UNIT – 2
Microprocessor Architecture – 2
In the protected-mode, memory larger than 1 MB can be accessed. Windows XP operates in the protected mode. In addition, segments can be of variable size. Some system control instructions are only valid in the protected mode. In protected mode, the base: offset logical memory addressing scheme (which is used in real mode) is changed.
The offset part of the logical memory address is still used. However, when in the protected mode, the processor can work either with 16-bit offsets (the 16-bit instruction mode) or with 32- bit offsets (the 32-bit instruction mode). A 32-bit offset allows segments of up to 4G bytes in length. Notice that in real-mode the only available instruction mode is the 16-bit mode (during which accessing 32-bit registers requires the prefix 66h).
However, the segment base address calculation is different in protected mode. Instead of appending a 0 at the end of the segment register contents to create a segment base address (which gives a 20-bit physical address), the segment register contains a selector that selects a descriptor from a descriptor table. The descriptor describes the memory segment's location, length, and access rights. This is similar to selecting one card from a deck of cards in one's pocket.
Because the segment register and offset address still create a logical memory address, protected mode instructions are the same as real mode instructions. In fact, most programs written to function in the real mode will function without change in the protected mode.
DESCRIPTORS:
The selector, located in the segment register, selects one of 8192 descriptors from one of two tables of descriptors (stored in memory): the global and local descriptor tables. The descriptor describes the location, length and access rights of the memory segment.
Each descriptor is 8 bytes long and its format is shown below: The 8192-descriptor table requires 8 * 8192 = 64K bytes of memory. The main parts of a descriptor are: Base (B31 – B0): indicates the starting location (base address) of the memory segment. This allows segments to begin at any location in the processor's 4G bytes of memory.
Limit (L19 – L0): contains the last offset address found in a segment. Since this field is 20 bits, the segment size could be anywhere between 1 and 1M bytes. However, if the G bit (granularity bit) is set, the value of the limit is multiplied by 4K bytes (i.e., appended with FFFH). In this 4K bytes. case, the segment size could be anywhere between 4K and 4G bytes in steps of Example, Base = Start = 10000000h Limit = 001FFh and G = 0 So, End = Base + Limit = 10000000h + 001FFh = 100001FFh Segment Size = 512 bytes Base = Start = 10000000h Limit = 001FFh and G = 1 So, End = Base + Limit * 4K = 10000000h + 001FFFFFh = 101FFFFFh Segment Size = 2M bytes
AV bit: is used by some operating systems to indicate that the segment is available (AV = 1) or not available (AV = 0).
D bit: If D = 0, the instructions are 16-bit instructions, compatible with the 8086-80286 microprocessors. This means that the instructions use 16-bit offset addresses and 16-bit registers by default. This mode is the 16-bit instruction mode or DOS mode. If D = 1, the instructions are 32-bits by default (Windows XP works in this mode). By default, the 32-bit instruction mode assumes that all offset addresses and all registers are 32 bits. Note that the default for register size and offset address can be overridden in both the 16- and 32-bit instruction modes using the 66h and 67h prefixes. In 16-bit protected-mode, descriptors are still used but segments are supposed to be a maximum of 64K bytes.
Access rights byte: It allows complete control over the segment. If the segment is a data segment, the direction of growth is specified. If the segment grows beyond its limit, the microprocessor's operating system program is interrupted, indicating a general protection fault. You can specify whether a data segment can be written or is write-protected. The code segment can have reading inhibited to protect software. This is why It is called protected mode. This kind of protection is unavailable in real mode.
|
Fig 1 Descriptor
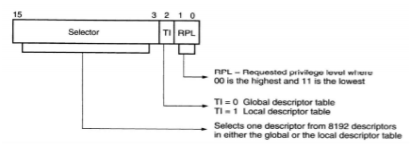
There are two descriptor tables: Global descriptors table: contains segment definitions that apply to all programs (also called system descriptors). Local descriptors table: usually unique to an application (also called application descriptors). Each descriptor table contains 8192 descriptors, so a total of 16,384 descriptors are available to an application at any time. This allows up to 16,384 memory segments to be described for each application. The Figure below shows the segment register in the protected mode.
It contains: 13-bit selector field: chooses one of the 8192 descriptors from the descriptor table (213 = 8192). Table indicator (TI) bit: selects either the global descriptor table (TI = 0) or the local descriptor table (TI = 1). Requested privilege level (RPL) field: requests the access privilege level of a memory segment. The highest privilege level is 00 and the lowest is 11.
If the requested privilege level matches or is higher in priority than the privilege level set by the access rights byte, access is granted. Windows uses privilege level 00 (ring 0) for the kernel and driver programs and level 11 (ring 3) for applications. Windows does not use levels 01 or 10. If privilege levels are violated, the system normally indicates a privilege level violation.
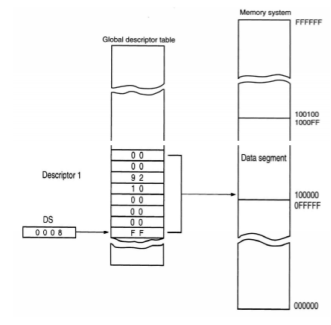
Real Mode: DS = 0008h, then the data segment begins at location 00080h and its length is 64K bytes. Protected Mode: DS = 0008h = 0000 0000 0000 1000, then the selector selects Descriptor 1 in the global descriptor table using a requested privilege level of 00. The global descriptor table is stored in memory as shown below.
|
Fig 2 Selector
Descriptor number 1 contains a descriptor that defines the base address as 00100000h with a segment limit of 000FFh. This refers to memory locations 00100000h – 001000FFh for the data segment.
|
Fig 3 Global Descriptor Table
Key takeaway
There are two descriptor tables: Global descriptors table: contains segment definitions that apply to all programs (also called system descriptors). Local descriptors table: usually unique to an application (also called application descriptors). Each descriptor table contains 8192 descriptors, so a total of 16,384 descriptors are available to an application at any time. This allows up to 16,384 memory segments to be described for each application.
Paging is enabled when the PG bit in control register CR0 is set. The paging mechanism can function in both the real and protected modes. When paging is enabled, physical memory is divided into small blocks (typically 4K bytes or 4M bytes) in size, and each block is assigned a page number. The operating system keeps a list of free pages in its memory. When a program makes a request for memory, the OS allocates a number of pages to the program. A key advantage to memory paging is that memory allocated to a program does not have to be contiguous, and because of that, there is very little internal fragmentation - thus little memory is wasted.
The Page Directory and Page Table
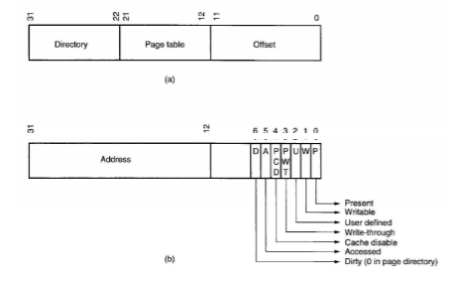
To convert a 32-bit linear address into a 32-bit physical address, we need to understand that the most significant 20 bits of the linear address indicate the linear page number, while the least significant 12 bits of the linear address indicate the offset within this page. The offset should remain the same but the linear page number has to be converted into a physical page number.
|
Fig 4 Page Directory and Page Address
Each page directory entry is a physical address pointing to a page table, which contains page table entries. Each page table contains 1024-page table entries, each of which is 4 bytes (32 bits). This means that each page table is 4 K bytes long. Each page table entry points to the starting physical address of a page in memory. This means that if we have one page directory and 1024-page tables, then we have a total of 1M table entries or 1 M pages. Since each page is 4K bytes long, this will cover a total of 4G bytes of maximum physical memory
The figure below Part (a) shows the linear address (generated by the software) and how it selects one of the 1024-page directory entries from the page directory (using the left most 10 bits) and then selects one of the 1024-page table entries (using the next 10 bits). Part (b) of the figure shows the offset. page table entry, which contains the physical number that must be associated with the example, the linear addresses 00000000h-00000FFFh access the first page directory entry, and the first page table entry. Notice that one page is a 4K-byte address range.
|
Fig 5(a) Linear Address 5(b) Off-set
So, if that page table entry contains 00100000h, then the physical address of this page is 00100000h-00100FFFh for linear address 00000000h-00000FFFh. This means that when the program accesses a location between 00100000H and 00100FFFh, the microprocessor physically addresses location 00100FFFH.
Key takeaway
To convert a 32-bit linear address into a 32-bit physical address, we need to understand that the most significant 20 bits of the linear address indicate the linear page number, while the least significant 12 bits of the linear address indicate the offset within this page.
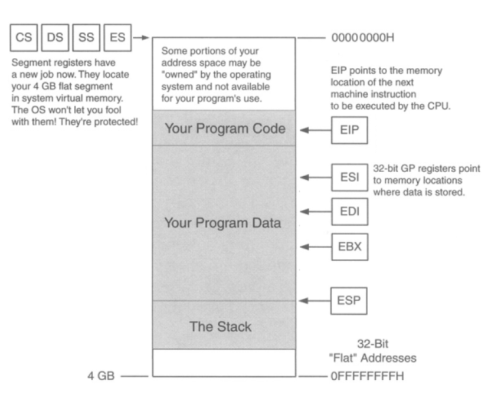
On 32-bit processors, Windows and Linux use the so-called protected mode flat memory model.
Under flat memory model,
Entire address space is described by a 32-bit segment, which provides 232 = 4 gigabytes of address space. Program can access up to 4 gigabytes of virtual or physical memory.
In protected mode,
Segment registers contain selector values rather than actual physical segment addresses. Selector values cannot be calculated by the program; they must be obtained by calling the operating system. Programs that update segment values or attempt to address memory directly do not work in protected mode.
|
Fig 6 Flat Mode Model Protected Mode
- The instruction pointer is 32 bits in size
- EIP can indicate any machine instruction anywhere in the 4 GB of memory.
- The segment registers still exist and define where 4 GB of program-accessible memory resides in physical or virtual memory
- The segment registers are now considered part of the operating system, you can neither read nor change them directly.
- When 32-bit program executes, it has access to 4-gig address space.
- Any general-purpose register by itself can specify any memory location in the entire memory address space of the 4 billion memory locations
- Attempting to actually read or write certain locations in your own program can be forbidden by the OS and will trigger an error.
- Challenges in programming for protected mode flat model are based on understanding the operating system, its requirements, and restrictions.
Key takeaway
2-bit Protected Mode supports much larger data structures than Real mode. Because code, data, and stack reside in the same segment, each segment register can hold the same value that never needs to change. Rather than using a formula to determine the physical address, protected mode processors use a look up table. Segment registers simply point to OS data structures that contain the information needed to access a location. Protected mode uses privilege levels to maintain system integrity and security. Programs cannot access data or code that is in a higher privilege level.
2.4.1 Data Addressing Modes
The instructions are used to transfer the data from one register to another register, from the memory to the register, and from the register to the memory without any change in the content.
Addressing modes in 8085 is divided into 5 groups −
Here, the 8/16-bit data is specified in the instruction itself as one of its operands. For example: MVI B, 40F means 40F is copied into register B.
Here, the data is copied from one register to another.
For example: MOV B, A: means data in register A is copied to register B.
Here, the data is directly copied from the given address to the register.
For example: LDB 5008H: means the data at address 5008H is copied to register B.
Here, the data is transferred from one register to another by using the address pointed by the register.
For example: MOV B, K: means data is transferred from the memory address pointed by the register K to the register B.
Here, it doesn’t require any operand; the data is specified by the opcode itself.
For example: CMP.
2.4.2 Program Memory Addressing Modes
We use programming memory in branch instructions. The JMP and CALL in 8086 are the branch instructions used [Ref.4]. The program memory addressing modes can be classified as
Direct Program Memory Addressing
• Direct program memory addressing is what many early microprocessors used for all jumps and calls.
• Direct program memory addressing is also used in high-level languages, such as the GOTO instruction.
• The microprocessor uses this form of addressing, but not as often as relative and indirect program memory addressing are used.
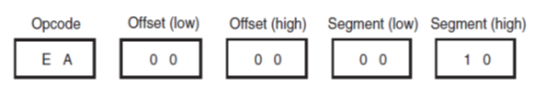
• The instructions for direct program memory addressing store the address with the opcode. For example, if a program jumps to memory location 10000H for the next instruction, the address (10000H) is stored following the opcode in the memory.
• Figure shows the direct intersegment JMP instruction and the 4 bytes required to store the address 10000H.
|
• This JMP instruction loads CS with 1000H and IP with 0000H to jump to memory location 10000H for the next instruction.
• An intersegment jump is a jump to any memory location within the entire memory system.) The direct jump is often called a far jump because it can jump to any memory location for the next instruction.
Relative Program Memory Addressing
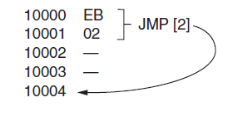
• Relative program memory addressing is not available in all early microprocessors, but it is available to this family of microprocessors. The term relative means relative to the instruction pointer (IP).
• For example, if a JMP instruction skips the next 2 bytes of memory, the address in relation to the instruction pointer is a 2 that adds to the instruction pointer. This develops the address of the next program instruction.
• An example of the relative JMP instruction is shown below.
|
• The JMP instruction is a 1-byte instruction, with a 1-byte or a 2-byte displacement that adds to the instruction pointer. A 1-byte displacement is used in short jumps, and a 2-byte displacement is used with near jumps and calls. Both types are considered to be intra segment jumps.
• An intra segment jump is a jump anywhere within the current code segment.
Indirect Program Memory Addressing
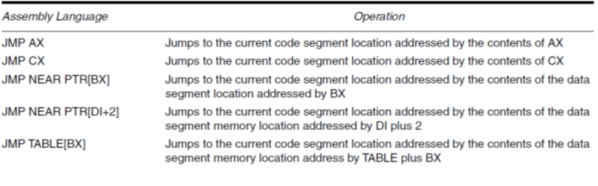
The microprocessor allows several forms of program indirect memory addressing for the JMP and CALL instructions.
|
Fig 7 Instruction Table
2.4.3 Stack Memory Addressing Modes
• The stack plays an important role in all microprocessors. It holds data temporarily and stores the return addresses used by procedures. The stack memory is a LIFO (last-in, first-out) memory, which describes the way that data are stored and removed from the stack. [Ref.4]
• Data are placed onto the stack with a PUSH instruction and removed with a POP instruction.
• The CALL instruction also uses the stack to hold the return address for procedures and a RET (return) instruction to remove the return address from the stack.
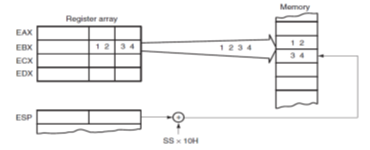
• The stack memory is maintained by two registers: the stack pointer (SP) and the stack segment register (SS). Whenever a word of data is pushed onto the stack, the high-order 8 bits are placed in the location addressed by SP – 1. The low-order 8 bits are placed in the location addressed by SP – 2. The SP is then decremented by 2 so that the next word of data is stored in the next available stack memory location.
|
Fig 8 Stack Memory Location
• The SP register always points to an area of memory located within the stack segment. The SP register adds to SS x 10h to form the stack memory address in the real mode.
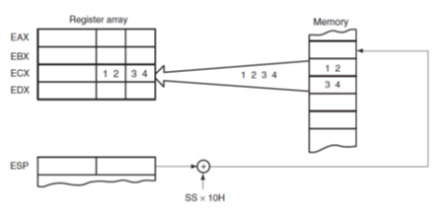
• Whenever data are popped from the stack, the low-order 8 bits are removed from the location addressed by SP. The high-order 8 bits are removed from the location addressed by SP+1. The SP register is then incremented by 2.
|
Fig 9 Stack memory Location
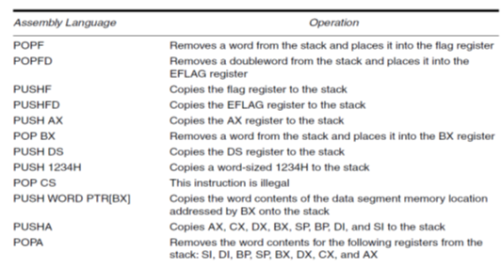
• PUSH and POP store or retrieve words of data—never bytes—in the 8086 microprocessors.
|
Fig 10 POP and PUSH instruction Table
• Data may be popped off the stack into any register or any segment register except CS. The reason that data may not be popped from the stack into CS is that this only changes part of the address of the next instruction.
Key takeaway
There are 5 addressing modes register, direct, indirect, implied and immediate modes.
Direct program memory addressing is what many early microprocessors used for all jumps and calls.
Reference:
1. Gaonkar, Ramesh S , “Microprocessor Architecture, Programming and Applications with 8085”, Penram International Publishing.
2. Ray A K, Bhurchandi K M, “Advanced Microprocessors and Peripherals”, TMH Hall D V, Microprocessor Interfacing’, TMH
3.Liu and, “Introduction to Microprocessor”, TMH
4. Brey, Barry B, “INTEL Microprocessors”, PHI