 UDP
UDP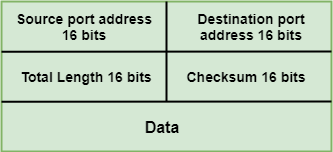 Where,
Where,The receiving TCP uses the sequence number to reassemble the segments if they arrive out of order or to eliminate the duplicate segments.
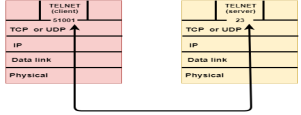
- Establish a connection between two TCPs.
- Data is exchanged in both the directions.
- The Connection is terminated.
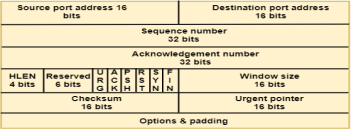 Where,
Where,- Window Size: The window is a 16-bit field that defines the size of the window.
- Checksum: The checksum is a 16-bit field used in error detection.
- Urgent pointer: If URG flag is set to 1, then this 16-bit field is an offset from the sequence number indicating that it is a last urgent data byte.
- Options and padding: It defines the optional fields that convey the additional information to the receiver.
Basis for Comparison
TCP
UDP
Definition
TCP establishes a virtual circuit before transmitting the data.
UDP transmits the data directly to the destination computer without verifying whether the receiver is ready to receive or not.
Connection Type
It is a Connection-Oriented protocol
It is a Connectionless protocol
Speed
Slow
High
Reliability
It is a reliable protocol.
It is an unreliable protocol.
Header size
20 bytes
8 bytes
acknowledgement
It waits for the acknowledgement of data and has the ability to resend the lost packets.
It neither takes the acknowledgement, nor it retransmits the damaged frame.
Port No
Protocol
Description
7
Echo
Resends a received datagram back to the sender.
9
Discard
Discards a received datagram.
11
Users
Shows active users.
13
Daytime
Gives the date and time.
17
Quote
Gives a Quote of the day.
19
Chargen
Gives a string of characters.
53
Nameserver
Shows Domain Name Service.
67
BOOTPs
Server port to download bootstrap information.
68
BOOTCPc
Client port to download bootstrap information.
69
TFTP
Trivial File Transfer Protocol.
111
RPC
Remote Procedure Call.
123
NTP
Network Time Protocol.
161
SNMP
Simple Network Management Protocol.
162
SNMP
Simple Network Management Protocol. (trap)
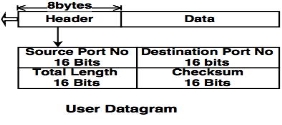
The important fields of user datagrams are:
1. Source Port Number
Checksum is used to detect the errors in the user datagram.
 Features of UDPSome features of UDP are as stated below:
Features of UDPSome features of UDP are as stated below:1.Connectionless service
UDP provides connectionless service. Each user datagram sent by the UDP is an independent datagram. There is no relationship between the different user datagrams even if they are coming from the same source and going to the same destination source.
Transmission Control protocol (TCP)
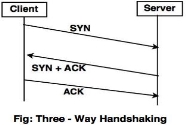
The Three - Way Handshaking protocol is used to establish connection between two TCPs.
1. A client sends a SYN data packet to server. The purpose of this step is to see if the server is open for new connection.
2. The server needs to keep all ports open to establish a new connection. When the server receives the SYN packet from the client, the client replies and returns the conformation SYN/ACK packet.
3. The client receives the SYN/ACK packet and replies with ACK packet to establish the connection.
 5.3 TCP Flow ControlTCP provides flow- control mechanism facility. A receiver can control the data which is sent by the user. This action is taken to prevent the data crash at the receiver's end. TCP uses byte-oriented flow control, according to numbering system.TCP Congestion Control
5.3 TCP Flow ControlTCP provides flow- control mechanism facility. A receiver can control the data which is sent by the user. This action is taken to prevent the data crash at the receiver's end. TCP uses byte-oriented flow control, according to numbering system.TCP Congestion Control 1. Slow start algorithm is used to control the congestion in TCP. In this algorithm, the size of window grows exponentially till the timeout occurs or the receiver's window is reached to the maximum threshold (64 kb = 65535 bytes).
Example:
Suppose that, the sender starts with congestion window = 20 = 1 MSS (Maximum Segment Size, each segment consists of 1byte). After receiving acknowledgement for segment 1, the size of window can be increased by one. Thus, the total size of congestion window = 21 = 2. When all the segments are acknowledged, the total size of congestion window = 23 = 8.
2. Congestion avoidance algorithm
Example
Start with, Congestion window = 1
By adding 1, congestion window = 1 + 1 = 2
1.Process-to-Process communication
SCTP uses all important ports of TCP.
2.Multi-Stream Facility
SCTP provides multi-stream service to each connection, called as association. If one stream gets blocked, then the other stream can deliver the data.
3.Full-Duplex Communication
SCTP provides full-duplex service ( the data can flow in both directions at the same time).
4. Connection- Oriented Service
The SCTP is a connection oriented protocol, just like TCP with the only difference that, it is called association in SCTP. If User1 wants to send and receive message from user2, the steps are :
Step1: The two SCTPs establish the connection with each other.
Step2: Once the connection is established, the data gets exchanged in both the directions.
Step3: Finally, the association is terminated.
5. Reliability
SCTP uses an acknowledgement mechanism to check the arrival of data.Features of SCTPSome important features of SCTP are as stated below:
1. Transmission Sequence Number (TSN)
The unit of data in SCTP is a data chunk. Data transfer in SCTP is controlled by numbering the data chunks. In SCTP, TSN is used to assign the numbers to different data chunks.
2. Stream Identifier (SI)
The SI is a 16 bit number and starts with 0. In SI, there are several streams in each association and it is needed to identify them. Each data chunk needs to carry the SI in the header, so that it is properly placed in its stream on arrival.
3. Packets
In SCTP, the data is carried out in the form of data chunks and control information is carried as control chunks. Data chunks and control chunks are packed together in the packet.
4. Multihoming
Multihoming allows both ends (sender and receiver) to define multiple IP addresses for communication. But, only one of these can be defined as primary address and the remaining can be used as alternative addresses. 5.4 Quality of services: Dataflow characteristics, Flow ControlQoS is an overall performance measure of the computer network.
Important flow characteristics of the QoS are given below:
1. Reliability
If a packet gets lost or acknowledgement is not received (at sender), the re-transmission of data will be needed. This decreases the reliability.
The importance of the reliability can differ according to the application.
For example:
E- mail and file transfer need to have a reliable transmission as compared to that of an audio conferencing.
2. Delay
Delay of a message from source to destination is a very important characteristic. However, delay can be tolerated differently by the different applications.
For example:
The time delay cannot be tolerated in audio conferencing (needs a minimum time delay), while the time delay in the e-mail or file transfer has less importance.
3. Jitter
The jitter is the variation in the packet delay.
If the difference between delays is large, then it is called as high jitter. On the contrary, if the difference between delays is small, it is known as low jitter.
Example:
Case1: If 3 packets are sent at times 0, 1, 2 and received at 10, 11, 12. Here, the delay is same for all packets and it is acceptable for the telephonic conversation.
Case2: If 3 packets 0, 1, 2 are sent and received at 31, 34, 39, so the delay is different for all packets. In this case, the time delay is not acceptable for the telephonic conversation.
4. Bandwidth
Different applications need the different bandwidth.
For example:
Video conferencing needs more bandwidth in comparison to that of sending an e-mail.