UNIT 1
INTRODUCTION TO COMPUTER HARDWARE AND SOFTWARE
1940 – 1956: First Generation – Vacuum Tubes
- These early computers used vacuum tubes as circuitry and magnetic drums for memory. As a result they were enormous, literally taking up entire rooms and costing a fortune to run.
- These were inefficient materials which generated a lot of heat, sucked huge electricity and subsequently generated a lot of heat which caused ongoing breakdowns.
- These first generation computers relied on ‘machine language. These computers were limited to solving one problem at a time.
- Input was based on punched cards and paper tape.
- Output came out on print-outs.
- The two notable machines of this era were the UNIVAC and ENIAC machines – the UNIVAC is the first every commercial computer which was purchased in 1951 by a business – the US Census Bureau.
1956 – 1963: Second Generation – Transistors
- The replacement of vacuum tubes by transistors saw the advent of the second generation of computing. Although first invented in 1947, transistors weren’t used significantly in computers until the end of the 1950s.
- They were a big improvement over the vacuum tube, despite still subjecting computers to damaging levels of heat. However, they were hugely superior to the vacuum tubes, making computers smaller, faster, cheaper and less heavy on electricity use. They still relied on punched card for input/printouts.
- The language evolved from cryptic binary language to symbolic (‘assembly’) languages. This meant programmers could create instructions in words.
- About the same time high level programming languages were being developed (early versions of COBOL and FORTRAN). Transistor-driven machines were the first computers to store instructions into their memories – moving from magnetic drum to magnetic core ‘technology’. The early versions of these machines were developed for the atomic energy industry.
1964 – 1971: Third Generation – Integrated Circuits
- By this phase, transistors were now being miniaturised and put on silicon chips (called semiconductors). This led to a massive increase in speed and efficiency of these machines.
- These were the first computers where users interacted using keyboards and monitors which interfaced with an operating system, a significant leap up from the punch cards and printouts.
- This enabled these machines to run several applications at once using a central program which functioned to monitor memory.
- As a result of these advances which again made machines cheaper and smaller, a new mass market of users emerged during the ‘60s.
1972 – 2010: Fourth Generation – Microprocessors
- This revolution can be summed in one word: Intel. The chip-maker developed the Intel 4004 chip in 1971, which positioned all computer components (CPU, memory, input/output controls) onto a single chip.
- The Intel chip housed thousands of integrated circuits. The year 1981 saw the first ever computer (IBM) specifically designed for home use and 1984 saw the MacIntosh introduced by Apple.
- Microprocessors even moved beyond the realm of computers and into an increasing number of everyday products.
- The increased power of these small computers meant they could be linked, creating networks. Which ultimately led to the development, birth and rapid evolution of the Internet. Other major advances during this period have been the Graphical user interface (GUI), the mouse and more recently the astounding advances in lap-top capability and hand-held devices.
2010- : Fifth Generation – Artificial Intelligence
- Computer devices with artificial intelligence are still in development, but some of these technologies are beginning to emerge and be used such as voice recognition.
- AI is a reality made possible by using parallel processing and superconductors. Leaning to the future, computers will be radically transformed again by quantum computation, molecular and nano technology.
- The essence of fifth generation will be using these technologies to ultimately create machines which can process and respond to natural language, and have capability to learn and organise themselves.
Bit = Binary digIT = 0 or 1
Byte = a sequence of 8 bits = 00000000, 00000001, ..., or 11111111
Word = a sequence of N bits where N = 16, 32, 64 depending on the computer
Processor (CPU / Central Processing Unit)
|
|
|
|
|
Internal Memory (RAM and ROM)
There are two types of internal memory – RAM and ROM.
RAM and ROM are used to store computer data which can be accessed by the CPU.
RAM and ROM are referred as “Primary Storage”
RAM (Random Access Memory)
- RAM is used to temporarily store information that is currently in use by the computer. This can include anything from word documents to videos.
- RAM can be read from and written to and so the information stored in RAM can change all the time.
- RAM is a fast memory. Data can be written to and read from RAM very quickly. RAM is generally measured in GB (Gigabytes).
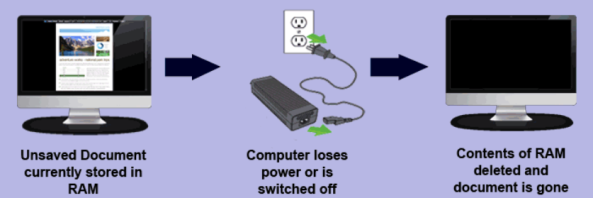
- RAM is Volatile Memory. This means that information stored in RAM is deleted as soon as the computer is turned off.
|
ROM (Read Only Memory)
- ROM is used to permanently store instructions that tell the computer how to boot (start- up). It also loads the operating system (e.g. Windows).
These instructions are known as the BIOS (Basic input/output system) or the boot program. - Information stored in ROM is known as READ ONLY. This means that the contents of ROM cannot be altered or added to by the user.
- ROM is fast memory. Data stored in ROM can be accessed and read very quickly.
- ROM is Non-Volatile memory. This means that stored information is not lost when the computer loses power.
- Other examples of ROM include:
- DVD/CD ROMS bought in stores containing pre-recorded music and movie files. These are played back at home but cannot be altered.
- ROM in printers which is used to store different font types.
Memory:
A memory is used to store data and instructions. Computer memory is the storage space in the computer, where data is to be processed and instructions required for processing are stored. The memory is divided into large number of small parts called cells. Each location or cell has a unique address, which varies from zero to memory size minus one.
For example, if the computer has 64k words, then this memory unit has 64 * 1024 = 65536 memory locations. The address of these locations varies from 0 to 65535.
Memory is primarily of three types −
- Cache Memory
- Primary Memory/Main Memory
- Secondary Memory
Cache Memory
Cache memory is a high -speed semiconductor memory which can speed up the CPU. It acts as a buffer between the CPU and the main memory. It is used to hold those parts of data and program which are most frequently used by the CPU. The parts of data and programs are transferred from the disk to cache memory by the operating system, from where the CPU can access them.
Advantages
The advantages of cache memory are as follows −
- Cache memory is faster than main memory.
- It consumes less access time as compared to main memory.
- It stores the program that can be executed within a short period of time.
- It stores data for temporary use.
Disadvantages
The disadvantages of cache memory are as follows −
- Cache memory has limited capacity.
- It is too expensive.
Primary Memory (Main Memory)
Primary memory holds only those data and instructions on which the computer is currently working. It has a limited capacity and data is lost when power is switched off. It is generally made up of semiconductor device. These memories are not as fast as registers. The data and instruction required to be processed resides in the main memory. It is divided into two subcategories RAM and ROM.
Characteristics of Main Memory
- These are semiconductor memories.
- It is known as the main memory.
- Usually volatile memory.
- Data is lost in case power is switched off.
- It is the working memory of the computer.
- Faster than secondary memories.
- A computer cannot run without the primary memory.
Secondary Memory
This type of memory is also known as external memory or non-volatile. It is slower than the main memory. These are used for storing data/information permanently. CPU directly does not access these memories, instead they are accessed via input-output routines. The contents of secondary memories are first transferred to the main memory, and then the CPU can access it. For example, disk, CD-ROM, DVD, etc.
Characteristics of Secondary Memory
- These are magnetic and optical memories.
- It is known as the backup memory.
- It is a non-volatile memory.
- Data is permanently stored even if power is switched off.
- It is used for storage of data in a computer.
- Computer may run without the secondary memory.
- Slower than primary memories.
A port is a physical docking point using which an external device can be connected to the computer. It can also be programmatic docking point through which information flows from a program to the computer or over the Internet.
Characteristics of Ports
A port has the following characteristics −
- External devices are connected to a computer using cables and ports.
- Ports are slots on the motherboard into which a cable of external device is plugged in.
- Examples of external devices attached via ports are the mouse, keyboard, monitor, microphone, speakers, etc.
Input and output devices allow the computer system to interact with the outside world by moving data into and out of the system. An input device is used to bring data into the system. Some input devices are:
- Keyboard
- Mouse
- Microphone
- Bar code reader
- Graphics tablet
An output device is used to send data out of the system. Some output devices are:
- Monitor
- Printer
- Speaker
Input/output devices are usually called I/O devices. They are directly connected to an electronic module inside the systems unit called a device controller.
For example, the speakers of a multimedia computer system are directly connected to a device controller called an audio card (such as a Soundblaster), which in turn is connected to the rest of the system.
Computers connected to a network are broadly categorized as servers or workstations.
Servers are generally not used by humans directly, but rather run continuously to provide "services" to the other computers (and their human users) on the network. Services provided can include printing and faxing, software hosting, file storage and sharing, messaging, data storage and retrieval, complete access control (security) for the network's resources, and many others.
Workstations are called such because they typically do have a human user which interacts with the network through them. Workstations were traditionally considered a desktop, consisting of a computer, keyboard, display, and mouse, or a laptop, with with integrated keyboard, display, and touchpad. With the advent of the tablet computer, and the touch screen devices such as iPad and iPhone, our definition of workstation is quickly evolving to include those devices, because of their ability to interact with the network and utilize network services.
Servers tend to be more powerful than workstations, although configurations are guided by needs. For example, a group of servers might be located in a secure area, away from humans, and only accessed through the network. In such cases, it would be common for the servers to operate without a dedicated display or keyboard. However, the size and speed of the server's processor(s), hard drive, and main memory might add dramatically to the cost of the system. On the other hand, a workstation might not need as much storage or working memory, but might require an expensive display to accommodate the needs of its user. Every computer on a network should be appropriately configured for its use.
The basic computer hardware components that are needed to set up a network are as follows −
Network Cables
Network cables are the transmission media to transfer data from one device to another. A commonly used network cable is category 5 cable with RJ – 45 connector, as shown in the image below:
Routers
A router is a connecting device that transfers data packets between different computer networks. Typically, they are used to connect a PC or an organization’s LAN to a broadband internet connection. They contain RJ-45 ports so that computers and other devices can connect with them using network cables.
Repeaters, Hubs, and Switches
Repeaters, hubs and switches connect network devices together so that they can function as a single segment.
A repeater receives a signal and regenerates it before re-transmitting so that it can travel longer distances.
A hub is a multiport repeater having several input/output ports, so that input at any port is available at every other port.
A switch receives data from a port, uses packet switching to resolve the destination device and then forwards the data to the particular destination, rather than broadcasting it as a hub.
Bridges
A bridge connects two separate Ethernet network segments. It forwards packets from the source network to the destined network.
Gateways
A gateway connects entirely different networks that work upon different protocols. It is the entry and the exit point of a network and controls access to other networks.
Network Interface Cards
NIC is a component of the computer to connect it to a network. Network cards are of two types: Internal network cards and external network cards.
Software means computer instructions or data. Anything that can be stored electronically is software in contrast to storage devices and display devices are called hardware.
A set of instructions that achieve a single outcome are called program or procedure. Many programs functioning together to do a task make a software.
An algorithm is a precise set of instructions that describes how to perform a specific task. It describes the environment and sequential/logic flow to accomplish the task.
In general programming language is a language that is used to code an algorithm in a way that a computer can eventually understand. Popular programming languages include Basic , Pascal, C++, Perl and Java.
A program is an algorithm or set of algorithms written using a programming language. Programs are often referred as code , the process of writing programs is called coding and the people who write programs are called programmers or coders.
A compiler is a special program that accomplishes this task it converts programming language instructions into machine level instructions.
An operating system (OS) is a collection of programs that coordinates the basic activities of computer system including managing computer files and communicating with the input/output and storage devices.
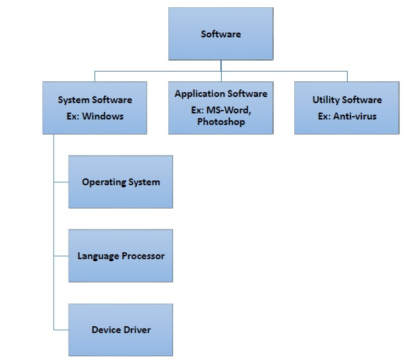
The types of software −
- System Software
- Application Software
- Utility Software
|
System Software
Software required to run the hardware parts of the computer and other application software are called system software. System software acts as interface between hardware and user applications. An interface is needed because hardware devices or machines and humans speak in different languages.
Application Software
A software that performs a single task and nothing else is called application software. Application software are very specialized in their function and approach to solving a problem. So a spreadsheet software can only do operations with numbers and nothing else. A hospital management software will manage hospital activities and nothing else. Here are some commonly used application software −
- Word processing
- Spreadsheet
- Presentation
- Database management
- Multimedia tools
Utility Software
Application software that assist system software in doing their work is called utility software. Thus, utility software is actually a cross between system software and application software. Examples of utility software include −
- Antivirus software
- Disk management tools
- File management tools
- Compression tools
- Backup tools
C program basically consists of the following parts −
Let us look at a simple code that would print the words "Hello World" –
#include <stdio.h>
int main() { /* my first program in C */ printf("Hello, World! \n");
return 0; } |
The various parts of the above program −
- The first line of the program #include <stdio.h> is a preprocessor command, which tells a C compiler to include stdio.h file before going to actual compilation.
- The next line int main() is the main function where the program execution begins.
- The next line /*...*/ will be ignored by the compiler and it has been put to add additional comments in the program. Such lines are called comments in the program.
- The next line printf(...) is another function available in C which causes the message "Hello, World!" to be displayed on the screen.
- The next line return 0; terminates the main() function and returns the value 0.
A C program source code can be written in any text editor; however, the file should be saved with .c extension. First C Program
#include<stdio.h> int main() { int num; printf("Enter your age: "); scanf("%d", &num); if (num <18) { printf("you are not eligible for voting"); } else { | ||
printf("You can vote!!"); } return 0; } Output:
Enter your age:25 Lets understand this Program: Comment: Comment start with’ /*’ and end with ‘*/’. Comments are not mandatory but still it’s a good practice if you use them, it improves the readability of the code. A program can have any number of comments. | ||
Include section: While writing program we use several keywords & statements and functions such as printf(), scanf() etc. The file that has definitions of these functions needs to be included in the program.
In the above program we have used stdio.h. There are several libraries and “stdio.h” is one of them, which is used for reading the data from terminal and to display the data on terminal.
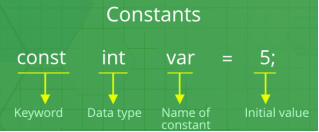
Constant:
|
- Constants refer to fixed values that the program may not alter during its execution. These fixed values are also called literals.
- Constants can be of any of the basic data types like an integer constant, a floating constant, a character constant, or a string literal. There are enumeration constants as well.
- Constants are treated just like regular variables except that their values cannot be modified after their definition.
In C/C++ program we can define constants in two ways as shown below:
- Using #define preprocessor directive
- Using a const keyword
Variables:
Variables are the names you give to computer memory locations which are used to store values in a computer program.
Here are the following three simple steps −
- Create variables with appropriate names.
- Store your values in those two variables.
- Retrieve and use the stored values from the variables.
When creating a variable, we need to declare the data type it contains.
Data types:
Programming languages define data types differently.
For example, almost all languages differentiate between ‘integers’ (or whole numbers, eg 12), ‘non-integers’ (numbers with decimals, eg 0.24), and ‘characters’ (letters of the alphabet or words).
- char – a single 16-bit Unicode character, such as a letter, decimal or punctuation symbol.
- boolean – can have only two possible values: true (1) or false (0). This data type is useful in conditional statements.
- byte - has a minimum value of -128 and a maximum value of 127 (inclusive).
- short– has a minimum value of -32,768 and a maximum value of 32,767
- int: – has a minimum value of -2,147,483,648 and a maximum value of 2,147,483,647 (inclusive).
- long – has a minimum value of -9,223,372,036,854,775,808 and a maximum value of 9,223,372,036,854,775,807 (inclusive).
- float – a floating point number with 32-bits of precision
- double – this is a double precision floating point number.
- The symbols that are used to perform logical and mathematical operations in C are called C operators.
- The C operators join individual constants and variables to form expressions.
- Operators, functions, constants and variables are combined together to form expressions.
OPERATORS | |
Mathematical | Addition(+) |
Subtraction(-) | |
Multiplication(*) | |
Division(/) | |
Modulus(%) | |
Power(^) | |
Relational | Less than(<) |
Greater than(>) | |
Less than or equal to(<=) | |
Greater than or equal to(>=) | |
Equal to (=) | |
Not equal to(<>) | |
Logical | NOT |
AND | |
OR | |
Expression
Expression is a code segment that is evaluated to give a single value. It only processes data with the help of operators.
E.g. : A+B
Here A+B is processed but not stored.
Writing Computer Expression
Certain rules must be followed while writing computer expression.
- All variables, constants and operators must be on same line.
- Operator must be between variables and/or constants. No operators are assumed. Every operator must be written explicitly.
- Parentheses are added when hierarchy has to be reordered.
Let us consider following expression : A (2B + 4) – Applying above rules appropriate computer expression becomes : A*(2*B + 4) – 4 * B / (A + 9)
|
Evaluating Mathematical Expression |
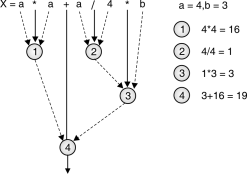
Let us consider mathematical expression: X = a2+a/4*b It can be written as X = a * a + a / 4 * b Mathematical expression must be evaluated according to hierarchy of operators. Expression is evaluated from left to right.
|
Fig.: Evaluating mathematical expression
Fig. shows how mathematical expression is evaluated according to hierarchy of operators. Solid line leading to a circle indicates operator and dashed line indicates operand.
1. Moving from left to right a*a will be evaluated first①.
2. According to hierarchy a/4 will be evaluated second ②.
3. The output obtained from②will then be multiplied with b.
4. The resultant③will then be added to①.
Ex. 1.5.1
Evaluate the following equations given P=3,Q=6,R=5,S=10.
Soln. :
We will use above technique to solve the problem :
(a) X=P*Q+S/R
Substituting values we get : X = 3 * 6 + 10 / 5 Solving according to hierarchy of operators X = 18 + 2 X = 20 |
(B) S MOD P*Q
Substituting values we get : 10 MOD 3 * 6 Solving according to hierarchy of operators → 1*6 → 6 |
(C) 7*P/S*(Q+1)
Substituting values we get : →7 * 3/10*(6+1) Solving according to hierarchy of operators → 21/10*(7) → 2*7 →14 |
(D) F = (P + 7 – R) MOD Q
Substituting values we get : F = (3 + 7 – 5) MOD 6 Solving according to hierarchy of operators F = 5 MOD 6 F = 5 |
(E) (R * (Q + 3 *P) + 5 *P )/R
Substituting values we get
→ (5*(6 + 3* 3)+5 * 3)/5 Solving according to hierarchy of operators → (5*(6+9)+5*3)/5 → (5*15+15)/5 → (75 +15)/5 → 90/5 |
→ 18
Evaluating Relational Expression
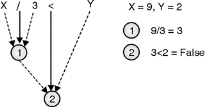
Let us consider relational expression : X / 3<Y
Relational expression must be evaluated according to hierarchy of operators. Expression is evaluated from left to right.
|
Fig: Evaluating relational expression
Fig. shows how relational expression is evaluated according to hierarchy of operators. Solid line leading to a circle indicates operator and dashed line indicates operand.
- Moving from left to right X/3would be evaluated first①.
- ① is compared with Y to give ②.
- Output is False.
Ex.
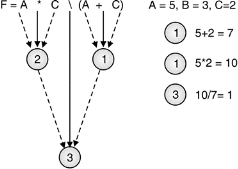
Evaluate for A = 5, B = 3 and C = 2 :(i) F=A*C / (A+C) (ii) F = (C * (B + 3 * A) + 5 * A)/C.
Soln. :
i) F = A*C / (A+C)
Let us consider mathematical expression.
Fig.: Evaluating mathematical expression |
F = A*C / (A+C)
Mathematical expression must be evaluated according to hierarchy of operators. Expression is evaluated from left to right.
Solid line leading to a circle indicates operator and dashed line indicates operand.
- Moving from left to right (A + C) would be evaluated first .
- According to hierarchy A*C would be evaluated second.
- The output obtained from will be divided by to get
Output is 1.
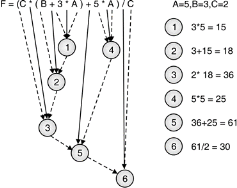
ii) F = (C*(B+3*A)+5*A)/C
Let us consider mathematical expression.
F = (C*(B+3*A)+5*A)/C
Mathematical expression must be evaluated according to hierarchy of operators. Expression is evaluated from left to right.
|
Fig. : Evaluating mathematical expression
- Let us consider logical expression.
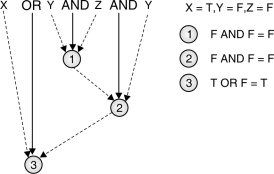
X OR Y AND Z AND Y
- Logical expression must be evaluated according to hierarchy of operators. Expression is evaluated from left to right.
|
Fig.: Evaluating Logical expression
Fig. shows how logical expression is evaluated according to hierarchy of operators. Solid line leading to a circle indicates operator and dashed line indicates operand.
- Moving from left to right Y AND Zwould be evaluated first①as AND has higher priority than OR.
- According to hierarchy①and Ywould be evaluated second②.
- OR operation will be performed on X and output obtained from②.
- The resultant is③.
Ex.
Evaluate the following Equations given P = False, Q = True, R = False, S = True
(a) X=P AND Q OR R AND S (b) X=NOT ( P AND Q) OR NOT(S AND R)
(c) X=(P OR Q) AND (S OR R) (d) X=NOT (P AND Q OR R) AND (P OR Q AND S)
Soln. :
(a) X = P AND Q OR R AND S
= F AND T OR F AND T=F OR F
= F
(b) X = NOT ( P AND Q) OR NOT(S AND R)
= NOT(F AND T)OR NOT(T AND F)
= NOT(F)OR NOT(F)=T OR T
= T
(c) X = (P OR Q) AND (S OR R)
= (F OR T ) AND (T OR F)=T AND T
= T
(d) X = NOT (P AND Q OR R) AND (P OR Q AND S)
= NOT (F AND T OR F) AND (F OR T AND T)
= NOT (F) AND (T)=T AND T
= T
References:
- The C programming language by Dennis Ritchie
- C programming by K.N. King
- The Complete Reference C Fourth Edition by Herbert Schilt
- Computer Fundamentals and Programming in C by Reema Theraja.
- C in a nutshell by Peter Prinz.