UNIT 5
Q1 What is database security?
Answer 1
Database Security
- Database security encompasses a range of security controls designed to protect the Database Management System (DBMS).
- Database security is the technique that protects and secures the database against intentional or accidental threats.
- Security concerns will be relevant not only to the data resides in an organization's database: the breaking of security may harm other parts of the system, which may ultimately affect the database structure.
- Database security includes hardware parts, software parts, human resources, and data. To efficiently do the uses of security needs appropriate controls, which are distinct in a specific mission and purpose for the system.
- The types of database security measures your business should use include protecting the underlying infrastructure that houses the database such as the network and servers), securely configuring the DBMS, and the access to the data itself.
- Database security consider
- Theft and fraudulent.
- Loss of confidentiality or secrecy.
- Loss of data privacy.
- Loss of data integrity.
- Loss of availability of data.
Database security controls: - Database security encompasses multiple controls, including system hardening, access, DBMS configuration, and security monitoring. These different security controls help to manage the circumventing of security protocols.
System hardening and monitoring: - The underlying architecture provides additional access to the DBMS. It is vital that all systems are patched consistently, hardened using known security configuration standards, and monitored for access, including insider threats.
DBMS configuration:-It is critical that the DBMS be properly configured and hardened to take advantage of security features and limit privileged access that may cause a misconfiguration of expected security settings. Monitoring the DBMS configuration and ensuring proper change control processes helps ensure that the configuration stays consistent.
Authentication Database security measures include authentication, the process of verifying if a user’s credentials match those stored in your database, and permitting only authenticated user’s access to your data, networks, and database platform.
Access A primary outcome of database security is the effective limitation of access to your data. Access controls authenticate legitimate users and applications, limiting what they can access in your database. Access includes designing and granting appropriate user attributes and roles and limiting administrative privileges.
Database auditing Monitoring (or auditing) actions as part of a database security protocol delivers centralized oversight of your database. Auditing helps to detect, deter, and reduce the overall impact of unauthorized access to your DBMS.
Backups A data backup, as part of your database security protocol, makes a copy of your data and stores it on a separate system. This backup allows you to recover lost data that may result from hardware failures, data corruption, theft, hacking, or natural disasters.
Encryption Database security can include the secure management of encryption keys, protection of the encryption system, management of a secure, off-site encryption backup, and access restriction protocols.
Application security Database and application security framework measures can help protect against common known attacker exploits that can circumvent access controls, including SQL injection.
Importance of Database Security
- Safeguarding the data your company collects and manages is of utmost importance.
- It can guard against a compromise of your database, which can lead to financial loss, reputation damage, consumer confidence disintegration, brand erosion, and non-compliance of government and industry regulation.
- Database security safeguards defend against a myriad of security threats and can help protect your enterprise from:
- Deployment failure
- Excessive privileges
- Privilege abuse
- Platform vulnerabilities
- Unmanaged sensitive data
- Backup data exposure
- Weak authentication
Q2 Explain authentication and authorization
Answer 2
Authentication
- Authentication involves the prevention of unauthorized access to computer systems.
- Authentication takes a variety of forms, ranging from verifying account credentials (using, amongst other things, a login name and password) to physical identity verification (using biometrics such as finger print scanning technology) to identifying that the client system from which a user is attempting to connect to a server is really the authorized client system.
- An authorization policy dictates what your identity is allowed to do.
- For example, any customer of a bank can create and use an identity (e.g., a user name) to log into that bank's online service but the bank's authorization policy must ensure that only you are authorized to access your individual account online once your identity is verified.
- Authentication does not give any privileges for particular tasks.
- It only establishes that the DBMS trusts that the user is who he/she claimed to be and that the user trusts that the DBMS is also the intended system.
- Authentication is a prerequisite for authorization.
- In client-server systems where data (not necessarily the database) is distributed, the authentication may be acceptable from a peer system.
- Authentication may be transmissible from system to system..
Authorization
- Authorization relates to the permissions granted to an authorised user to carry out particular transactions, and hence to change the state of the database (write item transactions) and/or receive data from the database (read-item transactions).
- The result of authorization, which needs to be on a transactional basis, is a vector:
- Authorization (item, auth-id, operation).
- A vector is a sequence of data values at a known location in the system.
- At a logical level, the system structure needs an authorization server, which needs to co-operate with an auditing server. There is an issue of server-to-server security and a problem with amplification as the authorization is transmitted from system to system.
- Amplification here means that the security issues become larger as a larger number of DBMS servers are involved in the transaction.
- Audit requirements are frequently implemented poorly. To be safe, you need to log all accesses and log all authorization details with transaction identifiers.
- There is a need to audit regularly and maintain an audit trail, often for a long period.
- Authorization can be applied to more granular levels than simply a web site or company intranet.
- Your individual identity can be included in a group of identities that share a common authorization policy.
Q3 What is access control and its types?
Answer 3
Access Controls
- The purpose of access control must always be clear.
- Access control is expensive in terms of analysis, design and operational costs. Database access control is a method of allowing access to company’s sensitive data only to those people (database users) who are allowed to access such data and to restrict access to unauthorized persons.
- It includes two main components:
- Authentication
- Authorization.
- Do not apply controls without all the above knowledge. Control always has to be appropriate to the situation
- It is applied to known situations, to known standards, to achieve known purposes.
- .A privilege allows a user to create or access some database object or to run some specific DBMS utilities.
- Privileges are granted users to achieve the tasks required for those jobs.
The usual way of supplying access controls to a database system is dependent on the granting and revoking of privileges within the database.
- Authentication is a method of verifying the identity of a person who is accessing your database. Note that authentication isn’t enough to protect data. An additional layer of security is required,
- Authorization, which determines whether a user should be allowed to access the data or make the transaction he’s attempting.
- Without authentication and authorization, there is no data security.
- Any company whose employees connect to the Internet, thus, every company today, needs some level of access control implemented.
Types of Access Control
- Obsolete access models include Discretionary Access Control (DAC) and Mandatory Access Control (MAC). Role Based Access Control (RBAC) is the most common method today, and the most recent model is Attribute Based Access Control (ABAC).
- Discretionary Access Control (DAC):- With DAC models, the data owner allows access. DAC is a means of assigning access rights based on user-specified rules.
- Mandatory Access Control (MAC):-MAC was developed using a nondiscretionary model, in which people are granted access based on an information clearance. MAC is a policy in which access rights are assigned based on central authority regulations.
- Role Based Access Control (RBAC):- RBAC grants access based on a user’s role and implements key security principles such as “least privilege” and “separation of privilege.” Thus, someone attempting to access information can only access data necessary for their role.
- Attribute Based Access Control (ABAC):- In ABAC, each resource and user are assigned a series of attributes. In this dynamic method, a comparative assessment of the user’s attributes, including time of day, position and location, are used to make a decision on access to a resource.
Q4 Explain rbac model for access control?
Answer 4
Role-Based Access Control
- Role-based access control (RBAC) emerged rapidly in the 1990s as a proven technology for managing and enforcing security in large-scale enterprise wide systems.
- Role Based Access Control (RBAC), also known as Non-discretionary Access Control, takes more of a real world approach to structuring access control
- Its basic notion is that permissions are associated with roles, and users are assigned to appropriate roles.
- Roles can be created using the CREATE ROLE and DESTROY ROLE commands. The GRANT and REVOKE commands discussed under DAC can then be used to assign and revoke privileges from roles.
- RBAC appears to be a viable alternative to traditional discretionary and mandatory access controls; it ensures that only authorized users are given access to certain data or resources.
- Many DBMSs have allowed the concept of roles, where privileges can be assigned to roles.
- Role hierarchy in RBAC is a natural way of organizing roles to reflect the organization’s lines of authority and responsibility.
- Another important consideration in RBAC systems is the possible temporal constraints that may exist on roles, such as time and duration of role activations, and timed triggering of a role by an activation of another role.
- Using an RBAC model is highly desirable goal for addressing the key security requirements of Web-based applications.
- RBAC is the most demanded in regard to access control systems. Not only is it in high demand among households, RBAC has also become highly sought-after in the business world.
- Role-based access control (RBAC) refers to the idea of assigning permissions to users based on their role within an organization.
- In RBAC systems, access is assigned by the system administrator and is stringently based on the subject’s role within the household or organization and most privileges are based on the limitations defined by their job responsibilities.
- So, rather than assigning an individual as a security manager, the security manager position already has access control permissions assigned to it.
- RBAC makes life much easier because rather than assigning multiple individuals particular access, the system administrator only has to assign access to specific job titles
- RBAC is the most demanded in regard to access control systems. Not only is it in high demand among households, RBAC has also become highly sought-after in the business world
- For example, an accountant in a company will be assigned to the Accountant role, gaining access to all the resources permitted for all accountants on the system. Similarly, a software engineer might be assigned to the developer role.
In RBAC, there are three rules:
- A person must be assigned a certain role in order to conduct a certain action, called a transaction.
- A user needs a role authorization to be allowed to hold that role.
- Transaction authorization allows the user to perform certain transactions. The transaction has to be allowed to occur through the role membership. Users won’t be able to perform transactions other than the ones they are authorized for.
Benefits of RBAC
- With RBAC, access management is easier as long as you adhere strictly to the role requirements. RBAC helps you:
- Create systematic, repeatable assignment of permissions.
- Easily audit user privileges and correct identified issues.
- Quickly add and change roles, as well as implement them across APIs.
- Cut down on the potential for error when assigning user permissions.
- Integrate third-party users by giving them pre-defined roles.
More effectively comply with regulatory and statutory requirements for confidentiality and privacy.
Q5 Explain intrusion detection?
Answer5
Intrusion Detection
- An intrusion detection system (IDS) is a type of security software designed to automatically alert administrators when someone or something is trying to compromise information system through malicious activities or through security policy violations.
- An IDS works by monitoring system activity through examining vulnerabilities in the system, the integrity of files and conducting an analysis of patterns based on already known attacks. It also automatically monitors the Internet to search for any of the latest threats which could result in a future attack.
- There are a multiple ways detection is performed by an IDS. In signature-based detection, a pattern or signature is compared to previous events to discover current threats. This is useful for finding already known threats, but does not help in finding unknown threats, variants of threats or hidden threats.
- Another type of detection is anomaly-based detection, which compares the definition or traits of a normal action against characteristics marking the event as abnormal.
There are three primary components of an IDS:
- Network Intrusion Detection System (NIDS): This does analysis for traffic on a whole subnet and will make a match to the traffic passing by to the attacks already known in a library of known attacks.
- Network Node Intrusion Detection System (NNIDS): This is similar to NIDS, but the traffic is only monitored on a single host, not a whole subnet.
- Host Intrusion Detection System (HIDS): This takes a “picture” of an entire system’s file set and compares it to a previous picture. If there are significant differences, such as missing files, it alerts the administrator.
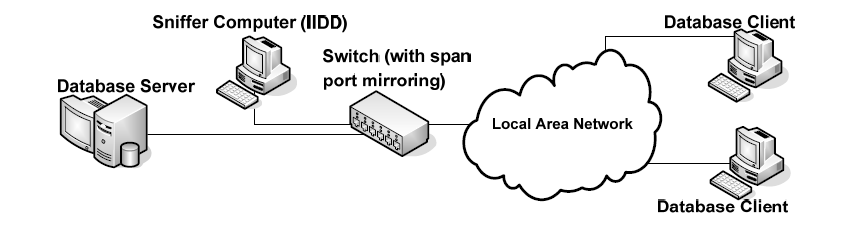
Figure: - Architecture setup
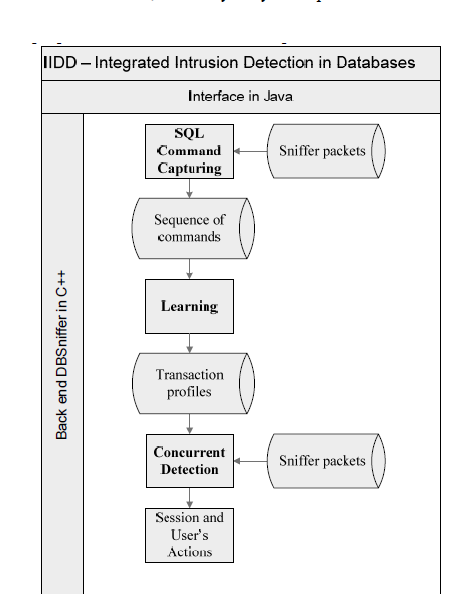
Figure 1 Integrated intrusion Detection
Q6 Explain data access model using mandatory access control?
Answer 6
Mandatory Access Control
- Mandatory Access Control (MAC) is the strictest of all levels of control. The design of MAC was defined, and is primarily used by the government.
- MAC takes a hierarchical approach to controlling access to resources. Under a MAC enforced environment access to all resource objects (such as data files) is controlled by settings defined by the system administrator.
- Mandatory Access Control (MAC) is is a set of security policies constrained according to system classification, configuration and authentication. MAC policy management and settings are established in one secure network and limited to system administrators.
- All access to resource objects is strictly controlled by the operating system based on system administrator configured settings. It is not possible under MAC enforcement for users to change the access control of a resource.
- Mandatory Access Control begins with security labels assigned to all resource objects on the system. These security labels contain two pieces of information - a classification (top secret, confidential etc) and a category (which is essentially an indication of the management level, department or project to which the object is available).
- Each user account on the system also has classification and category properties from the same set of properties applied to the resource objects.
- When a user attempts to access a resource under Mandatory Access Control the operating system checks the user's classification and categories and compares them to the properties of the object's security label.
- If the user's credentials match the MAC security label properties of the object access is allowed. It is important to note that both the classification and categories must match. A user with top secret classification,
- For example, cannot access a resource if they are not also a member of one of the required categories for that object.
- Mandatory Access Control is by far the most secure access control environment but does not come without a price.
- MAC requires a considerable amount of planning before it can be effectively implemented.
- Once implemented it also imposes a high system management overhead due to the need to constantly update object and account labels to accommodate new data, new users and changes in the categorization and classification of existing users.
- MAC defines and ensures a centralized enforcement of confidential security policy parameters
- Mandatory Access Control is more commonly utilized in organizations that require an elevated emphasis on the confidentiality and classification of data (ie. Military institutions).
- MAC doesn’t permit owners to have a say in the entities having access in a unit or facility, instead, only the owner and custodian have the management of the access controls.
- MAC will typically classify all end users and provide them with labels that permit them to gain access through security with established security guidelines
MAC advantages and disadvantages depend on organizational requirements, as follows:
- MAC provides tighter security because only a system administrator may access or alter controls.
- MAC policies reduce security errors.
- MAC enforced operating systems (OS) delineate and label incoming application data, which creates a specialized external application access control policy.
- By contrast, mandatory policies ensure a high degree of protection in a way, they prevent any illegal flow of information.
- Mandatory policies have the drawback of being too rigid and they are only applicable in limited environments.
- In many practical situations, discretionary policies are preferred because they offer a better trade-off between security and applicability.
Q7 Explain dac model?
Answer 7
Discretionary Access Control (DAC)
- Discretionary Access Control (DAC) allows each user to control access to their own data.
- DAC is typically the default access control mechanism for most desktop operating systems.
- Each resource object on a DAC based system has an Access Control List (ACL) associated with it. An ACL contains a list of users and groups to which the user has permitted access together with the level of access for each user or group.
- For example, User A may provide read-only access on one of her files to User B, read and write access on the same file to User C and full control to any user belonging to Group 1.
- Discretionary Access Control provides a much more flexible environment than Mandatory Access Control (MAC) but also increases the risk that data will be made accessible to users that should not necessarily be given access.
- Discretionary Access Control is a type of access control system that holds the business owner responsible for deciding which people are allowed in a specific location, physically or digitally.
- DAC is the least restrictive compared to the other systems, as it essentially allows an individual complete control over any objects they own, as well as the programs associated with those objects.
- Discretionary access control (DAC) is a type of security access control that grants or restricts object access via an access policy determined by an object's owner group and/or subjects
- DAC mechanism controls are defined by user identification with supplied credentials during authentication, such as username and password.
- In DAC, each system object (file or data object) has an owner, and each initial object owner is the subject that causes its creation. Thus, an object's access policy is determined by its owner.
- A typical example of DAC is UNIX file mode, which defines the read, write and execute permissions in each of the three bits for each user, group and others.
- A typical example of DAC is UNIX file mode, which defines the read, write and execute permissions in each of the three bits for each user, group and others.
DAC Advantages and Disadvantages:-
- User may transfer object ownership to another user(s).
- User may determine the access type of other users.
- After several attempts, authorization failures restrict user access.
- Unauthorized users are blind to object characteristics, such as file size, file name and directory path.
- Object access is determined during access control list (ACL) authorization and based on user identification and/or group membership.
- DAC is easy to implement and intuitive but has certain disadvantages, including:
- ACL maintenance or capability
- Grant and revoke permissions maintenance
- Limited negative authorization power
- Discretionary Access Control (DAC) policies are characterized by a high degree of flexibility, which makes them suitable for a large variety of application domains.
- The main drawback of DAC models is their vulnerability to malicious attacks, such as Trojan horses embedded in application programs.
Q8 What are effects of successful sql injection?
Answer 8
Definition: - SQL injection is a code injection technique, used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution (e.g. To dump the database contents to the attacker
- SQL injection is a web security vulnerability that allows an attacker to interfere with the queries that an application makes to its database.
- It generally allows an attacker to view data that they are not normally able to retrieve. This might include data belonging to other users, or any other data that the application itself is able to access. In many cases, an attacker can modify or delete this data, causing persistent changes to the application's content or behavior.
- In some situations, an attacker can escalate an SQL injection attack to compromise the underlying server or other back-end infrastructure, or perform a denial-of-service attack.
Impact of successful SQl injection
- A successful SQL injection attack can result in unauthorized access to sensitive data, such as passwords, credit card details, or personal user information.
- Many high-profile data breaches in recent years have been the result of SQL injection attacks, leading to reputational damage and regulatory fines.
- In some cases, an attacker can obtain a persistent backdoor into an organization's systems, leading to a long-term compromise that can go unnoticed for an extended period.
SQL injection examples: - There are a wide variety of SQL injection vulnerabilities, attacks, and techniques, which arise in different situations. Some common SQL injection examples include:
- Retrieving hidden data, where you can modify an SQL query to return additional results.
- Subverting application logic, where you can change a query to interfere with the application's logic.
- UNION attacks, where you can retrieve data from different database tables.
- Examining the database, where you can extract information about the version and structure of the database.
- Blind SQL injection, where the results of a query you control are not returned in the application's responses.
Detecting SQL injection vulnerabilities
- The majority of SQL injection vulnerabilities can be found quickly and reliably using Burp Suite's web vulnerability scanner.
- SQL injection can be detected manually by using a systematic set of tests against every entry point in the application. This typically involves:
- Submitting the single quote character ' and looking for errors or other anomalies.
- Submitting some SQL-specific syntax that evaluates to the base (original) value of the entry point, and to a different value, and looking for systematic differences in the resulting application responses.
- Submitting Boolean conditions such as OR 1=1 and OR 1=2, and looking for differences in the application's responses.
- Submitting payloads designed to trigger time delays when executed within an SQL query, and looking for differences in the time taken to respond.
- Submitting OAST payloads designed to trigger an out-of-band network interaction when executed within an SQL query, and monitoring for any resulting interactions
Q9 What are the benefits of using dac, mac and rbac models?
Answer 9
DAC Advantages and Disadvantages:-
- User may transfer object ownership to another user(s).
- User may determine the access type of other users.
- After several attempts, authorization failures restrict user access.
- Unauthorized users are blind to object characteristics, such as file size, file name and directory path.
- Object access is determined during access control list (ACL) authorization and based on user identification and/or group membership.
- DAC is easy to implement and intuitive but has certain disadvantages, including:
- ACL maintenance or capability
- Grant and revoke permissions maintenance
- Limited negative authorization power
- Discretionary Access Control (DAC) policies are characterized by a high degree of flexibility, which makes them suitable for a large variety of application domains.
- The main drawback of DAC models is their vulnerability to malicious attacks, such as Trojan horses embedded in application programs.
MAC advantages and disadvantages depend on organizational requirements, as follows:
- MAC provides tighter security because only a system administrator may access or alter controls.
- MAC policies reduce security errors.
- MAC enforced operating systems (OS) delineate and label incoming application data, which creates a specialized external application access control policy.
- By contrast, mandatory policies ensure a high degree of protection in a way, they prevent any illegal flow of information.
- Mandatory policies have the drawback of being too rigid and they are only applicable in limited environments.
- In many practical situations, discretionary policies are preferred because they offer a better trade-off between security and applicability.
Benefits of RBAC
- With RBAC, access management is easier as long as you adhere strictly to the role requirements. RBAC helps you:
- Create systematic, repeatable assignment of permissions.
- Easily audit user privileges and correct identified issues.
- Quickly add and change roles, as well as implement them across APIs.
- Cut down on the potential for error when assigning user permissions.
- Integrate third-party users by giving them pre-defined roles.
- More effectively comply with regulatory and statutory requirements for confidentiality and privacy.
Q10 Write difference between authorization and authentication?
Answer 10
S No | Authentication | Authorization |
1 | Determines whether users are who they claim to be. | Determines what users can and cannot access. |
2 | Challenges the user to validate credentials (for example, through passwords, answers to security questions, or facial recognition) | Verifies whether access is allowed through policies and rules |
3 | Usually done before authorization | Usually done after successful authentication |
4 | Generally, transmits info through an ID Token | Generally, transmits info through an Access Token |
5 | Generally governed by the OpenID Connect (OIDC) protocol | Generally governed by the OAuth 2.0 framework |
6 | Example: Employees in a company are required to authenticate through the network before accessing their company email | Example: After an employee successfully authenticates, the system determines what information the employees are allowed to access |