Unit - 1
Introduction
Q1) What is Parallel System of an operating system?
A1)
- Parallel Processing Systems are intended to accelerate the execution of programs by isolating the program into numerous pieces and processing those fragments simultaneously.
- Such systems are multiprocessor systems called as tightly coupled systems.
- Parallel systems manage the synchronous utilization of numerous computer resources that can incorporate a single computer with various processors, various computers associated by a network to frame a parallel processing cluster or a blend of both.
- Parallel systems are harder to program than computers with a single processor in light of the fact that the engineering of parallel computers fluctuates appropriately and the procedures of numerous CPUs must be composed and synchronized.
- A few models for interfacing processors and memory modules exist, and every topology requires an alternate programming model.
- The three models that are most regularly utilized in structuring parallel computers incorporate synchronous processors each with its very own memory, asynchronous processors each with its own memory and asynchronous processors with a typical, shared memory.
- Parallel operating systems are essentially worried about dealing with the resources of parallel machines.
- This task faces numerous difficulties: application software engineers request all the performance possible, numerous equipment configurations exist and change all around quickly, yet the operating system should progressively be good with the standard adaptations utilized in computers.
- Today, new applications emerge and request faster computers. Business applications are the most utilized on parallel computers.
- A computer that runs such an application; ought to have the option to process enormous amount of data in modern ways. These applications incorporate designs, virtual reality, and decision support, parallel databases, medical diagnosis, etc.
- We can say with almost certainly that business applications will characterize future parallel computers design however scientific applications will stay significant users of parallel processing innovation.
Q2) Explain Time Sharing System of an operating system.
A2)
- Time-sharing systems are not accessible in 1960s.
- Time-sharing or performing multiple tasks is a legitimate expansion of multiprogramming. That is processors time is shared among numerous users at the same time is called time-sharing.
- The primary contrast between Multi-programmed Batch Systems and Time-Sharing Systems is, in Multi-programmed batch systems its goal is expand processor use, while in Time-Sharing Systems its goal is minimize response time.
- Numerous jobs are executed by the CPU by switching between them, however the switches happen in such a less time, so that the user can gets a prompt response.
- For instance, in a transaction processing, processor execute every user program in a short burst or quantum of calculation.
- That is if n users are available, every user can get time quantum.
- At the point when the user presents the instruction, the response time is seconding all things considered.
- Operating system utilizes CPU scheduling and multiprogramming to give every user a little part of a time.
- Computer systems that were structured essentially as batch systems have been altered to time-sharing systems.
- For instance, IBM's OS/360.
Time-Sharing Operating System
- As the name itself recommends, in a time-sharing system or performing various tasks system, different jobs can be executed on a system simultaneously by sharing the CPU time among them.
- It is viewed as a logical expansion of multiprogramming on the grounds that the two does synchronous execution yet vary in their prime aims.
- The fundamental goal of time-sharing systems is to limit reaction time yet not boosting the processor use (which is the target of multiprogramming systems).
- The time-sharing systems were created to give an intuitive utilization of the computer system.
- A time-shared system utilizes CPU planning and multiprogramming to give every user a little segment of a period shared computer.
- It enables numerous users to share the computer resources all the while. As the system switches quickly from one user to the next, a brief timeframe opening is given to every user for their executions.
- The time-sharing operating system guarantees that every one of the assignments get the chance to get to the CPU individually and for a fixed little interval of time. This interval is known as the time quantum.
- E.g.: Unix Systems
Advantages of Time-Sharing OS:
- Each user gets an equivalent chance
- Less chances of duplication of programming
- CPU inert time can be diminished
Disadvantages of Time-Sharing OS:
- Unwavering quality issue
- One must need to deal with security and respectability of user programs and information.
- Information correspondence issue
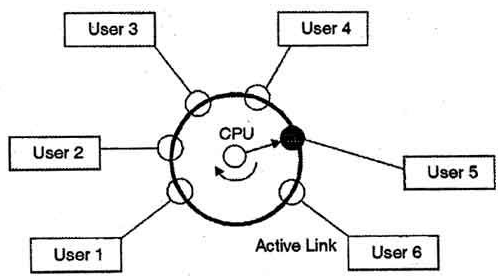
Fig 1. Time-Sharing Operating System
Q3) Explain Multi programmed Batch System of an operating system.
A3)
- This sort of OS is utilized to execute more than one job at the same time by a single processor.
- It builds CPU by sorting out jobs with the goal that the CPU consistently has one job to execute.
- The idea of multiprogramming is depicted as pursues:
- Every one of the jobs that enter the system are kept in the job pool (in a disk). The operating system stacks a lot of jobs from job pool into main memory and starts to execute.
- During execution, the job may need to wait for some task, for example, an I/O operation, to finish. In a multiprogramming system, the operating system basically changes to another activity and executes. At the point when that job needs to wait, the CPU is changed to another job, etc.
- At the point when the first job completes the process of waiting and it recovers the CPU.
- For whatever length of time that in any event one job needs to execute, the CPU is never idle.
- Multiprogramming operating systems utilize the component of job scheduling and CPU scheduling.
Q4) Explain the types of OS?
A4) Types of Operating system
● Batch Operating System
● Multitasking/Time Sharing OS
● Multiprocessing OS
● Real Time OS
● Distributed OS
● Network OS
● Mobile OS
Batch Operating System
Some computer processes are very lengthy and time-consuming. To speed the same process, a job with a similar type of needs are batched together and run as a group.
The user of a batch operating system never directly interacts with the computer. In this type of OS, every user prepares his or her job on an offline device like a punch card and submit it to the computer operator.
Multi-Tasking/Time-sharing Operating systems
Time-sharing operating system enables people located at a different terminal(shell) to use a single computer system at the same time. The processor time (CPU) which is shared among multiple users is termed as time sharing.
Real time OS
A real time operating system time interval to process and respond to inputs is very small. Examples: Military Software Systems, Space Software Systems.
Distributed Operating System
Distributed systems use many processors located in different machines to provide very fast computation to its users.
Network Operating System
Network Operating System runs on a server. It provides the capability to serve to manage data, user, groups, security, application, and other networking functions.
Mobile OS
Mobile operating systems are those OS which is especially that are designed to power smartphones, tablets, and wearables devices.
Some most famous mobile operating systems are Android and iOS, but others include BlackBerry, Web, and watchOS.
Q5) What are the services provided by OS?
A5)
An OS provides services to each the users and to the programs.
- It provides programs Associate in Nursing atmosphere to execute.
- It provides users the services to execute the programs during a convenient manner.
Following square measure many common services provided by Associate in Nursing OS Associate in Nursing
- Program execution
- I/O operations
- File System manipulation
- Communication
- Error Detection
- Resource Allocation
- Protection
Program execution
Operating systems handle several styles of activities from user programs to system programs like printer spooler, name servers, digital computer, etc. every of those activities is encapsulated as a method.
A method includes the entire execution context (code to execute, knowledge to govern, registers, OS resources in use). Following square measure, the foremost activities of Associate in Nursing OS with relevancy program management −
- Loads a program into memory.
- Executes the program.
- Handles program's execution.
- Provides a mechanism for method synchronization.
- Provides a mechanism for method communication.
- Provides a mechanism for impasse handling.
I/O Operation
An I/O scheme includes of I/O devices and their corresponding driver code. Drivers hide the peculiarities of specific hardware devices from the users.
- An OS manages the communication between user and device drivers.
- I/O operation suggests that scan or write operation with any file or any specific I/O device.
- Operating system provides the access to needed|the specified|the desired} I/O device once required.
File system manipulation
A file represents a group of connected data. Computers will store files on the disk (secondary storage), for long-run storage purpose. Samples of storage media embody mag tape, disk and storage device drives like CD, DVD. Every of those media has its own properties like speed, capacity, knowledge transfer rate and knowledge access strategies.
A classification system is often organized into directories for simple navigation and usage. These directories could contain files and alternative directions. Following square measure, the foremost activities of Associate in Nursing OS with relevancy file management −
- Program must scan a file or write a file.
- The OS offers the permission to the program for operation on file.
- Permission varies from read-only, read-write, denied so on.
- Operating System provides Associate in Nursing interface to the user to create/delete files.
- Operating System provides Associate in Nursing interface to the user to create/delete directories.
- Operating System provides Associate in Nursing interface to form the backup of classification system.
Communication
In case of distributed systems that square measure a group of processors that don't share memory, peripheral devices, or a clock, the OS manages communications between all the processes. Multiple processes communicate with each other through communication lines within the network.
The OS handles routing and association ways, and therefore the issues of competition and security. Following square measure the foremost activities of Associate in Nursing OS with relevancy
- Two processes usually need knowledge to be transferred between them
- Both the processes may be on one pc or on totally different computers, however square measure connected through a electronic network.
- Communication could also be enforced by 2 strategies, either by Shared Memory or by Message Passing.
Error handling
Errors will occur anytime and anyplace. a mistake could occur in computer hardware, in I/O devices or within the memory hardware. Following square measure, the foremost activities of Associate in Nursing OS with relevancy error handling −
- The OS perpetually checks for potential errors.
- The OS takes Associate in Nursing applicable action to make sure correct and consistent computing.
Resource Management
In case of multi-user or multi-tasking atmosphere, resources like main memory, computer hardware cycles and files storage square measure to be allotted to every user or job. Following square measure, the foremost activities of Associate in Nursing OS with relevancy resource management −
- The OS manages every kind of resources victimisation scheduler.
- Computer hardware planning algorithms square measure used for higher utilization of CPU.
Protection
Considering a ADPS having multiple users and multiprogramming of multiple processes, the assorted processes should be shielded from every other's activities.
Protection refers to a mechanism or the way to manage the access of programs, processes, or users to the resources outlined by a ADPS. Following square measure, the foremost activities of Associate in Nursing OS with relevancy
- The OS ensures that each one access to system resources is controlled.
- The OS ensures that external I/O devices square measure shielded from invalid access tries.
- The OS provides authentication options for every user by suggests that of passwords.
Q6) Explain operating system structure in detail.
A6)
The software package is split into numerous layers within the stratified software package and every of the layers have totally different functionalities. This sort of software package was created as associate degree improvement over the first monolithic systems.
Why Layering in operative System?
Layering provides a definite advantage in associate degree software package. All the layers are outlined severally and move with one another pro re nata. Also, it's easier to form, maintain and update the system if it's tired the shape of layers. Modification in one-layer specification doesn't have an effect on the remainder of the layers.
Each of the layers within the software package will solely move with the layers that square measure higher than and below it. Very cheap layer handles the hardware and therefore the topmost layer deals with the user applications.
Layers in stratified software package
There square measure six layers within the stratified software package. A diagram demonstrating these layers is as follows:
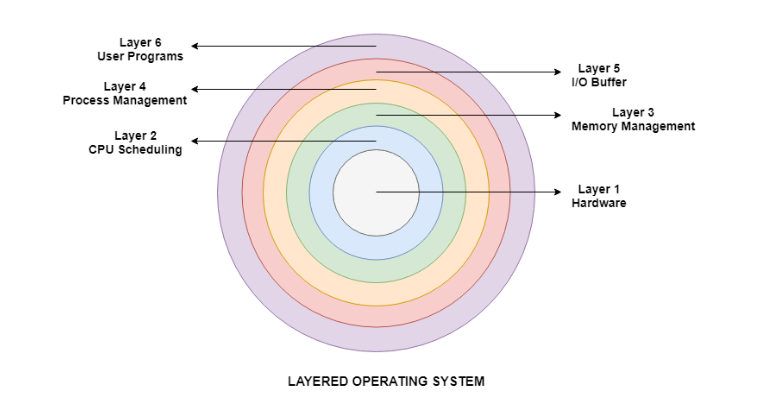
Fig 2 – Layered operating system
Details about the six layers are:
Hardware
This layer interacts with the system hardware and coordinates with all the peripheral devices used like printer, mouse, keyboard, scanner etc. The hardware layer is that the lowest layer within the stratified software package design.
CPU planning
This layer deals with planning the processes for the hardware. There square measure several planning queues that square measure wants to handle processes. Once the processes enter the system, they're place into the work queue. The processes that square measure able to execute within the main memory square measure unbroken within the prepared queue.
Memory Management
Memory management deals with memory and therefore the moving of processes from disk to primary memory for execution and back once more. This is often handled by the third layer of the software package.
Process Management
This layer is accountable for managing the processes i.e. distribution the method or to a process at a time. This is often referred to as method planning. The various algorithms used for method planning square measure FCFS (first come back 1st served), SJF (shortest job first), priority planning, round-robin planning etc.
I/O Buffer
I/O devices square measure important within the pc systems. They supply users with the means that of interacting with the system. This layer handles the buffers for the I/O devices and makes positive that they work properly.
User Programs
This is the best layer within the stratified software package. This layer deals with the various user programs associate degreed applications that run in an software package like word processors, games, browsers etc.
Monolithic
The entire software package works within the kernel house within the monolithic system. This will increase the dimensions of the kernel furthermore because the software package. This is often totally different than the microkernel system wherever the minimum computer code that's needed to properly implement associate software package is unbroken within the kernel.
A diagram that demonstrates the design of a monolithic system is as follows −−
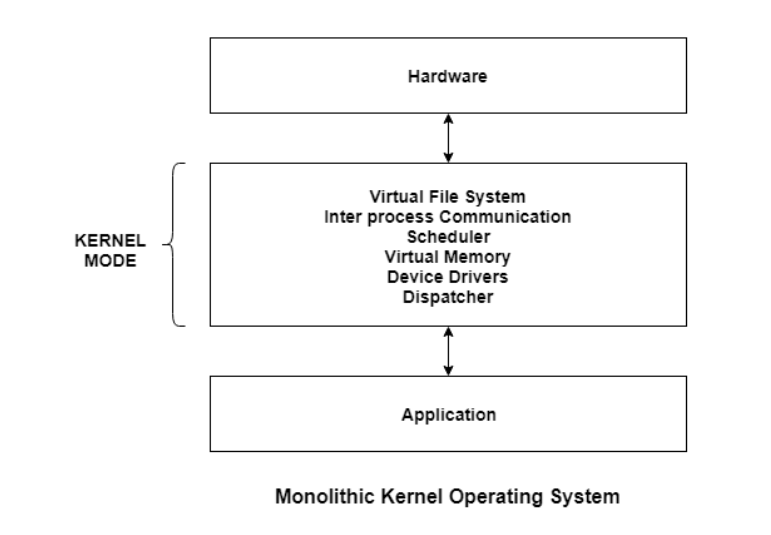
Fig 3 – Monolithic operating system
The kernel provides numerous services like memory management, file management, method programing etc. victimization perform calls. This makes the execution of the software package quite quick because the services square measure enforced beneath constant address house.
Differences between Microkernel and Monolithic Kernel
Some of the variations between microkernel and monolithic kernel square measure given as follows −
- The microkernel is far smaller in size as compared to the monolithic kernel.
- The microkernel is well protractible whereas this is often quite sophisticated for the monolithic kernel.
- The execution of the microkernel is slower as compared to the monolithic kernel.
- Much additional code is needed to jot down a microkernel than the monolithic kernel.
- Examples of Microkernel square measure QNX, Symbian, L4 UNIX operating system etc. Monolithic Kernel examples square measure UNIX operating system, BSD etc.
Advantages of Monolithic Kernel
Some of the benefits of monolithic kernel square measure square measure
- The execution of the monolithic kernel is kind of quick because the services like memory management, file management, method programming etc. are enforced beneath constant address house.
- A method runs utterly in an exceedingly single address house within the monolithic kernel.
- The monolithic kernel could be a static single computer file.
- Disadvantages of Monolithic Kernel
- Some of the disadvantages of monolithic kernel square measure square measure
- If any service fails within the monolithic kernel, it results in the failure of the whole system.
- To add any new service, the whole software package must be changed by the user.
Microkernel Operating Systems
Kernel is that the core a part of AN OS that manages system resources. It additionally acts sort of a bridge between application and hardware of the pc. It's one amongst the primary programs loaded on start-up (after the Bootloader).
Fig 4 – Kernel
Kernel mode and User mode of electronic equipment operation
The electronic equipment will execute bound instruction only it's within the kernel mode. These instruction ar referred to as privilege instruction. They permit implementation of special operation whose execution by the user program might interface with the functioning of OS or activity of another user program. As an example, instruction for managing memory protection.
- The OS puts the electronic equipment in kernel mode once it's corporal punishment within the kernel thus, that kernel will execute some special operation.
- The OS puts the electronic equipment in user mode once a user program is in execution thus, that user program cannot interface with the OS program.
- User-level instruction doesn't need special privilege. Example ar ADD,PUSH,etc.
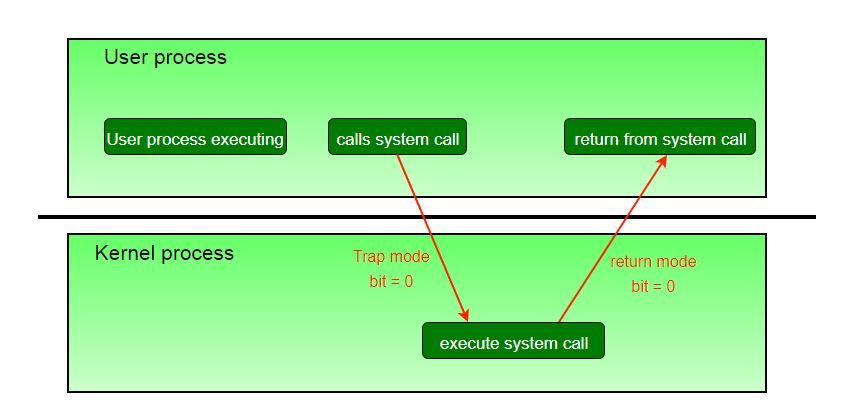
Fig 5- Process state
The conception of modes is extended on the far side 2, requiring over one mode bit CPUs that support virtualization use one amongst these additional bits to point once the virtual machine manager, VMM, is up to the mark of the system. The VMM has a lot of privileges than standard user programs, however not such a large amount of because the full kernel.
System calls are usually enforced within the sort of code interrupts, that causes the hardware’s interrupt handler to transfer management over to AN applicable interrupt handler, that is an element of the OS, switch the mode bit to kernel mode within the method. The interrupt handler checks specifically that interrupt was generated, checks extra parameters (usually more experienced registers) if applicable, so calls the acceptable kernel routine to handle the service requested by the call.
User programs’ tries to execute banned directions (privileged or non-existent directions), or to access prohibited memory areas, additionally generate code interrupts, that are cornered by the interrupt handler and management is transferred to the OS, that problems AN applicable error message, presumably dumps information to a log (core) file for later analysis, so terminates the violative program.
What is Microkernel?
Microkernel is one amongst the classification of the kernel. Being a kernel, it manages all system resources. However, during a microkernel, the user services and kernel services are enforced in numerous address house. The user services are unbroken in user address house, and kernel services are unbroken underneath kernel address house, therefore additionally reduces the dimensions of kernel and size of OS also.
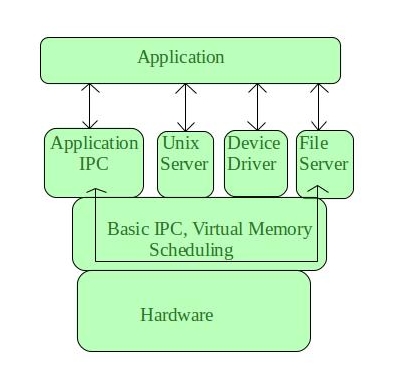
Fig 6 – Application
It provides token services of method and memory management. The communication between shopper program/application and services running in user address house is established through message passing, reducing the speed of execution microkernel. The OS remains unaffected as user services and kernel services are isolated thus if any user service fails it doesn't have an effect on kernel service. Therefore, it adds to at least one of the benefits during a microkernel. It's simply long i.e. if any new services are to be extra they're extra to user address house and therefore needs no modification in kernel house. It's additionally moveable, secure and reliable.
Microkernel design
Since kernel is that the core a part of the OS, thus it's meant for handling the foremost necessary services solely. Therefore, during this design solely, the foremost necessary services are within kernel and remainder of the OS services are gift within system computer program. Therefore, users are able to move with those not-so necessary services among the system application. And also, the microkernel is only to blame for the foremost necessary services of OS they're named as follows:
- Inter Process-Communication
- Memory Management
- CPU-Scheduling
Advantages of Microkernel
- The design of this kernel is little and isolated therefore it will perform higher.
- Expansion of the system is simpler, it's merely extra within the system application while not heavy the kernel.
Q7) Illustrate the Evolution of OS?
A7) The following is a timeline of an operating system's evolution:
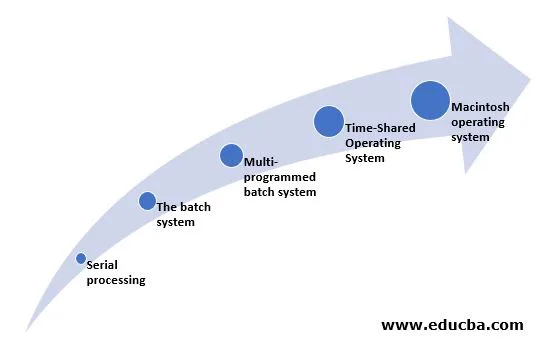
Fig 7: Evolution of OS
Serial Processing
By the 1940s and 1950s, programmers were embedded into hardware components without the use of an operating system. The scheduling and setup time are the issues here. By squandering computational time, the user logs in for machine time. When loading the compiler, saving the compiled programme, source programme, linking, and buffering, setup time is involved. If there is an intermediate error, the process is restarted.
The Batch System
It is used to improve computer utilization and application. On cards and tapes, jobs were scheduled and submitted. Then, using Job Control Language, they were successively executed on the monitors. The first computers employed in the batch operation method created a computer batch of jobs that didn't stop or pause. The software is written on punch cards and then transferred to the tape's processing unit. When the computer finishes one job, it immediately moves on to the next item on the tape. Professional operators are taught how to communicate with the machine where users drop off jobs and then return to pick up the results after the project is completed.
Despite the fact that it is inconvenient for the users, it is designed to keep the pricey computer as busy as possible by running a continuous stream of operations. The memory protection prevents the memory space that makes up the monitor from being changed, and the timer prevents the job from monopolizing the system. When the input and output devices are in use, the processor remains idle due to poor CPU utilization.
Multi-programmed Batch System
It's utilised when there are numerous jobs to run that need to be kept in main memory. The processor choose which application to run based on job scheduling.
Time-Shared Operating System
Substitute batch systems were developed using this method. Like an electric teletype, the user communicated directly with the computer via printing ports. Few users shared the computer instantly, and each job was completed in a fraction of a second before moving on to the next. The fast server may act on a large number of users' processes at the same time by creating iterations while they are receiving full attention. Multiple programmes use timesharing systems to apply to the computer system by sharing the system interactively.
Multiple communicative jobs are managed via multi-programming. The processor's time is divided among numerous users, and multiple users can access the system via terminals at the same time. Programs with the command-line user interface, in which the user has written responses to prompts or written instructions, required printing ports. As if it were a roll of paper, the interaction is scrolled down.
Printing terminals that displayed fixed-size characters were replaced with video terminals. Some are used to create shapes on the screen, but the majority are scrolled like a glass teletype. In the mid-1970s, personal computers became adaptable. The Altair 8800 was the first commercially viable personal computer, and it shocked the business world.
Macintosh Operating System
It was based on decades of research into graphical operating systems and applications for personal computers. The photo depicts a Sutherland pioneer programme sketchpad that was developed in 1960 employing many of the characteristics of today's graphical user interface, but the hardware components cost millions of dollars and took up a room.
After many research gaps, the Macintosh was commercially and fiscally viable thanks to a project on massive computers and hardware improvements. Many research laboratories are still working on research prototypes like sketchpads. It served as the foundation for anticipated products.
Q8) Describe the history of OS?
A8) History of OS
The operating system can be classified into four generations, as follows:
First Generation (1945-1955)
It marks the start of the development of electronic computing systems as a replacement for mechanical computers. Because of the flaws in mechanical computing devices, humans' calculation speed is limited, and they are prone to making mistakes. Because there is no operating system in this generation, the computer system is given instructions that must be carried out immediately.
Plug Boards are an example of a type of operating system and device.
Second Generation (1955-1965)
In the second generation, the batch processing system was implemented, which allows a job or task to be done in a series and then completed sequentially. The computer system in this generation does not have an operating system, although there are various operating system functionalities available, such as FMS and IBSYS.
Batch systems are an example of the type of operating system and devices employed.
Third Generation (1965-1980)
In the third generation, the operating system was designed to service numerous users at the same time. Interactive users can communicate with a computer via an online terminal, making the operating system multi-user and multiprogramming.
Multiprogramming is an example of a type of operating system and devices employed.
Fourth Generation (1980-Now)
The operating system is employed in this age for computer networks where users are aware of the existence of computers connected to one another.
The era of distributed computing has already begun, and users are comforted by a Graphical User Interface (GUI), which is an incredibly comfortable graphical computer interface.
The demand for traditional operating systems has increased as a result of the introduction of new wearable devices such as Smart Watches, Smart Glasses, VRGears, and others.
With the introduction of innovative gadgets such as Smart Watches, Smart Glasses, VR gears, and other wearable devices, the demand for unorthodox operating systems is also increasing.
Personal computers are an example of a type of operating system and device.
Q9) Explain allocation methods?
A9)
There are various methods which can be used to allocate disk space to the files. Selection of an appropriate allocation method will significantly affect the performance and efficiency of the system. Allocation method provides a way in which the disk will be utilized and the files will be accessed.
There are following methods which can be used for allocation.
- Contiguous Allocation.
- Extents
- Linked Allocation
- Clustering
- FAT
- Indexed Allocation
- Linked Indexed Allocation
- Multilevel Indexed Allocation
- Inode
Contiguous Allocation
If the blocks are allocated to the file in such a way that all the logical blocks of the file get the contiguous physical block in the hard disk then such allocation scheme is known as contiguous allocation.
In the image shown below, there are three files in the directory. The starting block and the length of each file are mentioned in the table. We can check in the table that the contiguous blocks are assigned to each file as per its need.
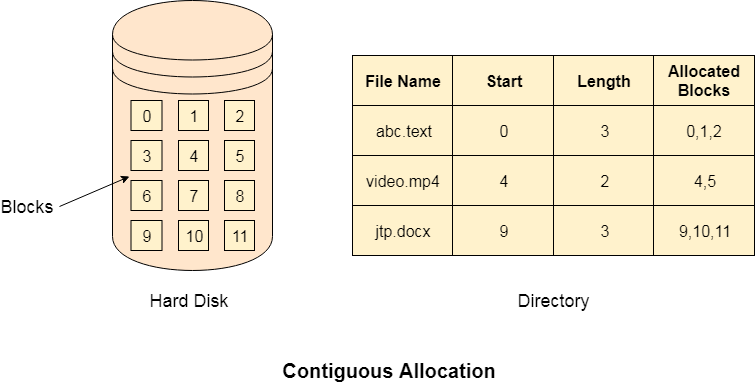
Fig 8: Contiguous allocation
Advantages
- It is simple to implement.
- We will get Excellent read performance.
- Supports Random Access into files.
Disadvantages
- The disk will become fragmented.
- It may be difficult to have a file grow.
Linked List Allocation
Linked List allocation solves all problems of contiguous allocation. In linked list allocation, each file is considered as the linked list of disk blocks. However, the disks blocks allocated to a particular file need not to be contiguous on the disk. Each disk block allocated to a file contains a pointer which points to the next disk block allocated to the same file.
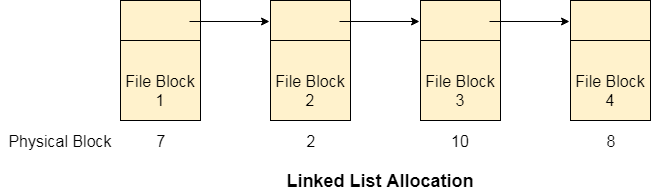
Fig 9: Linked list allocation
Advantages
- There is no external fragmentation with linked allocation.
- Any free block can be utilized in order to satisfy the file block requests.
- File can continue to grow as long as the free blocks are available.
- Directory entry will only contain the starting block address.
Disadvantages
- Random Access is not provided.
- Pointers require some space in the disk blocks.
- Any of the pointers in the linked list must not be broken otherwise the file will get corrupted.
- Need to traverse each block.
Indexed Allocation
Limitation of FAT
Limitation in the existing technology causes the evolution of a new technology. Till now, we have seen various allocation methods; each of them was carrying several advantages and disadvantages.
File allocation table tries to solve as many problems as possible but leads to a drawback. The more the number of blocks, the more will be the size of FAT.
Therefore, we need to allocate more space to a file allocation table. Since, file allocation table needs to be cached therefore it is impossible to have as many space in cache. Here we need a new technology which can solve such problems.
Indexed Allocation Scheme
Instead of maintaining a file allocation table of all the disk pointers, Indexed allocation scheme stores all the disk pointers in one of the blocks called as indexed block. Indexed block doesn't hold the file data, but it holds the pointers to all the disk blocks allocated to that particular file. Directory entry will only contain the index block address.
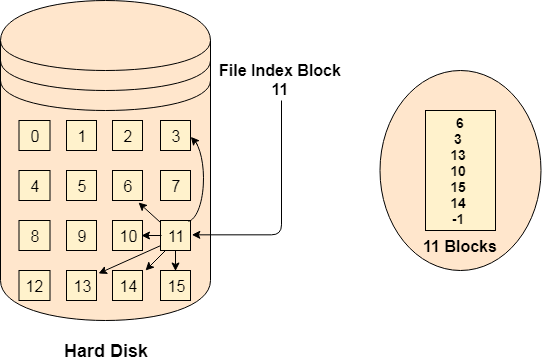
Fig 10: Index allocation
Advantages
- Supports direct access
- A bad data block causes the lost of only that block.
Disadvantages
- A bad index block could cause the lost of entire file.
- Size of a file depends upon the number of pointers, a index block can hold.
- Having an index block for a small file is totally wastage.
- More pointer overhead
Q10) What is the purpose and goal of disk arm scheduling algorithms?
A10)
As we know, a process needs two type of time, CPU time and IO time. For I/O, it requests the Operating system to access the disk.
However, the operating system must be fair enough to satisfy each request and at the same time, operating system must maintain the efficiency and speed of process execution.
The technique that operating system uses to determine the request which is to be satisfied next is called disk scheduling.
Let's discuss some important terms related to disk scheduling.
Seek Time
Seek time is the time taken in locating the disk arm to a specified track where the read/write request will be satisfied.
Rotational Latency
It is the time taken by the desired sector to rotate itself to the position from where it can access the R/W heads.
Transfer Time
It is the time taken to transfer the data.
Disk Access Time
Disk access time is given as,
Disk Access Time = Rotational Latency + Seek Time + Transfer Time
Disk Response Time
It is the average of time spent by each request waiting for the IO operation.
Purpose of Disk Scheduling
The main purpose of disk scheduling algorithm is to select a disk request from the queue of IO requests and decide the schedule when this request will be processed.
Goal of Disk Scheduling Algorithm
- Fairness
- High throughout
- Minimal traveling head time
Q11) What do you mean by system call?
A11) In an operating system software plays out every one of the following functions:
- Process management: Process management causes OS to create and delete processes. It likewise gives mechanisms for synchronization and communication among processes.
- Memory management: Memory management module plays out the role of assignment and de-allotment of memory space to programs needing the resources.
- File management: It deals with all the file-related task, for example, storage organization, recovery, naming, sharing, and protection of files.
- Device Management: Device management keeps tracks of all the devices. This module is in charge of the task also known as the I/O controller. It additionally plays out the undertaking of designation and de-distribution of the devices.
- I/O System Management: One of the primary objects of any OS is to conceal the identity of that hardware devices from the user.
- Secondary-Storage Management: Systems have a few degrees of storage which incorporates primary storage, secondary storage, and cache storage. Instructions and data must be put away in primary storage or cache so a running program can reference it.
- Security: Security module ensures the data and information of a computer system against malware danger and authorized access.
- Command interpretation: This module is interpreting directions given by the acting system and assign resources to process that directions.
- Networking: A distributed system is a collection of processors which don't share memory, hardware devices, or a clock. The processors speak with each other through the network.
- Job accounting: Keeping track of time and resource utilized by different job and users.
- Communication management: Manage the coordination and task of compilers, interpreters, and other software resource of the different users of the computer systems.
Q12) What are the types of system calls?
A12) System calls are divided into five categories.
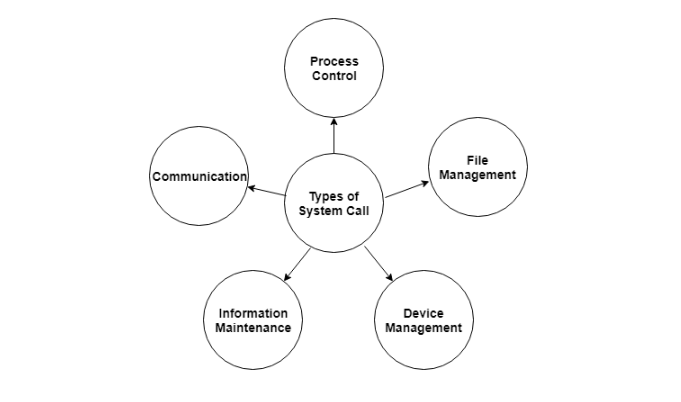
Fig 11: Types of system call
The following are the various sorts of system calls:
Process control
Processes such as process creation, process termination, and so on are handled by these system calls.
Functions
● End and Abort
● Load and Execute
● Create Process and Terminate Process
● Wait and Signal Event
● Allocate and free memory
File management
File manipulation is handled by these system calls, which include creating, reading, and writing to files.
Functions
● Create a file
● Delete file
● Open and close file
● Read, write, and reposition
● Get and set file attributes
Device management
Device manipulation, such as reading from device buffers and writing into device buffers, is handled by these system calls.
Functions
● Request and release device
● Logically attach/ detach devices
● Get and Set device attributes
Information maintenance
These system calls control the flow of data between the operating system and the user programme.
Functions
● Get or set time and date
● Get process and device attributes
Communication
These system calls can be used to communicate between processes. They're also in charge of setting up and disabling communication connections.
Functions
● Create, delete communications connections
● Send, receive message
● Help OS to transfer status information
● Attach or detach remote devices
Q13) Explain disk Scheduling Algorithms with example.
A13)
Disk Scheduling Algorithms
The list of various disks scheduling algorithm is given below. Each algorithm is carrying some advantages and disadvantages. The limitation of each algorithm leads to the evolution of a new algorithm.
- FCFS scheduling algorithm
- SSTF (shortest seek time first) algorithm
- SCAN scheduling
- C-SCAN scheduling
- LOOK Scheduling
- C-LOOK scheduling
FCFS Scheduling Algorithm
It is the simplest Disk Scheduling algorithm. It services the IO requests in the order in which they arrive. There is no starvation in this algorithm, every request is serviced.
Disadvantages
- The scheme does not optimize the seek time.
- The request may come from different processes therefore there is the possibility of inappropriate movement of the head.
Example
Consider the following disk request sequence for a disk with 100 tracks 45, 21, 67, 90, 4, 50, 89, 52, 61, 87, 25
Head pointer starting at 50 and moving in left direction. Find the number of head movements in cylinders using FCFS scheduling.
Solution
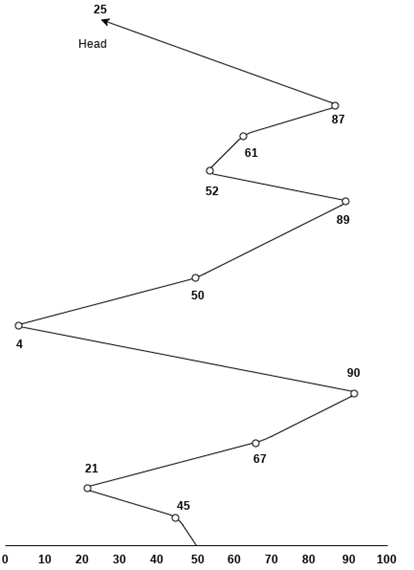
Number of cylinders moved by the head
= (50-45)+(45-21)+(67-21)+(90-67)+(90-4)+(50-4)+(89-50)+(61-52)+(87-61)+(87-25)
= 5 + 24 + 46 + 23 + 86 + 46 + 49 + 9 + 26 + 62
= 376
SSTF Scheduling Algorithm
Shortest seek time first (SSTF) algorithm selects the disk I/O request which requires the least disk arm movement from its current position regardless of the direction. It reduces the total seek time as compared to FCFS.
It allows the head to move to the closest track in the service queue.
Disadvantages
- It may cause starvation for some requests.
- Switching direction on the frequent basis slows the working of algorithm.
- It is not the most optimal algorithm.
Example
Consider the following disk request sequence for a disk with 100 tracks
45, 21, 67, 90, 4, 89, 52, 61, 87, 25
Head pointer starting at 50. Find the number of head movements in cylinders using SSTF scheduling.
Solution:
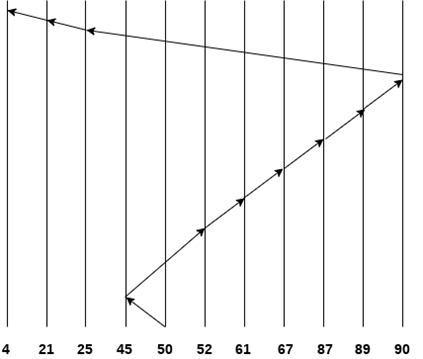
Number of cylinders = 5 + 7 + 9 + 6 + 20 + 2 + 1 + 65 + 4 + 17 = 136
SCAN and C-SCAN algorithm
Scan Algorithm
It is also called as Elevator Algorithm. In this algorithm, the disk arm moves into a particular direction till the end, satisfying all the requests coming in its path and then it turns back and moves in the reverse direction satisfying requests coming in its path.
It works in the way an elevator works, elevator moves in a direction completely till the last floor of that direction and then turns back.
Example
Consider the following disk request sequence for a disk with 100 tracks
98, 137, 122, 183, 14, 133, 65, 78
Head pointer starting at 54 and moving in left direction. Find the number of head movements in cylinders using SCAN scheduling.
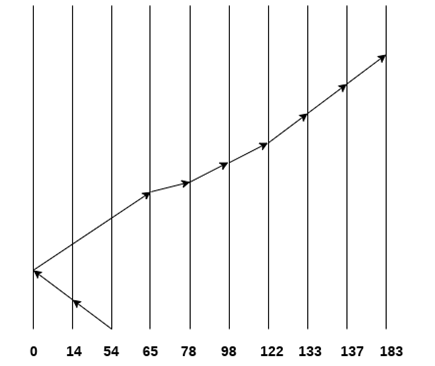
Number of Cylinders = 40 + 14 + 65 + 13 + 20 + 24 + 11 + 4 + 46 = 237
C-SCAN algorithm
In C-SCAN algorithm, the arm of the disk moves in a particular direction servicing requests until it reaches the last cylinder, then it jumps to the last cylinder of the opposite direction without servicing any request then it turns back and start moving in that direction servicing the remaining requests.
Example
Consider the following disk request sequence for a disk with 100 tracks
98, 137, 122, 183, 14, 133, 65, 78
Head pointer starting at 54 and moving in left direction. Find the number of head movements in cylinders using C-SCAN scheduling.
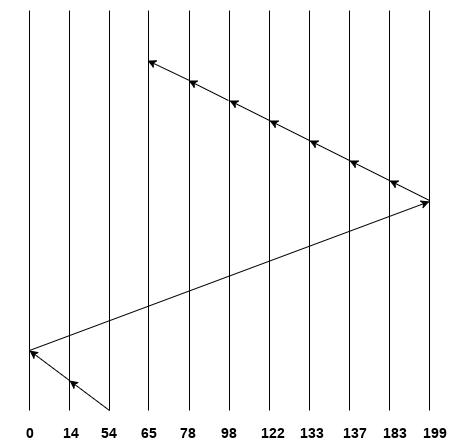
No. Of cylinders crossed = 40 + 14 + 199 + 16 + 46 + 4 + 11 + 24 + 20 + 13 = 387
Q14) What are the advantages of Monolithic Kernel?
A14)
Advantages of Monolithic Kernel
Some of the benefits of monolithic kernel square measure square measure
- The execution of the monolithic kernel is kind of quick because the services like memory management, file management, method programming etc. are enforced beneath constant address house.
- A method runs utterly in an exceedingly single address house within the monolithic kernel.
- The monolithic kernel could be a static single computer file.
- Disadvantages of Monolithic Kernel
- Some of the disadvantages of monolithic kernel square measure square measure
- If any service fails within the monolithic kernel, it results in the failure of the whole system.
- To add any new service, the whole software package must be changed by the user.
Q15) What is Microkernel?
A15)
Microkernel is one amongst the classification of the kernel. Being a kernel, it manages all system resources. However, during a microkernel, the user services and kernel services are enforced in numerous address house. The user services are unbroken in user address house, and kernel services are unbroken underneath kernel address house, therefore additionally reduces the dimensions of kernel and size of OS also.
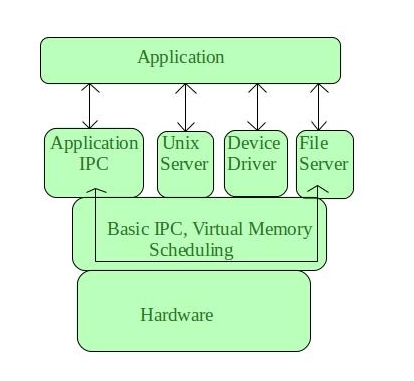
Fig 12 – Application
It provides token services of method and memory management. The communication between shopper program/application and services running in user address house is established through message passing, reducing the speed of execution microkernel. The OS remains unaffected as user services and kernel services are isolated thus if any user service fails it doesn't have an effect on kernel service. Therefore, it adds to at least one of the benefits during a microkernel. It's simply long i.e. if any new services are to be extra they're extra to user address house and therefore needs no modification in kernel house. It's additionally moveable, secure and reliable.
Microkernel design
Since kernel is that the core a part of the OS, thus it's meant for handling the foremost necessary services solely. Therefore, during this design solely, the foremost necessary services are within kernel and remainder of the OS services are gift within system computer program. Therefore, users are able to move with those not-so necessary services among the system application. And also, the microkernel is only to blame for the foremost necessary services of OS they're named as follows:
- Inter Process-Communication
- Memory Management
- CPU-Scheduling
Q16) What are the advantages and disadvantages of Batch Operating System?
A16)
Advantages of Batch Operating System:
- It is exceptionally hard to estimate or realize the time required by any job to finish. Processors of the batch systems realize to what extent the job would be when it is in line.
- Various users can share the batch systems
- The inert time for batch system is extremely less
- It is easy to oversee huge work more than once in batch systems
Disadvantages of Batch Operating System:
- The computer administrators should have complete information with batch systems
- Batch systems are difficult to debug
- It is at some point expense
- Different jobs should sit tight for an obscure time if any jobs fail
Q17) How many layers are there in stratified software package?
A17)
Layers in stratified software package
There square measure six layers within the stratified software package. A diagram demonstrating these layers is as follows:
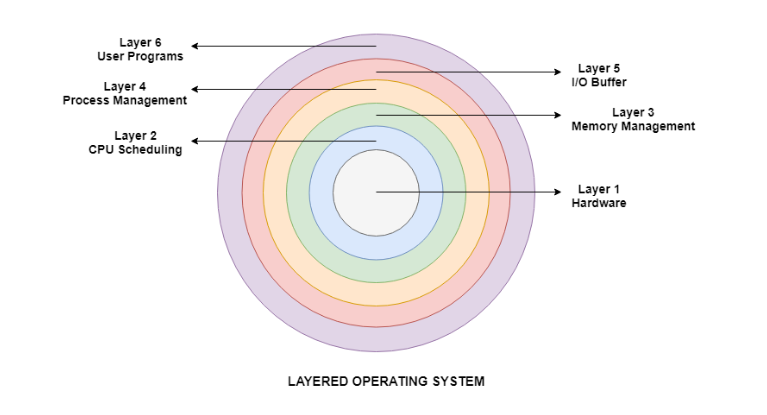
Fig 13 – Layered operating system
Details about the six layers are:
Hardware
This layer interacts with the system hardware and coordinates with all the peripheral devices used like printer, mouse, keyboard, scanner etc. The hardware layer is that the lowest layer within the stratified software package design.
CPU planning
This layer deals with planning the processes for the hardware. There square measure several planning queues that square measure wants to handle processes. Once the processes enter the system, they're place into the work queue. The processes that square measure able to execute within the main memory square measure unbroken within the prepared queue.
Memory Management
Memory management deals with memory and therefore the moving of processes from disk to primary memory for execution and back once more. This is often handled by the third layer of the software package.
Process Management
This layer is accountable for managing the processes i.e. distribution the method or to a process at a time. This is often referred to as method planning. The various algorithms used for method planning square measure FCFS (first come back 1st served), SJF (shortest job first), priority planning, round-robin planning etc.
I/O Buffer
I/O devices square measure important within the pc systems. They supply users with the means that of interacting with the system. This layer handles the buffers for the I/O devices and makes positive that they work properly.
User Programs
This is the best layer within the stratified software package. This layer deals with the various user programs associate degreed applications that run in an software package like word processors, games, browsers etc.
Q18) What is monolithic kernel?
A18)
The entire software package works within the kernel house within the monolithic system. This will increase the dimensions of the kernel furthermore because the software package. This is often totally different than the microkernel system wherever the minimum computer code that's needed to properly implement associate software package is unbroken within the kernel.
A diagram that demonstrates the design of a monolithic system is as follows −−
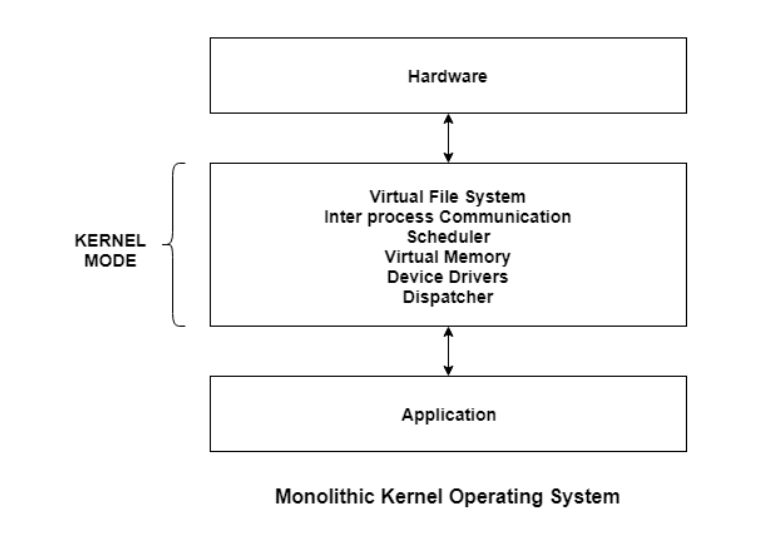
Fig 14 – Monolithic operating system
The kernel provides numerous services like memory management, file management, method programing etc. victimization perform calls. This makes the execution of the software package quite quick because the services square measure enforced beneath constant address house.
Q19) What is the differences between Microkernel and Monolithic Kernel?
A19)
Differences between Microkernel and Monolithic Kernel
Some of the variations between microkernel and monolithic kernel square measure given as follows −
- The microkernel is far smaller in size as compared to the monolithic kernel.
- The microkernel is well protractible whereas this is often quite sophisticated for the monolithic kernel.
- The execution of the microkernel is slower as compared to the monolithic kernel.
- Much additional code is needed to jot down a microkernel than the monolithic kernel.
- Examples of Microkernel square measure QNX, Symbian, L4 UNIX operating system etc. Monolithic Kernel examples square measure UNIX operating system, BSD etc.
Q20) Explain Linked List Allocation. Write its advantages and disadvantages.
A20)
Linked List Allocation
Linked List allocation solves all problems of contiguous allocation. In linked list allocation, each file is considered as the linked list of disk blocks. However, the disks blocks allocated to a particular file need not to be contiguous on the disk. Each disk block allocated to a file contains a pointer which points to the next disk block allocated to the same file.
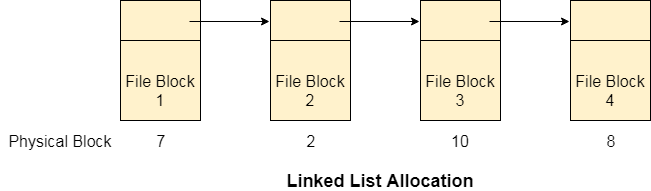
Fig 15: Linked list allocation
Advantages
- There is no external fragmentation with linked allocation.
- Any free block can be utilized in order to satisfy the file block requests.
- File can continue to grow as long as the free blocks are available.
- Directory entry will only contain the starting block address.
Disadvantages
- Random Access is not provided.
- Pointers require some space in the disk blocks.
- Any of the pointers in the linked list must not be broken otherwise the file will get corrupted.
- Need to traverse each block.