● However, remote login uses basic desktop sharing tools to "remote control" you.
● To access your computer and all of its software and hard drive files anywhere in the world from any internet-connected device.
● Remote login operates in much the same way as sharing a desktop.
● There are two different groups for desktop sharing.
● A host machine and a remote user for desktop sharing.
● The host machine enables a remote user to access the desktop content of the host computer over the internet.
● The host computer can also hand over the remote user's keyboard and mouse controls.
● Your home or work machine is the server, and you are the remote user, with remote login.
● For Terminal Network, TELNET is an abbreviation. As introduced by the International Organization for Standards, this is the basic TCP/IP protocol for virtual terminal services (ISO).
● TELNET allows a connection to the remote system to be created in such a way that the local terminal appears to be the terminal of the remote system.
Key takeaway :
● remote login uses basic desktop sharing tools to "remote control" .
● TELNET allows a connection to the remote system to be created in such a way that the local terminal appears to be the terminal of the remote system.
● A host machine and a remote user for desktop sharing.
There is a complex method for accessing a remote computer. This is because a special combination of characters is recognised by every machine and its operating system as tokens. The end-of-file token on a machine running the DOS operating system, for instance, is Ctrl+z, while Ctrl+d is remembered by the UNIX operating system.
There are heterogeneous structures we are concerned with. If we want to access any remote device in the world, we need to know first what kind of computer we're going to be connected to, and we need to instal the unique terminal emulator that that computer uses as well. By defining a common interface called the network virtual terminal (NVT) character set, TELNET solves this problem.
The TELNET client converts characters (data or commands) coming from the local terminal into NVT form through this interface and delivers them to the network. On the other hand, the TELNET server converts data and commands from the NVT form into a form that the remote device accepts.
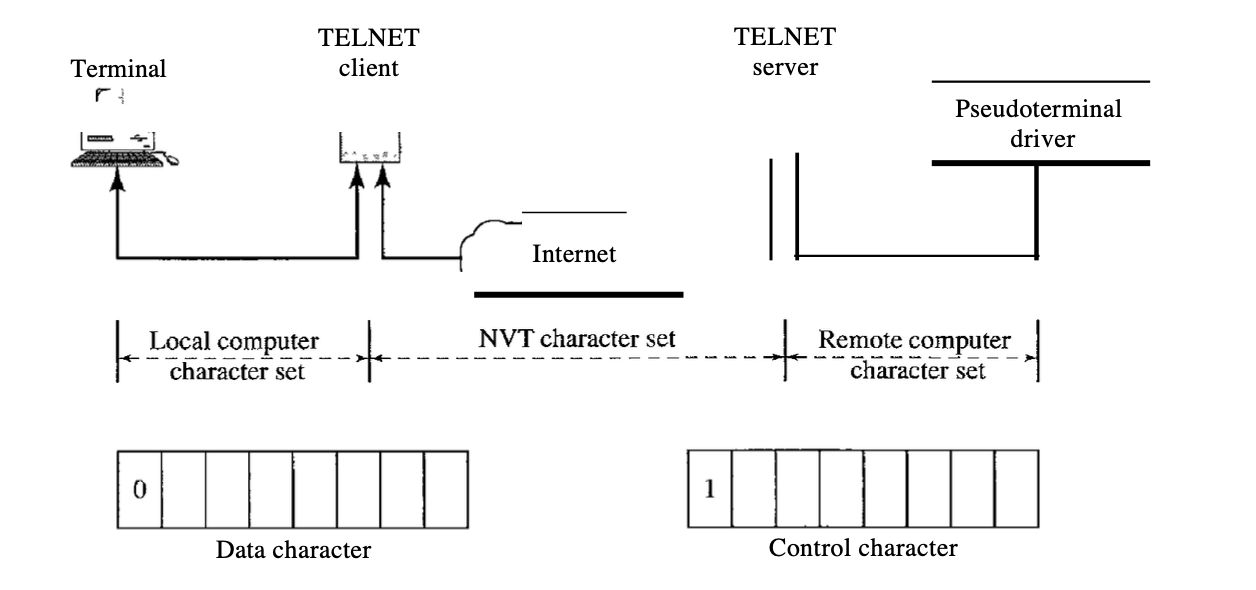
Fig 1: NVT
NVT Character Set Two character sets are used by NVT, one for data and the other for power. They're both 8-bit bytes. For data, NVT is an 8-bit character set in which ASCII is the same as the 7 lowest-order bits and O is the highest-order bit. NVT uses an 8-bit character set, in which the highest-order bit is set to l, to send control characters between computers (from client to server or vice versa).
Character | Code | Meaning |
EOF | 236 | End of file |
EOR | 239 | End of record |
SE | 240 | Suboption end |
NOP | 241 | No operation |
DM | 242 | Data mark |
BRK | 243 | Break |
IP | 244 | Interrupt process |
AO | 245 | Abort output |
Some control characters of NVT
Key takeaway :
● There is a complex method for accessing a remote computer.
● NVT is a network virtual terminal.
● TELNET server converts data and commands from the NVT form into a form that the remote device accepts.
Just one TCP link is used by TELNET. The well-known port 23 is used by the server, and the client uses an ephemeral port. For sending both data and control characters, the same link is used. By embedding the control characters in the data stream, TELNET achieves this. However, each series of control characters is followed by a special control character, called interpret as control character, to distinguish data from control characters (lAC). Imagine, for instance, that a user requires a server to view a file on a remote server.
If can type : catfilel
Suppose, however, that the file name has been mistyped (filea instead of filel). To fix this condition, the user utilises the backspace key.
Catfilea
However, when TELNET is introduced by default, the user is unable to edit locally; editing is performed on the remote server. Two remote characters (lAC EC) are converted into the backspace.
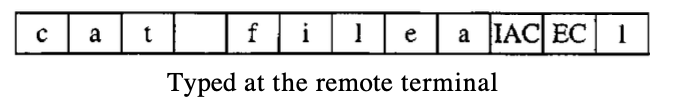
Fig 2: example of embedded
Key takeaway :
● one TCP link is used by TELNET.
● By embedding the control characters in the data stream, TELNET achieves this.
Options
Before or after the use of the server, TELNET helps the client and server to explore options. Additional features available to a user with a more advanced terminal are options. Default characteristics can be used for users of simplified terminals. To identify options, some control characters discussed earlier are used.
Option
Code | Option | Meaning |
0 | Binary | Interpret as 8-bit binary transmission. |
1 | Echo | Echo the data received on one side to the other. |
3 | Suppress go ahead | Suppress go-ahead signals after data. |
5 | Status | Request the status of TELNET. |
6 | Timing mark | Define the timing marks. |
24 | Terminal type | Set the terminal type. |
32 | Terminal speed | Set the terminal speed. |
34 | Line mode | Change to line mode. |
Option Negotiation
It first involves option negotiation between the client and the server to use any of the options listed in the previous section. For this reason, four control characters are used.
NVT character set for option negotiation
Character | Decimal | Binary | Meaning |
WILL | 251 | 11111011 | ● Offering to enable ● Accepting a request to enable |
WONT | 252 | 11111100 | ● Rejecting a request to enable ● Offering to disable ● Accepting a request to disable |
DO | 253 | 11111101 | ● Approving an offer to enable ● Requesting to enable |
DONT | 254 | 11111110 | ● Disapproving an offer to enable ● Approving an offer to disable ● Requesting to disable |
Sub-option Negotiation
Some possibilities need additional data. For example, to define a terminal's type or velocity, the negotiating method requires a string or number to define the type or velocity. In either case, for sub option negotiation, the two sub option characters indicated are necessary.
NVT set for sub-option negotiation
Character | Decimal | Binary | Meaning |
SE | 240 | 11110000 | Suboption end |
SB | 250 | 11111010 | Suboption begin |
Key takeaway :
● Before or after the use of the server, TELNET helps the client and server to explore options.
● It first involves option negotiation between the client and the server to use any of the options.
● for sub option negotiation, the two sub option characters indicated are necessary.
You need to access the Telnet Control Functions menu to pick which server functions that you want to control( Click the Attention key on your 5250 keyboard to get to this menu)
The following list gives you a brief overview of each control function of the Telnet client:
● Interrupting a process on the system Interrupt process or IP: This role cancels, interrupts, or suspends a server-started operation. For instance, when a process seems to be in a permanent loop, or if you have started a process by mistake, you can use IP.
● Querying connection status when the system becomes inactive Query connection status or AYT : This feature includes a server message that lets you know the machine is still running. When the machine is suddenly offline for a long period of time, you can use this control feature.
● Discarding remote output before it reaches your workstation Discard remote output data or AO : Without sending the output to your workstation, this feature allows a process that produces output to run to completion. This feature removes the system-system output already generated that has not yet been shown on your workstation.
● Clearing the data path between your system and the server Clear the data path or SYNCH : This feature discards all characters between your device and the server (except Telnet commands). You may use this feature when the flow control mechanisms of the network trigger buffering of other functions, such as IP or AO.
● Ending the Telnet session End Telnet session or QUIT : This function terminates the Telnet session and closes the TCP/IP (remote system) connection. This function can be requested at any time during the Telnet session, but the remote system should be signed off before this function is chosen. If you don't sign off, because the Telnet protocol doesn't have an end session sequence, you stay signed on to the machine.
● Using the Attention key to remote host option ATTN key to remote host: In order to show the Telnet Control Functions menu, press the Attention key.
● Telnet uses OUT OF BAND SIGNALING to make control characters effective in special scenarios.
● Control characters in OUT OF BAND SIGNALING are followed by IAC and are sent to the remote process.
● Imagine a scenario in which an infinite loop has been reached by the application programme running on the server site and does not allow any input data.
● The user needs to interrupt the application programme, but no data from the buffer is read by the application programme.
● TCP has noticed that the buffer is complete at the server site, and it sends a section stating that the size of the client window should be zero.
● In other words, TCP announces on the server site that no further normal traffic is approved.
● An urgent TCP section must be sent from client to server to address such a situation.
● The urgent section overrides the framework for normal flow control.
● While standard segments are not accepted by TCP, it must accept urgent segments.
● If a telnet process (client or server) wants to send characters to another process (client or server) out of the band sequence, it embeds the sequence in the data stream and inserts a special character called DM (i.e.Data Mark).
● It creates a TCP section in which urgent bit set and Urgent Pointer pointing to DM character, however, to notify the other party.
● It reads the data and discards any information that precedes the control characters when the receiving process recei
● The remaining data is treated normally until it enters the DM character.
● In other words, the DM character is used as a synchronisation character that moves from urgent mode to usual mode and resynchronizes both ends of the receiving method.
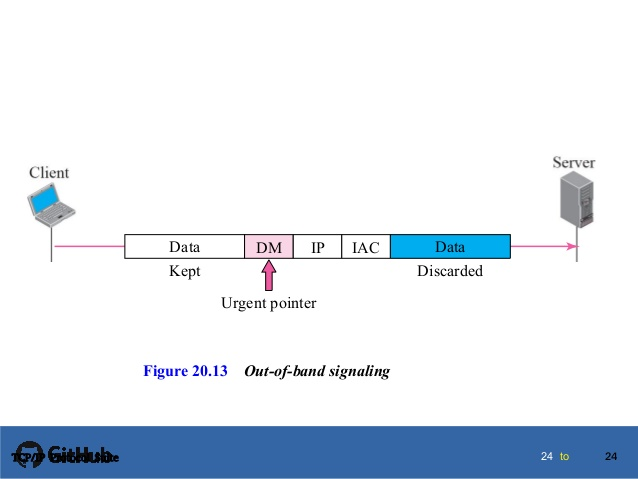
Fig 3: out of band signal
In this way, control characters (i.e. IP) are transmitted to the Operating System out of the band, using the Required feature to interrupt the running application programme.
Key takeaway :
● Telnet uses OUT OF BAND SIGNALING to make control characters effective in special scenarios.
● Control characters in OUT OF BAND SIGNALING are followed by IAC and are sent to the remote process.
● An urgent TCP section must be sent from client to server to address such a situation.
When you open a Telnet link, you may have something like this:
user@server# telnet 127.0.0.1 80
Trying 127.0.0.1...
Connected to 127.0.0.1.
Escape character is '^]'.
So, you only have to use the "escape character" as shown if you want to leave. But this character is not meant to be typed with 2 characters, such as "^" and then "]"; depending on your OS, you have to use a direct command that can be different:
● Windows: Ctrl + $
● Linux: Ctrl + Alt Gr + ]
● Mac OS: Ctrl + $
And, once you have inserted this escape character, press Enter so that you can get the regular telnet prompt and type quit to exit the prompt.
It will result in a command such as:
^]
telnet> quit
Connection closed.
user@server#
And here you go—you're from Telnet!
There are closed comments.
The majority of TELNET deployments work in one of three modes: default, character, or line mode.
Default mode
When no other modes are invoked through option negotiation, the default mode is used. The echoing is done by the client in this mode. A character is typed by the user, and the client echoes the character on the screen (or printer) but does not send it until the completion of an entire line.
Character mode
In character mode, each character entered is sent to the server by the client. Normally, the server echoes the character back to be shown on the client screen. The character echo can be delayed in this mode if the transmission time is long (such as in a satellite connection). It also generates overhead (traffic) for the network because, for each data character, three TCP segments must be sent.
Line mode
To compensate for the deficiencies of the default mode and the character mode, a new mode has been proposed. In this mode, called the line mode, the client performs line editing (echoing, character erasing, line erasing, and so on). The client then sends the server the entire line.
Key takeaway :
● When no other modes are invoked through option negotiation, the default mode is used.
● In character mode, each character entered is sent to the server by the client.
● To compensate for the deficiencies of the default mode and the character mode, a new mode has been proposed in line mode.
Name
Telnet - User Interface to a Remote System, Using the TELNET Protocol
Synopsis
/usr/bin/telnet [-8ELcdr][-e escape-char][-l user][-n tracefile]
[host [port]]
Description
Use the telnet command to log in remotely to a system running a different operating system or version of UNIX. Using the TELNET protocol, Telnet interacts with another host. If you invoke Telnet without arguments, the command mode is entered and the telnet> prompt is shown. It accepts and executes its associated commands in this mode. (See page 1326 for 'telnet commands.') If you invoke telnet with arguments, an open order with those arguments is executed.
Telnet enters the input mode once the connection has been opened. The text typed in this mode is sent to a remote.
If Telnet is invoked with a host argument, it implicitly executes an open command; see the definition down.
- 4 : Force IPv4 address resolution.
-6 : Force IPv6 address resolution.
- 8 : 8-bit Process Order. This triggers an attempt to negotiate both input and output with the TELNET BINARY alternative. Telnet is not an 8-bit cleaner by design.
- e escapechar : Sets the character to flee to escape. No escape, if no character is given, It will use a character. Telnet is caused to drop to command mode by entering the escape character when attached.
- 1 user : Specify the account you want to log in to as a remote device user. This is achieved by sending the stated name as the USER environment variable, so it requires that the TELNET ENVIRON option be supported by the remote device. This option implies the option -a and can be used with the open command as well.
- n tracefile : Opens tracefile for recording trace information.
host : Specifies a host to contact over the network.
Port : Enter the port number or service name you want to touch. Telnet, if not mentioned, The (23) port is used.
The standard mechanism provided by TCP/IP for copying a file from one host to another is the File Transfer Protocol (FTP). Although it seems simple and straightforward to transfer files from one system to another, some issues must be dealt with first. For example, different file name conventions may be used by two systems. There can be different ways for two systems to represent text and data.
FTP differs from other client/server applications in that two connections between the hosts are established. One connection is used for the transfer of data, the other for information control (commands and responses). Command separation and transfer of data makes FTP more efficient.
Control connection
● The connection to control uses very simple communication rules. Wc must transmit only a command line or a response line at a time.
● Two well-known TCP ports are used by FTP: port 21 is used for the control connection.
Data connection
● Due to the variety of data types transferred, the data connection , on the other hand, needs more complex rules. The complexity difference, however, is at the level of FTP, not TCP. Both connections are treated the same for TCP.
● TCP ports are used by FTP : port 20 is used for the data connection.
During the entire interactive FTP session, the control connection stays connected. For every file transferred, the data connection is opened and then closed. Every time commands involving file transfer are used, it opens and closes when the file is transferred.
In other words, the control connection opens when a user starts an FTP session. Whilst the control connection is open, if several files are transferred, the data connection can be opened and closed multiple times.
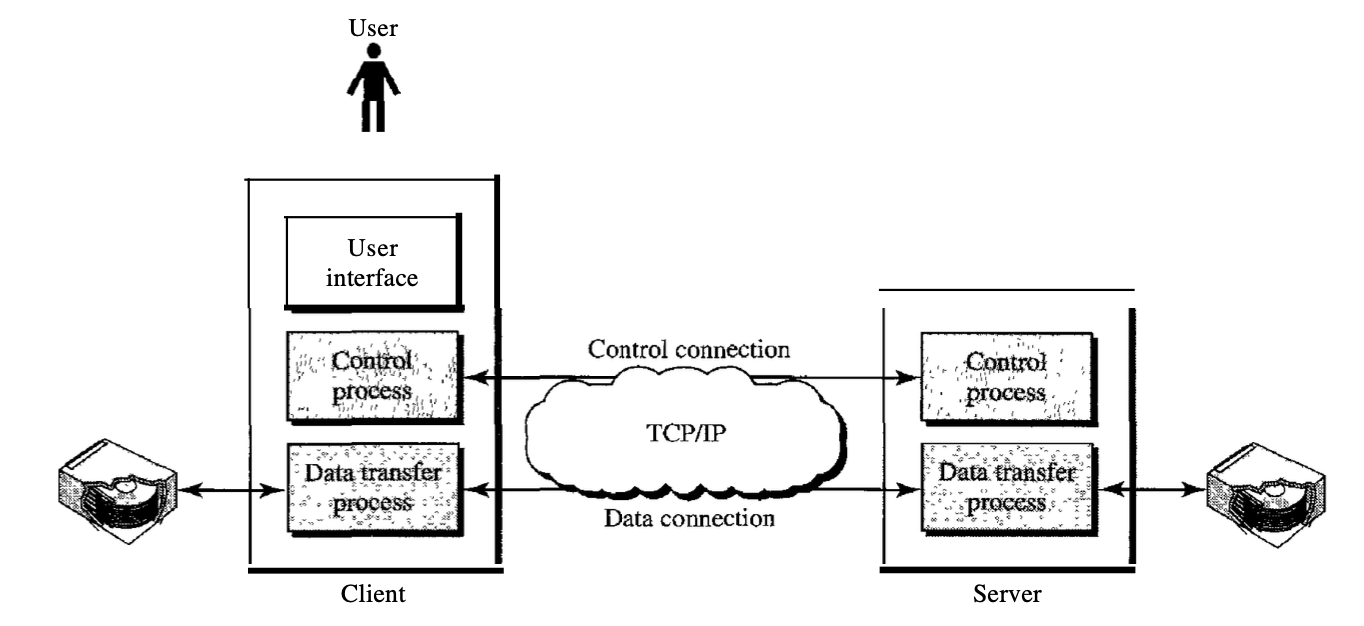
Fig 4: FTP
The client has three components: the user interface, the process of client control, and the process of transferring client data. The server has two components: the process of server control and the process of data transfer from the server. Between the control processes, the control connection is made. Between the data transfer processes, the data connection is made.
Key takeaway :
● FTP is a file transfer protocol.
● The standard mechanism provided by TCP/IP for copying a file from one host to another is the FTP.
● FTP differs from other client/server applications in that two connections between the hosts are established.
For data transformation, both the client and the server that operates on two distinct systems must be communicated. It uses two approaches to communication, i.e. communication over control links and communication over a data link, for communication.
Communication over control connection
For communicating through the control connection, FTP uses the same method as SMTP. It uses the ASCII 7-bit character set. Commands and responses accomplish communication. As we send one command (or response) at a time, this simple method is adequate for the control link. There is only one short line for each command or response, so we don't need to think about the file format or file structure. Each line is terminated with an end-of-line token of two characters (carriage return and line feed).
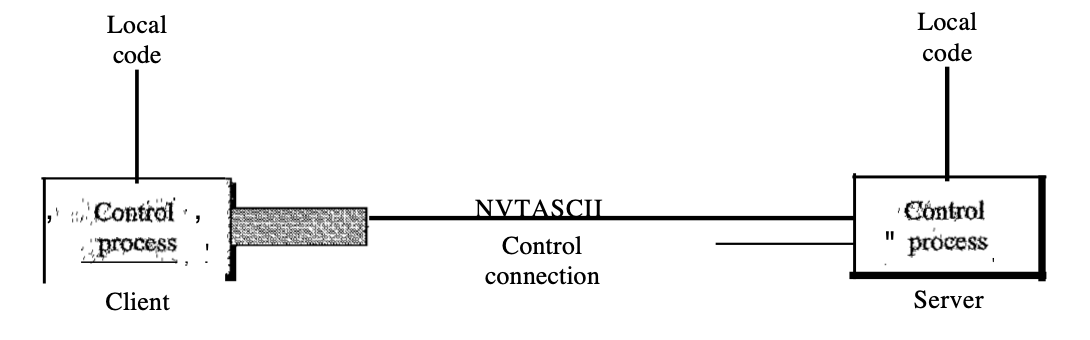
Fig 5: control connection
Communication over data connection
The function of the data connection is different from that of the control connection. File transfer takes place through the data connection under the control of the commands sent through the control connection. We want to transfer files through the data connection.
The client must specify the type of file to be transmitted, the data structure, and the mode of transmission. We plan for transmission through the control link before sending the file through the data connection. The heterogeneity problem is solved by specifying three communication attributes: type of file, data structure, and mode of transmission.

Fig 6: data connection
File type : FTP can transfer one of the following types of files over a data link: an ASCII file, an EBCDIC file, or a picture file. The ASCII file is the default text file transfer format. Using 7-bit ASCII, each character is encoded. The sender converts the file to ASCII characters from its own representation, and the recipient translates the ASCII characters to its own representation.
Data structure : By using one of the following interpretations of the structure of the data, FTP can transfer a file across the data connection: file structure, record structure, and page structure. The file is a continuous stream of bytes in the file structure format. The file is split into records inside the document structure.
Transmission mode : By using one of the following three transmission modes: stream mode, block mode, and compressed mode, FTP will transfer a file across the data link. The default mode is the Stream Mode. Data is transmitted as a continuous stream of bytes from FTP to TCP. TCP is responsible for the chopping of data into appropriate size segments.
Key takeaway :
● For data transformation, both the client and the server that operates on two distinct systems must be communicated.
● For communicating through the control connection, FTP uses the same method as SMTP.
● We plan for transmission through the control link before sending the file through the data connection.
FTP uses a control link to create contact between the client system and the server system. The client will send commands to the server during this process, and the server will send a response to the client in return.
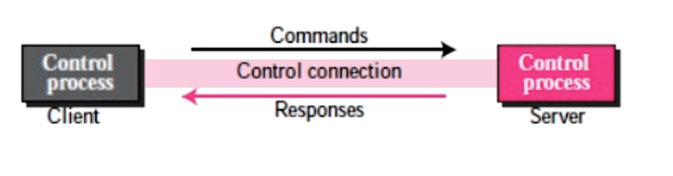
Fig 7: command processing
These commands are used to relay data. These commands have a single argument, i.e. the name of the file.
The list of file transfer commands below is
● RETR : The client uses this command to access files from the server.
● STOR : The client uses this command to store files on the server.
● APPE : It is identical to the STOR command, except the data must be appended to it if the file exists.
● STOU : It is also similar to the STOR command, except in the directory, every file name should be special.
● ALLO : This command is to assign the storage space on the server for files.
● STAT : The status of the specified files will be displayed by this instruction.
● REST : This command will position the marker for the file at the specified data points.
The FTP protocol command set provides a rich, complete set of instructions for implementing the File Transfer Protocol. A human user could employ those commands to perform file transfer functions directly with an FTP server. But to do this requires that the user have an intimate knowledge of how FTP works. The user must know exactly which commands to send at which time, and in what order.
User interface benefits
Memorizing internal FTP commands might be a reasonable assignment for an internetworking expert, but not for a typical TCP/IP application user. For this reason, the FTP protocol defines an additional protocol component as part of the User-FTP Process: the FTP user interface.
It provides three main benefits to the FTP user:
● User friendliness : The FTP user interface presents FTP to the human user in a way that is easier and simpler to use than issuing protocol commands. Instead of requiring the knowledge of all those four-letter codes, the user interface can allow functions to be performed with more intuitive human-language commands. For example, we can say “get” a file instead of knowing to use the command RETR.
● Customization : The command used to perform a particular function can be customised based on common parlance in the networking industry, without requiring changes to be made to the FTP protocol itself.
For example, the “image” transfer mode is now also commonly called “binary” mode, so a user command called “binary” has been created to set this mode.
● Detail Abstraction and Command Sequence Simplification : A single user command can be made to issue multiple FTP protocol commands, hiding internal FTP details and making the protocol easier to use. In particular, commands that are related to the maintenance of the connection and other “overhead” issues that users don't want to deal with can be automated.
For example, an FTP client normally issues a PASV or PORT command prior to each data transfer. The user interface can take care of issuing this command automatically prior to a RETR or STOR command when a user tells FTP to get or send a file.
Key takeaway :
● The FTP protocol command set provides a rich, complete set of instructions for implementing the File Transfer Protocol.
● The FTP user interface presents FTP to the human user in a way that is easier and simpler to use than issuing protocol commands.
On some sites whose files are available for public access, Anonymous FTP is enabled. Without having any username or password, a user can access these files. Instead, the username is set to anonymous by default and the guest's password. Here, there is very limited user access. The user may be allowed to copy files, for instance, but not to navigate through directories.
A user needs an account (user name) and a password on the remote server in order to use FfP. To enable anonymous FTP, some sites have a set of files available for public access. A user doesn't need to have an account or password to access these files. The user can use anonymous as the user name, instead, and guest as the password.
There is very limited user access to the system. Some sites permit only a subset of commands for anonymous users. Most sites, for instance, allow the user to copy some files, but do not allow the directories to be navigated.
Key takeaway :
● On some sites whose files are available for public access, Anonymous FTP is enabled.
● A user needs an account and a password on the remote server in order to use FfP.
● Some sites permit only a subset of commands for anonymous users.
The Trivial File Transfer Protocol has a very simple concept, and it also has a very simple nature because of its simple concept. Even though it has fewer features as opposed to File Transfer Protocol because of its basic nature. In general, no authentication is enforced by the Trivial File Transfer Protocol prior to file contact.
No authentication mechanisms apply to the Trivial File Transfer Protocol when filing communications. Since no authentication mechanism or security mechanism is enforced by the Trivial File Transfer Protocol, it could also not be used for file communication over the internet.
It is also a protocol for file transfer without sophisticated FTP functionality.
● For simple file transfers, such as during boot time, it is fine.
● It uses UDP protocols as the transport layer. The TFTP server must manage transmission errors (lost packets, checksum errors).
● It only uses one connection via port 69, which is well documented.
● Using a simple lock-step protocol, TFTP (each data packet needs to be acknowledged). The production is therefore small,
Types of TFTP
TFTP is of four types , they are-
● Read request
● Write request
● Data Packets
● Acknowledgment request
Advantages
● Uses UDP protocol
● Is easier to implement
● Requires less coding
● Less memory usage
Key takeaway :
● TFTP means trivial file transfer protocol.
● The TFTP has a very simple concept, and it also has a very simple nature because of its simple concept.
● No authentication is enforced by the Trivial File Transfer Protocol prior to file contact.
References :
2. Internetworking with TCP/IP by Douglas Comer
3. Computer Networking: A Top-Down Approach by Jim Kurose