Unit - 1
Introduction to Networks and Data Communications
Q1) What the characteristics and components of data communications?
A1) Data Communication is a process of exchanging data or information. In case of computer networks this exchange is done between two devices over a transmission medium. This process involves a communication system which is made up of hardware and software. The hardware part involves the sender and receiver devices and the intermediate devices through which the data passes. The software part involves certain rules which specify what is to be communicated, how it is to be communicated and when. It is also called as a Protocol. The following sections describes the fundamental characteristics that are important for the effective working of data communication process and is followed by the components that make up a data communications system.
Characteristics of Data Communication The effectiveness of any data communications system depends upon the following four fundamental characteristics:
1. Delivery: The data should be delivered to the correct destination and correct user.
2. Accuracy: The communication system should deliver the data accurately, without introducing any errors. The data may get corrupted during transmission affecting the accuracy of the delivered data.
3. Timeliness: Audio and Video data has to be delivered in a timely manner without any delay; such a data delivery is called real time transmission of data.
4. Jitter: It is the variation in the packet arrival time. Uneven Jitter may affect the timeliness of data being transmitted.
Components of Data Communication: A Data Communication system has five components as shown in the diagram below:
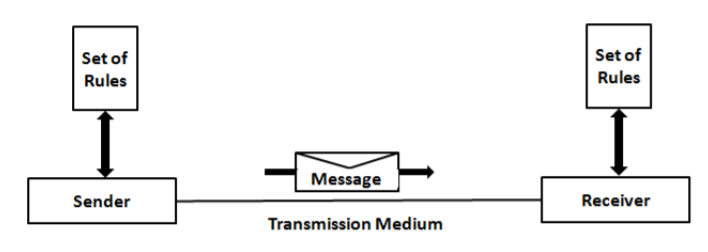
Fig. Components of a Data Communication System
1. Message: Message is the information to be communicated by the sender to the receiver.
2. Sender The sender is any device that is capable of sending the data (message).
3. Receiver The receiver is a device that the sender wants to communicate the data (message).
4. Transmission Medium It is the path by which the message travels from sender to receiver. It can be wired or wireless and many subtypes in both.
5. Protocol It is an agreed upon set or rules used by the sender and receiver to communicate data. A protocol is a set of rules that governs data communication. A Protocol is a necessity in data communications without which the communicating entities are like two persons trying to talk to each other in a different language without know the other language.
Q2) What are the modes of communication of the devices to have easy data flow?
A2) The devices communicate with each other by sending and receiving data. The data can flow between the two devices in the following ways.
- Simplex
- Half Duplex
- Full Duplex
Simplex
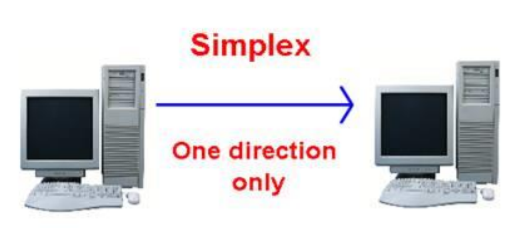
Figure: Simplex mode of communication
In Simplex, communication is unidirectional Only one of the devices sends the data and the other one only receives the data. Example: in the above diagram: a cpu send data while a monitor only receives data.
Half Duplex

Figure: Half Duplex Mode of Communication
In half duplex both the stations can transmit as well as receive but not at the same time. When one device is sending other can only receive and vice-versa (as shown in figure above.) Example: A walkie-talkie.
Full Duplex

Figure: Full Duplex Mode of Communication
In Full duplex mode, both stations can transmit and receive at the same time. Example: mobile phones
Q3) What are the standards in networking and standard organizations in field of networking?
A3) Standards are necessary in networking to ensure interconnectivity and interoperability between various networking hardware and software components. Without standards we would have proprietary products creating isolated islands of users which cannot interconnect.
Concept of Standard Standards provide guidelines to product manufacturers and vendors to ensure national and international interconnectivity.
Data communications standards are classified into two categories:
- De facto Standard
- These are the standards that have been traditionally used and mean by fact or by convention.
- These standards are not approved by any organized body but are adopted by widespread use.
2. De jure standard
- It means by law or by regulation.
- These standards are legislated and approved by anybody that is officially recognized.
Standard Organizations in field of Networking
- Standards are created by standards creation committees, forums, and government regulatory agencies.
- Examples of Standard Creation Committees:
1. International Organization for standardization (ISO)
2. International Telecommunications Union – Telecommunications Standard (ITU-T)
3. American National Standards Institute (ANSI)
4. Institute of Electrical & Electronics Engineers (IEEE) 5. Electronic Industries Associates (EIA)
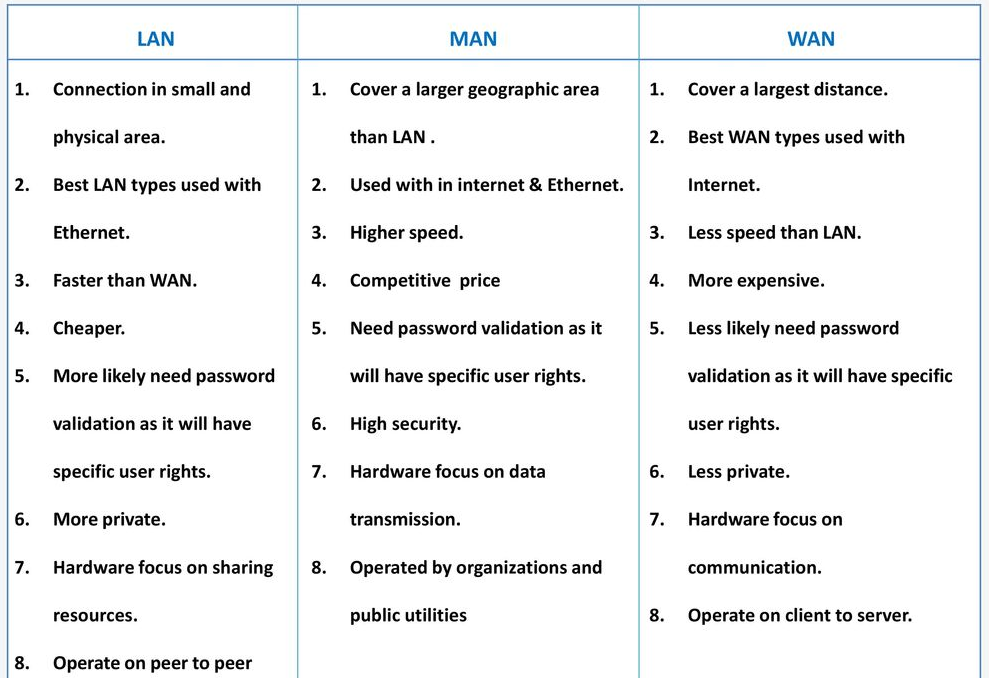
Q4) Write and compare the basic network categories?
A4) The basic network categories are LAN, MAN and WAN
Q5) Explain the two types of the computer network architectures?
A5) Computer Network Architecture is defined as the physical and logical design of the software, hardware, protocols, and media of the transmission of data. Simply we can say that how computers are organized and how tasks are allocated to the computer.
The two types of network architectures are used:
Peer-To-Peer network
Client/Server network
Peer-To-Peer network
Peer-To-Peer network is a network in which all the computers are linked together with equal privilege and responsibilities for processing the data. Peer-To-Peer network is useful for small environments, usually up to 10 computers. Peer-To-Peer network has no dedicated server. Special permissions are assigned to each computer for sharing the resources, but this can lead to a problem if the computer with the resource is down.
Advantages of Peer-To-Peer Network:
It is less costly as it does not contain any dedicated server. If one computer stops working but, other computers will not stop working. It is easy to set up and maintain as each computer manages itself.
Disadvantages of Peer-To-Peer Network:
In the case of Peer-To-Peer network, it does not contain the centralized system. Therefore, it cannot back up the data as the data is different in different locations. It has a security issue as the device is managed itself.
Client/Server Network
Client/Server network is a network model designed for the end users called clients, to access the resources such as songs, video, etc. from a central computer known as Server. The central controller is known as a server while all other computers in the network are called clients. A server performs all the major operations such as security and network management. A server is responsible for managing all the resources such as files, directories, printer, etc. All the clients communicate with each other through a server. For example, if client1 wants to send some data to client 2, then it first sends the request to the server for the permission. The server sends the response to the client 1 to initiate its communication with the client 2.
Advantages of Client/Server network:
A Client/Server network contains the centralized system. Therefore, we can back up the data easily. A Client/Server network has a dedicated server that improves the overall performance of the whole system. Security is better in Client/Server network as a single server administers the shared resources. It also increases the speed of the sharing resources.
Disadvantages of Client/Server network:
Client/Server network is expensive as it requires the server with large memory. A server has a Network Operating System (NOS) to provide the resources to the clients, but the cost of NOS is very high. It requires a dedicated network administrator to manage all the resources.
Q6) Explain the OSI model with all its layers and their respective working?
A6) SI Model
OSI model is not a network architecture because it does not specify the exact services and protocols for each layer. It simply tells what each layer should do by defining its input and output data. It is up to network architects to implement the layers according to their needs and resources available.
These are the seven layers of the OSI model −
- Physical layer −It is the first layer that physically connects the two systems that need to communicate. It transmits data in bits and manages simplex or duplex transmission by modem. It also manages Network Interface Card’s hardware interface to the network, like cabling, cable terminators, topography, voltage levels, etc.
- Data link layer − It is the firmware layer of Network Interface Card. It assembles datagrams into frames and adds start and stop flags to each frame. It also resolves problems caused by damaged, lost or duplicate frames.
- Network layer − It is concerned with routing, switching and controlling flow of information between the workstations. It also breaks down transport layer datagrams into smaller datagrams.
- Transport layer − Till the session layer, file is in its own form. Transport layer breaks it down into data frames, provides error checking at network segment level and prevents a fast host from overrunning a slower one. Transport layer isolates the upper layers from network hardware.
- Session layer − This layer is responsible for establishing a session between two workstations that want to exchange data.
- Presentation layer − This layer is concerned with correct representation of data, i.e. syntax and semantics of information. It controls file level security and is also responsible for converting data to network standards.
- Application layer − It is the topmost layer of the network that is responsible for sending application requests by the user to the lower levels. Typical applications include file transfer, E-mail, remote logon, data entry, etc.
Fig – Client server machine
It is not necessary for every network to have all the layers. For example, network layer is not there in broadcast networks.
When a system wants to share data with another workstation or send a request over the network, it is received by the application layer. Data then proceeds to lower layers after processing till it reaches the physical layer.
At the physical layer, the data is actually transferred and received by the physical layer of the destination workstation. There, the data proceeds to upper layers after processing till it reaches application layer.
At the application layer, data or request is shared with the workstation. So each layer has opposite functions for source and destination workstations. For example, data link layer of the source workstation adds start and stop flags to the frames but the same layer of the destination workstation will remove the start and stop flags from the frames.
Q7) What is TCP/IP protocol. Explain all its layers?
A7) TCP/IP
TCP/IP stands for Transmission Control Protocol/Internet Protocol. TCP/IP is a set of layered protocols used for communication over the Internet. The communication model of this suite is client-server model. A computer that sends a request is the client and a computer to which the request is sent is the server.
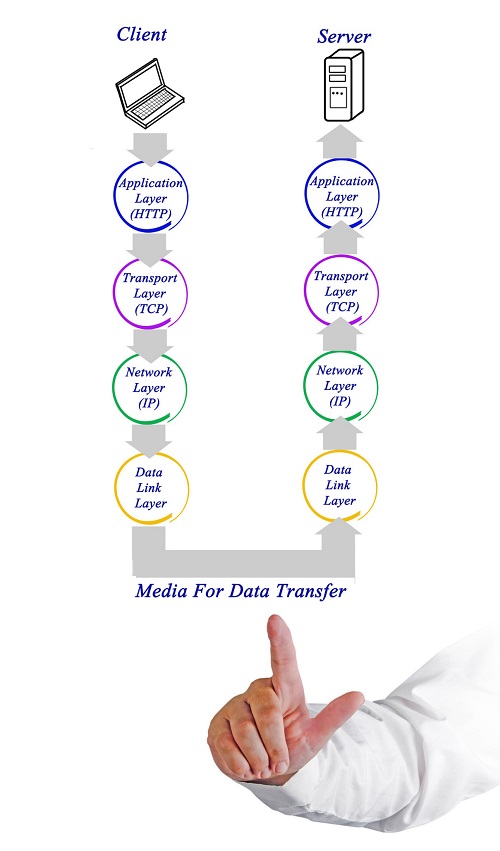
Fig – Media for data transfer
TCP/IP has four layers −
- Application layer − Application layer protocols like HTTP and FTP are used.
- Transport layer − Data is transmitted in form of datagrams using the Transmission Control Protocol (TCP). TCP is responsible for breaking up data at the client side and then reassembling it on the server side.
- Network layer − Network layer connection is established using Internet Protocol (IP) at the network layer. Every machine connected to the Internet is assigned an address called IP address by the protocol to easily identify source and destination machines.
- Data link layer − Actual data transmission in bits occurs at the data link layer using the destination address provided by network layer.
TCP/IP is widely used in many communication networks other than the Internet.
Q8) Write the goals of the network?
A8) Goals of Network
The following are the network's key objectives.
● Resource sharing: A computer network's primary goal is to accomplish this. It means that any computer on the network will share all of its programs, peripherals, and data with all other computers on the network, regardless of their physical locations. As a result, users at a great distance will share resources or view data on a device in the same way that local users do.
Load sharing is another type of resource sharing. That is, if necessary, a job can be done on several computers in a network by portioning it, which reduces time and load on each computer.
● Cost reduction: A second aim of networking is to save money. Sharing resources automatically lowers costs, allowing money to be saved.
● High reliability: Another aim is to ensure high reliability by providing many supply sources. For example, all files could be replicated on two or three computers, so that if one of them goes down, the others will still work.
● Improve performance: Another aim that is closely related is to improve the system's efficiency. As the workload on a machine increases, its output can be enhanced by adding one or more processors. For example, instead of replacing the device with a larger one that is more expansive, it is easier to add more processors to it at a lower cost and with less inconvenience to the consumer.
● Communication medium: Computer networks are an effective means of communication. A file that has been updated/modified on a network is instantly visible to all users on the network.
Q9) What are the applications of the network?
A9) Application of Network
The following are some examples of network applications in various fields.
- Financial services
- Marketing and sales
- Manufacturing
- Information services
- Cellular telephone
- Cable television
- EDI
- E-mail etc.
- Teleconferencing
- CAD, CAM etc.
Q10) Explain the types of networks?
A10) Types of Networks
A computer network is a set of computers linked together by a communication medium such as cable or wire.
The geographic area and number of computers that make up a network can be used to determine the scale of the network. It can range from a single computer in a single room to millions of devices distributed across the globe.
Based on their complexity, computer networks are divided into four categories:

Fig: Types of networks
- PAN: A personal area network (PAN) is a computer network that is formed around an individual. A computer, a cell phone, or a personal digital assistant are the most common components. PAN can be used to link these personal devices to a digital network and the internet by establishing contact between them.

Fig: PAN
2. LAN: A Local Area Network (LAN) is a set of computers and peripheral devices linked in a small area, such as a classroom, laboratory, home, or office building. It's a popular network for sharing resources such as files, printers, games, and other software. Connecting computers and a printer in someone's home or office is the most basic form of LAN network. LAN will be used as one form of transmission medium in general.
It's a network of less than 5000 interconnected devices spread over several buildings.
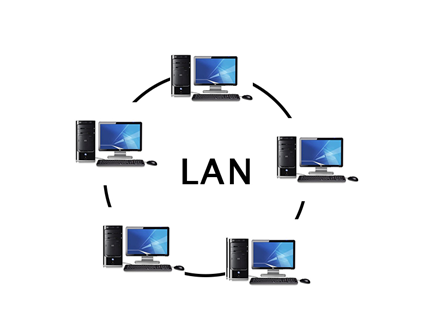
Fig: LAN
3. MAN: A Metropolitan Area Network, or MAN, is a computer network that spans a city, a college campus, or a small area. This network is far larger than a LAN, which is usually restricted to a single building or location. This form of network can cover a range of distances from a few miles to tens of miles, depending on the configuration.

Fig: MAN
4. WAN: Another significant computer network that spans a vast geographical area is the WAN (Wide Area Network). A WAN network system may be a LAN link that uses telephone lines and radio waves to connect to other LANs. It is usually restricted to a single company or organization.
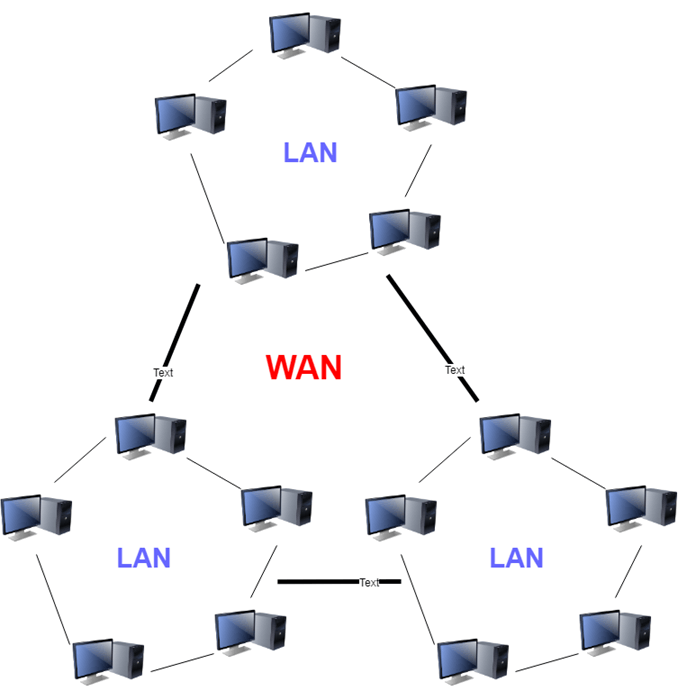
Fig 11 WAN
Q11) Write the Network devices and components?
A11) Network devices and components
The major components used to install the program are computer network components. NIC, switch, cable, hub, router, and modem are all essential network components. Some network components can be removed depending on the type of network we need to install. The wireless network, for example, does not require the use of a cable.
The following are the main elements needed to set up a network:
NIC: The term "network interface card" refers to a computer's network interface card. A network interface card (NIC) is a hardware component that connects two computers on a network. It can transmit data at speeds ranging from 10,100 to 1000 Mb/s. The MAC address, also known as the physical address, is encoded on the network card chip and allocated by the IEEE to uniquely identify each network card. The PROM stores the MAC address (Programmable read-only memory).
Types of NIC
● Wired NIC: The Wired NIC can be found on the motherboard. To pass data, wired NICs use cables and connectors.
● Wireless NIC: The antenna for establishing a wireless network link is housed in the wireless NIC. The wireless NIC, for example, is used on a laptop computer.
Hub: A hub is a piece of hardware that splits a network link between multiple devices. When a device requests information from a network, the request is first sent via cable to the Hub. This request will be transmitted to the entire network by Hub. Both devices will search to see whether the request is theirs or not. Otherwise, the appeal would be ignored.
The Hub's operation uses more bandwidth and restricts the amount of data that can be sent. Hubs are no longer used and have been replaced by more modern computer network components such as switches and routers.
Switch: A switch is a computer network hardware device that links several computers. A Switch is more advanced than a Hub in terms of functionality. The Switch houses a modified table that determines whether or not data is transmitted. Based on the physical address in the incoming message, Switch sends the message to the correct destination.
Unlike the Hub, a Switch does not broadcast the message to the whole network. It identifies the computer to which the message will be sent. As a result, we may assume that the switch establishes a direct link between the source and the destination. It boosts the network's efficiency.
Router: A router is a hardware device that connects a local area network (LAN) to the internet. It receives, analyzes, and forwards incoming packets to a different network. A router is part of the OSI Reference Model's Layer 3 (Network layer).
The packet is forwarded by a router based on the details in the routing table. It selects the best route for packet transmission from among the available options.
Modem: A modem is a piece of hardware that enables a computer to link to the internet using an existing phone line. A modem is not built into the motherboard; instead, it is mounted in a PCI slot on the motherboard. Modulator/Demodulator is what it stands for. It uses telephone lines to transform digital data into an analog signal.
Q12) Write the difference between OSI and TCP/IP model?
A12) Difference between OSI and TCP/IP Model
OSI Model | TCP/IP |
It stands for Open System Interconnection. | It stands for Transmission Control Protocol. |
The transport layer offers a guarantee for packet delivery in the OSI model.
| The distribution of packets is not guaranteed by the transport layer. Nonetheless, we may assume that it is a trustworthy model. |
The vertical method is used in this model. | The horizontal method is used in this model. |
It consists of 7 layers. | It consists of 4 layers. |
The OSI model was created by ISO (International Standard Organization). | ARPANET was the company that produced it (Advanced Research Project Agency Network). |
The network layer in this model offers both connection-oriented and connectionless services. | Only connectionless services are provided by the network layer.
|
This model isn't seen very much. | This model is quite popular. |
It allows devices such as routers, motherboards, switches, and other hardware to be standardized. | It does not provide devices with standardization. It allows computers to communicate with one another. |
Q13) Describe Network performance and transmission impairments?
A13) Network performance and transmission impairments
Network performance relates to the customer's perception of a network's service quality.
Since each network is unique in its nature and design, there are several different ways to assess its performance. Instead of measuring efficiency, it can be modeled and simulated; one example is using state transition diagrams to model queuing performance or using a Network Simulator.
The following steps are often regarded as crucial:
● Bandwidth: The maximum rate at which information can be transmitted is calculated in bits per second.
● Throughput: The rate at which data is transmitted is known as throughput.
● Latency: Latency is the time between when a signal is sent and when it is decoded by the receiver. It is primarily a function of the signal's transit time and the processing time at any nodes the information passes through.
● Jitter: Jitter variance in packet delay at the information receiver
● Error rate: The number of corrupted bits expressed as a percentage or fraction of the total sent is known as the error rate.
Transmission impairments
When a transmitting impairment causes the received signal to differ from the transmitted signal. Signal output would be harmed as a result of transmission problems.
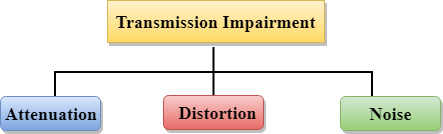
Fig: Transmission impairment
Attenuation: Attenuation refers to the loss of energy caused by the signal's intensity decreasing as the distance between them increases.
Distortion: When the form of a signal changes, it is said to be distorted. Different signals of different frequencies are analyzed for this form of distortion. Due to the fact that each frequency variable has its own propagation speed, they arrive at different times, resulting in delay distortion.
Noise: When data is sent over a transmission medium, an unwanted signal is mixed in, resulting in noise.
Q14) What is the meaning of internet today explain with diagram?
A15) Today, we witness a rapid growth both in the infrastructure and new applications. The Internet today is a set of pier networks that provide services to the whole world. What has made the Internet so popular is the invention of new applications.
- World Wide Web The 1990s saw the explosion of Internet applications due to the emergence of the World Wide Web (WWW). The Web was invented at CERN by Tim Berners-Lee. This invention has added the commercial applications to the Internet.
- Multimedia Recent developments in the multimedia applications such as voice over IP (telephony), video over IP (Skype), view sharing (YouTube), and television over IP (PPLive) has increased the number of users and the amount of time each user spends on the network.
- Peer-to-Peer Applications Peer-to-peer networking is also a new area of communication with a lot of potential.
The most notable internet is called the Internet, and is composed of thousands of interconnected networks. Figure below shows a conceptual (not geographical) view of the Internet. The figure shows the Internet as several backbones, provider networks, and customer networks.
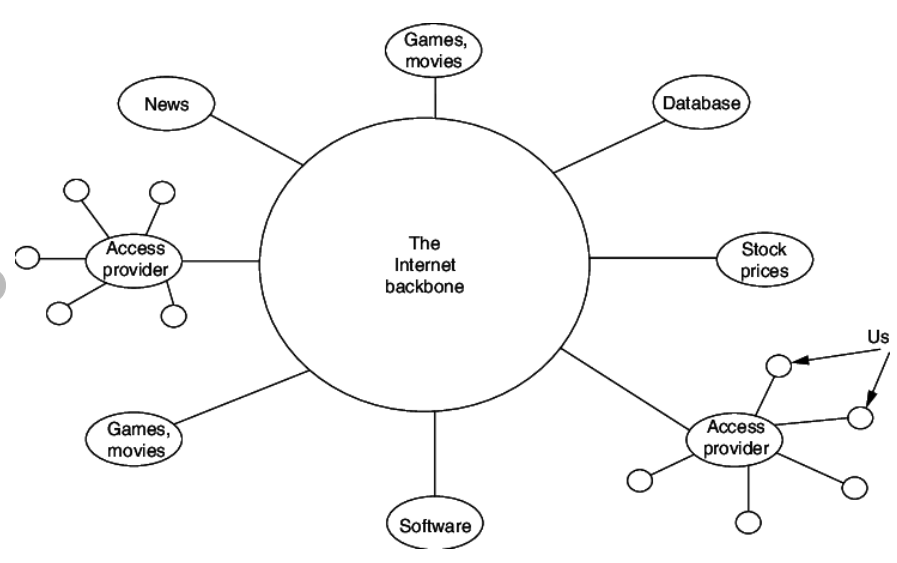
Fig: The Internet Today
- At the top level, the backbones are large networks owned by some communication companies such as Sprint, Verizon (MCI), AT&T, and NTT.
- The backbone networks are connected through some complex switching systems, called peering points.
- At the second level, there are smaller networks, called provider networks, that use the services of the backbones for a fee.
- The provider networks are connected to backbones and sometimes to other provider networks.
- The customer networks are networks at the edge of the Internet that actually use the services provided by the Internet. They pay fees to provider networks for receiving services.
- Backbones and provider networks are also called Internet Service Providers (ISPs).
- The backbones are often referred to as international ISPs; the provider networks are often referred to as national or regional ISPs.
Q15) How the layers of ISO model are layered to perform task. Draw and explain?
A16) In layered architecture of Network Model, one whole network process is divided into small tasks. Each small task is then assigned to a particular layer which works dedicatedly to process the task only. Every layer does only specific work.
In layered communication system, one layer of a host deals with the task done by or to be done by its peer layer at the same level on the remote host. The task is either initiated by layer at the lowest level or at the top most level. If the task is initiated by the-top most layer, it is passed on to the layer below it for further processing. The lower layer does the same thing, it processes the task and passes on to lower layer. If the task is initiated by lower most layer, then the reverse path is taken.
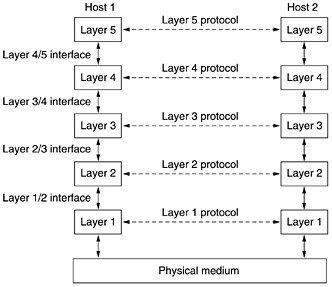
Fig: Layered Task
Every layer clubs together all procedures, protocols, and methods which it requires to execute its piece of task. All layers identify their counterparts by means of encapsulation header and tail.
Q16) Explain the layer 3 network addressing of Network Layer?
A17) In layer 3 network addressing is one of the major tasks of Network Layer.
Network Addresses are Logical which means these are software- based addresses which are changed by appropriate configurations.
A network address always points to host / node / server or it can represent a whole network.
Network address is always configured on network interface card and is generally mapped by system with the MAC address of the machine for Layer-2 communication.
There are different kinds of network addresses that is:
- IP
- IPX
- AppleTalk
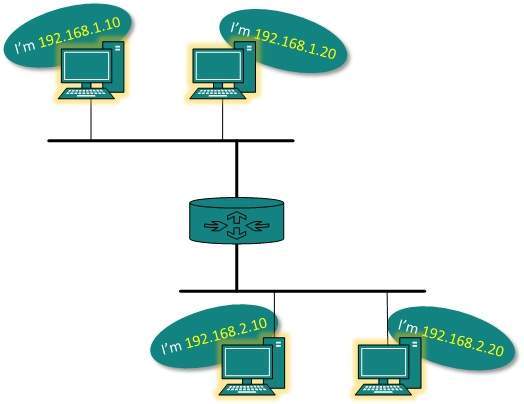
IP addressing provides a mechanism to differentiate between hosts and network. Because IP addresses are assigned in hierarchical manner the host always resides under a specific network.
The host which needs to communicate outside its subnet, needs to know destination network address where the packet/data is to be sent.
Hosts in different subnet need a mechanism to locate each other. This task is done by DNS. DNS is a server which provides Layer-3 address of remote host mapped with its domain name.
When a host acquires the Layer-3 Address (IP Address) of the remote host, it forwards all its packet to its gateway. A gateway is a router equipped with all the information which leads to route packets to the destination host.
Q17) What is line coding? Explain its properties?
A18) A line code is the code used for data transmission of a digital signal over a transmission line. This process of coding is chosen so as to avoid overlap and distortion of signal such as inter-symbol interference.
Properties of Line Coding
Following are the properties of line coding −
- As the coding is done to make more bits transmit on a single signal, the bandwidth used is much reduced.
- For a given bandwidth, the power is efficiently used.
- The probability of error is much reduced.
- Error detection is done and the bipolar too has a correction capability.
- Power density is much favorable.
- The timing content is adequate.
- Long strings of 1s and 0s is avoided to maintain transparency.
Q18) Explain the Unipolar signaling with its waveforms?
A19) Unipolar Signaling
Unipolar signaling is also called as On-Off Keying or simply OOK.
The presence of pulse represents a 1 and the absence of pulse represents a 0.
There are two variations in Unipolar signaling −
- Non Return to Zero NRZ
- Return to Zero RZRZ
Unipolar Non-Return to Zero NRZ
In this type of unipolar signaling, a High in data is represented by a positive pulse called as Mark, which has a duration T0 equal to the symbol bit duration. A Low in data input has no pulse.
The following figure clearly depicts this.
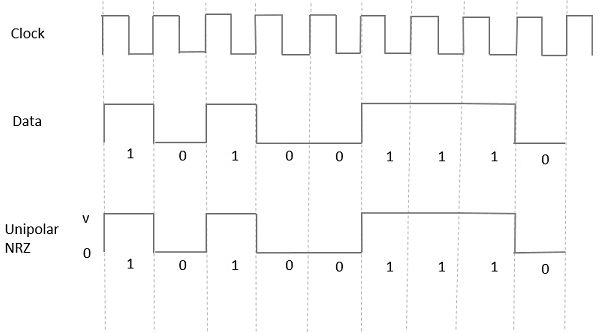
Fig: Uni-polar NRZ
Advantages
The advantages of Unipolar NRZ are −
- It is simple.
- A lesser bandwidth is required.
Disadvantages
The disadvantages of Unipolar NRZ are −
- No error correction done.
- Presence of low frequency components may cause the signal droop.
- No clock is present.
- Loss of synchronization is likely to occur (especially for long strings of 1s and 0s).
Unipolar Return to Zero RZRZ
In this type of unipolar signaling, a High in data, though represented by a Mark pulse, its duration T0 is less than the symbol bit duration. Half of the bit duration remains high but it immediately returns to zero and shows the absence of pulse during the remaining half of the bit duration.
It is clearly understood with the help of the following figure.
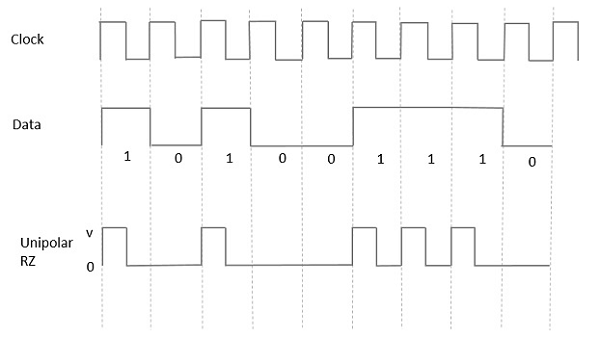
Fig: Unipolar RZ
Advantages
The advantages of Unipolar RZ are −
- It is simple.
- The spectral line present at the symbol rate can be used as a clock.
Disadvantages
The disadvantages of Unipolar RZ are −
- No error correction.
- Occupies twice the bandwidth as unipolar NRZ.
- The signal droop is caused at the places where signal is non-zero at 0 Hz.
Q19) Explain Polar Signaling with its types?
A20) There are two methods of Polar Signaling. They are −
- Polar NRZ
- Polar RZ
Polar NRZ
In this type of Polar signaling, a High in data is represented by a positive pulse, while a Low in data is represented by a negative pulse. The following figure depicts this well.
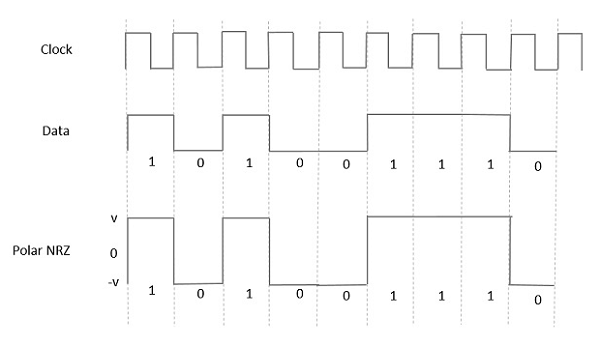
Fig: Polar NRZ
Advantages
The advantages of Polar NRZ are −
- It is simple.
- No low-frequency components are present.
Disadvantages
The disadvantages of Polar NRZ are −
- No error correction.
- No clock is present.
- The signal droop is caused at the places where the signal is non-zero at 0 Hz.
Polar RZ
In this type of Polar signaling, a High in data, though represented by a Mark pulse, its duration T0 is less than the symbol bit duration. Half of the bit duration remains high but it immediately returns to zero and shows the absence of pulse during the remaining half of the bit duration.
However, for a Low input, a negative pulse represents the data, and the zero level remains same for the other half of the bit duration. The following figure depicts this clearly.
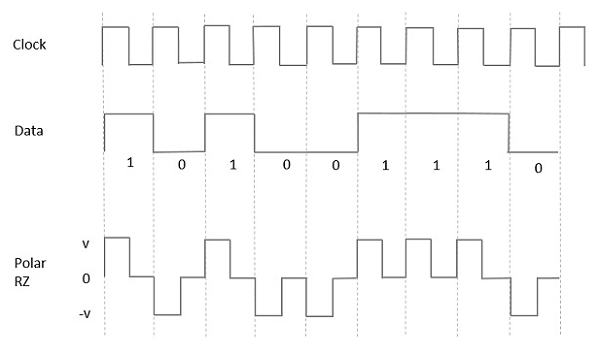
Fig: Polar RZ
Advantages
The advantages of Polar RZ are −
- It is simple.
- No low-frequency components are present.
Disadvantages
The disadvantages of Polar RZ are −
- No error correction.
- No clock is present.
- Occupies twice the bandwidth of Polar NRZ.
- The signal droop is caused at places where the signal is non-zero at 0 Hz.