Unit 4
Network Layer
Q1) Explain Class-full Addressing?
A1)
Classful Addressing
With classful routing, IP v4 addresses were divided into five classes(A to E).
Classes A-C : unicast addresses
Class D : multiclass addresses
Class E : Reserved for future use.
In a class A address, the first bit of the first octet is always ‘0’. Thus, class A addresses range from 0.0.0.0 to 127.255.255.255(as 01111111 in binary converts to 127 in decimal).
The first 8 bits or the first octet denote the network portion and the rest 24 bits or the 3 octets belong to the host portion.
Example 10.1.1.1
Exception
-127.X.X.X is reserved for loopback
-0.X.X.X is reserved for default network.
Therefore, the actual range of class A addresses is: 1.0.0.0 to 126.255.255.255
In a class B address, the first octet would always start with ’10’. Thus, class B addresses range from 128.0.0.0 to 191.255.255.255.
The first 16 bits or the first two octets denote the network portion and the remaining 16 bits or two octets belong to the host portion.
Example 172.16.1.1
In a class C address, the first octet would always start with ‘110’. Thus, class C addresses range from 192.0.0.0 to 223.255.255.255. The first 24 bits or the first three octets denote the network portion and the rest 8 bits or the remaining one octet belong to the host portion.
Example 192.168.1.1
Class D is used for multicast addressing and in a class D address the first octet would always start with ‘1110’. Thus, class D addresses range from 224.0.0.0 to 239.255.255.255.
Example 239.2.2.2
Class D addresses are used by routing protocols like OSPF, RIP, etc.
Class E addresses are reserved for research purposes and future use. The first octet in a class E address starts with ‘1111’. Thus, class E addresses range from 240.0.0.0 to 255.255.255.255.
Q2) Explain Sub netting and Super netting?
A2)
Sub netting is the procedure to divide the network into sub-networks or small networks.
Supernetting is the procedure of combine the small networks into larger space. In subnetting the Network addresses’ bits are increased. The Host addresses’ bits are increased.
Subnetting is implemented via Variable-length subnet masking, While super netting is implemented via Classless interdomain routing.
Q.3 Explain the differences of sub netting or super netting?
A3)
Difference between Subnetting and Supernetting:
Sl No | Subnetting | Supernetting |
1 | Subnetting is the procedure to divide the network into sub networks | It is the procedure of combining the small networks |
2 | Network addresses’ bits are increased | Host addresses bits are increased |
3 | The mask bits are moved towards the right | The mask bits are moved towards the left |
4 | Variable length subnet masking | Classless interdomain routing |
5 | Address depletion is reduced or removed | Simplify routing process |
Q4) Explain classless addressing?
A4)
CIDR Block-
When a user asks for specific number of IP Addresses,
Rules For Creating CIDR Block-
A CIDR block is created based on the following 3 rules-
Rule-01:
All the IP Addresses in the CIDR block must be contiguous.
Rule-02:
The size of the block must be presentable as power of 2.
Rule-03:
First IP Address of the block must be divisible by the size of the block.
CIDR Notation-
CIDR IP Addresses look like-
a.b.c.d / n
Example-
An example of CIDR IP Address is-
182.0.1.2 / 28
It suggests-
Q5) Explain delivery?
A5)
The network layer supervises the handling of the packets by the underlying physical networks.
This handling is called as delivery of a packet.
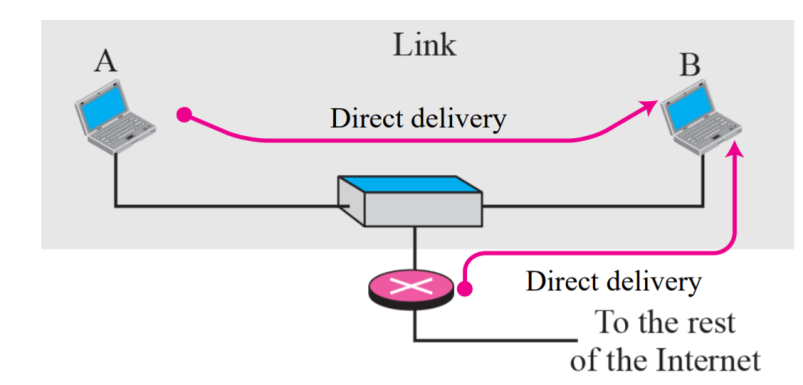
The delivery of a packet to its final destination is accomplished using two different methods of delivery: direct and indirect
Direct Delivery:
The final destination of the packet is a host connected to the same physical network as the deliverer.
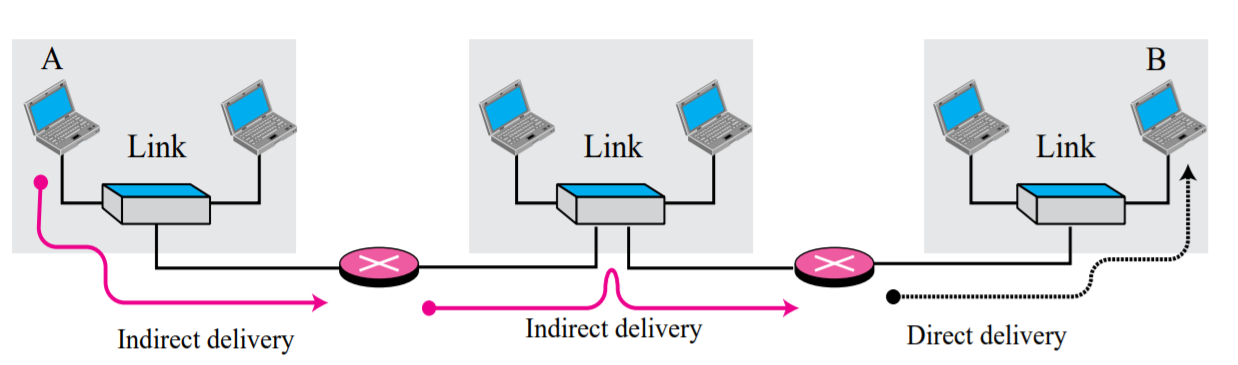
Indirect Delivery:
The destination host in not on the same network as the delivery
Q6) Explain forward and routing?
A6)
Routing is the process of deciding where to send a received packet. If this is the destination host, we send it up the stack to an application process. If not, we use the destination IP address and the IP routing table to choose an interface that is the best route to the next hop.
Forwarding is the act of sending the packet to the next hop. It also has a more generic meaning of passing on something received from the network rather than accepting it on this host; which can also be applied to application level traffic like e-mail and newsgroup messages - often in the expression “store-and-forward”.
Q7) Explain routing methods?
A7)
Shortest path
Link state Routing
The LSP is transmitted to all other routers who each update their own records. When a router receives LSPs from all routers it can use collectively that information to make topology-level decisions.
Distance vector routing
A distance-vector routing (DVR) protocol requires that the router inform its neighbours that topology changes periodically.
Distance Vector Algorithm –
Q8) Explain link state routing?
A8)
State Routing –
While distance vector routers use a distributed algorithm to compute their routing tables, link-state routing uses link-state routers to exchange messages that allow each router to learn the entire network topology.
Based on this topologyeach router is able to compute its routing table by using a shortest path computation.
Features of link state routing protocols –
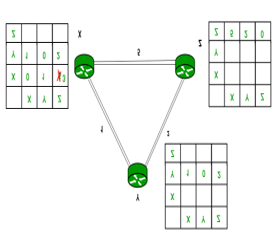
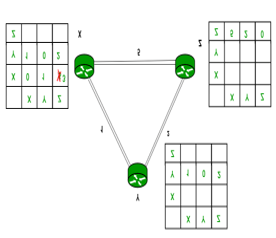
Consider 3-routers X, Y and Z as shown in figure. Each router has their routing table. Every routing table will contain distance to the destination nodes.
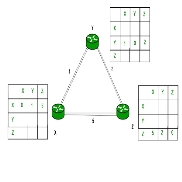
Consider router X , X will share it routing table to neighbours and neighbours will share it routing table to it to X and distance from node X to destination will be calculated using bellmen- ford equation.
Dx(y) = min{C(x,v) + Dv(y)} for each node y ∈ N
We can see that distance will be less going from X to Z when Y is intermediate node (hop) so that it updates the routing table X.
Similarly, for Z also
Finally, the routing table for all –
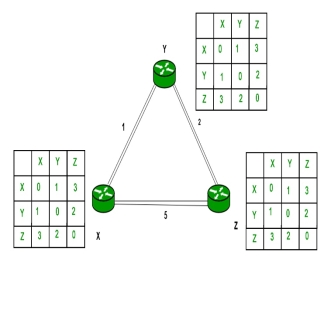
Q9) Explain broadcast routing?
A9)
Q10) Explain congestion algorithms?
A10)
Principles:
Congestion in a network occur if the load on the network that is the number of packets sent to the network is greater than the capacity of the network that is the number of packets a network can handle. Congestion control refers to the mechanism and techniques to control the congestion and keep the load below the capacity.
Congestion Prevention policies
The incoming messages have finite size however overflowing queues will cause packets to be dropped. Long queue delays will cause packets to be resent and the dropped packets will cause packets to be resent.
The senders that are trying to transmit to a congested destination also become congested. They must continually resend packets that have been dropped in memory or that have timed out. They must continue to hold outgoing/ unacknowledged messages in memory.
Q11) Explain the congestion control approaches?
A11)
Congestion control in datagram subnet
Congestion control approaches which can be used in the datagram subnets. The techniques are:
Load shedding:
The principle of load shedding states that when the routers are being inundated by the packets away. A router which is flooding with packets due to congestion can drop any packets at random. The policy for dropping a packet depends on the type of packet. So, the policy for file transfer called wine and that for the multimedia is called milk. To, implement such an intelligent discard policy, co-operation from the sender is essential. The applications that mark their packets are to be discarded the routers can first drop packets from lowest class.
Jitter control:
Jitter is defined as the variation in delay for the packets belonging to the same flow. The real time audio and video cannot tolerate jitter on the other hand the jitter does not matter if the packets are carrying an information contained in a file. For the audio and video transmission if the packets take 20 msec to 30msec to reach the destination, it does not matter, provided the delay remains constant. When a packet arrives at a router, the router will check to see whether the packet is behind or ahead and by what time. This information is stored in the packet and updated every hop. If the packet is ahead of the schedule then the router will hold it for slightly longer time and if the packet is behind the schedule, then the router will try to send it out as quickly as possible.