Unit - 1
Introduction
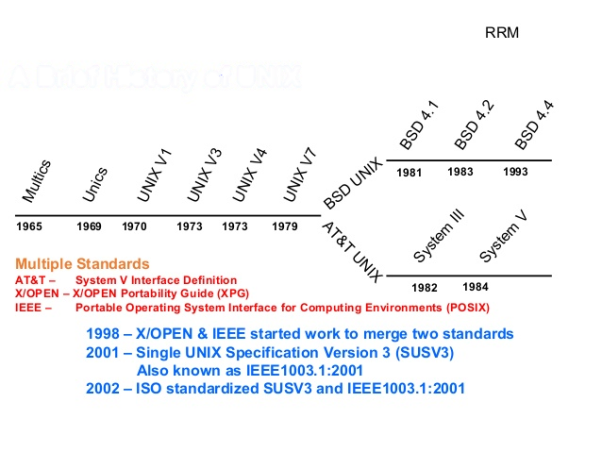
In MULTICS, which stands for Multiplexed Operating and Computing System, the Unix operating system has reached its origins. As a collaborative venture by General Electric, the Massachusetts Institute of Technology and Bell Laboratories, the MULTICS project begun in the mid-1960s. Bell Laboratories dropped out of the initiative in 1969.
Ken Thompson was one of the persons from Bell Laboratories participating in the research. He liked the opportunity MULTICS had, but thought it was too hard and that it was easier to do the same thing. He wrote the first Unix version, called UNICS, in 1969. The Uniplexed Operating and Computer System was UNICS. Although the operating system changed, the name stuck and gradually became known as UNIX.
|
Unix, developed by Bell Laboratories in 1969, is a multi-user, multi-task operating system. In a multi-user system, the system can be accessed concurrently by multiple users. A system of multitasking is capable of performing multiple tasks. In this type of operating system, each user communicates with its own shell instance and can launch applications as needed.
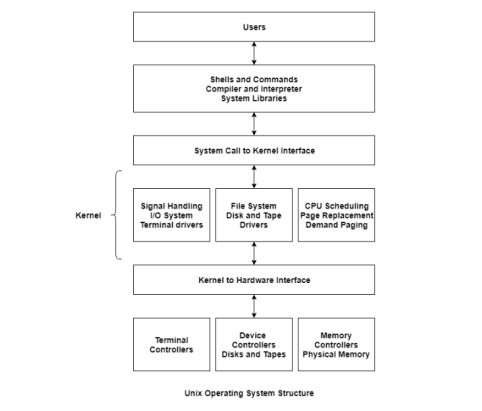
A picture that displays the configuration of the Unix operating system is –
|
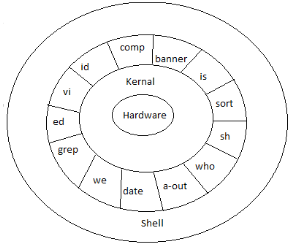
1.2.1 Kernel
A bridge is given by the kernel between the hardware and the user. It is an application for applications and is fundamental to the operating system. The kernel manages the operating system directories, memory, computers, processes and the network. The kernel is responsible for ensuring that both the machine and user functions are done correctly.
1.2.2 The Shell
The shell is known as the program between the user and the kernel. This converts the several instructions to the terminal session that are typed. These commands are known as the script of the shell. There are two main types of shells in Unix. Both are C Shell and Bourne Shell. For version 7 Unix, the Bourne kernel is the default shell.
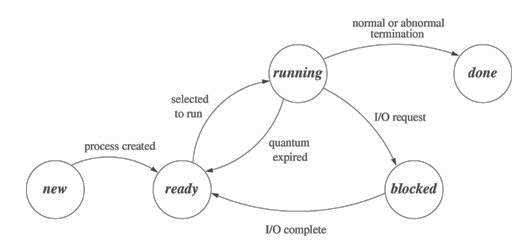
A ASCII text file is our program ASCII text file, an executable file is that the program for our ASCII text file and therefore the process is that the instance of our program in execution. Many processes can execute simultaneously in uix. (Multiprogramming or multitasking). Also many instances of 1 program can run simultaneously. Each instance of this program is one process. Various system calls allow control of the state of the method. The state of a process indicates its status at a specific time. the method state could by anybody of the subsequent.
Process state information alongside other useful information is stored during a process control block. Every process has its own process control block or PCB.
Unix shell allows three sorts of commands.
An executable file created by compilation of our ASCII text file .
An executable command that contains a sequence of shell commands.
An internal shell commands.
The shell, usually, run the commands synchronously. However these commands also can be run asynchronously.
Unix allows user to write down small programs, during a modular way. These programs are often used as building blocks to create the complex programs.
Unix has three standard files:
1. Standard input data
2. Standard computer file
3. Standard error file
Typically once we run shell our terminal (monitor) is serving as these three files. (remember devices are often treated as files).
One primitive building block available to the shell user is that the redirect I/O. for instance
ls
this command list down all the files within the current directory.
ls > output
this command will send this list of files to a file named “output” rather than the terminal.
The second building block primitive is that the PIPE. Pipe allows a stream of knowledge to be passed from processes. there's one reader process and one writer process.
1.4.1 Init
Init is the first method in any UNIX system that delivers the single most essential service in a UNIX system, being the last thing the kernel does when it boots. When init begins, it continues the boot loop by executing separate initialization tasks (checking and mounting filesystems, starting daemons, etc).
The particular list of items that init does depends on the palate it has; there are many things to pick from. The definition of single user mode is typically provided by init, in which no one can log in and root uses a console shell; the normal mode is called multi-user mode. Some flavors generalize this as run levels; two run levels are known to be single and multi-user modes, and there can also be alternate ones, such as running X on the console.
Up to 10 run levels, 0-9, are permitted by Linux, but typically only some of these are specified by default. "System halt " is defined as run level 0. Run level 1 is defined as "single user mode ". Run level 3 is known as "multi user" because, under normal day-to-day conditions, it is the run level that the device boots into. "Typically, run level 5 is the same as 3 except that a GUI is now started. Run level 6 is known as "machine reset." Other run levels depend on how they have been defined by your particular distribution, and they differ greatly between distributions. Looking at the contents of /etc/init tab would generally provide an idea of what the predefined run levels are and what they were defined as.
Init ensures that getty functions (to allow users to log in) and adopts orphan processes in regular operation (processes whose parent has died; in UNIX all processes must be in a single tree, so orphans must be adopted).
It is init that is responsible for terminating all other processes while the machine is shut down, unmounting all filesystems and stopping the cpu, along with everything else it has been programmed to do.
1.4.2 Login from terminals
The getty software provides logins from terminals (via serial lines) and the console (when not running X). For each terminal on which logins are to be enabled, init initiates a separate instance of getty. Getty reads the username and executes the password-reading login program. If the username and password are right, the shell will be run by Login. Init detects this as the shell stops, i.e. the user logs out, or when login terminates because the username and password did not fit, and begins a new instance of getty. There is no definition of logins in the kernel, both of which are done by machine programs.
1.4.3 Syslog
The kernel and several programs in the system create bugs, alerts, and other messages. It is also important to be able to access these messages later, even much later, so that they can be written to a file. Syslog is the software that does this . It can be programmed to arrange the messages according to writer or degree of value to various folders. Kernel messages, for instance, are often guided to a different file from others, since kernel messages are often more important and need to be read frequently to find issues.
1.5.4 Periodic command execution: cron and at
Commands often need to be run periodically by both users and system administrators. For example, the system administrator might want to run a command to clean directories from old files with temporary files (/tmp and /var/tmp), to keep the disks from filling up, because not all programs are properly cleaned up.
To do this, the cron service is configured. Each user can have a crontab file in which the commands they want to execute are listed and the times they should be executed. When specified, the cron daemon takes care of starting the commands.
The at service is similar to cron, but it is once only: the command is executed at the given time, but it is not repeated. Later, we're going to go further into this. For more in-depth data, see the manual pages cron(1), crontab(1), crontab(5), at(1) and atd(8).
1.4.5 Graphical User Interface
UNIX and Linux do not incorporate the user interface into the kernel, but instead allow programs at the user level to implement it. For both text mode and graphical environments, this applies.
This arrangement makes the system more flexible, but has the disadvantage that it is simple for each program to implement a different user interface, making it more difficult to learn the system.
The graphical environment used mainly for Linux is known as the X Window System (X for short). A user interface is also not implemented by X; it only implements a window system, i.e. tools with which to implement a graphical user interface. Fvwm, icewm, black box, and windowmaker are some common window managers.
Two popular desktop managers, KDE and Gnome, are also present.
1.4.6 Networking
The act of connecting two or more computers so that they can interact with each other is networking. The actual methods of connecting and communicating are slightly complicated, but the end result is very useful.
There are many networking features on UNIX operating systems. Most basic services (filesystems, printing, backups, etc) can be done over the network. This can facilitate system administration by allowing centralized administration while still reaping the benefits of microcomputing and distributed computing, such as lower costs and improved fault tolerance.
1.4.7 Network logins
Network logins function slightly differently from normal logins. There is a separate virtual network connection for each person logging in via the network, and any number of these can be available depending on the bandwidth available. Therefore, for each possible virtual connection, it is not possible to run a separate Getty. There are also several different ways of logging in through a network, the main ones being telnet and ssh in TCP/IP networks.
Many Linux system administrators these days consider telnet and rlogin to be unsafe and prefer ssh, the " safe shell " which encrypts network traffic, making it far less likely that the malicious will 'sniff" your connection and gain sensitive information such as usernames and passwords. It is strongly recommended that you use ssh instead of telnet or rlogin.
Assumptions about the hardware
It operates on two levels while a method is executed on Unix, or we may say it runs in two modes.
User mode processes are able to evaluate their own instructions, but not the kernel instructions or other process instructions. In kernel mode, on the other hand, processes can access kernel data and instructions, as well as user information and instructions.
The machine calls can only be executed in the kernel mode. If a device is called by a user process operating in user mode, the process switches from user mode to kernel mode, and then the request is serviced by the kernel service, and the system returns to user mode after the request is serviced.
|
Unix and Unix-like operating systems are a group of computer operating systems descended from Bell Labs' initial Unix Framework.
The HP-UX and SunOS systems were the first proprietary derivatives. However, as the incompatibility between these systems grew, interoperability requirements such as POSIX were created. Linux and its derivatives, as well as Mac OS, are modern POSIX systems.
Unix is the most powerful and widely used operating system for multi-user and multi-tasking applications. The Multics initiative, which began in 1969, gave birth to the fundamental principles of Unix. The Multics system was designed to be a time-sharing system that would enable many users to use a mainframe computer at the same time.
For the PDP-7, Ken Thompson, Dennis Ritchie, and others created the fundamental building blocks of Unix, such as a hierarchical file structure, procedures, and a command line interpreter. Multiple generations of Unix were created from there for different computers.
Interoperability specifications such as POSIX and Single Unix Specification were created in response to growing incompatibility between these systems.
Unix systems are built around a set of core philosophies, which include single-purpose, interoperable, and structured text interface standards. Unix systems are based on a kernel that controls the whole system as well as the other operations.
Thread management, file management, memory management, network management, and other kernel subsystems are examples.
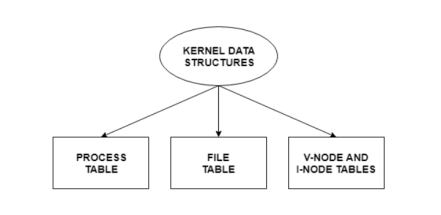
As they store data about the current state of the machine, the kernel data structures are very important. If a new process is created in the code, for example, a kernel data structure is created that includes the process information.
Only the kernel and its subsystems can control most kernel data structures. They can contain both data and pointers to other structures of data.
1.7.1 Kernel Components
A lot of information is stored and organised by the kernel. So it has information about which processes in the system are running, their memory requirements, files in use, etc. Three significant structures are used to handle all this. These are the data for the process table, file table and v node/i node.
|
Linux is a major computing technology powerhouse. Linux is powered by most web servers, mobile phones, personal computers, supercomputers and cloud servers. A Linux system administrator's task is to manage a computer system's operations, such as maintaining, enhancing, creating user account/reporting, taking backups using Linux tools and command line interface tools. Because of its high stability, high security, and open-source environment, most computing devices are powered by Linux. Some of the things a Linux system administrator should know and understand are as follows:
References:
1. “Unix Concepts and Administration”, Sumit abha Das, TMGH, 3rd Edition.
2. “Unix Shell Programming”, Yeshvant Kanetkar, BPB Publications.
3. “Unix Utilities”, Tare, MGM.
4. “Advanced Programming in the UNIX Environment”, Stevens and Rego, Pearson Education, 2nd Edition.