Unit - 6
Security
Q1) What is cyber security?
A1)
Cyber security is primarily about people, processes, and technologies working together to encompass the full range of threat reduction, vulnerability reduction, deterrence, international engagement, incident response, resiliency, and recovery policies and activities, including computer network operations, information assurance, law enforcement, etc.
OR
Cyber security is the body of technologies, processes, and practices designed to protect networks, computers, programs and data from attack, damage or unauthorized access.
The term cyber security refers to techniques and practices designed to protect digital data. The data that is stored, transmitted or used on an information system.
OR
Cyber security is the protection of Internet-connected systems, including hardware, software, and data from cyber attacks.
It is made up of two words one is cyber and other is security.
Cyber is related to the technology which contains systems, network and programs or data. Whereas security related to the protection which includes systems security, network security and application and information security.
Q2) What are Cyber security Fundamentals?
A2)
Confidentiality
Confidentiality is about preventing the disclosure of data to unauthorized parties. It also means trying to keep the identity of authorized parties involved in sharing and holding data private and anonymous.
Often confidentiality is compromised by cracking poorly encrypted data, Man-in-the-middle (MITM) attacks, disclosing sensitive data.
Standard measures to establish confidentiality include:
- Data encryption
- Two-factor authentication
- Biometric verification
- Security tokens
Integrity
Integrity refers to protecting information from being modified by unauthorized parties.
Standard measures to guarantee integrity include:
- Cryptographic checksums
- Using file permissions
- Uninterrupted power supplies
- Data backups
Availability
Availability is making sure that authorized parties are able to access the information when needed. Standard measures to guarantee availability include: Backing up data to external drives implementing firewalls
Having backup power supplies Data redundancy.
Q3) Draw diagram of cyber security layers?
A3)
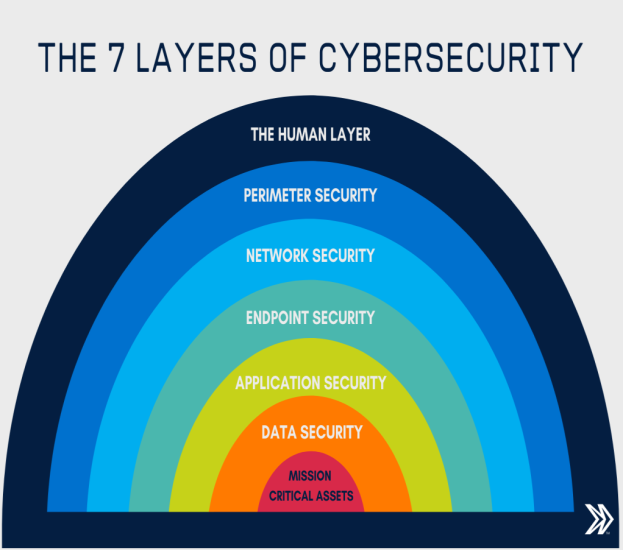
Q4) Define various security layers?
A4)
The 7 layers of cyber security should centre on the mission critical assets you are seeking to protect.
1: Mission Critical Assets – This is the data you need to protect
2: Data Security – Data security controls protect the storage and transfer of data.
3: Application Security – Applications security controls protect access to an application, an application’s access to your mission critical assets, and the internal security of the application.
4: Endpoint Security – Endpoint security controls protect the connection between devices and the network.
5: Network Security – Network security controls protect an organization’s network and prevent unauthorized access of the network.
6: Perimeter Security – Perimeter security controls include both the physical and digital security methodologies that protect the business overall.
7: The Human Layer – Humans are the weakest link in any cyber security posture. Human security controls include phishing simulations and access management controls that protect mission critical assets from a wide variety of human threats, including cyber criminals, malicious insiders, and negligent users.
Q5) Explain CIA triads?
A5)
CIA Triad
The CIA Triad is actually a security model that has been developed to help people think about various parts of IT security.
CIA triad broken down into following.
Confidentiality
It's crucial in today's world for people to protect their sensitive, private information from unauthorized access. Protecting confidentiality is dependent on being able to define and enforce certain access levels for information. In some cases, doing this involves separating information into various collections that are organized by who needs access to the information and how sensitive that information actually is - i.e., the amount of damage suffered if the confidentiality was breached.
Some of the most common means used to manage confidentiality include access control lists, volume and file encryption, and Unix file permissions.
Integrity
Data integrity is what the "I" in CIA Triad stands for. This is an essential component of the CIA Triad and designed to protect data from deletion or modification from any unauthorized party, and it ensures that when an authorized person makes a change that should not have been made the damage can be reversed.
Availability
This is the final component of the CIA Triad and refers to the actual availability of your data. Authentication mechanisms, access channels and systems all have to work properly for the information they protect and ensure it's available when it is needed. Understanding the CIA triad
The CIA Triad is all about information. While this is considered the core factor of the majority of IT security, it promotes a limited view of the security that ignores other important factors. For example, even though availability may serve to make sure you don't lose access to resources needed to provide information when it is needed, thinking about information security in itself doesn't guarantee that someone else hasn't used your hardware resources without authorization. It's important to understand what the CIA Triad is, how it is used to plan and also to implement a quality security policy while understanding the various principles behind it. It's also important to understand the limitations it presents. When you are informed, you can utilize the CIA Triad for what it has to offer and avoid the consequences that may come along by not understanding it.
Q6) What are active security attacks?
A6)
Types of Active attacks
Masquerade: in this attack, the intruder pretends to be a particular user of a system to gain access or to gain greater privileges than they are authorized for. A masquerade may be attempted through the use of stolen login IDs and passwords, through finding security gaps in programs or through bypassing the authentication mechanism.
Session replay: In this type of attack, a hacker steals an authorized user’s log in information by stealing the session ID. The intruder gains access and the ability to do anything the authorized user can do on the website.
Message modification: In this attack, an intruder alters packet header addresses to direct a message to a different destination or modify the data on a target machine.
Denial of service (DoS)attack, users are deprived of access to a network or web resource. This is generally accomplished by overwhelming the target with more traffic than it can handle.
Distributed denial-of-service (DDoS) exploit, large numbers of compromised systems (sometimes called a botnet or zombie army) attack a single target.
Passive Attacks: Passive attacks are relatively scarce from a classification perspective, but can be carried out with relative ease, particularly if the traffic is not encrypted.
Q7) What are passive attacks?
A7)
Types of Passive attacks:
Eavesdropping (tapping): the attacker simply listens to messages exchanged by two entities. For the attack to be useful, the traffic must not be encrypted. Any unencrypted information, such as a password sent in response to an HTTP request, may be retrieved by the attacker.
Traffic analysis: the attacker looks at the metadata transmitted in traffic in order to deduce information relating to the exchange and the participating entities, e.g., the form of the exchanged traffic (rate, duration, etc.). In the cases where encrypted data are used, traffic analysis can also lead to attacks by cryptanalysis, whereby the attacker may obtain information or succeed in un encrypting the traffic.
Software Attacks: Malicious code (sometimes called malware) is a type of software designed to take over or damage a computer user's operating system, without the user's knowledge or approval. It can be very difficult to remove and very damaging.
Q8) Explain various virus attacks?
A8)
Attack | Characteristics |
Virus | A virus is a program that attempts to damage a computer system and replicate itself to other computer systems. A virus: Requires a host to replicate and usually attaches itself to a host file or a hard drive sector. Replicates each time the host is used. Often focuses on destruction or corruption of data. Usually attaches to files with execution capabilities such as .doc, .exe, and .bat extensions. Often distributes via e-mail. Many viruses can e-mail themselves to everyone in your address book.
|
Worm | A worm is a self-replicating program that can be designed to do any number of things, such as delete files or send documents via e-mail. A worm can negatively impact network traffic just in the process of replicating itself. A worm: Can install a backdoor in the infected computer. Is usually introduced into the system through a vulnerability. Infects one system and spreads to other systems on the network. Example: Code Red.
|
Trojan horse | A Trojan horse is a malicious program that is disguised as legitimate software. Discretionary environments are often more vulnerable and susceptible to Trojan horse attacks because security is user focused and user directed. Thus, the compromise of a user account could lead to the compromise of the entire environment. A Trojan horse: Cannot replicate itself. Often contains spying functions (such as a packet sniffer) or backdoor functions that allow a computer to be remotely controlled from the network. Often is hidden in useful software such as screen savers or games. Example: Back Orifice, Net Bus, Whack-a-Mole.
|
Logic Bomb | A Logic Bomb is malware that lies dormant until triggered. A logic bomb is a specific example of an asynchronous attack. A trigger activity may be a specific date and time, the launching of a specific program, or the processing of a specific type of activity. Logic bombs do not self-replicate.
|
Q9) Design model for network security?
A9)
MODEL FOR NETWORK SECURITY
Using this model requires us to:
1. Design a suitable algorithm for the security transformation
2. Generate the secret information (keys) used by the algorithm.
3. Develop methods to distribute and share the secret information.
4. Specify a protocol enabling the principals to use the transformation and secret information for a security service
SYMMETRIC ENCRYPTION
Sender ad recipient share a common key
All classical encryption algorithms are private-key
Was only type prior to invention of public key in 1970’s
And by far mostly used.
Some basic terminology
Plaintext – original message
Cipher text – coded message
Cipher – algorithm for transforming plaintext to ciphertext
Key – info used in cipher known only to sender/receiver
Encipher (encrypt) – converting plaintext to ciphertext
Decipher (decrypt) – recovering ciphertext from plaintext
Cryptography – study of encryption principles /methods
Cryptanalysis (codebreaking) – study of principles /methods of deciphering cipher text without knowing key.
Cryptology – field of both cryptography and cryptanalysis
Q10) Define Cryptography?
A10)
Cryptography is a phenomenon in which a plain text is sent in Network converting it into cipher text to prevent miss use of data while transmission in a network.
Cryptography
Private key Traditional private/secret/single key cryptography uses one key Shared by both sender and receiver
- If this key is disclosed communications are compromised
- Also is symmetric, parties are equal
- Hence does not protect sender from receiver forging a message & claiming is sent by sender
Uses two keys
- A public & a private key.
• Asymmetric since parties are not equal
• Uses clever application of number theoretic concepts to function
• Complements rather than replaces private key crypto • Developed to address two key issues:
Key distribution
How to have secure communications in general without having to trust a with your key
Digital signatures
How to verify a message comes intact from the claimed sender
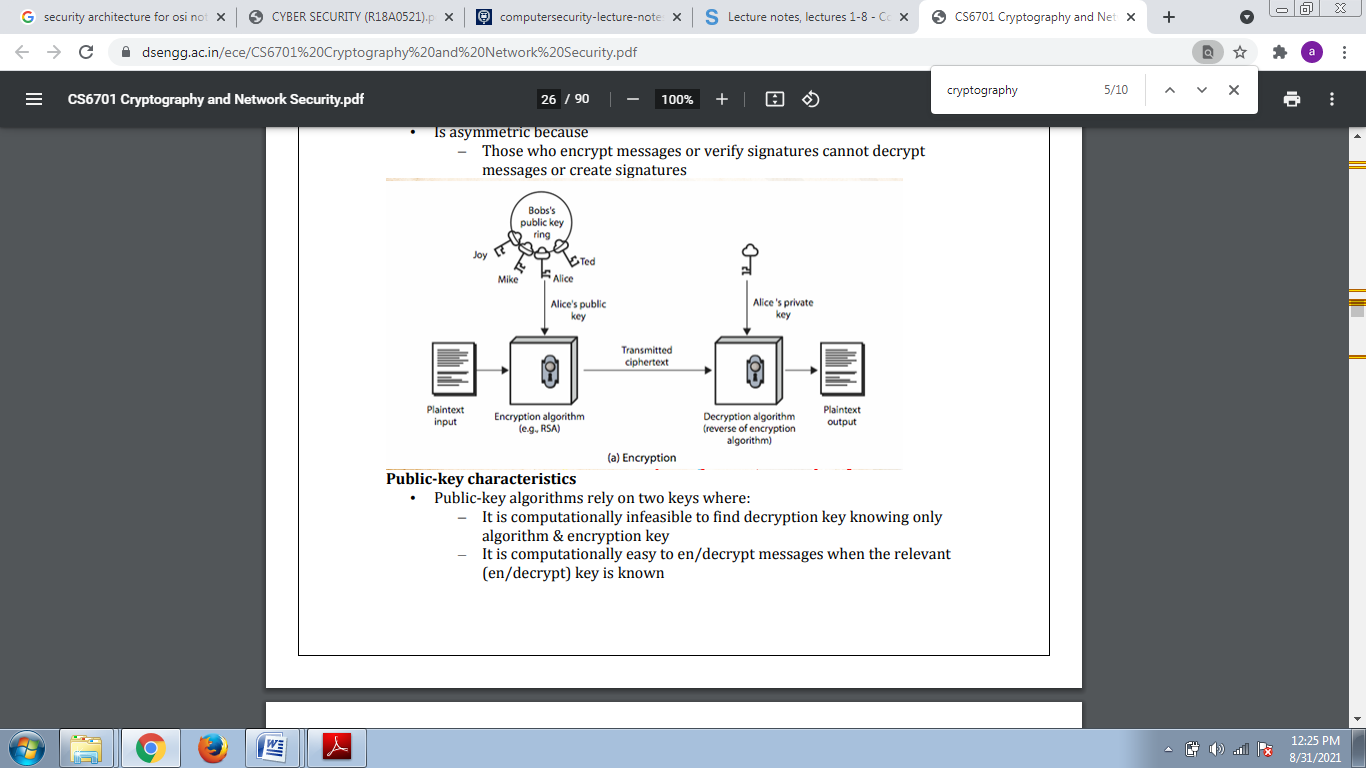
Asymmetric cryptography involves the use of two keys:
A public-key, which may be known by anybody, and can be used to encrypt messages, and verify signatures
A private-key, known only to the recipient, used to decrypt messages, and sign (create) signatures
• Is asymmetric because Those who encrypt messages or verify signatures cannot decrypt messages or create signature.
Q11) Explain TSL?
A11)
TLS (Transport layer security)
Standard rfc 2246 similar to sslv3 with minor differences
In record format version number Uses hmac for mac A pseudo-random function expands secrets Has additional alert codes Some changes in supported ciphers Changes in certificate types & negotiations Changes in crypto computations & padding.
Application security
There are two components of security in mobile computing:
Security of devices and security in networks. A secure network access involves authentication between the device and the base stations or Web servers. This is to ensure that only authenticated devices can be connected to the network for obtaining the requested services. No Malicious Code can impersonate the service provider to trick the device into doing something it does not mean to. Thus, the networks also play a crucial role in security of mobile devices. Some eminent kinds of attacks to which mobile devices are subjected to are: push attacks, pull attacks and crash attacks. Authentication services security is important given the typical attacks on mobile devices through wireless networks: Dos attacks, traffic analysis, eavesdropping, man-in-the-middle attacks and session hijacking. Security measures in this scenario come from Wireless Application Protocols (WAPs), use of VPNs, media access control (MAC) address filtering and development in 802.xx standards.
Q12) What is MIME?
A12)
S/MIME (Secure/Multipurpose Internet Mail Extensions)
Security enhancement to mime email original internet rfc822 email was text only Mime provided support for varying content types and multi part messages with encoding of binary data to textual form S/mime added security enhancements Have s/mime support in many mail agent. Eg MS outlook, Mozilla, mac mail etc.
S/MIME functions
- Enveloped data
- Encrypted content and associated keys
- Signed data
- Encoded message + signed digest
- Clear-signed data
- Clear text message + encoded signed digest
- Signed & enveloped data
- Nesting of signed & encrypted entities
S/MIME cryptographic algorithms
Digital signatures: dss & rsa Hash functions: sha-1 & md5
Session key encryption: elgamal & rsa Message encryption: aes, triple des, rc2/40 and others Mac: hmac with sha-1 Have process to decide which algorithms to use.
S/MIME messages
S/mime secures a mime entity with a signature, encryption, or both Forming a mime wrapped packets object Have a range of content types Enveloped data, Signed data, Clear-signed data,
Registration request, Certificate only message.
Q13) What is IPSEC?
A13)
IP Security
Have a range of application specific security mechanisms
E.g. S/mime, pgp, kerberos, ssl/https. However, there are security concerns that cut across protocol layers Would like security implemented by the network for all applications.
General ip security mechanisms Provides
Authentication
Confidentiality
Key management
Applicable to use over lans, across public & private wans, & for the internet.
Benefits of IPSEC
- In a firewall/router provides strong security to all traffic crossing the perimeter
- In a firewall/router is resistant to bypass
- Is below transport layer, hence transparent to applications
- Can be transparent to end users
- Can provide security for individual users
- Secures routing architecture
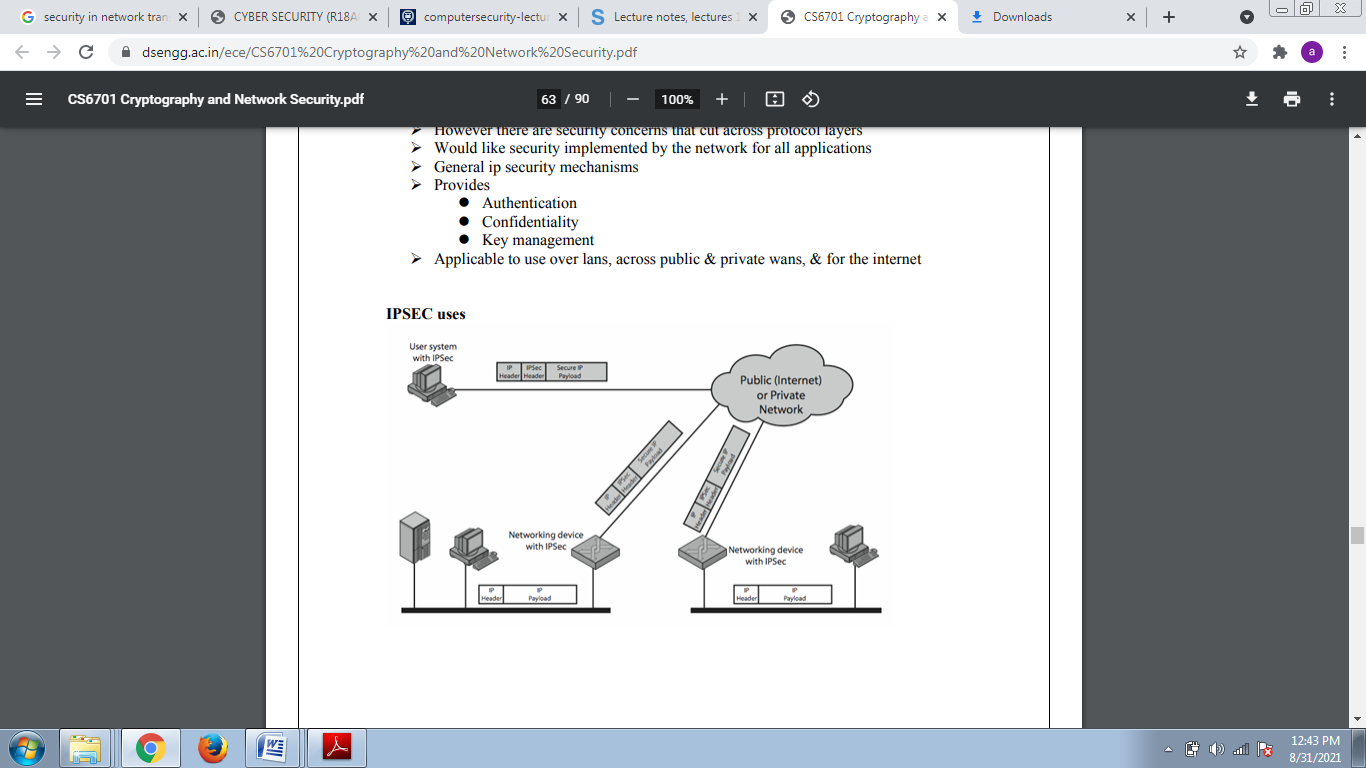
Q14) What do you mean by SSL?
A14)
SSL (Secure Socket Layer)
Transport layer security service Originally developed by Netscape Version 3 designed with public input Subsequently became internet standard known as tls (transport layer security) Uses tcp to provide a reliable end-to-end service SSL has two layers of protocols.
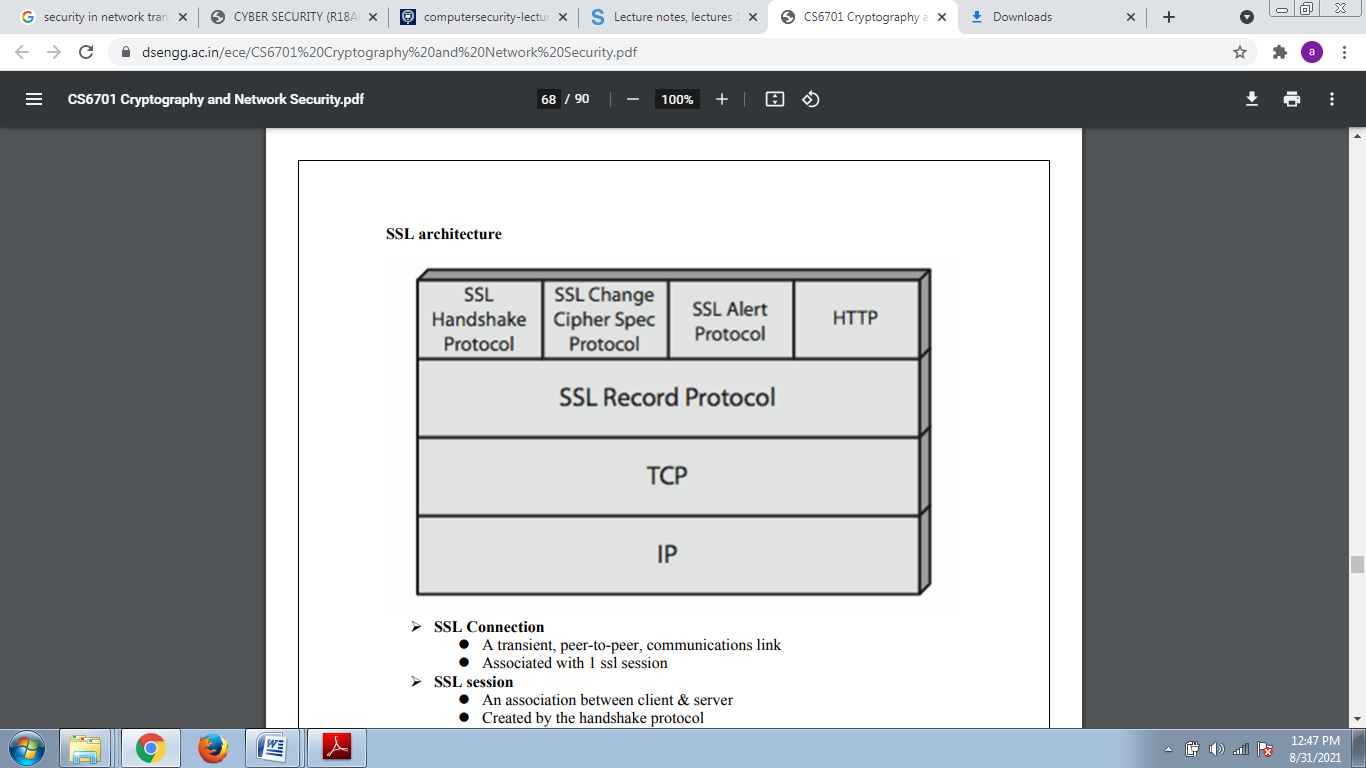
SSL Connection
A transient, peer-to-peer, communications link Associated with 1 ssl session.
SSL session
An association between client & server Created by the handshake protocol Define a set of cryptographic parameters May be shared by multiple ssl connections.
Q15) Write short note on HTTPS?
A15)
HTTPS stands for Hypertext Transfer Protocol Secure. It is the protocol where encrypted HTTP data is transferred over a secure connection. By using secure connection such as Transport Layer Security or Secure Sockets Layer, the privacy and integrity of data are maintained and authentication of websites is also validated.
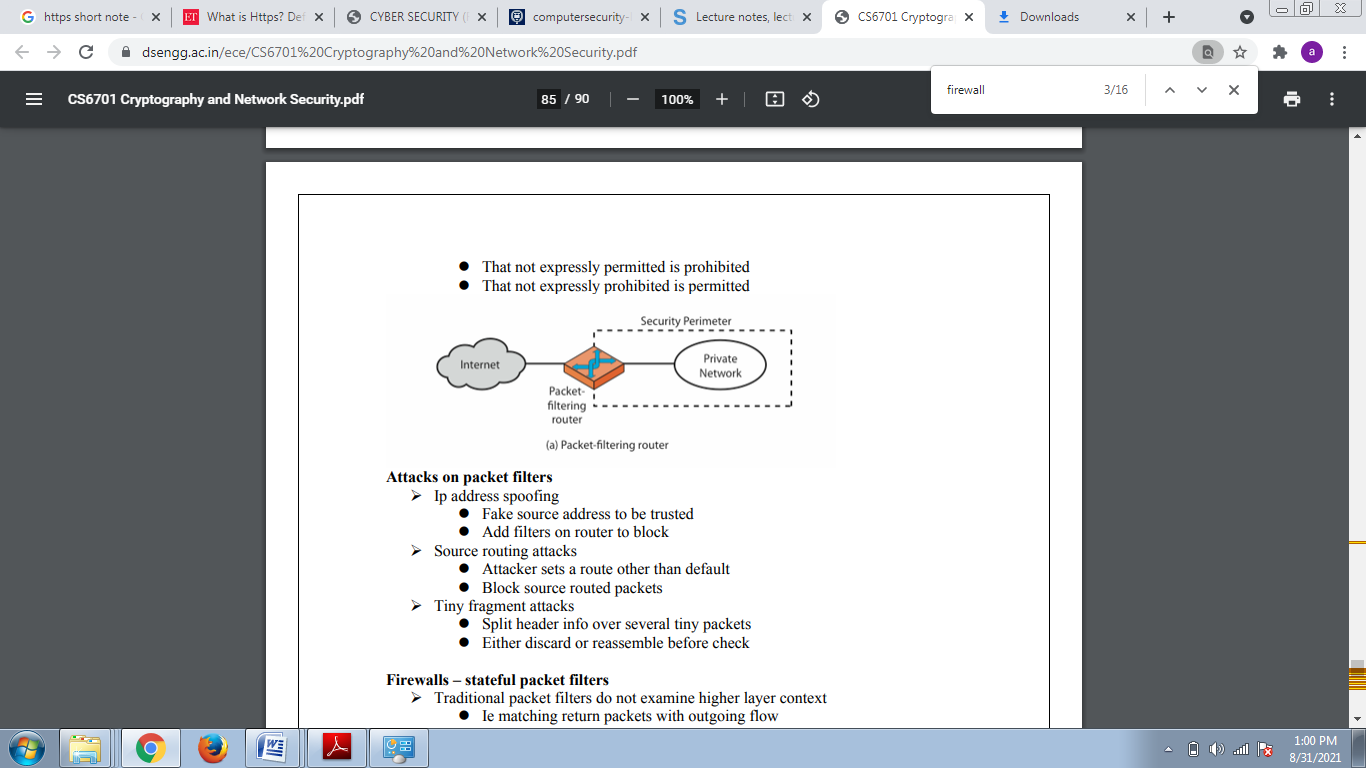
Q16) What is firewall?
A16)
It is a choke point of control and monitoring Interconnects networks with differing trust Imposes restrictions on network services. Only authorized traffic is allowed Auditing and controlling access Can implement alarms for abnormal behavior Provide Nat & usage monitoring Implement vpns using IPsec Must be immune to penetration.
Firewall limitations
- Cannot protect from attacks bypassing it
- Cannot protect against internal threats
- Cannot protect against transfer of all virus infected programs or files
- Because of huge range of o/s & file types
Firewalls packet filters
Simplest, fastest firewall component. Foundation of any firewall system
Examine each ip packet (no context) and permit or deny according to rules. Hence restrict access to services (ports) Possible default policies.
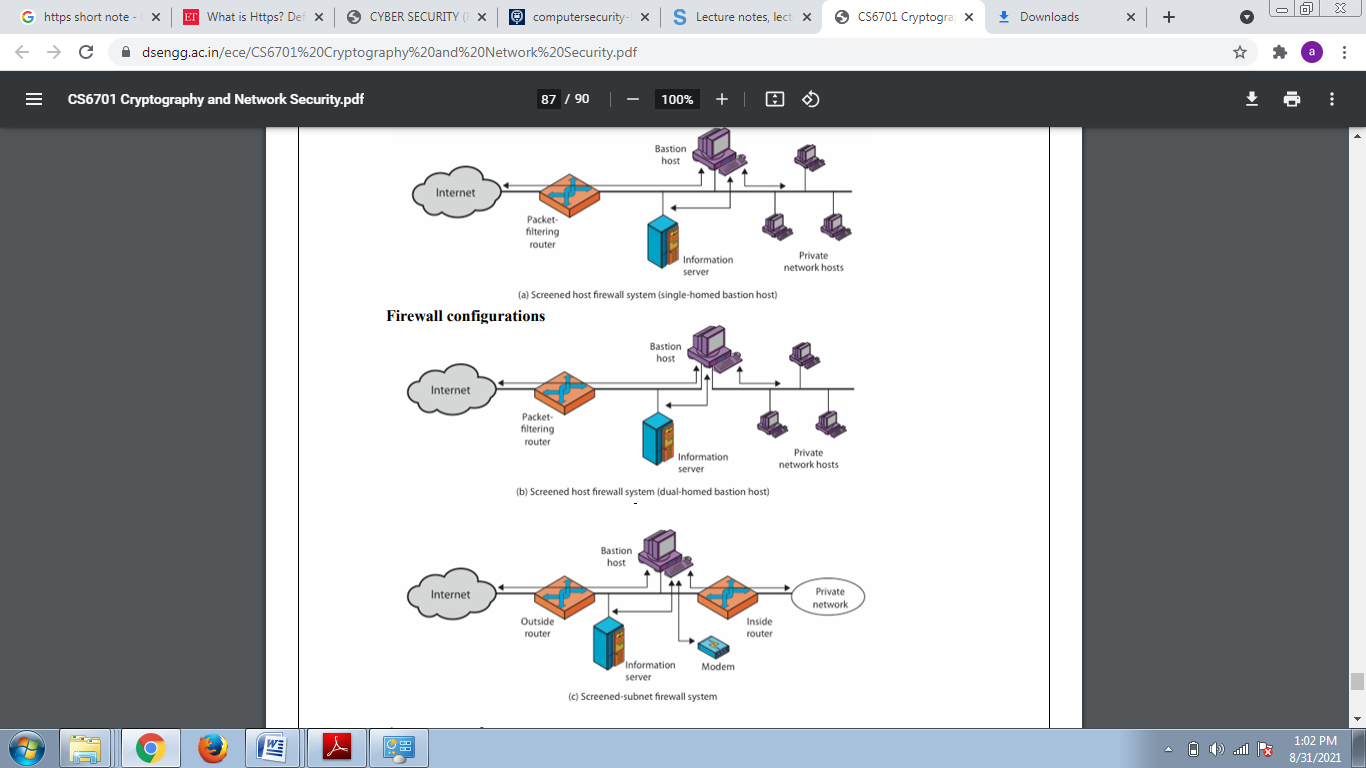
Various firewall configurations are shown below.
Intrusion Detections
Significant issue for networked systems is hostile or unwanted access Either via network or local Can identify classes of intruders. Masquerader, Misfeasor, Clandestine user Varying levels of competence. Clearly a growing publicized problem.
Intrusion techniques
Aim to gain access and/or increase privileges on a system. Basic attack methodology Target acquisition and information gathering’ Initial access Privilege escalation Covering track’s Key goal often is to acquire passwords So then exercise access rights of owner
Password guessing
One of the most common attacks Attacker knows a login (from email/web page etc) Then attempts to guess password for it Defaults, short passwords, common word searches User info (variations on names, birthday, phone, common words/interests) Exhaustively searching all possible passwords Check by login or against stolen password fill Success depends on password chosen by user Surveys show many users choose poorly.
Password capture
Another attack involves password capture Watching over shoulder as password is entered Using a trojan horse program to collect
Monitoring an insecure network login E.g., Telnet, ftp, web, email
Extracting recorded info after successful login (web history/cache, last number dialled etc.) Using valid login/password can impersonate user
Users need to be educated to use suitable precautions/countermeasures.
Intrusion detection
In evitably will have security failures So need also to detect intrusions so can Block if detected quickly Act as deterrent Collect info to improve security Assume intruder will behave differently to a legitimate user but will have imperfect distinction between.
Approaches to intrusion detection
- Statistical anomaly detection
- Threshold
- Profile based
- Rule-based detection
- Anomaly
- Penetration identification
Q17) Draw Digital Forensics Lifecycle?
A17)
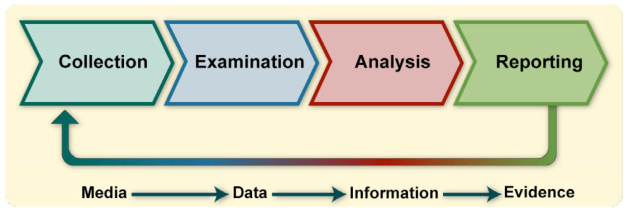
Collection: The first step in the forensic process is to identify potential sources of data and acquire data from them.
Examination: After data has been collected, the next phase is to examine the data, which involves assessing and extracting the relevant pieces of information from the collected data. This phase may also involve bypassing or mitigating OS or application features that obscure data and code, such as data compression, encryption, and access control mechanisms.
Analysis: Once the relevant information has been extracted, the analyst should study and analyze the data to draw conclusions from it. The foundation of forensics is using a methodical approach to reach appropriate conclusions based on the available data or determine that no conclusion can yet be drawn.
Reporting: The process of preparing and presenting the information resulting from the analysis phase.
Q18) What are the Challenges in Computer Forensics?
A18)
Digital forensics has been defined as the use of scientifically derived and proven methods towards the identification, collection, preservation, validation, analysis, interpretation, and presentation of digital evidence derivative from digital sources to facilitate the reconstruction of events found to be criminal. But these digital forensics investigation methods face some major challenges at the time of practical implementation. Digital forensic challenges are categorized into three major heads as per Fahdi, Clark, and Furnell are.
- Technical challenges
- Legal challenges
- Resource Challenges
Q19) Define various Categories of vulnerabilities?
A19)
Categories of vulnerabilities Corrupted (Loss of integrity)
- Leaky (Loss of confidentiality)
- Unavailable or very slow (Loss of availability)
- Threats represent potential security harm to an asset when vulnerabilities are exploited Attacks are threats that have been carried out Passive Make use of information from the system without affecting system resources Active Alter system resources or affect operation
- Insider Initiated by an entity inside the organization
- Outsider Initiated from outside the perimeter
- Computer criminals Computer criminals have access to enormous amounts of hardware, software, and data they have the potential to cripple much of effective business and government throughout the world. In a sense, the purpose of computer security is to prevent these criminals from doing damage. We say computer crime is any crime involving a computer or aided by the use of one. Although this definition is admittedly broad, it allows us to consider ways to protect ourselves, our businesses, and our communities against those who use computers maliciously. One approach to prevention or moderation is to understand who commits these crimes and why. Many studies have attempted to determine the characteristics of computer criminals. By studying those who have already used computers to commit crimes, we may be able in the future to spot likely criminals and prevent the crimes from occurring.
Q20) Explain various types of computer virus?
A20)
1.Virus
It is a type of malicious software program that spread throughout the computer files without the knowledge of a user. It is a self-replicating malicious computer program that replicates by inserting copies of itself into other computer programs when executed. It can also execute instructions that cause harm to the system.
2. Worm
It is a type of malware whose primary function is to replicate itself to spread to uninfected computers. It works same as the computer virus. Worms often originate from email attachments that appear to be from trusted senders.
3. Trojan horse
It is a malicious program that occurs unexpected changes to computer setting and unusual activity, even when the computer should be idle. It misleads the user of its true intent. It appears to be a normal application but when opened/executed some malicious code will run in the background.
4. Backdoors
It is a method that bypasses the normal authentication process. A developer may create a backdoor so that an application or operating system can be accessed for troubleshooting or other purposes.
5. Bots
A bot (short for "robot") is an automated process that interacts with other network services. Some bots program run automatically, while others only execute commands when they receive specific input. Common examples of bot’s program are the crawler, chatroom bots, and malicious bots.