Unit - 4
The Structure of Process
A process is an instance of an execution program. Combined together, a series of processes render a complete application.
Unix has two types of processes, namely,
User processes: In user mode, they are managed.
Processes in the kernel: They are run in kernel mode.
4.1.1 Process States
The states in which a process joins function from beginning to end are known as process states. All are referred to below as:
Crested- Newly created by machine call, Created-Process is not ready to run
User running-Process runs in user mode, which means it's a process for the user.
Kernel Running-Process Implies is a kernel process that operates in kernel mode.
Zombie- There is no process/ is terminated.
Preempted- It is said to be preempted as the process runs from kernel mode to user mode.
Ready to run in memory- It revealed that the process has entered a state where it is ready to run in memory, waiting for it to be scheduled by the kernel.
Sleep, swapped- The process is in a blocked state and has been swapped to secondary storage.
Asleep in memory- The mechanism is in memory, but in a blocked state (not swapped to secondary storage).
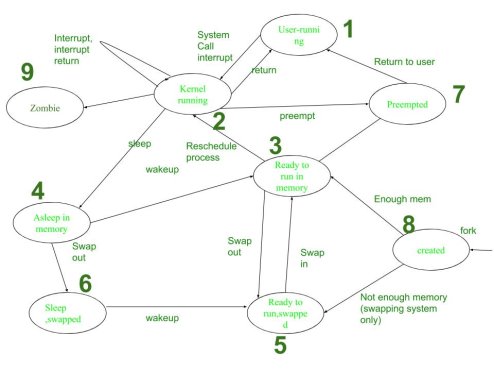
4.1.2 Process Transitions
The following measures clarify the functioning of the process:
User-running: User-running is a method.
Kernel-running: This method is delegated to the kernel and is, thus, in kernel mode.
Ready to run in memory: In addition, the process is rescheduled to the Kernel.i.e. after loading in the main memory process. The process is not running but is ready to run as soon as the kernel schedules it.
Asleep in memory: The mechanism is asleep, but the primary memory resides. Waiting for the assignment to commence.
Ready to run, switched: The loop is ready to run and can be swapped into main memory by the cpu, enabling the kernel to plan execution.
Pre-empted: The kernel pre-empts an existing allocation process for another process, while the first process transfers from the kernel to the user mode.
Created: Newly created process, but not running. For all operations, this is the starting state.
Zombie: The procedure was fully implemented and the escape call was activated.
The system, therefore, no longer exists. But, for the treatment, it stores a statistical log.
The ultimate condition of all systems is this.
There are three logical aspects of the UNIX system: text, data, and stack. The region and region are identical to the file table and the inode structure File device structure: Many processes are able to exchange portions of their addresses Space through an area, as often as they can share access to a file through an inode; each one of them. The method accesses the region through a private maternity admission, even like it accesses the region Inode in its user file descriptor table and kernel file table via private entries.
4.2.1 Region:
4.2.2 Pregion:
A process sense consists of the contents of its (user) address space and the contents of the process related hardware registers and kernel data structures.
The context of a method is the union of its context at the user level, the context of the register, and the context at the machine level.
The background of the user level consists of the process text, data, user stack, and shared memory occupying the process virtual address space.
A part of the user-level sense is also part of the virtual address space of a process that occasionally does not exist in the main memory due to switching or paging.
The context of the register consists of a component:
The kernel saves a process context if a new device is moved, Layer of background. In specific, this occurs when the machine is interrupted, when a system call is executed by a process, or when a context transition is made by the kernel.
Interrupts and Exceptions: the device is responsible for interrupt management, If they come from hardware (such as clock or peripheral hardware Devices), from a programmed interrupt (execution of instructions designed for the cause of "software interrupts"), or exceptions (such as page faults).
The entry in the area table contains the details required to identify a region.
Domain. Area. It includes the following entries in particular:
The reference count, which gives the number of processes referring the field.
4.5.1 Locking a region and Unlocking it:
The kernel has lock and unlock operations for an area, irrespective of the region allocation and free operations, much like the file system has lock-unlock and allocate-release operations for inodes (algorithms iget and iput).
The kernel will then lock and assign a region and then unlock it without the region needing to be released. Similarly, if an assigned area is to be abused, the region will be locked to avoid entry from such systems and then released.
4.5.2 Assigning a region:
The kernel assigns a new area (algorithm allocreg) during device calls to fork, exec, and shmget (shared memory). The kernel includes a region table whose entries appear either on a list with a free link or on a list with an active link.
The kernel removes the first available entry from the free list while allocating a region table entry, places it in the active list, locks the region, and labels its sort (shared or private). With only a few exceptions, as a consequence of a previous exec call, each method is connected with an executable file, and allocreg sets the inode field in the area table entry to point to the executable file inode.
References:
1. “Unix Concepts and Administration”, Sumitabha Das, TMGH, 3rd Edition.
2. “Unix Shell Programming”, YeshvantKanetkar, BPB Publications.
3. “Unix Utilities”, Tare, MGM.
4. “Advanced Programming in the UNIX Environment”, Stevens and Rego, Pearson Education, 2nd Edition.