Unit - 3
Network Layer
Q1) What is switching in computer network and why switching is required?
A1) When a user accesses the internet or another computer network outside their immediate location, messages are sent through the network of transmission media. This technique of transferring the information from one computer network to another network is known as switching.
Switching in a computer network is achieved by using switches. A switch is a small hardware device which is used to join multiple computers together with one local area network (LAN).
Network switches operate at layer 2 (Data link layer) in the OSI model.
Switching is transparent to the user and does not require any configuration in the home network.
Switches are used to forward the packets based on MAC addresses.
A Switch is used to transfer the data only to the device that has been addressed. It verifies the destination address to route the packet appropriately.
It is operated in full duplex mode.
Packet collision is minimum as it directly communicates between source and destination.
It does not broadcast the message as it works with limited bandwidth.
Why is Switching Concept required?
Switching concept is developed because of the following reasons:
Bandwidth: It is defined as the maximum transfer rate of a cable. It is a very critical and expensive resource. Therefore, switching techniques are used for the effective utilization of the bandwidth of a network.
Collision: Collision is the effect that occurs when more than one device transmits the message over the same physical media, and they collide with each other. To overcome this problem, switching technology is implemented so that packets do not collide with each other.
Q2) What is switching mode and what are different types of switching mode?
A2)
Switching Modes
The layer 2 switches are used for transmitting the data on the data link layer, and it also performs error checking on transmitted and received frames.
The layer 2 switches forward the packets with the help of MAC address.
Different modes are used for forwarding the packets known as Switching modes.
In switching mode, Different parts of a frame are recognized. The frame consists of several parts such as preamble, destination MAC address, source MAC address, user's data, FCS.
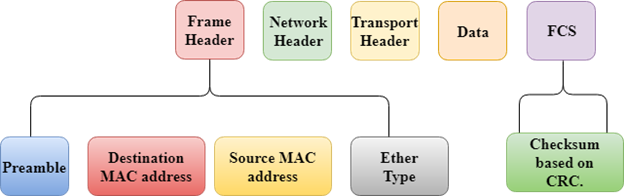
There are three types of switching modes:
Store-and-forward
Cut-through
Fragment-free
Store-and-forward
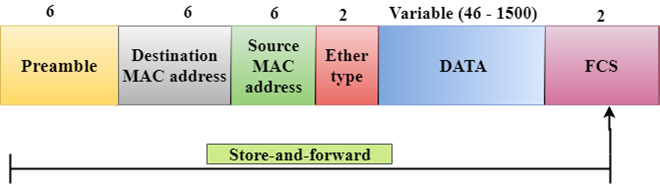
Store-and-forward is a technique in which the intermediate nodes store the received frame and then check for errors before forwarding the packets to the next node.
The layer 2 switch waits until the entire frame has received. On receiving the entire frame, switch store the frame into the switch buffer memory. This process is known as storing the frame.
When the frame is stored, then the frame is checked for the errors. If any error found, the message is discarded otherwise the message is forwarded to the next node. This process is known as forwarding the frame.
CRC (Cyclic Redundancy Check) technique is implemented that uses a number of bits to check for the errors on the received frame.
The store-and-forward technique ensures a high level of security as the destination network will not be affected by the corrupted frames.
Store-and-forward switches are highly reliable as it does not forward the collided frames.
Cut-through Switching
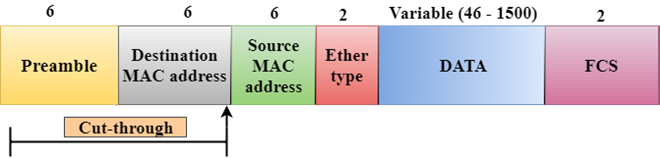
Cut-through switching is a technique in which the switch forwards the packets after the destination address has been identified without waiting for the entire frame to be received.
Once the frame is received, it checks the first six bytes of the frame following the preamble, the switch checks the destination in the switching table to determine the outgoing interface port, and forwards the frame to the destination.
It has low latency rate as the switch does not wait for the entire frame to be received before sending the packets to the destination.
It has no error checking technique. Therefore, the errors can be sent with or without errors to the receiver.
A Cut-through switching technique has low wait time as it forwards the packets as soon as it identifies the destination MAC address.
In this technique, collision is not detected, if frames have collided will also be forwarded.
Fragment-free Switching
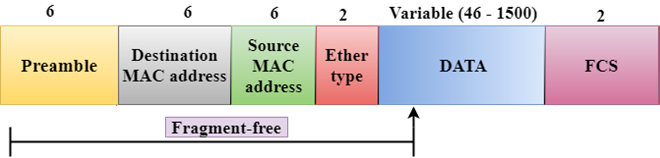
A Fragment-free switching is an advanced technique of the Cut-through Switching.
A Fragment-free switching is a technique that reads atleast 64 bytes of a frame before forwarding to the next node to provide the error-free transmission.
It combines the speed of Cut-through Switching with the error checking functionality.
This technique checks the 64 bytes of the ethernet frame where addressing information is available.
A collision is detected within 64 bytes of the frame, the frames which are collided will not be forwarded further.
Q3) Differences b/w Store-and-forward and Cut-through Switching.
A3)
Store-and-forward Switching | Cut-through Switching |
Store-and-forward Switching is a technique that waits until the entire frame is received. | Cut-through Switching is a technique that checks the first 6 bytes following the preamble to identify the destination address. |
It performs error checking functionality. If any error is found in the frame, the frame will be discarded otherwise forwarded to the next node. | It does not perform any error checking. The frame with or without errors will be forwarded. |
It has high latency rate as it waits for the entire frame to be received before forwarding to the next node. | It has low latency rate as it checks only six bytes of the frame to determine the destination address. |
It is highly reliable as it forwards only error-free packets. | It is less reliable as compared to Store-and-forward technique as it forwards error prone packets as well. |
It has a high wait time as it waits for the entire frame to be received before taking any forwarding decisions. | It has low wait time as cut-through switches do not store the whole frame or packets. |
Q4) Explain message switching
A4) Message Switching
Message Switching is a switching technique in which a message is transferred as a complete unit and routed through intermediate nodes at which it is stored and forwarded.
In Message Switching technique, there is no establishment of a dedicated path between the sender and receiver.
The destination address is appended to the message. Message Switching provides a dynamic routing as the message is routed through the intermediate nodes based on the information available in the message.
Message switches are programmed in such a way so that they can provide the most efficient routes.
Each and every node stores the entire message and then forward it to the next node. This type of network is known as store and forward network.
Message switching treats each message as an independent entity.
Advantages Of Message Switching
Data channels are shared among the communicating devices that improve the efficiency of using available bandwidth.
Traffic congestion can be reduced because the message is temporarily stored in the nodes.
Message priority can be used to manage the network.
The size of the message which is sent over the network can be varied. Therefore, it supports the data of unlimited size.
Disadvantages Of Message Switching
The message switches must be equipped with sufficient storage to enable them to store the messages until the message is forwarded.
The Long delay can occur due to the storing and forwarding facility provided by the message switching technique.
Q5) What is packet switching explain in detail with advantages and disadvantages?
A5)
Packet Switching
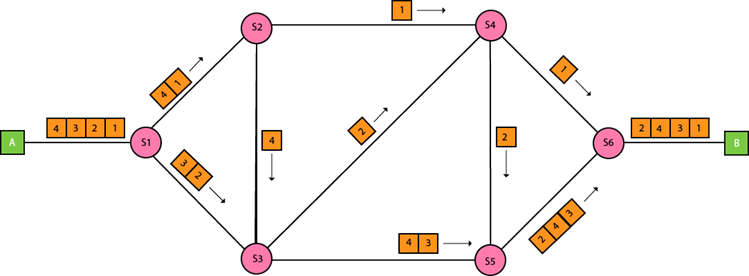
The packet switching is a switching technique in which the message is sent in one go, but it is divided into smaller pieces, and they are sent individually.
The message splits into smaller pieces known as packets and packets are given a unique number to identify their order at the receiving end.
Every packet contains some information in its headers such as source address, destination address and sequence number.
Packets will travel across the network, taking the shortest path as possible.
All the packets are reassembled at the receiving end in correct order.
If any packet is missing or corrupted, then the message will be sent to resend the message.
If the correct order of the packets is reached, then the acknowledgment message will be sent.
Approaches Of Packet Switching:
There are two approaches to Packet Switching:
Datagram Packet switching:
It is a packet switching technology in which packet is known as a datagram, is considered as an independent entity. Each packet contains the information about the destination and switch uses this information to forward the packet to the correct destination.
The packets are reassembled at the receiving end in correct order.
In Datagram Packet Switching technique, the path is not fixed.
Intermediate nodes take the routing decisions to forward the packets.
Datagram Packet Switching is also known as connectionless switching.
Virtual Circuit Switching
Virtual Circuit Switching is also known as connection-oriented switching.
In the case of Virtual circuit switching, a preplanned route is established before the messages are sent.
Call request and call accept packets are used to establish the connection between sender and receiver.
In this case, the path is fixed for the duration of a logical connection.
Let's understand the concept of virtual circuit switching through a diagram:
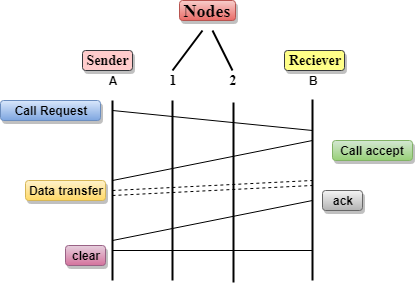
In the above diagram, A and B are the sender and receiver respectively. 1 and 2 are the nodes.
Call request and call accept packets are used to establish a connection between the sender and receiver.
When a route is established, data will be transferred.
After transmission of data, an acknowledgment signal is sent by the receiver that the message has been received.
If the user wants to terminate the connection, a clear signal is sent for the termination.
Differences b/w Datagram approach and Virtual Circuit approach
Datagram approach
Virtual Circuit approach
Node takes routing decisions to forward the packets.
Node does not take any routing decision.
Congestion cannot occur as all the packets travel in different directions.
Congestion can occur when the node is busy, and it does not allow other packets to pass through.
It is more flexible as all the packets are treated as an independent entity.
It is not very flexible.
Advantages Of Packet Switching:
Cost-effective: In packet switching technique, switching devices do not require massive secondary storage to store the packets, so cost is minimized to some extent. Therefore, we can say that the packet switching technique is a cost-effective technique.
Reliable: If any node is busy, then the packets can be rerouted. This ensures that the Packet Switching technique provides reliable communication.
Efficient: Packet Switching is an efficient technique. It does not require any established path prior to the transmission, and many users can use the same communication channel simultaneously, hence makes use of available bandwidth very efficiently.
Disadvantages Of Packet Switching:
Packet Switching technique cannot be implemented in those applications that require low delay and high-quality services.
The protocols used in a packet switching technique are very complex and requires high implementation cost.
If the network is overloaded or corrupted, then it requires retransmission of lost packets. It can also lead to the loss of critical information if errors are nor recovered.
Q6) What is IP address and explain IPv4 in detail and its drawbacks?
A6) An IP stands for internet protocol. An IP address is assigned to each device connected to a network. Each device uses an IP address for communication. It also behaves as an identifier as this address is used to identify the device on a network. It defines the technical format of the packets. Mainly, both the networks, i.e., IP and TCP, are combined together, so together, they are referred to as a TCP/IP. It creates a virtual connection between the source and the destination.
We can also define an IP address as a numeric address assigned to each device on a network. An IP address is assigned to each device so that the device on a network can be identified uniquely. To facilitate the routing of packets, TCP/IP protocol uses a 32-bit logical address known as IPv4(Internet Protocol version 4).
An IP address consists of two parts, i.e., the first one is a network address, and the other one is a host address.
There are two types of IP addresses:
IPv4
IPv6
What is IPv4?
IPv4 is a version 4 of IP. It is a current version and the most commonly used IP address. It is a 32-bit address written in four numbers separated by 'dot', i.e., periods. This address is unique for each device.
For example, 66.94.29.13
The above example represents the IP address in which each group of numbers separated by periods is called an Octet. Each number in an octet is in the range from 0-255. This address can produce 4,294,967,296 possible unique addresses.
In today's computer network world, computers do not understand the IP addresses in the standard numeric format as the computers understand the numbers in binary form only. The binary number can be either 1 or 0. The IPv4 consists of four sets, and these sets represent the octet. The bits in each octet represent a number.
Each bit in an octet can be either 1 or 0. If the bit the 1, then the number it represents will count, and if the bit is 0, then the number it represents does not count.
Representation of 8 Bit Octet

The above representation shows the structure of 8- bit octet.
Now, we will see how to obtain the binary representation of the above IP address, i.e., 66.94.29.13
Step 1: First, we find the binary number of 66.
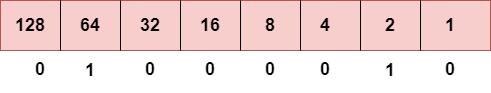
To obtain 66, we put 1 under 64 and 2 as the sum of 64 and 2 is equal to 66 (64+2=66), and the remaining bits will be zero, as shown above. Therefore, the binary bit version of 66 is 01000010.
Step 2: Now, we calculate the binary number of 94.
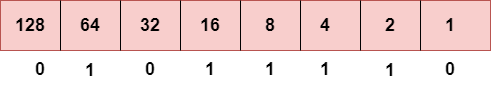
To obtain 94, we put 1 under 64, 16, 8, 4, and 2 as the sum of these numbers is equal to 94, and the remaining bits will be zero. Therefore, the binary bit version of 94 is 01011110.
Step 3: The next number is 29.
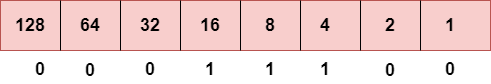
To obtain 29, we put 1 under 16, 8, 4, and 1 as the sum of these numbers is equal to 29, and the remaining bits will be zero. Therefore, the binary bit version of 29 is 00011101.
Step 4: The last number is 13.
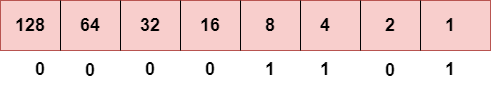
To obtain 13, we put 1 under 8, 4, and 1 as the sum of these numbers is equal to 13, and the remaining bits will be zero. Therefore, the binary bit version of 13 is 00001101.
Drawback of IPv4
Currently, the population of the world is 7.6 billion. Every user is having more than one device connected with the internet, and private companies also rely on the internet. As we know that IPv4 produces 4 billion addresses, which are not enough for each device connected to the internet on a planet. Although the various techniques were invented, such as variable- length mask, network address translation, port address translation, classes, inter-domain translation, to conserve the bandwidth of IP address and slow down the depletion of an IP address. In these techniques, public IP is converted into a private IP due to which the user having public IP can also use the internet. But still, this was not so efficient, so it gave rise to the development of the next generation of IP addresses, i.e., IPv6.
Q7) What is IPv6?
A7) IPv4 produces 4 billion addresses, and the developers think that these addresses are enough, but they were wrong. IPv6 is the next generation of IP addresses. The main difference between IPv4 and IPv6 is the address size of IP addresses. The IPv4 is a 32-bit address, whereas IPv6 is a 128-bit hexadecimal address. IPv6 provides a large address space, and it contains a simple header as compared to IPv4.
It provides transition strategies that convert IPv4 into IPv6, and these strategies are as follows:
Dual stacking: It allows us to have both the versions, i.e., IPv4 and IPv6, on the same device.
Tunneling: In this approach, all the users have IPv6 communicates with an IPv4 network to reach IPv6.
Network Address Translation: The translation allows the communication between the hosts having a different version of IP.
This hexadecimal address contains both numbers and alphabets. Due to the usage of both the numbers and alphabets, IPv6 is capable of producing over 340 undecillion (3.4*1038) addresses.
IPv6 is a 128-bit hexadecimal address made up of 8 sets of 16 bits each, and these 8 sets are separated by a colon. In IPv6, each hexadecimal character represents 4 bits. So, we need to convert 4 bits to a hexadecimal number at a time
Address format
The address format of IPv4:
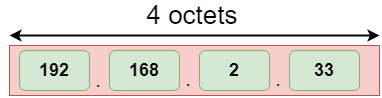
The address format of IPv6:
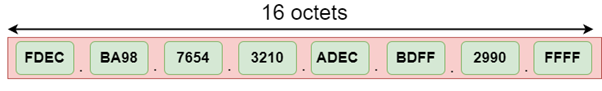
The above diagram shows the address format of IPv4 and IPv6. An IPv4 is a 32-bit decimal address. It contains 4 octets or fields separated by 'dot', and each field is 8-bit in size. The number that each field contains should be in the range of 0-255. Whereas an IPv6 is a 128-bit hexadecimal address. It contains 8 fields separated by a colon, and each field is 16-bit in size.
Q8) Differences between IPv4 and IPv6
A8)
| Ipv4 | Ipv6 |
Address length | IPv4 is a 32-bit address. | IPv6 is a 128-bit address. |
Fields | IPv4 is a numeric address that consists of 4 fields which are separated by dot (.). | IPv6 is an alphanumeric address that consists of 8 fields, which are separated by colon. |
Classes | IPv4 has 5 different classes of IP address that includes Class A, Class B, Class C, Class D, and Class E. | IPv6 does not contain classes of IP addresses. |
Number of IP address | IPv4 has a limited number of IP addresses. | IPv6 has a large number of IP addresses. |
VLSM | It supports VLSM (Virtual Length Subnet Mask). Here, VLSM means that Ipv4 converts IP addresses into a subnet of different sizes. | It does not support VLSM. |
Address configuration | It supports manual and DHCP configuration. | It supports manual, DHCP, auto-configuration, and renumbering. |
Address space | It generates 4 billion unique addresses | It generates 340 undecillion unique addresses. |
End-to-end connection integrity | In IPv4, end-to-end connection integrity is unachievable. | In the case of IPv6, end-to-end connection integrity is achievable. |
Security features | In IPv4, security depends on the application. This IP address is not developed in keeping the security feature in mind. | In IPv6, IPSEC is developed for security purposes. |
Address representation | In IPv4, the IP address is represented in decimal. | In IPv6, the representation of the IP address in hexadecimal. |
Fragmentation | Fragmentation is done by the senders and the forwarding routers. | Fragmentation is done by the senders only. |
Packet flow identification | It does not provide any mechanism for packet flow identification. | It uses flow label field in the header for the packet flow identification. |
Checksum field | The checksum field is available in IPv4. | The checksum field is not available in IPv6. |
Transmission scheme | IPv4 is broadcasting. | On the other hand, IPv6 is multicasting, which provides efficient network operations. |
Encryption and Authentication | It does not provide encryption and authentication. | It provides encryption and authentication. |
Number of octets | It consists of 4 octets. | It consists of 8 fields, and each field contains 2 octets. Therefore, the total number of octets in IPv6 is 16. |
Q9) What is Address Resolution Protocol (ARP) and what are its types?
A9) Address Resolution Protocol (ARP) is a communication protocol used to find the MAC (Media Access Control) address of a device from its IP address. This protocol is used when a device wants to communicate with another device on a Local Area Network or Ethernet.
Types of ARP
There are four types of Address Resolution Protocol, which is given below:
Proxy ARP
Gratuitous ARP
Reverse ARP (RARP)
Inverse ARP
Proxy ARP - Proxy ARP is a method through which a Layer 3 devices may respond to ARP requests for a target that is in a different network from the sender. The Proxy ARP configured router responds to the ARP and map the MAC address of the router with the target IP address and fool the sender that it is reached at its destination.
At the backend, the proxy router sends its packets to the appropriate destination because the packets contain the necessary information.
Example - If Host A wants to transmit data to Host B, which is on the different network, then Host A sends an ARP request message to receive a MAC address for Host B. The router responds to Host A with its own MAC address pretend itself as a destination. When the data is transmitted to the destination by Host A, it will send to the gateway so that it sends to Host B. This is known as proxy ARP.
Gratuitous ARP - Gratuitous ARP is an ARP request of the host that helps to identify the duplicate IP address. It is a broadcast request for the IP address of the router. If an ARP request is sent by a switch or router to get its IP address and no ARP responses are received, so all other nodes cannot use the IP address allocated to that switch or router. Yet if a router or switch sends an ARP request for its IP address and receives an ARP response, another node uses the IP address allocated to the switch or router.
There are some primary use cases of gratuitous ARP that are given below:
The gratuitous ARP is used to update the ARP table of other devices.
It also checks whether the host is using the original IP address or a duplicate one.
Reverse ARP (RARP) - It is a networking protocol used by the client system in a local area network (LAN) to request its IPv4 address from the ARP gateway router table. A table is created by the network administrator in the gateway-router that is used to find out the MAC address to the corresponding IP address.
When a new system is set up or any machine that has no memory to store the IP address, then the user has to find the IP address of the device. The device sends a RARP broadcast packet, including its own MAC address in the address field of both the sender and the receiver hardware. A host installed inside of the local network called the RARP-server is prepared to respond to such type of broadcast packet. The RARP server is then trying to locate a mapping table entry in the IP to MAC address. If any entry matches the item in the table, then the RARP server sends the response packet along with the IP address to the requesting computer.
Inverse ARP (InARP) - Inverse ARP is inverse of the ARP, and it is used to find the IP addresses of the nodes from the data link layer addresses. These are mainly used for the frame relays, and ATM networks, where Layer 2 virtual circuit addressing are often acquired from Layer 2 signaling. When using these virtual circuits, the relevant Layer 3 addresses are available.
ARP conversions Layer 3 addresses to Layer 2 addresses. However, its opposite address can be defined by InARP. The InARP has a similar packet format as ARP, but operational codes are different.
Q10) Explain Dynamic Host Configuration Protocol its components and benefits
A10) Dynamic Host Configuration Protocol (DHCP) is a network management protocol used to dynamically assign an IP address to nay device, or node, on a network so they can communicate using IP (Internet Protocol). DHCP automates and centrally manages these configurations. There is no need to manually assign IP addresses to new devices. Therefore, there is no requirement for any user configuration to connect to a DHCP based network.
DHCP can be implemented on local networks as well as large enterprise networks. DHCP is the default protocol used by the most routers and networking equipment. DHCP is also called RFC (Request for comments) 2131.
DHCP does the following:
DHCP manages the provision of all the nodes or devices added or dropped from the network.
DHCP maintains the unique IP address of the host using a DHCP server.
It sends a request to the DHCP server whenever a client/node/device, which is configured to work with DHCP, connects to a network. The server acknowledges by providing an IP address to the client/node/device.
DHCP is also used to configure the proper subnet mask, default gateway and DNS server information on the node or device.
There are many versions of DCHP are available for use in IPV4 (Internet Protocol Version 4) and IPV6 (Internet Protocol Version 6).
How DHCP works
DHCP runs at the application layer of the TCP/IP protocol stack to dynamically assign IP addresses to DHCP clients/nodes and to allocate TCP/IP configuration information to the DHCP clients. Information includes subnet mask information, default gateway, IP addresses and domain name system addresses.
DHCP is based on client-server protocol in which servers manage a pool of unique IP addresses, as well as information about client configuration parameters, and assign addresses out of those address pools.
The DHCP lease process works as follows:
First of all, a client (network device) must be connected to the internet.
DHCP clients request an IP address. Typically, client broadcasts a query for this information.
DHCP server responds to the client request by providing IP server address and other configuration information. This configuration information also includes time period, called a lease, for which the allocation is valid.
When refreshing an assignment, a DHCP clients request the same parameters, but the DHCP server may assign a new IP address. This is based on the policies set by the administrator.
Components of DHCP
When working with DHCP, it is important to understand all of the components. Following are the list of components:
DHCP Server: DHCP server is a networked device running the DCHP service that holds IP addresses and related configuration information. This is typically a server or a router but could be anything that acts as a host, such as an SD-WAN appliance.
DHCP client: DHCP client is the endpoint that receives configuration information from a DHCP server. This can be any device like computer, laptop, IoT endpoint or anything else that requires connectivity to the network. Most of the devices are configured to receive DHCP information by default.
IP address pool: IP address pool is the range of addresses that are available to DHCP clients. IP addresses are typically handed out sequentially from lowest to the highest.
Subnet: Subnet is the partitioned segments of the IP networks. Subnet is used to keep networks manageable.
Lease: Lease is the length of time for which a DHCP client holds the IP address information. When a lease expires, the client has to renew it.
DHCP relay: A host or router that listens for client messages being broadcast on that network and then forwards them to a configured server. The server then sends responses back to the relay agent that passes them along to the client. DHCP relay can be used to centralize DHCP servers instead of having a server on each subnet.
Benefits of DHCP
There are following benefits of DHCP:
Centralized administration of IP configuration: DHCP IP configuration information can be stored in a single location and enables that administrator to centrally manage all IP address configuration information.
Dynamic host configuration: DHCP automates the host configuration process and eliminates the need to manually configure individual host. When TCP/IP (Transmission control protocol/Internet protocol) is first deployed or when IP infrastructure changes are required.
Seamless IP host configuration: The use of DHCP ensures that DHCP clients get accurate and timely IP configuration IP configuration parameter such as IP address, subnet mask, default gateway, IP address of DND server and so on without user intervention.
Flexibility and scalability: Using DHCP gives the administrator increased flexibility, allowing the administrator to move easily change IP configuration when the infrastructure changes.