Unit – VI
Internet & its uses
Q.1) What is the internet?
A1: The Internet is a system design that allows diverse computer networks throughout the world to communicate, revolutionizing communications and business. The Internet, sometimes known as a "network of networks," first appeared in the United States in the 1970s but did not become widely known until the early 1990s. By 2020, it is expected that 4.5 billion individuals, or more than half of the world's population, would have Internet connectivity.
The Internet has such a broad and powerful capability that it may be used for nearly any information-based purpose, and it is accessible to anybody who connects to one of its constituent networks. It facilitates human contact through social media, electronic mail (e-mail), "chat rooms," newsgroups, and audio and video transmission, as well as allowing people to collaborate remotely. Many programs, like the World Wide Web, can use it to access digital information. The Internet has proved to be a spawning ground for a large and growing number of “e-businesses” (including subsidiaries of traditional “brick-and-mortar” companies) that carry out most of their sales and services over the Internet. (See electronic commerce.)
Q.2) Write the history of the internet?
A2: It is an interconnected computer network system that spans the globe. It makes use of the TCP/IP protocol, which is widely used on the internet. A unique IP address is assigned to every machine on the Internet. An IP Address (for example, 110.22.33.114) is a series of integers that identify the location of a computer.
A DNS (Domain Name Server) computer is used to give an IP Address a name so that a user can find a computer by name.
ARPANET was expanded to connect the Department of Defense with US colleges conducting defense-related research. It included most of the country's major universities. When University College London (UK) and Royal Radar Network (Norway) joined to the ARPANET and formed a network of networks, the concept of networking received a boost.
Stanford University's Vinton Cerf, Yogen Dalal, and Carl Sunshine invented the name "internet" to characterize this network of networks. They also collaborated on protocols to make information sharing via the Internet easier. The Transmission Control Protocol (TCP) is still the networking's backbone.
In the 1960s, the Internet was created as a means for government researchers to communicate information. In the 1960s, computers were enormous and stationary, and in order to access information stored on them, one had to either travel to the computer's location or have magnetic computer tapes transported through the mail system.
The escalation of the Cold War was another factor in the development of the Internet. The launch of the Sputnik satellite by the Soviet Union prompted the United States Defense Department to examine how information may be distributed even after a nuclear attack. This eventually led to the creation of the ARPANET (Advanced Research Projects Agency Network), which eventually evolved into the Internet we know today. ARPANET was a huge success, but it was only open to a few academic and research institutions with Defense Department contracts. As a result, new networks were formed to facilitate information sharing.
The Internet celebrates its formal birthday on January 1, 1983. Prior to this, there was no standard means for computer networks to communicate with one another. Transfer Control Protocol/Internetwork Protocol (TCP/IP) was created as a new communication protocol.
This allowed various types of computers on various networks to "speak" to one another. On January 1, 1983, ARPANET and the Defense Data Network switched to the TCP/IP standard, resulting in the birth of the Internet. A universal language could now connect all networks.
Q.3) What do you mean by web browsing software?
A3: A web browser (sometimes known as a browser) is software that allows you to access the World Wide Web. The web browser receives the necessary content from the website's web server and then displays the page on the user's device when a user follows the URL of a web page from a certain website.
A web browser is not the same as a search engine, despite the fact that the two are sometimes confused. A search engine is a web page that contains links to other online pages. A user must, however, have a web browser installed in order to connect to a website's server and view its web pages.
Web browsers are used on PCs, laptops, tablets, and smartphones, among other devices. A browser was used by 4.9 billion people in 2020, according to estimates. With a 64 percent global market share across all devices, Google Chrome is the most popular browser, followed by Safari with 19 percent.
A web browser is a piece of software that allows you to explore the Internet and view webpages. Even if you didn't realize it, you're reading this page using a web browser right now! There are numerous online browsers available,
Google Chrome
Internet Explorer
Safari
Microsoft Edge, and
Mozilla Firefox are among the most popular.
Internet explorer ( )
)
Microsoft's Internet Explorer (IE) is a software product. This is the most widely used web browser on the planet. This was debuted in 1995 in conjunction with the release of Windows 95, and it surpassed Netscape in popularity in 1998.
Google chrome ( )
)
Google created this web browser, and the beta version was published on September 2, 2008 for Microsoft Windows. Chrome is now one of the most popular web browsers, with a global market share of more than 50%.
Mozilla Firefox ( )
)
Mozilla has created a new browser called Firefox. It was first introduced in 2004 and has since evolved to become the Internet's second most used browser.
Safari ( )
)
Safari is an Apple Inc. Web browser that comes standard with Mac OS X. It was originally made available to the public as a public beta in January 2003. Safari offers excellent compatibility for modern technologies like as XHTML and CSS2.
Opera ( )
)
Opera is a full-featured browser that is smaller and faster than most other browsers. With a keyboard interface, numerous windows, zoom functions, and more, it's quick and easy to use. There are Java and non-Java versions available. Ideal for novices to the Internet, schoolchildren, the handicapped, and as a CD-ROM and kiosk front-end.
Q.4) What is surfing and chatting on the internet?
A4: Surfing the internet
When we talk about surfing, we often picture ourselves on a beach, getting our surfboards ready to swim out and ride the waves. We don't give much thought to the fact that we surf on a daily basis.
Yes, we're talking about surfing the web. It's something we do all the time, and it's a lot of fun. We go “surfing” the Web in search of information from various sources.
It's like riding the data and information waves. After one wave has passed, another arrives, and we're back on the board. When surfing the Internet, however, we use different devices.
It's all about getting around. We must navigate something as we work our way through the steps to a decent recipe for a beautiful meal.
The term "internet surfing" refers to the use of hyperlinks to navigate from one page to the next on the World Wide Web. In a nutshell, it's what we refer to as internet browsing.
There are currently an infinite number of live websites, and the number of web pages continues to rise every day. Browsing allows us to quickly locate what we're looking for. Other factors, though, make using the internet more convenient.
Chatting on internet
Chatting on the Internet entails conversing with other people who are online at the same time as you. Typically, "talking" entails the exchange of typed-in messages, which necessitates the usage of a single site as the message repository (or "chat site") and a group of users who can participate from anywhere on the Internet.
Chatting is an online communication method that allows senders and receivers to send and receive text messages in real time. In order for other chat participants to respond quickly, chat messages are usually short. As a result of its resemblance to a spoken discussion, this technology is an appealing target for cybercriminals looking to hijack accounts and steal data.
Risk from chatting
Nowadays, the majority of chatting platforms and instant messaging websites are hotbeds of fraud, with the risks posed by other users being as follows:
Viruses - Email attachments, phishing, and instant messaging can all be used to attack chat. A user machine or a network can be hacked as a result of this.
Malicious software - Attackers can utilize chat rooms to trick legitimate users into visiting a bogus website and stealing their credentials.
Hacking that comes from Hacked Chat Servers - This hacking can occur when the game's server is compromised due to a vulnerability, putting all users connected to the talking server in jeopardy.
Q.5) Describe email?
A5: Electronic Mail (e-mail) is one of most widely used services on the Internet. This service allows an Internet user to send a message in formatted manner (mail) to the other Internet user in any part of the world. Messages in mail not only contain text, but it also contains images, audio and videos data. The person who is sending mail is called the sender and the person who receives mail is called the recipient. It is just like postal mail service.
Email messages are sent via email servers, which use a variety of protocols from the TCP/IP suite. For example, SMTP stands for simple mail transfer protocol and is used to send and receive messages, whereas IMAP and POP are used to retrieve messages from a mail server. To access your email account, all you need is a valid email address, a password, and the mail servers that will be used to send and receive messages.
Components of E-Mail System
The basic components of an email system are: User Agent (UA), Message Transfer Agent (MTA), Mail Box, and Spool file.
- User Agent (UA) :
The UA is normally a program which is used to send and receive mail. Sometimes, it is called a mail reader. It accepts a variety of commands for composing, receiving and replying to messages as well as for manipulation of the mailboxes.
2. Message Transfer Agent (MTA) :
MTA is actually responsible for transfer of mail from one system to another. To send mail, a system must have a client MTA and a system MTA. It transfers mail to the mailboxes of recipients if they are connected in the same machine. It delivers mail to the peer MTA if the destination mailbox is in another machine.
3. Mailbox :
It is a file on a local hard drive to collect mails. Delivered mails are present in this file. The user can read it and delete it according to his/her requirement. To use the e-mail system each user must have a mailbox. Access to mailboxes is only to the owner of the mailbox.
4. Spool file :
This file contains mails that are to be sent. User agent appends outgoing mails in this file using SMTP. MTA extracts pending mail from a spool file for their delivery. E-mail allows one name, an alias, to represent several different email addresses. It is known as a mailing list. Whenever a user has to send a message, the system checks the recipient's name against the alias database. If a mailing list is present for a defined alias, separate messages, one for each entry in the list, must be prepared and handed to MTA. If for a defined alias, there is no such mailing list present, the name itself becomes the naming address and a single message is delivered to the mail transfer entity.
Q.6) Write the concept of using emails?
A6: Email can be used for a variety of purposes: it can be used to communicate both within and outside of an organization, as well as between two persons or a big group of people. The majority of people gain from email communication with coworkers, friends, individuals, or small groups. It allows you to transmit and receive photographs, documents, links, and other things with people all over the world. Additionally, it provides users with the ability to communicate on their own time.
Another advantage of using email is that it can be used to remind participants of approaching due dates and time-sensitive activities, as well as send professional follow-up emails following appointments, if you use it to communicate between two people or small groups. Users can also utilize the email to swiftly remind everyone about future events or to announce a time change to the group. It can also be used by businesses or organizations to communicate information to big groups of employees or customers. Email is mostly used for newsletters, in which subscribers to a mailing list are delivered direct email marketing campaigns and promoted content from a brand.
Email can also be used to convert leads into paying customers or to convert a pending sale into a completed purchase. For example, a business might establish an email that is used to automatically send emails to online consumers who have items in their shopping cart. This email might remind customers that they have items in their shopping basket and encourage them to buy them before they run out of stock. Customers are often asked to leave evaluations after making a purchase via emails. They can conduct a survey by incorporating a question about service quality.
Tips for using emails
- Use different email accounts for different purposes - It's a good idea to have different email addresses for different purposes. You might have one for business and one for social activities, for example. This means you can read your personal email without having to think about or worry about business in the evening. It might spoil your weekend or evening if you receive an urgent message from your boss. You want to be able to get away from work at the end of the day. Allowing email to make you a slave to work is not a good idea. Some people believe that checking two different email accounts is inconvenient. However, the benefits definitely surpass the minor discomfort.
2. Don’t say anything you wouldn’t say in person - This piece of advice has undoubtedly been provided before. However, we should always be reminded of the necessity of being polite and avoiding excessive rudeness. We'll come to regret it afterwards. Because email is impersonal, it is simpler to use harsh language. We must exercise extreme caution.
3. Email is not always the best Form of contact - When you have a serious problem or are angry with someone, emailing isn't always the greatest option. Instead of sending an email, speak with the person directly if required.
4. Be careful about replying to all - If you're new to email, be sure you understand the distinction between answering to one person and replying to everyone on the original message. To put it another way, you'll send a lot of emails that you don't want everyone to see. It might be terribly humiliating to send a personal message that is visible to the entire world - but it does happen. If you have new employees, make sure they understand the difference. It will prevent a slew of potential issues.
5. Use a good title - The subject line of an email is often overlooked. If the topic shifts, don't revert to an old "re:irrelevant title." A strong headline increases the likelihood that people will read your email instead of saving it for later. A bad title may even get deleted as spam.
Q.7) Explain the network?
A7: A computer network is a collection of computers linked together by cables, optical fibers, or optical connections so that different devices can communicate with one another. The purpose of a computer network is to allow different devices to share resources. There are many different types of networks in computer network technology, ranging from simple to complicated.
Application of the network
The following are some examples of network applications in various fields.
- Financial services
- Marketing and sales
- Manufacturing
- Information services
- Cellular telephone
- Cable television
- EDI
- E-mail etc.
- Teleconferencing
- CAD, CAM etc.
Goals
The following are the network’s key objectives.
● Resource sharing: A computer network’s primary goal is to accomplish this. It means that any computer on the network will share all of its programs, peripherals, and data with all other computers on the network, regardless of their physical locations. As a result, users at a great distance will share resources or view data on a device in the same way that local users do.
Load sharing is another type of resource sharing. That is, if necessary, a job can be done on several computers in a network by portioning it, which reduces time and load on each computer.
● Cost reduction: A second aim of networking is to save money. Sharing resources automatically lowers costs, allowing money to be saved.
● High reliability: Another aim is to ensure high reliability by providing many supply sources. For example, all files could be replicated on two or three computers, so that if one of them goes down, the others will still work.
● Improve performance: Another aim that is closely related is to improve the system’s efficiency. As the workload on a machine increase, its output can be enhanced by adding one or more processors. For example, instead of replacing the device with a larger one that is more expansive, it is easier to add more processors to it at a lower cost and with less inconvenience to the consumer.
● Communication medium: Computer networks are an effective means of communication. A file that has been updated/modified on a network is instantly visible to all users on the network.
Q.8) What is LAN?
A8: A Local Area Network (LAN) is a set of computers and peripheral devices linked in a small area, such as a classroom, laboratory, home, or office building. It's a popular network for sharing resources such as files, printers, games, and other software. Connecting computers and a printer in someone's home or office is the most basic form of LAN network. LAN will be used as one form of transmission medium in general.
It's a network of less than 5000 interconnected devices spread over several buildings.
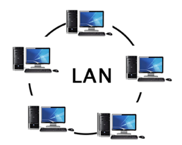
Fig 1: LAN
Advantages of LAN
The following are some of the advantages and disadvantages of using a LAN:
● Local area networks can share computer resources such as hard disks, DVD-ROMs, and printers. This lowers the cost of hardware purchases greatly.
● Instead of acquiring licensed software for each client in the network, you can utilize the same software across the network.
● All network users' data can be saved on the server computer's single hard disk.
● Data and messages can be easily transferred across networked computers.
● It will be simple to handle data in a single location, making data more secure.
● The ability to share a single internet connection among all LAN users is provided by a local area network.
Disadvantages of LAN
The following are the major disadvantages and downsides of LAN:
● Because of shared computer resources, LANs will save money, but the initial cost of setting up a LAN is fairly significant.
● Because the LAN administrator has access to every LAN user's personal data file, it does not provide adequate privacy.
● Unauthorized users can gain access to an organization's essential data if the LAN administrator fails to secure the centralized data repository.
● Because there are issues with software setup and hardware failures, a constant LAN administration is required.
Q.9) Define MAN?
A9: A Metropolitan Area Network, or MAN, is a computer network that spans a city, a college campus, or a small area. This network is far larger than a LAN, which is usually restricted to a single building or location. This form of network can cover a range of distances from a few miles to tens of miles, depending on the configuration.
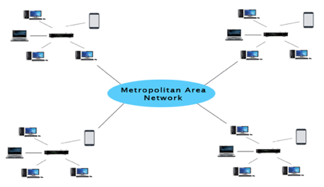
Fig 2: MAN
Advantages of MAN
The following are some of the advantages and disadvantages of adopting the MAN system:
● It provides high-speed communication over high-speed carriers such as fiber optic cables.
● It offers good support for a large network and increased WAN connectivity.
● The MAN network's dual bus allows data to be transmitted in both directions at the same time.
● A MAN network usually covers a portion of a city or the entire city.
Disadvantages of MAN
The following are some disadvantages and disadvantages of using the MAN network:
● To construct a MAN connection from one location to another, you'll need more cable.
● It's difficult to keep a MAN network secure from hackers.
Q.10) Write about WAN?
A10: Another significant computer network that spans a vast geographical area is the WAN (Wide Area Network). A WAN network system may be a LAN link that uses telephone lines and radio waves to connect to other LANs. It is usually restricted to a single company or organization.
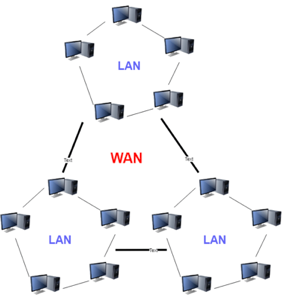
Fig 3: WAN
Advantages of WAN
The following are some of the advantages and disadvantages of using WAN:
● The Wide Area Network (WAN) allows you to cover a broader geographical area. As a result, corporate offices located at a greater distance can connect effortlessly.
● Mobile phones, laptops, tablets, desktops, game consoles, and other electronic gadgets are included.
● The radio transmitters and receivers embedded into client devices are used to establish WLAN connections.
Disadvantages of WAN
The following are some disadvantages and disadvantages of using WAN:
● The initial investment setup cost is really significant.
● The WAN network is difficult to maintain. You'll need technicians and network administrators who are well-versed in their fields.
● Because of the vast coverage and use of many technologies, there are more faults and issues.
● Because many wired and wireless technologies are involved, it takes longer to fix issues.
● When compared to other forms of networks, it provides less security.
Q.11) Write briefly about node and host?
A11: Node
Within a data transmission network, a node is a point of intersection/connection. These gadgets are all regarded nodes in an environment where all devices are connected to the network. The sort of network to which each node refers determines its individual definition.
Each home device capable of transmitting or receiving information over the network, for example, comprises a node inside the physical network of a smart home domestics system. A patch panel, for example, would not be regarded a node because it is a passive distribution point.
Information is created, received, and communicated by nodes, which then stores or relays it to other nodes. In a computer network, for example, a scanner creates images and delivers them to a computer, whereas a router organizes data received from the internet and distributes it to the network's different devices.
The term "node" has multiple meanings, but in the broadest sense, nodes are the key hubs via which internet traffic is normally directed. Because these same internet nodes are also referred to as internet hubs, this usage is a little confusing.
The adoption of packet-switching theory and the concept of dispersed networks popularized the concept of nodes. Nodes in this context were gateways that could accept, store, and transfer data across various routes in a dispersed network. Each node was given an equal status inside the network, ensuring that the loss of any one node would not have a substantial impact on the overall network.
A node, on the other hand, is merely one of the devices that performs a certain job in an office or personal network. As a result, losing that node frequently means losing functionality, such as the inability to print. Cables (wired network) or other wireless technologies such as communication satellites, terrestrial microwave, Bluetooth, or Wi-Fi can be used to connect the network's nodes.
Host
A host is a computer that is connected to the internet. A client, server, or any other form of computer can be used. Each host has a unique identifier known as a hostname that other computers can use to connect to it.
A computer's hostname can be a domain name, an IP address, or simply a unique text string, depending on the network protocol. A computer on a local network, for example, would have the hostname Tech-Terms. Local, whereas an Internet hostname might be techterms.com. The hostname "localhost" allows a host to access its own data across a network protocol.
An IP host is a computer that participates in networks that use the Internet protocol suite. Internet hosts are specific computers that participate in the Internet. The network interfaces of Internet hosts and other IP hosts are assigned one or more IP addresses. The addresses are either manually configured by an administrator, or automatically at startup using the Dynamic Host Configuration Protocol (DHCP), or stateless address autoconfiguration methods.
Server or client systems are network hosts that engage in applications that use the client–server computing model. Network hosts may also function as nodes in peer-to-peer applications, in which all nodes share and consume resources in an equipotent manner.
Q.12) Explain these two topics: workstation and bandwidth?
A12: Workstation
A workstation is a high-performance computer system with advanced graphics capabilities, substantial storage space, and a powerful central processing unit that is primarily meant for a single user. A workstation is more competent than a personal computer (PC), but it lacks the sophistication of a server (which can manage a large network of peripheral PCs or workstations and handle immense data-processing and reporting tasks). Dumb terminals (i.e., those with no processing capacity) that were connected to mainframe computers were also referred to as workstations. Because of the larger random-access memory (RAM), drives, and drive capacity, a workstation has a higher multitasking capability. A workstation may also have faster graphics adapters and additional peripherals linked to it.
Workstations are often designed to handle extensive data manipulation and visualization. Image rendering and editing, computer-aided design (CAD), animations, and mathematical graphs are all examples. Workstations were the first to introduce collaboration tools, as well as innovative accessories and improvements. 3D mouse, multiple screens, and high-performance/capacity data storage devices are among them.
Workstation characteristics were eventually incorporated by mainstream PCs, resulting in the workstation market segment's demise. In addition, the price difference between lower-cost workstations and higher-cost PCs has narrowed. High-end PCs employed powerful processors such as the Intel Xeon, IBM Power, AMD Opteron, or Sun UltraSPARC - a powerhouse for computer-processing work. Low-end workstations used Intel Pentium 4 or AMD Athlon 64 CPUs, whereas low-end workstations used Intel Pentium 4 or AMD Athlon 64 CPUs.
High-end workstations can support high-resolution or three-dimensional graphic interfaces, sophisticated multitask applications, and enhanced abilities to communicate with other computers thanks to their raw processing power. Workstations are typically utilized for scientific and technical tasks that require a lot of computing. They've also found favor in a number of sophisticated financial and business applications. In addition, high-end workstations frequently service a network of connected "client" PCs that access and manipulate data stored on the workstation using resident tools and apps.
Bandwidth
It's defined as the amount of data that can be transferred in a given amount of time. It refers to the network/transmission medium's data carrying capability.
The maximum pace of data transport via a given path is known as bandwidth in computing. Network bandwidth, data bandwidth, and digital bandwidth are all examples of bandwidth.
This definition of bandwidth differs from that used in the fields of signal processing, wireless communications, modem data transmission, digital communications, and electronics [citation needed], where bandwidth refers to the frequency range between the lowest and highest attainable frequency while meeting a well-defined impairment level in signal processing. The exact bit rate that can be obtained is determined by both the signal bandwidth and the channel noise.
Bandwidth is a term used in computer networking to describe the quantity of data that can be moved between two sites in a given amount of time. Bandwidth is measured in bits, megabits, or gigabits per second and is shared across devices connected to the same network. This implies that activities such as streaming video material or downloading huge files can consume a lot of bandwidth and cause other devices on the network to slow down.
Q.13) Explain server?
A13: Servers are high-capacity computers that handle the network's resources. Users have access to network resources through the network operating system, which is normally installed on the server. File servers, database servers, print servers, and more types of servers exist.
A computer that serves data to other computers and users is known as a server. A computer, a hardware device, or a computer program loaded with data and information that can be sent to other computers are all examples of network components. A computer system that receives a request for a web content and provides the request information to the client is referred to as a "server."
A server in computing is a computer program or device that offers functionality to other programs or devices known as clients. The client–server model is the name for this architecture. Multiple processes or devices are used to perform a single overall computation. Servers can perform a variety of functions known as services.
These services involve data or resource sharing among numerous clients, as well as computation on behalf of a client. A single server can serve several clients, and a single client can use multiple servers. On the same device, a client process can execute. It can also connect to a server over the network and execute on a different device. Database servers, mail servers, print servers, file servers, web servers, application servers, and game servers are all examples of servers.
Types of servers
Application server - Web apps (computer programs that run inside a web browser) are hosted on these servers, allowing users on the network to run and utilize them without having to install a copy on their own machines. These servers do not have to be connected to the Internet. Clients are computers that have a web browser installed.
Catalog server - These servers keep a table of contents or index of information that can be found throughout a vast distributed network. Computers, users, files exchanged via file servers, and web apps can all be part of a distributed network. Directory servers and name servers are examples of catalog servers. Any computer application that needs to find something on the network is one of their clients. A Domain member trying to log in, an email client seeking for an email address, or a user looking for a file are all examples.
Communication server - These servers provide the environment required for one communication endpoint to locate and communicate with other endpoints. Depending on the network's openness and security standards, these servers may or may not include a directory of communication endpoints and a presence detection service. Clients are communication endpoints for them.
Database server - These servers keep track of and share any type of database across the internet. A database is a collection of data that is organized and has predetermined features and may be displayed in a table. Spreadsheets, accounting software, asset management software, or nearly any computer program that consumes well-organized data, especially in huge amounts, are clients of these servers.
File server - Over a network, shares files and folders, storage capacity to hold files and folders, or both. Clients are designed to be networked computers, yet local programs can also be clients.
Q.14) What is a client?
A14: A client is the device that receives requests and responds from the server. The client/server network is created when a server and its clients collaborate on a computer.
These are machines that access network resources by requesting or receiving information or services from servers.
Clients are important to both businesses and servers. There is a one-to-many link in both instances. A server can communicate with several customers in the same way that a business can. This is known as the client-server model in computer networking.
Any device that communicates with a server is referred to as a client. It could be a computer, a laptop, a smartphone, or any other network-enabled device. "Smart" gadgets, such as Wi-Fi-enabled thermostats, lighting, and appliances, are considered clients in a home network. Clients of the file server in an office network are systems that access files from network-attached storage. Client-to-client communication is possible on most networks, but data must pass through a central point, such as a router or switch.
On a broader scale, your device is the client, and the web server hosting the website is the server, anytime you browse a website. Your web browser is the client software, whereas the program that responds to requests on the web server (Apache, IIS, and so on) is the server software. When you check your email, you connect to a mail server in the same way. Your device is a mail server client, and the client software is your email program or webmail interface.
Q.15) Describe communication media?
A15: For transferring data from one computer terminal to the central computer or to multiple computer systems within a network, many media are used.
There are two types of communication media: print and electronic.
Analog - Analog transmissions include traditional radio, telephone, and television broadcasts.
Digital - Computer-mediated communication, computer networking, and telegraphy are all examples of digital communication.
The most commonly used data communication media include:
Physical transmission media used in communications include twisted-pair cable, coaxial cable, and fiber-optic cable. These cables typically are used within or underground between buildings. Ethernet and token ring LANs often use physical transmission media.
Guided media
The physical medium by which signals are transmitted is referred to as the transmission medium. Bounded media is another name for it.
Types of guided media:
Twisted-Pair Cable
One of the more commonly used transmission media for network cabling and telephone systems is twisted-pair cable. Each twisted-pair wire consists of two separate insulated copper wires that are twisted together. The wires are twisted together to reduce noise. Noise is an electric- cal disturbance that can degrade communications.
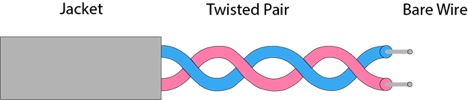
Fig 4: twisted pair cable
Types of twisted pair cable
- Unshielded twisted pair
- Shielded twisted pair
Coaxial Cable
Coaxial cable, often referred to as coax, consists of a single copper wire surrounded by at least three layers: (1) an insulating material, (2) a woven or braided metal, and (3) a plastic outer coating.
Cable television (CATV) network wiring often uses coaxial cable because it can be cabled over longer distances than twisted-pair cable. Most of today’s computer networks, however, do not use coaxial cable because other transmission media such as fiber-optic cable transmit signals at faster rates.
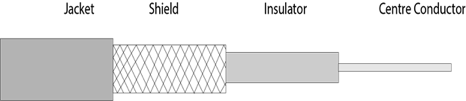
Fig 5: coaxial cable
Types of coaxial cable
- Baseband transmission
- Broadband transmission
Fiber-Optic Cable
The core of a fiber-optic cable consists of dozens or hundreds of thin strands of glass or plastic that use light to transmit signals. Each strand, called an optical fiber, is as thin as a human hair. Inside the fiber-optic cable, an insu- lating glass cladding and a protective coating surround each optical fiber.
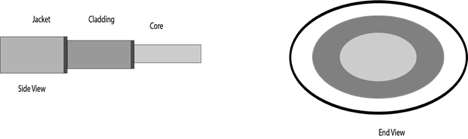
Fig 6: fiber optic cable
Fiber-optic cables have the following advantages over cables that use wire, such as twisted-pair and coaxial cables:
● Capability of carrying significantly more signals than wire cables
● Faster data transmission
● Less susceptible to noise (interference) from other devices such as a copy machine
● Better security for signals during transmission because they are less susceptible to noise
● Smaller size (much thinner and lighter weight)
Unguided media
The electromagnetic waves are transmitted without the use of any physical medium in an unguided transmission. Therefore, it is also known as wireless transmission.
Air is the medium through which electromagnetic energy can easily flow in unguided media.
Unguided transmission can be categorized into three types:
Radio waves: Radio waves are electromagnetic waves that travel through free space in all directions. Radio waves are omnidirectional, which means that the signals travel in all directions. Radio waves have a frequency range of 3 kHz to 1 kHz. The transmitting and receiving antennas are not compatible in the case of radio waves, so the wave transmitted by the sending antenna can be received by any receiving antenna.
Infrared: Infrared transmission is a wireless communication technology that works over short distances. Infrared waves with frequencies ranging from 300 GHz to 400 THz. It's used for short-range communication including data transfer between two mobile phones, TV remote control, and data transfer between a computer and a cell phone that's in the same room.
Q.16) Explain wireless network?
A16: Wireless networks are computer networks that are not connected by cables. Radio waves are commonly used to communicate between network nodes. They let devices to stay connected to the network while traveling inside its coverage area.
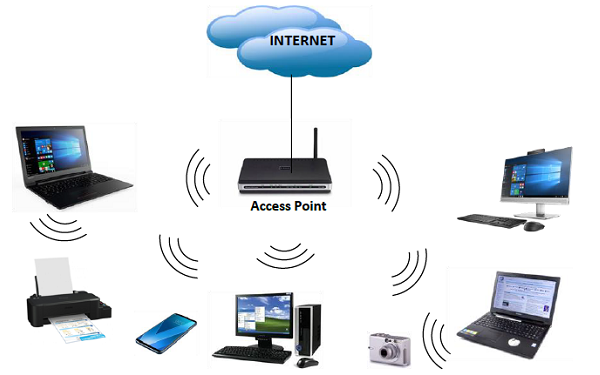
Fig 7: wireless network
Radio Frequency (RF) technology, a frequency related with radio wave transmission within the electromagnetic spectrum, is used to power wireless networks. When an RF current is sent into an antenna, it creates an electromagnetic field that can travel over space.
A wireless network's core is a mechanism known as an access point (AP). The fundamental function of an access point is to transmit a wireless signal that computers can detect and tune into. Because wireless networks are frequently linked to wired networks, access points frequently serve as a portal to the resources of the wired network, such as an Internet connection.
Example
● Mobile phone networks
● Wireless sensor networks
● Satellite communication networks
● Terrestrial microwave networks
Types
● Wireless LAN - Using wireless distribution techniques, connects two or more network devices.
WLAN is a form of network that uses a wireless distribution method to connect two or more computers. They have high-frequency radio waves as well as internet access points (APs).
They are convenient to use since they allow users to wander around the coverage area rather than being confined to a particular spot. Local Area Wireless Network is another name for them (LAWN).
● Wireless MAN - Connects two or more wireless LANs that are dispersed around a city.
The coverage range of MWAN is about the size of a city. It's smaller than WWAN, but it's bigger than WLAN. It is owned by a single entity, such as the government, an Internet Service Provider, or a group of people. Only authorized individuals or subscription devices have access to MWAN. *WiMAX is an example of a type of WMAN.
● Wireless WAN - Connects LANs, MANs, and personal networks in wide areas.
WWAN, commonly known as wireless broadband, is a technology that uses cell towers to transmit data. In contrast to WLAN, which has a range of only a few hundred feet, these towers transmit radio signals over thousands of miles. The Global System for Mobile Communications (GSM) and Code Division Multiple Access (CDMA), as well as the newer WiMAX, are the three key technologies.
These technologies are outside the scope of this essay, but you can find additional information about them here. It's worth noting that Wide Area Networks connect to multiple Local Area Networks rather than your individual machines.
Q.17) Write the advantages of wireless networks?
A17: Advantages
● Due to the lack of wires and cords, it provides clutter-free desks.
● Because the devices do not need to be connected to each other, it increases the mobility of network devices connected to the system.
● Because no connections are required, network devices can be accessed from any point within the network coverage or via a Wi-Fi hotspot.
● Wireless network installation and configuration is simpler.
● New devices can be quickly linked to the existing configuration because they do not require any wiring. Furthermore, because the cable capacity is not a constraint, the number of pieces of equipment that can be added or removed from the system might vary significantly. As a result, wireless networks are extremely scalable.
● Wireless networks necessitate the use of extremely few or no cables. As a result, the equipment and setup costs are reduced.