Unit - 2
Simplified DES
Q1) What do you mean by Simplified DES?
A1) The simplified DES's overall structure. The S-DES encryption technique takes a 10-bit key and an 8-bit block of plaintext as input and outputs an 8-bit block of ciphertext. The S-DES decryption technique takes an 8-bit block of ciphertext as input and outputs the original 8-bit block of plaintext using the same 10-bit key that was used to create the ciphertext.
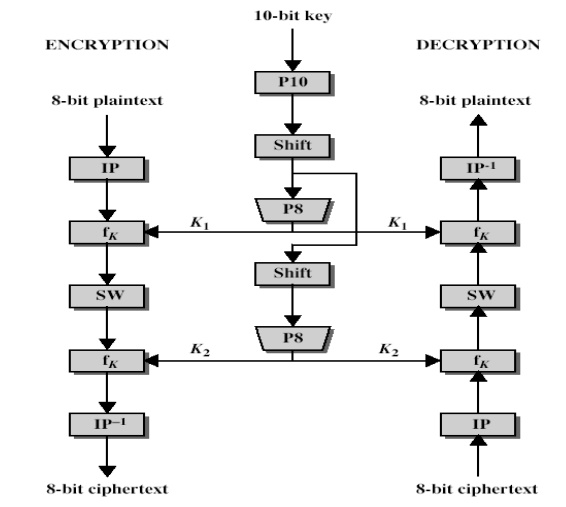
There are five functions in the encryption algorithm:
1. a first permutation (IP)
2.a complicated function called fk that uses permutation and substitution operations and is dependent on a key input
3.a basic permutation function that alternates the data's two halves (SW)
4.the fk function once more
5.a permutation function that is the inverse of the first one
The function fk accepts an 8-bit key as well as the data travelling through the encryption process. Two 8-bit subkeys are created from a 10-bit key in this case. A permutation test is performed on the key first (P10). After that, a shift operation is carried out. The shift operation's output is then sent through a permutation function, which generates an 8-bit output (P8) for the first subkey (K1). The second subkey is created by feeding the output of the shift operation into another shift and another instance of P8 (K2).
The encryption algorithm can be represented as a collection of functions:
The encryption algorithm can be expressed as a composition composition1 of functions: IP-1 ο fK2 ο SW ο fk1 ο IP
Which can also be written as
Ciphertext = IP-1 (fK2 (SW (fk1 (IP (plaintext)))))
Where
K1 = P8 (Shift (P10 (Key)))
K2 = P8 (Shift (shift (P10 (Key))))
Decryption can be shown as
Plaintext = IP-1 (fK1 (SW (fk2 (IP (ciphertext)))))
S-DES key generation
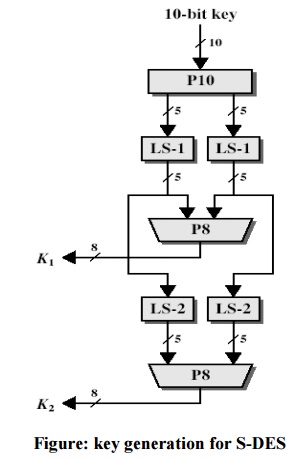
S-DES is based on the utilization of a shared 10-bit key between the sender and recipient. Two 8-bit subkeys are generated from this key for usage in specific phases of the encryption and decryption procedure. To begin, permute the key in the following order. Assign the 10-bit key the name (k1, K2, k3, k4, k5, k6, k7, k8, k9, k10). The permutation P10 is thus defined as follows:
(k1, k2, k3, k4, k5, k6, k7, k8, k9, k10) (k3, k5, K2, k7, k4, k10 10, k1, k9, k8, k6) The display can succinctly define P10:
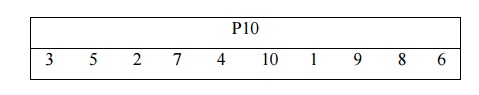
This table is read from left to right, with each position indicating the identity of the input bit that generates the output bit in that position. As a result, the first output bit corresponds to bit 3 of the input, the second output bit to bit 5, and so on. The key (1010000010), for example, is permuted to (10000 01100). Then, on the first five bits and the second five bits independently, do a circular left shift (LS-1), or rotation. In our case, the outcome is (00001 11000). Then we apply P8, which selects and permutes eight of the ten bits based on the following rule:
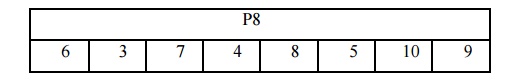
Subkey 1 is the result (K1). In our case, this results in (10100100). Then, on each of the two 5-bit strings created by the two LS-1 functions, we conduct a circular left shift of two-bit locations. The value (00001 11000) in our case becomes (00100 00011). P8 is then sprayed once again to make K2. In our case, the outcome is (01000011).
2 Encryption with S-DES
Encryption entails the execution of five procedures in a specific order.
Permutations in the beginning and in the end
The algorithm takes an 8-bit block of plaintext as input, which we permute first using the IP function:
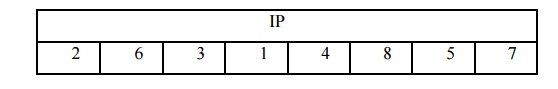
This keeps all 8 bits of plaintext but shuffles them around.
Assume that the plaintext is 11110011.
10111101 is the permuted output.
The inverse permutation is utilized at the end of the algorithm:
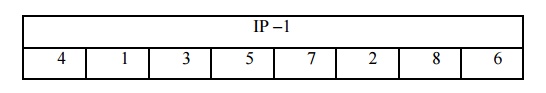
The fk Function
The function fk, which is made up of permutation and substitution functions, is the most complicated part of S-DES. The following is an example of a function. Let L and R be the leftmost 4 bits and rightmost 4 bits of the 8-bit input to f K, respectively, and F be a mapping from 4-bit strings to 4-bit strings (not necessarily one to one). Then we'll let it go.
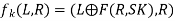
Where SK is subkey and ⨁ is the bit-by-bit exclusive-OR function
e.g., permuted output = 1011 1101 and suppose F(1101, SK)=(1110) for some key SK. Then fK(10111101)=1011⨁1110,1101=01011101
The mapping F is now described. A 4-bit number is used as the input (n1 n2 n3 n4). An expansion/permutation procedure is the initial step:
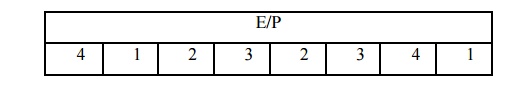
R= 1101 is an example.
11101011 is the E/P output.
It's easier to visualize the outcome this way:
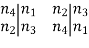 The 8-bit subkey K1 = (k11, k12 12, k13 13, k14 14, k15 15, k16 16, k17 17, k18) is added to this value using exclusive-OR:
The 8-bit subkey K1 = (k11, k12 12, k13 13, k14 14, k15 15, k16 16, k17 17, k18) is added to this value using exclusive-OR:
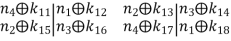
Let us rename these 8 bits:
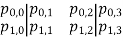
The first four bits (the first row of the preceding matrix) are fed into S0, which produces a two-bit output, and the remaining four bits (the second row) are fed into S1, which produces another two-bit output.
The following are the definitions for these two boxes:
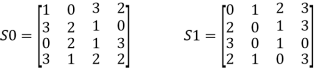
The S-boxes work in the following way. The first and fourth input bits are interpreted as a 2-bit number that specifies the S-row, box's while the second and third input bits indicate the S-column. box's The 2-bit output is the entry in that row and column in base 2. If (p0,0 p0,3) =) (00) and (p0,1 p0,2) = (10), the output is from S0's row 0, column 2, which is 3, or (11) in binary. Similarly, to obtain an additional 2 bits, (p1,0 p1,3) and (p1,1 p1,2) are used to index into a row and column of S1. The four bits produced by S0 and S1 are then permuted again as follows:
The output of P4 is the output of the function F.
3 The Switch Function
The function f K only alters the leftmost 4 bits of the input. The switch function (SW) interchanges the left and right 4 bits so that the second instance of f K operates on a different 4 bits. In this second instance, the E/P, S0, S1, and P4 functions are the same. The key input is K2. Finally apply inverse permutation to get the ciphertext.
Q2) What is Block cipher design principles?
A2) A block cypher is created by taking into account three key factors, which are given below:
1. Number of rounds
The strength of the block cypher algorithm is determined by the number of rounds. The greater the number of rounds, the more difficult it is for cryptanalysis to break the algorithm.
Even if the function F is somewhat weak, the algorithm is thought to be difficult to break due to the large number of rounds.
2. Function F Design
The block cipher's function F must be built in such a way that any cryptanalysis of the substitution is impossible. The non-linearity of the function F is a criterion that enhances it.
The more nonlinear the function F is, the more difficult it is to crack. Well, it should be validated that the function F has a good avalanche property, which states that a change in one bit of input must reflect a change in many bits of output.
The bit independence requirement, which specifies that the output bits must change independently if the input bit changes, should be included in the design of Function F.
3. Key Algorithm for Scheduling
The rigorous avalanche effect and bit independence condition should be confirmed by the key schedule, it is suggested.
Q3) What are the Block cipher modes of operation?
A3) NIST has specified five important block cypher modes of operation. These five modes of operation improve the method, allowing it to be adopted by a wide range of block cipher-based applications.
Mode of the Electronic Code Book
Q4) Describe Mode of the Electronic Code Book?
A4) Electronic Feedback
This is the most straightforward block cypher method of operation. The plain text is separated into blocks of 64 bits in electronic codebook mode (ECB).
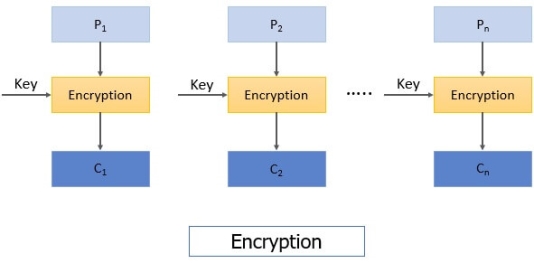
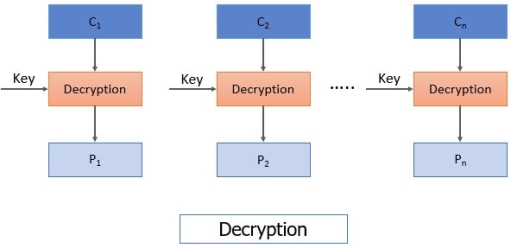
When the message, i.e., ciphertext, is received by the receiver. This ciphertext is separated into blocks of 64 bits each, and each block is decoded one at a time to acquire the plain text block corresponding to it. The same key that was used to encrypt each block is also used to decrypt each block.
Because the same key is used to encrypt each block of plain text, there is a risk that a repeated plain text block would yield the same cypher, making the technique easier to crack. As a result, ECB is suggested for encrypting tiny communications with a low likelihood of text repetition.
Q5) Define Block Chaining Mode for Ciphers?
A5) Block Chaining Mode for Ciphers
To get over ECB's drawback, which is that recurring blocks of plain text yield the same ciphertext, a new approach called Cipher Block Chaining (CBC) Mode was needed. Even if the plain text contains repeating blocks, CBC assures that the encryption will not yield the same cypher block.
Chaining has been introduced to the block cypher to achieve completely separate cypher blocks for two identical plain text blocks. This is accomplished by feeding the result of the first plaintext block's encryption into the encryption of the second plaintext box.
Each ciphertext block obtained as a result is reliant on the current plain text block input as well as all preceding plain text blocks. However, because no preceding plain text block is accessible during the encryption of the first plain text block, a random block of text called the Initialization vector is produced.
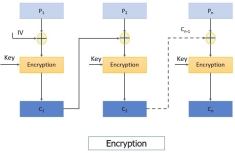
Let's have a look at the CBC encryption procedures.
Step 1: The initialization vector and the first plain text block are XORed, and the XOR result is then encrypted with the key to produce the first ciphertext block.
Step 2: The second plain text block is encrypted using the first ciphertext block. To obtain the second ciphertext block, the first ciphertext block and the second plain text block are XORed, and the result of the XOR is encrypted using the same key as in step 1.
The output of the encryption of the second plain text block, i.e., the second ciphertext block, is fed into the encryption of the third plain text block to produce the third ciphertext block. And so on, until all of the ciphertext blocks have been obtained.
You can see the steps of CBC in the figure below:
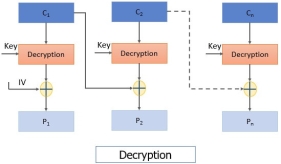
Decryption steps of CBC:
Step 1: The first ciphertext block is decrypted using the same key that was used for encrypting all plain text blocks. The result of decryption is then XORed with the initialization vector (IV) to obtain the first plain text block.
Step 2: The second ciphertext block is decrypted and the result of decryption is XORed with the first ciphertext block to obtain the second plain text block. And the process continues till all plain text blocks are retrieved.
There was a limitation in CBC that if we have two identical messages and if we use the same IV for both the identical message it would generate the same ciphertext block.
Q6) Define Feedback Mode for Ciphers?
A6) Cipher Feedback Mode
All applications may not be designed to operate on the blocks of data, some may be character or bit-oriented. Cipher feedback mode is used to operate on smaller units than blocks.
Let us discuss the encryption steps in cipher feedback mode:
Step 1: Here also we use initialization vector, IV is kept in the shift register and it is encrypted using the key.
Step 2: The left most s bits of the encrypted IV is then XORed with the first fragment of the plain text of s bits. It produces the first ciphertext C1 of s bits.
Step 3: Now the shift register containing initialization vector performs left shift by s bits and s bits C1 replaces the rightmost s bits of the initialization vector.
Then again, the encryption is performed on IV and the leftmost s bit of encrypted IV is XORed with the second fragment of plain text to obtain s bit ciphertext C2.
The process continues to obtain all ciphertext fragments.
Decryption Steps:
Step 1: The initialization vector is placed in the shift register. It is encrypted using the same key.
Keep a note that even in the decryption process the encryption algorithm is implemented instead of the decryption algorithm. Then from the encrypted IV s bits are XORed with the s bits ciphertext C1 to retrieve s bits plain text P1.
Step 2: The IV in the shift register is left-shifted by s bits and the s bits C1 replaces the rightmost s bits of IV.
The process continues until all plain text fragments are retrieved.
CFC Decryption cipher
It has a limitation that if there occur a bit error in any ciphertext Ci it would affect all the subsequent ciphertext units as Ci is fed to the encryption of next Pi+1 to obtain Ci+1. In this way, bit error would propagate.
Q7) Define Mode of Output Feedback?
A7) Output Feedback Mode
The output feedback (OFB) mode is almost similar to the CFB. The difference between CFB and OFB is that unlike CFB, in OFB the encrypted IV is fed to the encryption of next plain text block. The other difference is that CFB operates on a stream of bits whereas OFB operates on the block of bits.
Steps for encryption:
Step 1: The initialization vector is encrypted using the key.
Step 2: The encrypted IV is then XORed with the plain text block to obtain the ciphertext block.
The encrypted IV is fed to the encryption of next plain text block as you can see in the image below.
OFB Encryption Block cipher
Steps for decryption:
Step 1: The initialization vector is encrypted using the same key used for encrypting all plain text blocks.
Note: In the decryption process also the encryption function is implemented.
Step2: The encrypted IV is then XORed with the ciphertext block to retrieve the plain text block. The encrypted IV is also fed to the decryption process of the next ciphertext block. The process continues until all the plain text blocks are retrieved.
The advantage of OFB is that it protects the propagation of bit error means the if there occurs a bit error in C1 it will only affect the retrieval of P1 and won’t affect the retrieval of subsequent plain text blocks.
Q8) Define Counter-Strike?
A8) Counter Mode
It is similar to OFB but there is no feedback mechanism in counter mode. Nothing is being fed from the previous step to the next step instead it uses a sequence of number which is termed as a counter which is input to the encryption function along with the key. After a plain text block is encrypted the counter value increments by 1.
Steps of encryption:
Step1: The counter value is encrypted using a key.
Step 2: The encrypted counter value is XORed with the plain text block to obtain a ciphertext block.
To encrypt the next subsequent plain text block the counter value is incremented by 1 and step 1 and 2 are repeated to obtain the corresponding ciphertext.
Counter Mode Encryption
The process continues until all plain text block is encrypted.
Steps for decryption:
Step1: The counter value is encrypted using a key.
Note: Encryption function is used in the decryption process. The same counter values are used for decryption as used while encryption.
Step 2: The encrypted counter value is XORed with the ciphertext block
to obtain a plain text block.
Counter Mode Decryption
To decrypt the next subsequent ciphertext block the counter value is incremented by 1 and step 1 and 2 are repeated to obtain corresponding plain text.
The process continues until all ciphertext block is decrypted.
So, this is all about Block cipher, its designing principles and its mode of operation.
Q9) Define Data Encryption Standard?
A9) The Data Encryption Standard (DES) is a symmetric-key data encryption standard that is no longer in use.
Because DES encrypts and decrypts messages with the same key, both the sender and the receiver must know and use the same private key. DES has been replaced by the more secure Advanced Encryption Standard (AES) as the go-to symmetric-key technique for the encryption of electronic data.
DES was created by IBM researchers in the early 1970s and was officially accepted by the United States government as a Federal Information Processing Standard (FIPS) in 1977 for the encryption of commercial and sensitive but unclassified government computer data.
It was the first encryption algorithm permitted for public dissemination by the US government. As a result, DES was swiftly embraced by businesses like financial services, which have a high demand for secure encryption. Because of its simplicity, DES is widely used in embedded systems, smart cards, SIM cards, and network devices that require encryption, such as modems, set-top boxes, and routers.
Q10) What are the strength of DES?
A10) The Data Encryption Standard (DES) is a symmetric key block cypher that accepts 64 bits of plaintext and 56 bits of key as input and outputs 64 bits of cypher text. P and S-boxes make up the DES function. To generate an encryption, P-boxes transpose bits and S-boxes replace bits.
The strength of DES is based on two factors:
a. The usage of 56-bit keys: In encryption, 56-bit keys are employed, and there are 256 potential keys. On such a large number of keys, a brute force attack is impracticable.
b. The algorithm's nature: Cryptanalysts can do cryptanalysis by exploiting the DES algorithm's characteristics, but no one has yet discovered the flaw.
Weakness- A flaw in the cipher's architecture has been discovered:
a. Two different inputs to an S-box can produce the same output.
b. The initial and final permutation's function is unclear.
Q11) What is Differential Cryptanalysis?
A11) Differential Cryptanalysis
Differential cryptanalysis predates linear cryptanalysis, as it was created in 1990 as a DES attack. Differential cryptanalysis is similar to linear cryptanalysis in that it attempts to reverse engineer the encryption algorithm's action by mapping bitwise variations in inputs to differences in outputs. It aims to estimate the encryption technique by changing plaintexts or (looking at different plaintexts) and analyzing the impact of modifications to the plaintext on the ensuing ciphertext to discover a maximum probability estimator of the genuine encryption activity. Differential cryptanalysis is thus a plaintext attack of choice.
Q12) What is Linear cryptanalysis?
A12) Cryptanalysis in Linear Form
In 1993, the linear cryptanalysis paradigm was created as a theoretical attack on DES. It's now commonly used on block cyphers in the field of cryptanalysis, and it's a good place to start for constructing more complex attacks.
Linear Cryptanalysis: A Step-by-Step Guide
Except for the private key, we assume that everything about the encryption technique is known in the most typical use case. A block cipher's linear cryptanalysis usually consists of three steps.