Unit - 1
Introduction to Operating System
An Operating system (OS) is a software which acts as an interface between the end user and computer hardware. Every computer must have at least one OS to run other programs. An application like Chrome, MS Word, Games, etc needs some environment in which it will run and perform its task. The OS helps you to communicate with the computer without knowing how to speak the computer's language. It is not possible for the user to use any computer or mobile device without having an operating system.

Fig 1: Operating system
Features of Operating System
Here is a list commonly found important features of an Operating System:
● Protected and supervisor mode
● Allows disk access and file systems Device drivers Networking Security
● Program Execution
● Memory management Virtual Memory Multitasking
● Handling I/O operations
● Manipulation of the file system
● Error Detection and handling
● Resource allocation
● Information and Resource Protection

Types of Operating system
● Batch Operating System
● Multitasking/Time Sharing OS
● Multiprocessing OS
● Real Time OS
● Distributed OS
● Network OS
● Mobile OS
Batch Operating System
Some computer processes are very lengthy and time-consuming. To speed the same process, a job with a similar type of needs are batched together and run as a group.
The user of a batch operating system never directly interacts with the computer. In this type of OS, every user prepares his or her job on an offline device like a punch card and submit it to the computer operator.
Multi-Tasking/Time-sharing Operating systems
Time-sharing operating system enables people located at a different terminal(shell) to use a single computer system at the same time. The processor time (CPU) which is shared among multiple users is termed as time sharing.
Real time OS
A real time operating system time interval to process and respond to inputs is very small. Examples: Military Software Systems, Space Software Systems.
Distributed Operating System
Distributed systems use many processors located in different machines to provide very fast computation to its users.
Network Operating System
Network Operating System runs on a server. It provides the capability to serve to manage data, user, groups, security, application, and other networking functions.
Mobile OS
Mobile operating systems are those OS which is especially that are designed to power smartphones, tablets, and wearables devices.
Some most famous mobile operating systems are Android and iOS, but others include BlackBerry, Web, and watchOS.
Difference between Firmware and Operating System
Firmware | Operating System |
Firmware is one kind of programming that is embedded on a chip in the device which controls that specific device. | OS provides functionality over and above that which is provided by the firmware. |
Firmware is programs that been encoded by the manufacture of the IC or something and cannot be changed. | OS is a program that can be installed by the user and can be changed. |
It is stored on non-volatile memory. | OS is stored on the hard drive. |
Difference between 32-Bit vs. 64 Bit Operating System
Parameters | 32. Bit | 64. Bit |
Architecture and Software | Allow 32 bit of data processing simultaneously | Allow 64 bit of data processing simultaneously |
Compatibility | 32-bit applications require 32-bit OS and CPUs. | 64-bit applications require a 64-bit OS and CPU. |
Systems Available | All versions of Windows 8, Windows 7, Windows Vista, and Windows XP, Linux, etc. | Windows XP Professional, Vista, 7, Mac OS X and Linux. |
Memory Limits | 32-bit systems are limited to 3.2 GB of RAM. | 64-bit systems allow a maximum 17 Billion GB of RAM. |
The advantage of using Operating System
● Allows you to hide details of hardware by creating an abstraction
● Easy to use with a GUI
● Offers an environment in which a user may execute programs/applications
● The operating system must make sure that the computer system convenient to use
● Operating System acts as an intermediary among applications and the hardware components
● It provides the computer system resources with easy to use format
● Acts as an intermediator between all hardware's and software's of the system
Disadvantages of using Operating System
● If any issue occurs in OS, you may lose all the contents which have been stored in your system
● Operating system's software is quite expensive for small size organization which adds burden on them. Example Windows
● It is never entirely secure as a threat can occur at any time
Key Takeaway:
An operating system is a software which acts as an interface between the end user and computer hardware. Operating systems were first developed in the late 1950s to manage tape storage.
The kernel is the central component of a computer operating systems. The only job performed by the kernel is to the manage the communication between the software and the hardware
Need of Operating System
● OS as a platform for Application programs: The operating system serves as a foundation for other programmes known as application programmes to execute on. These application programmes make it easier for consumers to complete a given task. It serves as a link between the user and the computer. It is created in such a way that it can operate, control, and execute various computer applications.
● Managing Input-Output unit: The computer's operating system also allows it to manage its own resources, such as memory, display, keyboard, printer, and so on. Effective usage of these resources necessitates resource management. The operating system manages the system's input-output resources and distributes them to users or programmes based on their needs.
○ Consistent user interface: The operating system offers the user with an easy-to-use user interface, allowing the user to focus on the content and be productive as quickly as possible without having to learn a new UI each time. The operating system provides templates and UI components to make using a computer as simple as possible for the user.
● Multitasking: Memory is managed by the operating system, which allows several programmes to execute in their own space and even connect with one another via shared memory. Users benefit from multitasking since they can complete multiple tasks on a computer at the same time.
● Booting: The process of starting the computer is known as booting. When the CPU is turned on for the first time, there is nothing in the memory. So, in order to turn on the computer, we must first load the operating system into main memory. As a result, booting is the process of loading the operating system into main memory in order to start the computer. As a result, the operating system aids in the initialization of the computer when the power is turned on.
● Platform for other application software: Different application programmes are required by users to complete particular jobs on the system. The operating system (OS) supervises and regulates these programmes to ensure that they run smoothly. To put it another way, it serves as a link between the user and the programmes.
● Manages the memory: It aids in the management of the computer's main memory. It also allocates and deallocates memory for all programmes and tasks.
● Manages the system files: It aids in the organisation of files on the computer. All of the data on the system is stored in files, as we all know. It makes working with the files simple.
● Provides Security: It uses authorisation to keep the system and applications safe. As a result, the operating system protects the system.
Functions of Operating System
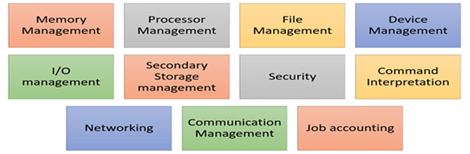
Fig 2: Function of an Operating System
In an operating system software performs each of the function:
- Process management: Process management helps OS to create and delete processes. It also provides mechanisms for synchronization and communication among processes.
- Memory management: Memory management module performs the task of allocation and deallocation of memory space to programs in need of this resources.
- File management: It manages all the file-related activities such as organization storage, retrieval, naming, sharing, and protection of files.
- Device Management: Device management keeps tracks of all devices. This module also responsible for this task is known as the I/O controller. It also performs the task of allocation and deallocation of the devices.
- I/O System Management: One of the main objects of any OS is to hide the peculiarities of that hardware devices from the user.
- Secondary-Storage Management: Systems have several levels of storage which includes primary storage, secondary storage, and cache storage. Instructions and data must be stored in primary storage or cache so that a running program can reference it.
- Security: Security module protects the data and information of a computer system against malware threat and authorized access.
- Command interpretation: This module is interpreting commands given by the and acting system resources to process that commands.
- Networking: A distributed system is a group of processors which do not share memory, hardware devices, or a clock. The processors communicate with one another through the network.
- Job accounting: Keeping track of time & resource used by various job and users.
- Communication management: Coordination and assignment of compilers, interpreters, and another software resource of the various users of the computer systems.
The UNIX operating system is a set of programs that act as a link between the computer and the user. The computer programs that allocate the system resources and coordinate all the details of the computer's internal is called the operating system or kernel.
Users communicate with the kernel through a program known as the shell. The shell is a command line interpreter; it translates commands entered by the user and converts them into a language that is understood by the kernel.
Unix was originally developed in 1969 by a group of AT&T employees at Bell Labs, including Ken Thompson, Dennis Ritchie, Douglas Mcllroy, and Joe Ossanna.
There are various Unix variants available in the market. Solaris Unix, AIX, HP Unix and BSD are few examples, Linux is also a flavor of Unix which is freely available.
Several people can use a UNIX computer at the same time, hence UNIX is called a multiuser system. A user can also run multiple programs at the same time; hence UNIX is called multitasking.
A Brief History of UNIX
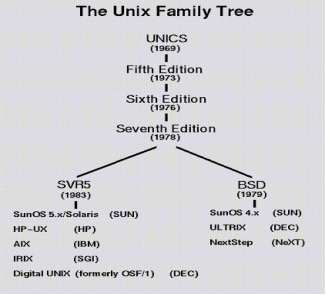
Key takeaway
The UNIX operating system is a set of programs that act as a link between the computer and the user. The computer programs that allocate the system resources and coordinate all the details of the computer's internal is called the operating system or kernel.
What is Linux?
From smartphones to cars, supercomputers and home appliances, home desktops to enterprise servers, the Linux operating system is everywhere.
Linux has been around since the mid-1990s and has since reached a user-base that spans the globe. Linux is actually everywhere: It?s in your phones, your thermostats, in your cars, refrigerators, Roku devices, and televisions. It also runs most of the Internet, all of the world’s top 500 supercomputers, and the world’s stock exchanges.
But besides being the platform of choice to run desktops, servers, and embedded systems across the globe, Linux is one of the most reliable, secure and worry-free operating systems available. Here is all the information you need to get up to speed on the Linux platform.
Just like Windows, iOS, and Mac OS, Linux is an operating system. In fact, one of the most popular platforms on the planet, Android, is powered by the Linux operating system. An operating system is software that manages all of the hardware resources associated with your desktop or laptop. To put it simply, the operating system manages the communication between your software and your hardware. Without the operating system (OS), the software wouldn?t function.
The Linux operating system comprises several different pieces:
● Bootloader – The software that manages the boot process of your computer. For most users, this will simply be a splash screen that pops up and eventually goes away to boot into the operating system.
● Kernel – This is the one piece of the whole that is actually called ?Linux?. The kernel is the core of the system and manages the CPU, memory, and peripheral devices. The kernel is the lowest level of the OS.
● Init system – This is a sub-system that bootstraps the user space and is charged with controlling daemons. One of the most widely used init systems is systemd? which also happens to be one of the most controversial. It is the init system that manages the boot process, once the initial booting is handed over from the bootloader (i.e., GRUB or GRand Unified Bootloader).
● Daemons – These are background services (printing, sound, scheduling, etc.) that either start up during boot or after you log into the desktop.
● Graphical server – This is the sub-system that displays the graphics on your monitor. It is commonly referred to as the X server or just X.
● Desktop environment – This is the piece that the users actually interact with. There are many desktop environments to choose from (GNOME, Cinnamon, Mate, Pantheon, Enlightenment, KDE, Xfce, etc.). Each desktop environment includes built-in applications (such as file managers, configuration tools, web browsers, and games).
● Applications – Desktop environments do not offer the full array of apps. Just like Windows and macOS, Linux offers thousands upon thousands of high-quality software titles that can be easily found and installed. Most modern Linux distributions (more on this below) include App Store-like tools that centralize and simplify application installation. For example, Ubuntu Linux has the Ubuntu Software Center (a rebrand of GNOME Software? Figure 1) which allows you to quickly search among the thousands of apps and install them from one centralized location.
Features of Linux
Some of the most significant features of the Linux Operating System are mentioned below.
● Portable - Software's portability refers to its ability to run on various types of hardware in the same way. The Linux kernel and application programs can be installed on virtually any hardware platform.
● Open Source - Linux is a community-based programming project with freely available source code. Multiple teams collaborate to improve the capabilities of the Linux operating system, which is constantly changing.
● Multi-User - Linux is a multiuser system, which means that multiple users can share system resources such as memory, ram, and application programs.
● Multiprogramming - Linux is a multiprogramming method, which means it can run several programs at the same time.
● Hierarchical File System - System files and user files are organized in a common file structure in Linux.
● Shell - Linux has a special interpreter program that can be used to run operating system commands. It can be used to perform a variety of tasks, such as calling application programs.
● Security - User security is provided by Linux by authentication features such as password protection, restricted access to sensitive files, and data encryption.
Why use Linux?
This is the one question that most people ask. Why bother learning a completely different computing environment, when the operating system that ships with most desktops, laptops, and servers works just fine?
To answer that question, I would pose another question. Does that operating system you’re currently using really work ?just fine?? Or, do you find yourself battling obstacles like viruses, malware, slow downs, crashes, costly repairs, and licensing fees?
If you struggle with the above, Linux might be the perfect platform for you. Linux has evolved into one of the most reliable computer ecosystems on the planet. Combine that reliability with zero cost of entry and you have the perfect solution for a desktop platform.
That’s right, zero cost of entry… as in free. You can install Linux on as many computers as you like without paying a cent for software or server licensing.
Let’s take a look at the cost of a Linux server in comparison to Windows Server 2016. The price of the Windows Server 2016 Standard edition is $882.00 USD (purchased directly from Microsoft). That doesn’t include Client Access License (CALs) and licenses for other software you may need to run (such as a database, a web server, mail server, etc.). For example, a single user CAL, for Windows Server 2016, costs $38.00. If you need to add 10 users, for example, that’s $388.00 more dollars for server software licensing. With the Linux server, it?s all free and easy to install. In fact, installing a full-blown web server (that includes a database server), is just a few clicks or commands away (take a look at ?Easy LAMP Server Installation? to get an idea how simple it can be).
If zero cost isn’t enough to win you over? what about having an operating system that will work, trouble free, for as long as you use it? I’ve used Linux for nearly 20 years (as both a desktop and server platform) and have not had any issues with ransomware, malware, or viruses. Linux is generally far less vulnerable to such attacks. As for server reboots, they’re only necessary if the kernel is updated. It is not out of the ordinary for a Linux server to go years without being rebooted. If you follow the regular recommended updates, stability and dependability are practically assured.
Open source:
Linux is also distributed under an open source license. Open source follows these key tenants:
● The freedom to run the program, for any purpose.
● The freedom to study how the program works, and change it to make it do what you wish.
● The freedom to redistribute copies so you can help your neighbour.
● The freedom to distribute copies of your modified versions to others.
These points are crucial to understanding the community that works together to create the Linux platform. Without a doubt, Linux is an operating system that is by the people, for the people. These tenants are also a main factor in why many people choose Linux. It’s about freedom and freedom of use and freedom of choice.
What is a “distribution?”
Linux has a number of different versions to suit any type of user. From new users to hard-core users, you’ll find a “flavor” of Linux to match your needs. These versions are called distributions (or, in the short form, “distros”). Nearly every distribution of Linux can be downloaded for free, burned onto disk (or USB thumb drive), and installed (on as many machines as you like).
Popular Linux distributions include:
● LINUX MINT.
● MANJARO.
● DEBIAN.
● UBUNTU.
● ANTERGOS.
● SOLUS.
● FEDORA.
● ELEMENTARY OS.
● OPENSUSE.
Each distribution has a different take on the desktop. Some opt for very modern user interfaces (such as GNOME and Elementary OS’s Pantheon), whereas others stick with a more traditional desktop environment (openSUSE uses KDE).
And don’t think the server has been left behind. For this arena, you can turn to:
- Red Hat Enterprise Linux.
- Ubuntu Server.
- Centos.
- SUSE Enterprise Linux.
Some of the above server distributions are free (such as Ubuntu Server and CentOS) and some have an associated price (such as Red Hat Enterprise Linux and SUSE Enterprise Linux). Those with an associated price also include support.
Which distribution is right for you?
Which distribution you use will depend on the answer to three simple questions:
- How skilled of a computer user are you?
- Do you prefer a modern or a standard desktop interface?
- Server or desktop?
If your computer skills are fairly basic, you’ll want to stick with a newbie-friendly distribution such as Linux Mint, Ubuntu (Figure 3), Elementary OS or Deepin. If your skill set extends into the above-average range, you could go with a distribution like Debian or Fedora. If, however, you’ve pretty much mastered the craft of computer and system administration, use a distribution like Gentoo. If you really want a challenge, you can build your very own Linux distribution, with the help of Linux From Scratch.
If you’re looking for a server-only distribution, you will also want to decide if you need a desktop interface, or if you want to do this via command-line only. The Ubuntu Server does not install a GUI interface. This means two things your server won’t be bogged down loading graphics and you’ll need to have a solid understanding of the Linux command line.
However, you can install a GUI package on top of the Ubuntu Server with a single command like sudo apt-get install ubuntu-desktop. System administrators will also want to view a distribution with regards to features. Do you want a server-specific distribution that will offer you, out of the box, everything you need for your server? If so, CentOS might be the best choice. Or, do you want to take a desktop distribution and add the pieces as you need them? If so, Debian or Ubuntu Linux might serve you well.
Installing Linux:
For many people, the idea of installing an operating system might seem like a very daunting task. Believe it or not, Linux offers one of the easiest installations of all operating systems. In fact, most versions of Linux offer what is called a Live distribution? which means you run the operating system from either a CD/DVD or USB flash drive without making any changes to your hard drive. You get the full functionality without having to commit to the installation. Once you’ve tried it out, and decided you wanted to use it, you simply double-click the “Install” icon and walk through the simple installation wizard.
Typically, the installation wizards walk you through the process with the following steps (We’ll illustrate the installation of Ubuntu Linux):
- Preparation: Make sure your machine meets the requirements for installation. This also may ask you if you want to install third-party software (such as plugins for MP3 playback, video codecs, and more).
- Wireless setup (if necessary): If you are using a laptop (or machine with wireless), you’ll need to connect to the network, in order to download third-party software and updates.
- Hard drive allocation (Figure 4): This step allows you to select how you want the operating system to be installed. Are you going to install Linux alongside another operating system (called “dual booting”), use the entire hard drive, upgrade an existing Linux installation, or install over an existing version of Linux.
- Location: Select your location from the map.
- Keyboard layout: Select the keyboard for your system.
- User setup: Set up your username and password.
That’s it. Once the system has completed the installation, reboot and you’re ready to go. For a more in-depth guide to installing Linux, take a look at “How to Install and Try Linux the Absolutely Easiest and Safest Way” or download the Linux Foundation’s PDF guide for Linux installation.
Installing software on Linux:
Just as the operating system itself is easy to install, so too are applications. Most modern Linux distributions include what most would consider an app store. This is a centralized location where software can be searched and installed. Ubuntu Linux (and many other distributions) rely on GNOME Software, Elementary OS has the AppCenter, Deepin has the Deepin Software Center, openSUSE has their AppStore, and some distributions rely on Synaptic.
Regardless of the name, each of these tools do the same thing? a central place to search for and install Linux software. Of course, these pieces of software depend upon the presence of a GUI. For GUI-less servers, you will have to depend upon the command-line interface for installation.
Let’s look at two different tools to illustrate how easy even the command line installation can be. Our examples are for Debian-based distributions and Fedora-based distributions. The Debian-based distros will use the apt-get tool for installing software and Fedora-based distros will require the use of the yum tool. Both work very similarly. We’ll illustrate using the apt-get command. Let’s say you want to install the wget tool (which is a handy tool used to download files from the command line). To install this using apt-get, the command would like like this:
Sudo apt-get install wget?
The sudo command is added because you need super user privileges in order to install software. Similarly, to install the same software on a Fedora-based distribution, you would first su to the super user (literally issue the command su and enter the root password), and issue this command:
Yum install wget
That’s all there is to installing software on a Linux machine. It’s not nearly as challenging as you might think. Still in doubt? Recall the Easy Lamp Server Installation from earlier? With a single command:
Sudo tasksel
You can install a complete LAMP (Linux Apache MySQL PHP) server on either a server or desktop distribution. It really is that easy.
Linux Design Principles:
In its overall design, Linux resembles another non-microkernel UNIX implementation. It is a multi-user, multi-tasking system with complete UNIX-compatible tools. The Linux file system follows the traditional UNIX semantics, and the UNIX standard network model is implemented as a whole. The internal characteristics of Linux design have been influenced by the history of the development of this operating system.
Although Linux can run on a variety of platforms, at first it was developed exclusively on PC architecture. Most of the initial development was carried out by individual enthusiasts, not by large funded research facilities, so that from the start Linux tried to include as much functionality as possible with very limited funds. Currently, Linux can run well on multiprocessor machines with very large main memory and disk space that is also very large, but still capable of operating in a useful amount of RAM smaller than 4 MB.
Linux Design Principles:
As a result of the development of PC technology, the Linux kernel is also becoming more complete in implementing UNIX functions. Fast and efficient are important design goals, but lately the concentration of Linux development has focused more on the third design goal, standardization. The POSIX standard consists of a collection of specifications from different aspects of operating system behavior. There are POSIX documents for ordinary operating system functions and for extensions such as processes for threads and real-time operations. Linux is designed to fit the relevant POSIX documents; there are at least two Linux distributions that have received POSIX official certification.
Because Linux provides a standard interface to programmers and users, Linux does not make many surprises to anyone who is familiar with UNIX. But the Linux programming interface refers to the UNIX SVR4 semantics rather than BSD behavior. A different collection of libraries is available to implement the BSD semantics in places where the two behaviors are very different.
There are many other standards in the UNIX world, but Linux’s full certification of other UNIX standards sometimes becomes slow because it is more often available at a certain price (not freely), and there is a price to pay if it involves certification of approval or compatibility of an operating system with most standards . Supporting broad applications is important for all operating systems so that the implementation of the standard is the main goal of developing Linux even though its implementation is not formally valid. In addition to the POSIX standard, Linux currently supports POSIX thread extensions and subsets of extensions for POSIX real-time process control.
Linux System Components:
The Linux system consists of three important code parts:
● Kernel: Responsible for maintaining all important abstractions of the operating system, including things like processes and virtual memory.
● System library: defines a set of standard functions where applications can interact with the kernel, and implements almost all operating system functions that do not require full rights to the kernel.
● System Utility: is a program that performs management work individually and specifically.
Kernel:
Although various modern operating systems have adopted a message-passing architecture for their internal kernel, Linux uses the historical UNIX model: the kernel was created as a single, monolithic binary. The main reason is to improve performance: Because all data structures and kernel code are stored in one address space, context switching is not needed when a process calls an operating system function or when a hardware interrupt is sent. Not only scheduling core and virtual memory code occupies this address space; all kernel code, including all device drivers, file systems, and network code, come in the same address space.
The Linux kernel forms the core of the Linux operating system. It provides all the functions needed to run the process, and is provided with system services to provide settings and protection for access to hardware resources. The kernel implements all the features needed to work as an operating system. However, if alone, the operating system provided by the Linux kernel is not at all similar to UNIX systems. It does not have many extra UNIX features, and the features provided are not always in the format expected by the UNIX application. The interface of the operating system that is visible to the running application is not maintained directly by the kernel. Instead, the application makes calls to the system library, which then invokes the operating system services that are needed.
System Library:
The system library provides many types of functions. At the easiest level, they allow applications to make requests to the kernel system services. Making a system call involves transferring controls from non-essential user mode to important kernel mode; the details of this transfer are different for each architecture. The library has the duty to collect system-call arguments and, if necessary, arrange those arguments in the special form needed to make system calls.
Libraries can also provide more complex versions of basic system calls. For example, the buffered file-handling functions of the C language are all implemented in the system library, which results in better control of file I / O than those provided by the basic kernel system call. The library also provides routines that have nothing to do with system calls, such as sorting algorithms, mathematical functions, and string manipulation routines. All functions needed to support the running of UNIX or POSIX applications are implemented in the system library.
System Utilities:
Linux systems contain many user-mode programs: system utilities and user utilities. The system utilities include all the programs needed to initialize the system, such as programs for configuring network devices or for loading kernel modules. Server programs that are running continuously are also included as system utilities; This kind of program manages user login requests, incoming network connections, and printer queues.
Not all standard utilities perform important system administration functions. The UNIX user environment contains a large number of standard utilities for doing daily work, such as making directory listings, moving and deleting files, or showing the contents of a file. More complex utilities can perform text-processing functions, such as compiling textual data or performing pattern-searches on text input. When combined, these utilities form the standard toolset expected by users on any UNIX system; even if it doesn’t perform any operating system functions, utilities are still an important part of a basic Linux system.
Key takeaway-
Just like Windows, iOS, and Mac OS, Linux is an operating system. In fact, one of the most popular platforms on the planet, Android, is powered by the Linux operating system. An operating system is software that manages all of the hardware resources associated with your desktop or laptop. To put it simply, the operating system manages the communication between your software and your hardware. Without the operating system (OS), the software wouldn?t function.
The following are the key distinctions between Linux and Windows
Sr. No. | Key | Linux | Windows |
1 | Open Source | Linux is an open source operating system that is completely free to use. | Windows isn't free to use and isn't open source. |
2 | Case sensitivity | The case of files in the Linux file system is important. | The Windows file system does not care about case. |
3 | Kernel type | Linux uses monolithic kernel. | Windows uses micro kernel. |
4 | Efficiency | When compared to Windows, Linux is more efficient in terms of operations. | In terms of operations, Windows is less efficient. |
5 | Path Separator | The forward slash is used in Linux as a path separator between directories. | The backward slash is used as a path separator in Windows. |
6 | Security | In comparison to Windows, Linux is quite secure. | When compared to Linux, Windows offers inferior security. |
The Linux operating system is a common variant of the UNIX operating system that aims to provide a free or low-cost operating system for personal computer users. It earned a reputation as a system that was both fast and effective. This is an incredibly comprehensive operating system, with features such as a graphical user interface (GUI), TCP/IP, the Emacs editor, and the X Window System. Debian, Ubuntu, Fedora, Red Hat Linux, SUSE Linux, Gentoo, Kali Linux, and Centos are the best Linux operating systems.
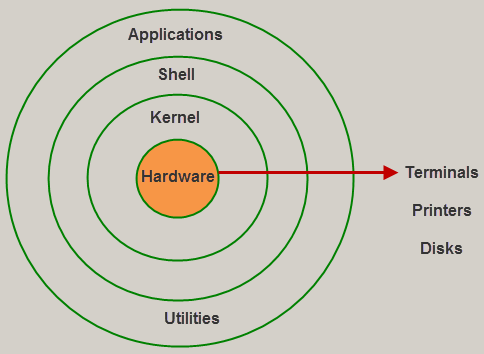
Fig 3: Linux architecture
Kernel
The kernel is the most important component of Linux. It is in charge of the operating system's main functions. It is made up of different modules that communicate directly with the hardware. Kernel provides the required abstraction for device or application programs to hide low-level hardware information.
The kernel is the central interface between a computer's hardware and its processes and is the most important part of a Linux operating system (OS). It interacts between the two, allowing for the most effective use of resources.
The following are the different forms of Kernels:
● Monolithic Kernel
● Microkernels
● Exo kernels
● Hybrid kernels
The kernel performs four functions:
- Memory management - Keep track of how much memory is being used for what, and where it is being stored.
- Process management - Determine can processes, when and for how long, should use the central processing unit (CPU).
- Device driver - Act as a liaison between the hardware and the processes.
- System call and security - Receive service requests from the processes.
Shell
The shell is a user-to-kernel interface that allows the kernel to provide services to the user. It receives user commands and performs the kernel's functions. The Shell can be used in a variety of operating systems and is divided into two categories: command-line shells and graphical shells.
A command-line interface is provided by command-line shells, while a graphical user interface is provided by graphical line shells. Despite the fact that both shells execute operations, graphical user interface shells are slower than command line interface shells.
An interface to the kernel that conceals the ambiguity of the kernel's functions from the user. The shell receives user commands and performs kernel functions.
Shells are divided into four categories:
● Korn shell
● Bourne shell
● C shell
● POSIX shell
Application (Utilities)
● It is in charge of performing specialized and individual tasks.
● Utility services provide the majority of an operating system's functionality to the user.
Logout
The logout command allows you to log out of your session programmatically. Causes the session manager to take the action specified right away.
Example-1:
To logout from current user session:
$ logout
Output:
No output on screen, current user session will be logged out.
Key takeaway:
The Linux operating system is a common variant of the UNIX operating system that aims to provide a free or low-cost operating system for personal computer users.
The kernel is the central interface between a computer's hardware and its processes and is the most important part of a Linux operating system.
The shell is a user-to-kernel interface that allows the kernel to provide services to the user.
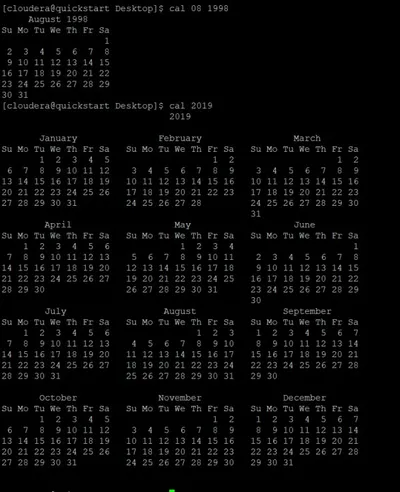
Cal command
The cal command in Linux is used to display the calendar for a particular month or for the entire year.
Syntax:
Cal [ [ month ] year]
Or
Cal [options] [month] [year]
Calendar other option
-1 - As a production, it shows a single month.
-3 - Prev/current/next month production is shown.
-s - The first day of the week is shown as Sunday.
-m - The first day of the week is shown as Monday.
-j - Julian dates are shown (days one-based, numbered from January 1).
-y - The current year's calendar is shown.
Example 1:
Cal -3 5 2008
The calendar for the months of April, May, and June in the year 2008 is shown.
Example 2:
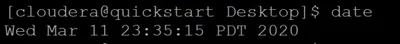
Date command
The date command is used to show the current date and time on the machine. The date command is often used to set the system's date and time.
Syntax:
$date
Example:
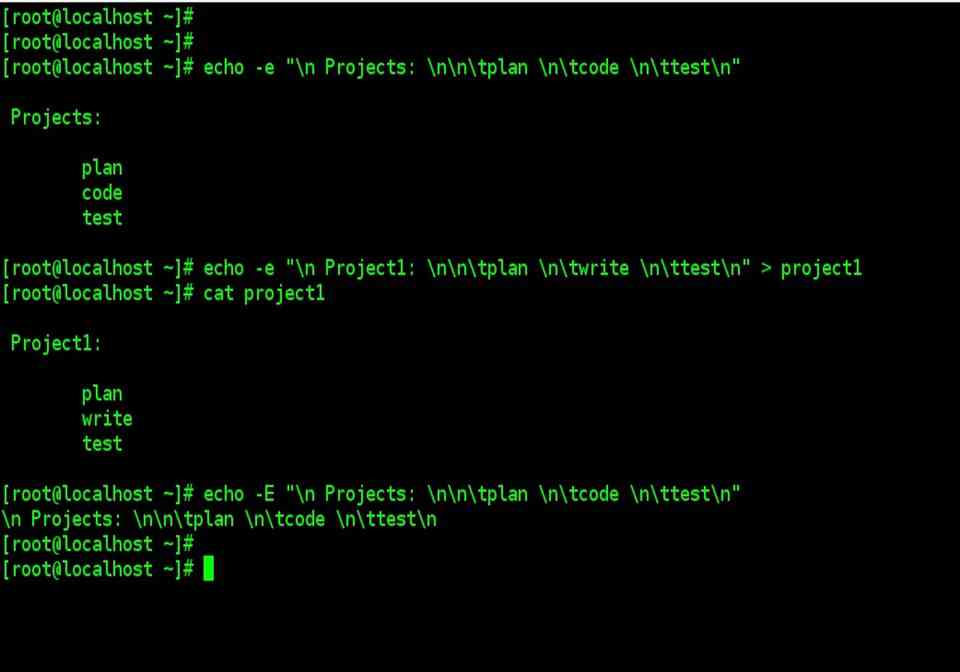
Echo command
In Linux, the echo command is used to show a line of text/string that has been passed as an argument. This is a built-in command that outputs status text to the screen or a file. It's mainly used in shell scripts and batch files.
Syntax:
Echo "enter text"
Example:
In this example, we use the -p command line option to enter the input on the same PROMPT:
Read -p PROMPT <variable_name>
Echo option
-n: The trailing newline should not be production.
-E: STRINGs would not be able to read certain sequences.
Example:
Who command
Who w – Command: UNIX maintains an account for all the current system. Because it is a multi-user system it is prudent for the user to be aware of other current users so that s/he can communicate with them if required. The user login details of all the current users by using the who command. The use of who command provides a list of all the current users in the three-column format by default, as shown follows:
$ who
Raj console Nov 19 09:35
Reena tty01 Nov 19 09:40
Priya tty02 Nov 19 09:41
The first column shows the name of the users, the second column shows the device names and the third column shows the login time. Some options like -H, -u and -T can be used with this command.
The H option provides headers for the columns and the -u option provides more details like idle time, PID and comments as shown in the example below.
$ who-Hu
NAME LINE TIME IDLE PID COMMENTS
Raj console Nov 19 09:35 # 32
Reena tty01 Nov 19 09:40 0:20 33
Priya tty01 Nov 19 09:41 0:40 34
If any terminal is idle If any terminal is idle (not active) for the last 1 minute, the information, that is, for how long that terminal is idle will be indicated on the IDLE column. Thus, 0:20 indicates that reena's terminal is IDLE for the last 20 minutes. This information will be useful to the system administrator. The PID indicates the process identification number. The self-login details of a user can be obtained as a single line output using am and i arguments along with the who command as follows.
$ who am i
Reena tty01 Nov 1909:40
Generally, the who command is used by the system administrator for monitoring terminals.
The w command is a quick way to see who is logged on and what they are doing.
Mkdir
The command mkdir means 'make directory.' You can construct a new directory anywhere in your system by using the mkdir command. Simply type "mkdir dir name>" (instead of dir name>, type the name of the new directory you want to create) and hit enter.
Syntax:
Mkdir <dirname>
Mkdir option
Option | Description |
Mkdir, -p, -parents | Add the directory, as well as its subdirectories. |
Mkdir, -v, -verbose | For each newly formed directory, print a message. |
Mkdir -m -mode=MODE | Set the permissions for entry. |
Rmdir
Removing Directories
The rmdir command can be used to remove directories as follows:
$rmdir dirname
$
If you want to delete a directory, make sure it's empty, which means there should be no files or subdirectories inside.
You can delete several folders at the same time by doing the following:
$rmdir dirname1 dirname2 dirname3
$
If the directories dirname1, dirname2, and dirname3 are empty, the command above removes them. If the rmdir command is effective, no output is generated.
Rmdir -p
This command deletes a directory and all of its subdirectories at the same time. The command 'rmdir -p' was used to remove all sub-directories.
Cd
To modify the current working directory in Linux, use the cd command ( i.e., in which the current user is working). 'Change directory' is represented by the letter "cd." In the Linux terminal, it's one of the most commonly used commands.
Syntax:
Cd <dirname>
It's one of the most critical and widely used commands in the Linux system, and you'll see it a lot. We can navigate through our system's directories with the aid of this order. We may go back to the previous directory, forward to the next directory, or anywhere else.
The cd command can be used for more than just changing directories. By specifying a valid absolute or relative path, you can change to any directory. The syntax is as follows:
$cd dirname
$
The name of the directory you want to change to is provided by dirname. For instance, the command
$cd /usr/local/bin
$
Changes to the /usr/local/bin directory. You may use the following relative path to cd to the directory /usr/home/amrood from this directory:
$cd ../../home/amrood
$
Listing Files
Use the following command to get a list of the files and folders in the current directory:
$ls
Here is an example of the above command's output:
$ls
Bin hosts lib res.03
Ch07 hw1 pub test_results
Ch07.bak hw2 res.01 users
Docs hw3 res.02 work
The -l option of the programme ls can be used to gain extra information about the files shown.
$ls -l
Total 1962188
Drwxrwxr-x 2 amrood amrood 4096 Dec 25 09:59 uml
-rw-rw-r-- 1 amrood amrood 5341 Dec 25 08:38 uml.jpg
Drwxr-xr-x 2 amrood amrood 4096 Feb 15 2006 univ
Drwxr-xr-x 2 root root 4096 Dec 9 2007 urlspedia
-rw-r--r-- 1 root root 276480 Dec 9 2007 urlspedia.tar
Drwxr-xr-x 8 root root 4096 Nov 25 2007 usr
Drwxr-xr-x 2 200 300 4096 Nov 25 2007 webthumb-1.01
-rwxr-xr-x 1 root root 3192 Nov 25 2007 webthumb.php
-rw-rw-r-- 1 amrood amrood 20480 Nov 25 2007 webthumb.tar
-rw-rw-r-- 1 amrood amrood 5654 Aug 9 2007 yourfile.mid
-rw-rw-r-- 1 amrood amrood 166255 Aug 9 2007 yourfile.swf
Drwxr-xr-x 11 amrood amrood 4096 May 29 2007 zlib-1.2.3
$
Here's the lowdown on each of the listed columns.
● The file type and permissions granted on the file are represented in the first column. The following is a list of all types of files and their descriptions.
● The number of memory blocks taken by the file or directory is represented in the second column.
● The owner of the file is represented by the third column. This is the name of the Unix user who made this file.
● The owner's group is represented in the fourth column. Every Unix user will be assigned to a group.
● The file size in bytes is represented in the fifth column.
● The date and time when this file was last created or updated are represented in the sixth column.
● The file or directory name is represented in the seventh column.
Metacharacters
In Unix, metacharacters have a special meaning. * and?, for example, are metacharacters. A question mark (?) matches a single character, while * matches 0 or more characters.
For Example −
$ls ch*.doc
Displays all files with names that begin with ch and conclude with.doc.
Ch01-1.doc ch010.doc ch02.doc ch03-2.doc
Ch04-1.doc ch040.doc ch05.doc ch06-2.doc
Ch01-2.doc ch02-1.doc c
* serves as a meta character that can be used with any other character. If you only want to see files that end in.doc, type the following command.
$ls *.doc
Hidden Files
The dot or the period character is the first character of an unseen file (.). The majority of these files are used by Unix programmes (including the shell) to hold configuration information.
Among the most common hidden files are the folders-
● .profile − The Bourne shell ( sh) initialization script
● .kshrc − The Korn shell ( ksh) initialization script
● .cshrc − The C shell ( csh) initialization script
● .rhosts − The remote shell configuration file
Specify the -a option to ls to list the hidden files.
$ ls -a
. .profile docs lib test_results
.. .rhosts hosts pub users
.emacs bin hw1 res.01 work
.exrc ch07 hw2 res.02
.kshrc ch07.bak hw3 res.03
$
● Single dot (.) − This represents the current directory.
● Double dot (..) − This represents the parent directory.
Creating Files
On any Unix system, the vi editor can be used to create ordinary files. All you have to do is type the following command:
$ vi filename
The command above will open a file with the specified name. To access the edit mode, hit the key i. You can start writing your information in the file once you're in edit mode, as seen in the following programme.
This is unix file....I created it for the first time.....
I'm going to save this content in this file.
When you've finished with the programme, follow these instructions.
● To exit the edit mode, press the esc key.
● To exit the file altogether, press the keys Shift + ZZ simultaneously.
In the current directory, a file named filename will be created.
$ vi filename
$
Editing Files
The vi editor can be used to edit an existing file. We'll go over how to open an existing file in a nutshell.
$ vi filename
You can enter edit mode by pressing the key I after the file has been opened, and then you can edit the file. If you want to move about within a file, you must first exit edit mode by pressing Esc. After that, you can navigate within a file by pressing the following keys:
● l key to move to the right side.
● h key to move to the left side.
● k key to move upside in the file.
● j key to move downside in the file.
As a result, you can put your cursor wherever you wish to modify using the keys listed above. After you've positioned yourself, press the I key to enter edit mode. After you've finished modifying your file, use Esc and then the two keys Shift + ZZ simultaneously to exit it fully.
Display Content of a File
The cat command can be used to view the contents of a file. Here is a simple sample of the content of the previously produced file:
$ cat filename
This is unix file....I created it for the first time.....
I'm going to save this content in this file.
$
Using the -b option with the cat command, you can see the line numbers as follows:
$ cat -b filename
1 This is unix file....I created it for the first time.....
2 I'
Copying Files
Use the cp command to make a copy of a file. The command's fundamental syntax is as follows:
$ cp source_file destination_file
The following is an example of how to make a copy of an existing file named filename.
$ cp filename copyfile
$
In your current directory, you will now notice another file named copyfile. The name of this file will be identical to the name of the original file.
Deleting Files
Use the rm command to remove an existing file. The fundamental syntax is as follows:
$ rm filename
A file may contain useful information, so proceed with caution. It's usually a good idea to use caution while using the Delete command. It is preferable to use the -i option in conjunction with the rm command.
The example below demonstrates how to entirely delete the existing file filename.
$ rm filename
$
You can remove multiple files at a time with the command given below −
$ rm filename1 filename2 filename3
$
Ls - list directory contents. The command to list our directories and files is ls, With options it can provide information about the size, type of file, permissions, dates of file creation, change and access.
Syntax:
Is [options] [argument]
Common Options: When no argument is used, the listing will be of the current directory. There are many useful options for the Is command. A listing of many of them follows. When using the command, string the desired options together preceded by "."
-a lists all files, including those beginning with a dot (.)
-d lists only names of directories, not the files in the directory
-F indicates type of entry with a trailing symbol:
Directories /
Sockets =
Symbolic links @
Executables*
-g displays Unix group assigned to the file, requires the -l option (BSD only)-or on an SVR4 machine, e.g. Solaris, this option has the opposite effect
-L if the file is a symbolic link, lists the information for the file or directory the link references, not the information for the link itself.
-I long listing: lists the mode, link information, owner. Size. Last modification time).
If the file is a symbolic link, an arrow (-->) precedes the pathname of the linked-to file.
The mode field is given by the -I option and consists of 10 characters. The first character is one of the following:
Character if entry is a:
d directory
- plain file
b block-type special file
c character-type special file
1 symbolic link
s socket
The next 9 characters are in 3 sets of 3 characters each. They indicate the file access permissions: the first 3 characters refer to the permissions for the user, the next three for the users in the UNIX group assigned to the file, and the last 3 to the permissions for other users on the system.
Designations are as follows:
r read permission
w write permission
x execute permission
-no permission
There are a few less commonly used permission designations for special circumstances. These are explained in the man page for ls.
Examples:
(i) To list the files in a directory:
$ ls
Demofiles frank linda
(ii) To list all files in a directory, including the hidden (dot) files try:
$ Is –a
..cshrc .history -plan .rhosts frank
...emacs .login .profile demofiles linda
(iii) To show the hidden files, but not the current directory) and (parent directory), use option -A.
(iv) To show all the files recursively, use -R option. When we do this from /, it shows all the unhidden files in the whole file system recursively.
$Is /etc/sysconfig/networking
Devices profiles
$Is -R -R/etc/sysconfig/networking
/etc/sysconfig/networking:
Devices profiles
/etc/sysconfig/networking/devices:
/etc/sysconfig/networking/profiles:
Default
/etc/sysconfig/networking/profiles/default:
(v) To get a long listing:
$ Is-al
Total 24
Drwxr-sr-x 5 workshop acs 512 Jun7 11:12 .
Drwxr-xr-x 6 root sys 512 May29 09:59 ..
-rw-------- 1 workshop acs 525 May20 21:29 .emacs
-rwxr-xr-x 1 workshop acs 238 May 14 09:44 .login
-rw-r—r-- 1 workshop acs 273 May 22 23:53 .plan
-rwxr-xr-x 1 workshop acs 413 May 14 09:36 .profile
Drwx------- 3 workshop acs 512 May 24 11:18 demofiles
Drwx------- 2 workshop acs 512 May 21 10:48 frank
Drwx------- 3 workshop acs 512 May 24 10:59 linda
Instead of doing the 'ls - and then the checking for the first character to determine the type of file. We can use -F which classifies the file with different special character for different kind of files.
$ ls -F
Desktop/ Documents/ Ubuntu-App@ firstfile Music/ Public/ Templates/
Thus in the above output
/-directory.
Nothing - normal file.
@- link file.
*- Executable file
(vi) $ Is-d Displays only directories
(vii) $ Is -r Displays files in reverse order.
(viii) $ Is -f Interprets each name as a directory, not a file.
Mv command
Mv - move a file: Rename a file with the move command, mv.
Syntax: mv (options] old_filename new_filename
Common Options:
-i interactive (prompt and wait for confirmation before proceeding)
-f don't prompt, even when copying over an existing target file (overrides-i)
Examples:
$ mvold_filename new_filename
i) We now have a file called new_filename and the file old filename is gone. Actually all we've done is to update name the directory table entry to give the file a new name
Ii) The contents of the file remain where they were.
Cat command
The command 'cat' is the most often used and powerful. It's regarded as one of the most commonly used commands. It can display a file's content, copy content from one file to another, concatenate the contents of multiple files, display the line number, display $ at the end of a line, and so on.
Syntax:
Cat [OPTION]... [FILE]..
To make a file, follow these steps:
Cat > <file name>
// Enter file content
To save the file, press the "CTRL+ D" keys. To see the contents of the file, run it like this:
Cat <file name>
Linux cat command usage
Option | Function |
Cat > [fileName] | To create a file. |
Cat [oldfile] > [newfile] | Copy material from an older file to a new one. |
Cat [file1 file2 and so on] > [new file name] | To combine the contents of several files into a single file. |
Cat -n/cat -b [fileName] | To display line numbers. |
Cat -e [fileName] | The $ character will be displayed at the end of each line. |
Cat [fileName] <<EOF | Used to indicate the end of a page. |
Cp command
'cp' stands for copy. To copy a file or a directory, use the 'cp' command.
Syntax:
To copy in the same directory:
Cp <existing file name> <new file name>
Cp Options
Option | Function |
Cp -r | To duplicate a directory and all of its subdirectories.. |
Cp file1 file 2 directory name | Multiple files or directories in a directory are copied. |
Cp -backup | Before overwriting an existing file, make a backup. |
Cp -i | Asks for confirmation. |
Cp -l | To create a file with a hard link. |
Cp -p | Preserves a file's attribute. |
Cp -u -v | To ensure that the source file is older than the destination file. |
Rm command
'rm' stands for 'remove.' To remove a file, use this command. Unlike other GUIs, the command line does not feature a recycling bin or trash to recover files. As a result, exercise extreme caution when using this command. When you delete a file, it is permanently deleted.
Syntax:
Rm <file name>
Rm Options
Option | Description |
Rm *extension | Deletes files with the same extension. |
Rm -r or R | To recursively erase a directory. |
Rm -i | Interactively delete a file. |
Rm -rf | Forcefully delete a directory. |
A file type is used to describe the type of data that is saved in a file. Linux recognizes seven different file forms. Regular files, Directory files, Link files, Character special files, Block special files, Socket files, and Named pipe files are all examples of file types.
A list of these file types can be found in the table below.
/-----------------------------------------------\
|-|Regular File|
|d|Directory|
|l|Symbolic Link|
|b|Block Special File|
|c|Character Special File
|p|Named Pipe|
|s|Socket|
\-----------------------------------------------/
Regular file
Text, audio, video, images, scripts, and programs are only some of the content types that can be stored in regular or ordinary files. There are a plethora of content styles to choose from. Standard files, with or without an extension, can be built in Linux.
An extension is a collection of characters added to the end of a file name to give it a unique identity or to group it with other files of the same type of material. Files of various content types often use well-known file extensions for ease of identification and processing.
Despite the fact that the Linux file system does not need file extensions, you can still use them. They assist us in recognizing the different types of content contained in files. If a file's extension is.mp4, for example, you can assume it's a video file.
The /etc/mime.types file contains a full list of content types and file extensions that your Linux framework supports. The MIME (Multipurpose Internet Mail Extensions) standard assigns file content types a standard designation and classification.
To access the contents of this file, use any standard file reading command.
Directory
File systems use folders to arrange data in a hierarchy. Directories are similar to files, but instead of storing data, they keep track of where other files are located. Directory entries are used to store the location of files stored in the directory. A single file's name and location are stored in each directory entry.
The Linux file system begins with the directory /, also known as the root directory. This directory is where all files and directory files are made. Each directory, with the exception of the root directory, has a parent directory.
Symbolic link
We can use a file with a different filename and from a different location with link files. We use connecting files for this. A connection file is a file that contains a reference to another file. A hard connection and a symbolic or soft link are the two forms of connections.
A hard connection makes a copy of the original file that is identical to it. A hard connection to a directory or file on another filesystem is not possible. A reference to the original file is created by a soft or symbolic connection. A soft connection to a directory or file on another filesystem can be formed.
Block or Character special file
Block Special Files are used to communicate with hardware in blocks of data of 512 bytes, 1024 bytes, or 2048 bytes, depending on the hardware.
Hard drives, printers, displays, terminal emulators, and CD/DVD drives are all treated as special files in Linux. This ensures that a program can view and use files and devices in the same way that a user can. This feature makes it simpler and more versatile to build programs in Linux.
The /dev directory is where Linux stores all special files and system files. A character special file and a block special file are the two types of special files. A character special file represents a computer, such as a monitor or printer, that transfers data in bytes. A block special file represents a computer, such as a hard drive, that transfers data in blocks.
One character at a time is communicated with hardware using the Character Special File. Block and Character Special Files are usually found in the /dev directory.
Named pipe
A named pipe is a file that transfers data from one process to another.
The data that is passed between one process writing data into a named pipe and another process reading data from the named pipe is not stored in the named pipe. The mkfifo command can be used to build a named pipe.
We can use Linux to send the output of some process or command as the input to another process or command. The pipe is the name for this element. Only when both processes are initiated by the same user and are in the same parent process space do pipes function.
Standard pipes will not function if processes are run under different user names and permissions. Named pipes are used in these situations. Named pipes are similar to regular pipes, but they can be accessed via the filesystem.
The empty pipe files are known as named pipe files. Named pipe files are processed by the kernel without being written to the file system. Pipe files with names can be found anywhere in the file system. The FIFO (First In First Out) files are also known as pipe files.
Socket
The Socket File is a stylized inter-process communication mechanism.
It is highly uncommon for a user or even a system administrator to build a socket directly.
A socket is a data-exchange communication endpoint used by applications. When an application needs to communicate with another application, it connects to the application's socket.
A socket is used for any application that offers services to other applications or remote clients. Each socket has an IP address and port number associated with it, allowing it to accept connections from clients.
For example, if a local system application needs to communicate with a remote system application, it connects to that application's socket using the IP address and port number associated with that socket.
Sockets are very difficult to understand. Socket files are used by Linux to make communication between local applications easier. Socket files allow local device applications to share data without having to go through the complicated networking and sockets processes.
Socket files are files that use a file name instead of an IP address and port number as their address. To allow inter-process communication between local applications, socket files use the sendmsg() and recvmsg() system calls.
Key takeaway:
Directories are similar to files, but instead of storing data, they keep track of where other files are located.
Block and Character Special Files are usually found in the /dev directory.
A named pipe is a file that transfers data from one process to another.
A socket is used for any application that offers services to other applications or remote clients.
The Socket File is a stylized inter-process communication mechanism.
Chmod: Changing file permissions: The command name chmod stands for "change mode", and it is used to define the way a file can be accessed. Chmod (change mode) is one of the most frequently used commands in unix or linux operating system. The chmod command is used to change the file or directory access permissions.
Syntax:
Chmod [options] permissions filename
There are three different permissions. They are:
Read (4): Permitted to read the contents of the file. In case of directory, you can view all the files and subdirectories in that directory
Write (2): Permitted to write to the file. In case of directory, you can create files and sub-directories
Execute (1): Execute the file as a program/shell script. In case of directory, You can enter into that directory.
Here in the above, the numbers in the brackets represents the numeric values for the corresponding permissions. If you want to have a combination of permissions add the required numbers. For example, for read and execute, it is 4+1= 5.
Chmod [options]
-R: recursively change the permissions of a directory.
-v: Verbose
Chmod Examples in Linux / Unix:
1. Give read, write and execute permissions to everyone. Read, write and execute: 4+2+1=7
$ chmod 777 sample.sh
In the above example, you can see that the permissions are specified with a three digit number. The first digit is for user permissions, second is for group and third is for others permission. This type of representation is called octal representation. Alternatively, you can use the symbolic representation to give the permissions.
Chmod ugo+rwx sample.sh
We will see more details about the symbolic representation later.
2. Give read permission to user, write permission to group and execute permission to others
$ chmod 421 sample.sh
3. Recursive permissions to directory
To give read and write permissions to all the users to a directory (including files and subdirectories) use the recursive option -R.
Chmod -R 666 /dir
Symbolic Representation of Permissions: The following symbols are used to represent the users, groups and others:
● u: User
● g: Group
● o: Others
● a: All (user, group and others)
The following symbols represent the permissions:
● r: read
● W: write
● X: execute
The following symbols represent the permissions grant or revoke:
● + : Additional permissions. Selected permissions are added.
● - : Revoke the permissions. Selected permissions are revoked.
● = : Specific permissions. Only selected permissions are assigned.
Examples
1. Remove write permission from group
$ chmod g-w sample.sh
This will only removes the write permission for the group.
2. Add new permission execute to others
$ chmod o+x sample.sh
In addition to the existing permissions, this will add execute permission to others.
3. Give only read permissions to the user
$chmod u=w sample.sh
This will remove the existing permissions to the user and gives only write permission to the user.
The first n lines of the supplied text files are displayed.
We can filter / read the first or top lines or row of data, as the name implies. It will read the first 10 lines or records of the given data by default. If we need to read additional lines, we must use the "-n" option to define the number of lines that we need to read.
Syntax:
Head [-number_of_lines_to_print] [path]
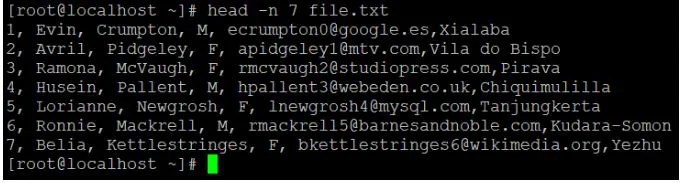
Head -n 7 file.txt
Explanation:
● We have a data sample file with ten records in it.
● The default "head" command is now being used to read the data file.
● We'll use the "-n" option to read the number of lines of records if we need to read or get data other than the default value.
Cat file.txt
Output
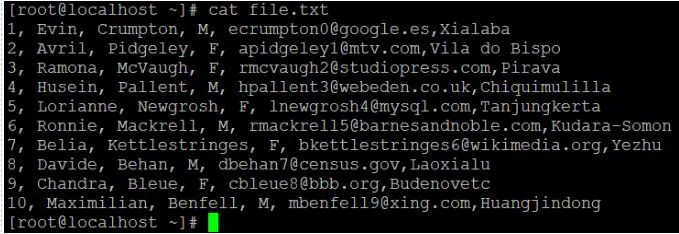
Head file.txt
Output:

Head -n 7 file.txt
Output:
Tail
We'll use the tail command to collect data from the bottom of the file if we need it. It will read the latest 10 lines or records of the given data by default. If we need to read additional lines, we must use the "-n" option to define the number of lines that we need to read.
Syntax:
Tail <file name>
Code:
Tail -n 3 file.txt
Explanation:
● To read the data file, we use the default "tail" command.
● We'll use the "-n" option to read the number of lines of records if we need to read or get data other than the default value.
Tail file.txt
Output:
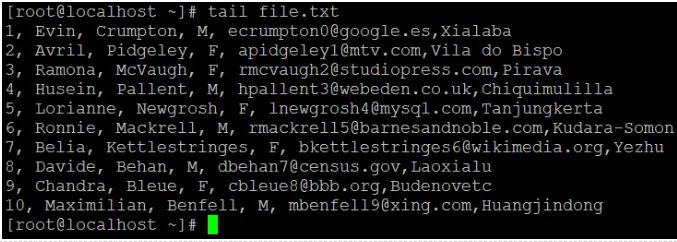
Tail -n 4 file.txt
Output:

Sort
Sorting text lines alphabetically or numerically is done with the sort command. The lines in the food file are sorted in the following example.
$sort food
Afghani Cuisine
Bangkok Wok
Big Apple Deli
Isle of Java
Mandalay
Sushi and Sashimi
Sweet Tooth
Tio Pepe's Peppers
$
By default, the sort command groups text lines alphabetically. There are numerous choices for controlling the sorting.
Sr.No. | Description |
1 | -n Sorts numerically (example: 10 will sort after 2), ignores blanks and tabs. |
2 | -r Reverses the order of sort. |
3 | -f Sorts upper and lowercase together. |
4 | +x Ignores first x fields when sorting. |
A pipe can be made up of more than two commands. Using grep and a prior pipe example, we can further sort the files updated in August by size.
The commands ls, grep, and sort make up the following pipe.
$ls -l | grep "Aug" | sort +4n
-rw-rw-r-- 1 carol doc 1605 Aug 23 07:35 macros
-rw-rw-r-- 1 john doc 2488 Aug 15 10:51 intro
-rw-rw-rw- 1 john doc 8515 Aug 6 15:30 ch07
-rw-rw-rw- 1 john doc 11008 Aug 6 14:10 ch02
$
This pipe organises all of the files in your August-modified directory by size and prints them on the terminal screen. The +4n sort option skips four fields (fields are separated by blanks) before sorting the lines numerically.
Grep
The grep command looks for lines that match a pattern in a file or files. The syntax is as follows:
$grep pattern file(s)
The term "grep" comes from the command g/re/p in the ed (a Unix line editor), which means "globally search for a regular expression and print all lines containing it."
A regular expression is a combination of plain text (for example, a word) and special characters that are used to match patterns.
The most basic application of grep is to seek for a single-word pattern. It can be used in a pipe to send to the standard output just the lines of the input files that contain a specific string. If you don't give grep a filename to read, it reads its standard input; that's the way all filter programs work −
$ls -l | grep "Aug"
-rw-rw-rw- 1 john doc 11008 Aug 6 14:10 ch02
-rw-rw-rw- 1 john doc 8515 Aug 6 15:30 ch07
-rw-rw-r-- 1 john doc 2488 Aug 15 10:51 intro
-rw-rw-r-- 1 carol doc 1605 Aug 23 07:35 macros
$
You can use the grep command with a number of different arguments.
Sr.No. | Option & Description |
1 | -v All lines that do not match the pattern are printed. |
2 | -n The matching line and its line number are printed. |
3 | -l Only the names of files with matching lines are printed (letter "l"). |
4 | -c Only the number of matching lines is printed. |
5 | -i Matches upper and lowercase letters. |
Vi stands for visual editor. It is a full screen editor. It is available with almost all the UNIX variants. Vi editor became famous because of its full screen editing capabilities and many other visual options. Vi editor is available under Linux in the form of vim (vi improved). It uses the terminal display as a window to the buffer and 25 lines can be displayed at all times. All unused lines of a file are marked by a -(tilde) called as empty buffer line flag. The last line is reserved for commands. The vi editor works in three modes that are:
1. The Command mode: This is the mode into which the user gets into as soon as the vi command is invoked from shell by using vi <filename>. In this mode all the keys pressed by the user are interpreted to be the editor commands. The keys that are pressed are not displayed on the screen. The user can get into the input mode by giving o, O, r, R, i, I, s, S, a, A commands.
2. The input mode: This mode is also known as insert mode. This mode permits the insertion of new text, appending to the existing text and replacement of the text. To exit or switch from this mode to command mode press Esc key.
3. The ex mode: This mode is also known as last line mode and allows user to use the commands in the bottom line (command line) on the vi screen. From the command mode the user can get in to the ex mode by typing the colon character (). Here this character is displayed in the command line. A colon (:) indicates that the editor is now in the ex mode. The user can get back to the command mode by using the Enter key

1. The input mode command:
(i) Insert (i, I):
i - Insert text to the left of the cursor position. Existing text will be shifted right
This is a file
Isimple [Esc]
This is a simple file
I- Insert text at the beginning of the line.
This is a file
I/*[Esc]
/*This is a simple file
(ii) Append (a, A):
a- Append text to the right of the cursor position. Existing text will be shifted right.
This is a file
Isimple [Esc]
This is a simple file
A- Appends text at end of the line.
This is a file
A*/ [Esc]
This is a simple file */
(iii) Open a line (o, O):
o- Opens a new line below the current line.
Hello
How
You
Oare [Esc]
Hello
How
Are
You
O-Opens a new line above the current line.
Hello
How
You
Osumit [Esc]
Hello
Sumit
How
Are
You
(iv) Replace (r, R, s, S):
r- Replace single character.
This is a dile
Rf
This is a file
R-Replaces all text on the right of the cursor position.
This is a simple file
Rdevice[Esc]
This is a device file
s- Replace one character with many.
This is a device file
Sone[Esc]
This is one device file
S - Replaces the entire line irrespective of the cursor position (existing line disappears).
2. The ex-mode command:
(i) :w- To save a file and remain in the editing mode.
: w
"ss", 8 lines, 150 characters
The message shows the name of the file i.e. ss along with the number of lines and character saved. We can also specify another file in the last line (In MS word, save as).
:w ss1
"ss1", 8 lines, 150 characters
If ssl is already exist then we use exclamation mark (!) with w
:w! ss1
Content of ss will be overwrite to ssl.
If we want to save fifth line to the another file then we will use
: 5w ss1
If we want to save ten to fifteenth line to the another file then we will use
: 10, 15w ss1
There are two symbols used with w have special significance - The dot (,) and dollar ($). The dot (.) represents the current line and dollar ($) represent the last line.
:.w ss1 //saves current line
: $w ss1 //saves last line
: .,$ ss1 //saves current line through end
(ii): q - Aborting editing : It is also possible to abort the editing process and quitting from the editing mode without saving the content with the help of : q command.
: q[enter]
$_
Vi also has a safety mechanism that prevents we from aborting accidentally if we have modified the file. The following message will be displayed.
No write since last change
If the buffer has been changed and we still want to abandon the changes then we will use
:q! //ignores all changes made and quits
(iii): wq - saving and quitting : We can also use: wq to save and exit from vi editor.
:wq ss1
(iv):sh - Escapes to UNIX shell:
Vi editor provide temporary escape to the shell to run the cc command.
:sh
This return a shell prompt execute cc or any other command here and then return to the editor using exit or
[Ctrl - d]
/* don't execute vi command once again - an undesirable situation */
3. The command mode command:
A command mode command doesn't on the screen but simply performs a function.
k- Moves cursor up
i- Move cursor down
h - Moves cursor left
1 - Moves cursor right
The repeat factor can be used as a command prefix with all these four commands. Thus 4k command moves the cursor 4 lines up and 20h takes it 20 characters to the left
b - Moves back to the beginning of word
w - Moves forward to the beginning of word
e - Moves forward to the end of word
0 - Moves cursor to extreme left
$ - Moves cursor to extreme right
|(pipe) - Moves cursor to specific column
The repeat factor can also be used with this command. Thus 5b takes the cursor 5 words back and 3w takes the cursor three words forward.
[Ctrl – f]- Scroll forward
[Ctrl - b]- Scrolls backward
[Ctrl – d]- Scrolls half page forward
[Ctrl – u]- Scrolls half page backward
The repeat factor can also be used with this command. Thus 10[Ctrl – f], to scroll 10 pages forward. When we start vi editor, it displays the total number of lines in the last line. To know the current line number we will use.
[Ctrl – g]- To know the current line number
"file1" [read only] line 67 of 233 -32%-
The cursor is on line 67 i.e. (32% of 233)
(i) G- Move to the specific line number (absolute movement)
23G //Goes to line number 23
1G //Goes to line number 1
G //Goes to end of file
(ii) x - Deletes a single character: The character under the cursor gets deleted and the text on the right shifts left to fill up the space. A repeat factor also used here. Thus 4x deletes the current character as well as three characters from the right
Dd - Deletes an entire line:
Dd command deletes a current line where cursor can be anywhere in the line. A repeat factor can also be used here, thus 4dd deletes the current line as well as three lines below.
p- Put character on the right of the cursor
When we delete parts of line
P- Put character on the left of the cursor
e.g.
If we want to correct sdtio.h to stdio.h, then we will have to transpose the characters d and t, i.e. delete the d and put it after t. Move your cursor to the d in sdtio.h then press.
x //sdtio.h becomes stio.h :cursor on t
p //d put on right : stio.h becomes stdio.h
p - Put character on the above of the current line When we delete an entire line
P- Put character on the below of the current line
p and P place text on the left and right only when you delete parts of lines. But the same keys get associated with above and below when we delete complete line.
(ii) Yanking (copying) the text:
Yh - Yank a character to the left of the current cursor position.
3yh - Yank three characters to the left of the current cursor position.
Yw - Yank from the current character to the next word.
Yor yy - Yanks the current line.
y2k - Yank current line and two lines above the current line.
3Y or 3yy - yank three lines including the current line.
Y$ - Yank till the end of the current line.
y) - Yank from the current character to next sentence.
y} - Yank from the current character till the end of the paragraph.
3y - yank three character.
(iii) Joining the line:
J - To join the current line and the line following it.
4J - To join the current line with 3 lines following it.
(iv) Undoing last editing instruction:
u - Undo the most recent single editing change by restoring the position before the change.
U-Undo all the changes before move away from the line.
[Ctrl -r] This command is used to redo the undone actions.
The repeat factor also works here. 10u is completely reversed with 10[Ctrl -r]
(v) Searching for a pattern (/ or?):
/pattern - Searches forward for pattern.
?pattern - Searches backward for pattern.
Eg.
If we are looking for the string echo, Then use
/echo @
The search begins forward to position the cursor on the first instance of the word, vi searches the entire line, so if the pattern can't be located till the end of the file is reached the search wraps around to resume from the beginning of the file. If the search still fails, vi respond with the message pattern not found
?echo @ (same like /)
The search begins backward direction.
Repeating the last pattern search:
n - Repeats search in same direction along which previous search was made.
N - Repeats search in opposite direction to that along which previous search
Was made.
Command mode
You can use this mode to conduct administrative activities including saving files, running commands, moving the cursor, cutting (yanking) and pasting lines or words, and finding and replacing. Whatever you type in this mode is regarded as a command.
Vi starts in command mode by default. You must be in insert mode to enter text, which you may do by typing i. To exit the insert mode, press the Esc key, which will return you to command mode.
You can move around by pressing the arrow keys or the vi movement keys, as shown below:
h | Left |
j | Down |
k | Up |
l | Right |
Insert mode
This mode allows you to add text to the document. In this mode, whatever you type is treated as input and saved to the file.
You can insert or append text in the input mode. In command mode, press I to insert text before the cursor's current position. Similarly, you can use a to append after the cursor. Keep in mind that you can't use the cursor keys in this mode. When you're through typing, press Esc to return to command mode.
Ex mode
This mode is used to enter commands on the command line at the bottom of the vi editor. Press the escape key to enter Ex command mode, then type: (colon). To save the contents of the vi editor and exit it, hit wq after the: (colon). Wq.
Ex mode is a command mode that has been extended. To get started, press Esc, then: (the colon). At a colon prompt, the pointer will move to the bottom of the screen. Enter:w to create a new file and:q to close it. By entering:wq, you can save and exit at the same time. If you're done with your file, though, Shift-z-z from command mode is usually more convenient.
References:
1. Operating System Concepts – Silberschatz, Galvin and Gagne
2. Operating System By Godbole
3. Linux Bible 9th Edition by Christoper Negus ISBN :978-1-118-99987-5
4. Ball, Using Linux, PHI, 1998. ISBN-10: 0789716232
5. UNIX: Concepts and Applications Das (4th Ed), TMH, 2006 ISBN 13: 9780070635463
Unit - 1
Introduction to Operating System
An Operating system (OS) is a software which acts as an interface between the end user and computer hardware. Every computer must have at least one OS to run other programs. An application like Chrome, MS Word, Games, etc needs some environment in which it will run and perform its task. The OS helps you to communicate with the computer without knowing how to speak the computer's language. It is not possible for the user to use any computer or mobile device without having an operating system.
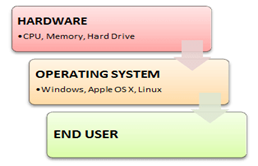
Fig 1: Operating system
Features of Operating System
Here is a list commonly found important features of an Operating System:
● Protected and supervisor mode
● Allows disk access and file systems Device drivers Networking Security
● Program Execution
● Memory management Virtual Memory Multitasking
● Handling I/O operations
● Manipulation of the file system
● Error Detection and handling
● Resource allocation
● Information and Resource Protection

Types of Operating system
● Batch Operating System
● Multitasking/Time Sharing OS
● Multiprocessing OS
● Real Time OS
● Distributed OS
● Network OS
● Mobile OS
Batch Operating System
Some computer processes are very lengthy and time-consuming. To speed the same process, a job with a similar type of needs are batched together and run as a group.
The user of a batch operating system never directly interacts with the computer. In this type of OS, every user prepares his or her job on an offline device like a punch card and submit it to the computer operator.
Multi-Tasking/Time-sharing Operating systems
Time-sharing operating system enables people located at a different terminal(shell) to use a single computer system at the same time. The processor time (CPU) which is shared among multiple users is termed as time sharing.
Real time OS
A real time operating system time interval to process and respond to inputs is very small. Examples: Military Software Systems, Space Software Systems.
Distributed Operating System
Distributed systems use many processors located in different machines to provide very fast computation to its users.
Network Operating System
Network Operating System runs on a server. It provides the capability to serve to manage data, user, groups, security, application, and other networking functions.
Mobile OS
Mobile operating systems are those OS which is especially that are designed to power smartphones, tablets, and wearables devices.
Some most famous mobile operating systems are Android and iOS, but others include BlackBerry, Web, and watchOS.
Difference between Firmware and Operating System
Firmware | Operating System |
Firmware is one kind of programming that is embedded on a chip in the device which controls that specific device. | OS provides functionality over and above that which is provided by the firmware. |
Firmware is programs that been encoded by the manufacture of the IC or something and cannot be changed. | OS is a program that can be installed by the user and can be changed. |
It is stored on non-volatile memory. | OS is stored on the hard drive. |
Difference between 32-Bit vs. 64 Bit Operating System
Parameters | 32. Bit | 64. Bit |
Architecture and Software | Allow 32 bit of data processing simultaneously | Allow 64 bit of data processing simultaneously |
Compatibility | 32-bit applications require 32-bit OS and CPUs. | 64-bit applications require a 64-bit OS and CPU. |
Systems Available | All versions of Windows 8, Windows 7, Windows Vista, and Windows XP, Linux, etc. | Windows XP Professional, Vista, 7, Mac OS X and Linux. |
Memory Limits | 32-bit systems are limited to 3.2 GB of RAM. | 64-bit systems allow a maximum 17 Billion GB of RAM. |
The advantage of using Operating System
● Allows you to hide details of hardware by creating an abstraction
● Easy to use with a GUI
● Offers an environment in which a user may execute programs/applications
● The operating system must make sure that the computer system convenient to use
● Operating System acts as an intermediary among applications and the hardware components
● It provides the computer system resources with easy to use format
● Acts as an intermediator between all hardware's and software's of the system
Disadvantages of using Operating System
● If any issue occurs in OS, you may lose all the contents which have been stored in your system
● Operating system's software is quite expensive for small size organization which adds burden on them. Example Windows
● It is never entirely secure as a threat can occur at any time
Key Takeaway:
An operating system is a software which acts as an interface between the end user and computer hardware. Operating systems were first developed in the late 1950s to manage tape storage.
The kernel is the central component of a computer operating systems. The only job performed by the kernel is to the manage the communication between the software and the hardware
Need of Operating System
● OS as a platform for Application programs: The operating system serves as a foundation for other programmes known as application programmes to execute on. These application programmes make it easier for consumers to complete a given task. It serves as a link between the user and the computer. It is created in such a way that it can operate, control, and execute various computer applications.
● Managing Input-Output unit: The computer's operating system also allows it to manage its own resources, such as memory, display, keyboard, printer, and so on. Effective usage of these resources necessitates resource management. The operating system manages the system's input-output resources and distributes them to users or programmes based on their needs.
○ Consistent user interface: The operating system offers the user with an easy-to-use user interface, allowing the user to focus on the content and be productive as quickly as possible without having to learn a new UI each time. The operating system provides templates and UI components to make using a computer as simple as possible for the user.
● Multitasking: Memory is managed by the operating system, which allows several programmes to execute in their own space and even connect with one another via shared memory. Users benefit from multitasking since they can complete multiple tasks on a computer at the same time.
● Booting: The process of starting the computer is known as booting. When the CPU is turned on for the first time, there is nothing in the memory. So, in order to turn on the computer, we must first load the operating system into main memory. As a result, booting is the process of loading the operating system into main memory in order to start the computer. As a result, the operating system aids in the initialization of the computer when the power is turned on.
● Platform for other application software: Different application programmes are required by users to complete particular jobs on the system. The operating system (OS) supervises and regulates these programmes to ensure that they run smoothly. To put it another way, it serves as a link between the user and the programmes.
● Manages the memory: It aids in the management of the computer's main memory. It also allocates and deallocates memory for all programmes and tasks.
● Manages the system files: It aids in the organisation of files on the computer. All of the data on the system is stored in files, as we all know. It makes working with the files simple.
● Provides Security: It uses authorisation to keep the system and applications safe. As a result, the operating system protects the system.
Functions of Operating System
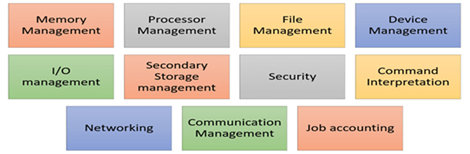
Fig 2: Function of an Operating System
In an operating system software performs each of the function:
- Process management: Process management helps OS to create and delete processes. It also provides mechanisms for synchronization and communication among processes.
- Memory management: Memory management module performs the task of allocation and deallocation of memory space to programs in need of this resources.
- File management: It manages all the file-related activities such as organization storage, retrieval, naming, sharing, and protection of files.
- Device Management: Device management keeps tracks of all devices. This module also responsible for this task is known as the I/O controller. It also performs the task of allocation and deallocation of the devices.
- I/O System Management: One of the main objects of any OS is to hide the peculiarities of that hardware devices from the user.
- Secondary-Storage Management: Systems have several levels of storage which includes primary storage, secondary storage, and cache storage. Instructions and data must be stored in primary storage or cache so that a running program can reference it.
- Security: Security module protects the data and information of a computer system against malware threat and authorized access.
- Command interpretation: This module is interpreting commands given by the and acting system resources to process that commands.
- Networking: A distributed system is a group of processors which do not share memory, hardware devices, or a clock. The processors communicate with one another through the network.
- Job accounting: Keeping track of time & resource used by various job and users.
- Communication management: Coordination and assignment of compilers, interpreters, and another software resource of the various users of the computer systems.
The UNIX operating system is a set of programs that act as a link between the computer and the user. The computer programs that allocate the system resources and coordinate all the details of the computer's internal is called the operating system or kernel.
Users communicate with the kernel through a program known as the shell. The shell is a command line interpreter; it translates commands entered by the user and converts them into a language that is understood by the kernel.
Unix was originally developed in 1969 by a group of AT&T employees at Bell Labs, including Ken Thompson, Dennis Ritchie, Douglas Mcllroy, and Joe Ossanna.
There are various Unix variants available in the market. Solaris Unix, AIX, HP Unix and BSD are few examples, Linux is also a flavor of Unix which is freely available.
Several people can use a UNIX computer at the same time, hence UNIX is called a multiuser system. A user can also run multiple programs at the same time; hence UNIX is called multitasking.
A Brief History of UNIX
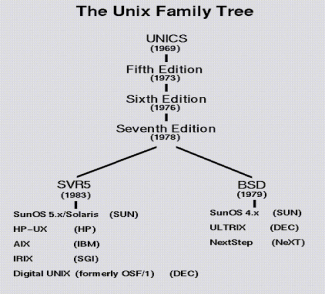
Key takeaway
The UNIX operating system is a set of programs that act as a link between the computer and the user. The computer programs that allocate the system resources and coordinate all the details of the computer's internal is called the operating system or kernel.
What is Linux?
From smartphones to cars, supercomputers and home appliances, home desktops to enterprise servers, the Linux operating system is everywhere.
Linux has been around since the mid-1990s and has since reached a user-base that spans the globe. Linux is actually everywhere: It?s in your phones, your thermostats, in your cars, refrigerators, Roku devices, and televisions. It also runs most of the Internet, all of the world’s top 500 supercomputers, and the world’s stock exchanges.
But besides being the platform of choice to run desktops, servers, and embedded systems across the globe, Linux is one of the most reliable, secure and worry-free operating systems available. Here is all the information you need to get up to speed on the Linux platform.
Just like Windows, iOS, and Mac OS, Linux is an operating system. In fact, one of the most popular platforms on the planet, Android, is powered by the Linux operating system. An operating system is software that manages all of the hardware resources associated with your desktop or laptop. To put it simply, the operating system manages the communication between your software and your hardware. Without the operating system (OS), the software wouldn?t function.
The Linux operating system comprises several different pieces:
● Bootloader – The software that manages the boot process of your computer. For most users, this will simply be a splash screen that pops up and eventually goes away to boot into the operating system.
● Kernel – This is the one piece of the whole that is actually called ?Linux?. The kernel is the core of the system and manages the CPU, memory, and peripheral devices. The kernel is the lowest level of the OS.
● Init system – This is a sub-system that bootstraps the user space and is charged with controlling daemons. One of the most widely used init systems is systemd? which also happens to be one of the most controversial. It is the init system that manages the boot process, once the initial booting is handed over from the bootloader (i.e., GRUB or GRand Unified Bootloader).
● Daemons – These are background services (printing, sound, scheduling, etc.) that either start up during boot or after you log into the desktop.
● Graphical server – This is the sub-system that displays the graphics on your monitor. It is commonly referred to as the X server or just X.
● Desktop environment – This is the piece that the users actually interact with. There are many desktop environments to choose from (GNOME, Cinnamon, Mate, Pantheon, Enlightenment, KDE, Xfce, etc.). Each desktop environment includes built-in applications (such as file managers, configuration tools, web browsers, and games).
● Applications – Desktop environments do not offer the full array of apps. Just like Windows and macOS, Linux offers thousands upon thousands of high-quality software titles that can be easily found and installed. Most modern Linux distributions (more on this below) include App Store-like tools that centralize and simplify application installation. For example, Ubuntu Linux has the Ubuntu Software Center (a rebrand of GNOME Software? Figure 1) which allows you to quickly search among the thousands of apps and install them from one centralized location.
Features of Linux
Some of the most significant features of the Linux Operating System are mentioned below.
● Portable - Software's portability refers to its ability to run on various types of hardware in the same way. The Linux kernel and application programs can be installed on virtually any hardware platform.
● Open Source - Linux is a community-based programming project with freely available source code. Multiple teams collaborate to improve the capabilities of the Linux operating system, which is constantly changing.
● Multi-User - Linux is a multiuser system, which means that multiple users can share system resources such as memory, ram, and application programs.
● Multiprogramming - Linux is a multiprogramming method, which means it can run several programs at the same time.
● Hierarchical File System - System files and user files are organized in a common file structure in Linux.
● Shell - Linux has a special interpreter program that can be used to run operating system commands. It can be used to perform a variety of tasks, such as calling application programs.
● Security - User security is provided by Linux by authentication features such as password protection, restricted access to sensitive files, and data encryption.
Why use Linux?
This is the one question that most people ask. Why bother learning a completely different computing environment, when the operating system that ships with most desktops, laptops, and servers works just fine?
To answer that question, I would pose another question. Does that operating system you’re currently using really work ?just fine?? Or, do you find yourself battling obstacles like viruses, malware, slow downs, crashes, costly repairs, and licensing fees?
If you struggle with the above, Linux might be the perfect platform for you. Linux has evolved into one of the most reliable computer ecosystems on the planet. Combine that reliability with zero cost of entry and you have the perfect solution for a desktop platform.
That’s right, zero cost of entry… as in free. You can install Linux on as many computers as you like without paying a cent for software or server licensing.
Let’s take a look at the cost of a Linux server in comparison to Windows Server 2016. The price of the Windows Server 2016 Standard edition is $882.00 USD (purchased directly from Microsoft). That doesn’t include Client Access License (CALs) and licenses for other software you may need to run (such as a database, a web server, mail server, etc.). For example, a single user CAL, for Windows Server 2016, costs $38.00. If you need to add 10 users, for example, that’s $388.00 more dollars for server software licensing. With the Linux server, it?s all free and easy to install. In fact, installing a full-blown web server (that includes a database server), is just a few clicks or commands away (take a look at ?Easy LAMP Server Installation? to get an idea how simple it can be).
If zero cost isn’t enough to win you over? what about having an operating system that will work, trouble free, for as long as you use it? I’ve used Linux for nearly 20 years (as both a desktop and server platform) and have not had any issues with ransomware, malware, or viruses. Linux is generally far less vulnerable to such attacks. As for server reboots, they’re only necessary if the kernel is updated. It is not out of the ordinary for a Linux server to go years without being rebooted. If you follow the regular recommended updates, stability and dependability are practically assured.
Open source:
Linux is also distributed under an open source license. Open source follows these key tenants:
● The freedom to run the program, for any purpose.
● The freedom to study how the program works, and change it to make it do what you wish.
● The freedom to redistribute copies so you can help your neighbour.
● The freedom to distribute copies of your modified versions to others.
These points are crucial to understanding the community that works together to create the Linux platform. Without a doubt, Linux is an operating system that is by the people, for the people. These tenants are also a main factor in why many people choose Linux. It’s about freedom and freedom of use and freedom of choice.
What is a “distribution?”
Linux has a number of different versions to suit any type of user. From new users to hard-core users, you’ll find a “flavor” of Linux to match your needs. These versions are called distributions (or, in the short form, “distros”). Nearly every distribution of Linux can be downloaded for free, burned onto disk (or USB thumb drive), and installed (on as many machines as you like).
Popular Linux distributions include:
● LINUX MINT.
● MANJARO.
● DEBIAN.
● UBUNTU.
● ANTERGOS.
● SOLUS.
● FEDORA.
● ELEMENTARY OS.
● OPENSUSE.
Each distribution has a different take on the desktop. Some opt for very modern user interfaces (such as GNOME and Elementary OS’s Pantheon), whereas others stick with a more traditional desktop environment (openSUSE uses KDE).
And don’t think the server has been left behind. For this arena, you can turn to:
- Red Hat Enterprise Linux.
- Ubuntu Server.
- Centos.
- SUSE Enterprise Linux.
Some of the above server distributions are free (such as Ubuntu Server and CentOS) and some have an associated price (such as Red Hat Enterprise Linux and SUSE Enterprise Linux). Those with an associated price also include support.
Which distribution is right for you?
Which distribution you use will depend on the answer to three simple questions:
- How skilled of a computer user are you?
- Do you prefer a modern or a standard desktop interface?
- Server or desktop?
If your computer skills are fairly basic, you’ll want to stick with a newbie-friendly distribution such as Linux Mint, Ubuntu (Figure 3), Elementary OS or Deepin. If your skill set extends into the above-average range, you could go with a distribution like Debian or Fedora. If, however, you’ve pretty much mastered the craft of computer and system administration, use a distribution like Gentoo. If you really want a challenge, you can build your very own Linux distribution, with the help of Linux From Scratch.
If you’re looking for a server-only distribution, you will also want to decide if you need a desktop interface, or if you want to do this via command-line only. The Ubuntu Server does not install a GUI interface. This means two things your server won’t be bogged down loading graphics and you’ll need to have a solid understanding of the Linux command line.
However, you can install a GUI package on top of the Ubuntu Server with a single command like sudo apt-get install ubuntu-desktop. System administrators will also want to view a distribution with regards to features. Do you want a server-specific distribution that will offer you, out of the box, everything you need for your server? If so, CentOS might be the best choice. Or, do you want to take a desktop distribution and add the pieces as you need them? If so, Debian or Ubuntu Linux might serve you well.
Installing Linux:
For many people, the idea of installing an operating system might seem like a very daunting task. Believe it or not, Linux offers one of the easiest installations of all operating systems. In fact, most versions of Linux offer what is called a Live distribution? which means you run the operating system from either a CD/DVD or USB flash drive without making any changes to your hard drive. You get the full functionality without having to commit to the installation. Once you’ve tried it out, and decided you wanted to use it, you simply double-click the “Install” icon and walk through the simple installation wizard.
Typically, the installation wizards walk you through the process with the following steps (We’ll illustrate the installation of Ubuntu Linux):
- Preparation: Make sure your machine meets the requirements for installation. This also may ask you if you want to install third-party software (such as plugins for MP3 playback, video codecs, and more).
- Wireless setup (if necessary): If you are using a laptop (or machine with wireless), you’ll need to connect to the network, in order to download third-party software and updates.
- Hard drive allocation (Figure 4): This step allows you to select how you want the operating system to be installed. Are you going to install Linux alongside another operating system (called “dual booting”), use the entire hard drive, upgrade an existing Linux installation, or install over an existing version of Linux.
- Location: Select your location from the map.
- Keyboard layout: Select the keyboard for your system.
- User setup: Set up your username and password.
That’s it. Once the system has completed the installation, reboot and you’re ready to go. For a more in-depth guide to installing Linux, take a look at “How to Install and Try Linux the Absolutely Easiest and Safest Way” or download the Linux Foundation’s PDF guide for Linux installation.
Installing software on Linux:
Just as the operating system itself is easy to install, so too are applications. Most modern Linux distributions include what most would consider an app store. This is a centralized location where software can be searched and installed. Ubuntu Linux (and many other distributions) rely on GNOME Software, Elementary OS has the AppCenter, Deepin has the Deepin Software Center, openSUSE has their AppStore, and some distributions rely on Synaptic.
Regardless of the name, each of these tools do the same thing? a central place to search for and install Linux software. Of course, these pieces of software depend upon the presence of a GUI. For GUI-less servers, you will have to depend upon the command-line interface for installation.
Let’s look at two different tools to illustrate how easy even the command line installation can be. Our examples are for Debian-based distributions and Fedora-based distributions. The Debian-based distros will use the apt-get tool for installing software and Fedora-based distros will require the use of the yum tool. Both work very similarly. We’ll illustrate using the apt-get command. Let’s say you want to install the wget tool (which is a handy tool used to download files from the command line). To install this using apt-get, the command would like like this:
Sudo apt-get install wget?
The sudo command is added because you need super user privileges in order to install software. Similarly, to install the same software on a Fedora-based distribution, you would first su to the super user (literally issue the command su and enter the root password), and issue this command:
Yum install wget
That’s all there is to installing software on a Linux machine. It’s not nearly as challenging as you might think. Still in doubt? Recall the Easy Lamp Server Installation from earlier? With a single command:
Sudo tasksel
You can install a complete LAMP (Linux Apache MySQL PHP) server on either a server or desktop distribution. It really is that easy.
Linux Design Principles:
In its overall design, Linux resembles another non-microkernel UNIX implementation. It is a multi-user, multi-tasking system with complete UNIX-compatible tools. The Linux file system follows the traditional UNIX semantics, and the UNIX standard network model is implemented as a whole. The internal characteristics of Linux design have been influenced by the history of the development of this operating system.
Although Linux can run on a variety of platforms, at first it was developed exclusively on PC architecture. Most of the initial development was carried out by individual enthusiasts, not by large funded research facilities, so that from the start Linux tried to include as much functionality as possible with very limited funds. Currently, Linux can run well on multiprocessor machines with very large main memory and disk space that is also very large, but still capable of operating in a useful amount of RAM smaller than 4 MB.
Linux Design Principles:
As a result of the development of PC technology, the Linux kernel is also becoming more complete in implementing UNIX functions. Fast and efficient are important design goals, but lately the concentration of Linux development has focused more on the third design goal, standardization. The POSIX standard consists of a collection of specifications from different aspects of operating system behavior. There are POSIX documents for ordinary operating system functions and for extensions such as processes for threads and real-time operations. Linux is designed to fit the relevant POSIX documents; there are at least two Linux distributions that have received POSIX official certification.
Because Linux provides a standard interface to programmers and users, Linux does not make many surprises to anyone who is familiar with UNIX. But the Linux programming interface refers to the UNIX SVR4 semantics rather than BSD behavior. A different collection of libraries is available to implement the BSD semantics in places where the two behaviors are very different.
There are many other standards in the UNIX world, but Linux’s full certification of other UNIX standards sometimes becomes slow because it is more often available at a certain price (not freely), and there is a price to pay if it involves certification of approval or compatibility of an operating system with most standards . Supporting broad applications is important for all operating systems so that the implementation of the standard is the main goal of developing Linux even though its implementation is not formally valid. In addition to the POSIX standard, Linux currently supports POSIX thread extensions and subsets of extensions for POSIX real-time process control.
Linux System Components:
The Linux system consists of three important code parts:
● Kernel: Responsible for maintaining all important abstractions of the operating system, including things like processes and virtual memory.
● System library: defines a set of standard functions where applications can interact with the kernel, and implements almost all operating system functions that do not require full rights to the kernel.
● System Utility: is a program that performs management work individually and specifically.
Kernel:
Although various modern operating systems have adopted a message-passing architecture for their internal kernel, Linux uses the historical UNIX model: the kernel was created as a single, monolithic binary. The main reason is to improve performance: Because all data structures and kernel code are stored in one address space, context switching is not needed when a process calls an operating system function or when a hardware interrupt is sent. Not only scheduling core and virtual memory code occupies this address space; all kernel code, including all device drivers, file systems, and network code, come in the same address space.
The Linux kernel forms the core of the Linux operating system. It provides all the functions needed to run the process, and is provided with system services to provide settings and protection for access to hardware resources. The kernel implements all the features needed to work as an operating system. However, if alone, the operating system provided by the Linux kernel is not at all similar to UNIX systems. It does not have many extra UNIX features, and the features provided are not always in the format expected by the UNIX application. The interface of the operating system that is visible to the running application is not maintained directly by the kernel. Instead, the application makes calls to the system library, which then invokes the operating system services that are needed.
System Library:
The system library provides many types of functions. At the easiest level, they allow applications to make requests to the kernel system services. Making a system call involves transferring controls from non-essential user mode to important kernel mode; the details of this transfer are different for each architecture. The library has the duty to collect system-call arguments and, if necessary, arrange those arguments in the special form needed to make system calls.
Libraries can also provide more complex versions of basic system calls. For example, the buffered file-handling functions of the C language are all implemented in the system library, which results in better control of file I / O than those provided by the basic kernel system call. The library also provides routines that have nothing to do with system calls, such as sorting algorithms, mathematical functions, and string manipulation routines. All functions needed to support the running of UNIX or POSIX applications are implemented in the system library.
System Utilities:
Linux systems contain many user-mode programs: system utilities and user utilities. The system utilities include all the programs needed to initialize the system, such as programs for configuring network devices or for loading kernel modules. Server programs that are running continuously are also included as system utilities; This kind of program manages user login requests, incoming network connections, and printer queues.
Not all standard utilities perform important system administration functions. The UNIX user environment contains a large number of standard utilities for doing daily work, such as making directory listings, moving and deleting files, or showing the contents of a file. More complex utilities can perform text-processing functions, such as compiling textual data or performing pattern-searches on text input. When combined, these utilities form the standard toolset expected by users on any UNIX system; even if it doesn’t perform any operating system functions, utilities are still an important part of a basic Linux system.
Key takeaway-
Just like Windows, iOS, and Mac OS, Linux is an operating system. In fact, one of the most popular platforms on the planet, Android, is powered by the Linux operating system. An operating system is software that manages all of the hardware resources associated with your desktop or laptop. To put it simply, the operating system manages the communication between your software and your hardware. Without the operating system (OS), the software wouldn?t function.
The following are the key distinctions between Linux and Windows
Sr. No. | Key | Linux | Windows |
1 | Open Source | Linux is an open source operating system that is completely free to use. | Windows isn't free to use and isn't open source. |
2 | Case sensitivity | The case of files in the Linux file system is important. | The Windows file system does not care about case. |
3 | Kernel type | Linux uses monolithic kernel. | Windows uses micro kernel. |
4 | Efficiency | When compared to Windows, Linux is more efficient in terms of operations. | In terms of operations, Windows is less efficient. |
5 | Path Separator | The forward slash is used in Linux as a path separator between directories. | The backward slash is used as a path separator in Windows. |
6 | Security | In comparison to Windows, Linux is quite secure. | When compared to Linux, Windows offers inferior security. |
The Linux operating system is a common variant of the UNIX operating system that aims to provide a free or low-cost operating system for personal computer users. It earned a reputation as a system that was both fast and effective. This is an incredibly comprehensive operating system, with features such as a graphical user interface (GUI), TCP/IP, the Emacs editor, and the X Window System. Debian, Ubuntu, Fedora, Red Hat Linux, SUSE Linux, Gentoo, Kali Linux, and Centos are the best Linux operating systems.
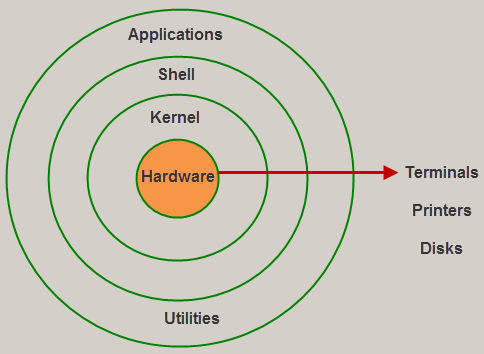
Fig 3: Linux architecture
Kernel
The kernel is the most important component of Linux. It is in charge of the operating system's main functions. It is made up of different modules that communicate directly with the hardware. Kernel provides the required abstraction for device or application programs to hide low-level hardware information.
The kernel is the central interface between a computer's hardware and its processes and is the most important part of a Linux operating system (OS). It interacts between the two, allowing for the most effective use of resources.
The following are the different forms of Kernels:
● Monolithic Kernel
● Microkernels
● Exo kernels
● Hybrid kernels
The kernel performs four functions:
- Memory management - Keep track of how much memory is being used for what, and where it is being stored.
- Process management - Determine can processes, when and for how long, should use the central processing unit (CPU).
- Device driver - Act as a liaison between the hardware and the processes.
- System call and security - Receive service requests from the processes.
Shell
The shell is a user-to-kernel interface that allows the kernel to provide services to the user. It receives user commands and performs the kernel's functions. The Shell can be used in a variety of operating systems and is divided into two categories: command-line shells and graphical shells.
A command-line interface is provided by command-line shells, while a graphical user interface is provided by graphical line shells. Despite the fact that both shells execute operations, graphical user interface shells are slower than command line interface shells.
An interface to the kernel that conceals the ambiguity of the kernel's functions from the user. The shell receives user commands and performs kernel functions.
Shells are divided into four categories:
● Korn shell
● Bourne shell
● C shell
● POSIX shell
Application (Utilities)
● It is in charge of performing specialized and individual tasks.
● Utility services provide the majority of an operating system's functionality to the user.
Logout
The logout command allows you to log out of your session programmatically. Causes the session manager to take the action specified right away.
Example-1:
To logout from current user session:
$ logout
Output:
No output on screen, current user session will be logged out.
Key takeaway:
The Linux operating system is a common variant of the UNIX operating system that aims to provide a free or low-cost operating system for personal computer users.
The kernel is the central interface between a computer's hardware and its processes and is the most important part of a Linux operating system.
The shell is a user-to-kernel interface that allows the kernel to provide services to the user.
Cal command
The cal command in Linux is used to display the calendar for a particular month or for the entire year.
Syntax:
Cal [ [ month ] year]
Or
Cal [options] [month] [year]
Calendar other option
-1 - As a production, it shows a single month.
-3 - Prev/current/next month production is shown.
-s - The first day of the week is shown as Sunday.
-m - The first day of the week is shown as Monday.
-j - Julian dates are shown (days one-based, numbered from January 1).
-y - The current year's calendar is shown.
Example 1:
Cal -3 5 2008
The calendar for the months of April, May, and June in the year 2008 is shown.
Example 2:
Date command
The date command is used to show the current date and time on the machine. The date command is often used to set the system's date and time.
Syntax:
$date
Example:
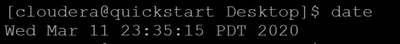
Echo command
In Linux, the echo command is used to show a line of text/string that has been passed as an argument. This is a built-in command that outputs status text to the screen or a file. It's mainly used in shell scripts and batch files.
Syntax:
Echo "enter text"
Example:
In this example, we use the -p command line option to enter the input on the same PROMPT:
Read -p PROMPT <variable_name>
Echo option
-n: The trailing newline should not be production.
-E: STRINGs would not be able to read certain sequences.
Example:
Who command
Who w – Command: UNIX maintains an account for all the current system. Because it is a multi-user system it is prudent for the user to be aware of other current users so that s/he can communicate with them if required. The user login details of all the current users by using the who command. The use of who command provides a list of all the current users in the three-column format by default, as shown follows:
$ who
Raj console Nov 19 09:35
Reena tty01 Nov 19 09:40
Priya tty02 Nov 19 09:41
The first column shows the name of the users, the second column shows the device names and the third column shows the login time. Some options like -H, -u and -T can be used with this command.
The H option provides headers for the columns and the -u option provides more details like idle time, PID and comments as shown in the example below.
$ who-Hu
NAME LINE TIME IDLE PID COMMENTS
Raj console Nov 19 09:35 # 32
Reena tty01 Nov 19 09:40 0:20 33
Priya tty01 Nov 19 09:41 0:40 34
If any terminal is idle If any terminal is idle (not active) for the last 1 minute, the information, that is, for how long that terminal is idle will be indicated on the IDLE column. Thus, 0:20 indicates that reena's terminal is IDLE for the last 20 minutes. This information will be useful to the system administrator. The PID indicates the process identification number. The self-login details of a user can be obtained as a single line output using am and i arguments along with the who command as follows.
$ who am i
Reena tty01 Nov 1909:40
Generally, the who command is used by the system administrator for monitoring terminals.
The w command is a quick way to see who is logged on and what they are doing.
Mkdir
The command mkdir means 'make directory.' You can construct a new directory anywhere in your system by using the mkdir command. Simply type "mkdir dir name>" (instead of dir name>, type the name of the new directory you want to create) and hit enter.
Syntax:
Mkdir <dirname>
Mkdir option
Option | Description |
Mkdir, -p, -parents | Add the directory, as well as its subdirectories. |
Mkdir, -v, -verbose | For each newly formed directory, print a message. |
Mkdir -m -mode=MODE | Set the permissions for entry. |
Rmdir
Removing Directories
The rmdir command can be used to remove directories as follows:
$rmdir dirname
$
If you want to delete a directory, make sure it's empty, which means there should be no files or subdirectories inside.
You can delete several folders at the same time by doing the following:
$rmdir dirname1 dirname2 dirname3
$
If the directories dirname1, dirname2, and dirname3 are empty, the command above removes them. If the rmdir command is effective, no output is generated.
Rmdir -p
This command deletes a directory and all of its subdirectories at the same time. The command 'rmdir -p' was used to remove all sub-directories.
Cd
To modify the current working directory in Linux, use the cd command ( i.e., in which the current user is working). 'Change directory' is represented by the letter "cd." In the Linux terminal, it's one of the most commonly used commands.
Syntax:
Cd <dirname>
It's one of the most critical and widely used commands in the Linux system, and you'll see it a lot. We can navigate through our system's directories with the aid of this order. We may go back to the previous directory, forward to the next directory, or anywhere else.
The cd command can be used for more than just changing directories. By specifying a valid absolute or relative path, you can change to any directory. The syntax is as follows:
$cd dirname
$
The name of the directory you want to change to is provided by dirname. For instance, the command
$cd /usr/local/bin
$
Changes to the /usr/local/bin directory. You may use the following relative path to cd to the directory /usr/home/amrood from this directory:
$cd ../../home/amrood
$
Listing Files
Use the following command to get a list of the files and folders in the current directory:
$ls
Here is an example of the above command's output:
$ls
Bin hosts lib res.03
Ch07 hw1 pub test_results
Ch07.bak hw2 res.01 users
Docs hw3 res.02 work
The -l option of the programme ls can be used to gain extra information about the files shown.
$ls -l
Total 1962188
Drwxrwxr-x 2 amrood amrood 4096 Dec 25 09:59 uml
-rw-rw-r-- 1 amrood amrood 5341 Dec 25 08:38 uml.jpg
Drwxr-xr-x 2 amrood amrood 4096 Feb 15 2006 univ
Drwxr-xr-x 2 root root 4096 Dec 9 2007 urlspedia
-rw-r--r-- 1 root root 276480 Dec 9 2007 urlspedia.tar
Drwxr-xr-x 8 root root 4096 Nov 25 2007 usr
Drwxr-xr-x 2 200 300 4096 Nov 25 2007 webthumb-1.01
-rwxr-xr-x 1 root root 3192 Nov 25 2007 webthumb.php
-rw-rw-r-- 1 amrood amrood 20480 Nov 25 2007 webthumb.tar
-rw-rw-r-- 1 amrood amrood 5654 Aug 9 2007 yourfile.mid
-rw-rw-r-- 1 amrood amrood 166255 Aug 9 2007 yourfile.swf
Drwxr-xr-x 11 amrood amrood 4096 May 29 2007 zlib-1.2.3
$
Here's the lowdown on each of the listed columns.
● The file type and permissions granted on the file are represented in the first column. The following is a list of all types of files and their descriptions.
● The number of memory blocks taken by the file or directory is represented in the second column.
● The owner of the file is represented by the third column. This is the name of the Unix user who made this file.
● The owner's group is represented in the fourth column. Every Unix user will be assigned to a group.
● The file size in bytes is represented in the fifth column.
● The date and time when this file was last created or updated are represented in the sixth column.
● The file or directory name is represented in the seventh column.
Metacharacters
In Unix, metacharacters have a special meaning. * and?, for example, are metacharacters. A question mark (?) matches a single character, while * matches 0 or more characters.
For Example −
$ls ch*.doc
Displays all files with names that begin with ch and conclude with.doc.
Ch01-1.doc ch010.doc ch02.doc ch03-2.doc
Ch04-1.doc ch040.doc ch05.doc ch06-2.doc
Ch01-2.doc ch02-1.doc c
* serves as a meta character that can be used with any other character. If you only want to see files that end in.doc, type the following command.
$ls *.doc
Hidden Files
The dot or the period character is the first character of an unseen file (.). The majority of these files are used by Unix programmes (including the shell) to hold configuration information.
Among the most common hidden files are the folders-
● .profile − The Bourne shell ( sh) initialization script
● .kshrc − The Korn shell ( ksh) initialization script
● .cshrc − The C shell ( csh) initialization script
● .rhosts − The remote shell configuration file
Specify the -a option to ls to list the hidden files.
$ ls -a
. .profile docs lib test_results
.. .rhosts hosts pub users
.emacs bin hw1 res.01 work
.exrc ch07 hw2 res.02
.kshrc ch07.bak hw3 res.03
$
● Single dot (.) − This represents the current directory.
● Double dot (..) − This represents the parent directory.
Creating Files
On any Unix system, the vi editor can be used to create ordinary files. All you have to do is type the following command:
$ vi filename
The command above will open a file with the specified name. To access the edit mode, hit the key i. You can start writing your information in the file once you're in edit mode, as seen in the following programme.
This is unix file....I created it for the first time.....
I'm going to save this content in this file.
When you've finished with the programme, follow these instructions.
● To exit the edit mode, press the esc key.
● To exit the file altogether, press the keys Shift + ZZ simultaneously.
In the current directory, a file named filename will be created.
$ vi filename
$
Editing Files
The vi editor can be used to edit an existing file. We'll go over how to open an existing file in a nutshell.
$ vi filename
You can enter edit mode by pressing the key I after the file has been opened, and then you can edit the file. If you want to move about within a file, you must first exit edit mode by pressing Esc. After that, you can navigate within a file by pressing the following keys:
● l key to move to the right side.
● h key to move to the left side.
● k key to move upside in the file.
● j key to move downside in the file.
As a result, you can put your cursor wherever you wish to modify using the keys listed above. After you've positioned yourself, press the I key to enter edit mode. After you've finished modifying your file, use Esc and then the two keys Shift + ZZ simultaneously to exit it fully.
Display Content of a File
The cat command can be used to view the contents of a file. Here is a simple sample of the content of the previously produced file:
$ cat filename
This is unix file....I created it for the first time.....
I'm going to save this content in this file.
$
Using the -b option with the cat command, you can see the line numbers as follows:
$ cat -b filename
1 This is unix file....I created it for the first time.....
2 I'
Copying Files
Use the cp command to make a copy of a file. The command's fundamental syntax is as follows:
$ cp source_file destination_file
The following is an example of how to make a copy of an existing file named filename.
$ cp filename copyfile
$
In your current directory, you will now notice another file named copyfile. The name of this file will be identical to the name of the original file.
Deleting Files
Use the rm command to remove an existing file. The fundamental syntax is as follows:
$ rm filename
A file may contain useful information, so proceed with caution. It's usually a good idea to use caution while using the Delete command. It is preferable to use the -i option in conjunction with the rm command.
The example below demonstrates how to entirely delete the existing file filename.
$ rm filename
$
You can remove multiple files at a time with the command given below −
$ rm filename1 filename2 filename3
$
Ls - list directory contents. The command to list our directories and files is ls, With options it can provide information about the size, type of file, permissions, dates of file creation, change and access.
Syntax:
Is [options] [argument]
Common Options: When no argument is used, the listing will be of the current directory. There are many useful options for the Is command. A listing of many of them follows. When using the command, string the desired options together preceded by "."
-a lists all files, including those beginning with a dot (.)
-d lists only names of directories, not the files in the directory
-F indicates type of entry with a trailing symbol:
Directories /
Sockets =
Symbolic links @
Executables*
-g displays Unix group assigned to the file, requires the -l option (BSD only)-or on an SVR4 machine, e.g. Solaris, this option has the opposite effect
-L if the file is a symbolic link, lists the information for the file or directory the link references, not the information for the link itself.
-I long listing: lists the mode, link information, owner. Size. Last modification time).
If the file is a symbolic link, an arrow (-->) precedes the pathname of the linked-to file.
The mode field is given by the -I option and consists of 10 characters. The first character is one of the following:
Character if entry is a:
d directory
- plain file
b block-type special file
c character-type special file
1 symbolic link
s socket
The next 9 characters are in 3 sets of 3 characters each. They indicate the file access permissions: the first 3 characters refer to the permissions for the user, the next three for the users in the UNIX group assigned to the file, and the last 3 to the permissions for other users on the system.
Designations are as follows:
r read permission
w write permission
x execute permission
-no permission
There are a few less commonly used permission designations for special circumstances. These are explained in the man page for ls.
Examples:
(i) To list the files in a directory:
$ ls
Demofiles frank linda
(ii) To list all files in a directory, including the hidden (dot) files try:
$ Is –a
..cshrc .history -plan .rhosts frank
...emacs .login .profile demofiles linda
(iii) To show the hidden files, but not the current directory) and (parent directory), use option -A.
(iv) To show all the files recursively, use -R option. When we do this from /, it shows all the unhidden files in the whole file system recursively.
$Is /etc/sysconfig/networking
Devices profiles
$Is -R -R/etc/sysconfig/networking
/etc/sysconfig/networking:
Devices profiles
/etc/sysconfig/networking/devices:
/etc/sysconfig/networking/profiles:
Default
/etc/sysconfig/networking/profiles/default:
(v) To get a long listing:
$ Is-al
Total 24
Drwxr-sr-x 5 workshop acs 512 Jun7 11:12 .
Drwxr-xr-x 6 root sys 512 May29 09:59 ..
-rw-------- 1 workshop acs 525 May20 21:29 .emacs
-rwxr-xr-x 1 workshop acs 238 May 14 09:44 .login
-rw-r—r-- 1 workshop acs 273 May 22 23:53 .plan
-rwxr-xr-x 1 workshop acs 413 May 14 09:36 .profile
Drwx------- 3 workshop acs 512 May 24 11:18 demofiles
Drwx------- 2 workshop acs 512 May 21 10:48 frank
Drwx------- 3 workshop acs 512 May 24 10:59 linda
Instead of doing the 'ls - and then the checking for the first character to determine the type of file. We can use -F which classifies the file with different special character for different kind of files.
$ ls -F
Desktop/ Documents/ Ubuntu-App@ firstfile Music/ Public/ Templates/
Thus in the above output
/-directory.
Nothing - normal file.
@- link file.
*- Executable file
(vi) $ Is-d Displays only directories
(vii) $ Is -r Displays files in reverse order.
(viii) $ Is -f Interprets each name as a directory, not a file.
Mv command
Mv - move a file: Rename a file with the move command, mv.
Syntax: mv (options] old_filename new_filename
Common Options:
-i interactive (prompt and wait for confirmation before proceeding)
-f don't prompt, even when copying over an existing target file (overrides-i)
Examples:
$ mvold_filename new_filename
i) We now have a file called new_filename and the file old filename is gone. Actually all we've done is to update name the directory table entry to give the file a new name
Ii) The contents of the file remain where they were.
Cat command
The command 'cat' is the most often used and powerful. It's regarded as one of the most commonly used commands. It can display a file's content, copy content from one file to another, concatenate the contents of multiple files, display the line number, display $ at the end of a line, and so on.
Syntax:
Cat [OPTION]... [FILE]..
To make a file, follow these steps:
Cat > <file name>
// Enter file content
To save the file, press the "CTRL+ D" keys. To see the contents of the file, run it like this:
Cat <file name>
Linux cat command usage
Option | Function |
Cat > [fileName] | To create a file. |
Cat [oldfile] > [newfile] | Copy material from an older file to a new one. |
Cat [file1 file2 and so on] > [new file name] | To combine the contents of several files into a single file. |
Cat -n/cat -b [fileName] | To display line numbers. |
Cat -e [fileName] | The $ character will be displayed at the end of each line. |
Cat [fileName] <<EOF | Used to indicate the end of a page. |
Cp command
'cp' stands for copy. To copy a file or a directory, use the 'cp' command.
Syntax:
To copy in the same directory:
Cp <existing file name> <new file name>
Cp Options
Option | Function |
Cp -r | To duplicate a directory and all of its subdirectories.. |
Cp file1 file 2 directory name | Multiple files or directories in a directory are copied. |
Cp -backup | Before overwriting an existing file, make a backup. |
Cp -i | Asks for confirmation. |
Cp -l | To create a file with a hard link. |
Cp -p | Preserves a file's attribute. |
Cp -u -v | To ensure that the source file is older than the destination file. |
Rm command
'rm' stands for 'remove.' To remove a file, use this command. Unlike other GUIs, the command line does not feature a recycling bin or trash to recover files. As a result, exercise extreme caution when using this command. When you delete a file, it is permanently deleted.
Syntax:
Rm <file name>
Rm Options
Option | Description |
Rm *extension | Deletes files with the same extension. |
Rm -r or R | To recursively erase a directory. |
Rm -i | Interactively delete a file. |
Rm -rf | Forcefully delete a directory. |
A file type is used to describe the type of data that is saved in a file. Linux recognizes seven different file forms. Regular files, Directory files, Link files, Character special files, Block special files, Socket files, and Named pipe files are all examples of file types.
A list of these file types can be found in the table below.
/-----------------------------------------------\
|-|Regular File|
|d|Directory|
|l|Symbolic Link|
|b|Block Special File|
|c|Character Special File
|p|Named Pipe|
|s|Socket|
\-----------------------------------------------/
Regular file
Text, audio, video, images, scripts, and programs are only some of the content types that can be stored in regular or ordinary files. There are a plethora of content styles to choose from. Standard files, with or without an extension, can be built in Linux.
An extension is a collection of characters added to the end of a file name to give it a unique identity or to group it with other files of the same type of material. Files of various content types often use well-known file extensions for ease of identification and processing.
Despite the fact that the Linux file system does not need file extensions, you can still use them. They assist us in recognizing the different types of content contained in files. If a file's extension is.mp4, for example, you can assume it's a video file.
The /etc/mime.types file contains a full list of content types and file extensions that your Linux framework supports. The MIME (Multipurpose Internet Mail Extensions) standard assigns file content types a standard designation and classification.
To access the contents of this file, use any standard file reading command.
Directory
File systems use folders to arrange data in a hierarchy. Directories are similar to files, but instead of storing data, they keep track of where other files are located. Directory entries are used to store the location of files stored in the directory. A single file's name and location are stored in each directory entry.
The Linux file system begins with the directory /, also known as the root directory. This directory is where all files and directory files are made. Each directory, with the exception of the root directory, has a parent directory.
Symbolic link
We can use a file with a different filename and from a different location with link files. We use connecting files for this. A connection file is a file that contains a reference to another file. A hard connection and a symbolic or soft link are the two forms of connections.
A hard connection makes a copy of the original file that is identical to it. A hard connection to a directory or file on another filesystem is not possible. A reference to the original file is created by a soft or symbolic connection. A soft connection to a directory or file on another filesystem can be formed.
Block or Character special file
Block Special Files are used to communicate with hardware in blocks of data of 512 bytes, 1024 bytes, or 2048 bytes, depending on the hardware.
Hard drives, printers, displays, terminal emulators, and CD/DVD drives are all treated as special files in Linux. This ensures that a program can view and use files and devices in the same way that a user can. This feature makes it simpler and more versatile to build programs in Linux.
The /dev directory is where Linux stores all special files and system files. A character special file and a block special file are the two types of special files. A character special file represents a computer, such as a monitor or printer, that transfers data in bytes. A block special file represents a computer, such as a hard drive, that transfers data in blocks.
One character at a time is communicated with hardware using the Character Special File. Block and Character Special Files are usually found in the /dev directory.
Named pipe
A named pipe is a file that transfers data from one process to another.
The data that is passed between one process writing data into a named pipe and another process reading data from the named pipe is not stored in the named pipe. The mkfifo command can be used to build a named pipe.
We can use Linux to send the output of some process or command as the input to another process or command. The pipe is the name for this element. Only when both processes are initiated by the same user and are in the same parent process space do pipes function.
Standard pipes will not function if processes are run under different user names and permissions. Named pipes are used in these situations. Named pipes are similar to regular pipes, but they can be accessed via the filesystem.
The empty pipe files are known as named pipe files. Named pipe files are processed by the kernel without being written to the file system. Pipe files with names can be found anywhere in the file system. The FIFO (First In First Out) files are also known as pipe files.
Socket
The Socket File is a stylized inter-process communication mechanism.
It is highly uncommon for a user or even a system administrator to build a socket directly.
A socket is a data-exchange communication endpoint used by applications. When an application needs to communicate with another application, it connects to the application's socket.
A socket is used for any application that offers services to other applications or remote clients. Each socket has an IP address and port number associated with it, allowing it to accept connections from clients.
For example, if a local system application needs to communicate with a remote system application, it connects to that application's socket using the IP address and port number associated with that socket.
Sockets are very difficult to understand. Socket files are used by Linux to make communication between local applications easier. Socket files allow local device applications to share data without having to go through the complicated networking and sockets processes.
Socket files are files that use a file name instead of an IP address and port number as their address. To allow inter-process communication between local applications, socket files use the sendmsg() and recvmsg() system calls.
Key takeaway:
Directories are similar to files, but instead of storing data, they keep track of where other files are located.
Block and Character Special Files are usually found in the /dev directory.
A named pipe is a file that transfers data from one process to another.
A socket is used for any application that offers services to other applications or remote clients.
The Socket File is a stylized inter-process communication mechanism.
Chmod: Changing file permissions: The command name chmod stands for "change mode", and it is used to define the way a file can be accessed. Chmod (change mode) is one of the most frequently used commands in unix or linux operating system. The chmod command is used to change the file or directory access permissions.
Syntax:
Chmod [options] permissions filename
There are three different permissions. They are:
Read (4): Permitted to read the contents of the file. In case of directory, you can view all the files and subdirectories in that directory
Write (2): Permitted to write to the file. In case of directory, you can create files and sub-directories
Execute (1): Execute the file as a program/shell script. In case of directory, You can enter into that directory.
Here in the above, the numbers in the brackets represents the numeric values for the corresponding permissions. If you want to have a combination of permissions add the required numbers. For example, for read and execute, it is 4+1= 5.
Chmod [options]
-R: recursively change the permissions of a directory.
-v: Verbose
Chmod Examples in Linux / Unix:
1. Give read, write and execute permissions to everyone. Read, write and execute: 4+2+1=7
$ chmod 777 sample.sh
In the above example, you can see that the permissions are specified with a three digit number. The first digit is for user permissions, second is for group and third is for others permission. This type of representation is called octal representation. Alternatively, you can use the symbolic representation to give the permissions.
Chmod ugo+rwx sample.sh
We will see more details about the symbolic representation later.
2. Give read permission to user, write permission to group and execute permission to others
$ chmod 421 sample.sh
3. Recursive permissions to directory
To give read and write permissions to all the users to a directory (including files and subdirectories) use the recursive option -R.
Chmod -R 666 /dir
Symbolic Representation of Permissions: The following symbols are used to represent the users, groups and others:
● u: User
● g: Group
● o: Others
● a: All (user, group and others)
The following symbols represent the permissions:
● r: read
● W: write
● X: execute
The following symbols represent the permissions grant or revoke:
● + : Additional permissions. Selected permissions are added.
● - : Revoke the permissions. Selected permissions are revoked.
● = : Specific permissions. Only selected permissions are assigned.
Examples
1. Remove write permission from group
$ chmod g-w sample.sh
This will only removes the write permission for the group.
2. Add new permission execute to others
$ chmod o+x sample.sh
In addition to the existing permissions, this will add execute permission to others.
3. Give only read permissions to the user
$chmod u=w sample.sh
This will remove the existing permissions to the user and gives only write permission to the user.
The first n lines of the supplied text files are displayed.
We can filter / read the first or top lines or row of data, as the name implies. It will read the first 10 lines or records of the given data by default. If we need to read additional lines, we must use the "-n" option to define the number of lines that we need to read.
Syntax:
Head [-number_of_lines_to_print] [path]
Head -n 7 file.txt
Explanation:
● We have a data sample file with ten records in it.
● The default "head" command is now being used to read the data file.
● We'll use the "-n" option to read the number of lines of records if we need to read or get data other than the default value.
Cat file.txt
Output
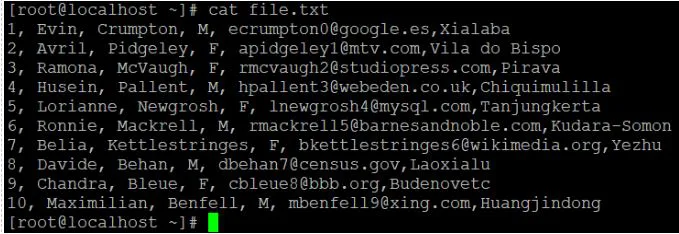
Head file.txt
Output:
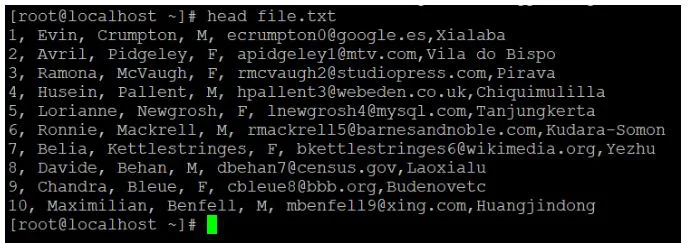
Head -n 7 file.txt
Output:
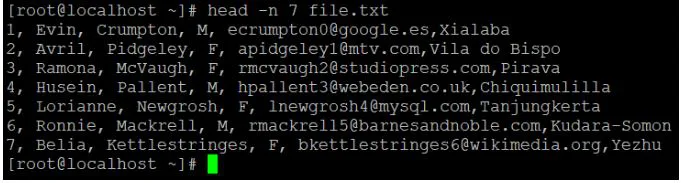
Tail
We'll use the tail command to collect data from the bottom of the file if we need it. It will read the latest 10 lines or records of the given data by default. If we need to read additional lines, we must use the "-n" option to define the number of lines that we need to read.
Syntax:
Tail <file name>
Code:
Tail -n 3 file.txt
Explanation:
● To read the data file, we use the default "tail" command.
● We'll use the "-n" option to read the number of lines of records if we need to read or get data other than the default value.
Tail file.txt
Output:
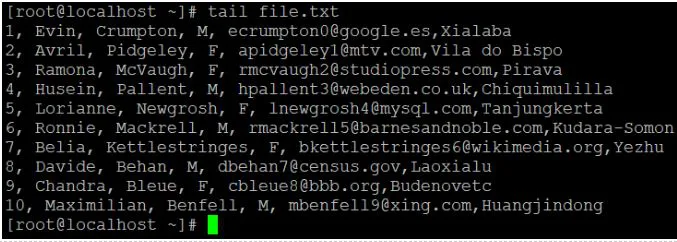
Tail -n 4 file.txt
Output:

Sort
Sorting text lines alphabetically or numerically is done with the sort command. The lines in the food file are sorted in the following example.
$sort food
Afghani Cuisine
Bangkok Wok
Big Apple Deli
Isle of Java
Mandalay
Sushi and Sashimi
Sweet Tooth
Tio Pepe's Peppers
$
By default, the sort command groups text lines alphabetically. There are numerous choices for controlling the sorting.
Sr.No. | Description |
1 | -n Sorts numerically (example: 10 will sort after 2), ignores blanks and tabs. |
2 | -r Reverses the order of sort. |
3 | -f Sorts upper and lowercase together. |
4 | +x Ignores first x fields when sorting. |
A pipe can be made up of more than two commands. Using grep and a prior pipe example, we can further sort the files updated in August by size.
The commands ls, grep, and sort make up the following pipe.
$ls -l | grep "Aug" | sort +4n
-rw-rw-r-- 1 carol doc 1605 Aug 23 07:35 macros
-rw-rw-r-- 1 john doc 2488 Aug 15 10:51 intro
-rw-rw-rw- 1 john doc 8515 Aug 6 15:30 ch07
-rw-rw-rw- 1 john doc 11008 Aug 6 14:10 ch02
$
This pipe organises all of the files in your August-modified directory by size and prints them on the terminal screen. The +4n sort option skips four fields (fields are separated by blanks) before sorting the lines numerically.
Grep
The grep command looks for lines that match a pattern in a file or files. The syntax is as follows:
$grep pattern file(s)
The term "grep" comes from the command g/re/p in the ed (a Unix line editor), which means "globally search for a regular expression and print all lines containing it."
A regular expression is a combination of plain text (for example, a word) and special characters that are used to match patterns.
The most basic application of grep is to seek for a single-word pattern. It can be used in a pipe to send to the standard output just the lines of the input files that contain a specific string. If you don't give grep a filename to read, it reads its standard input; that's the way all filter programs work −
$ls -l | grep "Aug"
-rw-rw-rw- 1 john doc 11008 Aug 6 14:10 ch02
-rw-rw-rw- 1 john doc 8515 Aug 6 15:30 ch07
-rw-rw-r-- 1 john doc 2488 Aug 15 10:51 intro
-rw-rw-r-- 1 carol doc 1605 Aug 23 07:35 macros
$
You can use the grep command with a number of different arguments.
Sr.No. | Option & Description |
1 | -v All lines that do not match the pattern are printed. |
2 | -n The matching line and its line number are printed. |
3 | -l Only the names of files with matching lines are printed (letter "l"). |
4 | -c Only the number of matching lines is printed. |
5 | -i Matches upper and lowercase letters. |
Vi stands for visual editor. It is a full screen editor. It is available with almost all the UNIX variants. Vi editor became famous because of its full screen editing capabilities and many other visual options. Vi editor is available under Linux in the form of vim (vi improved). It uses the terminal display as a window to the buffer and 25 lines can be displayed at all times. All unused lines of a file are marked by a -(tilde) called as empty buffer line flag. The last line is reserved for commands. The vi editor works in three modes that are:
1. The Command mode: This is the mode into which the user gets into as soon as the vi command is invoked from shell by using vi <filename>. In this mode all the keys pressed by the user are interpreted to be the editor commands. The keys that are pressed are not displayed on the screen. The user can get into the input mode by giving o, O, r, R, i, I, s, S, a, A commands.
2. The input mode: This mode is also known as insert mode. This mode permits the insertion of new text, appending to the existing text and replacement of the text. To exit or switch from this mode to command mode press Esc key.
3. The ex mode: This mode is also known as last line mode and allows user to use the commands in the bottom line (command line) on the vi screen. From the command mode the user can get in to the ex mode by typing the colon character (). Here this character is displayed in the command line. A colon (:) indicates that the editor is now in the ex mode. The user can get back to the command mode by using the Enter key

1. The input mode command:
(i) Insert (i, I):
i - Insert text to the left of the cursor position. Existing text will be shifted right
This is a file
Isimple [Esc]
This is a simple file
I- Insert text at the beginning of the line.
This is a file
I/*[Esc]
/*This is a simple file
(ii) Append (a, A):
a- Append text to the right of the cursor position. Existing text will be shifted right.
This is a file
Isimple [Esc]
This is a simple file
A- Appends text at end of the line.
This is a file
A*/ [Esc]
This is a simple file */
(iii) Open a line (o, O):
o- Opens a new line below the current line.
Hello
How
You
Oare [Esc]
Hello
How
Are
You
O-Opens a new line above the current line.
Hello
How
You
Osumit [Esc]
Hello
Sumit
How
Are
You
(iv) Replace (r, R, s, S):
r- Replace single character.
This is a dile
Rf
This is a file
R-Replaces all text on the right of the cursor position.
This is a simple file
Rdevice[Esc]
This is a device file
s- Replace one character with many.
This is a device file
Sone[Esc]
This is one device file
S - Replaces the entire line irrespective of the cursor position (existing line disappears).
2. The ex-mode command:
(i) :w- To save a file and remain in the editing mode.
: w
"ss", 8 lines, 150 characters
The message shows the name of the file i.e. ss along with the number of lines and character saved. We can also specify another file in the last line (In MS word, save as).
:w ss1
"ss1", 8 lines, 150 characters
If ssl is already exist then we use exclamation mark (!) with w
:w! ss1
Content of ss will be overwrite to ssl.
If we want to save fifth line to the another file then we will use
: 5w ss1
If we want to save ten to fifteenth line to the another file then we will use
: 10, 15w ss1
There are two symbols used with w have special significance - The dot (,) and dollar ($). The dot (.) represents the current line and dollar ($) represent the last line.
:.w ss1 //saves current line
: $w ss1 //saves last line
: .,$ ss1 //saves current line through end
(ii): q - Aborting editing : It is also possible to abort the editing process and quitting from the editing mode without saving the content with the help of : q command.
: q[enter]
$_
Vi also has a safety mechanism that prevents we from aborting accidentally if we have modified the file. The following message will be displayed.
No write since last change
If the buffer has been changed and we still want to abandon the changes then we will use
:q! //ignores all changes made and quits
(iii): wq - saving and quitting : We can also use: wq to save and exit from vi editor.
:wq ss1
(iv):sh - Escapes to UNIX shell:
Vi editor provide temporary escape to the shell to run the cc command.
:sh
This return a shell prompt execute cc or any other command here and then return to the editor using exit or
[Ctrl - d]
/* don't execute vi command once again - an undesirable situation */
3. The command mode command:
A command mode command doesn't on the screen but simply performs a function.
k- Moves cursor up
i- Move cursor down
h - Moves cursor left
1 - Moves cursor right
The repeat factor can be used as a command prefix with all these four commands. Thus 4k command moves the cursor 4 lines up and 20h takes it 20 characters to the left
b - Moves back to the beginning of word
w - Moves forward to the beginning of word
e - Moves forward to the end of word
0 - Moves cursor to extreme left
$ - Moves cursor to extreme right
|(pipe) - Moves cursor to specific column
The repeat factor can also be used with this command. Thus 5b takes the cursor 5 words back and 3w takes the cursor three words forward.
[Ctrl – f]- Scroll forward
[Ctrl - b]- Scrolls backward
[Ctrl – d]- Scrolls half page forward
[Ctrl – u]- Scrolls half page backward
The repeat factor can also be used with this command. Thus 10[Ctrl – f], to scroll 10 pages forward. When we start vi editor, it displays the total number of lines in the last line. To know the current line number we will use.
[Ctrl – g]- To know the current line number
"file1" [read only] line 67 of 233 -32%-
The cursor is on line 67 i.e. (32% of 233)
(i) G- Move to the specific line number (absolute movement)
23G //Goes to line number 23
1G //Goes to line number 1
G //Goes to end of file
(ii) x - Deletes a single character: The character under the cursor gets deleted and the text on the right shifts left to fill up the space. A repeat factor also used here. Thus 4x deletes the current character as well as three characters from the right
Dd - Deletes an entire line:
Dd command deletes a current line where cursor can be anywhere in the line. A repeat factor can also be used here, thus 4dd deletes the current line as well as three lines below.
p- Put character on the right of the cursor
When we delete parts of line
P- Put character on the left of the cursor
e.g.
If we want to correct sdtio.h to stdio.h, then we will have to transpose the characters d and t, i.e. delete the d and put it after t. Move your cursor to the d in sdtio.h then press.
x //sdtio.h becomes stio.h :cursor on t
p //d put on right : stio.h becomes stdio.h
p - Put character on the above of the current line When we delete an entire line
P- Put character on the below of the current line
p and P place text on the left and right only when you delete parts of lines. But the same keys get associated with above and below when we delete complete line.
(ii) Yanking (copying) the text:
Yh - Yank a character to the left of the current cursor position.
3yh - Yank three characters to the left of the current cursor position.
Yw - Yank from the current character to the next word.
Yor yy - Yanks the current line.
y2k - Yank current line and two lines above the current line.
3Y or 3yy - yank three lines including the current line.
Y$ - Yank till the end of the current line.
y) - Yank from the current character to next sentence.
y} - Yank from the current character till the end of the paragraph.
3y - yank three character.
(iii) Joining the line:
J - To join the current line and the line following it.
4J - To join the current line with 3 lines following it.
(iv) Undoing last editing instruction:
u - Undo the most recent single editing change by restoring the position before the change.
U-Undo all the changes before move away from the line.
[Ctrl -r] This command is used to redo the undone actions.
The repeat factor also works here. 10u is completely reversed with 10[Ctrl -r]
(v) Searching for a pattern (/ or?):
/pattern - Searches forward for pattern.
?pattern - Searches backward for pattern.
Eg.
If we are looking for the string echo, Then use
/echo @
The search begins forward to position the cursor on the first instance of the word, vi searches the entire line, so if the pattern can't be located till the end of the file is reached the search wraps around to resume from the beginning of the file. If the search still fails, vi respond with the message pattern not found
?echo @ (same like /)
The search begins backward direction.
Repeating the last pattern search:
n - Repeats search in same direction along which previous search was made.
N - Repeats search in opposite direction to that along which previous search
Was made.
Command mode
You can use this mode to conduct administrative activities including saving files, running commands, moving the cursor, cutting (yanking) and pasting lines or words, and finding and replacing. Whatever you type in this mode is regarded as a command.
Vi starts in command mode by default. You must be in insert mode to enter text, which you may do by typing i. To exit the insert mode, press the Esc key, which will return you to command mode.
You can move around by pressing the arrow keys or the vi movement keys, as shown below:
h | Left |
j | Down |
k | Up |
l | Right |
Insert mode
This mode allows you to add text to the document. In this mode, whatever you type is treated as input and saved to the file.
You can insert or append text in the input mode. In command mode, press I to insert text before the cursor's current position. Similarly, you can use a to append after the cursor. Keep in mind that you can't use the cursor keys in this mode. When you're through typing, press Esc to return to command mode.
Ex mode
This mode is used to enter commands on the command line at the bottom of the vi editor. Press the escape key to enter Ex command mode, then type: (colon). To save the contents of the vi editor and exit it, hit wq after the: (colon). Wq.
Ex mode is a command mode that has been extended. To get started, press Esc, then: (the colon). At a colon prompt, the pointer will move to the bottom of the screen. Enter:w to create a new file and:q to close it. By entering:wq, you can save and exit at the same time. If you're done with your file, though, Shift-z-z from command mode is usually more convenient.
References:
1. Operating System Concepts – Silberschatz, Galvin and Gagne
2. Operating System By Godbole
3. Linux Bible 9th Edition by Christoper Negus ISBN :978-1-118-99987-5
4. Ball, Using Linux, PHI, 1998. ISBN-10: 0789716232
5. UNIX: Concepts and Applications Das (4th Ed), TMH, 2006 ISBN 13: 9780070635463
Unit - 1
Introduction to Operating System
An Operating system (OS) is a software which acts as an interface between the end user and computer hardware. Every computer must have at least one OS to run other programs. An application like Chrome, MS Word, Games, etc needs some environment in which it will run and perform its task. The OS helps you to communicate with the computer without knowing how to speak the computer's language. It is not possible for the user to use any computer or mobile device without having an operating system.

Fig 1: Operating system
Features of Operating System
Here is a list commonly found important features of an Operating System:
● Protected and supervisor mode
● Allows disk access and file systems Device drivers Networking Security
● Program Execution
● Memory management Virtual Memory Multitasking
● Handling I/O operations
● Manipulation of the file system
● Error Detection and handling
● Resource allocation
● Information and Resource Protection
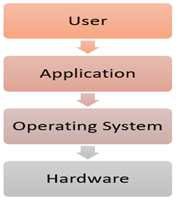
Types of Operating system
● Batch Operating System
● Multitasking/Time Sharing OS
● Multiprocessing OS
● Real Time OS
● Distributed OS
● Network OS
● Mobile OS
Batch Operating System
Some computer processes are very lengthy and time-consuming. To speed the same process, a job with a similar type of needs are batched together and run as a group.
The user of a batch operating system never directly interacts with the computer. In this type of OS, every user prepares his or her job on an offline device like a punch card and submit it to the computer operator.
Multi-Tasking/Time-sharing Operating systems
Time-sharing operating system enables people located at a different terminal(shell) to use a single computer system at the same time. The processor time (CPU) which is shared among multiple users is termed as time sharing.
Real time OS
A real time operating system time interval to process and respond to inputs is very small. Examples: Military Software Systems, Space Software Systems.
Distributed Operating System
Distributed systems use many processors located in different machines to provide very fast computation to its users.
Network Operating System
Network Operating System runs on a server. It provides the capability to serve to manage data, user, groups, security, application, and other networking functions.
Mobile OS
Mobile operating systems are those OS which is especially that are designed to power smartphones, tablets, and wearables devices.
Some most famous mobile operating systems are Android and iOS, but others include BlackBerry, Web, and watchOS.
Difference between Firmware and Operating System
Firmware | Operating System |
Firmware is one kind of programming that is embedded on a chip in the device which controls that specific device. | OS provides functionality over and above that which is provided by the firmware. |
Firmware is programs that been encoded by the manufacture of the IC or something and cannot be changed. | OS is a program that can be installed by the user and can be changed. |
It is stored on non-volatile memory. | OS is stored on the hard drive. |
Difference between 32-Bit vs. 64 Bit Operating System
Parameters | 32. Bit | 64. Bit |
Architecture and Software | Allow 32 bit of data processing simultaneously | Allow 64 bit of data processing simultaneously |
Compatibility | 32-bit applications require 32-bit OS and CPUs. | 64-bit applications require a 64-bit OS and CPU. |
Systems Available | All versions of Windows 8, Windows 7, Windows Vista, and Windows XP, Linux, etc. | Windows XP Professional, Vista, 7, Mac OS X and Linux. |
Memory Limits | 32-bit systems are limited to 3.2 GB of RAM. | 64-bit systems allow a maximum 17 Billion GB of RAM. |
The advantage of using Operating System
● Allows you to hide details of hardware by creating an abstraction
● Easy to use with a GUI
● Offers an environment in which a user may execute programs/applications
● The operating system must make sure that the computer system convenient to use
● Operating System acts as an intermediary among applications and the hardware components
● It provides the computer system resources with easy to use format
● Acts as an intermediator between all hardware's and software's of the system
Disadvantages of using Operating System
● If any issue occurs in OS, you may lose all the contents which have been stored in your system
● Operating system's software is quite expensive for small size organization which adds burden on them. Example Windows
● It is never entirely secure as a threat can occur at any time
Key Takeaway:
An operating system is a software which acts as an interface between the end user and computer hardware. Operating systems were first developed in the late 1950s to manage tape storage.
The kernel is the central component of a computer operating systems. The only job performed by the kernel is to the manage the communication between the software and the hardware
Need of Operating System
● OS as a platform for Application programs: The operating system serves as a foundation for other programmes known as application programmes to execute on. These application programmes make it easier for consumers to complete a given task. It serves as a link between the user and the computer. It is created in such a way that it can operate, control, and execute various computer applications.
● Managing Input-Output unit: The computer's operating system also allows it to manage its own resources, such as memory, display, keyboard, printer, and so on. Effective usage of these resources necessitates resource management. The operating system manages the system's input-output resources and distributes them to users or programmes based on their needs.
○ Consistent user interface: The operating system offers the user with an easy-to-use user interface, allowing the user to focus on the content and be productive as quickly as possible without having to learn a new UI each time. The operating system provides templates and UI components to make using a computer as simple as possible for the user.
● Multitasking: Memory is managed by the operating system, which allows several programmes to execute in their own space and even connect with one another via shared memory. Users benefit from multitasking since they can complete multiple tasks on a computer at the same time.
● Booting: The process of starting the computer is known as booting. When the CPU is turned on for the first time, there is nothing in the memory. So, in order to turn on the computer, we must first load the operating system into main memory. As a result, booting is the process of loading the operating system into main memory in order to start the computer. As a result, the operating system aids in the initialization of the computer when the power is turned on.
● Platform for other application software: Different application programmes are required by users to complete particular jobs on the system. The operating system (OS) supervises and regulates these programmes to ensure that they run smoothly. To put it another way, it serves as a link between the user and the programmes.
● Manages the memory: It aids in the management of the computer's main memory. It also allocates and deallocates memory for all programmes and tasks.
● Manages the system files: It aids in the organisation of files on the computer. All of the data on the system is stored in files, as we all know. It makes working with the files simple.
● Provides Security: It uses authorisation to keep the system and applications safe. As a result, the operating system protects the system.
Functions of Operating System
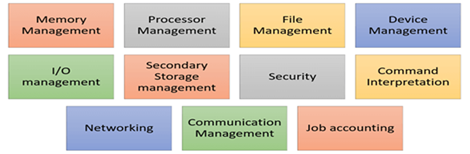
Fig 2: Function of an Operating System
In an operating system software performs each of the function:
- Process management: Process management helps OS to create and delete processes. It also provides mechanisms for synchronization and communication among processes.
- Memory management: Memory management module performs the task of allocation and deallocation of memory space to programs in need of this resources.
- File management: It manages all the file-related activities such as organization storage, retrieval, naming, sharing, and protection of files.
- Device Management: Device management keeps tracks of all devices. This module also responsible for this task is known as the I/O controller. It also performs the task of allocation and deallocation of the devices.
- I/O System Management: One of the main objects of any OS is to hide the peculiarities of that hardware devices from the user.
- Secondary-Storage Management: Systems have several levels of storage which includes primary storage, secondary storage, and cache storage. Instructions and data must be stored in primary storage or cache so that a running program can reference it.
- Security: Security module protects the data and information of a computer system against malware threat and authorized access.
- Command interpretation: This module is interpreting commands given by the and acting system resources to process that commands.
- Networking: A distributed system is a group of processors which do not share memory, hardware devices, or a clock. The processors communicate with one another through the network.
- Job accounting: Keeping track of time & resource used by various job and users.
- Communication management: Coordination and assignment of compilers, interpreters, and another software resource of the various users of the computer systems.
The UNIX operating system is a set of programs that act as a link between the computer and the user. The computer programs that allocate the system resources and coordinate all the details of the computer's internal is called the operating system or kernel.
Users communicate with the kernel through a program known as the shell. The shell is a command line interpreter; it translates commands entered by the user and converts them into a language that is understood by the kernel.
Unix was originally developed in 1969 by a group of AT&T employees at Bell Labs, including Ken Thompson, Dennis Ritchie, Douglas Mcllroy, and Joe Ossanna.
There are various Unix variants available in the market. Solaris Unix, AIX, HP Unix and BSD are few examples, Linux is also a flavor of Unix which is freely available.
Several people can use a UNIX computer at the same time, hence UNIX is called a multiuser system. A user can also run multiple programs at the same time; hence UNIX is called multitasking.
A Brief History of UNIX

Key takeaway
The UNIX operating system is a set of programs that act as a link between the computer and the user. The computer programs that allocate the system resources and coordinate all the details of the computer's internal is called the operating system or kernel.
What is Linux?
From smartphones to cars, supercomputers and home appliances, home desktops to enterprise servers, the Linux operating system is everywhere.
Linux has been around since the mid-1990s and has since reached a user-base that spans the globe. Linux is actually everywhere: It?s in your phones, your thermostats, in your cars, refrigerators, Roku devices, and televisions. It also runs most of the Internet, all of the world’s top 500 supercomputers, and the world’s stock exchanges.
But besides being the platform of choice to run desktops, servers, and embedded systems across the globe, Linux is one of the most reliable, secure and worry-free operating systems available. Here is all the information you need to get up to speed on the Linux platform.
Just like Windows, iOS, and Mac OS, Linux is an operating system. In fact, one of the most popular platforms on the planet, Android, is powered by the Linux operating system. An operating system is software that manages all of the hardware resources associated with your desktop or laptop. To put it simply, the operating system manages the communication between your software and your hardware. Without the operating system (OS), the software wouldn?t function.
The Linux operating system comprises several different pieces:
● Bootloader – The software that manages the boot process of your computer. For most users, this will simply be a splash screen that pops up and eventually goes away to boot into the operating system.
● Kernel – This is the one piece of the whole that is actually called ?Linux?. The kernel is the core of the system and manages the CPU, memory, and peripheral devices. The kernel is the lowest level of the OS.
● Init system – This is a sub-system that bootstraps the user space and is charged with controlling daemons. One of the most widely used init systems is systemd? which also happens to be one of the most controversial. It is the init system that manages the boot process, once the initial booting is handed over from the bootloader (i.e., GRUB or GRand Unified Bootloader).
● Daemons – These are background services (printing, sound, scheduling, etc.) that either start up during boot or after you log into the desktop.
● Graphical server – This is the sub-system that displays the graphics on your monitor. It is commonly referred to as the X server or just X.
● Desktop environment – This is the piece that the users actually interact with. There are many desktop environments to choose from (GNOME, Cinnamon, Mate, Pantheon, Enlightenment, KDE, Xfce, etc.). Each desktop environment includes built-in applications (such as file managers, configuration tools, web browsers, and games).
● Applications – Desktop environments do not offer the full array of apps. Just like Windows and macOS, Linux offers thousands upon thousands of high-quality software titles that can be easily found and installed. Most modern Linux distributions (more on this below) include App Store-like tools that centralize and simplify application installation. For example, Ubuntu Linux has the Ubuntu Software Center (a rebrand of GNOME Software? Figure 1) which allows you to quickly search among the thousands of apps and install them from one centralized location.
Features of Linux
Some of the most significant features of the Linux Operating System are mentioned below.
● Portable - Software's portability refers to its ability to run on various types of hardware in the same way. The Linux kernel and application programs can be installed on virtually any hardware platform.
● Open Source - Linux is a community-based programming project with freely available source code. Multiple teams collaborate to improve the capabilities of the Linux operating system, which is constantly changing.
● Multi-User - Linux is a multiuser system, which means that multiple users can share system resources such as memory, ram, and application programs.
● Multiprogramming - Linux is a multiprogramming method, which means it can run several programs at the same time.
● Hierarchical File System - System files and user files are organized in a common file structure in Linux.
● Shell - Linux has a special interpreter program that can be used to run operating system commands. It can be used to perform a variety of tasks, such as calling application programs.
● Security - User security is provided by Linux by authentication features such as password protection, restricted access to sensitive files, and data encryption.
Why use Linux?
This is the one question that most people ask. Why bother learning a completely different computing environment, when the operating system that ships with most desktops, laptops, and servers works just fine?
To answer that question, I would pose another question. Does that operating system you’re currently using really work ?just fine?? Or, do you find yourself battling obstacles like viruses, malware, slow downs, crashes, costly repairs, and licensing fees?
If you struggle with the above, Linux might be the perfect platform for you. Linux has evolved into one of the most reliable computer ecosystems on the planet. Combine that reliability with zero cost of entry and you have the perfect solution for a desktop platform.
That’s right, zero cost of entry… as in free. You can install Linux on as many computers as you like without paying a cent for software or server licensing.
Let’s take a look at the cost of a Linux server in comparison to Windows Server 2016. The price of the Windows Server 2016 Standard edition is $882.00 USD (purchased directly from Microsoft). That doesn’t include Client Access License (CALs) and licenses for other software you may need to run (such as a database, a web server, mail server, etc.). For example, a single user CAL, for Windows Server 2016, costs $38.00. If you need to add 10 users, for example, that’s $388.00 more dollars for server software licensing. With the Linux server, it?s all free and easy to install. In fact, installing a full-blown web server (that includes a database server), is just a few clicks or commands away (take a look at ?Easy LAMP Server Installation? to get an idea how simple it can be).
If zero cost isn’t enough to win you over? what about having an operating system that will work, trouble free, for as long as you use it? I’ve used Linux for nearly 20 years (as both a desktop and server platform) and have not had any issues with ransomware, malware, or viruses. Linux is generally far less vulnerable to such attacks. As for server reboots, they’re only necessary if the kernel is updated. It is not out of the ordinary for a Linux server to go years without being rebooted. If you follow the regular recommended updates, stability and dependability are practically assured.
Open source:
Linux is also distributed under an open source license. Open source follows these key tenants:
● The freedom to run the program, for any purpose.
● The freedom to study how the program works, and change it to make it do what you wish.
● The freedom to redistribute copies so you can help your neighbour.
● The freedom to distribute copies of your modified versions to others.
These points are crucial to understanding the community that works together to create the Linux platform. Without a doubt, Linux is an operating system that is by the people, for the people. These tenants are also a main factor in why many people choose Linux. It’s about freedom and freedom of use and freedom of choice.
What is a “distribution?”
Linux has a number of different versions to suit any type of user. From new users to hard-core users, you’ll find a “flavor” of Linux to match your needs. These versions are called distributions (or, in the short form, “distros”). Nearly every distribution of Linux can be downloaded for free, burned onto disk (or USB thumb drive), and installed (on as many machines as you like).
Popular Linux distributions include:
● LINUX MINT.
● MANJARO.
● DEBIAN.
● UBUNTU.
● ANTERGOS.
● SOLUS.
● FEDORA.
● ELEMENTARY OS.
● OPENSUSE.
Each distribution has a different take on the desktop. Some opt for very modern user interfaces (such as GNOME and Elementary OS’s Pantheon), whereas others stick with a more traditional desktop environment (openSUSE uses KDE).
And don’t think the server has been left behind. For this arena, you can turn to:
- Red Hat Enterprise Linux.
- Ubuntu Server.
- Centos.
- SUSE Enterprise Linux.
Some of the above server distributions are free (such as Ubuntu Server and CentOS) and some have an associated price (such as Red Hat Enterprise Linux and SUSE Enterprise Linux). Those with an associated price also include support.
Which distribution is right for you?
Which distribution you use will depend on the answer to three simple questions:
- How skilled of a computer user are you?
- Do you prefer a modern or a standard desktop interface?
- Server or desktop?
If your computer skills are fairly basic, you’ll want to stick with a newbie-friendly distribution such as Linux Mint, Ubuntu (Figure 3), Elementary OS or Deepin. If your skill set extends into the above-average range, you could go with a distribution like Debian or Fedora. If, however, you’ve pretty much mastered the craft of computer and system administration, use a distribution like Gentoo. If you really want a challenge, you can build your very own Linux distribution, with the help of Linux From Scratch.
If you’re looking for a server-only distribution, you will also want to decide if you need a desktop interface, or if you want to do this via command-line only. The Ubuntu Server does not install a GUI interface. This means two things your server won’t be bogged down loading graphics and you’ll need to have a solid understanding of the Linux command line.
However, you can install a GUI package on top of the Ubuntu Server with a single command like sudo apt-get install ubuntu-desktop. System administrators will also want to view a distribution with regards to features. Do you want a server-specific distribution that will offer you, out of the box, everything you need for your server? If so, CentOS might be the best choice. Or, do you want to take a desktop distribution and add the pieces as you need them? If so, Debian or Ubuntu Linux might serve you well.
Installing Linux:
For many people, the idea of installing an operating system might seem like a very daunting task. Believe it or not, Linux offers one of the easiest installations of all operating systems. In fact, most versions of Linux offer what is called a Live distribution? which means you run the operating system from either a CD/DVD or USB flash drive without making any changes to your hard drive. You get the full functionality without having to commit to the installation. Once you’ve tried it out, and decided you wanted to use it, you simply double-click the “Install” icon and walk through the simple installation wizard.
Typically, the installation wizards walk you through the process with the following steps (We’ll illustrate the installation of Ubuntu Linux):
- Preparation: Make sure your machine meets the requirements for installation. This also may ask you if you want to install third-party software (such as plugins for MP3 playback, video codecs, and more).
- Wireless setup (if necessary): If you are using a laptop (or machine with wireless), you’ll need to connect to the network, in order to download third-party software and updates.
- Hard drive allocation (Figure 4): This step allows you to select how you want the operating system to be installed. Are you going to install Linux alongside another operating system (called “dual booting”), use the entire hard drive, upgrade an existing Linux installation, or install over an existing version of Linux.
- Location: Select your location from the map.
- Keyboard layout: Select the keyboard for your system.
- User setup: Set up your username and password.
That’s it. Once the system has completed the installation, reboot and you’re ready to go. For a more in-depth guide to installing Linux, take a look at “How to Install and Try Linux the Absolutely Easiest and Safest Way” or download the Linux Foundation’s PDF guide for Linux installation.
Installing software on Linux:
Just as the operating system itself is easy to install, so too are applications. Most modern Linux distributions include what most would consider an app store. This is a centralized location where software can be searched and installed. Ubuntu Linux (and many other distributions) rely on GNOME Software, Elementary OS has the AppCenter, Deepin has the Deepin Software Center, openSUSE has their AppStore, and some distributions rely on Synaptic.
Regardless of the name, each of these tools do the same thing? a central place to search for and install Linux software. Of course, these pieces of software depend upon the presence of a GUI. For GUI-less servers, you will have to depend upon the command-line interface for installation.
Let’s look at two different tools to illustrate how easy even the command line installation can be. Our examples are for Debian-based distributions and Fedora-based distributions. The Debian-based distros will use the apt-get tool for installing software and Fedora-based distros will require the use of the yum tool. Both work very similarly. We’ll illustrate using the apt-get command. Let’s say you want to install the wget tool (which is a handy tool used to download files from the command line). To install this using apt-get, the command would like like this:
Sudo apt-get install wget?
The sudo command is added because you need super user privileges in order to install software. Similarly, to install the same software on a Fedora-based distribution, you would first su to the super user (literally issue the command su and enter the root password), and issue this command:
Yum install wget
That’s all there is to installing software on a Linux machine. It’s not nearly as challenging as you might think. Still in doubt? Recall the Easy Lamp Server Installation from earlier? With a single command:
Sudo tasksel
You can install a complete LAMP (Linux Apache MySQL PHP) server on either a server or desktop distribution. It really is that easy.
Linux Design Principles:
In its overall design, Linux resembles another non-microkernel UNIX implementation. It is a multi-user, multi-tasking system with complete UNIX-compatible tools. The Linux file system follows the traditional UNIX semantics, and the UNIX standard network model is implemented as a whole. The internal characteristics of Linux design have been influenced by the history of the development of this operating system.
Although Linux can run on a variety of platforms, at first it was developed exclusively on PC architecture. Most of the initial development was carried out by individual enthusiasts, not by large funded research facilities, so that from the start Linux tried to include as much functionality as possible with very limited funds. Currently, Linux can run well on multiprocessor machines with very large main memory and disk space that is also very large, but still capable of operating in a useful amount of RAM smaller than 4 MB.
Linux Design Principles:
As a result of the development of PC technology, the Linux kernel is also becoming more complete in implementing UNIX functions. Fast and efficient are important design goals, but lately the concentration of Linux development has focused more on the third design goal, standardization. The POSIX standard consists of a collection of specifications from different aspects of operating system behavior. There are POSIX documents for ordinary operating system functions and for extensions such as processes for threads and real-time operations. Linux is designed to fit the relevant POSIX documents; there are at least two Linux distributions that have received POSIX official certification.
Because Linux provides a standard interface to programmers and users, Linux does not make many surprises to anyone who is familiar with UNIX. But the Linux programming interface refers to the UNIX SVR4 semantics rather than BSD behavior. A different collection of libraries is available to implement the BSD semantics in places where the two behaviors are very different.
There are many other standards in the UNIX world, but Linux’s full certification of other UNIX standards sometimes becomes slow because it is more often available at a certain price (not freely), and there is a price to pay if it involves certification of approval or compatibility of an operating system with most standards . Supporting broad applications is important for all operating systems so that the implementation of the standard is the main goal of developing Linux even though its implementation is not formally valid. In addition to the POSIX standard, Linux currently supports POSIX thread extensions and subsets of extensions for POSIX real-time process control.
Linux System Components:
The Linux system consists of three important code parts:
● Kernel: Responsible for maintaining all important abstractions of the operating system, including things like processes and virtual memory.
● System library: defines a set of standard functions where applications can interact with the kernel, and implements almost all operating system functions that do not require full rights to the kernel.
● System Utility: is a program that performs management work individually and specifically.
Kernel:
Although various modern operating systems have adopted a message-passing architecture for their internal kernel, Linux uses the historical UNIX model: the kernel was created as a single, monolithic binary. The main reason is to improve performance: Because all data structures and kernel code are stored in one address space, context switching is not needed when a process calls an operating system function or when a hardware interrupt is sent. Not only scheduling core and virtual memory code occupies this address space; all kernel code, including all device drivers, file systems, and network code, come in the same address space.
The Linux kernel forms the core of the Linux operating system. It provides all the functions needed to run the process, and is provided with system services to provide settings and protection for access to hardware resources. The kernel implements all the features needed to work as an operating system. However, if alone, the operating system provided by the Linux kernel is not at all similar to UNIX systems. It does not have many extra UNIX features, and the features provided are not always in the format expected by the UNIX application. The interface of the operating system that is visible to the running application is not maintained directly by the kernel. Instead, the application makes calls to the system library, which then invokes the operating system services that are needed.
System Library:
The system library provides many types of functions. At the easiest level, they allow applications to make requests to the kernel system services. Making a system call involves transferring controls from non-essential user mode to important kernel mode; the details of this transfer are different for each architecture. The library has the duty to collect system-call arguments and, if necessary, arrange those arguments in the special form needed to make system calls.
Libraries can also provide more complex versions of basic system calls. For example, the buffered file-handling functions of the C language are all implemented in the system library, which results in better control of file I / O than those provided by the basic kernel system call. The library also provides routines that have nothing to do with system calls, such as sorting algorithms, mathematical functions, and string manipulation routines. All functions needed to support the running of UNIX or POSIX applications are implemented in the system library.
System Utilities:
Linux systems contain many user-mode programs: system utilities and user utilities. The system utilities include all the programs needed to initialize the system, such as programs for configuring network devices or for loading kernel modules. Server programs that are running continuously are also included as system utilities; This kind of program manages user login requests, incoming network connections, and printer queues.
Not all standard utilities perform important system administration functions. The UNIX user environment contains a large number of standard utilities for doing daily work, such as making directory listings, moving and deleting files, or showing the contents of a file. More complex utilities can perform text-processing functions, such as compiling textual data or performing pattern-searches on text input. When combined, these utilities form the standard toolset expected by users on any UNIX system; even if it doesn’t perform any operating system functions, utilities are still an important part of a basic Linux system.
Key takeaway-
Just like Windows, iOS, and Mac OS, Linux is an operating system. In fact, one of the most popular platforms on the planet, Android, is powered by the Linux operating system. An operating system is software that manages all of the hardware resources associated with your desktop or laptop. To put it simply, the operating system manages the communication between your software and your hardware. Without the operating system (OS), the software wouldn?t function.
The following are the key distinctions between Linux and Windows
Sr. No. | Key | Linux | Windows |
1 | Open Source | Linux is an open source operating system that is completely free to use. | Windows isn't free to use and isn't open source. |
2 | Case sensitivity | The case of files in the Linux file system is important. | The Windows file system does not care about case. |
3 | Kernel type | Linux uses monolithic kernel. | Windows uses micro kernel. |
4 | Efficiency | When compared to Windows, Linux is more efficient in terms of operations. | In terms of operations, Windows is less efficient. |
5 | Path Separator | The forward slash is used in Linux as a path separator between directories. | The backward slash is used as a path separator in Windows. |
6 | Security | In comparison to Windows, Linux is quite secure. | When compared to Linux, Windows offers inferior security. |
The Linux operating system is a common variant of the UNIX operating system that aims to provide a free or low-cost operating system for personal computer users. It earned a reputation as a system that was both fast and effective. This is an incredibly comprehensive operating system, with features such as a graphical user interface (GUI), TCP/IP, the Emacs editor, and the X Window System. Debian, Ubuntu, Fedora, Red Hat Linux, SUSE Linux, Gentoo, Kali Linux, and Centos are the best Linux operating systems.
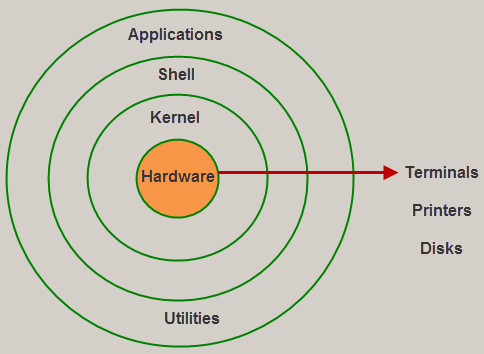
Fig 3: Linux architecture
Kernel
The kernel is the most important component of Linux. It is in charge of the operating system's main functions. It is made up of different modules that communicate directly with the hardware. Kernel provides the required abstraction for device or application programs to hide low-level hardware information.
The kernel is the central interface between a computer's hardware and its processes and is the most important part of a Linux operating system (OS). It interacts between the two, allowing for the most effective use of resources.
The following are the different forms of Kernels:
● Monolithic Kernel
● Microkernels
● Exo kernels
● Hybrid kernels
The kernel performs four functions:
- Memory management - Keep track of how much memory is being used for what, and where it is being stored.
- Process management - Determine can processes, when and for how long, should use the central processing unit (CPU).
- Device driver - Act as a liaison between the hardware and the processes.
- System call and security - Receive service requests from the processes.
Shell
The shell is a user-to-kernel interface that allows the kernel to provide services to the user. It receives user commands and performs the kernel's functions. The Shell can be used in a variety of operating systems and is divided into two categories: command-line shells and graphical shells.
A command-line interface is provided by command-line shells, while a graphical user interface is provided by graphical line shells. Despite the fact that both shells execute operations, graphical user interface shells are slower than command line interface shells.
An interface to the kernel that conceals the ambiguity of the kernel's functions from the user. The shell receives user commands and performs kernel functions.
Shells are divided into four categories:
● Korn shell
● Bourne shell
● C shell
● POSIX shell
Application (Utilities)
● It is in charge of performing specialized and individual tasks.
● Utility services provide the majority of an operating system's functionality to the user.
Logout
The logout command allows you to log out of your session programmatically. Causes the session manager to take the action specified right away.
Example-1:
To logout from current user session:
$ logout
Output:
No output on screen, current user session will be logged out.
Key takeaway:
The Linux operating system is a common variant of the UNIX operating system that aims to provide a free or low-cost operating system for personal computer users.
The kernel is the central interface between a computer's hardware and its processes and is the most important part of a Linux operating system.
The shell is a user-to-kernel interface that allows the kernel to provide services to the user.
Cal command
The cal command in Linux is used to display the calendar for a particular month or for the entire year.
Syntax:
Cal [ [ month ] year]
Or
Cal [options] [month] [year]
Calendar other option
-1 - As a production, it shows a single month.
-3 - Prev/current/next month production is shown.
-s - The first day of the week is shown as Sunday.
-m - The first day of the week is shown as Monday.
-j - Julian dates are shown (days one-based, numbered from January 1).
-y - The current year's calendar is shown.
Example 1:
Cal -3 5 2008
The calendar for the months of April, May, and June in the year 2008 is shown.
Example 2:

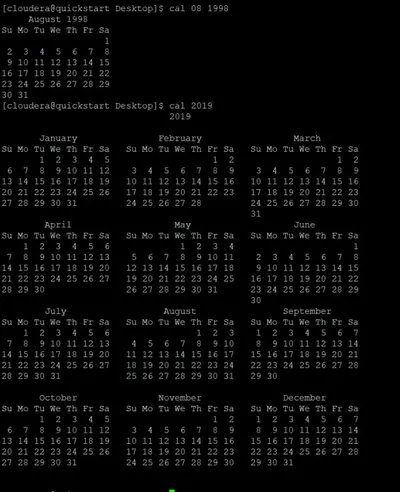
Date command
The date command is used to show the current date and time on the machine. The date command is often used to set the system's date and time.
Syntax:
$date
Example:
Echo command
In Linux, the echo command is used to show a line of text/string that has been passed as an argument. This is a built-in command that outputs status text to the screen or a file. It's mainly used in shell scripts and batch files.
Syntax:
Echo "enter text"
Example:
In this example, we use the -p command line option to enter the input on the same PROMPT:
Read -p PROMPT <variable_name>
Echo option
-n: The trailing newline should not be production.
-E: STRINGs would not be able to read certain sequences.
Example:
Who command
Who w – Command: UNIX maintains an account for all the current system. Because it is a multi-user system it is prudent for the user to be aware of other current users so that s/he can communicate with them if required. The user login details of all the current users by using the who command. The use of who command provides a list of all the current users in the three-column format by default, as shown follows:
$ who
Raj console Nov 19 09:35
Reena tty01 Nov 19 09:40
Priya tty02 Nov 19 09:41
The first column shows the name of the users, the second column shows the device names and the third column shows the login time. Some options like -H, -u and -T can be used with this command.
The H option provides headers for the columns and the -u option provides more details like idle time, PID and comments as shown in the example below.
$ who-Hu
NAME LINE TIME IDLE PID COMMENTS
Raj console Nov 19 09:35 # 32
Reena tty01 Nov 19 09:40 0:20 33
Priya tty01 Nov 19 09:41 0:40 34
If any terminal is idle If any terminal is idle (not active) for the last 1 minute, the information, that is, for how long that terminal is idle will be indicated on the IDLE column. Thus, 0:20 indicates that reena's terminal is IDLE for the last 20 minutes. This information will be useful to the system administrator. The PID indicates the process identification number. The self-login details of a user can be obtained as a single line output using am and i arguments along with the who command as follows.
$ who am i
Reena tty01 Nov 1909:40
Generally, the who command is used by the system administrator for monitoring terminals.
The w command is a quick way to see who is logged on and what they are doing.
Mkdir
The command mkdir means 'make directory.' You can construct a new directory anywhere in your system by using the mkdir command. Simply type "mkdir dir name>" (instead of dir name>, type the name of the new directory you want to create) and hit enter.
Syntax:
Mkdir <dirname>
Mkdir option
Option | Description |
Mkdir, -p, -parents | Add the directory, as well as its subdirectories. |
Mkdir, -v, -verbose | For each newly formed directory, print a message. |
Mkdir -m -mode=MODE | Set the permissions for entry. |
Rmdir
Removing Directories
The rmdir command can be used to remove directories as follows:
$rmdir dirname
$
If you want to delete a directory, make sure it's empty, which means there should be no files or subdirectories inside.
You can delete several folders at the same time by doing the following:
$rmdir dirname1 dirname2 dirname3
$
If the directories dirname1, dirname2, and dirname3 are empty, the command above removes them. If the rmdir command is effective, no output is generated.
Rmdir -p
This command deletes a directory and all of its subdirectories at the same time. The command 'rmdir -p' was used to remove all sub-directories.
Cd
To modify the current working directory in Linux, use the cd command ( i.e., in which the current user is working). 'Change directory' is represented by the letter "cd." In the Linux terminal, it's one of the most commonly used commands.
Syntax:
Cd <dirname>
It's one of the most critical and widely used commands in the Linux system, and you'll see it a lot. We can navigate through our system's directories with the aid of this order. We may go back to the previous directory, forward to the next directory, or anywhere else.
The cd command can be used for more than just changing directories. By specifying a valid absolute or relative path, you can change to any directory. The syntax is as follows:
$cd dirname
$
The name of the directory you want to change to is provided by dirname. For instance, the command
$cd /usr/local/bin
$
Changes to the /usr/local/bin directory. You may use the following relative path to cd to the directory /usr/home/amrood from this directory:
$cd ../../home/amrood
$
Listing Files
Use the following command to get a list of the files and folders in the current directory:
$ls
Here is an example of the above command's output:
$ls
Bin hosts lib res.03
Ch07 hw1 pub test_results
Ch07.bak hw2 res.01 users
Docs hw3 res.02 work
The -l option of the programme ls can be used to gain extra information about the files shown.
$ls -l
Total 1962188
Drwxrwxr-x 2 amrood amrood 4096 Dec 25 09:59 uml
-rw-rw-r-- 1 amrood amrood 5341 Dec 25 08:38 uml.jpg
Drwxr-xr-x 2 amrood amrood 4096 Feb 15 2006 univ
Drwxr-xr-x 2 root root 4096 Dec 9 2007 urlspedia
-rw-r--r-- 1 root root 276480 Dec 9 2007 urlspedia.tar
Drwxr-xr-x 8 root root 4096 Nov 25 2007 usr
Drwxr-xr-x 2 200 300 4096 Nov 25 2007 webthumb-1.01
-rwxr-xr-x 1 root root 3192 Nov 25 2007 webthumb.php
-rw-rw-r-- 1 amrood amrood 20480 Nov 25 2007 webthumb.tar
-rw-rw-r-- 1 amrood amrood 5654 Aug 9 2007 yourfile.mid
-rw-rw-r-- 1 amrood amrood 166255 Aug 9 2007 yourfile.swf
Drwxr-xr-x 11 amrood amrood 4096 May 29 2007 zlib-1.2.3
$
Here's the lowdown on each of the listed columns.
● The file type and permissions granted on the file are represented in the first column. The following is a list of all types of files and their descriptions.
● The number of memory blocks taken by the file or directory is represented in the second column.
● The owner of the file is represented by the third column. This is the name of the Unix user who made this file.
● The owner's group is represented in the fourth column. Every Unix user will be assigned to a group.
● The file size in bytes is represented in the fifth column.
● The date and time when this file was last created or updated are represented in the sixth column.
● The file or directory name is represented in the seventh column.
Metacharacters
In Unix, metacharacters have a special meaning. * and?, for example, are metacharacters. A question mark (?) matches a single character, while * matches 0 or more characters.
For Example −
$ls ch*.doc
Displays all files with names that begin with ch and conclude with.doc.
Ch01-1.doc ch010.doc ch02.doc ch03-2.doc
Ch04-1.doc ch040.doc ch05.doc ch06-2.doc
Ch01-2.doc ch02-1.doc c
* serves as a meta character that can be used with any other character. If you only want to see files that end in.doc, type the following command.
$ls *.doc
Hidden Files
The dot or the period character is the first character of an unseen file (.). The majority of these files are used by Unix programmes (including the shell) to hold configuration information.
Among the most common hidden files are the folders-
● .profile − The Bourne shell ( sh) initialization script
● .kshrc − The Korn shell ( ksh) initialization script
● .cshrc − The C shell ( csh) initialization script
● .rhosts − The remote shell configuration file
Specify the -a option to ls to list the hidden files.
$ ls -a
. .profile docs lib test_results
.. .rhosts hosts pub users
.emacs bin hw1 res.01 work
.exrc ch07 hw2 res.02
.kshrc ch07.bak hw3 res.03
$
● Single dot (.) − This represents the current directory.
● Double dot (..) − This represents the parent directory.
Creating Files
On any Unix system, the vi editor can be used to create ordinary files. All you have to do is type the following command:
$ vi filename
The command above will open a file with the specified name. To access the edit mode, hit the key i. You can start writing your information in the file once you're in edit mode, as seen in the following programme.
This is unix file....I created it for the first time.....
I'm going to save this content in this file.
When you've finished with the programme, follow these instructions.
● To exit the edit mode, press the esc key.
● To exit the file altogether, press the keys Shift + ZZ simultaneously.
In the current directory, a file named filename will be created.
$ vi filename
$
Editing Files
The vi editor can be used to edit an existing file. We'll go over how to open an existing file in a nutshell.
$ vi filename
You can enter edit mode by pressing the key I after the file has been opened, and then you can edit the file. If you want to move about within a file, you must first exit edit mode by pressing Esc. After that, you can navigate within a file by pressing the following keys:
● l key to move to the right side.
● h key to move to the left side.
● k key to move upside in the file.
● j key to move downside in the file.
As a result, you can put your cursor wherever you wish to modify using the keys listed above. After you've positioned yourself, press the I key to enter edit mode. After you've finished modifying your file, use Esc and then the two keys Shift + ZZ simultaneously to exit it fully.
Display Content of a File
The cat command can be used to view the contents of a file. Here is a simple sample of the content of the previously produced file:
$ cat filename
This is unix file....I created it for the first time.....
I'm going to save this content in this file.
$
Using the -b option with the cat command, you can see the line numbers as follows:
$ cat -b filename
1 This is unix file....I created it for the first time.....
2 I'
Copying Files
Use the cp command to make a copy of a file. The command's fundamental syntax is as follows:
$ cp source_file destination_file
The following is an example of how to make a copy of an existing file named filename.
$ cp filename copyfile
$
In your current directory, you will now notice another file named copyfile. The name of this file will be identical to the name of the original file.
Deleting Files
Use the rm command to remove an existing file. The fundamental syntax is as follows:
$ rm filename
A file may contain useful information, so proceed with caution. It's usually a good idea to use caution while using the Delete command. It is preferable to use the -i option in conjunction with the rm command.
The example below demonstrates how to entirely delete the existing file filename.
$ rm filename
$
You can remove multiple files at a time with the command given below −
$ rm filename1 filename2 filename3
$
Ls - list directory contents. The command to list our directories and files is ls, With options it can provide information about the size, type of file, permissions, dates of file creation, change and access.
Syntax:
Is [options] [argument]
Common Options: When no argument is used, the listing will be of the current directory. There are many useful options for the Is command. A listing of many of them follows. When using the command, string the desired options together preceded by "."
-a lists all files, including those beginning with a dot (.)
-d lists only names of directories, not the files in the directory
-F indicates type of entry with a trailing symbol:
Directories /
Sockets =
Symbolic links @
Executables*
-g displays Unix group assigned to the file, requires the -l option (BSD only)-or on an SVR4 machine, e.g. Solaris, this option has the opposite effect
-L if the file is a symbolic link, lists the information for the file or directory the link references, not the information for the link itself.
-I long listing: lists the mode, link information, owner. Size. Last modification time).
If the file is a symbolic link, an arrow (-->) precedes the pathname of the linked-to file.
The mode field is given by the -I option and consists of 10 characters. The first character is one of the following:
Character if entry is a:
d directory
- plain file
b block-type special file
c character-type special file
1 symbolic link
s socket
The next 9 characters are in 3 sets of 3 characters each. They indicate the file access permissions: the first 3 characters refer to the permissions for the user, the next three for the users in the UNIX group assigned to the file, and the last 3 to the permissions for other users on the system.
Designations are as follows:
r read permission
w write permission
x execute permission
-no permission
There are a few less commonly used permission designations for special circumstances. These are explained in the man page for ls.
Examples:
(i) To list the files in a directory:
$ ls
Demofiles frank linda
(ii) To list all files in a directory, including the hidden (dot) files try:
$ Is –a
..cshrc .history -plan .rhosts frank
...emacs .login .profile demofiles linda
(iii) To show the hidden files, but not the current directory) and (parent directory), use option -A.
(iv) To show all the files recursively, use -R option. When we do this from /, it shows all the unhidden files in the whole file system recursively.
$Is /etc/sysconfig/networking
Devices profiles
$Is -R -R/etc/sysconfig/networking
/etc/sysconfig/networking:
Devices profiles
/etc/sysconfig/networking/devices:
/etc/sysconfig/networking/profiles:
Default
/etc/sysconfig/networking/profiles/default:
(v) To get a long listing:
$ Is-al
Total 24
Drwxr-sr-x 5 workshop acs 512 Jun7 11:12 .
Drwxr-xr-x 6 root sys 512 May29 09:59 ..
-rw-------- 1 workshop acs 525 May20 21:29 .emacs
-rwxr-xr-x 1 workshop acs 238 May 14 09:44 .login
-rw-r—r-- 1 workshop acs 273 May 22 23:53 .plan
-rwxr-xr-x 1 workshop acs 413 May 14 09:36 .profile
Drwx------- 3 workshop acs 512 May 24 11:18 demofiles
Drwx------- 2 workshop acs 512 May 21 10:48 frank
Drwx------- 3 workshop acs 512 May 24 10:59 linda
Instead of doing the 'ls - and then the checking for the first character to determine the type of file. We can use -F which classifies the file with different special character for different kind of files.
$ ls -F
Desktop/ Documents/ Ubuntu-App@ firstfile Music/ Public/ Templates/
Thus in the above output
/-directory.
Nothing - normal file.
@- link file.
*- Executable file
(vi) $ Is-d Displays only directories
(vii) $ Is -r Displays files in reverse order.
(viii) $ Is -f Interprets each name as a directory, not a file.
Mv command
Mv - move a file: Rename a file with the move command, mv.
Syntax: mv (options] old_filename new_filename
Common Options:
-i interactive (prompt and wait for confirmation before proceeding)
-f don't prompt, even when copying over an existing target file (overrides-i)
Examples:
$ mvold_filename new_filename
i) We now have a file called new_filename and the file old filename is gone. Actually all we've done is to update name the directory table entry to give the file a new name
Ii) The contents of the file remain where they were.
Cat command
The command 'cat' is the most often used and powerful. It's regarded as one of the most commonly used commands. It can display a file's content, copy content from one file to another, concatenate the contents of multiple files, display the line number, display $ at the end of a line, and so on.
Syntax:
Cat [OPTION]... [FILE]..
To make a file, follow these steps:
Cat > <file name>
// Enter file content
To save the file, press the "CTRL+ D" keys. To see the contents of the file, run it like this:
Cat <file name>
Linux cat command usage
Option | Function |
Cat > [fileName] | To create a file. |
Cat [oldfile] > [newfile] | Copy material from an older file to a new one. |
Cat [file1 file2 and so on] > [new file name] | To combine the contents of several files into a single file. |
Cat -n/cat -b [fileName] | To display line numbers. |
Cat -e [fileName] | The $ character will be displayed at the end of each line. |
Cat [fileName] <<EOF | Used to indicate the end of a page. |
Cp command
'cp' stands for copy. To copy a file or a directory, use the 'cp' command.
Syntax:
To copy in the same directory:
Cp <existing file name> <new file name>
Cp Options
Option | Function |
Cp -r | To duplicate a directory and all of its subdirectories.. |
Cp file1 file 2 directory name | Multiple files or directories in a directory are copied. |
Cp -backup | Before overwriting an existing file, make a backup. |
Cp -i | Asks for confirmation. |
Cp -l | To create a file with a hard link. |
Cp -p | Preserves a file's attribute. |
Cp -u -v | To ensure that the source file is older than the destination file. |
Rm command
'rm' stands for 'remove.' To remove a file, use this command. Unlike other GUIs, the command line does not feature a recycling bin or trash to recover files. As a result, exercise extreme caution when using this command. When you delete a file, it is permanently deleted.
Syntax:
Rm <file name>
Rm Options
Option | Description |
Rm *extension | Deletes files with the same extension. |
Rm -r or R | To recursively erase a directory. |
Rm -i | Interactively delete a file. |
Rm -rf | Forcefully delete a directory. |
A file type is used to describe the type of data that is saved in a file. Linux recognizes seven different file forms. Regular files, Directory files, Link files, Character special files, Block special files, Socket files, and Named pipe files are all examples of file types.
A list of these file types can be found in the table below.
/-----------------------------------------------\
|-|Regular File|
|d|Directory|
|l|Symbolic Link|
|b|Block Special File|
|c|Character Special File
|p|Named Pipe|
|s|Socket|
\-----------------------------------------------/
Regular file
Text, audio, video, images, scripts, and programs are only some of the content types that can be stored in regular or ordinary files. There are a plethora of content styles to choose from. Standard files, with or without an extension, can be built in Linux.
An extension is a collection of characters added to the end of a file name to give it a unique identity or to group it with other files of the same type of material. Files of various content types often use well-known file extensions for ease of identification and processing.
Despite the fact that the Linux file system does not need file extensions, you can still use them. They assist us in recognizing the different types of content contained in files. If a file's extension is.mp4, for example, you can assume it's a video file.
The /etc/mime.types file contains a full list of content types and file extensions that your Linux framework supports. The MIME (Multipurpose Internet Mail Extensions) standard assigns file content types a standard designation and classification.
To access the contents of this file, use any standard file reading command.
Directory
File systems use folders to arrange data in a hierarchy. Directories are similar to files, but instead of storing data, they keep track of where other files are located. Directory entries are used to store the location of files stored in the directory. A single file's name and location are stored in each directory entry.
The Linux file system begins with the directory /, also known as the root directory. This directory is where all files and directory files are made. Each directory, with the exception of the root directory, has a parent directory.
Symbolic link
We can use a file with a different filename and from a different location with link files. We use connecting files for this. A connection file is a file that contains a reference to another file. A hard connection and a symbolic or soft link are the two forms of connections.
A hard connection makes a copy of the original file that is identical to it. A hard connection to a directory or file on another filesystem is not possible. A reference to the original file is created by a soft or symbolic connection. A soft connection to a directory or file on another filesystem can be formed.
Block or Character special file
Block Special Files are used to communicate with hardware in blocks of data of 512 bytes, 1024 bytes, or 2048 bytes, depending on the hardware.
Hard drives, printers, displays, terminal emulators, and CD/DVD drives are all treated as special files in Linux. This ensures that a program can view and use files and devices in the same way that a user can. This feature makes it simpler and more versatile to build programs in Linux.
The /dev directory is where Linux stores all special files and system files. A character special file and a block special file are the two types of special files. A character special file represents a computer, such as a monitor or printer, that transfers data in bytes. A block special file represents a computer, such as a hard drive, that transfers data in blocks.
One character at a time is communicated with hardware using the Character Special File. Block and Character Special Files are usually found in the /dev directory.
Named pipe
A named pipe is a file that transfers data from one process to another.
The data that is passed between one process writing data into a named pipe and another process reading data from the named pipe is not stored in the named pipe. The mkfifo command can be used to build a named pipe.
We can use Linux to send the output of some process or command as the input to another process or command. The pipe is the name for this element. Only when both processes are initiated by the same user and are in the same parent process space do pipes function.
Standard pipes will not function if processes are run under different user names and permissions. Named pipes are used in these situations. Named pipes are similar to regular pipes, but they can be accessed via the filesystem.
The empty pipe files are known as named pipe files. Named pipe files are processed by the kernel without being written to the file system. Pipe files with names can be found anywhere in the file system. The FIFO (First In First Out) files are also known as pipe files.
Socket
The Socket File is a stylized inter-process communication mechanism.
It is highly uncommon for a user or even a system administrator to build a socket directly.
A socket is a data-exchange communication endpoint used by applications. When an application needs to communicate with another application, it connects to the application's socket.
A socket is used for any application that offers services to other applications or remote clients. Each socket has an IP address and port number associated with it, allowing it to accept connections from clients.
For example, if a local system application needs to communicate with a remote system application, it connects to that application's socket using the IP address and port number associated with that socket.
Sockets are very difficult to understand. Socket files are used by Linux to make communication between local applications easier. Socket files allow local device applications to share data without having to go through the complicated networking and sockets processes.
Socket files are files that use a file name instead of an IP address and port number as their address. To allow inter-process communication between local applications, socket files use the sendmsg() and recvmsg() system calls.
Key takeaway:
Directories are similar to files, but instead of storing data, they keep track of where other files are located.
Block and Character Special Files are usually found in the /dev directory.
A named pipe is a file that transfers data from one process to another.
A socket is used for any application that offers services to other applications or remote clients.
The Socket File is a stylized inter-process communication mechanism.
Chmod: Changing file permissions: The command name chmod stands for "change mode", and it is used to define the way a file can be accessed. Chmod (change mode) is one of the most frequently used commands in unix or linux operating system. The chmod command is used to change the file or directory access permissions.
Syntax:
Chmod [options] permissions filename
There are three different permissions. They are:
Read (4): Permitted to read the contents of the file. In case of directory, you can view all the files and subdirectories in that directory
Write (2): Permitted to write to the file. In case of directory, you can create files and sub-directories
Execute (1): Execute the file as a program/shell script. In case of directory, You can enter into that directory.
Here in the above, the numbers in the brackets represents the numeric values for the corresponding permissions. If you want to have a combination of permissions add the required numbers. For example, for read and execute, it is 4+1= 5.
Chmod [options]
-R: recursively change the permissions of a directory.
-v: Verbose
Chmod Examples in Linux / Unix:
1. Give read, write and execute permissions to everyone. Read, write and execute: 4+2+1=7
$ chmod 777 sample.sh
In the above example, you can see that the permissions are specified with a three digit number. The first digit is for user permissions, second is for group and third is for others permission. This type of representation is called octal representation. Alternatively, you can use the symbolic representation to give the permissions.
Chmod ugo+rwx sample.sh
We will see more details about the symbolic representation later.
2. Give read permission to user, write permission to group and execute permission to others
$ chmod 421 sample.sh
3. Recursive permissions to directory
To give read and write permissions to all the users to a directory (including files and subdirectories) use the recursive option -R.
Chmod -R 666 /dir
Symbolic Representation of Permissions: The following symbols are used to represent the users, groups and others:
● u: User
● g: Group
● o: Others
● a: All (user, group and others)
The following symbols represent the permissions:
● r: read
● W: write
● X: execute
The following symbols represent the permissions grant or revoke:
● + : Additional permissions. Selected permissions are added.
● - : Revoke the permissions. Selected permissions are revoked.
● = : Specific permissions. Only selected permissions are assigned.
Examples
1. Remove write permission from group
$ chmod g-w sample.sh
This will only removes the write permission for the group.
2. Add new permission execute to others
$ chmod o+x sample.sh
In addition to the existing permissions, this will add execute permission to others.
3. Give only read permissions to the user
$chmod u=w sample.sh
This will remove the existing permissions to the user and gives only write permission to the user.
The first n lines of the supplied text files are displayed.
We can filter / read the first or top lines or row of data, as the name implies. It will read the first 10 lines or records of the given data by default. If we need to read additional lines, we must use the "-n" option to define the number of lines that we need to read.
Syntax:
Head [-number_of_lines_to_print] [path]
Head -n 7 file.txt
Explanation:
● We have a data sample file with ten records in it.
● The default "head" command is now being used to read the data file.
● We'll use the "-n" option to read the number of lines of records if we need to read or get data other than the default value.
Cat file.txt
Output
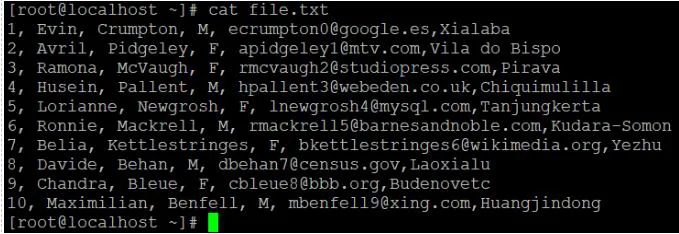
Head file.txt
Output:
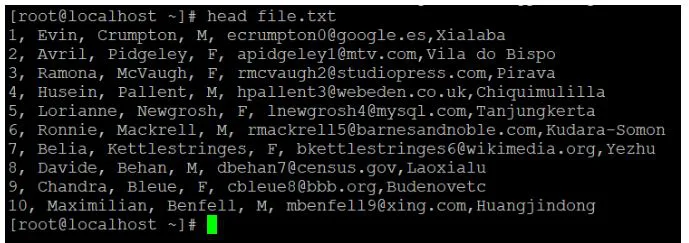
Head -n 7 file.txt
Output:
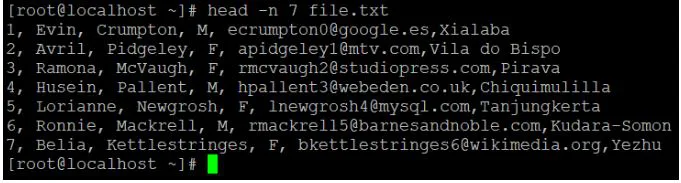
Tail
We'll use the tail command to collect data from the bottom of the file if we need it. It will read the latest 10 lines or records of the given data by default. If we need to read additional lines, we must use the "-n" option to define the number of lines that we need to read.
Syntax:
Tail <file name>
Code:
Tail -n 3 file.txt
Explanation:
● To read the data file, we use the default "tail" command.
● We'll use the "-n" option to read the number of lines of records if we need to read or get data other than the default value.
Tail file.txt
Output:
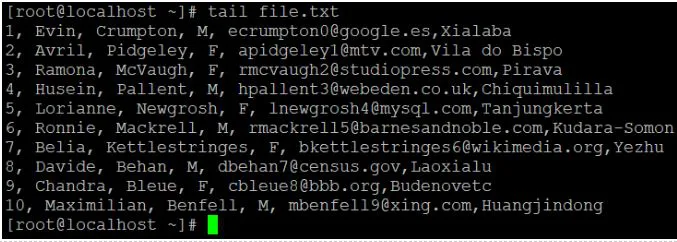
Tail -n 4 file.txt
Output:
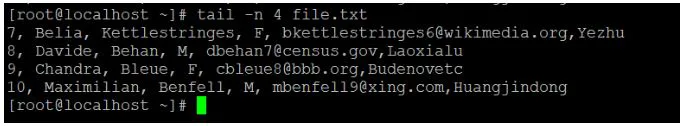
Sort
Sorting text lines alphabetically or numerically is done with the sort command. The lines in the food file are sorted in the following example.
$sort food
Afghani Cuisine
Bangkok Wok
Big Apple Deli
Isle of Java
Mandalay
Sushi and Sashimi
Sweet Tooth
Tio Pepe's Peppers
$
By default, the sort command groups text lines alphabetically. There are numerous choices for controlling the sorting.
Sr.No. | Description |
1 | -n Sorts numerically (example: 10 will sort after 2), ignores blanks and tabs. |
2 | -r Reverses the order of sort. |
3 | -f Sorts upper and lowercase together. |
4 | +x Ignores first x fields when sorting. |
A pipe can be made up of more than two commands. Using grep and a prior pipe example, we can further sort the files updated in August by size.
The commands ls, grep, and sort make up the following pipe.
$ls -l | grep "Aug" | sort +4n
-rw-rw-r-- 1 carol doc 1605 Aug 23 07:35 macros
-rw-rw-r-- 1 john doc 2488 Aug 15 10:51 intro
-rw-rw-rw- 1 john doc 8515 Aug 6 15:30 ch07
-rw-rw-rw- 1 john doc 11008 Aug 6 14:10 ch02
$
This pipe organises all of the files in your August-modified directory by size and prints them on the terminal screen. The +4n sort option skips four fields (fields are separated by blanks) before sorting the lines numerically.
Grep
The grep command looks for lines that match a pattern in a file or files. The syntax is as follows:
$grep pattern file(s)
The term "grep" comes from the command g/re/p in the ed (a Unix line editor), which means "globally search for a regular expression and print all lines containing it."
A regular expression is a combination of plain text (for example, a word) and special characters that are used to match patterns.
The most basic application of grep is to seek for a single-word pattern. It can be used in a pipe to send to the standard output just the lines of the input files that contain a specific string. If you don't give grep a filename to read, it reads its standard input; that's the way all filter programs work −
$ls -l | grep "Aug"
-rw-rw-rw- 1 john doc 11008 Aug 6 14:10 ch02
-rw-rw-rw- 1 john doc 8515 Aug 6 15:30 ch07
-rw-rw-r-- 1 john doc 2488 Aug 15 10:51 intro
-rw-rw-r-- 1 carol doc 1605 Aug 23 07:35 macros
$
You can use the grep command with a number of different arguments.
Sr.No. | Option & Description |
1 | -v All lines that do not match the pattern are printed. |
2 | -n The matching line and its line number are printed. |
3 | -l Only the names of files with matching lines are printed (letter "l"). |
4 | -c Only the number of matching lines is printed. |
5 | -i Matches upper and lowercase letters. |
Vi stands for visual editor. It is a full screen editor. It is available with almost all the UNIX variants. Vi editor became famous because of its full screen editing capabilities and many other visual options. Vi editor is available under Linux in the form of vim (vi improved). It uses the terminal display as a window to the buffer and 25 lines can be displayed at all times. All unused lines of a file are marked by a -(tilde) called as empty buffer line flag. The last line is reserved for commands. The vi editor works in three modes that are:
1. The Command mode: This is the mode into which the user gets into as soon as the vi command is invoked from shell by using vi <filename>. In this mode all the keys pressed by the user are interpreted to be the editor commands. The keys that are pressed are not displayed on the screen. The user can get into the input mode by giving o, O, r, R, i, I, s, S, a, A commands.
2. The input mode: This mode is also known as insert mode. This mode permits the insertion of new text, appending to the existing text and replacement of the text. To exit or switch from this mode to command mode press Esc key.
3. The ex mode: This mode is also known as last line mode and allows user to use the commands in the bottom line (command line) on the vi screen. From the command mode the user can get in to the ex mode by typing the colon character (). Here this character is displayed in the command line. A colon (:) indicates that the editor is now in the ex mode. The user can get back to the command mode by using the Enter key
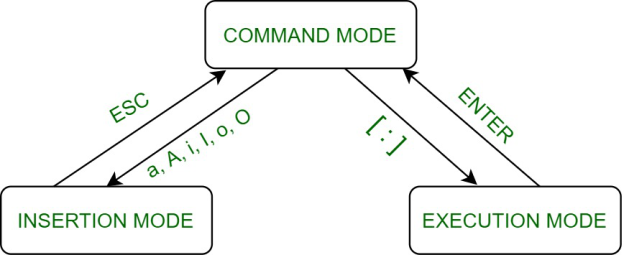
1. The input mode command:
(i) Insert (i, I):
i - Insert text to the left of the cursor position. Existing text will be shifted right
This is a file
Isimple [Esc]
This is a simple file
I- Insert text at the beginning of the line.
This is a file
I/*[Esc]
/*This is a simple file
(ii) Append (a, A):
a- Append text to the right of the cursor position. Existing text will be shifted right.
This is a file
Isimple [Esc]
This is a simple file
A- Appends text at end of the line.
This is a file
A*/ [Esc]
This is a simple file */
(iii) Open a line (o, O):
o- Opens a new line below the current line.
Hello
How
You
Oare [Esc]
Hello
How
Are
You
O-Opens a new line above the current line.
Hello
How
You
Osumit [Esc]
Hello
Sumit
How
Are
You
(iv) Replace (r, R, s, S):
r- Replace single character.
This is a dile
Rf
This is a file
R-Replaces all text on the right of the cursor position.
This is a simple file
Rdevice[Esc]
This is a device file
s- Replace one character with many.
This is a device file
Sone[Esc]
This is one device file
S - Replaces the entire line irrespective of the cursor position (existing line disappears).
2. The ex-mode command:
(i) :w- To save a file and remain in the editing mode.
: w
"ss", 8 lines, 150 characters
The message shows the name of the file i.e. ss along with the number of lines and character saved. We can also specify another file in the last line (In MS word, save as).
:w ss1
"ss1", 8 lines, 150 characters
If ssl is already exist then we use exclamation mark (!) with w
:w! ss1
Content of ss will be overwrite to ssl.
If we want to save fifth line to the another file then we will use
: 5w ss1
If we want to save ten to fifteenth line to the another file then we will use
: 10, 15w ss1
There are two symbols used with w have special significance - The dot (,) and dollar ($). The dot (.) represents the current line and dollar ($) represent the last line.
:.w ss1 //saves current line
: $w ss1 //saves last line
: .,$ ss1 //saves current line through end
(ii): q - Aborting editing : It is also possible to abort the editing process and quitting from the editing mode without saving the content with the help of : q command.
: q[enter]
$_
Vi also has a safety mechanism that prevents we from aborting accidentally if we have modified the file. The following message will be displayed.
No write since last change
If the buffer has been changed and we still want to abandon the changes then we will use
:q! //ignores all changes made and quits
(iii): wq - saving and quitting : We can also use: wq to save and exit from vi editor.
:wq ss1
(iv):sh - Escapes to UNIX shell:
Vi editor provide temporary escape to the shell to run the cc command.
:sh
This return a shell prompt execute cc or any other command here and then return to the editor using exit or
[Ctrl - d]
/* don't execute vi command once again - an undesirable situation */
3. The command mode command:
A command mode command doesn't on the screen but simply performs a function.
k- Moves cursor up
i- Move cursor down
h - Moves cursor left
1 - Moves cursor right
The repeat factor can be used as a command prefix with all these four commands. Thus 4k command moves the cursor 4 lines up and 20h takes it 20 characters to the left
b - Moves back to the beginning of word
w - Moves forward to the beginning of word
e - Moves forward to the end of word
0 - Moves cursor to extreme left
$ - Moves cursor to extreme right
|(pipe) - Moves cursor to specific column
The repeat factor can also be used with this command. Thus 5b takes the cursor 5 words back and 3w takes the cursor three words forward.
[Ctrl – f]- Scroll forward
[Ctrl - b]- Scrolls backward
[Ctrl – d]- Scrolls half page forward
[Ctrl – u]- Scrolls half page backward
The repeat factor can also be used with this command. Thus 10[Ctrl – f], to scroll 10 pages forward. When we start vi editor, it displays the total number of lines in the last line. To know the current line number we will use.
[Ctrl – g]- To know the current line number
"file1" [read only] line 67 of 233 -32%-
The cursor is on line 67 i.e. (32% of 233)
(i) G- Move to the specific line number (absolute movement)
23G //Goes to line number 23
1G //Goes to line number 1
G //Goes to end of file
(ii) x - Deletes a single character: The character under the cursor gets deleted and the text on the right shifts left to fill up the space. A repeat factor also used here. Thus 4x deletes the current character as well as three characters from the right
Dd - Deletes an entire line:
Dd command deletes a current line where cursor can be anywhere in the line. A repeat factor can also be used here, thus 4dd deletes the current line as well as three lines below.
p- Put character on the right of the cursor
When we delete parts of line
P- Put character on the left of the cursor
e.g.
If we want to correct sdtio.h to stdio.h, then we will have to transpose the characters d and t, i.e. delete the d and put it after t. Move your cursor to the d in sdtio.h then press.
x //sdtio.h becomes stio.h :cursor on t
p //d put on right : stio.h becomes stdio.h
p - Put character on the above of the current line When we delete an entire line
P- Put character on the below of the current line
p and P place text on the left and right only when you delete parts of lines. But the same keys get associated with above and below when we delete complete line.
(ii) Yanking (copying) the text:
Yh - Yank a character to the left of the current cursor position.
3yh - Yank three characters to the left of the current cursor position.
Yw - Yank from the current character to the next word.
Yor yy - Yanks the current line.
y2k - Yank current line and two lines above the current line.
3Y or 3yy - yank three lines including the current line.
Y$ - Yank till the end of the current line.
y) - Yank from the current character to next sentence.
y} - Yank from the current character till the end of the paragraph.
3y - yank three character.
(iii) Joining the line:
J - To join the current line and the line following it.
4J - To join the current line with 3 lines following it.
(iv) Undoing last editing instruction:
u - Undo the most recent single editing change by restoring the position before the change.
U-Undo all the changes before move away from the line.
[Ctrl -r] This command is used to redo the undone actions.
The repeat factor also works here. 10u is completely reversed with 10[Ctrl -r]
(v) Searching for a pattern (/ or?):
/pattern - Searches forward for pattern.
?pattern - Searches backward for pattern.
Eg.
If we are looking for the string echo, Then use
/echo @
The search begins forward to position the cursor on the first instance of the word, vi searches the entire line, so if the pattern can't be located till the end of the file is reached the search wraps around to resume from the beginning of the file. If the search still fails, vi respond with the message pattern not found
?echo @ (same like /)
The search begins backward direction.
Repeating the last pattern search:
n - Repeats search in same direction along which previous search was made.
N - Repeats search in opposite direction to that along which previous search
Was made.
Command mode
You can use this mode to conduct administrative activities including saving files, running commands, moving the cursor, cutting (yanking) and pasting lines or words, and finding and replacing. Whatever you type in this mode is regarded as a command.
Vi starts in command mode by default. You must be in insert mode to enter text, which you may do by typing i. To exit the insert mode, press the Esc key, which will return you to command mode.
You can move around by pressing the arrow keys or the vi movement keys, as shown below:
h | Left |
j | Down |
k | Up |
l | Right |
Insert mode
This mode allows you to add text to the document. In this mode, whatever you type is treated as input and saved to the file.
You can insert or append text in the input mode. In command mode, press I to insert text before the cursor's current position. Similarly, you can use a to append after the cursor. Keep in mind that you can't use the cursor keys in this mode. When you're through typing, press Esc to return to command mode.
Ex mode
This mode is used to enter commands on the command line at the bottom of the vi editor. Press the escape key to enter Ex command mode, then type: (colon). To save the contents of the vi editor and exit it, hit wq after the: (colon). Wq.
Ex mode is a command mode that has been extended. To get started, press Esc, then: (the colon). At a colon prompt, the pointer will move to the bottom of the screen. Enter:w to create a new file and:q to close it. By entering:wq, you can save and exit at the same time. If you're done with your file, though, Shift-z-z from command mode is usually more convenient.
References:
1. Operating System Concepts – Silberschatz, Galvin and Gagne
2. Operating System By Godbole
3. Linux Bible 9th Edition by Christoper Negus ISBN :978-1-118-99987-5
4. Ball, Using Linux, PHI, 1998. ISBN-10: 0789716232
5. UNIX: Concepts and Applications Das (4th Ed), TMH, 2006 ISBN 13: 9780070635463