Unit 5
Auditing Of Computerized Systems
Table of Contents
Sr No | Particulars |
5.1 | Introduction |
5.2 | Fundamentals Shifting From Traditional Audit System To Computerized System Audit |
5.3 | Recent Development In Audit System |
5.4 | Approaches Of Audit In Computerized Environment |
| - Auditing Around The Computer |
- Auditing Through The Computer | |
- Auditing With The Computer | |
- Application Controls | |
- Computer Assisted Auditing Techniques (Caat’s) | |
- TYPES OF Caats | |
ICAI’S GUIDANCE NOTES ON IMPORTANCE OF Caats | |
5.5 | Disparity Between The Approaches |
5.6 | Summary |
The crest of digitalization in the world has made everyone to be techno savvy. None of the organization will exist without accepting incredible enlargement and enhancement in IT sector. Every private and public entity has to adopt it to remain sustain in the global market. Studies have shown that the incorporation of digitalization has solutions for many issues in day to day life of an organization. As IT systems substitute the long standing manual accounting and auditing processes. Computerized system overcame the drawback of manual system. The implementation of computer is an essential to a certain level of assurance in working pattern of entities. IT provides inherent advantages of technology along with the new vulnerabilities in accounting and auditing system. It may be a bunch of challenges for non IT user. As IT field is unique of the greatest rapid changing system than others. Auditor needs to modernize by periodic revisions and supplements in turn with the emerging trends. Hence, before the auditor commence audit, it is important that auditor must have a meticulous understanding of CIS environment in bank. Without proper understanding of the functioning of each items or software, auditor would not be in position to complete the task effectively and efficiently. The auditor must have adequate knowledge and expertise of accounting and audit software. One should expect to understand software system adopted by the bank. Auditor needs to consider the following tasks during audit process.
- Sufficient understanding of the CIS environment
- Accounting system adopted by bank
- Effect of CIS environment on bank audit
- Audit Trails followed under system
- Controlling system
- Test used to evaluate the ICS
From the above discussion, it is understood that auditor should have enough information of CIS environment and audit approaches available. Hence, the researcher has put an attempt to highlights the type of CIS audit approaches, their shortcomings and its impact on audit. This topic deals with objectives of the study number 2 and problem of the study number 2.
Electronic data processing is the processing of data or transaction by a computer and its programs in an electronic communication environment. EDP system is used in an audit process by an organization instant of manual audit.
EDP audit or Audit under Computerized Information System environment means an examination of system efficiency, system effectiveness and safeguard of assets of an organization.
Chart no: EDP audit system
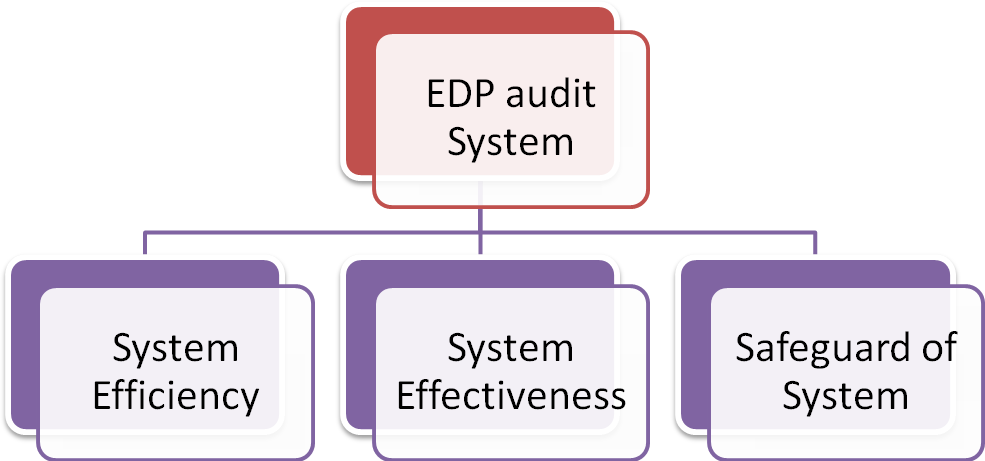
It helps in smooth functioning of audit process. Most of the works of auditor related to manual system get reduce. The auditor would be able to focus on the excellence of audit. The auditor needs to take precaution in terms of following aspects:
- Ensure that data and programmed are properly protected
- Check whether accurate security exists in the system
- Ascertain whether the processing of the data is proper
- Ensure that proper design of IT controls is maintained
- Ensure that proper allocation of obligations and errands of the software engineers
The implementation of CIS provides concurrent access to users due to shared sever system. It helps to increase the speed of audit process, efficiently and accurately generate report as per need of the management. As the digitalized process is created and implemented. It helps in reducing the costs of managing data by an extremely great amount. Due to this reduction in labor also takes place due to which efforts and duplications are also reduced.
The above description shows that CIS environment provides numerous benefits. This attribute is depends on the scope of audit process such as high speed of CIS audit process, Prevention of clerical error and concentration of duties in the arrows of specialized personnel.
The transformation from traditional or manual audit process to computerized system brings many changes or transformation in areas of audit process, mind-set of accounting and auditing staff an organization. This phase is based on certain aspect such as internal control system, application of software, use of technology etc.
The change in audit approach of computerized accounts as compared to audit of manual accounts is causes of difference between Conventional Accounting System and Computerized Accounting System. Following is the disparity between conventional accounting system and Computerized Accounting System.
Table: Disparity between Conventional Accounting System and Computerized Accounting System
Sr. No. | Particulars | Conventional Accounting System | Computerized Accounting System |
1 | Input documents | Transactions are recorded from source or input documents example bills, invoices, Receipts and voucher etc. | Data is entered “live” in an online system during transaction taken place. Hence no input documents are used. |
2 | Design/ Time Required | Easy to design and less time consuming. | Difficult to design hence it requires more time. |
3 | Effect on organization structure | Accounting and book-keeping functions are centralized in the finance department. | The activities and responsibilities may be centralized in the EDP department, unless all departments are fully computerized and linked by network e.g. (LAN). |
4 | Complexity | Less complex relationship between sub- Systems example: purchases, stores and production etc. | More complex and high degree of inter- Relationships between different sub- systems. |
5 | Reliability | Possibility of collusion in order to override the system cannot be discounted. Hence Less reliable. | Due to effectiveness of controls, it is considered more reliable. |
6 | Audit trail | Fully visible- all ends of the transactions can be neatly and clearly traced. | Due to deficit of input documents and storage of information inside the System, audit trail is less visible. |
It shows that both the system has pros and corns but demand of digitalization and several factors enforced an organization to adopt Computerized Audit System
There is no change until and unless it is in great demand. The requisite of such changes is based on needs of an entity. As in today’s generation everyone seems to be modernized with demand of the era which is based on certain parameters. If they do not, it may affect their position in the global market. Similarly, with the development or growth of business, expansion and diversification demands to transform from one aspect to another. There are numerous reasons for the transformation from manual to computerize one. The research has enlightened the following major causes of shifting from Traditional Audit System to Computerized Audit System.
- Application System development control
- System software control
- Disappearance of manual reasonableness.
- Impact of poor system
- Exception reporting
- Human- Machine interface
1. Application System Development Control:
Application system used in audit process should be develop and designed to provide rational assurance regarding authorisation and effectiveness of system. The developmental stage is dangerous if proper care has not taken. It is difficult to allocate the errors or frauds at during the installation.
The following aspects need to be considered:
- Testing, conversion, implementation and documentation of new revised system
- Changes to application system
- Admittance to system documentation
- Hire or acquisition of system
2. System Software Control:
System software control is based on assurance regarding development of software system. It is authorized and efficient. It is followed by endorsement, challenging, accomplishment and certification of new scheme software. This system control, maintain, restriction of access to system software with proper documentation by authorized personnel.
3. Disappearance of Manual Reasonableness:
The demand of manual system is vanishing day by day due to quick and essay availability of accounting and auditing process. The detailed analysis of physical system for renovation into a rational podium is possible with the transformation from traditional to computerised environment.
4. Exception Reporting:
Audit report severs the purpose of stakeholders. The types of audit report differ from each stakeholder requirement or demand. It is difficult to get report as per the demand of stakeholder timely and accurately. Such reports can be generated with electronic system. In the software system Management Information System (MIS) plays an important role. MIS can serve the purpose of stakeholders. MIS provides accuracy of data which is equally important. The expected report can be transform from one end to another which is difficult in conventional system.
5. Man- Machine Interface:
As both the method have two sides of coins, positive as well as negative. The application of traditional system is acceptable to certain extent. Beyond which none of the system work out in a better way. The interface of both the systems based on proposal, assessment and application of communicating computing system for wellbeing of human use. Hence, sense it is “no man without a machine and no machine without a man.” The researcher conclude with modern system is user centric cannot achieve purpose of audit in term of man machine interface.
With the above study it is acceptable to transform the manual audit system to computerized system in order to fulfill the demand of an entity. There are many studies focused on the implication of CIS environment in digitalized world. LPG is solitary important reasons for extensive demand of technology. It is mandatory for each sector to adopt it, otherwise they may fail to face the challenges in the competitive world. Hence an auditor should have sufficient knowledge about the recent changes and development in terms of technology. Auditor should be aware about speedy changes in IT sector.
It has been experienced by every one of us that Information Technology is upgrading tremendously. At the single stroke of time moment new innovation and invention has been noticed in every sector respective of nature of business. In such glory atmosphere of IT an auditor should be aware of upcoming trends in IT sectors. An auditor has to observe that every single changes in this felid leads to several changes in the auditing. It may affect the prime intention of audit. The rapid growth in IT field may create obstacles to an auditor. Due to deficiency of competency, knowledge, information, improper judgement the auditor cannot able to accomplish the task as per the provision or norms. An auditor may face several issues in their way. Therefore it’s commitment of an auditor to consider the recent changes and developments in digital era.
CA. Vikas Oswal has focused on some the recent changes in the modern era. Such alteration or up gradate has to be occupied into contemplation by the auditor before executing his duties.
The following are the recent changes in field of CIS audit process.
- End user computing
- Diminishing Hardware cost, boost in micro user
- Extensive use of Relational Data Base Management (RDBM)
- System development and Computer Aided Software Engineering (CASE) equipment accepted by numerous users
- Shift form DOS to UNIX and C language
- Acquaintance grounded and verdict sustenance system
- Augmented data communication and schmoosing
- Use of EDI (Electronic Data Interchange)
- Scanners and speech recognition system for involvement
The knowledge of recent development or growth in the audit process will help the auditor. Before commence of audit, the auditor will consideration all the changes and accordingly an auditor will prepare his plan, select methods and perform.
The selection of approaches is set up on the nature, size and system followed by an entity. The entity must clearly inform about the software system adopted by them. This will help the audit team in several ways.
The audit team must keep into consideration that the computerization of accounting does not change the basic aim and scope of auditing. It expresses the same opinion of The True and Fair view as in traditional audit process. However, the computerization has brought many changes in an organization, audit procedures and controlling system. This change in computerized environment requires certain modifications in conventional testing of compliance test and substantive test.
The auditors should program their audit functions to appraisal of core rheostat and examination of records generated by the system. The auditors should perform their duties connected with compliance and substantive test by using various tools and techniques to arrive on conclusion. Auditor has to study the audit risk and internal control system in the entity. The auditor view ensures the accuracy, validity and completeness of data. Accomplishment of such view they have to follow specified approaches. The auditor followed the approach as per their knowledge and expertise in handing computerized data.
Following are the types of audit approaches in computerized environment:
Auditing Around the Computer
Auditing Through the Computer
Auditing with the Computer
Auditing Around the Computer
Auditing around the Computer is oldest method of audit under CIS environment. It is also known as Black – Box approach. In this approach auditor more or less ignores the fact of use of computers for processing of information while determining the nature, timing and extent of the substantive procedures. The auditors mainly concentrate on input - output and ignore the specifics of how computer process the data or transactions. Accordingly the auditor matches the input with output. On the foundation of result obtained, it is assumes that the processing of transaction must be correct. It is similar to a manual system.
Under this method the preference has been given to basis documentation is processed correctly and the auditor verifies this with the output. The software system of the computer is not documented or audited.
In testing Payroll Application the auditor might first examine selected time cards for hours worked and employee earning cards for rates and then trace these to the payroll summary production and lastly associate eras, degree and extensions. The contrast of inputs and outputs may be done physically or with the aid of computer. The auditor is, therefore relying on the controls in user department.
After taking into consideration of the above discussion the researcher has listed the positive and negative aspect of this approach.
The following is positive features i.e. assistance of Auditing Around the Computer:
- Less audit cost:
As this method is just like the manual audit system hence around is no requirement of high level of competency in IT. As audit process is done manually hence no need to update or develop system software.
b. Limited computer knowledge:
Due to excess dependence on traditional trails there is less or basic use of computer. The basic task can be done by the person having basic knowledge of computer.
c. Effortlessness of comprehension as a tracing of documents:
Unlike computerized system transaction may automatically get transfer to several files as per the programmed set, in manual system every transaction gets recorded step by step and supported by vouchers. There is negligible use of computer. Hence it is easy to trace the documents.
d. No demand of in- depth study of application program:
As manual process follow a specify process of recording and execution of accounting and auditing. There is no concept of development of application programmed due to basic use of computer.
e. Suitable to small scale:
Small scale entity may have less transaction which can be manage with mostly manual system hence for this kind of organization Auditing around the computer is suitable.
Auditing around the computer is initial approach which may be used by every organization silently. But for the long run and large business unit it may not be possible. It has some drawback also which curb the organization not to use.
Such hindrances are as follows:
a. Expensive due printed data requirements:
In Semi manual system, auditor works manual in relation to computerized data. Auditors are more concern about the input and output. They may require both for verifying which add the cost to this approach as compared to traditional system.
b. Time consuming:
Excess depends on human being may spent more time in several audit task and process.
c. Ignorance of huge potential of computers to help the auditor:
Due to lack of knowledge or competency skills the auditor might not able to comprehend the potential of computers in terms of use, application and control.
d. No direct control:
Unlike other method, Auditing Around the Computer do not have complete control in the auditing. The rotation of staff may affect the accuracy and accountability. The system can be access by any one due lack of system control.
e. No ascertains about the underlying process:
This approach is based on technology cum manual. Mainly everything done manually, only for few aspects computer is used. Hence it is complicated to depict audit process.
With the above observation it is understand that Auditing Around the Computer can be applicable only to small scale business unit but by considering the loophole in it. This system may affect severely due to risk available. Before applying or using this approach the auditor should analysis the risk factor involvement. Most of author had focused on the factor responsible for audit risk such as:
- No testing of software system
- No audit generated evidence that the programs are working as documented
- Impossibility to determine the causes of errors
In order to overcome with several issues auditor should have proper information about the potential of technology. Auditor should prepare blueprint about what, how, when, where, whom. This will create console to conduct the audit. One should take precaution in assist of work and collection of evidences.
Applicable:
This approach is suitable when the application controls are difficult to comprehend. The auditor can test the computer processes by feeding hypothetical data in the computer for which manual solution is available. Comparison of such a solution can be made with computer generated output and if no material discrepancies are noted, the auditor can use this approach.
With the emergence of IT sector and to overcome the issues prevailing in system Auditing Around the Computer the other approach used by many organisation is Auditing through the Computer. Researcher has tries to give justified reflection based on available resources.
Auditing Through the Computer
Auditing through the Computer is moving from batch processing to on-line transaction process. It is budge from mainframe-mini system to LAN, WAN etc. This system has converted the office in to paperless office. Its contain most of data in electronic form which has made to change the audit gears and methods in the audit process.
Auditing through the Computer includes auditor investigates the system of data processing, and if the scheme is acceptably measured, the auditor follows the system and infer that the information processed by the system is accurate.
Under this approach, use of computer is as “live” and “dynamic devices”, which add value to process of auditing. It is treated as the target of auditing. In the nonstop changing sector audit through computer is essential. It has shown in several studies that the application of different approaches is depend on the necessity of an entity.
Some of the key aspect is as follows for the selection of this method such as:
- On-Line data entry
- Elimination or reduction of printouts
- Real time files updating
a. On-line data entry:
On-line data entry is an essential tasks performed through the computer. Under this system all the data able to be access on-line due to availability storage in computer. Unlike manual system the duplication of work can be reducing. It helps to reduce backlogs and duplication of work.
b. Elimination or reduction of printouts:
This system eliminate the hardcopy of output requires for several purpose. Again this one of positive aspect for Auditing through the Computer. Most of the analysis or report generation can be done in system only with the command.
c. Real time files updating
On-line input of data and auto generation of report and analysis helps to completed task on time. As compare to Auditing Around the Computer, Auditing Through the Computer is faster and accurate. This approach is consists of both the procedures compliance as well as substantive. Both the procedures are the indicator of Auditing Through the Computer. This approach gives importance to all the phases of CIS activities.
The phases under CIS Environment are as follows:
 Chart: The Phases under CIS Environment
Chart: The Phases under CIS Environment
Auditing through the computer is also known as the White Box approach. The processes and controls applied in audit environment are subject to audit, processing controls in operating and investigating system. In edict to style this process easy Computer Audit Software may be used by auditor.
Audit Software package may include of the following aspects:
- Interactive enquiry facilities to cross-examine files.
- It helps to analyze computer security logs for extraordinary usage of the computer.
- It has ability to compare sources and compile program codes in order to locate dissimilarities.
- It facilitates to execute and scrutinize computer treatment of “live transaction” by moving through the processing as it occurs.
- It helps in generation of test data.
- It helps in actual and higher level control. It leads to evaluate the compliance testing and substantive testing before an audit report is produced. Such generation of aids shows the logs of application programs.
Auditing through the Computer is addition to Auditing Around the Computer. In order to execute audit systematic and accurately, auditor must re-examine the other aspect of CIS system also. Following are the major aspect under this system which auditor needs to review and test before commencing the audit.
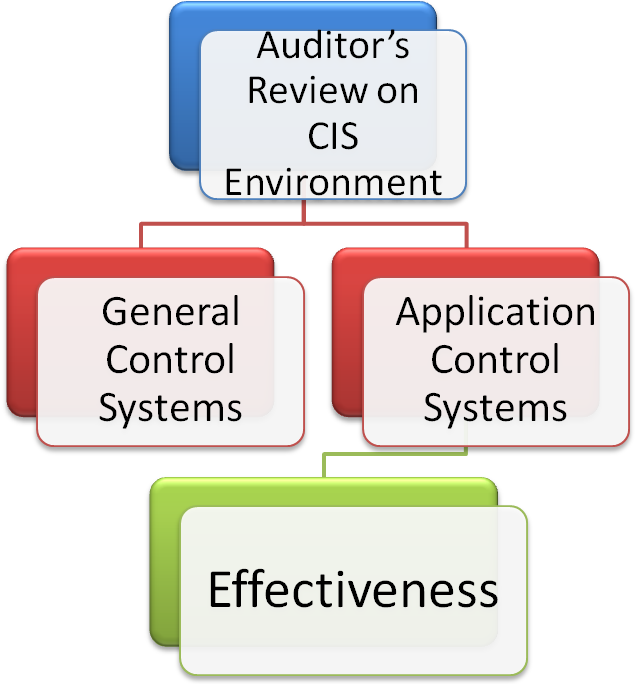 Chart: Auditor’s reflection on CIS Environment
Chart: Auditor’s reflection on CIS Environment
This will help auditor to analysis the system. It helps to estimate the level of effectiveness in software system. On the basis of it auditor can draft the audit planning and procedures.
Along with review of system control, auditor must be able to comprehend the level of organizational structure. This will help auditor to take defensive measure for the smooth execution of audit process. The five indispensable controls in audit process are as follow:

Chart: The Five essential control under audit process:
- Input control replicate that every data is accurate and authorised by concerned department.
2. Processing Control imitate that the dispensation of facts is carried by responsible personnel under the control of department.
3. Storage control reflects that the software should have proper coding storage facilities. It should not modify by anyone else and available for use as when as needed.
4. Output control ensures that no modification or addition without informing the authority and data provided to auditor should not altered till the task get over.
5. Data transmission control that information forwarded or transferred to other system should not be edited. Protected coding should be kept secretly.
The above controls are vital for auditor to give their opinions on the financial statement of bank. The major controls may affect the True and Fair View status of financial statement. Hence, the rational precaution would helps auditor to maintain control in audit process. The adequate controls over deterrence of unofficial entrance to computer and computerised database would help in audit process.
Following is the preventive measure undertaken by auditor to control organisational structure:
- Auditor has to separate or allocate task between staff into transaction processing and computerized system functioned.
- Auditor has to ensure adequate supervision of personnel administered.
- As the process of auditing is not a starlight forward flow of work from start to finish.
- Auditor has to check with the standard checklist or with list of questions.
This could be explained in better way, for example vouching of wages and salaries paid, here the auditor could use various controlling system such as record counts, limit test , check digits, hardware control etc. in order to maintain accuracy and reliability of transaction. With the above preventive measure, auditor would able to conduct audit systematically and effectively.
Auditing through the Computer could be applied in different perspective by an organization based on their obligation. The different perspective of Auditing Through the Computer as per the situation is as following:
Table: Different Perspective of Auditing Through the Computer
Sr. No. | Situation | Examples |
1 | Large Volume of Transaction | Cash sales in large organizations or Departmental stores |
2 | Highly Internal Control system | Operational banking system a computer programmed may group connections for separate tellers to deliver controls totals for settlement at the culmination of day’s dispensation |
3 | Efficient Processing System | EDP system used to scan accounts receivable balances for amount exceeding the credit limit and for confirming receivable accounts random sampling table can be used. |
4 | Facilitate Analysis | Summarizes inventory turnover statistics to Determine slow moving inventory items with help of software. |
5. | Cost Benefit | Identification of extensive difference in the Noticeable audit trail. |
Auditing through the Computer facilitate different function under computerized system. It is renounce then Auditing around the Computer. Functions concern with test data, process controlling, audit programmers is performed by this method.
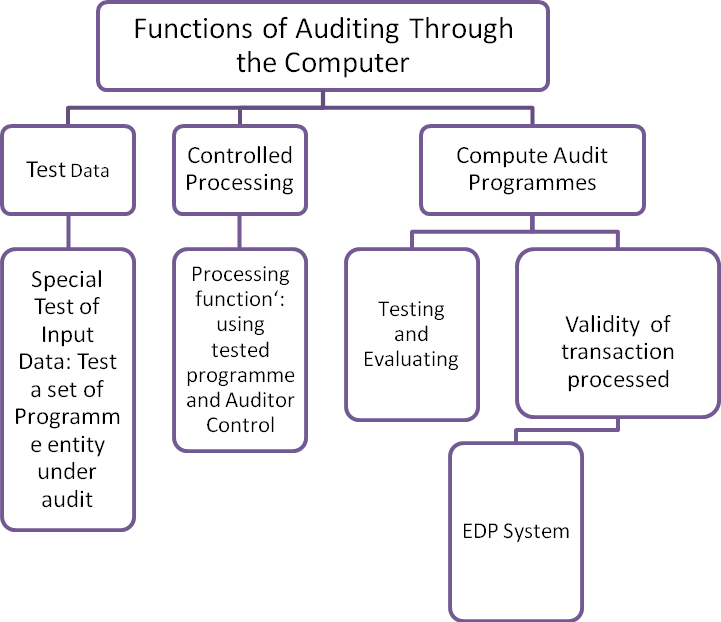
Chart: Functions of Auditing Through the Computer:
Auditing through the Computer is providing an additional feature in relation to former approach.
Some of the affirmative aspect of Auditing Through the Computer are as follow:
a) Excess internal control
This approach facilitates excess internal control in numerous forms. High level of internal control in general, application software and other control maintain the accuracy and effectiveness in an organization. Excess Internal control systems reduce the worry of auditor. Audit process would able to compete on time without any meddling or obligation.
The application of Software System requires high quality of software, internal control and qualified and experience staff to execute the system. It may add the cost to an organization. It is an additional cost above the other operating cost. Hence, it could be a reason for non acceptance such approach in may organization.
a. Over burden on staff as well as on auditor
The application software is demand of digital era and level of software is depends on the complexity level. The complexity level in terms of absence of input documents, lack of observable transaction trail and lack of detectable output etc increased the work of staff and auditor. The staff should be expert. Preventative measures need to under taken by the auditor.
b. Specialized /Professional course in computer auditing requires
Like manual audit system, audit under CIS environment is also required trained and qualified person to be carried out the audit. Several legal bodies have laid down the quality, qualification and expertise required to an auditor. Both the procedures compliance as well substance is needed to complete tasks correctly and effectually. Such multiple tasks enforce that auditor should have professional expertise to identify the events of an organization.
Auditing through the Computer demands excessive involvement. With the incredible growth in information system several new concept has boosted up under accounting and auditing system. Auditing with the Computer or Auditing by using the Computer is a most challenging approach in the area of audit. Researcher has focused on some the aspect of Auditing with the Computer based on available study in field of audit.
Auditing with the Computer / Auditing by using Computer:
Auditing with the Computer is the process of using CIS system of the client in gathering material evidence. It is a component of Auditing through the Computer.
Auditing through the Computer makes use of computer in auditing. Computers are useful tools and techniques used in performing audit. Many data files are in machine readable form, which cannot be easily examined by anyone. Hence, auditor need to utilize a computer programmes to examine those files and perform many of the clerical tasks previously performed by staff. Under this approach entire accounting and auditing process is based on software system and auditor should have keen knowledge about it. The techniques which use the computer itself for audit purpose are known as “Computer Assisted Auditing Techniques” (CAAT’s). It is the techniques which use the computer itself for audit purpose.
Application controls
Application controls are those controls (manual and computerised) that relate to the transaction and standing data pertaining to a computer-based accounting system. They are specific to a given application and their objectives are to ensure the completeness and accuracy of the accounting records and the validity of entries made in those records. An effective computer-based system will ensure that there are adequate controls existing at the point of input, processing and output stages of the computer processing cycle and over standing data contained in master files. Application controls need to be ascertained, recorded and evaluated by the auditor as part of the process of determining the risk of material misstatement in the audit client’s financial statements.
- Input controls
Control activities designed to ensure that input is authorised, complete, accurate and timely are referred to as input controls. Dependent on the complexity of the application program in question, such controls will vary in terms of quantity and sophistication. Factors to be considered in determining these variables include cost considerations, and confidentiality requirements with regard to the data input. Input controls common to most effective application programs include on-screen prompt facilities (for example, a request for an authorised user to ‘log-in’) and a facility to produce an audit trail allowing a user to trace a transaction from its origin to disposition in the system.
Specific input validation checks may include:
Format checks
These ensure that information is input in the correct form. For example , the requirement that the date of a sales in voice be input in numeric format only – not numeric and alphanumeric.
Range checks
these ensure that information input is reasonable in line with expectations. For example, where an entity rarely, if ever, makes bulk-buy purchases with a value in excess of $50,000, a purchase invoice with an input value in excess of $50,000 is rejected for review and follow-up.
Compatibility checks
these ensure that data input from two or more fields is compatible. For example, a sales invoice value should be compatible with the amount of sales tax charged on the invoice.
Validity checks
These ensure that the data input is valid. For example, where an entity operates a job costing system – costs input to a previously completed job should be rejected as invalid.
Exception checks
These ensure that an exception report is produced highlighting unusual situations that have arisen following the input of a specific item. For example, the carry forward of a negative value for inventory held.
Sequence checks
These facilitate completeness of processing by ensuring that documents processed out of sequence are reject ed. For example, where pre-numbered goods received notes are issued to ac knowledge the receipt of goods into physical inventory, any input of notes out of sequence should be rejected.
Control totals
These also facilitate completeness of processing by ensure that pre-input, manually prepared control totals are compared to control totals input. For example, non-matching totals of a ‘batch’ of purchase invoices should result in an on-screen user prompt, or the production of an exception report for follow-up. The use of control totals in this way are also commonly referred to as output controls (see below).
Check digit verification
This process uses algorithms to ensure that data input is accurate. For example, internally generated valid supplier numerical reference codes, should be formatted in such a way that any purchase invoices input with an incorrect code will be automatically rejected.
2. Processing controls
Processing controls exist to ensure that all data input is processed correctly and that data files are appropriately updated accurately in a timely manner. The processing controls for a specified application program should be designed and then tested prior to ‘live’ running with real data. These may typically include the use of run-to-run controls, which ensure the integrity of cumulative totals contained in the accounting records is maintained from one data processing run to the next. For example, the balance carried forward on the bank account in a company’s general (nominal) ledger. Other processing controls should include the subsequent processing of data rejected at the point of input, for example:
- A computer produced print-out of rejected items.
- Formal written instructions notifying data processing personnel of the procedures to follow with regard to rejected items.
- Appropriate investigation/follow up with regard to rejected items.
- Evidence that rejected errors have been corrected and re-input.
3. Output controls
Output controls exist to en sure that all data is processed and that output is distributed only to prescribed authorized users. While the degree of output controls will vary from one organization to another (dependent on the confidentiality of the information and size of the organization), common controls comprise:
- Use of batch control totals, as described above (see ‘input controls’).
- Appropriate review and follow up of exception report information to ensure that there are no permanently outstanding exception items.
- Careful scheduling of the processing of data to help facilitate the distribution of information to end users on a timely basis.
- Formal written instructions notifying data processing personnel of prescribed distribution procedures.
- Ongoing monitoring by a responsible official, of the distribution of output, to ensure it is distributed in accordance with authorized policy.
4. Master file controls
The purpose of master file controls is to ensure the ongoing integrity of the standing data contained in the master files. It is vitally important that stringent ‘security’ controls should be exercised over all master files.
These include:
- Appropriate use of passwords, to restrict access to master file data
- The establishment of adequate procedures over the amendment of data, comprising appropriate segregation of duties, and authority to amend being restricted to appropriate responsible individuals
- Regular checking of master file data to authorised data, by an independent responsible official
- Processing controls over the updating of master files, including the use of record counts and control totals.
Computer Assisted Auditing Techniques (CAAT’s):
CAATs are techniques that utilize the computer as an audit instrument. It comprises computer programmers and data that can be exercise by auditor in process of information system. Information Technology based tools and techniques are required to allow the auditor to access, analyze and evaluate the data stored on the computers. CAATs are nothing but software. The software is either available off-the-shelf, or is specifically developed. There are various types of CAATs available.
CAATs consist of both the procedures compliance as well as substantive. It consists of Test Packs and Integrated test data approach. Both the approaches have distinguished features. The selection or application of CAAT’s is based on silent factors. The auditor ought to consider those silent factors involved in audit approach before applying audit process in an organization. The selection of approach in CAAT’s is based on following aspects.
Chart: Factor affect the selection of approaches under CAAT:
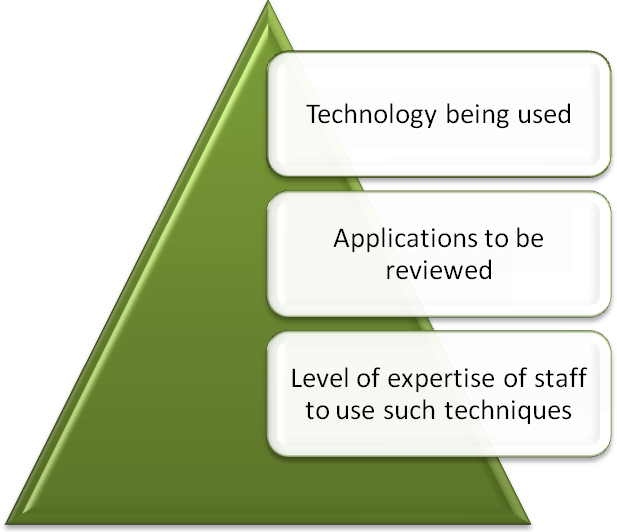
- Technology being used:
The auditor should verify type and level of technology used in an origination. Accordingly audit team will decided their way of functioning.
2. Applications to be reviewed
The application used in an organization has to be evaluated by entity. On the basis of evaluation report, auditor can come to know about the authenticity and accuracy of data.
3. Level of expertise of staff to use such techniques
Auditing With the Computer itself reflect the optimum requirements of techno savvy personnel in the audit process. Hence, while selecting the approach the auditor should able to understand the expertise level of staff. Programme building is done by one person and implementation done by third person who do not knows about the function. One has to understand and implement it.
Hence, to safeguard interest of CAAT’s application ICAI has placed the guideline for the same. ICAI’s guidance note on Computer Assisted Audit Techniques (CAATs) deals with the usage of CAATs. The guidance note recognizes that CAATs may enhance adeptness and productivity of audit measures. These guidance notes are based on certain principle recommended by The ICAI.
Following are the principal recommended by ICAI
- Availability of sufficient IT knowledge, expertise and experience among the member of audit team to plan, execute and use of results of the particular CAAT.
- Availability of CAATs, suitable computer facilities and data in appropriate format.
- Impracticability of manual test due to lack of evidence
a) Example : authorization of system generated transactions
b) Operation of programmed control procedures
c) Retention of transaction details in electronic form in summarized form of totaling
d) Printed in hard copy form
4. Impact on effectiveness and efficiency of application of software than manual system.
5. Time constraints- the auditor requires data. Some time data store for short period of time, the auditor may need to alter the timing of performing CAATs that requires such data.
With the above discussion it is cleared that CAAT’s overcome of other two approaches in respect of several aspect. It’s imperative need of digital era to follow the CAAT’s. Hence, the researcher has tries to explain the Following is the Needs for CAAT.
Chart: Need for CAAT in CIS environment :
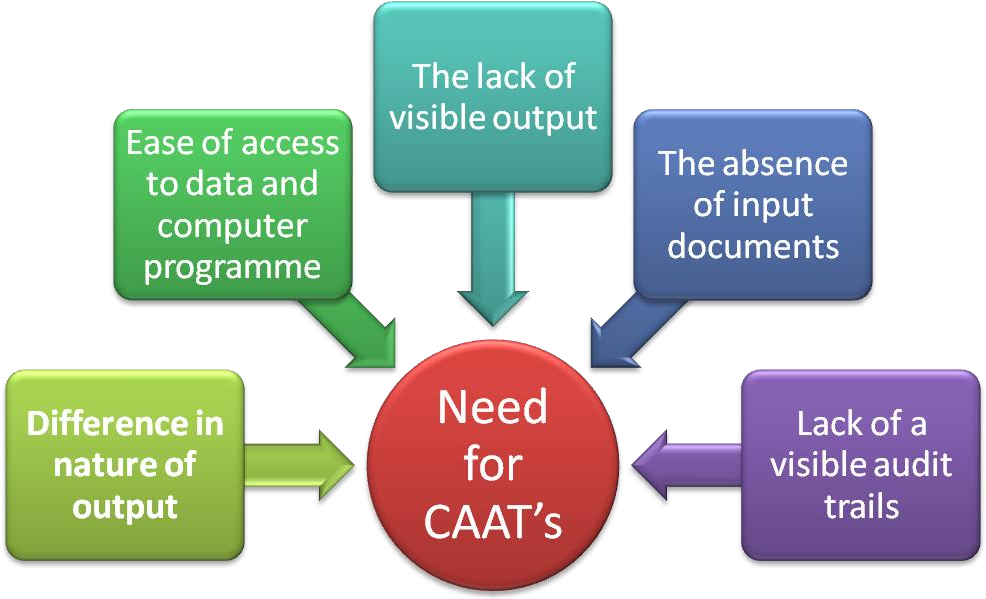
- Absence of input documents:
Under CIS environment, a number of transactions are fed into the system without there being any source of document. Hence in CIS environment data may be recorded into the computer system without supporting documents. For example sales transactions may be enter into computer directly by the salesmen without there being any source document. An individual data entry authorization may replace by other procedures in on- line transaction systems. Approval for order entry may be replaced by some other procedures. In some of the cases it was noticed that source document may be created for short duration.
2. Lack of visible transaction trails:
Transaction Trails means the consecutive junctures in the footage of the operation in the books of account through which an auditor may be able to dash the transaction. In a manual system, it is normally possible to follow a transaction through the system by examining relevant sources documents, books of account, records etc. In a CIS environment, source documents for many transactions may not exist. Moreover, the updating of multiple files may be done by a single transaction. For example, the purchase of a unit of raw material goods may be recorded by computer, in inventory records, purchase records and creditor records. Because of these characteristics, it may be difficult to relate the output to individual transactions. The additional difficulties associated to this that the final output report will be without the detailed data available. As in a traditional system an auditor can obtain requires document as when required with different sources of document like books of accounts, records, files and reports etc. The business deal track may be in machine readable form in EDP environment systems, which are exits only for a temporary.
3. Lack of visible output:
In traditional system it is feasible to access visually the results of processing. In electronic system a printed results of processing is not always possible, only in summary data may be admittance facts recalled on machine readable files.
4. Simplicity of entrance to data and computer programs:
Data and computer programs may be retrieved data. It can be rehabilitated at the computer or through the use of computer gear at inaccessible locations. The lack of appropriate controls leads to increased in potential for unauthorized access and alteration of data and programmers by internal or external user of an entity.
5. Difference in nature of output:
Under traditional system, visual examination of records enables an auditor to identify cuttings, insertions, overwriting etc. As these may designate an attempt to manipulate the records, the auditor examines these thoroughly. In CIS environment, on the additional indicator, the alteration of records cannot be identified through their visual examination. The auditor, therefore, has to apply other appropriate procedures to satisfy them that the records are into altered in an unauthorized manner.
CAATs allow the auditor to save period by investigating data deposited on computer media rather than on print-outs or other documents and in some cases, to demeanour tests which cannot be done physically because there is no noticeable indication or audit trajectory.
Hence the auditor have to take decision regarding testing of electronic data available in system. Alternatively, auditor could be strained to abandon manual tests because of unavailability of visible audit trail. In both the case, auditor must use either software or specially prepared audit facts to evaluate the inner workings of entity.
(c) Uses of CAAT in performing various auditing procedures:
CAAT is used in test of niceties of transactions and balances. It is applicable to compliance and substantive testing. It is applied in executing different auditing procedures. Following is the use of audit software to test entire transaction in a computer file.
- Analytical review procedures- to recognize extraordinary changing of items
- Compliance test to general EDP controls- specimen, the use of experiment data to test access measures to the program libraries
- Compliance test of EDP application controls- it helps to test the function of the programme procedures
- Detection of fraud: it helps emphasize on frauds. There is lack of documentary evidence to indicate that the application of audit software has unearthed the will concealed frauds.

Chart: Use of CAATs- audit process:
 Along with above use of CAAT in audit process, it has several uses in different forms. Such commonly used of CAATs is essential in today’s competitive era. The utility of CAATs are as follows:
Along with above use of CAAT in audit process, it has several uses in different forms. Such commonly used of CAATs is essential in today’s competitive era. The utility of CAATs are as follows:
Audit Software:
It comprises digital system used by the auditor as a fragment of this auditing practice to course data of audit implication.
- Package Programmed: It is generated to design to perform data processing. It is full compile of Computer programmed.
- Purpose Written Programmed: It is used in to execute audit tasks in definite situation. It is prepare by auditor, by the organization or by programmer engaged by auditor.
- Utility Programmed: It is used by an organization to execute familiar data processing functions. For example sorting, creating and printing files.
Test Data:
Test data is technique used in audit process in comparing input data with the output data with pre- determined results. It is applicable to several tests such as:
- Specific Control: It is used for specific controls in computer programmed such as on line password and data access controls.
- Test Transactions selected form previously processed transaction: It is based on historical data or data treated by the examiner to analysis sacrifice processing characteristics of an organization.
- Integrated Test Facility: It is used identify the dummy unit. It is posted through the normal processing.
The examiner must safeguard that the test connections are afterward eradicated from accounting records of an organization.
Many authors have focused on the relevant and usability of CAATs in numbers of way an organization. It has numerous features.
Types of CAATs:
CAATs have peculiar application in an organization. The application is based on requirements of an organization. Types of CAATs decide the performance of auditor in respect of demand for audit process. The types of CAATs used for audit purpose are discussed as follows:
(A) Test Data/ Packs:
An organization compares the results obtained with pre- determined results by using Test data techniques in directing audit measures by inflowing data into computer system. It involves use of specific data for testing a particular sequence or program operated by the system.
Characteristics of CAATs:
CAATs are significant tools and techniques used in CIS environment. In CIS environment there are possibilities of misappropriation of documents, authorities, duties and responsibilities. An auditor must insist an availability of visible records irrespective of total processing time. Under this system internal control is considered reliable and accurate. The thrashing of audit track can generate obstacles CIS-audit process. Hence to overcome these difficulties Computer Assisted Audit Techniques can be used. Application of CAATs has distinct advantage such as:
a) Audit Effectiveness:
Efficacy and proficiency of auditing can be improved with the adoption of CAAT in obtaining and evaluating audit evidence -for example:
- Some transactions may be tested effectively and efficiently by using the computer at similar level of cost. To examine all or a superior amount of transactions adequate selection required.
- Analytical review procedures help in reviewed and obtained intelligences of uncommon stuffs in printed form by the computer.
b) Saving of Time:
By using CAAT than other audit procedures, auditor can save period by revising the EDP controls.
c) Effective Test Checking and Examination in Depth:
CAAT licenses actual inspection in complexity of nominated dealings since the auditor “constructs” the absent audit path.
d) Ability to Scrutinize Large Volume of Data:
CAAT Provides fast and precise scrutinise of large volume of data without interference of manual.
e) Less Manual Procedure:
CAAT’s helps automatic transfer of data to several files and with the command generate quick data without much involvement of manpower.
- The test data use for processing purpose are:
- Based on past transaction
- Constructed deliberately for test purpose:
- Abnormal transaction
- Normal transaction
- Absurd transaction
- Auditor verifies how the computer system responds to test pack. Whether the transactions reports as abnormal or normal or accepts them as “Garbage- In- Garbage – Out (GIGO)”.
- The data in test pack is also processed manually: Auditor need to compares and scrutinize the results under manual and computerized processing and derives his conclusion. Examples:
e. Specific controls in computer programs such as password and data access controls are usually tested by test data system.
f. Throughout the ordinary dispensation test dealings recycled in a united test ability where a ‘dummy’ unit is established and to which test businesses are posted.
When examination data is administered with the organizations normal processing auditor should safeguard that the test businesses are afterward jettisoned from accounting records of an organization.
(B) Audit Software/ Computer Programs:
Auditing software include of computer program accepted by the auditor as a part of auditing procedure to route data of audit connotation. For examples, auditor can generate own computer program to prepare ageing schedule of debtors based on past data. In the computer stored and then compare it with the ageing schedule processed by computer system of an entity. Such types of software called as Purpose Written Audit Software. In many cases the auditor can use Generalized Audit Software (GAS).
Generalized audit software is a set of computer system that can perform certain shared data dispensation purposes such as:
a) Computer files
b) Selecting records
c) Performing calculation
d) Printing reports
It was discovered by software developing agencies and by large organization.
GAS performs the following functions:
- Verify calculations
- Examine records for correctness, consistency and completeness
- Evaluate information retrieved through order audit procedures with enterprise records
- Compare data on separate files
- Summaries or re-sequence data
- Select samples
On the above discussion emphasized that different audit software can be developed, according to demand of an entity. Hence audit software should consists of the following:
1. Package Programs
2. Purpose Written Programs Utility Programs
- Package Programs:
A package program is nothing but Generalized Audit Programs (GAP). Data processing procedure such as reading computer files, selecting information, creating data and printing reports are performed by GAP. GAP is meant for common purpose specified by the auditor.
2. Purpose Written Programs
As the name suggest it is developed for specific purpose for specific circumstances. It is use as per the need of an organization.
3. Utility Programs
These systems adopted by the organization to carry out regular data processing factions, such sorting, creating and printing files. These programs are generally not designed for audit purpose and therefore may not contain such feature as automatic records totals or rheostat wholes.
It can used for it is used for both the testing compliance and substantive. It helps to perform various auditing procedures.
CAATs application is alteration or substitute of exiting system. As this system has a numbers of positive features which helps to accomplice the objective of an entity. But the accurately and effectiveness of result is based on following factor which needs to undertake while adopting the CAATs.
Chart: Factor Responsible for Application CAAT’s

a) Accessibility of adequate IT knowledge and proficiency: CAATs is the part of Auditing with the computer. It means it has excess use of software system. The use of software system is either self-made or acquired from outside. In both the case the auditor and accountant must able to use it. The continuous development under this system demand high skill and knowledgeable staff to handle the system.
b) Incompatibility between CAATs and computer facilities (of entity): Most of time there is vast difference between the availability of facilities and required. Hence auditor must verify the entity’s capacity regarding the use of software system and their financial position to accept the same.
c) Impracticability of manual tests: It has been noticed that a single change in the operating environment not only affect organization but also the staff. Auditor should examine impact of CAATs on the manual audit process. The application of CAAT is inseparable part of manual system.
d) Influence on success and proficiency in removing a data: Auditor should safeguard that the enactment of CAAT. It should not affect the authenticity of data used in audit process. Usually it is noticed that the one acceptance affect the other one.
e) Time constraints: Manual audit system is based on different audit procedure. There is transformation from one to another. Coasting, totalling, posting, scrutiny task the time to complete. Due to nonexistence of audit trails in terms of input and output save the time under CIS environment. CIS environment keeps away from itself from the issues related with time constraints.
Hence the control procedures needed while using CAAT under both the application i.e. Software and control test applications. The application of Computer Audit Programme facilitates in audit procedure and provide silent feature. The following is brief characteristics of Computer Audit Programmed:

Chart: Characteristics of Computer Audit Program
Auditing and Assurance Standard (AAS) is establishing standard on measures to be shadowed when an audit is steered in CIS environment by Institute of Chartered Accountants of India (ICAI). The auditing standard is essential to maintain the standardized.
ICAI’s guidance notes on importance of CAATs:
It may be noted that test data and audit software data. It is complementary and not mutually exclusive. There are other techniques available which can be accepted by concern. Apart from test data and software ICAI’s guidance note identifies the following importance of CAATs:
Table: ICAI’s guidance notes on importance of CAATs
Sr. No. | Importance | Facilitates |
1 | Audit Automation | Perform various tasks: evaluating client’s risk management procedures, generating electronic working paper etc. |
2 | Core Image Comparison | Compare the executable adaptation of a system through secure master copy. It give assurance about the program in use is authorized or unaltered. |
3 | Database Analysis | To examine the rights associated with terminals and the ability of users to access information on a database which help to understand database management system. |
4 | Embedded Code | It is own programs used by the client for processing. It helps the auditor to examine transaction passing through the system and to find out unusual transactions. |
5 | Log Analyzers | To read and analyze records of computer activity and evaluate the efficacy of access control. |
6 | Mapping | To list unused program instructions which helps in identifying program codes which may be there for fraudulent purpose. |
7 | Modeling | To help to carry out variety of procedures such as analytical procedures, on client’s records. It also helps to project the result and compare actual result with expected results. |
8 | Online Testing | It help to verify whether a specific programs or test performing its task properly or not. |
9 | Program Code Analysis | It helps to examine the cradle code of actual program with a view to subsequent the judgment of the program to content himself that it will perform according to his understanding. |
10 | Program Library Analyzers | It helps the examiner to recognize dates on which changes were made to executable programs. |
11 | Source Comparison | It helps in comparison of source edition of a system through secure master copy. |
12 | Tracing | It helps to spot which guidelines were followed in a program and in what command. |
Auditing around the computer, Auditing through the computer and Auditing with the computer has distinctions prose and corn. As per the necessity of an organisation application of CIS environment is decided. Each approach has different features with the need of an entity. The following is the list of disparity between approaches:
Table: Disparity between Approaches
Sr. No | Particulars | Auditing through the Computer | Auditing around the Computer | Auditing with the Computer |
1 | Recognition of Computer | Under this systems are accepted as “live” and dynamic devices, which add value to the process Of auditing. | Computers are treated as mechanical book- keeping aids under this approach | It is integral part of computer. It is itself is computer program. |
2 | Audit Assurance | The focus of audit is to examine the accounting system and software used – to certify that they deliver audit pledge on the various features of Control | The focus of audit is to take voluminous reports and output and compare “input voucher” with “system output” to obtain audit Assurance | The focus of audit software used in audit process. Audit assurance focus of GAAT specific Generalize audit software (GAS). |
3 | Use of CAATs | Applicable | Non Applicable | Applicable |
4 | Extent Computer skill required | Knowledge of use of Software and programs required | No specific skill is required | Mote intensive knowledge is required. |
5. | Application of Approach involves | Testing of client’s data Files | Manual testing of Transaction data | Testing of client’s Programs |
Audit under Computerized Information System environment provides an examination of system efficiency, system effectiveness and safeguard of assets of an organization. Such examination of audit process reflects True and Fair View and accurate only when appropriate approach have been used. The approaches suggested by the expert and ICAI has its own prone and corns. Each approach has distinct feature and satiability level.
Auditing around the computer is basically similar to manual audit process. Under this approach an auditor basically focused on input data and output data. He does not bother about the how he got the output result. It has many advantages with disadvantage. Such approach can be applicable to small organization where volume of transaction is less.
The second approach i.e. Auditing through the Computer emphasise on excess use of computer. Under this approach an auditor need to comprehend the procedure system to make audit process effective and efficient. It is based on internal control system. Both the control system i.e. General and Application system must be control. It is also based on factor such as On-Line data entry, Elimination or reduction of printouts and Real time file updating. Auditing through the computer can be completed by applying method such as Test Data, Controlled Processing and Computer Audit Programmers. Even this approach has merits and demerits. It depends on auditor how he is using and understanding.
The last approach is Auditing with the Computer. This approach actual make the computer in use. It involves auditing system and programmers used in the entity by an examiner. The techniques which use the computer itself for audit purpose are known as “Computer Assisted Auditing Techniques” (CAAT’s). It is part of Auditing Through the Computer. CAATs are techniques that can be applied in auditing. It comprises computer programmers and data that can be accepted by auditor in process of information system. IT based tools and techniques are required to enable the auditor to access, analyze and evaluate the data stored on the computers. Again CAATs has different types such as test data and audit software. The application such types depends on audit purpose. ICAI has led down the guideline notes on the importance of CAATs in audit process.
Hence all the approaches have its characteristics. Every application restricted with certain impediment. Application of such approach depends on nature of business, knowledge of computer, availability computer.