UNIT - 4
Programming – 2
4.1.1 ASCII Arithmetic
The ASCII arithmetic instruction function with ASCII-coded numbers. These numbers range in value from 30H to 39H for the numbers 0 to 9. There are four instructions used with ASCII arithmetic operations:
AAA (ASCII Adjust after Addition)
AAD (ASCII Adjust before Division)
AAM (ASCII Adjust after Multiplication)
AAS (ASCII Adjust after Subtraction)
These instructions use register AX as the source and as destination.
AAA Instruction
- Adjust the sum of two unpacked BCD values to create an unpacked BCD result.
- The AL register is the implied source and destination operand for this instruction.
- The AAA instruction is only useful when it follows an ADD instruction that adds (binary addition) two unpacked BCD values.
- The AAA instruction then adjusts the contents of AL register to contain the correct 1-digit unpacked BCD result.
- If the addition produces a decimal carry, the AH register is incremented by 1, and the CF and AF flags are set.
AAD Instruction
- Unlike all other adjustment instructions, the AAD instruction appears before a division.
- The AAD instruction requires that the AX register contain a two-digit unpacked BCD number (not ASCII) before executing.
- After adjusting the AX register with AAD, it is divided by an unpacked BCD number to generate a single-digit result in AL with any remainder in AH.
Example:
MOV BL, 9H
MOV AX, 702H
AAD
DIV BL
The above example shows how 72 is unpacked BCD is divided by 9 to produce a quotient of 8. The 0702H loaded into AX register is adjusted by the AAD instruction to 0048H.
AAM Instruction
- Adjust the result of the multiplication of two unpacked BCD values to create a pair of unpacked BCD values.
- The AX register is the implied source and destination operand for this instruction.
- The AAM instruction is only useful when it follows an MUL instruction that multiplies (binary multiplication) two unpacked BCD values and stores a word result in AX registers.
AAS Instruction
- Adjust the result of the subtraction of two unpacked BCD values to create an unpacked BCD result.
- The AL register is the implied source and destination for this instruction.
- The AAS instruction is only useful when it follows a SUB instruction that subtracts (binary subtraction) one unpacked BCD valued from another and stores a byte result in the AL register.
- If the subtraction produced a decimal carry, the AH register is decremented by 1, and the CF and AF flags are set.
- If no decimal carry occurred, the CF and AF flags are cleared, and the AH register is unchanged.
4.1.2 BCD Arithmetic
Two instructions to process packed BCD numbers
- daa − Decimal adjust after addition
Used after add or adc instruction
- das − Decimal adjust after subtraction
Used after sub or sbb instruction
The daa instruction works as follows
- If the least significant four bits in AL are > 9 or if AF =1, it adds 6 to AL and sets AF
- If the most significant four bits in AL are > 9 or if CF =1, it adds 60H to AL and sets CF
Example: mov AL,71H
add AL,43H AL: = B4H
daa AL: = 14H and CF: = 1
The result including the carry (i.e., 114H) is the correct answer
The das instruction works as follows
- If the least significant four bits in AL are > 9 or if AF =1, it subtracts 6 from AL and sets AF
- If the most significant four bits in AL are > 9 or if CF =1, it subtracts 60H from AL and sets CF Example: mov AL,71H
sub AL,43H AL: = 2EH
das AL: = 28H
Key takeaway
There are four instructions used with ASCII arithmetic operations:
AAA (ASCII Adjust after Addition)
AAD (ASCII Adjust before Division)
AAM (ASCII Adjust after Multiplication)
AAS (ASCII Adjust after Subtraction)
These instructions use register AX as the source and as destination.
Instructions to perform logical operation
- NOT − It inverts each bit of a byte.
- AND − It adds each bit in a byte with the corresponding bit in another byte.
- OR − It multiplies each bit in a byte with the corresponding bit in another byte.
- XOR − It performs Exclusive-OR operation over each bit in a byte.
- TEST − It adds operands to update flags, without affecting operands.
Instructions to perform shift operations
- SHL/SAL − It shifts bits of a byte towards left by putting zero(S) in LSBs.
- SHR − It shifts bits of a byte towards right by putting zero(S) in MSBs.
- SAR − It shifts bits of a byte towards the right and copies the old MSB into the new MSB.
Instructions to perform rotate operations
- ROL − It rotates bits of word towards the left i.e. MSB to LSB.
- ROR − It rotates bits of word towards the right i.e. LSB to MSB.
- RCR − It rotates bits of word towards the right i.e. LSB to CF and CF to MSB.
- RCL − It rotates bits of word towards the left i.e. MSB to CF and CF to LSB.
It is a group of words and their memory is always placed in a sequential order.
Following are the instructions under this group −
- REP − It repeats the given instruction till CX ≠ 0.
- REPE/REPZ − It repeats the given instruction until zero flag ZF = 1 or CX = 0.
- REPNE/REPNZ − It repeats the given instruction until zero flag ZF = 1 or CX = 0.
- MOVS/MOVSB/MOVSW − It moves the byte from one string to another.
- COMS/COMPSB/COMPSW − It compares two string bytes.
- INS/INSB/INSW – It’s an input string byte from the I/O port given to the memory location.
- OUTS/OUTSB/OUTSW − It’s an input string byte from the memory location to the I/O port.
- SCAS/SCASB/SCASW − It scan’s a string and compares its byte with a byte present in AL or string word with a word present in AX.
- LODS/LODSB/LODSW − It stores the string byte into AL or AX.
Key takeaway
It is a group of words and their memory is always placed in a sequential order.
Instructions to transfer the instruction during an execution with some conditions −
- JA/JNBE − It jumps if instruction satisfies.
- JAE/JNB − It jumps if instruction satisfies.
- JBE/JNA − It jumps if instruction satisfies.
- JC − It jumps when carry flag is set.
- JE/JZ − It jumps when zero flag is set.
- JG/JNLE − It jumps when greater than / not less than / equal to instruction satisfies.
- JGE/JNL − It jumps when greater than / not less than / equal to instruction satisfies.
- JL/JNGE − It jumps when less than / not greater than / equal to instruction satisfies.
- JLE/JNG − − It jumps when less than / equal to / not greater than instruction satisfies.
- JNC − It jumps if no carry flag = 0
- JNE/JNZ − It jumps if no zero flag = 0
- JNO – Jump when overflow
- JNP/JPO – Jump when PF = 0
- JNS − Jump if no sign flag SF = 0
- JO – Jump when OF = 1
- JP/JPE – Jump when parity/ even parity PF = 1
- JS – Jump when SF = 1
Key takeaway
These are the instructions to transfer the instruction during an execution with some conditions.
Example-1: write a procedure named Square that squares the contents of BL and places the result in BX.
Solution:
Square: PUSH AX
MOV AL, BL
MUL BL
MOV BX, AX
POP AX RET
Example-2: write a program that computes y = (AL)2 + (AH)2 + (DL)2 places the result in CX. Make use of the SQUARE subroutine defined in the previous example.
Solution: MOV CX, 0000H
MOV BL, AL
CALL Square
ADD CX, BX
MOV BL, AH
CALL Square
ADD CX, BX
MOV BL, DL
CALL Square
ADD CX, BX
HLT
Example-3: Write a program to move a block of 100 consecutive bytes of data starting at offset address 400H in memory to another block of memory locations starting at offset address 600H. Assume both block at the same data segment F000H.
Solution: MOV AX, F000H
MOV DS, AX
MOV SI, 0400H
MOV DI, 0600H
MOV CX, 64H
NEXTPT: MOV AH, [SI]
MOV [DI], AH
INC SI
INC DI
LOOP NEXTPT
HLT
Example-4: Using string operation, implement the previous example to copy block of memory to another location.
Solution: MOV CX, 64H
MOV AX, F000H
MOV DS, AX
MOV ES, AX
MOV SI, 400H
MOV DI, 600H
CLD
NXTPT: MOVSB
LOOP NXTPT
HTL
Example-5: Write a program loads the block of memory locations from A000H through 0A00FH with number 5H.
Solution: MOV AX, 0H
MOV DS, AX
MOV ES, AX
MOV AL, 05
MOV DI, 0A000H
MOV CX, 0FH
CLD
AGAIN: STOSB
LOOP AGAIN
A procedure is a set of code that can be branched to and returned from in such a way that the code is as if it were inserted at the point from which it is branched to. The branch to procedure is referred to as the call, and the corresponding branch back is known as the return. The return is always made to the instruction immediately following the call regardless of where the call is located.
The CALL instruction not only branches to the indicated address, but also pushes the return address onto the stack. The RET instruction simply pops the return address from the stack. The registers used by the procedure need to be stored before their contents are changed, and then restored just before their contents are changed, and then restored just before the procedure is excited.
A CALL may be direct or indirect and intra segment or intersegment. If the CALL is intersegment, the return must be intersegment. Intersegment call must push both (IP) and (CS) onto the stack. The return must correspondingly pop two words from the stack. In the case of intra segment call, only the contents of IP will be saved and retrieved when call and return instructions are used.
Procedures are used in the source code by placing a statement of the form at the beginning of the procedure
Procedure name PROC Attribute and by terminating the procedure with a statement
Procedure name ENDP
The attribute that can be used will be either NEAR or FAR. If the attribute is NEAR, the RET instruction will only pop a word into the IP register, but if it is FAR, it will also pop a word into the CS register.
A procedure may be in:
- The same code segment as the statement that calls it.
- A code segment that is different from the one containing the statement that calls it, but in the same source module as the calling statement.
- A different source module and segment from the calling statement.
In the first case, the attribute could be NEAR provided that all calls are in the same code segment as the procedure. For the latter two cases the attribute must be FAR. If the procedure is given a FAR attribute, then all calls to it must be intersegment calls even if the call is from the same code segment. For the third case, the procedure name must be declared in EXTRN and PUBLIC statements.
Saving and Restoring Registers
When both the calling program and procedure share the same set of registers, it is necessary to save the registers when entering a procedure, and restore them before returning to the calling program.
MSK PROC NEAR
PUSH AX
PUSH BX
PUSH CX
POP CX
POP BX
POP AX
RET
MSK ENDP
Procedure Communication
There are two general types of procedures, those operate on the same set of data and those that may process a different set of data each time they are called. If a procedure is in the same source module as the calling program, then the procedure can refer to the variables directly. When the procedure is in a separate source module it can still refer to the source module directly provided that the calling program contains the directive
PUBLIC ARY, COUNT, SUM
EXTRN ARY: WORD, COUNT: WORD, SUM: WORD
Recursive Procedures
When a procedure is called within another procedure it called recursive procedure. To make sure that the procedure does not modify itself, each call must store its set of parameters, registers, and all temporary results in a different place in memory. Example Recursive procedure to compute the factorial.
Key takeaway
A procedure is a set of code that can be branched to and returned from in such a way that the code is as if it were inserted at the point from which it is branched to. There are two general types of procedures, those operate on the same set of data and those that may process a different set of data each time they are called.
- An interrupt is a condition that arises during the working of a microprocessor. The microprocessor services it by executing a subroutine called Interrupt Service Routine (ISR).
- There are three sources of interrupts for 8086:
Hardware interrupt-
These interrupts occur as signals on the external pins of the microprocessor. 8086 has two pins to accept hardware interrupts, NMI and INTR.
Software interrupt-
These interrupts occur by writing the software interrupt instruction INT n where ‘n’ can be any value from 0 to 255 (00H to FFH). Hence all 256 interrupts can be invoked by software.
Error conditions (Exception or types)-
8086 is interrupted when some special conditions occur while executing certain instructions in the program. Example: An error in division automatically causes the INT 0 interrupt.
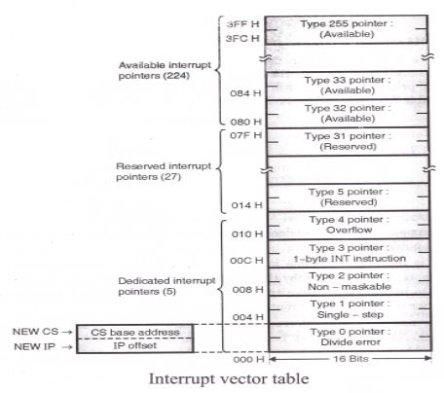
Interrupt Vector Table (IVT):
|
- The interrupt vector (or interrupt pointer) table is the link between an interrupt type code and the procedure that has been designated to service interrupts associated with that code. 8086 supports total 256 types i.e. 00H to FFH.
- For each type of interrupt it has to reserve four bytes i.e. double word.
- The higher addressed word contains the base address of the segment and is normally referred as NEW CS.
- The lower addressed word consists of the procedure’s offset and is normally referred as NEW IP.
- Thus NEW CS provides new physical address from where user ISR routine will start.
- Here, four bytes (2 for NEW CS and 2 for NEW IP) are required; hence interrupt pointer table occupies up to the first 1k bytes (i.e. 256 x 4 = 1024 bytes) of lower order memory.
- The total interrupt vector table is divided into three groups namely,
A. Dedicated interrupts (INT 0…..INT 4)
B. Reserved interrupts (INT 5…..INT 31)
C. Available interrupts (INT 32…..INT 225)
Dedicated interrupts (INT 0…..INT 4):
- INT 0 (Divide Error)-
- This interrupt occurs whenever there is division error. This condition normally occurs when the divisor is very small as compared to the dividend or the divisor is zero.
- Its ISR address is stored at location 0 x 4 = 00000H in the IVT.
- INT 1 (Single Step)-
- The microprocessor executes this interrupt after every instruction if the TF is set.
- Its ISR displays contents for all registers. Its ISR address is stored at location 1 x 4 = 00004H in the IVT.
- INT 2 (Non mask-able Interrupt)-
- The microprocessor executes this ISR in response to an interrupt on the NMI (Non mask-able Interrupt) line.
- Its ISR address is stored at location 2 x 4 = 00008H in the IVT.
- INT 3 (Breakpoint Interrupt)-
- This interrupt causes breakpoints in the program. It occurs by writing the instruction INT 03H or simply INT.
- It is useful in debugging large programs.
- Its ISR is used to display the contents of all registers on the screen. Its ISR address is stored at location 3 x 4 = 0000CH in the IVT.
- INT 4 (Overflow Interrupt)-
- It occurs if the overflow flag is set and the microprocessor executes the INTO (Interrupt on Overflow) instruction.
- It detects overflow error in signed arithmetic operations.
- Its ISR address is stored at location 4 x 4 = 00010H in the IVT.
Reserved interrupts (INT 5…..INT 31):
These levels are reserved by Intel to be used in higher processors like 80386, Pentium etc. They are not available to the user.
Available interrupts (INT 32…..INT 225):
- These are user defined, software interrupts.
- ISRs are written by the users to service various user defined conditions.
- These interrupts are invoked by writing the instruction INT n.
- Its ISR address is obtained by the microprocessor from location n x 4 in the IVT.
Hardware Interrupts:
- NMI (Non mask-able interrupt)-
- This is a non-mask-able, edge triggered, high priority interrupt.
- On receiving this, the microprocessor executes INT instruction.
- Microprocessor obtains the ISR address from location 2 x 4 = 00008H from the IVT.
- It reads 4 locations starting from this address to get the values for IP and CS to execute the ISR.
- INTR-
- This is a mask-able, level triggered, low priority interrupt.
- On receiving an interrupt on INTR line, the microprocessor executes 2 INTA pulses.
- It is masked by making IF = 0 by software through CLI instruction.
- It is unmasked by making IF = 1 by software through STI instruction.
Interrupt processing and pre-defined interrupts
The first five interrupt types are reserved for specific functions.
|
Fig Interrupts
- INT 0 (Divide Error)-
- This interrupt occurs whenever there is division error. This condition normally occurs when the divisor is very small as compared to the dividend or the divisor is zero.
- Its ISR address is stored at location 0 x 4 = 00000H in the IVT.
- INT 1 (Single Step)-
- The microprocessor executes this interrupt after every instruction if the TF is set.
- Its ISR displays contents for all registers. Its ISR address is stored at location 1 x 4 = 00004H in the IVT.
- INT 2 (Non mask-able Interrupt)-
- The microprocessor executes this ISR in response to an interrupt on the NMI (Non mask-able Interrupt) line.
- Its ISR address is stored at location 2 x 4 = 00008H in the IVT.
- INT 3 (Breakpoint Interrupt)-
- This interrupt causes breakpoints in the program. It occurs by writing the instruction INT 03H or simply INT.
- It is useful in debugging large programs.
- Its ISR is used to display the contents of all registers on the screen. Its ISR address is stored at location 3 x 4 = 0000CH in the IVT.
- INT 4 (Overflow Interrupt)-
- It occurs if the overflow flag is set and the microprocessor executes the INTO (Interrupt on Overflow) instruction.
- It detects overflow error in signed arithmetic operations.
- Its ISR address is stored at location 4 x 4 = 00010H in the IVT.
Key takeaway
The first five interrupt types are reserved for specific functions.
|
These instructions are used to control the processor action by setting/resetting the flag values.
Following are the instructions under this group −
- STC – It sets CF to 1
- CLC – It clears CF to 0
- CMC − It complements the carry flag CF.
- STD − It sets the direction flag DF to 1
- CLD – It clears the direction flag DF to 0
- STI − It enables INTR input.
- CLI − It clears the interrupt enable flag.
Key takeaway
These instructions are used to control the processor action by setting/resetting the flag values.
Reference:
1. Gaonkar, Ramesh S , “Microprocessor Architecture, Programming and Applications with 8085”, Penram International Publishing.
2. Ray A K, Bhurchandi K M, “Advanced Microprocessors and Peripherals”, TMH Hall D V, Microprocessor Interfacing’, TMH
3.Liu and, “Introduction to Microprocessor”, TMH
4. Brey, Barry B, “INTEL Microprocessors”, PHI