UNIT 3
Memory Management and Deadlock
Q1) What are System modes in an operating system?
A1)
a) Request. The process request for the resource first. In the event that the request can't be assigned quickly (for instance, if the resource is being utilized by another process), at that point the mentioning process must wait until it can procure the resource.
b) Use. The process can work on the resource (for instance, if the resource is a printer, the process can print on the printer).
c) Release. The process release the resource after utilizing it.
6. A lot of processes is in a deadlocked state when each process in the set is waiting for an event that can be caused uniquely by another process in the set.
7. The event with which we are fundamentally worried here are resource acquirement and release. The resources might be either physical resources (for instance, printers, tape drives, memory space, and CPU cycles) or logical resources (for instance, files, semaphores, and monitors).
Q2) Explain Deadlock characterization.
A2)
In a deadlock, processes never complete its execution, and system resources are tied up, keeping different jobs from beginning.
a) A deadlock occurs in operating system when at least two processes need some resource to finish their execution that is held by the different process.
b) A deadlock happens if the four Coffman conditions prove to be true. But, these conditions are not totally related. They are describes as follows:
Mutual Exclusion :
a) There ought to be a resource that must be held by one process at once.
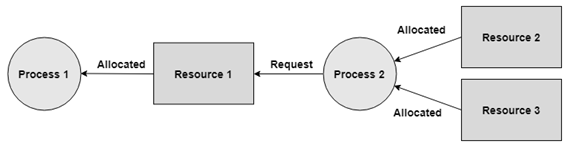
b) In the figure below, there is a single instance of Resource 1 and it is held by Process 1 as it were.


Allocated

Hold and Wait :
a) A process can hold numerous resources and still demand more resources from different processes which are holding them.
b) In the graph given beneath, Process 2 holds Resource 2 and Resource 3 and is mentioning the Resource 1 which is held by Process 1.
No Preemption :
a) A resource can't be pre-empted forcefully from a process. A process can just release a resource wishfully.
b) In the graph underneath, Process 2 can't preempt Resource 1 from Process 1. It might be discharged when Process 1 gives up it intentionally after its execution is finished.

Circular Wait :
a) A process is waiting for the resource held continuously by other process, which is waiting for the resource held by the third process, etc, till the last process is waiting for a resource held by the first process. This structures a round chain.
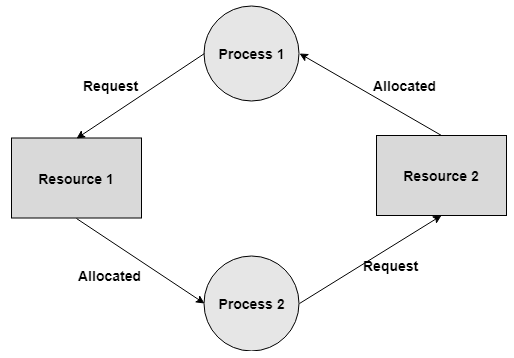
b) For instance: Process 1 is assigned Resource 2 and it is requesting Resource 1. Likewise, Process 2 is assigned Resource 1 and it is requesting Resource 2. This structures a circular wait loop.
Q3) What is Resource-Allocation Graph in an operating system?
A3)
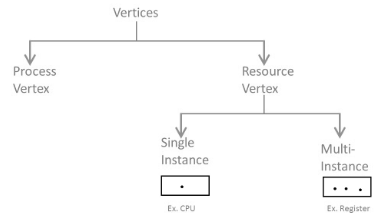
a) Process vertex – Every process will be shown as a process vertex. In RAG, the process will be drawn with a circle.
b) Resource vertex – Every resource will be shown as a resource vertex. It is likewise of two types –
- Assign Edges-
- Assign edges shows the assigned of resources to the processes.
- They are drawn as an arrow pointed towards the process and tail focuses to the resource.
- Request Edges-
- Request edges shows the waiting condition of processes for the resources.
- They are drawn as arrow where the head of the arrow indicates the instance of the resource and tail of the arrow focuses to the process.
- On the off chance that a process requires 'n' instances of a resource type, at that point 'n' assign edges will be drawn.
Example- Resource Allocation Graph is shown in figure below:
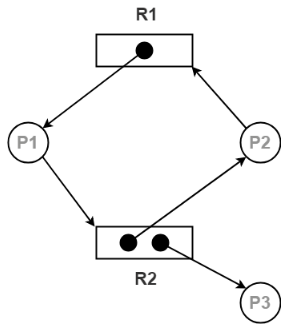
The above graph describes the accompanying data:
Q4) Explain Methods for handling in an operating system.
A4)
- We can utilize a protocol to prevent or avoid deadlocks, through which we can guarantee that the system will never enter a deadlock state.
- In second way we can enable the system to enter a deadlock state, detect it, and recover from it.
- Third solution is the simplest one in which we can ignore the issue and imagine that deadlock never happen in the system.
Q5) What is Deadlocks Deadlock prevention in an operating system?
A5)
- Necessitate that all processes demand all resources one at the same time. This can be wastage of system resources if a process needs one resource in the initial stage of its execution and does not need some other resource until some other time.
- Necessitate that processes holding resources must discharge them before requesting new resources, and after that re-acquire the resources alongside the new ones out of a single new demand. This can be an issue in the event that a process has somewhat finished an activity utilizing a resource and, at that point neglects to get it re-allocated after releasing it.
- Both of the strategies portrayed above can prompt starvation if a process requires at least one well known resources.
- One methodology is that in the event that a process is compelled to hold up when mentioning another resource, at that point every other resource recently held by this process are certainly discharged, (appropriated), constraining this process to re-acquire the old resources alongside the new resources in a single request.
- Another methodology is that when a resource is requested and not accessible, at that point the system hopes to perceive what different processes right now have those resources and are themselves blocked waiting for some other resource. On the off chance that such a process is discovered, at that point a portion of their resources may get acquired and added to the list of resources for which the process is waiting.
- Both of these methodologies might be relevant for resources whose states are effectively saved and resorted, for example, registers and memory, yet are commonly not applicable to different devices, for example, printers and tape drives.
b. One approach to stay away from circular wait is to number all resources, and to require that processes request resources just in carefully expanding (or diminishing) order.
c. On contrast, so as to demand resource Rj, a process should initially discharge all Ri with the end goal that i >= j.
d. One major test in this plan is deciding the overall requesting of the various resources.
Approach:
Q6) What is Deadlock avoidance in an operating system?
A6)
Process | Maximum needs | Current allocated |
P0 | 8 | 4 |
P1 | 4 | 2 |
P2 | 8 | 2 |
b. Process P0 is having 4 tape drives, P1 is having 2 tape drives and P2 is having 2 tape drives.
c. For a safe sequence process P0 needs 4 more tape drives to completes its execution. Similarly process P1 needs 2 and P2 needs 6. Total available resources are 2.
d. Since process P0 needs 5 tape drives, but available is only 2, so process P1 will wait till gets resources. Process P1 needs only 2 so its request will be fulfilled and as P1 will finish its execution it will return all resources.
e. Now currently available resources are 4. Then process P2 will wait as available resources are 4 and P2 needs 6.
f. The system will now fulfil the needs of P0. Process P0 will execute and release its all resources. Now available resources are 8. And in the last request of process P2 will be fulfilled.
g. So, the safe sequence will be <P1, P0, P2>.
h. There is one thing to be note here that any system can go from a safe state to unsafe state if any process request more resources.
Q7) Explain Resource-Allocation-Graph Algorithm.
A7)
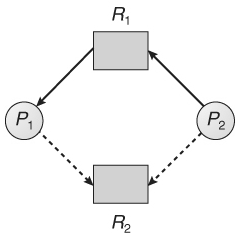
1) The subsequent resource-allocation graph would have a cycle in it, thus the request can't be granted.
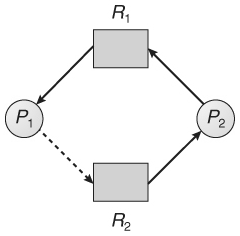
Q8) What is Banker’s Algorithm?
A8)
2) Resource allocation graph works only for single instance. In case of more than one instance an alternative approach is used known as bankers algorithm.
3) The Banker's Algorithm gets its name since it is a strategy that bankers could use to guarantee that when they loan out resources they will even now have the option to fulfill every one of their clients request.
4) At the point when a process starts, it must state ahead of time the maximum resources it might ask for, up to the amount available on the system.
5) At the point when a request is made, the scheduler decides if giving the request would leave the system in a safe state. In case, the process did not get a chance it must wait until the request can be granted securely.
6) The banker’s algorithm depends on a few key data structures: (where n is the quantity of processes and m is the quantity of resource types.)
7) For simplification of concept, we mention the accompanying notations/objective facts:
Q9) What is Safety Algorithm?
A9)
We would now be able to exhibit the algorithm for seeing if or not a system is in a safe state. This algorithm can be portrayed as follows:
Work = Available and Finish[i] = false for i = 0, 1, ... , n - 1.
2. Find an index i with the end goal that both
On the off chance that no such i exists, go to step 4.
3. Work = Work + Allocation;
Finish[i] = true
Go to step 2.
4. In case Finish[i] = = true for all i, at that point the system is in a safe state.
This algorithm may require a request for m x n2 operations to decide if a state is safe or not.
Resource-Request Algorithm:- If Requesti ≤ Needi, go to step 2. Otherwise, raise an error condition, since the process has exceeded its maximum claim.
- In the event that Requesti ≤ Available, go to step 3. Otherwise Pi must wait, since the resources are not accessible.
- Have the system claim to have assigned the requested resources to process Pi by modifying the state as follows:
Available = Available – Requesti ;
Allocationi = Allocationi + Requesti ;
Needi = Needi – Requesti ;
4. In case the final resource-allocation state is safe, the transaction is finished, and process Pi is allocated its resources. Nonetheless, if the new state is unsafe, at that point Pi must wait for Requesti, and the old resource-allocation state is restored.
Q10) What is Deadlock detection in an operating system?
A10)
- Single instance of resource: Here to detect deadlock, we can run a algorithm to check for cycle in the Resource Allocation Graph. Presence of cycle in the graph is the adequate condition for deadlock.
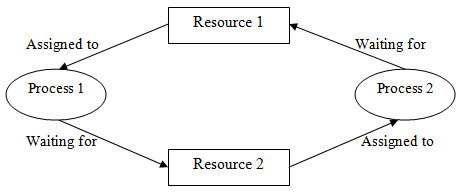
In the above graph, resource 1 and resource 2 have single occasions. There is a cycle R1 → P1 → R2 → P2. Thus, Deadlock is confirmed.
2. Multiple instance of resources: Detection of the cycle is essential yet not adequate condition for deadlock detection, for this situation, the system might be in halt fluctuates as per various circumstances.