Unit 6
Cloud computing services and data security in cloud
Iaas is called as Hardware as a Service (HaaS). It is a layer of the cloud computing platform. It supports customers to outsource their IT infrastructures like servers, networking, processing, storage, virtual machines, and other resources. Customers access these resources on the Internet using a pay-per-use method.
In traditional hosting services, IT infrastructure is also rentedout for a specific period of time, with fixed hardware configuration. The client paid for the configuration and time, regardless of the actual use. With the help of the IaaS layer, clients dynamically change the configuration to fulfill changing requirements and are billed only for the services actually used.
IaaS cloud computing platform layer eliminates the need for each organization to maintain the IT infrastructure.IaaS is used in three models like public, private, and hybrid cloud. The private cloud support the infrastructure resides at the customer-premise. In public cloud, it is located at the cloud computing platform vendor's data center, and the hybrid cloud is a combination of the two in which the customer selects the best of both public cloud and private cloud.
IaaS provider provides the following services such as
- Compute
Computing as a Service contains virtual central processing units and virtual main memory for the VMs that is provisioned to the end-users.
2. Storage
IaaS provider provides back-end storage for storing data as well as files.
3. Network
Network as a Service (NaaS) provides networking components like routers, switches, and bridges for the virtual machines.
4. Load balancers
It provides load balancing capability at the infrastructure layer.
Advantages of IaaS
Following are the advantages of IaaS computing layer
1. Shared infrastructure
IaaS support multiple users to share the same physical infrastructure.
2. Web access to the resources
Iaas allows IT users to access multiple resources on the internet.
3. Pay-as-per-use model
IaaS provide services on the pay-as-per-use basis that means users are required to pay for what they have used.
4. Focus on the core business
IaaS providers focus on the organization's core business instead of IT infrastructure.
5. On-demand scalability
On-demand scalability is one of the most important advantage of IaaS. Using IaaS, users do not need to upgrade software and troubleshoot the issues related to hardware components.
Disadvantages of IaaS
1. Security
Security is a biggest issues in IaaS. Most of the IaaS providers are not able to provide 100 percent security.
2. Maintenance and Upgrade
The IaaS service providers maintain the software, but they do not upgrade software for the some organizations.
3. Interoperability issues
It is difficult to migrate VM from one IaaS provider to the other therefore customers may be face problem related to vendor lock-in.
About IaaS
IaaS cloud computing platform can’t replace the traditional hosting method, but it provides more than that, and every resource are predictable as per the usage.
IaaS cloud computing platform not eliminate the need for an inhouse IT department. It will be need to control the IaaS setup. Breakdowns at the IaaS cloud computing platform vendor's can halt your business. The Service Level Agreement provide backups for data, hardware, network, and application failures. It also provide image portability and third-party support.
The IaaS cloud computing platform vendor get access to your sensitive data. Therefore engage with credible companies or organizations and also study their security policies and precautions.
Iaas Providers
IaaS Vendor | Iaas Solution | Details |
Amazon Web Services | Elastic, Elastic Compute Cloud (EC2) MapReduce, Route 53, Virtual Private Cloud, etc. | The cloud computing platform Amazon perform automatic scaling, cloud monitoring, and load balancing features. |
Netmagic Solutions | Netmagic IaaS Cloud | Netmagic runs from data centers in Mumbai, Chennai, and Bangalore, and a virtual data center in the United States. |
Rackspace | Cloud servers, cloud files, cloud sites, etc. | The cloud computing platform vendors arekeep the track of enterprise-level hosting services. |
Reliance Communications | Reliance Internet Data Center | RIDC supports both traditional hosting and cloud services, with data centers in Mumbai, Bangalore, Hyderabad, and Chennai. The cloud services provided by RIDC contains IaaS and SaaS. |
Sify Technologies | Sify IaaS | Sify's cloud computing platform is powered by HP's converged infrastructure. The vendor support three types of cloud services: IaaS, PaaS, and SaaS. |
Tata Communications | InstaCompute | InstaCompute is Tata Communications IaaS offering. InstaCompute data centers is located in Hyderabad and Singapore and operations performed in both countries. |
Platform as a Service (PaaS) it provides a runtime environment for applicatons. It supports programmers to easily create, test, run, and deploy web applications. You can also purchase these applications from a cloud service provider on a pay-as-per use basis and access with the Internet connection. In PaaS cloud computing layer back end is managed by the cloud service provider therefore the end users do not require to worry about managing the infrastructure.
PaaS consist of infrastructure like servers, storage, networking and platforms likemiddleware, development tools, database management systems, business intelligenceto support the web application devolopment life cycle.
Example: Google App Engine, Force.com, Joyent, Azure.
PaaS providers manages the Programming languages, Application frameworks, Databases, and Other tools also.
1. Programming languages
With the help of multiple programming languages PaaS helps to the developers to develop an applications. Some popular programming languages provided by PaaS are Java, PHP, Ruby, Perl, and Go.
2. Application frameworks
It provides a application frameworks to easily understand the application development. Application frameworks which are provided by PaaS providers is Node.js, Drupal, Joomla, WordPress, spring, Play, Rack, and Zend.
3. Databases
PaaS supports multiple databases such as ClearDB, PostgreSQL, MongoDB, and Redis to communicate with the other applications.
4. Other tools
PaaS providers provide various other tools that are required to develop, test, and deploy the developed applications.
Advantages of PaaS
Following are the advantages of PaaS
1) Simplified Development
PaaS allows developers to focus on development and innovation without need to take worry about infrastructure management.
2) Lower risk
No need for up-front investment in hardware and software. Developers only required a PC and an internet connection to start developing an applications.
3) Inbuilt business functionality
Some PaaS vendors also provide already defined business functionality so that users no need to build everything from very scratch and therefore they directly start the projects only.
4) Instant community
PaaS vendors frequently provide online communities in these the developer can get the ideas to share experiences and seek advice from others.
5) Scalability
Applications deployed can scale from one to thousands of users without making the change in applications.
Disadvantages of PaaS
1) Vendor lock-in
The applications are written according to the platform provided by the PaaS vendor, therefore the migration of an application to another PaaS vendor creates a problem.
2) Data Privacy
Corporate data also be a private, so if it is not located within the walls of the company, there is a risk in terms of privacy of data.
3) Integration with systems applications
Sometime the applications are local, and some are in the cloud. So there will be chances of increased complexity when we want to use data which in the cloud with the local data.
PaaS Providers
The following table shows some popular PaaS providers and services
Providers | Services |
Google App Engine (GAE) | App Identity, URL Fetch, Cloud storage client library, Logservice |
Salesforce.com | Faster implementation, Rapid scalability, CRM Services, Sales cloud, Mobile connectivity, Chatter. |
Windows Azure | Compute, security, IoT, Data Storage. |
AppFog | Justcloud.com, SkyDrive, GoogleDocs |
Openshift | RedHat, Microsoft Azure. |
Cloud Foundry from VMware | Data, Messaging, and other services. |
SaaS is called as "On-Demand Software". It is a software distribution model in this services are hosted by a cloud service provider. These services are available to end-users on the internet therefore the end-users do not required to install any software on their devices to access these services.
The services are provided by SaaS providers as
Business Services
SaaS Provider provides different business services to start the business. The SaaS business services consist of ERP (Enterprise Resource Planning), CRM (Customer Relationship Management), billing, and sales.
Document Management
SaaS document management is a software application provided by a third party to create, manage, and track electronic documents.
Example: Slack, Samepage, Box, and Zoho Forms.
Social Networks
Social networking sites are used by the general user, so social networking service providers use SaaS for their convenience and handle the general public's information.
Mail Services
To handle the unpredictable number of users and load on e-mail services for that many e-mail providers offers their services using SaaS.
Advantages of SaaS
1.easy to buy
Price of SaaS is depends on a monthly fee or annual fee subscription, so it allows organizations to access business functionality at a low cost, which is minimum than licensed applications.
Same as traditional software, which is sold as a licensed based with an up-front cost. SaaS providers are generally pricing the applications using a subscription fee, most commonly a monthly or annually fee.
2. One to Many
SaaS services are provided as a one-to-many model means a single instance of the application is shared by multiple users.
3. Less hardware
The software is hosted remotely because of this the organizations do not need to purchase in additional hardware.
4. Low maintenance
In Software as a service not required installation, set-up, and daily maintenance for the organizations. The basic set-up cost for SaaS is less than the enterprise software. SaaS vendors are decides cost of their applications depending on usage parameters, like a number of users using the application. SaaS is easy to monitor and perform automatic updates.
5. No special software or hardware versions required
All users use the same version of the software for development application and access it through the web browser. SaaS reduces IT support costs by outsourcing hardware and software maintenance and support to the IaaS provider.
6. Multidevice support
SaaS services are accessed from any device such as desktops, laptops, tablets, phones, and thin clients.
7. API Integration
SaaS services easily integrate with other software or services with the help of standard APIs.
8. No client-side installation
SaaS services are accessed directly from the service provider using the internet connection so there isno need to require any software installation.
Disadvantages of SaaS
1) Security
The data is stored in the cloud therefore the security may be an issue for some users. However, cloud computing is not more secure than home deployment.
2) Latency issue
The data and applications are stored in the cloud at different distance from the end-user thereforethe possibility that there may be greater latency when they interacting with the application compared with local deployment. Therefore, the SaaS model is not suitable for applications which have response time is in milliseconds.
3) Total Dependency on Internet
Without an internet connection theSaaS applications are not working.
4) Switching between SaaS vendors is difficult
Switching between SaaS vendors makes the difficult and slow task of transferring the very large amount of data files through the internet and then converting and importing them into another SaaS also.
Popular SaaS Providers
The following table illustrate popular SaaS providers with their services
Provider | Services |
Salseforce.com | On-demand CRM solutions |
Microsoft Office 365 | Online office suite |
Google Apps | Gmail, Google Calendar, Docs, and sites |
NetSuite | ERP, accounting, order management, CRM, Professionals Services Automation (PSA), and e-commerce applications. |
GoToMeeting | Online meeting and video-conferencing software |
Constant Contact | E-mail marketing, online survey, and event marketing |
Oracle CRM | CRM applications |
Workday, Inc | Human capital management, payroll, and financial management. |
Database as a service (DBaaS) is a cloud computing managed service. It provides access to a database without needthe setup of physical hardware and the installation of software or the requirement to configure the database. The maintenance and administrative tasks are handled by the service provider.
DBaaS service
In computing environment the database server is part of the on-premises computing infrastructure and is installed, managed and run by an organization's IT staff.
The DBaaS model is a fee-based subscription service in which the provider maintains the physical infrastructure as well as database and delivers as a private cloud service. The service covers high-level administrative burdens like installation, initial configuration, maintenance and upgrades. The database administration (DBA) services like backup and performance management is provided by DBaaS. Making the control over thecontents and usage of the database is the responsibility of the customer.
Database categories of DBaaS
DBaaS offers both relational and NoSQL database types. Relational DBaaS makes utilization of SQL database and traditional database management systems that is DBMS like Db2, Oracle, SQL Server and MySQL, and also for cloud-only database systems like Amazon RDS and Azure. NoSQL DBaaS offerings span multiple DBMS types, including graph, document, and wide column and key/value stores.
Multiple types of cloud database provide elastic database services for application development, test and production deployment, with the help of easy to use web console and RESTful API.
DBaaS uses
The DBaaS model is used for smaller to medium sized businesses which not have sufficient staff in IT departments. Offloading the service and maintenance of the database to the DBaaS provider supports small to medium-sized businesses to implement applications and systems that they otherwise could not afford to build and support on-premises.
Workloads contains the data with stringent regulatory requirements which are not suitable for a DBaaS model. Furthermore, mission-critical applications that require optimal performance and 99.99% of uptime may be better suited for on-premises implementation.
This is not to say that mission-critical workloads cannot run on cloud services, but much of the DBaaS adoption to date has been for less crucial applications, such as development and pilot programs.
Advantages of DBaaS
The DBaaS model provide some specific advantages over traditional database system management, includes:
- Reduced management requirements: the DBaaS provider takes on many management and administrative burdens.
- Elimination of physical infrastructure: the infrastructure required to run the database is provided by the DBaaS provider.
- Reduced IT costs: The users do not required to manage and plan for database hardware upgrades.
- Increased savings: users do not need to invest in costly hardware, because the physical infrastructure is no longer required. Additional savings are come from reduced capital expenditures, less staff, minimizing electrical and Hardware Cooperating costs and a smaller physical space.
Disadvantages of DBaaS
There are some disadvantages with DBaaS in comparing with traditional on-premises database technologies.
Lack of control over the IT infrastructure is the most significant issue with DBaaS versus an in-house solution. In a provider managed infrastructure organization's technicians not have direct access to the servers and storage used to implement the database.
If an organization's internet connection not work properly or if the system experiences an outage at the service provider location, the organization will not have access to its data until the service provider repairs the problem occurs due to the outage.
Latency is another issue. The additional time required to access enterprise data on the internet cause performance issues. These performance issues increase when we load large amounts of data, which is very slow and time-consuming.
DBaaS tools
DBaaS is based on a cloud database to store, manage and access data. The cloud service and the database service not required from the same provider. For example, an organization can use AWS for cloud service with a Microsoft SQL Server database.
- Oracle database
- Microsoft SQL Server
- IBM Db2
- MySQL
The next step is to decide which cloud service provider to use important is that not every DBMS is supported on every cloud platform. Popular cloud service provider options include:
- AWS
- Microsoft Azure
- Oracle cloud
- Google Cloud Platform
An organization provides the appropriate tools to handle the databases and build applications using the DBaaS implementation.
Many existing database and DBA tools like Navicat and Oracle Developer are used to manage databases and build applications that access the database in the cloud.
IT staff organizations understand the tooling which is provided by their selected service providers also the DBaaS and cloud service providers supply tools to help customers use their services.
1) Machine learning and AI
It helps to increase your business knowledge by performing Artificial Intelligence which creates learning patterns for supervised, unsupervised, reinforced and deep learning. ISM Canada helps customers to get back the data and creates the algorithms to understandyour business and makes you the most intelligent in your industry.
2) IOT
IOT is the powerful assistance of data and algorithms, from asset management data that optimizes your real estate and facilities. Improve your software and systems engineering to add velocity to your digital transformation. ISM Canada deploys, manages and optimizes your IOT landscape with the help of industry leading tools.
3) Blockchain
Blockchain is a distributed ledger technology which is protected by cryptographic technologies and provides significant potential for innovation across a plethora of use cases. ISM Canada serves customers by identification and development of blockchain for business application.
4) Amazon Web Services (AWS)
Amazon Web Services (AWS) is a very large size of public cloud computing. The company was very fast to identify the enormous potential of the cloud as a whole, and so invested heavily in developing an extensive infrastructure to provide the best and most reliable service.
The company offers large range of IaaS and PaaS services containing Elastic Compute Cloud (EC2), Elastic Beanstalk, Elastic Block Store (EBS), and Simple Storage Service (S3), Glacier storage, DynamoDB NoSQL database and Relational Database Service (RDS).
It also offers most powerful tools and services for development, networking, data processing and management for AWS’s reputation as the go to cloud service that gives seamless integration, with the best tools and services available today.
For businesses, AWS provdes high resource scalability at a fraction of the price that it would require otherwise. Many businesses feel that due to Amazon’s extensive focus on remaining ahead of the game that they are actually investing in a system that will only get better with time same as a traditional in-house server system, which quickly outdated.
The important drawback of AWS is not open-source, something which frustrated many developers along with the restricted control that Amazon’s internal management creates.
5) Google Cloud Platform
Google’s Cloud Platform make competition with AWS in main area of public cloud. Thanks to global domination of their Android system, the company introduce its users to its cloud system with the help of their phones and tablets. The most basic function is to allow us all to sync our phones with other devices contains tablets and our computers when using Chrome web browser.
This platform provides some well developed and reliable tools, including their Compute Engine, App Engine, Container Engine, Cloud Storage and BigQuery. Google combines their cloud resources with their Android system and some parts of their cloud platform are set to explode in terms of market share. With reliable and fast global internet, the big issue of smartphone storage space is completely disappear.
6) Microsoft Azure
Microsoft provides the full spectrum of IaaS, PaaS and SaaS services to its customers. The company was caught napping when it came to its core Windows operating system and its migration to the smartphone therefore it is good news from their investor’s standpoint that they have managed to carve out a good percentage of the cloud market. They have managed to successfully integrate their other flagship product, the Office suite onto the cloud, something that will guarantee a healthy revenue stream in the future.
The important product of its existing Windows operating system is the relationships that it brings up with a large number of companies same as HPE, Adobe, SAP, and Cisco, all of they are reviving this relationship with their own moves into cloud-based systems. So far as the numbers go, Microsoft’s cloud business is on a solid growth trajectory. Microsoft reported that its revenues increased 5 percent to surpass $6.7 billion, something that would put it in the number 2 spot behind AWS.
It is used by the U.S Government and a number of big companies, the main problem of Microsoft Azure is the cost. It trails all the main cloud services in terms of price, which are more than all the others and are reportedly causing it to suffer when it comes to uptake by small and medium-sized businesses.
7) IBM Cloud
IBM always work with the big business market and by most indications they seemed to have followed the same approach with their cloud platform. The company is mainlyfocused on PaaS and SaaS cloud systems and its Bluemix development tool isused from the software development community and its range of powerful cloud SaaS management tools and services are score some more successes.
The IBM Cloud has some unique offers that its competitors are not currently able to match. Consider the example in which only major cloud vendor emphasizes its bare metal servers, which ismore attractive for organizations that have particular performance or security requirements. IBM provides organizations more flexibility and customization options, on a scale that the other big three don’t. It takes many hours to configure and deploy a custom server because of this many customers to finally turn their back on IBM.
IBM offers seamless integration with existing IBM architectures lke PowerServers, something which is a strong incentive to for its customers to use their cloud service. The strong feature of IBM’s cloud services is that its tools and security features work perfect on multi-cloud environments. This is backed up by a high level of IT support.
8) Oracle Cloud
Oracle provides respectable range of IaaS, PaaS and Saas services. RightNow suite of applications, which are excellent tools are designed for web, social and contact center customer services and deliverable across multiple channels. This suite contains access to live chat features, email support, case management, virtual assistants and much more.
The oracle cloud company’s Ravello tools are easily migrating virtual machines to the cloud, while its Paas services for data management, business analytics, and app development have all attracting an increasing number of users who prefer Oracle’s approach.
9) GoDaddy
GoDaddy is a most popular cloud platform for smaller businesses which require low-cost access to basic cloud services, web hosting, and domains. They are really an IaaS focused cloud system with a specialty in web development. Features are reliable uptime, excellent tools, and low costs. GoDaddy is a popular choice for individuals and small businesses which are looking to bring down costs and have to access some really powerful web development tools.
The website builder is available in three versions that is GoCentral, Online Store, and WordPress. This means you can use the different versions to develop your site on any of these three platforms.
10) VMware
VMWare vCenter Server is a cloud system that support you to manage the virtual infrastructure by centralizing it all under one roof. It is designed to work wthbusinesses of all sizes to improve system integration by enabling complete overview and control of what is going on. VMware is a powerful tool when it used to improve the efficiency and effectiveness of your company.
This cloud platform is preferred choice of many developers because of their overall approach and high levels of support. This model is hard to find customers who report having a negative experience with them, which may be something which some of the top cloud providers on this list could learn from.
Another important feature of VMware is that it is available in 20 different languages which are available to all.
Cloud computing is used for making global access to mutual pools of resources like services, apps, data, servers, and computer networks. It is done on either a third-party server located in a data center or a privately owned cloud. This makes data-accessing contrivances more reliable and efficient, with minimum administration effort.
Because cloud technology depends on the allocation of resources to maintain consistency and economy of scale, similar to a utility, it is also cost-effective, making it the choice for multiple small businesses and firms.
But there are also challenges present in cloud computing, and if you’re not prepared to deal with them, you won’t realize the benefits. There are six common challenges consider before implementing cloud computing technology.
1. Cost
Cloud computing is very affordable, but selecting the platform according to the company’s requirement is more expensive. Therefore the expense of transferring the data to public clouds can prove to be a problem for short-lived and small-scale projects.
Companies are save money on system maintenance, management, and acquisitions. But they want to invest more in additional bandwidth, and the absence of routine control in infinitely scalable computing platform increase costs of cloud.
2. Service Provider Reliability
The capacity and capability of a technical service provider is very important same as price. The service provider is required to available when you need them. The main important thing is the service provider’s sustainability and reputation. Make sure you comprehend the techniques via which a provider observes its services and defends dependability claims.
3. Downtime
Downtime could be a significant shortcoming of cloud technology. No seller can promise a platform that’s freedfrom possible downtime. Cloud technology makes small companies reliant on their connectivity therefore companies with an untrusted internet connection want to deliberate before adopting cloud computing.
4. Password Security
Industrious password supervision plays an important role in cloud security. However, the more people you’ve got your cloud account, the less secure it’s. Anybody attentive your passwords are able to access the data you store there.
Businesses perform multi-factor authentication and confirm that passwords are protected and altered regularly, particularly when staff members leave. Access rights associate with passwords and usernames should only be allocated to those that require them.
5. Data privacy
Sensitive and private information is placed within the cloud defined only for internal use only which isnot shared with third parties. Businesses required a plan to securely and efficiently manage the information they gather.
6. Vendor lock-in
Entering into the cloud computing agreement is not more complicated than leaving it. “Vendor lock-in” use when altering providers is more expensive or simply insufferable. It can be that the service is nonstandard or that there is no viable vendor substitute.
It comes down to buyer carefulness. Guarantee the services you involve are typical and transportable to other providers, and above all, understand the requirements.
Cloud computing is a good solution for many businesses, but it’s important to know what you’re getting into. Having plans to address these six prominent challenges first will help ensure a successful experience.
The data volumes is increased then data handling become the talk of the town. When companies moved to the cloud, there is a higher emphasis that everything is safe and secure, and no risk of data hacking or breaches. When cloud allows people to work without hardware and software investments then users can acquire flexibility and data agility. Therefore the Cloud is shared between multiple users, security is an immediate concern for Cloud owners.
Security Issues in Cloud
Cloud vendors provide a layer of security to user’s data. Therefore it is not enough because the confidentiality of data can be at risk. There are many types of attacks, which is from password guessing attacks and man-in-the-middle attacks to insider attacks, shoulder surfing attacks, and phishing attacks. Following is the list of security challenges which are present in the cloud:
1) Data Protection and Misuse
When multiple organizations use the cloud to store their data, there is a risk of data misuse. To avoid this risk, there is need to secure the data repositories. To achieve this task there is need to use authentication and restrict access control for the cloud’s data.
2) Locality
Within the cloud data is distributed on a series of regions therefore it is more challenging to find the correct location of the data storage. When data is transferred from one country to other then the rules for the data storage is also change because of this compliance issues and data privacy is occurs, which consider as the storage of data within the cloud. As a cloud service provider, the service provider has to inform the users of their data storage laws, and finds location of the data storage server.
3) Integrity
The system needs to be rigged in such a manner so to provide security and access restrictions. The data access should lie with authorized person only. In a cloud environment, data integrity should be maintained at all times to avoid any inherent data loss. Apart from restricting access, the permissions to make changes to the data should be limited to specific people, so that there is no widespread access problem at a later stage.
4) Access
Data security policies related to the access and control of data are essential in the long run. Authorized data owners are need to give part access to individuals so that every person gets access when only it requires for parts of the data stored within the data mart. By controlling and restricting access, there is many types of control and data security which is used to maximums security for stored data.
5) Confidentiality
There is a large amount of sensitive data which may be stored in the cloud. This data has to require extra layers of security on it to minimize the chances of breaches and phishing attacks. This can be implemented by the service provider and also the organization. Therefore for safety data confidentiality should have highest priority for sensitive material.
6) Breaches
Breaches in the cloud are not unheard. Hackers can break security parameters in the cloud, and steal the data which is considered confidential for organizations. On the contrary, a breach is an internal attack therefore organizations need to lay particular emphasis in tracking employee actions to restrict any unwanted attacks on stored data.
7) Storage
In organizations the data is stored and made available virtually. Then for service providers, it is necessary to store the data in physical infrastructures, which makes the data vulnerable and conducive to physical attacks.
These are the security issues which is a part of the cloud computing environment. Therefore these are not difficult to minimize especially with the available levels of technological resources these days. There is a more number of emphasis on ensuring maximum security for the stored data so that it complies with the rules and regulations, also with the organization’s internal compliance policies.
Data security is an important issue in information technology. In the cloud computing environment, it becomes serious because the data is located at different places even in all the globe. Data security and privacy protection aretwo important factors of users which isrelated with the cloud technology.
Data security and privacy protection are more important for the future development of cloud computing technology in government, industry, and also in business. Data security and privacy protection issues are related to both hardware and software in cloud architecture.
This is important to review different security techniques and challenges from both software and hardware aspects for protecting data in the cloud and enhancing the data security and privacy protection for the trustworthy cloud environment.
Introduction
In the cloud computing environment applications and resources both are delivered on demand on the Internet as services. Cloud is environment of the hardware and software resources in the data centers that provide diverse services over the network or the Internet to fulfill user's need.
Cloud computing provides a suitable on demand network access to a shared pool of configurable computing resources. Resources used for computing applications, network resources, platforms, software services, virtual servers, and computing infrastructure.
Data security is a major issue in IT. Data security is important in the cloud computing environment, because data is stored on different machines and storage devices containing the servers, PCs, and various mobile devices such as wireless sensor networks and smart phones. Data security in the cloud computing is more complicated compare with data security in the traditional information systems.
Cloud computing save an organization's time and money, but trusting the system is more important. Because the real wealth of an organization is the data which they share in the cloud to use the required services by putting it either directly in the relational database or eventually in a relational database with the help of application.
Cloud computing finds a number of attributes that need special attention when it comes to trusting the system. The trust of whole system is depends upon the data protection and prevention techniques. Security is the made up with confidentiality, the prevention of the unauthorized disclosure of information, integrity, the prevention of the unauthorized amendment or deletion of information, availability, and the prevention of unauthorized withholding of information.
The main issues in cloud computing contains resource security, resource management, and resource monitoring. There are no standard rules and regulations to deploy applications in the cloud, and there is a lack of standardization control in the cloud.
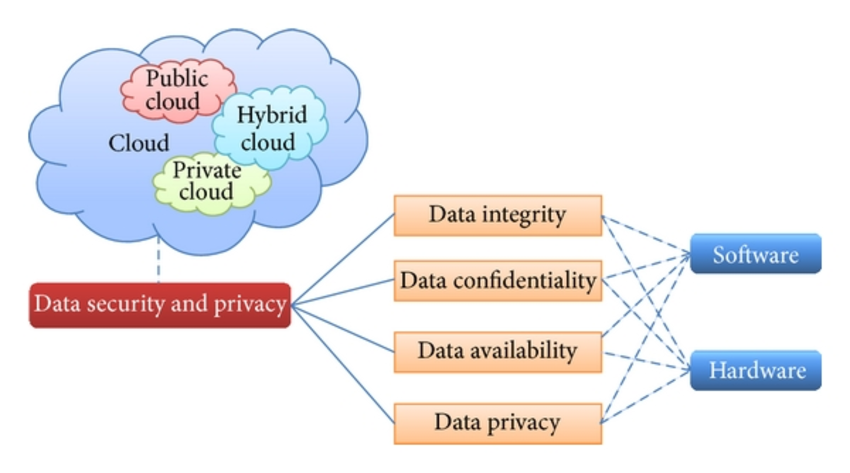
Figure 6.8 (I)shows organization of data security and privacy in cloud computing environment.
Data Confidentiality and encryption
Data confidentiality is important factor for users to store their private or confidential data in the cloud. Authentication and access control techniques are used to achieve data confidentiality. The data confidentiality, authentication, and access control issues in cloud computing are overcome by increasing the cloud reliability.
Because the users do not trust the cloud providers and cloud storage service providers are virtually not possible to reduce potential insider threat therefore it is dangerous for users to store their sensitive data in cloud storage directly. Key management problem is occurs in simple encryption technique and can’t support complex requirements like query, parallel modification, and fine-grained authorization.
A. Homomorphic Encryption
Encryption is used to manage the confidentiality of data. Homomorphic encryption is a method of encryption system introduced by Rivest et al. It says that the cipher text algebraic operation results are consistent with the clear operation after encryption results and the entire process does not required to decrypt the data. The implementation of this technique improve confidentiality of data and data operations in the cloud computing.
Gentry firstly introduce the fully homomorphic encryption method, which can do any operation that can be performed in clear text without decryption. Breakthrough is very important in the homomorphic encryption technology. Therefore the encryption system contains very complicated calculation and price of computing and storage is very high. But the fully homomorphic encryption not implemented in real applications.
A cryptographic algorithm Diffie-Hellman is invented for secure communication, which is different to the key distribution management mechanism.
A hybrid technique it combines many encryption algorithms such as RSA, 3DES, and random number generator are used for flexibility and security. RSA is used for making secure communication connection through digital signature based authentication and 3DES is useful for encryption of block data.
B. Encrypted Search and Database
Because the homomorphic encryption algorithm is not sufficient, researchers start study the applications of limited homomorphic encryption algorithm in the cloud environment. Encrypted search is a common operation in algorithm.
Manivannan and Sujarani introduce a lightweight technique for database encryption called as transposition, substitution, folding, and shifting algorithm. Therefore the numbers of keys are increased, the amount of computations and processing is also increases.
Memory Database encryption technique is introduced for privacy and security of sensitive data in untrusted cloud environment. A synchronizer is present between the owner and the client for making access to the data. Client require a key from the synchronizer to decrypt the encrypted shared data it receives from the owner. The synchronizer is used to store the correlated shared data and the keys are separately. The output is that the delays occur due to the additional communication with the central synchronizer. Therefore this limitation is mitigated by adopting group encryption and through minimizing communication between nodes and synchronizer.
Huang and Tso proposed an asymmetric encryption mechanism for databases in the cloud. In the proposed mechanism, the commutative encryption is applied on data more than once and the order of public/private key used for encryption/decryption does not matter. Re-encryption mechanism is also used in the proposed scheme which shows that the cipher-text data is encrypted once again for duality. Such schemes are very useful in the cloud applications where privacy is a key concern.
A privacy-preserving multikeyword ranked search method over encrypted cloud data is introduced which can search the encrypted cloud data and rank the search results without interrupting of the user's privacy.
C. Distributive Storage
Distributive storage of data is important concept in the cloud computing. The solution was found by AlZain et al. on security issues related to data privacy in the cloud computing including integrity of data, intrusion, and availability of service in the cloud. To achieve the data integrity need to store data in multiple clouds or cloud databases. The data need to protect from internal or external unauthorized access therefore it is divided into chunks and Shamir's secret algorithm is used to generate a polynomial function related to each chunk.
Ram and Sreenivaasanproposed a technique called security as a service for securing cloud data. This technique achieve maximum security by dividing the user's data into pieces. These data chunks then encrypted and stored in separated databases by following the data distribution on cloud. Because each segment of data is encrypted and separately distributed in databases over the cloud, this provides security against multiple types of attacks.
Arfeen et al. Says that the distribution of resources for cloud computing is depends on the tailored active measurement. The tailored measurement technique is used for network design and the specific routes for the incoming and outgoing traffic. It also changing the resources according to the user needs. Tailored measurement depends on the computing and storage resources. Due to the changing nature of networks, the allocation of resources at particular time is depend on the tailored active method. The resources can be increase or decrease therefore the system has to optimize changes according to the user requirement may be offline or on-line and the resource connectivity.
D. Hybrid Technique
A hybrid technique is made for data confidentiality and integritywhich uses both key sharing and authentication techniques. The connectivity between the user and the cloud service provider is more secure by utilizing powerful key sharing and authentication processes. RSA public key algorithm used for secure distribution of the keys between the user and cloud service providers.
A three-layered data security technique is used which contains the first layerused for authenticity of the cloud user either by one factor or by two factor authentications; the second layer encrypts the user's data for achieving protection and privacy and the last that isthird layerperform fast recovery of data with the help of a speedy decryption process.
An event-based isolation of critical data in the cloud approach is proposed, TrustDraw, a transparent security extension for the cloud it combines virtual machine introspection (VMI) and trusted computing (TC).
E. Data Concealment
Data concealment used to maintain the data confidentiality in the cloud. Delettre et al. Proposed a concealment concept for databases security. Data concealment concept merge real data with the visual fake data to identify the real data's volume. Therefore the authorized users easily differentiate the fake data from the real data.
Data concealment techniques increase the volume of real data but provide advance security for the private data. The goal of data concealment is to make the real data safe and secure from unwanted users and attackers. Watermarking method is considered as a key for the real data. Only the authorized users have key of watermarking therefore authentication of users is the key to make sure the true data to be accessible for right users.
F. Deletion Confirmation
Deletion confirmation means data couldn’t be recovered when users delete their data after the deletion confirmation. The problem is serious because more than one copy exists in the cloud for the security and convenience of data recovery. When users delete their own data with confirmation then all copies of data is also deleted at the same time. Multiple data recovery technologies are present to recover the data deleted by users from the hard disks. So the cloud storage providers should confirm that the deleted data of users not recovered and used by other unauthenticated users.
To avoid the data be recovered and unauthenticated used it is method to encrypt the data before uploading to the cloud storage space. FADE system is based on technologies like Ephemerizer. In this data are encrypted before they are uploaded to the cloud storage. When users want to delete their data, the system just to apply the particular strategy to all the storage space covered with new data for replacing the deletion operation.
In Data availability when problem as hard disk damage, IDC fire, and network failures occur then user's data is used or recovered. The users verify their data by techniques instead of depending on the credit guarantee by the cloud service provider alone.
The problem in storing data on the transboarder servers is a very serious for clients because the cloud vendors are governed by the local laws andthe cloud clients should be cognizant of those laws. The cloud service provider make sure that the data security, data confidentiality and integrity. The cloud provider need to share all such concerns with the client and make a trust relationship in this connection. The cloud vendor also provide guarantees of data safety and explain jurisdiction of local laws to the clients.
Locating data is used to increase the trust of user on the cloud. Cloud storage provides the transparent storage service for users which reduce the complexity of cloud and also minimize the control ability on data storage of users.
A. Reliable Storage Agreement
The common behavior of untrusted storage is that the cloud service providers can be discard part of the user's update data, which is hard to be checked by depending on the simple data encryption. A good storage agreement need to support concurrent modification by many users.
Mahajan et al. Introduce Depot which can guarantee Fork-Join-Causal-Consistency and eventual consistency. It can effectively avoid attacks like discarding and it can support the implementation of other safety protections in the trusted cloud storage environment same as Amazon S3.
Feldman et al. Proposed SPORC it implements the safe and reliable real-time interaction and collaboration for many users with the help of the trusted cloud environment, and untrusted cloud servers only access the encrypted data.
Therefore the operation types supported by reliable storage protocol support are limited, and manycalculations can only occur in the client.
B. Reliability of Hard-Drive
Hard-drive is the important storage media in the cloud environment. Reliability of hard disks manages the foundation of cloud storage. Pinheiro et al. Studied the error rate of hard-drives depends upon the historical data of hard-drive. They found that the error rate of hard-drives is not closely related to the temperature and the frequency is used. The error rate of hard-drives is strong clustering characteristics. Current SMART mechanismnot predict the error rate of hard disks. Tsai et al. Understand the relation between the soft error and hard error of hard disks, and found that the soft error predict the hard errors of hard-drives only about 1/3 probability that hard errors follow the soft errors.
Data integrity is most critical elements in any information system. Data integrity means protecting data from unauthorized deletion, modification, or fabrication. Managing entity's admittance and rights to specific enterprise resources make sure that valuable data and services are not abused, misappropriated, or stolen.
Data integrity is easily achieved in a standalone system with a single database. Data integrity in the standalone system is maintained through database constraints and transactions, which is finished by a database management system. Transactions need to follow ACID atomicity, consistency, isolation, and durability properties to perform data integrity. Most databases support ACID transactions and preserve data integrity.
Authorization is used to control the access of data. It is the process by which a system identifies what level of access a particular authenticated user should have to secure resources controlled by the system.
Data integrity in the cloud system means maintaining information integrity. The data should not be lost or modified by unauthorized users. Data integrity is the main part to provide cloud computing service like SaaS, PaaS, and IaaS. Instead of data storage of large-scaled data, cloud computing environment provides data processing service. Data integrity can be obtained by techniques as RAID-like strategies and digital signature.
Getting the large quantity of entities and access points in a cloud environment, authorization is critical in assuring that only authorized entities can interact with data. Avoiding the unauthorized access the organization achieve greater confidence in data integrity. The monitoring process provides the greater visibility to find out who or what may have altered data or system information and affecting their integrity. Cloud computing providers are trusted to manage data integrity and accuracy. Therefore it is necessary to build the third party supervision process besides users and cloud service providers.
Verifying the integrity of data in the cloud remotely is the requirement to deploy applications. Bowers et al. Introduced a theoretical framework “Proofs of Retrievability” to identify the remote data integrity checking by combining error correction code and spot-checking. The HAIL system uses POR mechanism to check the storage of data in different clouds, and it can ensure the redundancy of different copies and realize the availability and integrity checking. Schiffman et al. Proposed trusted platform module remote checking to check the data integrity remotely.
A cloud storage gateway is a hardware or software component which provides a bridge between local applications and remote cloud-based storage.
A cloud storage gateway provides the protocol translation and simple connectivity to make incompatible technologies for communication. The gateway should be hardware or a virtual machine (VM) image.
The requirement for a gateway between cloud storage and enterprise applications is necessary because of the incompatibility between protocols used for public cloud technologies and legacy storage systems. Most public cloud providers based on Internet protocols, a RESTful API over HTTP, instead of conventional storage area network (SAN) or network-attached storage (NAS) protocols.
Gateways are used for archiving in the cloud system. This pairs with automated storage reset, in this data is replicated between fast, local disk and cheaper cloud storage to balance space, cost, and data archiving needs.
The challenge in traditional cloud gateways which front the cloud with on-premise hardware and use the cloud like another storage tower is that the cloud is very costly for hot data that used to be frequently accessed, resulting in high retrieval costs.
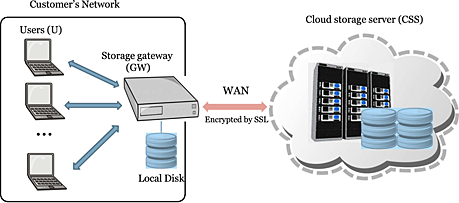
Fig 6.11(I) shows cloud storage network
Advantages of Cloud Storage Gateway
1) Support standard protocols
Cloud Storage Gateway provides the features such as protocol conversion, allowing you to access cloud storage using standard protocols containing SMB, FTP, AFP, NFS, WebDAV and iSCSI. You can easily access cloud storage from Windows®, Mac®, and Linux® devices.
2) Access cloud data with near-LAN speeds
By enabling local caching on the NAS, the access speed of frequently-used data is greatly optimized and allowing you to enjoy low-latency access to cached cloud files with near-LAN speeds through the Internet.
3) Maximize cloud storage efficiency
Cloud Storage Gateway fully integrates with public cloud storage to centrally store data which is generated from multiple locations with the flexibility and convenience of cloud storage expansion.
4) Minimize network usage cost
Cloud Storage Gateway caches most recently-accessed data on the NAS. In this when many peoples are using the same file at a time, they do notrequired to download each copy it minimize the network usage charges for downloading data from the cloud object storage.
Reference Books
1. Cloud Computing Black Book- Jayaswal, Kallakurchi, Houde, Shah, Dreamtech Press.
2. Cloud Computing: Principles and Paradigms – Buyya, Broburg, Goscinski.
Reference Links
1. Https://www.javatpoint.com/infrastructure-as-a-service.
2. Https://journals.sagepub.com/doi/full/10.1155/2014/190903
3. Https://www.qnap.com/solution/cloud-storage-gateway/en-in/