Unit - 6
Message authentication
Q1) What do you mean by Message authentication?
A1) Risks to data integrity and the usage of hashing techniques to identify data tampering assaults
The lack of message authentication is another form of threat to data. In this threat, the sender of the message is unknown to the user. Message authentication can be accomplished using cryptographic algorithms that employ secret keys, similar to how encryption is accomplished.
MAC stands for Message Authentication Code and is a symmetric key cryptography mechanism for message authentication. The transmitter and receiver exchange a symmetric key K to establish the MAC process.
Essentially,
A message authentication code (MAC) is an encrypted checksum generated on the underlying message that is sent with the transmission.
The following diagram depicts the procedure of using MAC for authentication.
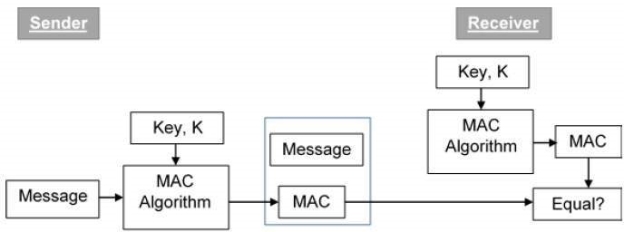
Let's take a closer look at the entire process now.
Q2) What are the Authentication requirements?
A2) The following assaults can be discovered in the context of network communications.
Disclosure: Making the contents of a message available to anybody or anything who does not have the relevant cryptographic key.
Traffic analysis: It is the process of determining the pattern of traffic between two parties. The frequency and length of connections could be determined in a connection-oriented application. The volume and length of messages sent between parties could be determined in either a connection-oriented or a connectionless environment.
Masquerade: Using a phone source to send messages into the network. This includes the fabrication of messages by an adversary that appear to come from a legitimate source. Fraudulent acknowledgments of message receipt or nonreceipt by someone other than the message recipient is also included.
Content modification: It includes insertion, deletion, transposition, and alteration of a message's contents.
Insertion, deletion, and rearranging of messages in a series between parties are all examples of sequence modification.
Modify the timing of communications by delaying or replaying them. An complete session or sequence of messages in a connection-oriented application may be a replay of a previously valid session, or individual messages in the sequence could be delayed or replayed. A unique communication (e.g., datagram) in a connectionless application.
Source repudiation is when a source refuses to send a message.
Rejection of a message by the intended recipient (destination repudiation).
The first two attacks are dealt with in Part One, and the measures to cope with them are in the realm of message confidentiality. Message authentication refers to the steps taken to address points (3) through (2) in the preceding list. Digital signatures are mechanisms for dealing specifically with item (7). In most cases, a digital signature mechanism will also protect against some or all of the attacks outlined in items (3) through (6). To deal with item (8), you might need to utilize a combination of digital signatures and a protocol designed to thwart this attack. In a nutshell, message authentication is a technique for ensuring that received communications are genuine and have not been tampered with. Message authentication can also be used to check the order and timeliness of messages. A digital signature is an authentication method that also contains safeguards against the source's repudiation.
Q3) Describe Authentication functions?
A3) There are two degrees of functionality in any message authentication or digital signature system. There must be a function at the lower level that generates an authenticator: a value that may be used to authenticate a message. This lower-level function is subsequently utilized as a primitive in a higher-level authentication protocol, allowing a recipient to confirm the message's validity.
This section discusses the many functions that can be used to create an authenticator. These can be divided into three categories.
Function to hash: A function that converts any length message into a fixed-length hash result that serves as an authenticator.
Encryption of messages: The entire message's ciphertext acts as an authenticator.
Q4) Describe Message Authentication Code?
A4) The employment of a secret key to construct a short fixed-size block of data known as a cryptographic checksum or MAC that is attached to the message is an alternate authentication mechanism. This method is based on the assumption that two communication parties, say A and B, have a shared secret key K. A calculates the MAC as a function of the message and the key when it has a message to send to B:
MAC = MAC(K, M), where
M is the input message.
C stands for the MAC function.
K stands for shared secret key.
The message authentication code (MAC) is a code that identifies a message.
The message plus MAC is transmitted to the intended recipient. The recipient per- forms the same calculation on the received message, using the same secret key, to
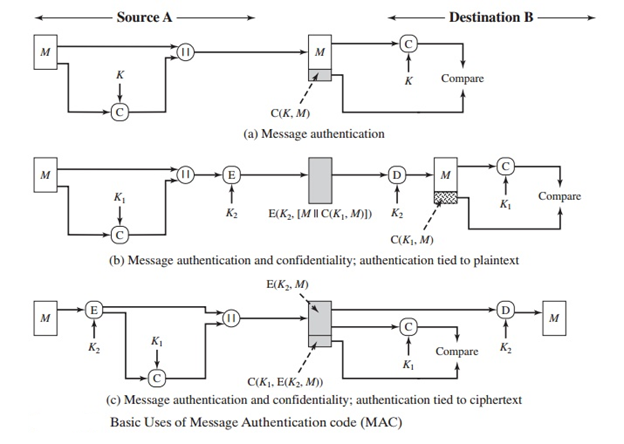
create a new MAC address. The calculated and received MACs are compared (Figure). If the secret key's identity is known only by the receiver and sender, and the received MAC matches the computed MAC, then
Encryption is analogous to the MAC function. One difference is that unlike decryption, the MAC method does not have to be reversible. The MAC function is a many-to-one function in general. The function's domain is made up of messages of any length, while the range is made up of all conceivable MACs and keys. There are 2n potential MACs if an n-bit MAC is employed, but there are N possible messages with N 77 2n. Furthermore, there are 2k potential keys with a k-bit key.
Q5) Describe Hash functions?
A5) Hash functions are incredibly valuable and may be found in practically every application that deals with information security.
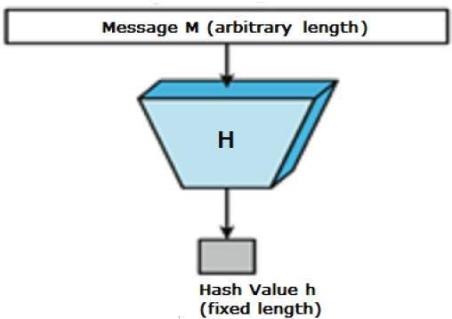
A hash function turns a numerical input value into another compressed numerical value. The input to the hash function can be any length, but the output is always the same.
Message digests, or simply hash values, are the results of a hash algorithm. The hash function is depicted in the diagram below.
Q6) What are the Characteristics the Hash Functions?
A6) The following are some of the most common characteristics of hash functions:
Q7) What do you mean by Fixed Length Output?
A7) The hash function converts arbitrary-length data to a fixed-length format. Hashing the data is a term used to describe this operation.
Hash functions are sometimes referred to as compression functions because the hash is usually substantially less than the original data.
A digest is also known as a hash since it is a smaller representation of a larger material.
An n-bit hash function is a hash function having an output of n bits. Popular hash functions provide values ranging from 160 to 512 bits.
Q8) Define Operational Efficiency?
A8) In general, computing h(x) for any hash function h with input x is a quick procedure.
Hash functions are substantially faster than symmetric encryption in terms of computation.
Q9) What is Hash Functions' Characteristics?
A9) The hash function should have the following features in order to be a successful cryptographic tool:
Resistance to Pre-Image
This feature indicates that reversing a hash function should be computationally difficult.
In other words, if a hash function h produces a hash value z, finding any input value x that hashes to z should be challenging.
This property guards against an attacker who only has a hash value and is trying to figure out what the input is.
Resistance to the Second Pre-Image
This property implies that given an input and its hash, finding another input with the same hash should be difficult.
In other words, if a hash function h provides the hash value h(x) for an input x, it should be impossible to discover any additional input y where h(y) = h(x) (x).
This characteristic of the hash function protects against an attacker who has access to an input value and its hash and wishes to replace a different value as a legitimate value for the original input value.
Q10) Define Resistance to Collision?
A10) This feature implies that finding two different inputs of any length that produce the same hash should be difficult. Collision-free hash function is another name for this property.
To put it another way, it's difficult to discover any two separate inputs x and y for a hash function h such that h(x) = h(y) (y).
It is impossible for a hash function to not have collisions because it is a compression function with a set hash length. This attribute of collision-free merely adds to the likelihood that these collisions will be difficult to locate.
An attacker will have a hard time finding two input values with the same hash because of this characteristic.
It is also second if a hash algorithm is collision pre-image resistant.
Q11) What do you mean by Secure Hash algorithm?
A11) SHA-0, SHA-1, SHA-2, and SHA-3 are the four SHA algorithms that make up the SHA family. Despite being from the same family, they are structurally distinct.
The National Institute of Standards and Technology (NIST) published the original version of SHA-0, a 160-bit hash function, in 1993. It had few flaws and did not gain widespread popularity. Later in 1995, SHA-1 was created to address SHA-0's reported flaws.
Of the available SHA hash functions, SHA-1 is the most extensively used. It's utilised in a variety of popular applications and protocols, including the Secure Socket Layer (SSL) security protocol.
In 2005, a method for discovering SHA-1 collisions in a reasonable amount of time was discovered, casting doubt on SHA-1's long-term viability.
SHA-224, SHA-256, SHA-384, and SHA-512 are four more SHA variants based on the number of bits in their hash value. The SHA-2 hash function has yet to be successfully attacked.
SHA-2 is a powerful hash function. Despite the fact that it is radically different, its basic design is similar to that of SHA-1. As a result, the National Institute of Standards and Technology (NIST) has requested new competitive hash function designs.
The Keccak algorithm was chosen as the new SHA-3 standard by the NIST in October 2012. Keccak has a number of advantages, including efficient performance and strong assault resistance.