- Session Layer: This layer is in charge of establishing connections, maintaining sessions, authenticating users, and ensuring security.
- Presentation Layer: The Translation layer is also known as the Presentation layer. The data from the application layer is extracted and manipulated here so that it can be transmitted over the network in the appropriate format.
- Application Layer: The Application layer, which is implemented by network applications, is at the very top of the OSI Reference Model stack of layers. These applications generate the data that must be sent over the network. This layer also acts as a window for application services to connect to the network and present the information they receive to the user.
Key takeaway:
- In the present day scenario security of the system is the sole priority of any organization.
- The main aim of any organization is to protect their data from attackers.
TCP/IP Reference Model is a four-layered suite of communication protocols. It was developed by the DoD (Department of Defense) in the 1960s. It is named after the two main protocols that are used in the model, namely, TCP and IP. TCP stands for Transmission Control Protocol and IP stands for Internet Protocol.
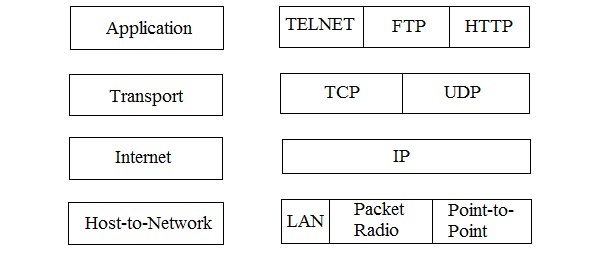
Fig 19: TCP/IP protocol suit
The four layers in the TCP/IP protocol suite are −
Host-to- Network Layer −It is the lowest layer that is concerned with the physical transmission of data. TCP/IP does not specifically define any protocol here but supports all the standard protocols.
Internet Layer −It defines the protocols for logical transmission of data over the network. The main protocol in this layer is Internet Protocol (IP) and it is supported by the protocols ICMP, IGMP, RARP, and ARP.
Transport Layer − It is responsible for error-free end-to-end delivery of data. The protocols defined here are Transmission Control Protocol (TCP) and User Datagram Protocol (UDP).
Application Layer − This is the topmost layer and defines the interface of host programs with the transport layer services. This layer includes all high-level protocols like Telnet, DNS, HTTP, FTP, SMTP, etc.
The advantages of TCP/IP protocol suite are
- It is an industry–standard model that can be effectively deployed in practical networking problems. It is interoperable, i.e., it allows cross-platform communications among heterogeneous networks.
- It is an open protocol suite. It is not owned by any particular institute and so can be used by any individual or organization.
- It is a scalable, client-server architecture. This allows networks to be added without disrupting the current services.
- It assigns an IP address to each computer on the network, thus making each device to be identifiable over the network. It assigns each site a domain name. It provides name and address resolution services.
The disadvantages of the TCP/IP model are
- It is not generic in nature. So, it fails to represent any protocol stack other than the TCP/IP suite. For example, it cannot describe the Bluetooth connection. It does not clearly separate the concepts of services, interfaces, and protocols. So, it is not suitable to describe new technologies in new networks.
- It does not distinguish between the data link and the physical layers, which have very different functionalities. The data link layer should concern with the transmission of frames. On the other hand, the physical layer should lay down the physical characteristics of transmission. A proper model should segregate the two layers.
- It was originally designed and implemented for wide area networks. It is not optimized for small networks like LAN (local area network) and PAN (personal area network). Among its suite of protocols, TCP and IP were carefully designed and well implemented. Some of the other protocols were developed ad hoc and so proved to be unsuitable in the long run. However, due to the popularity of the model, these protocols are being used even 30–40 years after their introduction.
Key takeaway:
- TCP/IP Reference Model is a four-layered suite of communication protocols.
- It is named after the two main protocols that are used in the model, namely, TCP and IP.
- TCP stands for Transmission Control Protocol and IP stands for Internet Protocol.
Difference between OSI and TCP/IP Model
OSI Model | TCP/IP |
It stands for Open System Interconnection. | It stands for Transmission Control Protocol. |
The transport layer offers a guarantee for packet delivery in the OSI model.
| The distribution of packets is not guaranteed by the transport layer. Nonetheless, we may assume that it is a trustworthy model. |
The vertical method is used in this model. | The horizontal method is used in this model. |
It consists of 7 layers. | It consists of 4 layers. |
The OSI model was created by ISO (International Standard Organization). | ARPANET was the company that produced it (Advanced Research Project Agency Network). |
The network layer in this model offers both connection-oriented and connectionless services. | Only connectionless services are provided by the network layer.
|
This model isn't seen very much. | This model is quite popular. |
It allows devices such as routers, motherboards, switches, and other hardware to be standardized. | It does not provide devices with standardization. It allows computers to communicate with one another. |
References:
- Forouzan, "Data Communication and Networking", TMH
- A.S. Tanenbaum, Computer Networks, Pearson Education
- W. Stallings, Data and Computer Communication, Macmillan Press
- Bhavneet Sidhu, An Integrated approach to Computer Networks, Khanna Publishing House