Module - I
Data Communication, Networking and Internet
The components of a communication system are as follows:
● Message : It is the facts or information that will be communicated. Text, numbers, graphics, sound, or video, or any combination of these, can be used.
● Sender : That message is generated and sent by the device/computer.
● Receiver : The message is received by the device or computer. The receiving computer is usually located somewhere other than the sending computer. The distance between transmitter and recipient is determined by the network types utilized in the middle.
● Medium : It is the physical road or channel by which the message is sent from the sender to the receiver. The medium may be wired, such as twisted pair wire, coaxial cable, or fiber-optic cable, or wireless, such as lasers or radio waves, and microwaves.
● Protocol : It's a collection of rules that regulate how devices communicate with one another. Both the sender and the recipient communicate using the same protocols.
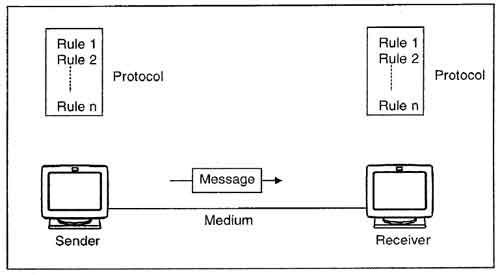
Fig 1: Component of data communication
The following are the functions of a protocol:
● Data sequencing - It refers to the process of dividing a large communication into smaller, fixed-size packets. Data sequencing rules specify how to number packets in order to detect packet loss or duplication, as well as correctly identify packets that belong to the same message.
● Data routing - The most efficient path between the source and the destination is defined by data routing.
● Data formatting - Data formatting rules specify which bits or characters in a packet are used to represent data, control, addressing, or other data.
● Flow control - A communication protocol also protects a slow receiver from being overwhelmed by a fast sender. By managing the flow of data over communication cables, it ensures resource sharing and traffic congestion prevention.
● Error control - These rules are intended to detect message mistakes and ensure that the proper messages are transmitted. Retransmitting an erroneous message block is the most usual way. A block with an error is discarded by the receiver and retransmitted by the sender in this situation.
● Precedence and order of transmission - These rules ensure that, according to the priority assigned to them, all nodes receive a chance to use the network's communication lines and other resources.
● Connection establishment and termination - When two nodes in a network desire to interact with each other, these rules specify how connections are made, maintained, and terminated.
● Data security - Most communication software packages also provide data security and privacy features. It prohibits unauthorized individuals from accessing data.
● Log information - Several communication software programs are designed to create log information, which includes all jobs and data communications tasks completed. This information could be used to charge network users based on their consumption of network resources.
Data Representation
Data is a collection of unprocessed facts that is used to derive information.
Data can be represented in a number of different ways. The following are some examples of data types used in communications:
Text : Combinations of upper and lower case alphabets are used in the text. It is saved as a bit pattern. The most widely used encoding system is: ASCII, Unicode.
Numbers : Numbers are made up of digits ranging from 0 to 9. It is saved as a bit pattern. The most widely used encoding system is: ASCII, Unicode.
Images : A popular proverb goes, "A picture is worth a thousand words." Images are digitally saved on computers. The smallest constituent of an image is a pixel. A picture or image is a matrix of pixel elements, to put it simply.
The bits are used to represent the pixels. Each pixel would require a varied number of bits to indicate the value of a pixel depending on the type of image (black and white or color).
The number of pixels (also known as resolution) and the bit pattern used to express the value of each pixel determine the size of an image.
For example, if an image is entirely black and white (two colors), each pixel can be represented by a value of 0 or 1, requiring just 100 bits in memory to hold a 10 x 10 pixel image.
An image with grayscale may, on the other hand, require two bits to represent each pixel value (00 – black, 01 – dark gray, 10 – light gray, 11 – white). As a result, storing the identical 10 × 10 pixel image now requires 200 bits of memory. Image formats that are commonly used include jpg, png, bmp, and others.
Audio : Sound can also be used to represent data, which can be recorded and disseminated. For example, what we hear on the radio is a data or information source. The data in audio is continuous rather than discrete.
Video : The term "video" refers to the transmission of data in the form of a picture or a movie.
Distributed processing
Distributed Processing is a method of disseminating data over a number of devices, which could be computers or data terminals with some intelligence. The devices are linked by communication systems. A distributed system is one in which components on networked computers communicate and coordinate their operations solely through the transmission of messages.
Examples
● The internet
● An intranet which is a portion of the internet managed by an organization
Key takeaway:
- Data is a collection of unprocessed facts that is used to derive information.
- Data can be represented in a number of different ways.
- Distributed Processing is a method of disseminating data over a number of devices, which could be computers or data terminals with some intelligence.
- A distributed system is one in which components on networked computers communicate and coordinate their operations solely through the transmission of messages.
Definition, Types (LAN, MAN, WAN) Advantages
Data is communicated over computer networks.
A collection of nodes can be defined as a computer network. Any device capable of transmitting or receiving data might be considered a node. Communication links must be established between the communicating nodes.
A data network is made up of a collection of hosts linked together through network devices. Any device that sends and receives data through a network is referred to as a host. Devices that are connected to hosts are referred to as peripherals. Some devices have the ability to function as both hosts and peripherals. A printer linked to a networked laptop, for example, is considered a peripheral. The printer serves as a host when it is linked directly to a network device such as a hub, switch, or router.
Computer networks are used in businesses, homes, schools, and government institutions all around the world. The Internet connects many of the networks.
It is possible to connect various types of devices to a network:
● Desktop computers.
● Laptops.
● Printers
● Scanners
● Personal digital assistants (PDA).
● Smartphones.
● Print and file servers.
Types
A computer network is a set of computers linked together by a communication medium such as cable or wire.
The geographic area and number of computers that make up a network can be used to determine the scale of the network. It can range from a single computer in a single room to millions of devices distributed across the globe.
Based on their complexity, computer networks are divided into following categories:
- LAN : A Local Area Network (LAN) is a set of computers and peripheral devices linked in a small area, such as a classroom, laboratory, home, or office building. It's a popular network for sharing resources such as files, printers, games, and other software. Connecting computers and a printer in someone's home or office is the most basic form of LAN network. LAN will be used as one form of transmission medium in general.
It's a network of less than 5000 interconnected devices spread over several buildings.
Fig 2: LAN
Advantages of LAN
The following are some of the advantages and disadvantages of using a LAN:
● Local area networks can share computer resources such as hard disks, DVD-ROMs, and printers. This lowers the cost of hardware purchases greatly.
● Instead of acquiring licensed software for each client in the network, you can utilize the same software across the network.
● All network users' data can be saved on the server computer's single hard disk.
● Data and messages can be easily transferred across networked computers.
● It will be simple to handle data in a single location, making data more secure.
● The ability to share a single internet connection among all LAN users is provided by a local area network.
Disadvantages of LAN
The following are the major disadvantages and downsides of LAN:
● Because of shared computer resources, LANs will save money, but the initial cost of setting up a LAN is fairly significant.
● Because the LAN administrator has access to every LAN user's personal data files, it does not provide adequate privacy.
● Unauthorized users can gain access to an organization's essential data if the LAN administrator fails to secure the centralized data repository.
● Because there are issues with software setup and hardware failures, a constant LAN administration is required.
2. MAN : A Metropolitan Area Network, or MAN, is a computer network that spans a city, a college campus, or a small area. This network is far larger than a LAN, which is usually restricted to a single building or location. This form of network can cover a range of distances from a few miles to tens of miles, depending on the configuration.
Fig 3: MAN
Advantages of MAN
The following are some of the advantages and disadvantages of adopting the MAN system:
● It provides high-speed communication over high-speed carriers such as fiber optic cables.
● It offers good support for a large network and increased WAN connectivity.
● The MAN network's dual bus allows data to be transmitted in both directions at the same time.
● A MAN network usually covers a portion of a city or the entire city.
Disadvantages of MAN
The following are some disadvantages and disadvantages of using the MAN network:
● To construct a MAN connection from one location to another, you'll need more cable.
● It's difficult to keep a MAN network secure from hackers.
3. WAN : Another significant computer network that spans a vast geographical area is the WAN (Wide Area Network). A WAN network system may be a LAN link that uses telephone lines and radio waves to connect to other LANs. It is usually restricted to a single company or organization.
Fig 4: WAN
Advantages of WAN
The following are some of the advantages and disadvantages of using WAN:
● The Wide Area Network (WAN) allows you to cover a broader geographical area. As a result, corporate offices located at a greater distance can connect effortlessly.
● Mobile phones, laptops, tablets, desktops, game consoles, and other electronic gadgets are included.
● The radio transmitters and receivers embedded into client devices are used to establish WLAN connections.
Disadvantages of WAN
The following are some disadvantages and disadvantages of using WAN:
● The initial investment setup cost is really significant.
● The WAN network is difficult to maintain. You'll need technicians and network administrators who are well-versed in their fields.
● Because of the vast coverage and use of many technologies, there are more faults and issues.
● Because many wired and wireless technologies are involved, it takes longer to fix issues.
● When compared to other forms of networks, it provides less security.
Key takeaway:
- A computer network is a set of computers linked together by a communication medium such as cable or wire.
- A LAN is a set of computers and peripheral devices linked in a small area, such as a classroom, laboratory, home, or office building.
- A MAN is a computer network that spans a city, a college campus, or a small area.
- A WAN network system may be a LAN link that uses telephone lines and radio waves to connect to other LANs.
Network Structures – Server Based, Client server, Peer to Peer
Computer Network Architecture is defined as the physical and logical design of the software, hardware, protocols, and media of the transmission of data. Simply we can say how computers are organized and how tasks are allocated to the computer.
The two types of network architectures are used:
● Peer-To-Peer network
● Client/Server network
Client/Server Network
Client/Server network is a network model designed for the end users called clients, to access the resources such as songs, video, etc. from a central computer known as Server. The central controller is known as a server while all other computers in the network are called clients. A server performs all the major operations such as security and network management.
A server is responsible for managing all the resources such as files, directories, printers, etc. All the clients communicate with each other through a server. For example, if client1 wants to send some data to client 2, then it first sends the request to the server for the permission. The server sends the response to client 1 to initiate its communication with client 2.
Advantages of Client/Server network:
A Client/Server network contains the centralized system. Therefore, we can back up the data easily. A Client/Server network has a dedicated server that improves the overall performance of the whole system. Security is better in the Client/Server network as a single server administers the shared resources. It also increases the speed of sharing resources.
Disadvantages of Client/Server network:
Client/Server network is expensive as it requires the server with large memory. A server has a Network Operating System (NOS) to provide the resources to the clients, but the cost of NOS is very high. It requires a dedicated network administrator to manage all the resources.
Peer-To-Peer network
Peer-To-Peer network is a network in which all the computers are linked together with equal privilege and responsibilities for processing the data. Peer-To-Peer network is useful for small environments, usually up to 10 computers. Peer-To-Peer network has no dedicated server. Special permissions are assigned to each computer for sharing the resources, but this can lead to a problem if the computer with the resource is down.
Advantages of Peer-To-Peer Network:
It is less costly as it does not contain any dedicated server. If one computer stops working, other computers will not stop working. It is easy to set up and maintain as each computer manages itself.
Disadvantages of Peer-To-Peer Network:
In the case of the Peer-To-Peer network, it does not contain the centralized system. Therefore, it cannot back up the data as the data is different in different locations. It has a security issue as the device is managed itself.
Key takeaway:
- Computer Network Architecture is defined as the physical and logical design of the software, hardware, protocols, and media of the transmission of data.
- Peer-To-Peer network is a network in which all the computers are linked together with equal privilege and responsibilities for processing the data.
- Client/Server network is a network model designed for the end users called clients, to access the resources such as songs, video, etc.
Topologies – Star, Bus, Ring
Topology refers to the network's structure and how all of the elements are linked to one another. Physical and logical topology are the two forms of topology.
The geometric representation of all the nodes in a network is known as physical topology.
● Bus topology : The bus topology is set up in such a way that all of the stations are linked together by a single backbone cable. Each node is either connected to the backbone cable through a drop cable or is directly connected to it.
When a node wishes to send a message across the network, it does so by sending a message across the network. Regardless of whether the message has been answered, it will be received by all available stations in the network.
The bus topology is commonly used in regular networks such as 802.3 (ethernet) and 802.4 (wireless). In comparison to other topologies, the configuration of a bus topology is very straightforward. The backbone cable is thought of as a "single path" from which the message is sent to all of the stations.
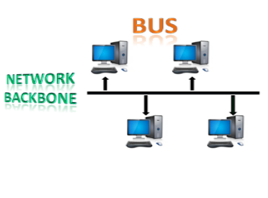
Fig 5: bus topology
● Ring topology : The topology of a ring is similar to that of a bus, but with connected ends. The node that receives the previous computer's message will retransmit to the next node. The data is unidirectional, meaning it only moves in one direction.
The data is continually flowed in a single loop, which is referred to as an infinite loop. It has no terminated ends, which means that each node is connected to the next and has no point of termination.
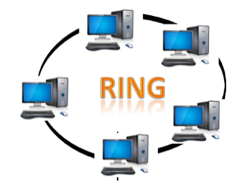
Fig 6: ring topology
● Star topology : The star topology is a network configuration in which each node is connected to a central hub, switch, or device. The central computer is referred to as a server, and the peripheral devices connected to it as clients.
The computers are connected via coaxial cable or RJ-45 cables. In a physical star topology, hubs or switches are primarily used as connection devices. The star topology is the most widely used network topology.
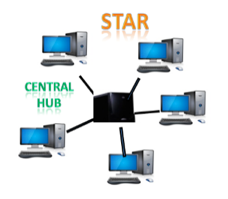
Fig 7: star topology
Key takeaway:
- Topology refers to the network's structure and how all of the elements are linked to one another.
- The bus topology is set up in such a way that all of the stations are linked together by a single backbone cable.
- The star topology is a network configuration in which each node is connected to a central hub, switch, or device.
Network Media, Wired-Twisted Pair, Co-axial, Fiber Optic and Wireless – Radio and Infrared
Physical transmission media used in communications include twisted-pair cable, coaxial cable, and fiber-optic cable. These cables typically are used within or underground between buildings. Ethernet and token ring LANs often use physical transmission media.
Guided media
The physical medium by which signals are transmitted is referred to as the transmission medium. Bounded media is another name for it.
Types of guided media :
Twisted-Pair Cable
One of the more commonly used transmission media for network cabling and telephone systems is twisted-pair cable. Each twisted-pair wire consists of two separate insulated copper wires that are twisted together. The wires are twisted together to reduce noise. Noise is an electric- cal disturbance that can degrade communications.
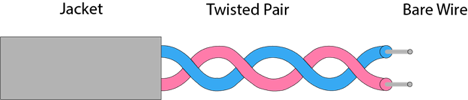
Fig 8: twisted pair cable
Types of twisted pair cable
- Unshielded twisted pair
- Shielded twisted pair
Coaxial Cable
Coaxial cable, often referred to as coax, consists of a single copper wire surrounded by at least three layers: (1) an insulating material, (2) a woven or braided metal, and (3) a plastic outer coating.
Cable television (CATV) network wiring often uses coaxial cable because it can be cabled over longer distances than twisted-pair cable. Most of today’s computer networks, however, do not use coaxial cable because other transmission media such as fiber-optic cable transmit signals at faster rates.
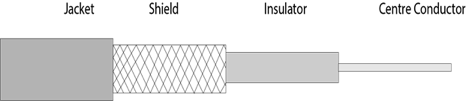
Fig 9: coaxial cable
Types of coaxial cable
- Baseband transmission
- Broadband transmission
Fiber-Optic Cable
The core of a fiber-optic cable consists of dozens or hundreds of thin strands of glass or plastic that use light to transmit signals. Each strand, called an optical fiber, is as thin as a human hair. Inside the fiber-optic cable, an insu- lating glass cladding and a protective coating surround each optical fiber.
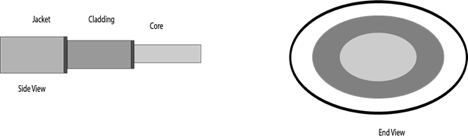
Fig 10: fiber optic cable
Fiber-optic cables have the following advantages over cables that use wire, such as twisted-pair and coaxial cables:
● Capability of carrying significantly more signals than wire cables
● Faster data transmission
● Less susceptible to noise (interference) from other devices such as a copy machine
● Better security for signals during transmission because they are less susceptible to noise
● Smaller size (much thinner and lighter weight)
Unguided media
The electromagnetic waves are transmitted without the use of any physical medium in an unguided transmission. Therefore it is also known as wireless transmission.
Air is the medium through which electromagnetic energy can easily flow in unguided media.
Unguided transmission can be categorized into three types:
Radio waves: Radio waves are electromagnetic waves that travel through free space in all directions. Radio waves are omnidirectional, which means that the signals travel in all directions. Radio waves have a frequency range of 3 kHz to 1 kHz. The transmitting and receiving antennas are not compatible in the case of radio waves, so the wave transmitted by the sending antenna can be received by any receiving antenna.
Infrared: Infrared transmission is a wireless communication technology that works over short distances. Infrared waves with frequencies ranging from 300 GHz to 400 THz. It's used for short-range communication including data transfer between two mobile phones, TV remote control, and data transfer between a computer and a cell phone that's in the same room.
Key takeaway:
- One of the more commonly used transmission media for network cabling and telephone systems is twisted-pair cable.
- Each twisted-pair wire consists of two separate insulated copper wires that are twisted together.
- The core of a fiber-optic cable consists of dozens or hundreds of thin strands of glass or plastic that use light to transmit signals.
- The electromagnetic waves are transmitted without the use of any physical medium in an unguided transmission.
- Radio waves are electromagnetic waves that travel through free space in all directions.
- Infrared waves with frequencies ranging from 300 GHz to 400 THz.
Network Hardware: Hubs, Bridges, Switches, and Routers
Hubs
In a computer network, a hub is used to connect numerous computers or LAN segments. It's usually used for a modest Peer-to-Peer Home Network. LAN Hub receives data packets (frames) via one port and broadcasts them to all other ports, allowing all other computers or network devices to see them.
For example, a LAN configured with an Ethernet hub falls under the star type topology group. The central controller in a star architecture is the hub. It does, however, logically, fit into the bus topology category. The majority of commercially available network hubs contain eight or sixteen ports. The physical layer of the OSI model is where networking hubs operate. Traditional Networking hubs support 10 Mbps rated speeds (data rate or bandwidth) only, but Newer technology Dual-speed hubs support 100 Mbps. There is no routing table in the hub, as you find in routers or switches.
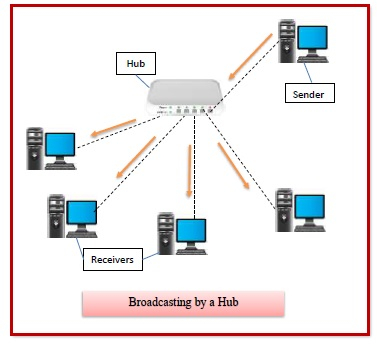
Fig 11: hub
Types of hubs
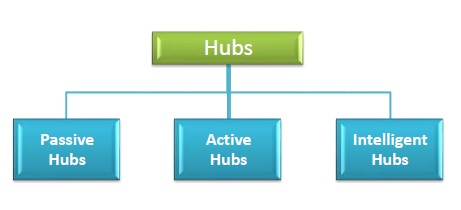
Fig 12: types of hub
- Active Hubs
Active hubs are a type of networking device that strengthens signals before transmitting them to the destination devices. It's also referred to as a "multiport repeater." Active hubs are typically utilized to connect nodes in a physical star topology. It has the ability to increase the maximum media distance over a network.
2. Passive Hubs
The signal is not amplified before being disseminated over a network through passive hubs. They merely kept a physical connection open and received the frames, which they then rebroadcast throughout the network. It is simply a connector that joins wires from several branches. The passive hub is the location at which signals from many stations collide and clash.
3. Switching hubs or intelligent hubs
The advantages of intelligent hubs over active and passive hubs are numerous. Switching hubs read the frames of each unit of data and transmit them to the intended port on behalf of the MAC address. It's a Layer 2 gadget. Using popular typologies such as Ethernet and Token Ring, switching hubs support 10, 16, and 100Mbps bandwidth.
Bridges
Bridges are network connection devices that work at the data link layer of the OSI model. Bridges, in comparison to Layer 1 devices like repeaters and hubs, have additional connectivity features. Bridges are used to segment networks that have expanded to the point where data traffic through the network's physical environment is slowing down global information transit.
Bridges, like repeaters, are used to connect similar LANs together, such as Ethernet-to-Ethernet, and operate at the OSI model's bottom two tiers, the physical layer and the data link layer. It sends only required data to other signals because it functions on the second layer of the OSI model. MAC addresses (physical addresses) are used to determine whether data is necessary or not.
MAC addresses (also known as hardware addresses; these are recorded in the NIC of each computer on the network) in each data packet that circulates through the segments of the network that connect the bridge can be examined by bridges (which usually include bridge hardware and some bridge operating system software). The bridge can block data traffic from a certain segment from flowing through to another segment of the network that is also linked to the bridge by knowing which MAC addresses belong in each of the network segments.
It sends data from one LAN segment to another based on the packet's destination address. To put it another way, when a bridge receives data through one of its ports, it looks for a MAC address in the data. The bridge transfers data through this port if this address matches that of the node linked to the other port. This is referred to as forwarding. The bridge discards the address if it does not match any node linked to another port. Filtering is the term for this action. Bridges, unlike repeaters, include buffers to hold and forward packets if the destination link is overburdened with traffic.
Switches
Switches are networking devices that operate at the OSI model's layer 2 or data link layer. They connect network devices and use packet switching to deliver, receive, and forward data packets or data frames across the network.
A switch has a number of ports into which computers can be connected. When a data frame arrives at any port of a network switch, it is examined for the destination address, relevant checks are performed, and the frame is sent to the appropriate device (s). It may communicate in unicast, multicast, and broadcast modes.
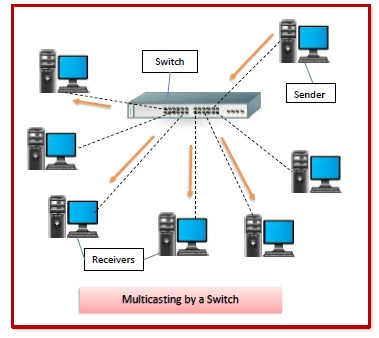
Fig 13: switches
Features of switches
A switch is part of the OSI model's layer 2, or data link layer.
● It is a multiport network bridge that functions as an intelligent network device.
● It sends data packets to designated destination ports using MAC addresses (medium access control sublayer addresses).
● It receives and forwards data packets from the source to the destination device using packet switching technology.
● Unicast (one-to-one), multicast (one-to-many), and broadcast (one-to-all) communications are all supported.
● Full duplex transmission means that communication in the channel occurs in both directions at the same time. Collisions are avoided as a result of this.
Types of switches
There are four types of switches that can be broadly classified as follows:
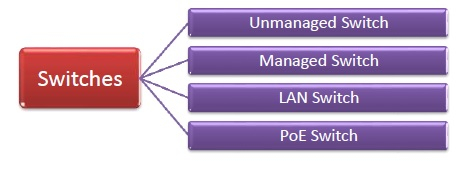
Fig 14: types of switch
Unmanaged switch – These are low-cost switches that are frequently found in home networks and small companies. They may be set up by just plugging them into the network and they will immediately begin to function. When more devices are needed, this plug-and-play mechanism allows for the addition of extra switches. They're called u managed since they don't need to be configured or monitored.
Managed switch – Because they may be configured to extend the functionality of a regular switch, these are expensive switches that are employed in organizations with vast and complicated networks. QoS (Quality of Service) features such as stronger security levels, more precision control, and complete network management could be included. They are favoured in growing enterprises due to their scalability and flexibility, despite their high cost. For setting managed switches, the Simple Network Management Protocol (SNMP) is utilized.
LAN switch – Local Area Network (LAN) switches connect devices on an organization's internal LAN. Ethernet switches and data switches are other names for them. These switches are especially useful for removing network bottlenecks or congestion. They allot bandwidth in such a way that data packets in a network do not overlap.
PoE switch – PoE Gigabit Ethernets employ Power over Ethernet (PoE) switches. PoE technology combines data and power transmission over a single cable, allowing devices connected to it to receive both electricity and data. PoE switches provide more flexibility and make cabling connections easier.
Routers
Routers connect LANs that are both similar and distinct. The physical layer, data link layer, and network layer are used by the router to provide connectivity, addressing, and switching on the network layer of the OSI model. These are extremely sophisticated gadgets. In a TCP/IP network, Internet Protocol (IP) addresses are used as network addresses; this is the router that understands the IP address and reliably delivers the packet.
Now, we can state that the router transmits network layer data and, as a result, allows data to be transmitted between LANs that utilize different data link protocols but the same network layer protocol. Routers are protocol sensitive; they often support many protocols as well as large and varied packet sizes, such as those required to support both Ethernet and Token Ring.
Unlike bridges, a network made up of routers can have numerous pathways. Normally, packets are transferred via the shortest of all network pathways.
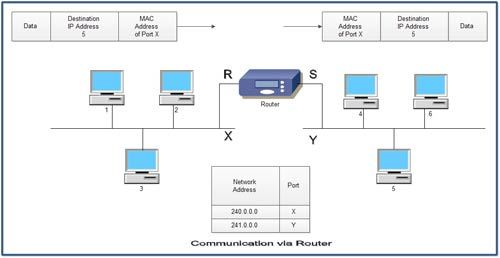
Fig 15: routers
Characteristics of routers
● Routers are devices having several ports and high-speed backbones.
● Like bridges, routers support filtering and encapsulation.
● Routers, like bridges, are self-learning because they can transmit their existence. To other devices, and can learn about new routers, nodes, and LAN segments.
● As previously stated, they route traffic by examining the entire network. It demonstrates that they employ a high level of intelligence in order to complete this assignment. This distinguishes them from hubs and bridges because they only look at the network on a link-by-link basis.
● The destination address, packet priority level, least-cost route, minimum route delay, minimum route distance, and route congestion level are all examples of packets handled by routers.
● Routers continuously monitor the state of the network as a whole in order to dynamically respond to changes in the network's state.
● They usually have some measure of redundancy, making them less prone to catastrophic failure.
Key takeaway
- In a computer network, a hub is used to connect numerous computers or LAN segments. It's usually used for a modest Peer-to-Peer Home Network.
- Bridges are network connection devices that work at the data link layer of the OSI model.
- Bridges, in comparison to Layer 1 devices like repeaters and hubs, have additional connectivity features.
- Switches are networking devices that operate at the OSI model's layer 2 or data link layer.
- They connect network devices and use packet switching to deliver, receive, and forward data packets or data frames across the network.
Network Protocols – TCP/IP, OSI Model
TCP/IP Reference Model is a four-layered suite of communication protocols. It was developed by the DoD (Department of Defence) in the 1960s. It is named after the two main protocols that are used in the model, namely, TCP and IP. TCP stands for Transmission Control Protocol and IP stands for Internet Protocol.
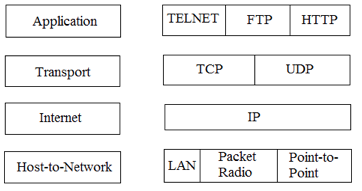
Fig 16: TCP/IP protocol suit
The four layers in the TCP/IP protocol suite are −
Host-to- Network Layer −It is the lowest layer that is concerned with the physical transmission of data. TCP/IP does not specifically define any protocol here but supports all the standard protocols.
Internet Layer −It defines the protocols for logical transmission of data over the network. The main protocol in this layer is Internet Protocol (IP) and it is supported by the protocols ICMP, IGMP, RARP, and ARP.
Transport Layer − It is responsible for error-free end-to-end delivery of data. The protocols defined here are Transmission Control Protocol (TCP) and User Datagram Protocol (UDP).
Application Layer − This is the topmost layer and defines the interface of host programs with the transport layer services. This layer includes all high-level protocols like Telnet, DNS, HTTP, FTP, SMTP, etc.
The advantages of TCP/IP protocol suite are
- It is an industry–standard model that can be effectively deployed in practical networking problems. It is interoperable, i.e., it allows cross-platform communications among heterogeneous networks.
- It is an open protocol suite. It is not owned by any particular institute and so can be used by any individual or organization.
- It is a scalable, client-server architecture. This allows networks to be added without disrupting the current services.
- It assigns an IP address to each computer on the network, thus making each device to be identifiable over the network. It assigns each site a domain name. It provides name and address resolution services.
The disadvantages of the TCP/IP model are
- It is not generic in nature. So, it fails to represent any protocol stack other than the TCP/IP suite. For example, it cannot describe the Bluetooth connection. It does not clearly separate the concepts of services, interfaces, and protocols. So, it is not suitable to describe new technologies in new networks.
- It does not distinguish between the data link and the physical layers, which have very different functionalities. The data link layer should concern with the transmission of frames. On the other hand, the physical layer should lay down the physical characteristics of transmission. A proper model should segregate the two layers.
- It was originally designed and implemented for wide area networks. It is not optimized for small networks like LAN (local area network) and PAN (personal area network). Among its suite of protocols, TCP and IP were carefully designed and well implemented. Some of the other protocols were developed ad hoc and so proved to be unsuitable in the long run. However, due to the popularity of the model, these protocols are being used even 30–40 years after their introduction.
OSI Model
OSI stands for Open System Interconnection is a reference model that describes how information from a software application in one computer moves through a physical medium to the software application in another computer’s consists of seven layers, and each layer performs a particular network function’s model was developed by the International Organization for Standardization (ISO) in 1984, and it is now considered as an architectural model for the inter-computer communications.
The OSI model divides the whole task into seven smaller and manageable tasks. Each layer is assigned a particular task. Each layer is self-contained, so that tasks assigned to each layer can be performed independently.
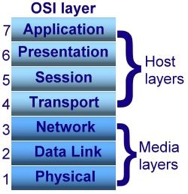
Fig17 : OSI model
The OSI model is divided into two layers: upper layers and lower layers. The upper layer of the OSI model mainly deals with the application related issues, and they are implemented only in the software. The application layer is closest to the end user. Both the end user and the application layer interact with the software applications. An upper layer refers to the layer just above another layer. The lower layer of the OSI model deals with the data transport issues. The data link layer and the physical layer are implemented in hardware and software. The physical layer is the lowest layer of the OSI model and is closest to the physical medium. The physical layer is mainly responsible for placing the information on the physical medium.
There are seven OSI layers.
Each layer has different functions. A list of seven layers are given below:
- Physical Layer: The physical layer is the lowest layer in the OSI reference model. It is in charge of establishing a physical link between the devices. Bits of information are stored in the physical layer. It is in charge of sending individual bits from one node to another. As this layer receives data, it converts the signal received into 0s and 1s and sends them to the Data Link layer, which reassembles the frame.
2. Data-Link Layer : The data link layer is in charge of message transmission from node to node. The main purpose of this layer is to ensure that data transfers from one node to another over the physical layer are error-free. It is DLL's duty to send a packet to the Host using its MAC address when it arrives in a network.
3. Network Layer : The network layer is responsible for data transmission between hosts on different networks. It also handles packet routing, which is the selection of the shortest path to transmit a packet from a large number of options. The network layer places the IP addresses of the sender and receiver in the header.
4. Transport Layer : The application layer receives services from the transport layer, and the network layer receives services from the transport layer. Segments are the units of data in the transport layer. It is in charge of the full message's delivery from beginning to end.
5. Session Layer : This layer is in charge of establishing connections, maintaining sessions, authenticating users, and ensuring security.
6. Presentation Layer : The Translation layer is also known as the Presentation layer. The data from the application layer is extracted and manipulated here so that it can be transmitted over the network in the appropriate format.
7. Application Layer : The Application layer, which is implemented by network applications, is at the very top of the OSI Reference Model stack of layers. These applications generate the data that must be sent over the network. This layer also acts as a window for application services to connect to the network and present the information they receive to the user.
Key takeaway:
- In the present day scenario security of the system is the sole priority of any organization.
- The main aim of any organization is to protect their data from attackers.
- TCP/IP Reference Model is a four-layered suite of communication protocols.
- It is named after the two main protocols that are used in the model, namely, TCP and IP.
- TCP stands for Transmission Control Protocol and IP stands for Internet Protocol.
1.3.1 Definition, Types of connections, sharing internet connection, Hot Spots
The Internet is a worldwide network that connects billions of computers to one another and to the World Wide Web. It connects billions of computer users around the world using the standard internet protocol suite (TCP/IP). It is built up utilizing optical fiber cables as well as other wireless and networking technologies. The internet is currently the fastest method of sending or sharing data and information amongst computers all over the world. The internet is thought to have been created by the US Department of Defense's "Defense Advanced Projects Agency" (DARPA). It was also connected for the first time in 1969.
Fig 18: internet
Advantages
Instant Messaging : You can use the internet to send messages or communicate with others via email, audio chat, video conferencing, and other methods.
Get directions : You can acquire instructions to practically any location in a city, country, or other location using GPS technology. Near your area, you can discover restaurants, shopping malls, and other services.
Online shopping : It allows you to shop online for clothes, shoes, movie tickets, train tickets, and airplane tickets, among other things.
Pay bills : Electricity payments, gas bills, tuition fees, and other obligations can all be paid online.
Entertainment : You can listen to music online, watch films or movies online, and play games online.
Work from home : If you need to work from home, a computer with internet connectivity will suffice. Many businesses now allow their staff to work from home.
Disadvantages
However, while the Internet has shown to be a valuable source of information in practically every sector, there are a number of disadvantages that are addressed below:
● Personal information such as a person's name, address, or credit card number can be lost at any time. As a result, extreme caution should be exercised when disclosing such information. Credit cards should only be used on secure websites.
● Spamming is another downside.
● Spamming refers to the mass distribution of undesired emails. These emails are pointless and cause the entire system to become clogged.
● Viruses can readily infect machines connected to the internet. Such malware attacks may cause your computer to crash or erase crucial data.
Types of Connections
There are several different forms of networking connections between two endpoints. One of the most popular examples is home networks and the Internet. Many different types of devices and approaches are used to bind to these types of network architectures.
Connecting computers to these types of networks necessitates the use of a networking system to do so. Point-to-Point Connection and Multipoint Connection are the two types of computer network connections discussed on this page.
- Point-to-point connection: A direct link between two devices, such as a computer and a printer, is known as a point-to-point connection. The devices are connected through a dedicated connection. The transmission between those two devices consumes the entire link's power. Modems and PSTN (Public Switched Telephone Network) communications are responsible for the majority of today's point-to-point connections. There are numerous links between individual pairs of machines in point-to-point networks.
A packet (short message) will take a variety of routes to get from point A to point B. PPP (Point-to-Point Protocol) is a data link protocol that is widely used in networking to create a direct connection between two networking nodes. It has the ability to authenticate connections, encrypt transmissions, and compress data. Serial cable, phone line, trunk line, cellular telephone, advanced radio communications, and fiber optic links such as SONET are all examples of physical networks where PPP is used. PPP is often used to link to the Internet.
2. Multipoint connection: A multipoint connection is a connection that connects three or more devices together. Multi-drop configuration is another name for it. Broadcast Networks are networks that have a multipoint architecture.
A message or packet transmitted by any machine in a broadcast network is received by all other machines in the network. The address field in the packet determines the recipient. Any computer checks the packet's address field when it receives it. It processes the transmitted packet if it is for that specific machine; otherwise, it ignores it.
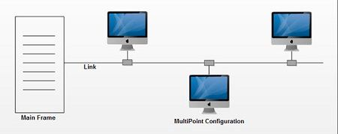
Fig 19: multipoint connection
Sharing internet connections
The Internet Connection Sharing (ICS) feature allows a device with Internet connectivity to act as a host or access point for other devices to connect to the Internet.
Microsoft and Windows 7 make connecting to the Internet and sharing an Internet connection with other computers in your network simple. You can make advantage of the advantage of this method of Internet sharing is that it does not require the use of a router; nevertheless, the host device (computer) must be turned on in order for other computers to connect to the Internet.
To use the Windows 7 Internet Connection Sharing function, follow these steps:
- Choose Start→Control Panel→Network and Internet. Click the Network and Sharing Center link.
The Network and Sharing Center opens.
2. In the resulting Network and Sharing Center window, click the Manage Wireless Network’s link.
The window that appears lets you “Manage Wireless Networks That Use (Wireless Network Connect).”
3. Click a connection and then click the Adapter Properties link.
The Connection Properties dialog box appears.
4. Click the Sharing tab.
This tab doesn’t give you a whole lot of options.
5. Select the Allow Other Network Users to Connect through This Computer’s Internet Connection check box.
Allow Other Network Users to Control or Disable the Shared Internet Connection check box may also be available (Optional). Other people on your network can use this feature to enable or disable the shared Internet connection.
6. Click OK and then close the Manage Wireless Networks window to save the shared connection settings.
Users on your network must first set up their TCP/IP settings so that they receive an IP connection automatically before they can utilize your shared connection.
Hotspots
A hotspot is a specific location where you can connect to the Internet via a wireless local area network (WLAN). The term is usually used to refer to a Wi-Fi connection. A modem and wireless router are the most important components of a hotspot network. The wireless network's radio frequency (RF) waves travel in all directions from its main location. As these signals travel further away from the central site or due to interference, they get weaker.
Types of hotspot
There are two types of hotspots:
Free WiFi hotspot – This is essentially a Wi-Fi router without the need for a password, allowing all users in range to connect to the Internet using the same network.
Commercial hotspot – For a price, these access points give wireless coverage. When connecting to the Internet via a commercial hotspot, the user is frequently led to a screen that requests login information or payment information.
Millions of Internet users benefit from hotspots, yet they are riddled with security risks. Hackers and identity thieves frequently target free public hotspots, for example. The attackers build rogue or phony hotspots that appear exactly like real ones. If consumers connect to these rogue access points inadvertently and use their personal data for login or other purposes, the attackers can simply retrieve the sensitive data using several tactics.
Key takeaway:
- A direct link between two devices, such as a computer and a printer, is known as a point-to-point connection.
- The devices are connected through a dedicated connection.
- A multipoint connection is a connection that connects three or more devices together.
Services on net- WWW, Email-Blogs
World Wide Web, which is also known as a Web, is a collection of websites or web pages stored in web servers and connected to local computers through the internet. These websites contain text pages, digital images, audios, videos, etc. Users can access the content of these sites from any part of the world over the internet using their devices such as computers, laptops, cell phones, etc. The WWW, along with the internet, enables the retrieval and display of text and media to your device.

Fig 20: WWW
The building blocks of the Web are web pages which are formatted in HTML and connected by links called "hypertext" or hyperlinks and accessed by HTTP. These links are electronic connections that link related pieces of information so that users can access the desired information quickly. Hypertext offers the advantage to select a word or phrase from text and thus to access other pages that provide additional information related to that word or phrase.
A web page is given an online address called a Uniform Resource Locator (URL). A particular collection of web pages that belong to a specific URL is called a website, e.g., www.facebook.com, www.google.com, etc. So, the World Wide Web is like a huge electronic book whose pages are stored on multiple servers across the world.
Small websites store all of their WebPages on a single server, but big websites or organizations place their WebPages on different servers in different countries so that when users of a country search their site they can get the information quickly from the nearest server.
So, the web provides a communication platform for users to retrieve and exchange information over the internet. Unlike a book, where we move from one page to another in a sequence, on the World Wide Web we follow a web of hypertext links to visit a web page and from that web page to move to other web pages. You need a browser, which is installed on your computer, to access the Web.
Difference between World Wide Web and Internet:
Some people use the terms 'internet' and 'World Wide Web' interchangeably. They think they are the same thing, but it is not so. The Internet is entirely different from WWW. It is a worldwide network of devices like computers, laptops, tablets, etc. It enables users to send emails to other users and chat with them online. For example, when you send an email or chat with someone online, you are using the internet.
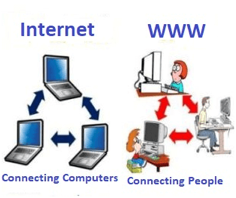
Fig 21: Internet and WWW
But, when you have opened a website like google.com for information, you are using the World Wide Web; a network of servers over the internet. You request a webpage from your computer using a browser, and the server renders that page to your browser. Your computer is called a client who runs a program (web browser), and asks the other computer (server) for the information it needs.
Email – blog
Electronic Mail (e-mail) is one of most widely used services on the Internet. This service allows an Internet user to send a message in formatted manner (mail) to the other Internet user in any part of the world. Messages in mail not only contain text, but it also contains images, audio and videos data. The person who is sending mail is called the sender and the person who receives mail is called the recipient. It is just like postal mail service.
Components of E-Mail System
The basic components of an email system are : User Agent (UA), Message Transfer Agent (MTA), Mail Box, and Spool file.
- User Agent (UA) :
The UA is normally a program which is used to send and receive mail. Sometimes, it is called a mail reader. It accepts a variety of commands for composing, receiving and replying to messages as well as for manipulation of the mailboxes.
2. Message Transfer Agent (MTA) :
MTA is actually responsible for transfer of mail from one system to another. To send mail, a system must have a client MTA and a system MTA. It transfers mail to the mailboxes of recipients if they are connected in the same machine. It delivers mail to the peer MTA if the destination mailbox is in another machine.
3. Mailbox :
It is a file on a local hard drive to collect mails. Delivered mails are present in this file. The user can read it and delete it according to his/her requirement. To use the e-mail system each user must have a mailbox . Access to mailboxes is only to the owner of the mailbox.
4. Spool file :
This file contains mails that are to be sent. User agent appends outgoing mails in this file using SMTP. MTA extracts pending mail from a spool file for their delivery. E-mail allows one name, an alias, to represent several different email addresses. It is known as a mailing list. Whenever a user has to send a message, the system checks the recipient's name against the alias database. If a mailing list is present for a defined alias, separate messages, one for each entry in the list, must be prepared and handed to MTA. If for a defined alias, there is no such mailing list present, the name itself becomes the naming address and a single message is delivered to the mail transfer entity.
Key takeaway:
- World Wide Web, which is also known as a Web, is a collection of websites or web pages stored in web servers and connected to local computers through the internet.
- A web page is given an online address called a Uniform Resource Locator (URL).
- Electronic Mail (e-mail) is one of most widely used services on the Internet. This service allows an Internet user to send a message in formatted manner (mail) to the other Internet user in any part of the world.
IP addresses, Domain names, URLs, Hyperlinks, Web Browsers
The internet protocol address (IP address) is a numerical identifier that is connected with a certain computer or computer network. When computers are connected to the internet, the IP address allows them to send and receive data.
Computers use IP addresses to send and receive data over the internet. The majority of IP addresses are numerical, however as internet usage grows, certain addresses have letters appended to them.
IP addresses are divided into four categories: public, private, static, and dynamic. While public and private imply network location (private being used within a network and public being utilized outside of a network), static and dynamic represent network permanency.
A static IP address is one that was created manually rather than being assigned. A static IP address is likewise permanent, but a dynamic IP address is assigned by a Dynamic Host Configuration Protocol (DHCP) server and can change. The most prevalent type of internet protocol address is dynamic IP addresses. Dynamic IP addresses are only valid for a certain period of time before they expire. Either the computer will automatically request a new lease or it will be assigned a new IP address.
Domain names
The Domain Name System (DNS) is a hierarchical decentralized naming system for computers, services, or other resources connected to the Internet or a private network. It associates various information with domain names assigned to each of the participating entities.
Currently, the limit on domain name length is 63 characters, including www. And .com or other extensions. Domain names are also restricted to only a subset of ASCII characters, making many other languages unable to properly represent their names and words. Punycode-based IDNA systems, which map Unicode strings to valid DNS character sets, have been validated and adopted by some registries as a workaround.
A protocol that can be used on various platforms is DNS. The domain name space (tree) is split into three separate parts on the Internet: generic domains, country domains, and the inverse domain.
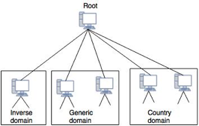
Fig 22: DNS in internet
Generic Domains
Based on their generic behaviour, the generic domains identify registered hosts. A domain, which is an index to the domain name space database, is specified by each node in the tree.
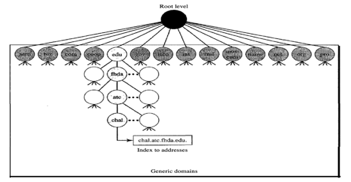
Fig 23: Generic domain
Looking at the tree, we see that 14 possible labels are allowed by the first level in the generic domains segment.
Label | Description |
Aero | Airlines and aerospace companies |
Biz | Business or firms |
Com | Commercial organizations |
Coop | Cooperative business organization |
Edu | Educational institutions |
Gov | Government institutions |
Info | Information service provider |
Int | International organizations |
Mil | Military groups |
Museum | Museum and other nonprofit organization |
Name | Personal name |
Net | Network support centers |
Org | Nonprofit organizations |
Pro | Professional individual organizations |
Country Domains
The segment on country domains utilises two-character country abbreviations (e.g., us for United States). The second labels may be organisational, or national designations may be more precise.
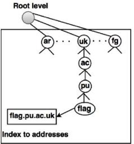
Fig 24: country domain
For instance, the country domain is "au" for Australia, India is .in, and the UK is .uk
Inverse domains
For mapping an address to a name, the inverse domain is used. This can happen when a server has received a request from a client to do a task for testing. Although the server has a file containing a list of approved clients, only the client's IP address (extracted from the IP packet received) is identified. The server prompts its resolver to send a question to the DNS server to map a name to an address to decide if the client is on the approved list.
A reverse or pointer (PTR) query is called this type of query. The inverse domain is added to the domain name space with a first-level node named arpa to handle a pointer query (for historical reasons). One single node called in-addr is also the second stage (for inverse address). IP addresses are specified in the rest of the domain.
Also, the servers managing the inverse domain are hierarchical.
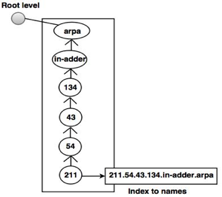
Fig 25: inverse domain
For example, when a client sends a request to a server to perform a specific task, the server finds an approved client list. The list includes only the client's IP addresses.
URLs
URL, or Uniform Resource Locator, is the address of a web resource or a locally stored file. A Web page, a text file, a graphics file, or an application program are all examples of resources kept on a server. The address has three parts: the type of protocol used to access the file (e.g., HTTP for a Web page, ftp for an FTP site); the domain name or IP address of the server where the file is stored; and, optionally, the pathname to the file (i.e., a description of the file's location).
Every URL contains the following information:
● The scheme name or protocol.
● A colon, two slashes.
● A host, normally called a domain name but sometimes as a literal IP address.
● A colon followed by a port number.
● Full path of the resource.
Hyperlinks
By clicking on text or an image, you can go somewhere else on the Web, within a document or collection of documents, or launch something, such as a movie clip. Hyperlinks are an important aspect of Web browsing because they allow users to swiftly and simply go from one area of interest to another.
Underlined text (typically in blue), graphics, drop-down menus, animations, and so on are all examples of hyperlinks. Hyperlinks can be included in a variety of electronic documents, such as a Microsoft Word document, a PDF file, or an email, in addition to being embedded in Web pages.
Hyperlinks are essential components of bigger hypertext systems that arrange various sorts of data. The ability to explore these links fluidly is crucial. Consider how helpful it would be if you had a knowledgeable librarian guiding you through your research.
The World Wide Web is an Internet-based collection of hyperlinked documents, content, and media. Web browsers, the programs we use to search the Internet, were created to take use of hyperlinks and make their use as simple as possible. HTML is the hypertext markup language that is used to create web pages. For all of this to work, the Internet supplies the underlying structure (or network).
Hypertext hyperlinks can be bidirectional in some cases: they can be followed in both directions, acting as anchors and targets on both ends. Many-to-many links, for example, are more sophisticated structures.
Web browsers
A web browser is a piece of software that allows us to browse the internet and view and explore information. By simply typing a URL into the address box, a user can request any web page.
Text, audio, video, animation, and other media can be shown in a web browser. A web browser's job is to interpret the content and commands on a web page.
Web browsers used to be text-based, but today graphical-based or voice-based browsers are now available.
The most popular web browsers currently are as follows:
Browser | Vendor |
Internet Explorer | Microsoft |
Google Chrome | |
Mozilla Firefox | Mozilla |
Netscape Navigator | Netscape Communications Corp. |
Opera | Opera Software |
Safari | Apple |
Sea Monkey | Mozilla Foundation |
K-meleon | K-meleon |
Features of web browser
The majority of web browsers have capabilities such as:
● Refresh button : The refresh button allows the website to reload the web pages' contents. Most web browsers use a caching technique to save local copies of visited pages to improve performance. Sometimes it prevents you from viewing the most recent information; in this situation, you can see the most recent information by using the refresh button.
● Stop button : It's used to block the web browser from communicating with the server and from loading the page's content. For example, if a dangerous site is unintentionally entered into the browser, it is possible to save yourself by pressing the stop button.
● Home button : It gives customers the option of going to the website's pre-defined home page.
● Web address bar : It allows users to view a website by typing a web address into the address bar.
● Tabbed browsing : It allows users to open many websites in a single browser window. It enables users to read many webpages at once. When you search for something in the browser, for example, it returns a list of search results for your query. By right-clicking on each link and staying on the same page, you can open all of the results.
● Bookmarks : It allows users to bookmark a certain website for subsequent retrieval of information that has been pre-defined by the users.
Key takeaway
- Computers can send and receive data using an internet protocol (IP) address.
- IP addresses are divided into four categories: public, private, static, and dynamic.
- Because IP addresses allow information to be delivered and received to the appropriate parties, they can also be used to track down a user's physical location.
- DNS is a directory service that maps a host's name to its numerical address on a network.
- DNS is necessary for the internet to work.
- Based on their generic behaviour, the generic domains identify registered hosts.
Searching Directories, Search engines, Boolean search (AND, OR, NOT), Advanced search, Meta Search Engines
A search directory is a categorized online index of websites, similar to the yellow pages in a phone book. Search directories are populated through application and approval processes, unlike search engines, which utilize web crawlers to visit websites and collect data for indexing.
A well-known example of a search directory is the Open Directory Project (DMOZ), which is maintained by a vast global network of volunteer editors.
Importance
Search engine optimization (SEO) encompasses all of the techniques that a website can use to boost its ranking in the organic (non-paid) section of search engine results pages (SERPs). The ultimate goal is to appear on the first page of search results, preferably near the top. When was the last time you looked past the first page of Google search results?
On-page and off-page SEO methods are sometimes separated into two groups. Only the latter will be discussed for our purposes. Off-page SEO entails working on your website's performance from outside of it. Although off-page SEO can be divided down into numerous tactics, there is only one fundamental goal: to gain connections from other websites to your own. Every time you receive a link from a third-party source, you increase your Domain Authority, which is a major component in organic search results.
Search Engines
A search engine is a large database of online resources including web pages, newsgroups, programs, and images, among other things. It aids in the search for information on the World Wide Web.
Any information can be found by entering a query in the form of keywords or phrases. It then searches its database for relevant information before returning to the user.
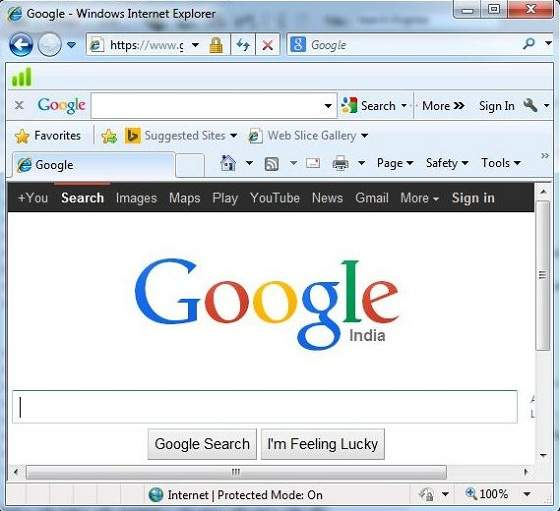
Fig 26: search engines
Search Engine Components
In general, a search engine has three basic components, which are listed below:
- Web crawler – It's also called a spider or a bot. It's a piece of software that collects data from the internet.
2. Database – All of the material on the internet is saved in a database. It is made up of a large number of web resources.
3. Search interface – This component serves as a user-to-database interface. It assists the user in searching the database.
Example
Search Engine | Description |
It was originally called BackRub. It is the most popular search engine globally. | |
Bing | It was launched in 2009 by Microsoft. It is the latest web-based search engine that also delivers Yahoo’s results. |
Ask | It was launched in 1996 and was originally known as Ask Jeeves. It includes support for match, dictionary, and conversation questions. |
AltaVista | It was launched by Digital Equipment Corporation in 1995. Since 2003, it is powered by Yahoo technology. |
AOL.Search | It is powered by Google. |
LYCOS | It is a top 5 internet portal and 13th largest online property according to Media Matrix. |
Alexa | It is a subsidiary of Amazon and used for providing website traffic information. |
Boolean Search (AND, OR, NOT)
A Boolean search is a query strategy that connects individual keywords or phrases within a single query using Boolean Logic. The term "Boolean" refers to a logic system created by George Boole, a mathematician and early computer pioneer. AND, OR, and NOT are the three main Boolean operators used in Boolean searching.
Boolean search is a sort of search that lets users combine keywords with operators (or modifiers) like AND, NOT, and OR to get more relevant results. A Boolean search might be "hotel" AND "New York," for example. This would narrow down the search results to documents that contained both keywords.
AND – Your search is narrowed by using the AND operator. When you use two keywords together, it will look for posts that contain both of them. The Boolean search “Cats AND Dogs,” for example, will return any postings that contain both words. Within NodeXL, the absence of an operator between words is treated as an AND operator. For example, "Cats Dogs" and "Cats AND Dogs" are treated the same.
OR – The OR operator broadens the scope of your search. Any posts that contain at least one of the search terms will be returned using the OR operator. The Boolean search “Cats OR Dogs,” for example, will return entries that contain either term.
NOT – A NOT operator filters out posts that include the term. The NOT operator will filter out any postings that contain the keyword that follows the operator. For example, the Boolean search "Cats NOT Dogs" will return all posts that contain the term "Cats" unless they also contain the word "Dogs." Within Boolean queries, Twitter additionally understands the minus symbol () as a NOT operator (for example, “Cats -Dogs”). When collecting data using NodeXL, the “-” operator should be used instead of the term NOT.
Advanced Search
Most search engines on the internet have advanced search options, which are a set of filters. They assist you find the exact stuff you're looking for by narrowing the scope of a search query to eliminate extraneous information.
Web search engines like Google aren't the only ones with advanced search filters. Advanced search options can be added to any website that has a search function, such as people search engines, music and video streaming services, social media websites, reference sites, and blogs.
How to use advanced search options
Because different search engines employ different algorithms and operators, an advanced search feature from one site is unlikely to work on another. Furthermore, accessing a website's sophisticated search options isn't always straightforward.
For a list of sophisticated Google search operators, see our Google Cheat Sheet. Google's advanced search can be found at google.com/advanced search.
Bing is yet another search engine that offers a variety of advanced search possibilities. Bing search tips include how to search by IP address, find RSS feeds, and more.
Fig 27: example
Meta Search Engine
The Metasearch Engine is a search engine that aggregates the results of several different search engines into a single result. It's also known as an internet information search engine.
Individual search engines were prone to spam owing to people attempting to boost their website rankings online, so the Metasearch Engine was created. The search engine searches a number of different websites and compiles a database of them. Indexing is another term for this. Every second, any search engine responds to many searches.
Most other search engines are queried by metasearch engines, which then reflect the results in the form of summaries of such sites.
Example of meta search engine
● InfoSpace LLC created Dogpile, a metasearch engine. It returns results from Google and Yahoo's individual search engines. It combines text, image, new, and other search results.
● Sputtr is a meta search engine that integrates results from Google, Yahoo, Bing, Ask.com, Twitter, Facebook, YouTube, LinkedIn, IMDb, Slashdot, Dictionary.com, About.com, New York Times, and other major search engines.
● Trivago, a hotel booking site that emphasizes this principle in its marketing, is another famous site. Booking.com, Airbnb, Expedia, Trip.com, and Agoda are just a few of the numerous hotel booking sites that it returns results from. Trivago can be visited at www.trivago.com.
Advantages
● Individual searches are unneeded because the meta search engine looks for all search engines at once.
● It's a really user-friendly toolbar that's simple to install.
● The metasearch engine allows you to look up the white pages and yellow pages.
● The metasearch engine is available for free. Its features are comparable to those of other search engines.
● The metasearch engine can be customized according to the requirements of the users.
● The results include coverage data that is more detailed than individual site results.
Disadvantages
● Parsing is not a feature of the meta search engine.
● It is not as well-known as other search engines such as Google and Yahoo.
● The query syntax is not properly translated by the meta search engine.
● Its trustworthiness is on par with that of other search engines.
● They frequently place a higher value on pay-per-click links than on more relevant search results.
● Typically, the results include up to 10 links from a single site, leaving out key links from major sites.
● Because the amount of hyperlinks available is limited, the search query results are incomplete.
Key takeaway
- A search directory is a categorized online index of websites, similar to the yellow pages in a phone book.
- A search engine is a large database of online resources including web pages, newsgroups, programs, and images, among other things.
- A Boolean search is a query strategy that connects individual keywords or phrases within a single query using Boolean Logic.
- The term "Boolean" refers to a logic system created by George Boole, a mathematician and early computer pioneer.
- The Metasearch Engine is a search engine that aggregates the results of several different search engines into a single result.
Email – POP/SMTP accounts in Email, Different parts of an Email address. Receiving and sending emails with attachments by scanning attachments for viruses
Post Office Protocol (POP) is an acronym for Post Office Protocol. SMTP is a message transfer agent, as we all know. SMTP is used to convey the message from the client to the server, and then to the recipient server, when it is sent. However, the Message Access Agent is used to send the message from the receiver server to the actual server. POP3 and IMAP are the two types of protocols supported by the Message Access Agent.
It's a location where multiple devices can share a connection and communicate with one another. It is a man-made demarcation point (a point where a company's public network ends and the customer's private network begins, such as the point where your broadband cable enters the house) between communicating entities. It is made up of high-speed telecommunications equipment and technology that help bring individuals from all across the internet together.
Characteristics of POP
● Internet RFCs specify the Post Office Protocol, which is an open protocol.
● It allows new mail to be accessed from a variety of client platforms.
● It allows you to download and delete files even while you're not connected to the internet.
● Because of its original nature, it does not require any mail gateways.
● POP can only manage email access while SMTP is used to send the emails.
SMTP
Simple Mail Transfer Protocol (SMTP) is an acronym for Simple Mail Transfer Protocol. It's a TCP/IP protocol for exchanging electronic mail between computers. It adheres to postal protocol (POP).
SMTP is used to send mail straight from a client to an intermediary host, but it can only receive mail from computers that are constantly connected to the Internet, such as Internet Service Providers (ISPs). The mail is subsequently offloaded to the users to whom the ISP provides Internet access.
For this service, SMTP uses TCP port 25. As a result, e-mail is transmitted from source to destination by using a TCP connection from the source machine to port 25 on the destination machine.
A system must have a client MTA to send mail, and a system must have a server MTA to receive mail. This message is sent from the client MTA to the server MTA through SMTP. The message is transferred between an MTA client and an MTA server using SMTP commands and responses. SMTP is used twice while sending an email: once between the sender and the sender's mail server, and again between the two mail servers.
Each command or response has two characters at the conclusion (CR and LF) Carriage Return is abbreviated as CR, and Line Feed is abbreviated as LF.
The Windows NT Resource Kit and the Windows NT Option Pack 4 both provide an SMTP mail client. Your LAN mail will be routed on and off the Internet using Microsoft Exchange Server.
Different parts of an Email address
The User Agent (UA), Message Transfer Agent (MTA), Mail Box, and Spool file are the four main components of an email system. These are explained in the next paragraphs.
User Agents (UA)
The UA is typically a program that sends and receives mail. It is also known as a mail reader. It supports a wide range of instructions for sending, receiving, and replying to messages, as well as manipulating mailboxes.
Message Transfer Agent (MTA)
MTA is in charge of transferring mail from one system to another. A system must have both a client MTA and a system MTA in order to send email. If the recipients are connected to the same machine, it sends mail to their mailboxes. If the destination mailbox is on another machine, it sends mail to a peer MTA.
Mailboxes
It's a local hard drive file that collects emails. This file contains delivered emails. The user can read it or remove it depending on his or her needs. Each user must have a mailbox in order to utilize the e-mail system. Only the mailbox owner has access to the mailbox.
Spool file
This file contains all of the emails that need to be sent. SMTP is used by the user agent to attach outgoing email to this file. For delivery, MTA pulls pending mail from the spool file. In email, a single name, known as an alias, can be used to represent many email addresses. Whenever a user needs to send a message, the system validates the recipient's name against the alias database. If a mailing list is present for a defined alias, separate messages must be produced and handed to MTA, one for each entry in the list. If no mailing list exists for the provided alias, the name becomes the naming address, and a single message is delivered to the mail transfer entity.
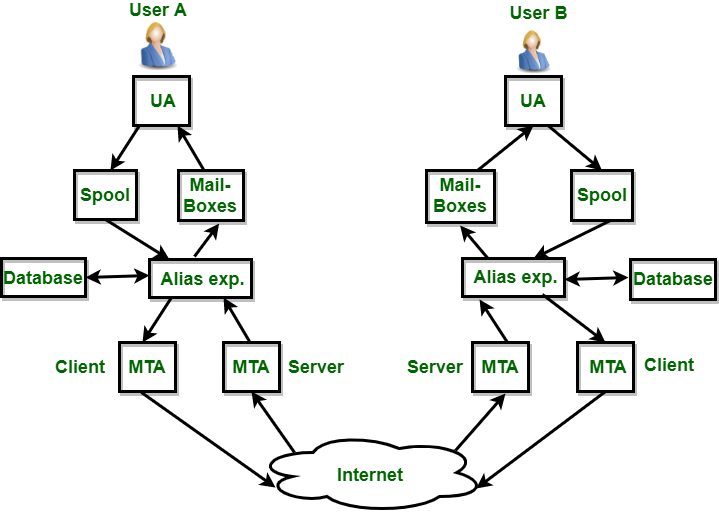
Fig 28: parts of email
Key takeaway
- Post Office Protocol (POP) is an acronym for Post Office Protocol. SMTP is a message transfer agent, as we all know.
- Simple Mail Transfer Protocol (SMTP) is an acronym for Simple Mail Transfer Protocol.
- It's a TCP/IP protocol for exchanging electronic mail between computers.
Cyber Crime, Hacking, Sniffing, Spoofing
Cybercrime, often known as computer-oriented crime, is a type of crime that involves the use of a computer and a network. It's possible that the computer was utilized in the commission of a crime or that it was the intended target.
The use of a computer as a weapon for crimes such as fraud, identity theft, and privacy invasion is known as cyber crime. As the computer has become vital to every industry such as commerce, entertainment, and government, cyber crime, particularly through the Internet, has expanded in prominence. Cybercrime can jeopardize a person's or a country's security and financial well-being.
Cybercrime encompasses a wide range of actions, however they can be categorized into two groups:
- Computer network or device-related crimes. Different threats (such as viruses, bugs, and so on) and denial-of-service (DoS) attacks are used in these types of crimes.
2. Crimes committed through the use of computer networks for the purpose of committing other crimes. Cyber stalking, money fraud, and identity theft are examples of these types of crimes.
Classification of cyber crime
- Cyber Terrorism
The use of a computer and the internet to commit violent acts that end in death is known as cyber terrorism. This could entail a variety of operations carried out by software or hardware in order to endanger civilians' lives.
In general, cyber terrorism is described as a terrorist act carried out through cyberspace or computer resources.
2. Cyber Extortion
When a website, e-mail server, or computer system is subjected to or threatened with repeated denial of service or other attacks by malevolent hackers, this is known as cyber extortion. These hackers want a large sum of money in exchange for assurances that the assaults will be stopped and that they will be protected.
3. Cyber Warfare
The use or targeting of computers, online control systems, and networks in a battle area or warfare setting is known as cyber warfare. It includes offensive and defensive actions in response to cyber threats, espionage, and sabotage.
4. Internet Fraud
Internet fraud is a type of deception or fraud that uses the Internet to deceive individuals for money or property. It might include withholding information or delivering inaccurate information. Internet fraud is not a unique, distinct crime; rather, it encompasses a wide range of illegal and illicit activities carried out in cyberspace.
5. Cyber Stalking
This is an example of internet harassment in which the victim is bombarded with texts and emails. In this situation, the stalkers are familiar with their victims and, rather than stalking them offline, they use the Internet to do so. If they realize that internet stalking isn't having the desired effect, they'll combine it with offline stalking to make the victims' life even more difficult.
Hacking
Hacking is the act of detecting and exploiting security flaws in a computer system or network in order to obtain access to personal or company data. Using a password cracking technique to obtain access to a computer system is one example of computer hacking.
Computers have become a must for operating a successful business. It is not enough to have separate computer systems; they must be networked in order to communicate with outside firms. This makes them vulnerable to hacking and the outside world. System hacking is defined as the use of computers to commit fraudulent acts such as fraud, invasion of privacy, theft of corporate/personal data, and so on. Cyber crimes cost many organizations millions of dollars every year. Businesses need to protect themselves against such attacks.
Types of Hackers
Hackers are categorized based on the purpose of their actions. The following is a list of different sorts of hackers and how they are classified based on their intentions:
Ethical Hacker (White hat): A security hacker who gains access to systems in order to remedy the flaws that have been discovered. Penetration testing and vulnerability assessments may also be performed by them.
Cracker (Black hat): For personal gain, a hacker who gains unauthorized access to computer systems. Typically, the goal is to steal company data, violate privacy rights, and move money from bank accounts, among other things.
Grey hat: A hacker who falls somewhere in the middle of ethical and black hat hackers. He or she enters computer systems without authorization in order to find flaws and reveal them to the system owner.
Script kiddies: A non-skilled person who uses pre-made tools to gain access to computer systems.
Hacktivist: A hacker who uses hacking to send messages about social, religious, and political issues, among other things. This is usually accomplished by hijacking websites and posting the message there.
Phreaker: A hacker who targets and exploits flaws in telephones rather than computers.
Sniffing
Sniffing is the technique of continuously monitoring and recording all data packets that transit via a network. Network/system administrators employ sniffers to monitor and troubleshoot network traffic. Sniffers are used by attackers to capture data packets containing sensitive data such as passwords and account information. Sniffers can be installed as hardware or software in the system. A hostile intruder can gather and analyze all network traffic by using a packet sniffer in promiscuous mode on a network.
Types of sniffing
- Active sniffing
Active sniffing is sniffing in the switch. A switch is a network device that connects two points. The switch controls the flow of data between its ports by continuously checking the MAC address on each port, ensuring that data is only sent to the correct destination. To collect communication between targets, sniffers must actively inject traffic into the LAN to enable traffic sniffing. This can be accomplished in a variety of ways.
2. Passive sniffing
This is how you scent your way through the hub. All machines on the segment can observe any traffic that passes across the non-switched or unbridged network segment. Sniffers work at the network's data connection layer. Any data sent over the LAN is sent to each and every machine connected to the network. The term "passive" refers to sniffers that are placed by attackers and passively wait for data to be delivered before capturing it.
Spoofing
Spoofing is the act of misrepresenting an unknown source's message as coming from a known, trusted source. Spoofing can be as simple as a computer impersonating an IP address, Address Resolution Protocol (ARP), or Domain Name System (DNS) server, or as complex as a computer spoofing an IP address, ARP, or DNS server.
Spoofing can be used to acquire access to a target's personal information, to spread malware via infected links or attachments, to circumvent network access rules, or to redistribute traffic in order to launch a denial-of-service attack. Spoofing is a common approach for a bad actor to get access to a system in order to carry out a wider cyber attack like an advanced persistent threat or a man-in-the-middle attack.
Successful attacks on corporations can result in infected computer systems and networks, data breaches, and/or revenue loss, all of which can harm the company's public image. Furthermore, spoofing that causes internet traffic to be rerouted can cause networks to become overburdened or send customers/clients to dangerous websites that steal information or distribute malware.
Types of spoofing
● Email spoofing
When an attacker uses an email message to deceive a recipient into thinking it came from a known and/or trusted source, this is known as email spoofing. These emails could contain harmful links or malware-infected attachments, or they could use social engineering to persuade the receiver to freely divulge important information.
● Caller ID spoofing
Attackers can use caller ID spoofing to make it look as if their phone calls are originating from a specific number—either one that the recipient knows and/or trusts, or one that signals a specific geographic location. Attackers can then employ social engineering to persuade their targets to reveal personal information such as passwords, account information, social security numbers, and more over the phone, sometimes impersonating someone from a bank or customer service.
● Website spoofing
When a website is built to imitate an existing site that the user is familiar with and/or trusts, it is referred to as website spoofing. Attackers utilize these sites to steal users' login credentials and other sensitive information.
● IP spoofing
Attackers may employ IP (Internet Protocol) spoofing to hide the sender's identity or impersonate another computer system by masking a computer's IP address.
● DNS server spoofing
Domain Name System (DNS) servers convert URLs and email addresses to IP addresses. DNS spoofing enables attackers to redirect traffic to a new IP address, directing users to malicious websites. One goal of IP address spoofing is to obtain access to networks that utilize IP addresses to authenticate users.
In most cases, however, attackers will impersonate a target's IP address in order to flood the victim with traffic in a denial-of-service assault. When packet recipients transmit a response, they are routed to the target's faked IP address, and the attacker will send packets to many network recipients.
● ARP spoofing
The Address Resolution Protocol (ARP) is a data-transmission protocol that converts IP addresses to Media Access Control (MAC) addresses. ARP spoofing links an attacker's MAC address to a genuine network IP address, allowing the attacker to receive data intended for the owner of that IP address. ARP spoofing is frequently used to steal or manipulate data, but it can also be used in denial-of-service, man-in-the-middle, and session hijacking attacks.
Key takeaway
- Cybercrime, often known as computer-oriented crime, is a type of crime that involves the use of a computer and a network.
- Hacking is the act of detecting and exploiting security flaws in a computer system or network in order to obtain access to personal or company data.
- Sniffing is the technique of continuously monitoring and recording all data packets that transit via a network.
- Network/system administrators employ sniffers to monitor and troubleshoot network traffic.
- Spoofing is the act of misrepresenting an unknown source's message as coming from a known, trusted source.
- Spoofing can be as simple as a computer impersonating an IP address, Address Resolution Protocol (ARP), or Domain Name System (DNS) server, or as complex as a computer spoofing an IP address, ARP, or DNS server.
References :
- Forouzan, "Data Communication and Networking", TMH
- A.S. Tanenbaum, Computer Networks, Pearson Education
- W. Stallings, Data and Computer Communication, Macmillan Press
- Bhavneet Sidhu, An Integrated approach to Computer Networks, Khanna Publishing House
- Https://ecomputernotes.com/