UNIT 3
Inter-process Communication
- Request. The process request for the resource first. In the event that the request can't be assigned quickly (for instance, if the resource is being utilized by another process), at that point the mentioning process must wait until it can procure the resource.
- Use. The process can work on the resource (for instance, if the resource is a printer, the process can print on the printer).
- Release. The process releases the resource after utilizing it.
2. Explain Deadlock characterization
Mutual Exclusion


Allocated

Hold and Wait
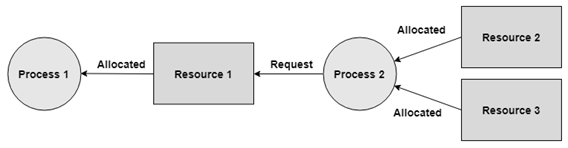
No Pre-emption
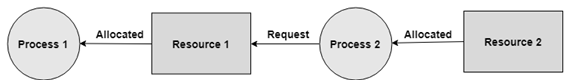
Circular Wait
3. What is Resource-Allocation Graph in an operating system?
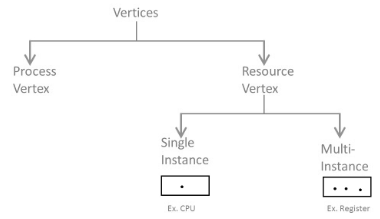
- Process vertex – Every process will be shown as a process vertex. In RAG, the process will be drawn with a circle.
- Resource vertex – Every resource will be shown as a resource vertex. It is likewise of two types –
- Single instance type resource – It is drawn as a rectangle, inside the rectangle, there will be one dot. So the quantity of dots demonstrate what number of instances are available of every resource type.
- Multi-resource instance type resource – It is also shown as a rectangle, inside the rectangle, there will be numerous dots present.
- Assign Edges-
- Assign edges shows the assigned of resources to the processes.
- They are drawn as an arrow pointed towards the process and tail focuses to the resource.
- Request Edges-
- Request edges shows the waiting condition of processes for the resources.
- They are drawn as arrow where the head of the arrow indicates the instance of the resource and tail of the arrow focuses to the process.
- On the off chance that a process requires 'n' instances of a resource type, at that point 'n' assign edges will be drawn.
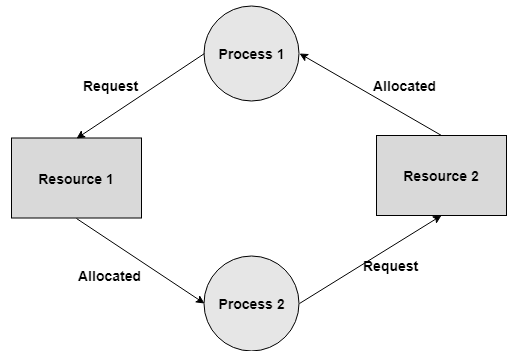
Example- Resource Allocation Graph is shown in figure below:
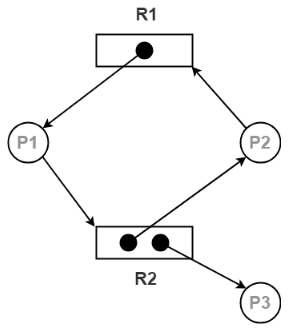
The above graph describes the accompanying data:
4. Explain Methods for handling in an operating system
- We can utilize a protocol to prevent or avoid deadlocks, through which we can guarantee that the system will never enter a deadlock state.
- In second way we can enable the system to enter a deadlock state, detect it, and recover from it.
- Third solution is the simplest one in which we can ignore the issue and imagine that deadlock never happen in the system.
5. What is Deadlocks Deadlock prevention in an operating system?
- Necessitate that all processes demand all resources one at the same time. This can be wastage of system resources if a process needs one resource in the initial stage of its execution and does not need some other resource until some other time.
- Necessitate that processes holding resources must discharge them before requesting new resources, and after that re-acquire the resources alongside the new ones out of a single new demand. This can be an issue in the event that a process has somewhat finished an activity utilizing a resource and, at that point neglects to get it re-allocated after releasing it.
- Both of the strategies portrayed above can prompt starvation if a process requires at least one well known resource.
No Pre-emption
- One methodology is that in the event that a process is compelled to hold up when mentioning another resource, at that point every other resource recently held by this process are certainly discharged, (appropriated), constraining this process to re-acquire the old resources alongside the new resources in a single request.
- Another methodology is that when a resource is requested and not accessible, at that point the system hopes to perceive what different processes right now have those resources and are themselves blocked waiting for some other resource. On the off chance that such a process is discovered, at that point a portion of their resources may get acquired and added to the list of resources for which the process is waiting.
- Both of these methodologies might be relevant for resources whose states are effectively saved and resorted, for example, registers and memory, yet are commonly not applicable to different devices, for example, printers and tape drives.
Approach
6. What is Deadlock avoidance in an operating system?
Process | Maximum needs | Current allocated |
P0 | 8 | 4 |
P1 | 4 | 2 |
P2 | 8 | 2 |
7. Explain Resource-Allocation-Graph Algorithm
8. What is Banker’s Algorithm?
- Available[m] demonstrates what numbers of resources are at present available of each kind.
- Max[n][m] demonstrates the maximum request of each process of every resource.
- Allocation[n][m] demonstrates the quantity of every resource class allocated to each process.
- Need[n][m] demonstrates the rest of the resources required of each type for each process. (Note that Need[i][j] = Max[i][j] - Allocation[i][j] for all i, j)
- One row of the Need vector, Need[i], can be treated as a vector comparing to the requirements of process i, and comparatively for Allocation and Max.
- A vector X is viewed as <= a vector Y if X[i] <= Y[i] for all i.
9. What is Safety Algorithm?
We would now be able to exhibit the algorithm for seeing if or not a system is in a safe state. This algorithm can be portrayed as follows:
Work = Available and Finish[i] = false for i = 0, 1, ... , n - 1.
2. Find an index i with the end goal that both
On the off chance that no such i exists, go to step 4.
3. Work = Work + Allocation;
Finish[i] = true
Go to step 2.
4. In case Finish[i] = = true for all i, at that point the system is in a safe state.
This algorithm may require a request for m x n2 operations to decide if a state is safe or not.
Resource-Request Algorithm- If Requesti ≤ Needi, go to step 2. Otherwise, raise an error condition, since the process has exceeded its maximum claim.
- In the event that Requesti ≤ Available, go to step 3. Otherwise Pi must wait, since the resources are not accessible.
- Have the system claim to have assigned the requested resources to process Pi by modifying the state as follows:
Available = Available – Requesti ;
Allocationi = Allocationi + Requesti ;
Needi = Needi – Requesti ;
4. In case the final resource-allocation state is safe, the transaction is finished, and process Pi is allocated its resources. Nonetheless, if the new state is unsafe, at that point Pi must wait for Requesti, and the old resource-allocation state is restored.
10. What is Deadlock detection in an operating system?
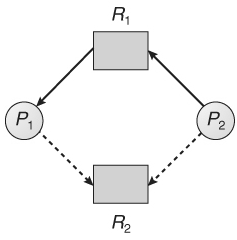
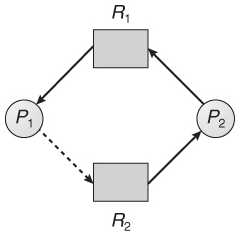
- Single instance of resource: Here to detect deadlock, we can run a algorithm to check for cycle in the Resource Allocation Graph. Presence of cycle in the graph is the adequate condition for deadlock.
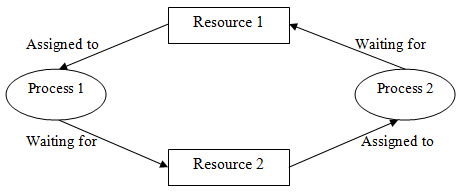
In the above graph, resource 1 and resource 2 have single occasions. There is a cycle R1 → P1 → R2 → P2. Thus, Deadlock is confirmed.
2. Multiple instances of resources: Detection of the cycle is essential yet not adequate condition for deadlock detection, for this situation, the system might be in halt fluctuates as per various circumstances.