UNIT - 1
UNIX
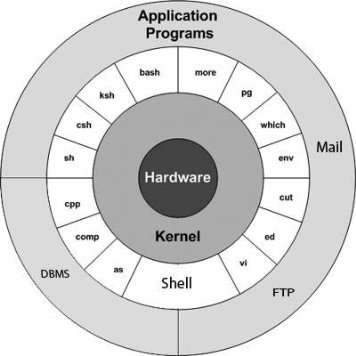
Unix System: The UNIX operating system is a set of programs that act as a link between the computer and the user. The computer programs that allocate the system resources and coordinate all the details of the computer's internal is called the operating system or kernel.
Users communicate with the kernel through a program known as the shell. The shell is a command line interpreter; it translates commands entered by the user and converts them into a language that is understood by the kernel.
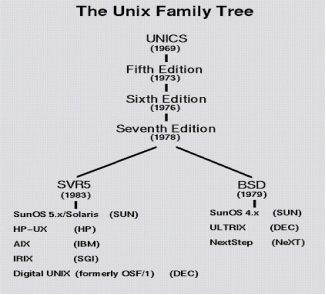
Unix was originally developed in 1969 by a group of AT&T employees at Bell Labs, including Ken Thompson, Dennis Ritchie, Douglas Mcllroy, and Joe Ossanna.
There are various Unix variants available in the market. Solaris Unix, AIX, HP Unix and BSD are few examples, Linux is also a flavor of Unix which is freely available.
Several people can use a UNIX computer at the same time, hence UNIX is called a multiuser system. A user can also run multiple programs at the same time; hence UNIX is called multitasking.
|
Figure 2
The main concept that unites all versions of UNIX is the following four basics:
Kernel: The kernel is the essential center of a computer operating system, the core that provides basic services for all other parts of the operating system. A synonym is nucleus. A kernel can be contrasted with a shell, the outermost part of an operating system that interacts with user commands. In other word, the kernel is the heart of the operating system. It interacts with hardware and most of the tasks like memory management, task scheduling and file management
Shell: The shell is the utility that processes your requests. When you type in a command at your terminal, the shell interprets the command and calls the program that you want. The shell uses standard syntax for all commands. C Shell, Boume Shell and Korn Shell are most famous shells which are available with most of the Unix variants.
Commands and Utilities: There are various command and utilities which you would use in your day to day activities. cp, mv, cat andgrep etc, are few examples of commands and utilities. There are over 250 standard commands plus numerous others provided through 3rd party software. All the commands come along with various optional options
Files and Directories: All data in UNIX is organized into files. All files are organized into directories. These directories are organized into a tree-like Structure called the file system.
1. Kernel: The Kernel performs various primitive operations on behalf of user programs:
(i) Control of execution of processes: Creation, synchronization, termination, suspension and communication of processes.
(ii) Scheduling of processes: Deciding of time-sharing of processes.
(iii) Memory management: Allocation of memory for executing processes. Two methods are used, which overcomes the limitations of simple time-sharing.
(a) Swapping: Entire process written to swap device to accommodate another process.
(b) Paging: Pages of memory written to swap device
(iv) File system service: Allocation of secondary storage efficiently for user data files.
(v) Controlled access to peripherals, which are treated as special files.
2. Hardware transparency: Processes usually run in one of the two modes:
(i) User mode: User mode cannot access kernel instructions and data.
(ii) Kernel mode: Kernel mode can access kernel and user addresses and privileged instructions not allowed for user mode.
The hardware only view processes in terms of kernel or user modes. It does not distinguish between the user processes and the OS has internal book keeping distinguishing between processes.
3. Interrupts and Exceptions:
Interrupt: It is a signal by which priorities and instruction-scheduling sequence can be controlled. The kernel saves the current context (a frozen image of what the processes was doing) when an interrupt occurs. After servicing the interrupt the context is restored and the process proceeds. The order in which an interrupt is serviced depends upon its priority.
Exception: An exception is an unexpected event like reference to an illegitimate address caused by events external to a process. Exceptions usually occur in the middle of a process where as interrupts occur between them. Different algorithms are used to handle interrupts/exceptions efficiently.
4. Processor Execution Levels: Based on the priority level of an interrupt the kernel masks certain interrupts in order that a critical process may proceed without error.
The priority levels in descending order are:
Higher Priority Lower Priority
|
There would be no disk interrupts while manipulating linked lists.
5. Memory management: The concept of a Virtual Machine is central to memory management under UNIX. The compiler generates addresses for a virtual machine as if no other program will execute simultaneously on the physical machine. Virtual addresses generated by the compiler need not be identical to the actual physical addresses in the machine. The memory management coordinates with the machine hardware to set-up a virtual to physical address translation that maps the compiler-generated address to the physical machine address.
The major features of UNIX can be listed as follows:
(i) Multiuser, time sharing OS
(ii) Multitasking OS
(iii) Portability
(iv) Modularity
(v) System security
(vi) File structure and security
(vii) Device Independent
(viii) Communication
(i) Multiuser, time sharing OS: UNIX allows several users, nearly 24 to 500, to use the same computer simultaneously by attaching terminals (keyboard and display) dumb or intelligent such that users of these terminals can run programs, access files, print documents, all at once. This is facilitated by time sharing the resources between the users. Scheduling algorithms are used to provide fast and non interfering usage of the computer.
(ii) Multitasking OS: In UNIX we can perform more than one task at a time i.e. while it is printing a document, we can start editing a new document or we can make the system scan a mailing list for an operation like sorting or process another document on the editor.) Multitasking is supported by placing few tasks in the "background" while we work on a task in the "foreground".
(iii) Portability: UNIX system itself is extremely portable. With few modifications, the UNIX system can be installed on a variety of hardware. It contains a set of programs that will let us connect our old computer to our new one and transfer data easily thus, providing a high version to version compatibility.
(iv) Modularity: UNIX comes with several hundred supplied programs in terms of utilities and tools which provide a rich and productive environment to create bigger modules from smaller ones. Integral utilities are part of the UNIX system that provide necessary support to the operating system for the practical operation of a computer with UNIX like command interpreter and shell program. Tools are programs that though are not essential for UNIX's basic operation but provide significant value addition Examples are electronic spreadsheets, word processing packages, mail programs, etc.
(v) System security: Computer system security means protecting computer hardware and information contained within the system. Threats to the system can be both internal and external. External threats include unauthorized access to the computer system, unauthorized tapping of data being transferred over the network, fire, electric power faults, natural disasters etc. Internal threats are of a more serious nature like destruction of software data by mistake or on purpose, examination or access of sensitive data by unauthorized users, alteration of this data. UNIX provides several safeguards in terms of:
(a) Password protection for system access.
(b) Control of access to individual files.
(c) Encryption of data files.
(d) Encryption of passwords.
(e) System accounting functions.
(vi) File structure and security: UNIX uses hierarchical file system for easy maintenance. It has consistent format for files, the byte stream, making application programs easier to write. UNIX permits more than one user to update the same file at virtually the same time. But if two users update the same file at exactly the same time, problems that affect the integrity of the data may occur. For example, the write operation of one user can undo the one just performed by the other user. To minimize these problems, file, record locks and explicit permissions are implemented.
(vii) Device independence: In UNIX, one of the design principles is to treat disk files and I/O devices as files from a user's perspective thus, safe guarding the user from the intricacies of the device. This provides device independence to the user. The hardware devices are given names in the file systems. These device special files are though known to the kernel as device interfaces, but are accessed by the user in the same way as other files
(viii) Communication: Communication has been one of UNIX's strong points. UNIX has extensive electronic mail facilities, some of the commands have subsequently been enhanced to run over a network, and even on the Internet. User processes communicate with network protocols via the socket facility.
(ix) Benefits of UNIX Operating System: The system is written in a high-level language, making it easy to read, understand, change, and move to other machines. Ritchie estimates that the first system in C was 20 to 40 percent larger and slower because it was not written in assembly language, but the advantages of using a higher-level language far out weight the disadvantages. It has a simple user interface that has the power to provide the services that users want. It provides primitives that permit complex programs to be built from simpler programs. It uses a hierarchical file system that allows easy maintenance and efficient implementation. It uses a consistent format for files, the byte stream, making application programs easier to write.
It provides a simple, consistent interface to peripheral devices. It is a multi user, multiprocessor system; each user can execute several processes simultaneously. It hides the machine architecture from the user, making it easier to write programs that run on different hardware implementations.
1) mv - move a file: Rename a file with the move command, mv.
Syntax: mv (options] old_filename new_filename
Common Options:
-i interactive (prompt and wait for confirmation before proceeding)
-f don't prompt, even when copying over an existing target file (overrides-i)
Examples:
$ mvold_filename new_filename
i) We now have a file called new_filename and the file old filename is gone. Actually all we've done is to update name the directory table entry to give the file a new name
ii) The contents of the file remain where they were.
2. who w – Command: UNIX maintains an account for all the current system. Because it is a multi-user system it is prudent for the user to be aware of other current users so that s/he can communicate with them if required. The user login details of all the current users by using the who command. The use of who command provides a list of all the current users in the three-column format by default, as shown follows:
$ who raj console Nov 19 09:35 reena tty01 Nov 19 09:40 priya tty02 Nov 19 09:41 |
The first column shows the name of the users, the second column shows the device names and the third column shows the login time. Some options like -H, -u and -T can be used with this command.
The H option provides headers for the columns and the -u option provides more details like idle time, PID and comments as shown in the example below.
$ who-Hu NAME LINE TIME IDLE PID COMMENTS raj console Nov 19 09:35 # 32 reena tty01 Nov 19 09:40 0:20 33 priya tty01 Nov 19 09:41 0:40 34 |
If any terminal is idle If any terminal is idle (not active) for the last 1 minute, the information, that is, for how long that terminal is idle will be indicated on the IDLE column. Thus, 0:20 indicates that reena's terminal is IDLE for the last 20 minutes. This information will be useful to the system administrator. The PID indicates the process identification number. The self-login details of a user can be obtained as a single line output using am and i arguments along with the who command as follows.
$ who am i reena tty01 Nov 1909:40 |
Generally, the who command is used by the system administrator for monitoring terminals.
The w command is a quick way to see who is logged on and what they are doing.
3. nl : line number: To add line numbers to a file in Unix, use the nl command. For example, given an input file cherry.txt,
Loveliest of trees, the cherry now
is hung with bloom along the bough,
And stands about the woodland ride
Wearing white for Eastertide.
The command $ nl cherry.txt Gives output:
1 Loveliest of trees, the cherry now 2 Is hung with bloom along the bough, 3 And stands about the woodland ride 4 Wearing white for Eastertide.
It is also possible to start from a different number. The command:
$ nl-v 100 cherry.txt
Gives the output:
100 Loveliest of trees, the cherry now 101 Is hung with bloom along the bough, 102 And stands about the woodland ride 103 Wearing white for Eastertide. |
4. touch: Changing the Time Stamps: We may sometimes need to set the modification and access times to predefined values. The touch command changes these times, and is used in the following manner:
Syntax:
touch [options] expression filename (s)
Common Options:
-a change the access time of the file (SVR4 only)
-c don't create the file if it doesn't already exist -f force the touch, regardless of read/write permissions -m change the modification time of the file (SVR4 only) -t time use the time specified, not the current time (SVR4 only) |
Example:
1. When touch is used without options or expression, both times are set to the current time. The file is created if it doesn't exist :
$ touch emp.lst Creates file if it doesn't exist 2. When touch is used without options but with expression, it changes both times. The expression consists of an eight-digit number using the format MMDDHHMM (month, day, hour and minute). Optionally, we can suffix a
two- or four-digit year string :
$ touch 03161430 emp.lst
$ ls –l emp.lst
-rw-r--r-1 kumar metal 870 Mar 16 14:30 emp.lst |
5. wall - send a message to everybody's terminal.
Syntax:
wall [-n] [message ]
Description: wall sends a message to everybody logged in. The message can be given as an argument to wall, or it can be sent to wall's standard input. When using the standard input from a terminal, the message should be terminated with the EOF key (usually Control-D). The length of the message is limited to 20 lines.
OPTIONS :
-n: Suppresses the normal banner printed by wall, changing it to "Remote broadcast message". This option is only available for root if wall is installed set-group-id, and is used by rpc.walld(8).
Note: The length of the message is limited to 22 lines. For every invocation of wall a notification will be written to syslog, with facility LOG_USER and level LOG_INFO
6. arp - manipulate the system ARP cache
arp [-evn] [-H type] [-i if] -a [hostname] arp [-v] [-i if] -d hostname (pub] arp [-v] [-H type] [-i if]-s hostname hw_addr [temp]
arp [-v] [-H type] [-i if] -s hostname hw_addr [netmask nm] pub arp [-v] [-H type] [-i if] - Ds hostname ifa [netmask nm] pub arp [-vnD] [-H type] [-i if] -f [filename]
Description: Arp manipulates the kernel's ARP cache in various ways. The primary options are clearing an address mapping entry and manually setting up one. For debugging purposes, the arp program also allows a complete dump of the ARP cache.
Options:
-V, --verbose Tell the user what is going on by being verbose.
-n, --numeric shows numerical addresses instead of trying to determine symbolic host, port or user names.
-H type, -hw-type type, -t type When setting or reading the ARP cache, this optional parameter tells arp which class of entries it should check for. The default value of this parameter is ether (ie. hardware code 0x01 for IEEE 802.3 10Mbps Ethernet). Other values might include network technologies such as ARCnet (arcnet) PROnet (pronet), AX.25 (ax25) and NET/ROM (netrom).
-a [hostname), --display [hostname]
Shows the entries of the specified hosts. If the hostname parameter is not used, all entries will be displayed. The entries will be displayed in alternate (BSD) style.
-d hostname, --delete hostname Remove any entry for the specified host. This can be used if the indicated host is brought down, for example.
-D, -use-device Use the interface ifa's hardware address.
-e Shows the entries in default (Linux) style. |
7. useradd : create a new user or update default new user information
SYNOPSIS:
Tag | Description |
useradd [options] LOGIN useradd -D useradd -D [options]
| |
DESCRIPTION:
When invoked without the -D option, the useradd command creates a new user account using the values specified on the command line and the default values from the system. Depending on command line options, the useradd command will update system files and may also create the new user's home directory and copy initial files. The version provided with Red Hat Linux will create a group for each user added to the system by default.
OPTIONS:
The options which apply to the useradd command are:
-c, -comment COMMENT | Any text string. It is generally a short description of the login, and is currently used as the field for the user's full name. |
-b, -base-dir BASE_DIR
| The default base directory for the system if –d dir is not specified. BASE_DIR is concatenated with the account name to define the home directory. If the -m option is not used, BASE_DIR must exist. |
-d, -home HOME DIR
| The new user will be created using HOME DIR as the value for the user's login directory. The default is to append the LOGIN name to BASE_DIR and use that as the login directory name. The directory HOME_DIR does not have to exist but will not be created if it is missing. |
-e, expiredate EXPIRE_DATE | The date on which the user account will be disabled. The date is specified in the format YYYY-MM-DD.
|
-f, -inactive INACTIVE | The number of days after a password expires until the account is permanently disabled. A value of 0 disables the account as soon as the password has expired, and a value of -1 disables the feature. The default value is -1.
|
-g, -gid GROUP | The group name or number of the user's initial login group. The group name must exist. A group number must refer to an already existing group, /etc/default/useradd.
|
8. ls - list directory contents. The command to list our directories and files is ls, With options it can provide information about the size, type of file, permissions, dates of file creation, change and access.
Syntax: Is [options] [argument]
Common Options: When no argument is used, the listing will be of the current directory. There are many useful options for the Is command. A listing of many of them follows. When using the command, string the desired options together preceded by "."
-a lists all files, including those beginning with a dot (.) -d lists only names of directories, not the files in the directory -F indicates type of entry with a trailing symbol: directories / sockets = symbolic links @ executables*
-g displays Unix group assigned to the file, requires the -l option (BSD only)-or on an SVR4 machine, e.g. Solaris, this option has the opposite effect -L if the file is a symbolic link, lists the information for the file or directory the link references, not the information for the link itself.
-I long listing: lists the mode, link information, owner. size. last modification time). If the file is a symbolic link, an arrow (-->) precedes the pathname of the linked-to file.
The mode field is given by the -I option and consists of 10 characters. The first character is one of the following:
character if entry is a:
d directory - plain file b block-type special file c character-type special file 1 symbolic link s socket
The next 9 characters are in 3 sets of 3 characters each. They indicate the file access permissions: the first 3 characters refer to the permissions for the user, the next three for the users in the UNIX group assigned to the file, and the last 3 to the permissions for other users on the system.
Designations are as follows:
r read permission w write permission x execute permission -no permission
There are a few less commonly used permission designations for special circumstances. These are explained in the man page for ls. |
Examples: (i) To list the files in a directory: $ ls Demofiles frank linda
(ii) To list all files in a directory, including the hidden (dot) files try: $ Is –a ..cshrc .history -plan .rhosts frank ...emacs .login .profile demofiles linda
(iii) To show the hidden files, but not the current directory) and (parent directory), use option -A.
(iv) To show all the files recursively, use -R option. When we do this from /, it shows all the unhidden files in the whole file system recursively.
$Is /etc/sysconfig/networking devices profiles
$Is -R -R/etc/sysconfig/networking /etc/sysconfig/networking: devices profiles
/etc/sysconfig/networking/devices: /etc/sysconfig/networking/profiles: Default
/etc/sysconfig/networking/profiles/default:
(v) To get a long listing: $ Is-al
total 24
drwxr-sr-x 5 workshop acs 512 Jun7 11:12 . drwxr-xr-x 6 root sys 512 May29 09:59 .. -rw-------- 1 workshop acs 525 May20 21:29 .emacs -rwxr-xr-x 1 workshop acs 238 May 14 09:44 .login -rw-r—r-- 1 workshop acs 273 May 22 23:53 .plan -rwxr-xr-x 1 workshop acs 413 May 14 09:36 .profile drwx------- 3 workshop acs 512 May 24 11:18 demofiles drwx------- 2 workshop acs 512 May 21 10:48 frank drwx------- 3 workshop acs 512 May 24 10:59 linda Instead of doing the 'ls - and then the checking for the first character to determine the type of file. We can use -F which classifies the file with different special character for different kind of files. $ ls -F Desktop/ Documents/ Ubuntu-App@ firstfile Music/ Public/ Templates/ Thus in the above output /-directory. nothing - normal file. @- link file. *- Executable file
(vi) $ Is-d Displays only directories: (vii) $ Is -r Displays files in reverse order. (viii) $ Is -f Interprets each name as a directory, not a file. |
9. Pwd : ‘pwd' stands for 'Print Working Directory. As the name states, command 'pwd' prints the current working directory or simply the directory user is, at present. It prints the current directory name with the complete path starting from root (/). This command is built in shell command and is available on most of the shell - bash, Bourne shell, ksh,zsh, etc.
Syntax :
$ pwd [option] e.g., /home/frank/src
Option:
-L (logical) Use PWD from environment, even if it contains symbolic links
-P (physical) Avoid all symbolic links
-help Display this help and exit
--version Output version information and exit
If both -L' and'-P options are used, option 'L' is taken into priority. If no option is specified at the prompt pwd will avoid all symlinks, i.e., take option -P into account |
10. echo: Displaying a message : This command is often used in shell scripts to display diagnostic messages on the terminal, or to issue prompts for input. So far, we have used it in two ways :
(i) To display a message (like echo Sun Solaris).
(ii) To evaluate shell variables (like echo (SHELL)).
Originally, echo was an external command, but today all shells have echo built-in.
Syntax : echo[option] [string]
Option :
-n do not output the trailing newline -e enable interpretation of backslash escapes -E disable interpretation of backslash escapes (default) --help display this help and exit --version output version information and exit |
If -e is in effect, the following sequences are recognized :
\0NNN | the character whose ASCII code is NNN (octal) |
\\ | Backslash |
\a | alert (BEL) |
\b | Backspace |
\c | suppress trailing newline |
\f | form feed |
\n | new line |
\r | carriage return |
\t | horizontal tab |
\v | vertical tab |
Note: Your shell may have its own version of echo, which usually supersedes the version described here. Please refer to your shell's documentation for details about the options it supports.
11. Find: Locating Files: Find is one of the power tools of the UNIX system. It recursively examines a directory tree to look for files matching some criteria, and then takes some action on the selected files.
Syntax:
Find path_list selection_criteria action This is how find operates: (i) First, it recursively examines all files in the directories specified in path_list. (ii) It then matches each file for one or more selection criteria." (iii) Finally, it takes some action on those selected files. The path_list comprises one or more subdirectories separated by whitespace. It can also be a host of selection_criteria that we can use to match a file, and multiple actions to dispose of the file. Example: As our first example, let's use find to locate all files named a.out (the executable file generated by the C compiler): $ find / -name a.out –print /home/kumar/scripts/a.out /home/tiwary/scripts/reports/a.out /home/sharma/a.out The path list () indicates that the search should start from the root directory. Each file in the list is then matched against the selection criteria (-name a. out), which always consists of an expression in the form operator argument. If the expression matches the file (ie, the file has the name a. out), the file is selected. The third section specifics the action (-print) to be taken on the files; in this case, a simple display on the terminal. We can also use relative names (like .) in the path list, and find will then output a list of relative pathnames. When find is used to match a group of filenames with a wild-card pattern, the pattern should be quoted to prevent the shell from looking at it: $ find.-name "*.c"-print All files with extension .c $ find.-name '[A-Z]*’-print Single quotes will also do The first command looks for all C program source files in the current directory tree. The second one searches for all files whose names begin with an uppercase letter We must not forget to use the -print option because without it find on UNIX systems will look for files all right but won't print the list. The-name is not the only operator used in framing the selection criteria. Locating a File by Inode Number (- inum): Use the -inum option to find all
filenames that have the same inode number: $ find / -inum 13975 –print Find: cannot read dir /usr/lost+found: Permission denied /usr/bin/gzip /usr/bin/gunzip /usr/bin/gzcat "Cats" a compressed file There is possibility of same inode number for more than one file and find throws an error message when it can't change to a directory. Sometimes, there will be so many of them on our screen that we would find it difficult to spot the files that actually show up as find's output. To avoid these messages, simply redirect the standard error to /dev/null.
File Type and Permissions (-type and -perm): The -type option followed by the letter f, d or I selects files of the ordinary, directory and symbolic link type. Here's how we locate all directories of our home directory tree: $ cd; find. - type d-print 2>/dev/null. Shows the . also ./.netscape Displays hidden directories also ./java_progs ./cjjrogs ./cjjrogs/include ./cj>rogs/lib ./shellscripts ./.ssh The relative pathname find displays, but that's because the pathname itself was relative (.). Find also doesn't necessarily display an ASCII sorted list. The sequence in which files are displayed depends on the internal organization of the file system The -perm option specifies the permissions to match. For instance, -perm 666 selects files having read and write permission for all categories of users. Such files are security hazards. We'll often want to use two options in combination to restrict the search to only directories:
$ find SOME -perm 777-type d-print
(i) Find uses an AND condition (an implied -a operator between -perm and - type) to select directories that provide all access rights to everyone. (ii) It selects files only if both selection criteria (-perm and -type) are fulfilled.
Finding Unused Files (-mtime and-atlme): Files tend to build up incessantly on disk. Some of them remain unaccessed or unmodified for months even years. find's options can easily match a file's modification (-mtime) and access (-atime) times to select them, -mtime helps in backup operations by providing a list of those files that have been modified, say in less than 2 days: $ find. -mtime -2-print -2 here means less than 2 days. To select from the /home directory all files that have not been accessed for more than a year, a positive value has to be used with - atime: $ find /home -atime +365 -print | mailx root Because find uses standard output the list can be stored in a file or used to mail a message. Remember, +365 means greater than 365 days, -365 means less than 365 days. For specifying exactly 365, use 365. The find Operators (!, -o and -a) : There are three operators that are commonly used with find. The ! operator is used before an option to negate its meaning. So, to selects C program files use: $ find. ! -name ".c" -print To look for both Shell and Perl scripts, use the-o operator which represents an OR condition. We need to use an escaped pair of parentheses here: find /home \(-name "*.sh" -o -name "*.pl" \)-print The (and) are special characters that are interpreted by the shell to group commands. The same characters are used by find to group expressions using the - o and -a operators, the reason why they need to be escaped. |
12. more: Paging Output: The more command displays its output a page at a time. This is possible because it sends its output to a pager program. UNIX offers the more pager (originally from Berkeley) which has today replaced pg, the original pager of UNIX. Linux also offers more but less is its standard pager. To view the file chap01, enter the command with the filename:
$ more chap01 Press q to exit We'll see the contents of chap01 on the screen, one page at a time. At the bottom of the screen, we'll also see the filename and percentage of the file that has been viewed: --More- (17%) More has a couple of internal commands that don't show up on the screen when we invoke them, the command used to exit more, is an internal command. Navigation : Irrespective of version, more uses the spacebar to scroll forward a page at a time. We can also scroll by small and large increments of lines or screens. To move forward one page, use f or the spacebar and to move back one page, use b. The use of Repeat Factor: As a command prefix simply repeats the command that number of times. This means we can use 10f for scrolling forward by 10 pages and 30b for scrolling back 30 pages. Just ember that the commands themselves are not displayed on the screen-even for a moment. Searching for a Pattern: We can perform a search for a pattern with the / command followed by the string. For instance, to look for the first while loop in our program, we'll have to enter this: /while Press (Enter] also We can repeat this search for viewing the next whileloop section by pressing n, and we can do that repeatedly until we have scanned the entire file. Move back with b (using a repeat factor, if necessary) to arrive at the first page. Internal commands: Spacebar of f one page forward 10f 10 page forward Enter key one line forward B one page back 10b 10 page back :n next file :P previous file .(Dot) repeat last command q Quit |
13. yacc : The yacc command converts context-free grammar specification into a set of tables for a simple automaton that executes an LALR(1) parsing algorithm. The grammar can be ambiguous; specified precedence rules are used to break ambiguities.
Syntax: yacc - options grammar Examples: The following command: $ yacc grammar.y
It draws yacc rules from the grammar.y file, and places the output in y.tab.c. We must compile the output file, y.tab.c, with a C language compiler to produce a yyparse function |
14. umask: Default file and directory permissions : When we create files and directories, the permissions assigned to them depend on the system's default setting. The UNIX system has the following default permissions for all files and directories:
(i) rw-rw-rw- (octal 666) for regular files. (ii) rwxrwxrwx (octal 777) for directories. However, we don't see these permissions when we create a file or directory. Actually, this default is transformed by subtracting the user mask from it to remove one or more permissions. To understand what this means, let's evaluate the current value of the mask by using umask without arguments: $ umask 022 This is an octal number which has to be subtracted from the system default to obtain the actual default. This becomes 644 (666 - 022) for ordinary files and 755 (777 - 022) for directories. When we create a file on this system, it will have the permissions rw-r-r-. umask is a shell built-in command though it also exists as an external command. A user can also use this command to set a new default. Here's an extreme setting: $ umask 000 All read-write permissions on An umask value of 000 means that we haven't subtracted anything and this could be dangerous. The system's default then applies (666 for files and 777 for directories). All files and directories are then writable by all; nothing could be worse than that! However, a mask value of 666 or 777 doesn't make much sense either; we'll then be creating files and directories with no permissions.
|
15. ps: Process Status The use of ps command to display some process attributes, ps can be seen as the process counterpart of the file system's ls command. The command reads through the kernel's data structures and process tables to fetch the characteristics of processes. By default, ps display the processes owned by the user running the command. If we execute the command immediately after logging in, what we see could look like this:
$ps PID TTY TIME CMD 291 console 0:00 bash The login shell of this user
|
Ignoring the header, each line (here, only one) shows the PID, the terminal (TTY) with which the process is associated (the controlling terminal), the cumulative processor time (TIME) that has been consumed since the process has been started, and the process name (CMD).
We can see that our login shell (bash) has the PID 291, the same number echoed by the special variable, $$.
ps Options :
Full Listing (-f): To get a detailed listing which also shows the parent of every process, use the -f (full) option: $ ps -f UID PID PPID C STIME TTY TIME CMD raj 367 291 0 12:35:16 console 0:00 vi create_user.sh raj 291 1 0 10:24:58 console 0:00 -bash raj 368 367 0 12:35:18 console 0:00 /usr/bin/bash -i |
Now we can see the parent (PPID) and owner (UID) of every process. Apart from the vi editor, there are two shells running here, and the -f option easily identifies a login shell by the hyphen preceding the command name. Here C is the header information. STIME shows the time the process started. CMD displays the entire command line with its arguments.
Displaying Process of a user (-u) : The system administrator needs to use the -u (user) option to know the activities of any user. The following output shows a user working on the X Window system rather than a character terminal and X running number of processes on the user's behalf:
$ ps-u raj PID TTY TIME CMD 378 ? 0:05 Xsun 403 ? 0:00 Xsession 339 pts/3 0:00 bash 346 pts/3 0:00 vi 347 pts/3 0:00 bash 478 ? 0:00 dtfile
|
Displaying All User Processes (a): The -a (all) option lists processes of all users but doesn't display the system processes. To see all the system processes we can use (-e or -A) option.
16. nice: Job execution with low priority : Processes in the UNIX system are usually executed with equal priority. This is not always desirable since high-priority jobs must be completed at the earliest. UNIX offers the nice command, which is used with the & operator to reduce the priority of jobs. More important jobs can then have greater access to the system resources (being "nice" to our neighbors).
Example: To run a job with a low priority, the command name should be prefixed with nice: $ nice wc – uxmanual or better still with $ nice wc -1 uxmanual &
nice is a built-in command in the C shell, nice values are system-dependent and typically range from 1 to 19. Commands execute with a nice value that is generally in the middle of the range usually 10. A higher nice value implies a lower priority, nice reduces the priority of an process, thereby raising its nice value. We can also specify the nice value explicitly with the -n option:
$ nice -n 5 wc –l uxmanual & Nice value increased by 5 units
A non-privileged user can't increase the priority of a process; that power is reserved for the super user. The nice value is displayed with the $ ps -o nice command. |
17. rmdir: Removing Directories: The rmdir (remove directory) command removes directories. We simply have to do this to remove the directory pis:
$ rmdir pis Directory must be empty
The rmdir can also delete more than one directory in one shot for instance, the three directories and subdirectories can be removed by using rmdir with a reversed set of arguments:
$ rmdir pis/data pis/progs pis
When we delete a directory and its subdirectories, a reverse logic has to be applied. $ rmdir pis pis/progs pis/data rmdir: directory "pis": Directory not empty
We observed one thing from the error message? rmdir, has silently deleted the lowest level subdirectories progs and data. This error message leads to two important rules that we should remember when deleting directories:
(a) We can't delete a directory with rmdir unless it is empty. In this case, the pis directory couldn't be removed because of the existence of the subdirectories, progs and data, under it. (b) We can't remove a subdirectory unless we are placed in a directory which is hierarchically above the one we have chosen to remove.
The first rule follows logically from the example above. To illustrate the second cardinal rule, try removing the progs directory by executing the command from the same directory itself: $ cd progs pwd /home/kumar/pis/progs $ rmdir /home/kumar/pis/progs Trying to remove the current directory rmdir: directory M/home/kumar/pis/progs": Directory does not exist To remove this directory, we must position ourself in the directory above progs, ie, pis, and then remove it from there: $ cd /home/kumar/pis $ pwd /home/kumar/pis $ rmdir progs
|
The mkdir and rmdir commands work only in directories owned by the user Generally, a user is the owner of his/her home directory, and he/she can create and remove subdirectories (as well as regular files) in this directory or in any subdirectories created by him/her. However, he/she normally won't be able to create or remove files and directories in other users' directories.
18. chmod: Changing file permissions: The command name chmod stands for "change mode", and it is used to define the way a file can be accessed. Chmod (change mode) is one of the most frequently used commands in unix or linux operating system. The chmod command is used to change the file or directory access permissions.
Syntax: chmod [options] permissions filename There are three different permissions. They are: Read (4): Permitted to read the contents of the file. In case of directory, you can view all the files and sub-directories in that directory Write (2): Permitted to write to the file. In case of directory, you can create files and sub-directories
Execute (1): Execute the file as a program/shell script. In case of directory, You can enter into that directory. Here in the above, the numbers in the brackets represents the numeric values for the corresponding permissions. If you want to have a combination of permissions add the required numbers. For example, for read and execute, it is 4+1= 5. chmod [options] -R: recursively change the permissions of a directory. -v: Verbose Chmod Examples in Linux / Unix: 1. Give read, write and execute permissions to everyone. Read, write and execute: 4+2+1=7 $ chmod 777 sample.sh In the above example, you can see that the permissions are specified with a three digit number. The first digit is for user permissions, second is for group and third is for others permission. This type of representation is called octal representation. Alternatively, you can use the symbolic representation to give the permissions. chmod ugo+rwx sample.sh We will see more details about the symbolic representation later.
2. Give read permission to user, write permission to group and execute permission to others $ chmod 421 sample.sh
3. Recursive permissions to directory To give read and write permissions to all the users to a directory (including files and subdirectories) use the recursive option -R. chmod -R 666 /dir Symbolic Representation of Permissions: The following symbols are used to represent the users, groups and others:
The following symbols represent the permissions:
The following symbols represent the permissions grant or revoke:
Examples 1. Remove write permission from group $ chmod g-w sample.sh This will only removes the write permission for the group. 2. Add new permission execute to others $ chmod o+x sample.sh In addition to the existing permissions, this will add execute permission to others. 3. Give only read permissions to the user $chmod u=w sample.sh This will remove the existing permissions to the user and gives only write permission to the user. |
19. man: On Linux and other Unix-like operating systems, man is the interface used to view the system's reference manuals.
Syntax: man <options> <command name> Description: man is the system's manual viewer, it can be used to display manual pages, scroll up and down, search for occurrences of specific text and other useful functions.
Each argument given to man is normally the name of a program, utility or function. The manual page associated with each of these arguments is then found and displayed. A section number, if provided, will direct man to look only in that section of the manual. The default action is to search in all of the available sections, following a pre-defined order and to show only the first page found, even if page exists in several sections, General Options
-h,--help Print a help message and exit.
-V,--version Display version information and exit
-C file,--config-file=file Use configuration file rather the defaut of ~/.man path. -d, --debug Print debugging information -D,--default This option when used, is normally specified as the first soption; it resets man's behavior to its default. Its use is to reset those options that may have been set in $MANOPT. Any options that follow -I will have their usual effect. --warnings[=wamings] Enable warnings from the groff text formatter. Warnings are a comma-separated list of warning names, if it is not supplied, the default is "mac". See the "Warnings" node the groff info page for a list of available warning names.
|
20. telnet: The telnet program is a user interface to the TELNET protocol.
Syntax: telnet [option] [host [port]] |
Description: The telnet command is used for interactive communication with another host using the TELNET protocol. It begins in command mode, where it prints a telnet command prompt ("telnet>"). If telnet is invoked with a host argument, it performs an open command implicitly (see the Commands section below for details).
Options:
-4 | Force IPv4 address resolution |
-6 | Force IPv6 address resolution |
-8 | Request 8-bit operation. This causes an attempt to negotiate the TELNET BINARYoption for both input and output. By default telnet is not "8-bit clean" (it does not recognize 8-bit character encodings such as Unicode). |
-E | Disables the escape character functionality; that is, sets the escape character to "no character". |
-L | Specifies an 8-bit data path on output. This causes the TELNET BINARY option to be negotiated on just output |
-a | Attempt automatic login. Currently, this sends the user name via the USER variable of the ENVIRON option if supported by the remote system. The username is retrieved via the getlogin system call |
-b address | Use bind on the local socket to bind it to a specific local address. |
-d | Sets the initial value of the debug toggle to TRUE. |
-r | Emulate rlogin. In this mode, the default escape character is a tilde. Also, the interpretation of the escape character is changed: an escape character followed by a dot causes telnet to disconnect from the remote host. A^Z (Control-Z) instead of a dot suspends telnet, and a ^] (Control-Close Bracket, the default telnet escape character) generates a normal telnet prompt. These codes are accepted only at the beginning of a line. |
-S tos | Sets the IP type-of-service (TOS) option for the telnet connection to the value tos. |
-eescapechar | Sets the escape character to escapechar. If no character is supplied, no escape character will be used. Entering the escape character while connected causes telnet to drop to command mode. |
-I user | Specify user as the user to log in as on the remote system. This is accomplished by sending the specified name as the USER environment variable, so it requires that the remote system support the TELNET ENVIRON option. This option implies the -a option, and may also be used with the open command. |
-n tracefile | Opens tracefile for recording trace information. See the set tracefile command below. |
Host | Specifies a host to contact over the network. |
Port | Specifies a port number or service name to contact. If not specified, the telnet port (23) is used. |
Examples:
telnet myhost.com
Attempts to open a connection to the remote host myhost.com. If a connection is established, the host will prompt for a login name and password.
telnet I myusername myhost.com:5555
Attempts to open a connection to the remote host myhost.com on port 5555, using the login name myuserrame. If successful, the host will prompt for myusername's password
21. uname: It is abbreviation for unix name. The uname command displays certain features of the operating system running on machine. By default, it simply displays the name of the operating system.
$uname
Output: Sunos Using suitable options, it can display certain key features of the operating system and also the name of the machine. The output will depend on the system. (a) The current release and implementation name (-r and -s): Since UNIX comes in many flavors, vendors have customized a number of commands to behave in the way they want and not as AT&T decreed. A UNIX command often varies across versions so much so that we'll need to use the -r option to find out the version of operating system.
$ uname –r 5.8 This is SunOS 5.8 The implementation name of this operating system can be obtained with the s option: $ uname –s SunOS
Note: The complete name of the operating system is actually a combination of the output of the two options
(b) The Machine Name (-n): If machine is connected to a network, then it must have a name (called hostname). If network is connected to the Internet, then this hostname is a component of machine's domain name. The -n option display the hostname:
$ uname -n mercury The first word of the domain name The same output would be obtained with the hostname command. To copy files from a remote machine named mercury, we have to run ftp mercury.
|
22. passwd: passwd command is used to change the password. First it prompts for the old password then it prompts for the new password and finally asks to reenter the new password.
$ passwd
passwd: Changing password for Chintamani
Enter login password: **** New password: **** Re-enter new password: ****
passwd: password successfully changed for Chintamani
|
23. stty: Displaying and Setting Terminal Characteristics. Different terminals have different characteristics and it's possible that terminal may not behave in the way we expect it to. For instance, command interruption may not be possible with system. The stty command helps to change the settings to match the ones used at previous place of work. stty uses a very large number of keywords (options that look different)
Syntax: stty [option][-][mode]
option:
-a (all): The -a option displays the current settings, $ stty –a speed 38400 baud; rows =25; columns=80; ypixels =0; xpixels=0; intr = ^c; quit =\; erase = ^; kill=^u; eof=^d;eol=<undef>; eol2^c; quit =\; erase = ; kill=^u;
eof=^d;eol=<undef>; eol2 = <undef>; swtch = <undef>; start=^; stop=^s; susp=^z; dsusp=^y: -parenb -parodd cs8 -cstopb -hupclcread - clocal -loblk -crtscts -crtsxoff-pare xt -ignbrk brkint ignpar -parmrk -inpck -istrip -inclr -igncr icrnl -iuclcixon -ixany -ixoff imaxbelisig icanon -xcase echo echoe echok-echonl - noflsh -tostop echocti -echoprt echoke -defecho -flusho -pendin iextenopost -olcuc onclr-ocrnl -onocr-onlret -ofill -ofdel tab3
Changing the settings: Whether backspacing should Erase Character(echo): The keyword echo decides whether backspacing over a character sometimes removes it from sight and sometimes doesn't. Since it is set here backspacing removes the character from display. The same keyword can be used to reverse string. stty-echoe
Entering a password through a shell script (echo): The echo setting has to be manipulated to let shell programs accept a password-like string that must not be displayed on the screen. By default, the option is turned on, but we can turn it off in the following way:
stty –echo Turns off keyboard input
Changing the end of file key(eof) When using bc, ctrl + d was used to terminate the input. Instead of ctrl +d ctrl + a can be used as the end of character.
stty eof \^a
When everything fails(sane) stty also provides another argument to set the terminal characteristics to values that will work on most terminals.
stty sane Restores sanity to the terminal |
24. The cal command: cal command is used to display the calendar. If no arguments are specified, the current month is displayed.
Syntax: cal [options] [[[day] month) year]
Options:
-1, --one Display single month output (This is the default). -3, --three Display three months spanning the date. -n. --months numbe Display number of months, starting from the month containing the date -S, --span Display months spanning the date -s, -sunday Display Sunday as the first day of the week.
|
25. The bc command: The bc command is used to for mathematical calculations. It is also called as bench calculator
Syntax:
bc [options]
Options:
-c Compile only. The output is de commands that are sent to the standard output
-1 Define the math functions and initialize scale to 20, instead of the default zero.Filename Name of the file that contains the basic calculator commands to be calculated this is not a necessary command.
Example:
1. bc
Output
bc 1.06 Copyright 1991-1994,1997,1998,2000 Free Software Foundation, Inc. This is free software with ABSOLUTELY NO WARRANTY. For details type 'Warranty'. 9*2 18
The above command used is for mathematical calculations.
2. bc -1
Output:
bc 1.06 Copyright 1991-1994, 1997,1998,2000 Free Software Foundation, Inc. This is free software with ABSOLUTELY NO WARRANTY. For details type
warranty', 1+2 3
The above command displays the sum of ‘1+2’ 3. bc calc.bxt
Output:
bc 1.06 Copyright 1991-1994 1997 1998, 2000 Free Software Foundation, Inc. This is free software with ABSOLUTELY NO WARRANTY. For details type 'warranty'.
|
26. The script command: script makes a record of everything printed on your screen. The record is written to filename. If no file name is given, the record is saved in the file 'typescript'. The script command forks and creates a sub-shell, according to the value of $SHELL, and records the text from this session. The script ends when the forked shell exits or when CTRL-D is typed.
Syntax : script [ -a ][ filename ]
Options: -a Append the session record to filename, rather than overwrite it. Note: script places everything that appears on the screen in filename, including prompts.
|
27. The date command: The date command is used to print out, or change the value of, the system's time and date information
Syntax: date [OPTION]... [+FORMAT] date [-u |-utc|--universal] [MMDDhhmm[[CC][YY][ss]]
Options: -d. --date=STRING display time described by string STRING, as opposed to the default, which is 'now' -f, --file-DATEFILE like --date, but processed once for each line of file DATEFILE. -s, --set-STRING set time described by string STRING. -u, -utc, --universal print or set Coordinated Universal Time. -help Display a help message and exit. --version Display version information and exit. Date Format
Format is a sequence of characters which specifies how output will appear. It comprises some combination of the following sequences:
%% a literal percent sign ("%"). %a The abbreviated weekday name (e.g., Sun). %A The full weekday name (e.g., Sunday). %b The abbreviated month name (e-g. Jan). %B locale's full month name (e.g., January). %c The date and time (e.g., Thu Mar 3 23:05:25 2005). %C The current century; like %Y, except omit last two digits (e.g, 20)
date examples
date
Running date with no options will output the system date and time, as in the following output: Thu Feb 8 16:47:32 MST 2001
date -s "11/20/2003 12:48:00”
Set the system date and time to November 20, 2003, 12:48 PM. date "+DATE: %m/%d/%y%n TIME: %H:%M:%S"
Outputs the date and time in the following format:
DATE: 02/08/21
TIME: 16:44:55
|
28. The we command : Displaying number of new lines words, and character in a file.
Syntax : wc [OPTIONS]…[FILE]. Option:
-c, --bytes : print the byte counts -m, -chars : print the character counts -1 –lines : print the newline counts
|
29. The gzip and gunzip command: Compressing and decompressing files
A gzip command is used to compress a file. It provides the extension .gz to the compressed filename and removes the original. To check whether the file is compressed or not,we note the file size, both before and after compressing, using wc -c command.
Snytax:
$ wc –c file1 456 file1 $ gzip file1 $ wc-c file1.gz 156 file1 $ gzip file1 file2
Option:
-1: If we want to know how much compression we have achieved for both files, we use -l option.
$ gzip –1 file1 file2
Compressed uncompressed ratio uncompressed name 156 456 79.6% file1 456 756 65.5% file2 612 1212 78.4% (totals) -d: To uncompress/decompress a file, use -d option or gunzip command.
$ gzip -d file1.gz Or $ gunzip file1.gz
-r: Like cp, we can also compress and decompress a directory structure with option
$ gzip -r doc //it will compress the entire file in the doc directory. Similarly we can decompress all the files in the doc directory with following command,
$ gunzip –r doc
|
30. lp command : The direct access to printer is not allowed to any user. Instead, spooling of job has to be performed along with others in the print queue. Spooling ensures the orderly printing of jobs and relieves the user from the necessity of administering the print resources. The spooling facility in System V is provided by the lp (line print) command.
Syntax: Lp -I request-ID (option) file nam
Example:
To print a file named rfc882.ps lp command is used in the following way: $ lp rfc882.ps request Id Is prl_320 (1 file) $_ The lp command returns the prompt immediately after the output. lp options:
-d: lp accepts the command as a default printer has been defined. If more than one printer is attached then we can use -d option with the printers name. lp-dlaser chap01.ps
-t: The -t(title) option followed by the title string prints the title on the first page. lp--t*First chapter* chap01.ps
-m: The -m(mail) option is used to notify the user that the file has been printed. Multiple copies of the same file can be printed by using the -n option. lp-n3-m chap01.ps
|
31. od command: od command is used to display the non-printing characters with octal values. The -b option displays this value for each character separately.
$ od -b file 0000000 127 150 151 164 145 040 163 160 141 143 145………….. $ od -bc file 0000000 127 150 151 164 145 040 163 160 141 143 145………….. W h I t e s p a c e………………
|
In the above example with -c option it will display the octal representation in first line and the printable characters and escape sequences are shown in second line. The first character in the first line is the letter W having the octal value 127.
32. tar: For creating a disk archive that contains a group of files or an entire directory structure, tar command is used. This command comes with the following key options:
Only one option at a time can be used. To compress and decompress gzip and gunzip are used respectively.
1. Creating an Archive: To create an archive, the name of the archive has to be specified with -f option, the copy or write operations as -c and filenames as arguments. Additionally -v option is used to display the progress while the tar command works.
$ tar -cvf archive.tar libc.html User_Guide.ps a libc.html 3785K a User_Guide.ps 364K
Using gzip with tar: If the created file is very big, the compression of the file is done in the following way using the gzip command:
gzip archive.tar Archived and compressed.
The above command creates a "tar-gzipped" file,archive.tar.gz. This file can then be sent out by ftp or as an email attachment.
2. Extracting file from the archive (-x): tar uses -x option to extract files from an archive.
tar -xvf progs.tar Extracts three directories
To extract any file using tar command the file has to be to be unzipped first using gunzip command and then it is extracted.
$ gunzip archive.tar.gz Retrieves archive.tar
$ tar -xvf archive.tar Extract files
x libc.htm, 3875302 bytes, 7569 tape blocks x User_Guide.ps,372267 bytes, 728 tape blocks
To extract a single file from the archive following command can be used:
tar -xvf archive.tar User guide.ps
3. Viewing the archive (-t): To view the archive -t(table of contents) option is used. It doesn't extract the files; it normally shows the attributes of the files.
Star-tvf archive.tar -rw-r-r-102/10 3875302 Aug 24 19:49 2002 libc.html -rw-r---102/10 372267 Aug 24 19:48 2002 User_Guide.ps
|
33. df : Reporting free space
The operating system is supported by multiple file systems. The df (disk free) command reports the amount of free space available for each file system separately:
#df / (/dev/dsk/c0t0d0s0):3491876 blocks 483932 files /usr (/dev/dsk/cotod0s4):2434820 blocks 458466 files /proc (/proc ): 0 blocks 15875 files /dev/fd (fd): 0 blocks 0 files /etc/mnttab (mnttab): 0 blocks 0 files
The above output is inferred as, from the first line we can say that the root file system (/) has 3491876 blocks of disk space free. It also has 483932 inodes free.
The-t (total) option include the above output as well as the total free space in the file system. -k option is the informative option which reports the free space in units of KB.
$ df -k// usr |
34. du: Disk Usage
du is the command which reports the usage of disk by recursive examination of the directory tree.
Example:
#du/home/sales/tml
11554 /home/sales/tml/forms 12820 /home/sales/tml/data ………. 25170 /home/sales/tml
By default, du lists the usage of each subdirectory of its argument and finally produces a summary.
To enlist the summary of the usage -s option can be used.
#du-s /home/sales/tml
25170 /home/sales/tml
Most of the dynamic space is used by the users' home directories and data files. du with -s command can be used to report each user's home directory.
#du-s /home/*
144208 /home/henry 98920 /home/image
du with -a command can also report each file in a directory
|
35. Mount: When mounting a new file system, it takes two arguments - the device name of the file system and the mount point. Before mounting a file system, an empty directory must be made available in the main file system. The root directory of the new file system has to be mounted on this directory. mount uses an option to specify the type of the file system.
mount-t ext2 /dev/hda3/oracle linux |
36. Umount: Unmounting is achieved with the umount command which requires either the file system or mount point as argument
unmount /oracle
unmount /dev/hda3
Unmounting a file system is not possible if the file is open.
37. nl command: nl is a Unix utility for numbering lines, either from a file or from standard input, reproducing output on standard output.
Snytax: nl [option] filename Options:
-b, --body-numbering=STYLE use STYLE for numbering body lines -i, --line-increment=NUMBER line number increment at each line -1, -join-blank-lines=NUMBER group of NUMBER empty lines counted as one -n, -number-format=FORMAT insert line numbers according to FORMAT -v, --starting-line-number=NUMBER first line number on each logical page -w. --number-width=NUMBER use NUMBER columns for line numbers
STYLE is one of:
A number all lines T number only nonempty lines N number no lines
FORMAT is one of:
1n left justified, no leading zeros Rm right justified, no leading zeros Rz right justified, leading zeros
Example:
$ cat fruit.txt
mango apple banana litchie orange
$ nl frult.txt
1 mango 2 apple 3 banana 4 litchie 5 orange
$ nl i5 fruit.txt
1 mango 6 apple 11 banana 16 litchie 21 orange
The following example numbers only the lines that begin with a capital letter A (matching on the regular expression /^A/), filename is optional.
$nl -b p^A filename apple
1 Apple BANANA
2 Allspice strawberry
|
38. Page/pg:
Description: Display all or parts of a file, type q to quit, press space bar to continue Syntax:
$ page [option](file list) $pg [option] file list
Options:
-c Clears the screen before displaying the next page of the file. This can be quicker than watching pages scroll by. -d Displays a prompt at the bottom of the screen-involving brief instructions. -f Wrap text to fit the screen width and judges the page length accordingly. -1 Ignore form feeds at the end of a page. -s Squeeze ignores multiple blank lines.
The following commands may be entered at the prompt. Commands preceded by i accept a number as argument, positive or negative. If this argument starts with + or -, it is interpreted relative to the current position in the input file, otherwise relative to the beginning.
I<newline> Display the next or the indicated page. id, ^D Display the next halfpage. If i is given, it is always interpreted relative to the current position /1 Display the next or the indicated line. /f Skip a page forward. i must be a positive number and is always interpreted relative to the current position iw, iz Behave as <newline> except that i becomes the new page size. .,^L Redraw the screen. $ Advance to the last line of the input file. /n Advance to the next file or i files forward. /p Reread the previous file or i files backward. q,Q Quit
|
39. Join Command: Join command is one of the text processing utility in Unix/Linux Join command is used to combine two files based on a matching fields in the files. If we know SQL, the join command is similar to joining two tables in a database.
Syntax : Join [options] file1 file2 options:
-1 field number: Join on the specified field number in the first file. -2 field number: Join on the specified field number in the second file. -j field number Equivalent to -1 fieldnumber and -2 fieldnumber. -o list : displays only the specified fields from both the files. -t char: input and output field delimiter. -a filenumber: Prints non matched lines in a file. -i: ignore case while joining.
Examples of the unix join command :
$ cat 1.txt
1 abc 2 Imn 3 pqr
$ cat 2.txt
1 abc 3 Imn 9 opq
$ join 1.txt 2.txt
1 abc abc 3 pgr Imn
Since the two files are trying to match on the 1st column, and both have a 1 and a 3 in that column. To tell join to use the second column to join with, we type: $join -1 2 -2 2 1.txt 2.txt
* (where "-1 2" stands for the 2nd field of the 1st file, and "-2 2" stands for the 2nd field of the 2nd file.
abc 1 1 Imn 2 3
which are just those fields that match in both files. This is referred to as an inner join. Inner joins look for rows that match rows in the other table. The problem with inner joins is that only rows that match between tables are returned.
$ join -a1 -1 2 -2 2 1.txt 2.txt
#(where "-al" says include all the records from the first file).
abc 1 1
Imn 2 3
pqr 3
this is missing a number for pqr for the second file (since there is no pqr in that file) and is missing "9 opq" from the second file. This is an example of a left outer join, called such because it includes all of the rows from the left (or first) file specified.
$ join -a1 -a2 -1 2 -2 2 1.txt 2.txt #(adding "-a2" to tell join to also include all records from the second file).
abc 1 1 Imn 2 3 opq 9 pqr 3
Which has all of the records. This is an example of a full outer join since it has all of the rows from both files. (Missing from these examples is the case where we had the -a2 without the -al. That would have produced a right outer join which contained all of the records from the second (right) file and only those rows from the first (left) file that matched).
While this example has all of the rows from both files, we still have a problem since we cannot tell which file the count is for on the last two records.
|
40. ftp command (protocol).
ftp command is used to ftp protocol using which files are transferred over two systems.
Syntax :
ftp [option] hostname Option :
(i) -d - enable debugging. (ii) -g - disable filename globbing. (iii) -i - turn off interactive prompts. (iv) -v - verbose on show all responses from remote server.
ftp hostname by default will connect to the system, it must have a login id to be able to transfer the files. Two types of files can be transferred, ASCII or Binary. Bin at ftp> prompt will set the transfer to binary.
|
41. Rlogin command:
rlogin command is used to log on to remote Unix systems, user must have permissions on both systems as well as same userid, or an id defined in remote hosts file.
Syntax: rlogin [option] host Option: (i) -8 - will allow 8 bit data to pass, instead of 7-bit data. (ii) -e c -will use escape character c. (iii) -l user - will login as user to remote host, instead of same as local host. |
42. Talk command:
talk command is used to invoke talk program available on all unix system which lets two users exchange information back and forth in real time.
Syntax: talk userid@hostname
|
43. The finger command :
Finding Out who's logged in, in detail
$ finger Login Name TTY Idle when where
Albert Albert sahu pts/19 Fri 09:40 (172.16.0.19) Robert Robert dewangan pts/29 12 Fri 14:40 (172.16.0.16) Sam Sam verma pts/39 16 Fri 16:40 (172.16.0.20)
The first column shows the user's name. There are 3 users currently working on the system. The second column shows the full name of the user. The third field shows their terminals preceded by an asterisk if the terminal doesn't have write permission. Fourth column shows the idle time - the time that has elapsed since the last keystroke was entered. The last column shows the machine id from where the user logged in
Like who command, finger command can also provide details about single user.
$ finger Albert
Login Name: Albert Directory: /home /users/ Albert shell: /usr/bin/bash On since Jan 13 12:56:33 on pts/4 from 172.16.0.15 No mail No plan
|
44. cpio command: cpio command is useful to backup the file systems. It copy file archives in from or out to tape or disk, or to another location on the local machine.
Syntax: cpio flags [options]
flags: -i, -o, -p
cpio -i [options] [patterns]
cpio -i copy in files whose name matches selected patterns. If no pattern is used all files are copied in. It is used to write to a tape.
cpio –o : Copy out a list of files whose names are given on standard output cpio –p : Copy files to another directory on the same system.
Options :
(i) t - Lists files in archive (must use with -i). (ii) c - Read or write header information as ASCII character. (iii) d - Create directories as needed. (iv) 1 - Link files instead of copying. (v) o file - Direct output to a file. (vi) r - Rename files interactively. (vii) RID - Reassign file ownership and group information to the user's login ID. (viii) - Print a list of filenames. (ix) fexp - Copies all files except those in exp.
Examples
$ ls | cpio-ov > /dev/rdsk/abc
Array.pl Calendar Script44.sh 246 blocks
$ cpio -iv < /dev/rdsk/abc
Array.pl Calendar Script44.sh 256 blocks
$ cpio -- "*.c"< /dev/rdsk/abc $ cpio ivf "*.c"< /dev/rdsk/abc
#it will select all files except those in the expression i.e. file with .c extension.
|
UNIX File System: All data in UNIX is arranged in files, so it is essential to understand the UNIX file system, both on a logical level and also as it is implemented on the physical device. UNIX treats everything it knows and understands as a file. A file to UNIX is an array of bytes and its size is simply equal to the number of bytes present in it. For UNIX, even directories and devices are files. A file can contain text, object code or a directory structure. The dominant file type is text, which contains a series of bytes, sometimes with a suitable delimiter to separate fields. The UNIX system features a host of tools that can be used with such files. In UNIX, all files have places, and are collectively arranged as a top down tree structure.
Features of UNIX file System:
1. Hierarchical structure:
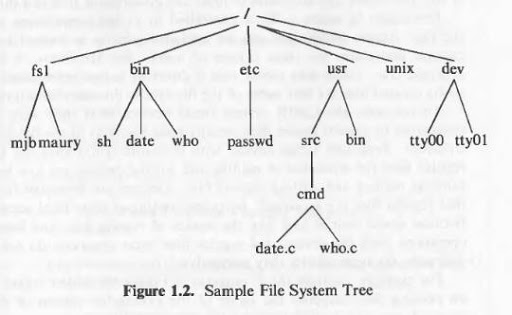
(i) The file system is organized as a tree with a single root node called root (written "/"); every non-leaf node of the file system structure is a directory of files, and files at the leaf nodes of the tree are either directories, regular files, or special device files.
(ii) The name of a file is given by a path name that describes how to locate the file in the file system hierarchy. A path name is a sequence of component names separated by slash characters; a component is a sequence of characters that designates a file name that is uniquely contained in the previous (directory) component
(iii) A full path name starts with a slash character and specifies a file that can be found by starting at the file system root and traversing the file tree, following the branches that lead to successive component names of the path name.
(iv) Thus, the path names "/etc/passwd", "/bin/who", and "/usr/src/cmd/who.c" designate files in the tree shown in figure but "/bin/passwd" and "/usr/src/date.c" do not.
|
(v) A path name does not have to start from root but can be designated relative to the current directory of an executing process, by omitting the initial slash in the path name. Thus, starting from directory "/dev", the path name "tty01" designates the file whose full path name is "/dev/tty01".
2. Consistent treatment of file data UNIX imposes no format what so ever on the contents of a file. For it all files are just streams of bytes. Any format that is imposed is done by the utility that creates these files and not the UNIX operating system. For example, C programs must have a .c extension, this is the requisite of C compiler. A UNIX file does not contain the end-of-file mark or its name.
3. The ability to create and delete files: Permission to access a file is controlled by access permissions associated with the file. Access permissions can be set independently to control read, write, and execute permission for three classes of users: the file owner, a file group, and everyone else. Users may create files if directory access permissions allow it. The newly created files are leaf nodes the file system directory structure.
4. Dynamic growth of files: The size of a file is only restricted by the amount of disk-storage available. The sizes of the files and the number of files can be dynamically modified.
5. The protection of file data: UNIX provides security at different levels. Files are protected using file ownership mechanisms. The users are divided into three groups and each group is granted access or denied access in terms of read, writes and executes permissions for each file separately.
6. Treatment of peripheral devices (such as terminals and tape units) as files: As devices and directories are also treated as files in UNIX, user does not need to know the details of device related operations and procedures.
References
- Sumitabha Das: UNIX – Concepts and Applications, 4th Edition, Tata McGraw Hill, 2006.
- Behrouz A. Forouzan and Richard F. Gilberg: UNIX and Shell Programming, Cengage Learning, 2005.
- M.G. Venkateshmurthy: UNIX & Shell Programming, Pearson Education, 2005.