Unit - 3
Multiple Access
Q1) What is channelization in multiple access techniques?
A1) In this, the available bandwidth of the link is shared in time, frequency and code to multiple stations to access channel simultaneously.
- Frequency Division Multiple Access (FDMA) – The available bandwidth is divided into equal bands so that each station can be allocated its own band. Guard bands are also added so that no to bands overlap to avoid crosstalk and noise.
- Time Division Multiple Access (TDMA) – In this, the bandwidth is shared between multiple stations. To avoid collision time is divided into slots and stations are allotted these slots to transmit data. However, there is overhead of synchronization as each station needs to know its time slot. This is resolved by adding synchronization bits to each slot. Another issue with TDMA is propagation delay which is resolved by addition of guard bands.
For more details refer – Circuit Switching - Code Division Multiple Access (CDMA) – One channel carries all transmissions simultaneously. There is neither division of bandwidth nor division of time. For example, if there are many people in a room all speaking at the same time, then also perfect reception of data is possible if only two persons speak the same language. Similarly, data from different stations can be transmitted simultaneously in different code languages.
Q2) Compare the multiple access techniques?
A2)
Approach | SDMA | TDMA | FDMA | CDMA |
Idea | Segment space into cells/sectors | Segment sending time into disjoint time-slots, demand driven or fixed patters | Segment the frequency band into disjoint sub-bands | Spread the spectrum using orthogonal codes
|
Terminals | Only one terminal can be active in one cell/one sector | All terminals are active for short periods of time on the same frequency | Every terminal has its own frequency. Uninterrupted | All terminals can be active at the same place at the same moment uninterrupted. |
Signal separation | Cell structure, directed antennas | Synchronization in the time domain | Filtering in the frequency domain | Code plus special receivers |
Advantages | Very simple, increases capacity per km2 | Established, fully digital, flexible | Simple, established robust | Flexible, less frequency planning needed, soft handover |
Disadvantages | Inflexible, antennas typically fixed | Guard space needed (multipath propagation), synchronization difficult | Inflexible, frequencies are a scarce resource | Complex receivers, needs more complicated power control for senders |
Comment | Only in combination with TDMA, FDMA or CDMA useful | Standard in fixed networks, together with FDMA/SDMA used in many mobile networks | Typically combined with TDMA (frequency hopping patterns) and SDMA (frequency reuse) | Still faces some problems, higher complexity, lowered expectations: will be integrated with TDMA/FDMA |
Q3) How CSMA/CA avoids collision?
A3) Carrier sense multiple access with collision avoidance. The process of collisions detection involves sender receiving acknowledgement signals. If there is just one signal (its own) then the data is successfully sent but if there are two signals (its own and the one with which it has collided) then it means a collision has occurred. To distinguish between these two cases, collision must have a lot of impact on received signal. However, it is not so in wired networks, so CSMA/CA is used in this case.
CSMA/CA avoids collision by:
- Inter frame space – Station waits for medium to become idle and if found idle it does not immediately send data (to avoid collision due to propagation delay) rather it waits for a period of time called Inter frame space or IFS. After this time it again checks the medium for being idle. The IFS duration depends on the priority of station.
- Contention Window – It is the amount of time divided into slots. If the sender is ready to send data, it chooses a random number of slots as wait time which doubles every time medium is not found idle. If the medium is found busy it does not restart the entire process, rather it restarts the timer when the channel is found idle again.
- Acknowledgement – The sender re-transmits the data if acknowledgement is not received before time-out.
Q4) Explain the access modes of CSMA?
A4) Carrier Sense Multiple Access ensures fewer collisions as the station is required to first sense the medium (for idle or busy) before transmitting data. If it is idle then it sends data, otherwise it waits till the channel becomes idle. However there is still chance of collision in CSMA due to propagation delay. For example, if station A wants to send data, it will first sense the medium. If it finds the channel idle, it will start sending data. However, by the time the first bit of data is transmitted (delayed due to propagation delay) from station A, if station B requests to send data and senses the medium it will also find it idle and will also send data. This will result in collision of data from station A and B.
CSMA access modes-
- 1-persistent: The node senses the channel, if idle it sends the data, otherwise it continuously keeps on checking the medium for being idle and transmits unconditionally (with 1 probability) as soon as the channel gets idle.
- Non-Persistent: The node senses the channel, if idle it sends the data, otherwise it checks the medium after a random amount of time (not continuously) and transmits when found idle.
- P-persistent: The node senses the medium, if idle it sends the data with p probability. If the data is not transmitted ((1-p) probability) then it waits for some time and checks the medium again, now if it is found idle then it sends with p probability. This repeat continues until the frame is sent. It is used in Wifi and packet radio systems.
- O-persistent: Superiority of nodes is decided beforehand and transmission occurs in that order. If the medium is idle, node waits for its time slot to send data.
Q5) Explain the random access protocols in computer network?
A5)
In this, all stations have same superiority that is no station has more priority than another station. Any station can send data depending on medium’s state (idle or busy). It has two features:
- There is no fixed time for sending data
- There is no fixed sequence of stations sending data
The Random-access protocols are further subdivided as:
(a) ALOHA – It was designed for wireless LAN but is also applicable for shared medium. In this, multiple stations can transmit data at the same time and can hence lead to collision and data being garbled.
- PureAloha:
When a station sends data it waits for an acknowledgement. If the acknowledgement doesn’t come within the allotted time. Then the station waits for a random amount of time called back-off time (Tb) and re-sends the data. Since different stations wait for different amount of time, the probability of further collision decreases. - Vulnerable Time = 2* Frame transmission time
- Throughput = G exp{-2*G}
Maximum throughput = 0.184 for G=0.5
- Slotted Aloha:
- It is similar to pure aloha, except that we divide time into slots and sending of data is allowed only at the beginning of these slots. If a station misses out the allowed time, it must wait for the next slot. This reduces the probability of collision.
- Vulnerable Time = Frame transmission time
- Throughput = G exp{-*G}
Maximum throughput = 0.368 for G=1
Q6) Explain the process of collision detection in CSMA/CD?
A6) Process –
The entire process of collision detection is explained as:
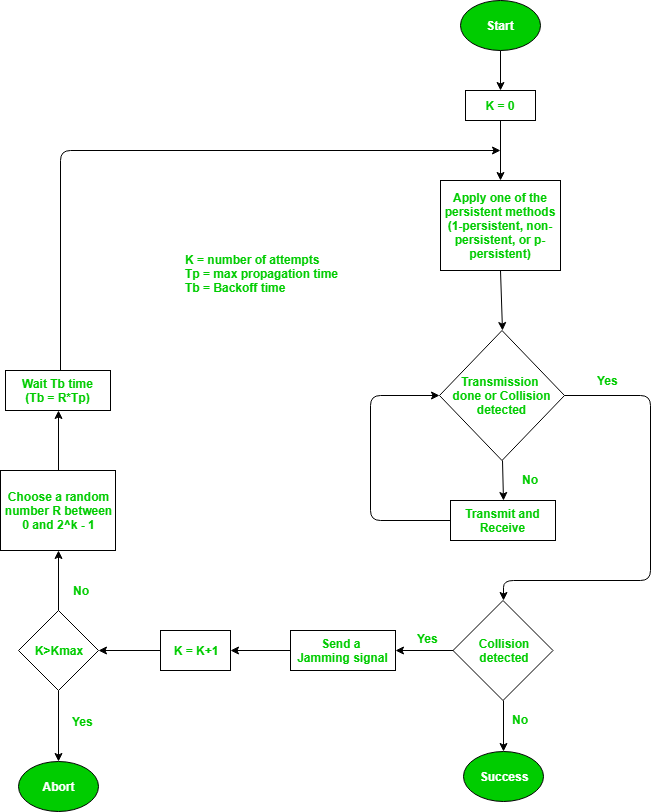
Fig: Process of collision detection
Throughput and Efficiency – The throughput of CSMA/CD is much greater than pure or slotted ALOHA.
- For 1-persistent method throughput is 50% when G=1.
- For non-persistent method throughput can go upto 90%.
Q7) Explain the strategies of CSMA/CA?
A7) Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) –
In CSMA/CA is that the station should be able to receive while transmitting to detect a collision from different stations.
In wired networks, if a collision has occurred then the energy of received signal almost doubles and the station can sense the possibility of collision.
In wireless networks, most of the energy is used for transmission and the energy of received signal increases by only 5-10% if there is collision.
It cannot be used by the station to sense collision. Therefore CSMA/CA has been specially designed for wireless networks.
These are three types of strategies:
- InterFrame Space (IFS) – When a station finds the channel busy, it waits for a period of time called IFS time. IFS can also be used to define the priority of a station or a frame. Higher the IFS lower is the priority.
- Contention Window – It is the amount of time divided into slots. A station which is ready to send frames chooses random number of slots as wait time.
Acknowledgements – The positive acknowledgements and time-out timer can help guarantee a successful transmission of the frame.
Q8) Explain Polling the controlled access technique?
A8) Polling
- Polling process similar to roll-call is performed in class. Just like the teacher, a controller sends a message to each node in turn.
- In this, one acts as a primary station(controller) and the others are secondary stations. All data exchanges must be made through the controller.
- The message sent by the controller contains the address of the node being selected for granting access.
- Although all nodes receive the message only the addressed one responds to it and sends data. If there is no data, usually a “poll reject” (NAK) message is sent back.
- Problems include high overhead of the polling messages and high dependence on the reliability of the controller.
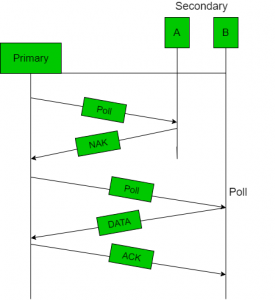
Fig: Polling
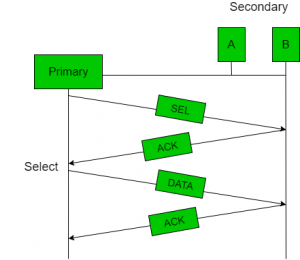
Fig: Polling Acknowledge
Efficiency
Let Tpoll be the time for polling and Tt be the time required for transmission of data. Then,
Efficiency = Tt / (T t + T poll)
Q9) Explain how only one channel occupies the entire bandwidth of the link in CDMA?
A9) CDMA means communication with different codes. CDMA differs from FDMA because only one channel occupies the entire bandwidth of the link. It differs from TDMA because all stations can send data simultaneously and there is no timesharing.
Let us assume we have four stations 1, 2, 3, and 4 connected to the same channel. The data from station 1 are d1, from station 2 are d2, and so on. The code assigned to first station is c1, and second is c2, and so on. We assume that the assigned codes have two properties.
1. If we multiply each code by another, we get 0.
2. If we multiply each code by itself, we get 4 that is the number of stations.
With this in picture the four stations can send data using the same common channel, as shown in the following figure.
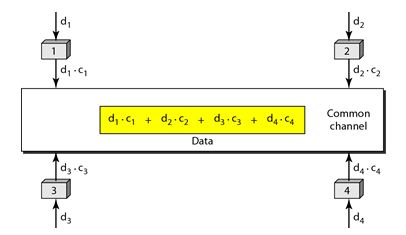
Fig: Four station sending data using common channel
Station 1 multiplies its data by its code to get d1.c1. Station 2 multiplies its data by its code to get d2.c2. And so on. The data that go on the channel are the sum of all these terms, as shown in the box.
Any station that wants to receive data from one of the other three multiplies the data on the channel by the code of the sender.
For example, suppose stations 1 and 2 are talking to each other. Station 2 wants to hear what station 1 is saying. It multiplies the data on the channel by c1 the code of station1.
Because (c1.c1) is 4, but (c2. c1), (c3. c1), and (c4 .c1) are all 0s, station 2 divides the result by 4 to get the data from station1.
Data =(d1.c1+d2.c2+d3.c3+d4.c4).c1
= c1. d1. c1+ c1. d2. c2+ c1. d3. c3+ c1. d4. c4= 4d1
Q10) Explain the CSMA/CD?
A10) Carrier Sense Multiple Access with Collision Detection (CSMA/CD) –
In this method, a station monitors the medium after it sends a frame to see if the transmission was successful. If successful, the station is finished, if not, the frame is sent again.
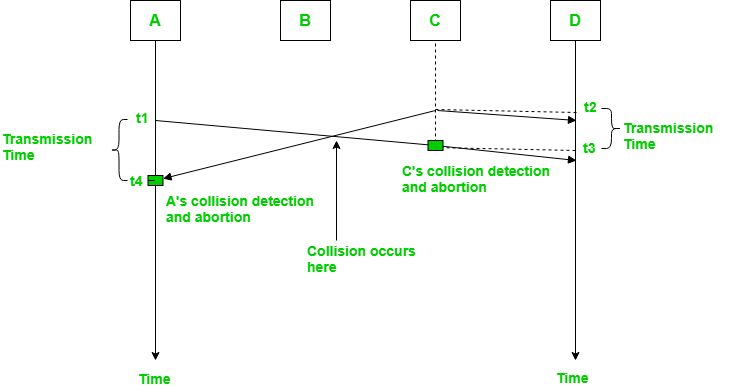
Fig: Frame Transmission
In the diagram, A starts to send the first bit of its frame at t1 and since C sees the channel idle at t2, starts sending its frame at t2. C detects A’s frame at t3 and aborts transmission. A detects C’s frame at t4 and aborts its transmission. Transmission time for C’s frame is therefore t3-t2 and for A’s frame is t4-t1.
Therefore, frame transmission time (Tfr) should be at least twice the maximum propagation time (Tp). This can be deduced when the two stations involved in collision are maximum distance apart.
Process–
The entire process of collision detection is explained as:
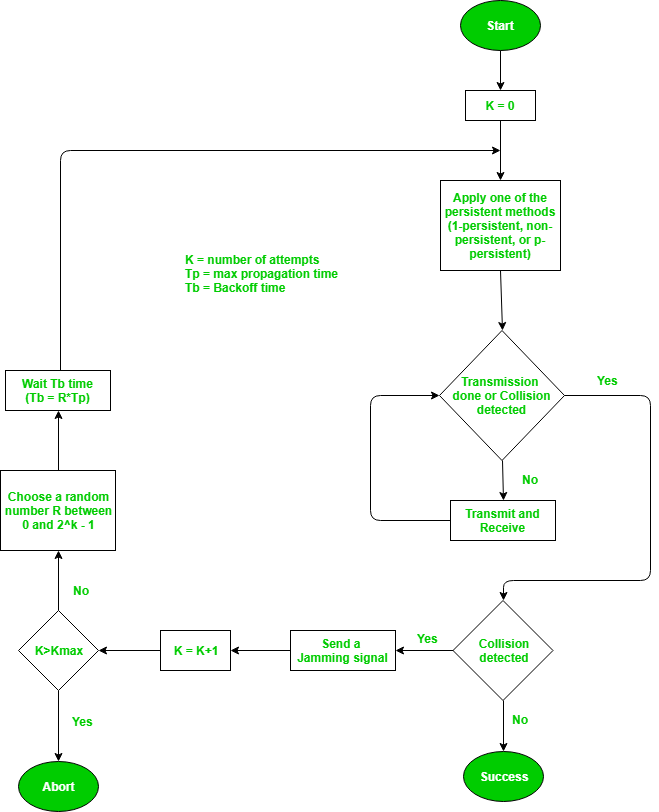
Fig: Process of collision detection
Throughput and Efficiency – The throughput of CSMA/CD is much greater than pure or slotted ALOHA.
- For 1-persistent method throughput is 50% when G=1.
- For non-persistent method throughput can go upto 90%.
Q11) Explain the reservation controlled access method?
A11) Reservation
- In the reservation method, a station needs to make a reservation before sending data.
- The time-line has two kinds of periods:
- Reservation interval of fixed time length
- Data transmission period of variable frames.
- If there are M stations, the reservation interval is divided into M slots, and each station has one slot.
- Suppose if station 1 has a frame to send, it transmits 1 bit during the slot 1. No other station can transmit during this slot.
- In general, i th station may announce that it has a frame to send by inserting a 1 bit into i th slot. After all N slots have been checked, each station knows which stations wish to transmit.
- The stations which have reserved their slots transfer their frames in that order.
- After data transmission period, next reservation interval begins.
- Since everyone agrees on who goes next, there will never be any collisions.
The following figure shows a situation with five stations and a five- slot reservation frame.
In the first interval, only stations 1, 3, and 4 have made reservations. In the second interval, only station 1 has made a reservation.

Fig: Stations with slot reservations
Q12) What is token passing in controlled access techniques. List the performance parameter of the token ring?
A12) Token Passing
- In token passing scheme, the stations are connected logically to each other in form of ring and access of stations is governed by tokens.
- A token is a special bit pattern or a small message, which circulate from one station to the next in some predefined order.
- In Token ring, token is passed from one station to another adjacent station in the ring whereas in Token bus, each station
uses the bus to send the token to the next station in some predefined order. - In both cases, token represents permission to send. If a station has a frame queued for transmission when it receives the token, it can send that frame before it passes the token to the next station. If it has no queued frame, it passes the token simply.
- After sending a frame, each station must wait for all N stations (including itself) to send the token to their neighbours and the other N – 1 stations to send a frame, if they have one.
- Problems like duplication of token or token is lost or insertion of new station, removal of a station, which need be tackled for correct and reliable operation of this scheme.

Fig: Token
Performance
Performance of token ring is concluded by 2 parameters: -
- Delay, which is a measure of time between when the packet is ready and when it is delivered. So, the average time (delay) required to send a token to the next station = a/N.
- Throughput, which is a measure of the successful traffic.
Throughput S = 1/(1+a/N) for a<1 and
S= 1/ {a(1+1/N)} for a>1
Where N = number of stations
a = Tp / Tt; Tp = Propagation delay, Tt = Transmission delay.
Q13) What is fast ethernet?
A13) Ethernet is very popular physical layer LAN technology which is in use today. It defines that how many conductors that are required for a connection, the performance thresholds that can be expected, and most importantly provides the framework for data transmission. A standard Ethernet network can transmit the data at a rate up to 10 Megabits per second (10 Mbps). Other LAN types include Token Ring, Fast Ethernet, Gigabit Ethernet, 10 Gigabit Ethernet, Fibre Distributed Data Interface (FDDI), Asynchronous Transfer Mode (ATM) and Local Talk.
Ethernet is popular because it strikes a very good balance between speed, cost and ease of installation. These benefits, combined with wide acceptability in the computer marketplace and the ability to support virtually all the popular network protocols, which make Ethernet an ideal networking technology for most of the computer users today.
The Institute for Electrical and Electronic Engineers developed an Ethernet standard that is known as IEEE Standard 802.3. This standard defines the rules for configuring an Ethernet network and then also specifies how the elements in an Ethernet network interact with one another and work. By adhering to the IEEE standard, network equipment and network protocols can communicate very efficiently.
Fast Ethernet
Fig: Twisted pair cable
The fast Ethernet is a type of Ethernet network that can be transfer the data at a speed of 100 Mbps using a twisted-pair cable or a fibre-optic cable. The older 10 Mbps Ethernet is still used, but such kind of networks does not provide necessary bandwidth for some network-based video applications.
Fast Ethernet is based on CSMA/CD Media Access Control (MAC) protocol, and use10BaseT cabling. Data can move from 10 Mbps to 100 Mbps without any protocol translation or changes done to the application and networking software.
Q14) Write short notes on IEEE 802.11?
A14) IEEE 802.11 is a set of standards carrying out wireless local area network (WLAN) computer communication in the 2.4, 3.6 and 5 GHz frequency bands. They are created and maintained by the IEEE LAN/MAN Standards Committee (IEEE 802)
802.11a — an extension to 802.11 that applies to wireless LANs and provides up to 54-Mbps in the 5GHz band. 802.11a uses an orthogonal frequency division multiplexing encoding scheme rather than FHSS or DSSS.
802.11b — an extension to 802.11 that applies to wireless LANS and provides 11 Mbps transmission in the 2.4 GHz band. 802.11b uses only DSSS. 802.11b was a 1999 ratification to the original 802.11 standard, allowing wireless functionality comparable to Ethernet.
802.11e — a wireless draft standard that defines the Quality of Service support for LANs, and is an enhancement to the 802.11a and 802.11b wireless LAN (WLAN) specifications. 802.11e adds QoS features and multimedia support to the existing IEEE 802.11b and IEEE 802.11a wireless standards, while maintaining full backward compatibility with these standards.
802.11g — applies to wireless LANs and is used for transmission over short distances at up to 54-Mbps in the 2.4 GHz bands.
802.11n — 802.11n builds upon previous 802.11 standards by adding multiple-input multiple-output. The additional transmitter and receiver antennas allow for increased data throughput through spatial multiplexing and increased range by exploiting the spatial diversity through coding schemes like Alamouti coding. The real speed would be 100 Mbit/s (even 250 Mbit/s in PHY level), and so up to 4-5 times faster than 802.11g.
Q15) Explain the architecture of IEEE 802.16?
A15) The IEEE 802.16 standard provides for two main distinct uses of this technology, point to point (PTP) and point to multipoint (PMP), as shown in Figure 13. PTP connections may be independent from all other systems or networks. A PMP system allows a radio system to provide services to multiple users. WiMAX systems consist of:
- Subscriber stations (SS) – receive and convert radio signals into user information.
- Base stations (BS) – this is the cell site. Base stations convert signals from SSs into a form that can be transferred into the wireless network and conversely.
- Interconnecting switches and transmission lines – transfer signals between BS and other systems (such as PSTN or the Internet)
- Databases – similar to cellular network structure, these are collections of data that is interrelated and stored in memory. These databases usually contain subscriber information, equipment configuration, feature lists and security codes.
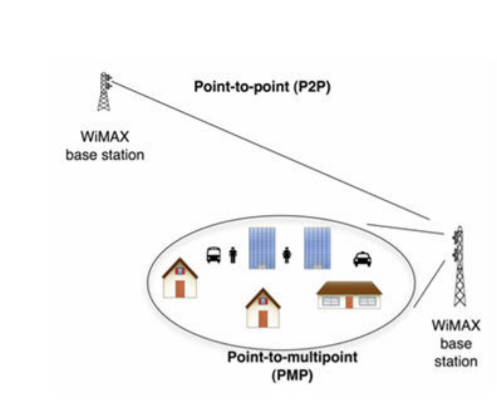
Fig: Description of PTP and PMP
The original 802.16 industry specification was for a line of sight system that would operate in the 10GHz to 66 GHz radio spectrum. Not long after, there was a growing need to operate in the lower ranges, namely in the 2GHz to 11GHz bands, because they are less susceptible to physical obstacles. The 802.16a specification was developed to address operation in the new spectrum ranges. Recently, several different revisions have been developed to address an operating range between 2GHz and 66GHz that allow for mobility and higher data rates. More importantly, the new revisions allow for operation in both line-of-sight (LOS) and non-line-of-sight (NLOS) environments as shown in Figure below.
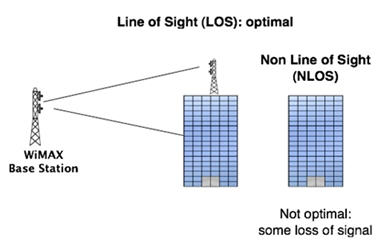
Figure: LOS vs. NLOS
Q16) List the difference between 802.11 and 802.16?
A17)
S.No. | 802.16 | 802.11 |
01. | IEEE 802.16 standard defines WiMAX. | IEEE 802.11 standard defines WLAN or WiFi. |
02. | It is designed for long distance/wide area. | It is designed for limited area. |
03. | It provides a coverage range of 7 km to 50 km. | It provides a coverage range of 30 m to 100m. |
04. | 802.16 standard is used for outdoor usage. | 802.11 standard is used for indoor usage. |
05. | It operates on frequencies of 2.4 GHz, 5 GHz. | It operates on frequencies of 2.5 GHz, 3.5 GHz, 5.8GHz. |
06. | Standard variants of 802.16 are 802.16a, 802.16d, 802.16e, 802.16m etc. | Standard variants of 802.11 are 802.11a, 11b, 11g, 11n, 11ac, 11ad etc. |
07. | It provides a data rate of 100 Mbps in a 20 MHz channel. | It provides a data rate of 54 Mbps in 20 MHz channel. |
08. | Large number of customers are connected to this as it covers a wide area. | Limited number of customers/devices are connected which are with in the limited range. |
09. | For encryption purpose it uses Data Encryption Standard with Advanced Encryption Standard. | For encryption purpose it uses Rivest Cipher 4. |
10. | Different QoS options are available like UGS, rtPS, nrtPS, BE, etc | It does not provide any QoS but Supported in IEEE 802.11e. |
11. | Bandwidths varies dynamically as per user requirement from 1.5 to 28 MHz. | Bandwidth variants are 20 MHz, 40MHz, 80MHz and 160 MHz. |
Q17) Explain protocol layering of 802.16 in data link layer?
A18) 802.16 MAC Layers and Sublayers Media Access Control (MAC) controls access to whatever physical transmission medium is being used by the device that wishes to transmit. The functionality of the MAC layer is usually “hard-coded” into the device and always includes a unique address (the MAC address) that identifies the machine that houses the network adapter. The 802.16 MAC protocol was designed with a number of required characteristics in mind. First, it was created to handle the demands of PTMP broadband wireless applications. Within that definition, it also was designed to provide very high, full-duplex (uplink and downlink) bandwidth, with that bandwidth being capable of being parceled out across a collection of channels with scores of users in each channel.
Additionally, users place varying demands on the channels they are allocated; this translates into a requirement to support traditional voice and data services as well as packet-based Voice over Internet Protocol (VoIP) and other Internet Protocol (IP) data services. The MAC, then, must be able to handle the demands of both constant bit rate (CBR) and bursty traffic and must support variable QoS as demanded by the user community.
The MAC layer consists of three sublayers – convergence sublayer, common part sublayer, and security sublayer as shown in Figure below. The MAC includes a convergence sublayer to better handle the higher-layer protocols placed above the MAC. The central part of the MAC is the common part sublayer. It handles channel access, connection establishment and maintenance, and QoS. The third sublayer is the security sublayer, providing authentication, secure key exchange, and secure data exchange. The security sublayer is out of the scope of this thesis. The convergence sublayer is not a physical, but rather a logical interface since it is a separate part of the MAC.
The common part sublayer is the central part of the IEEE 802.16 MAC. It defines the multiple-access mechanism. In the downlink for the 802.16d, the base station is the only transmitter that is operating. Therefore, it does not have to coordinate its transmissions with other stations. The base station broadcasts to all stations. Stations check the address in the received messages and retain only those addressed to them. In the uplink direction, the user stations share the channel.
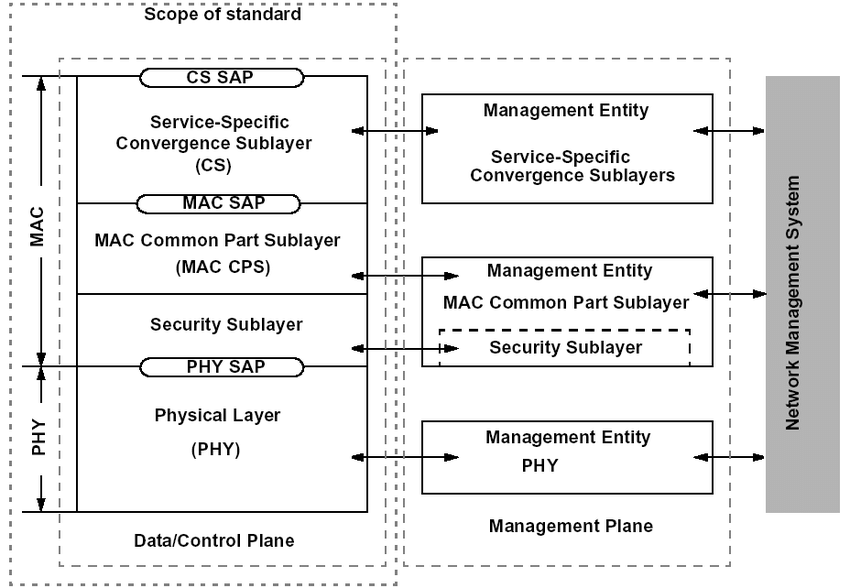
Figure: Protocol Layering of 802.16
Q18) What is Gigabit Ethernet?
A19) Gigabit Ethernet

Fig: Optic fiber cable
The Gigabit Ethernet is a type of Ethernet network that is capable of transferring data at a speed of 1000 Mbps based on a twisted-pair or fiber optic cable, and it is very commonly used. The type of twisted-pair cables that support Gigabit Ethernet is the Cat 5e cable, where all the four pairs of twisted wires of the cable are used to achieve the very high data transfer rates. The 10 Gigabit Ethernet is a very latest generation Ethernet capable of transferring data at a speed of 10 GBPS using twisted-pair or fiber optic cable.