USP
Unit -1Unix Operating System Q1) What is operating system?A1) The computer programs that allocate the system resources and coordinate all the details of the computer's internal is called the operating system or kernel.
Q2) What is UNIX operating system?A2) Unix System: The UNIX operating system is a set of programs that act as a link between the computer and the user. Users communicate with the kernel through a program known as the shell. The shell is a command line interpreter; it translates commands entered by the user and converts them into a language that is understood by the kernel.Unix was originally developed in 1969 by a group of AT&T employees at Bell Labs, including Ken Thompson, Dennis Ritchie, Douglas Mcllroy, and Joe Ossanna.
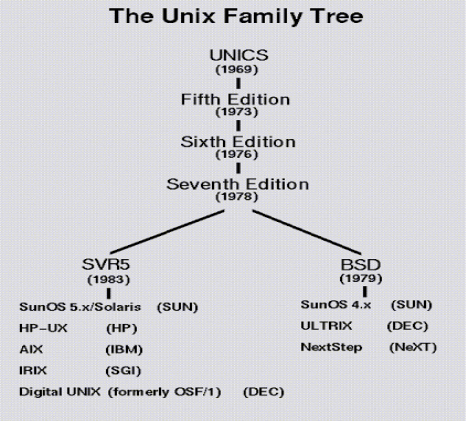
Q3) What are the various Unix variants available in the market?A3) There are various Unix variants available in the market. Solaris Unix, AIX, HP Unix and BSD are few examples, Linux is also a flavor of Unix which is freely available.
Q4) How UNIX is multiuser?A4) Several people can use a UNIX computer at the same time, hence UNIX is called a multiuser system. A user can also run multiple programs at the same time; hence UNIX is called multitasking.Q5)Give a brief history of UNIX operating system.
Q6) Describe UNIX Architecture in brief.A6)
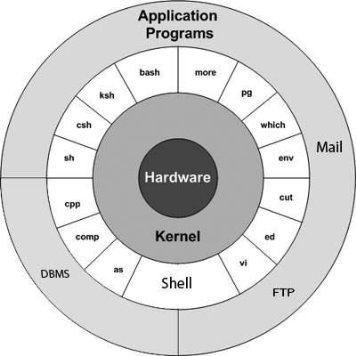
The main concept that unites all versions of UNIX is the following four basics: Kernel: The kernel is the essential center of a computer operating system, the core that provides basic services for all other parts of the operating system. A synonym is nucleus. A kernel can be contrasted with a shell, the outermost part of an operating system that interacts with user commands. In other word, the kernel is the heart of the operating system. It interacts with hardware and most of the tasks like memory management, task scheduling and file managementShell: The shell is the utility that processes your requests. When you type in a command at your terminal, the shell interprets the command and calls the program that you want. The shell uses standard syntax for all commands. C Shell, Boume Shell and Korn Shell are most famous shells which are available with most of the Unix variants.Commands and Utilities: There are various command and utilities which you would use in your day to day activities. cp, mv, cat andgrep etc, are few examples of commands and utilities. There are over 250 standard commands plus numerous others provided through 3rd party software. All the commands come along with various optional optionsFiles and Directories: All data in UNIX is organized into files. All files are organized into directories. These directories are organized into a tree-like Structure called the file system.Q7) What are the functions of operating systems?A7)1. Kernel : The Kernel performs various primitive operations on behalf of user programs :(i) Control of execution of processes: Creation, synchronization, termination, suspension and communication of processes.(ii) Scheduling of processes: Deciding of time-sharing of processes. (iii) Memory management: Allocation of memory for executing processes. Two methods are used, which overcomes the limitations of simple time-sharing.(a) Swapping: Entire process written to swap device to accommodate another process.(b) Paging: Pages of memory written to swap device (iv) File system service: Allocation of secondary storage efficiently for user data files. (v) Controlled access to peripherals, which are treated as special files.2. Hardware transparency: Processes usually run in one of the two modes:(i) User mode: User mode cannot access kernel instructions and data. (ii) Kernel mode: Kernel mode can access kernel and user addresses and privileged instructions not allowed for user mode.The hardware only view processes in terms of kernel or user modes. It does not distinguish between the user processes and the OS has internal book keeping distinguishing between processes.3. Interrupts and Exceptions:Interrupt: It is a signal by which priorities and instruction-scheduling sequence can be controlled. The kernel saves the current context (a frozen image of what the processes was doing) when an interrupt occurs. After servicing the interrupt the context is restored and the process proceeds. The order in which an interrupt is serviced depends upon its priority.Exception: An exception is an unexpected event like reference to an illegitimate address caused by events external to a process. Exceptions usually occur in the middle of a process where as interrupts occur between them. Different algorithms are used to handle interrupts/exceptions efficiently.4. Processor Execution Levels: Based on the priority level of an interrupt the kernel masks certain interrupts in order that a critical process may proceed without error.The priority levels in descending order are:
 Higher Priority
Higher Priority  Lower Priority
Lower Priority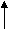 There would be no disk interrupts while manipulating linked lists.5. Memory management: The concept of a Virtual Machine is central to memory management under UNIX. The compiler generates addresses for a virtual machine as if no other program will execute simultaneously on the physical machine. Virtual addresses generated by the compiler need not be identical to the actual physical addresses in the machine. The memory management coordinates with the machine hardware to set-up a virtual to physical address translation that maps the compiler-generated address to the physical machine address.
There would be no disk interrupts while manipulating linked lists.5. Memory management: The concept of a Virtual Machine is central to memory management under UNIX. The compiler generates addresses for a virtual machine as if no other program will execute simultaneously on the physical machine. Virtual addresses generated by the compiler need not be identical to the actual physical addresses in the machine. The memory management coordinates with the machine hardware to set-up a virtual to physical address translation that maps the compiler-generated address to the physical machine address.
|
|
Machine Errors |
Clock |
Disk |
Network Devices |
Terminals |
Software Interrupts |
 Higher Priority
Higher Priority  Lower Priority
Lower Priority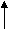 There would be no disk interrupts while manipulating linked lists.5. Memory management: The concept of a Virtual Machine is central to memory management under UNIX. The compiler generates addresses for a virtual machine as if no other program will execute simultaneously on the physical machine. Virtual addresses generated by the compiler need not be identical to the actual physical addresses in the machine. The memory management coordinates with the machine hardware to set-up a virtual to physical address translation that maps the compiler-generated address to the physical machine address.
There would be no disk interrupts while manipulating linked lists.5. Memory management: The concept of a Virtual Machine is central to memory management under UNIX. The compiler generates addresses for a virtual machine as if no other program will execute simultaneously on the physical machine. Virtual addresses generated by the compiler need not be identical to the actual physical addresses in the machine. The memory management coordinates with the machine hardware to set-up a virtual to physical address translation that maps the compiler-generated address to the physical machine address. Q8) What are the features of UNIX?A8) The major features of UNIX can be listed as follows:(i) Multiuser, time sharing OS(ii) Multitasking OS(iii) Portability (iv) Modularity(v) System security (vi) File structure and security (vii) Device Independent(viii) Communication(i) Multiuser, time sharing OS: UNIX allows several users, nearly 24 to 500, to use the same computer simultaneously by attaching terminals (keyboard and display) dumb or intelligent such that users of these terminals can run programs, access files, print documents, all at once. This is facilitated by time sharing the resources between the users. Scheduling algorithms are used to provide fast and non interfering usage of the computer. (ii) Multitasking OS: In UNIX we can perform more than one task at a time i.e. while it is printing a document, we can start editing a new document or we can make the system scan a mailing list for an operation like sorting or process another document on the editor.) Multitasking is supported by placing few tasks in the "background" while we work on a task in the "foreground".(iii) Portability: UNIX system itself is extremely portable. With few modifications, the UNIX system can be installed on a variety of hardware. It contains a set of programs that will let us connect our old computer to our new one and transfer data easily thus, providing a high version to version compatibility. (iv) Modularity: UNIX comes with several hundred supplied programs in terms of utilities and tools which provide a rich and productive environment to create bigger modules from smaller ones. Integral utilities are part of the UNIX system that provide necessary support to the operating system for the practical operation of a computer with UNIX like command interpreter and shell program. Tools are programs that though are not essential for UNIX's basic operation but provide significant value addition Examples are electronic spreadsheets, word processing packages, mail programs, etc.(v) System security: Computer system security means protecting computer hardware and information contained within the system. Threats to the system can be both internal and external. External threats include unauthorized access to the computer system, unauthorized tapping of data being transferred over the network, fire, electric power faults, natural disasters etc. Internal threats are of a more serious nature like destruction of software data by mistake or on purpose, examination or access of sensitive data by unauthorized users, alteration of this data. UNIX provides several safeguards in terms of:(a) Password protection for system access. (b) Control of access to individual files.(c) Encryption of data files.(d) Encryption of passwords.(e) System accounting functions.(vi) File structure and security: UNIX uses hierarchical file system for easy maintenance. It has consistent format for files, the byte stream, making application programs easier to write. UNIX permits more than one user to update the same file at virtually the same time. But if two users update the same file at exactly the same time, problems that affect the integrity of the data may occur. For example, the write operation of one user can undo the one just performed by the other user. To minimize these problems, file, record locks and explicit permissions are implemented.(vii) Device independence: In UNIX, one of the design principles is to treat disk files and I/O devices as files from a user's perspective thus, safe guarding the user from the intricacies of the device. This provides device independence to the user. The hardware devices are given names in the file systems. These device special files are though known to the kernel as device interfaces, but are accessed by the user in the same way as other files(viii) Communication: Communication has been one of UNIX's strong points. UNIX has extensive electronic mail facilities, some of the commands have subsequently been enhanced to run over a network, and even on the Internet. User processes communicate with network protocols via the socket facility.(ix) Benefits of UNIX Operating System: The system is written in a high-level language, making it easy to read, understand, change, and move to other machines. Ritchie estimates that the first system in C was 20 to 40 percent larger and slower because it was not written in assembly language, but the advantages of using a higher-level language far out weight the disadvantages. It has a simple user interface that has the power to provide the services that users want. It provides primitives that permit complex programs to be built from simpler programs. It uses a hierarchical file system that allows easy maintenance and efficient implementation. It uses a consistent format for files, the byte stream, making application programs easier to write.It provides a simple, consistent interface to peripheral devices. It is a multi-user, multiprocessor system; each user can execute several processes simultaneously. It hides the machine architecture from the user, making it easier to write programs that run on different hardware implementations. Q9) Write the use and syntax of following commands. Give examples also.a)mvb)nlc)touchd)pwde)echof)chmodg)passwdA9)1) mv - move a file: Rename a file with the move command, mv. Syntax: mv (options] old_filename new_filename Common Options: -i interactive (prompt and wait for confirmation before proceeding) -f don't prompt, even when copying over an existing target file (overrides-i) Examples: $ mvold_filename new_filename i) We now have a file called new_filename and the file old filename is gone. Actually all we've done is to update name the directory table entry to give the file a new nameii) The contents of the file remain where they were. 2. nl : line number: To add line numbers to a file in Unix, use the nl command. For example, given an input file cherry.txt, Loveliest of trees, the cherry now is hung with bloom along the bough,And stands about the woodland rideWearing white for Eastertide. The command$ nl cherry.txtGives output: 1 Loveliest of trees, the cherry now2 Is hung with bloom along the bough,3 And stands about the woodland ride4 Wearing white for Eastertide. It is also possible to start from a different number. The command: $ nl-v 100 cherry.txt Gives the output: 100 Loveliest of trees, the cherry now101 Is hung with bloom along the bough,102 And stands about the woodland ride103 Wearing white for Eastertide. 3. touch: Changing the Time Stamps : We may sometimes need to set the modification and access times to predefined values. The touch command changes these times, and is used in the following manner: Syntax: touch [options] expression filename (s) Common Options: -a change the access time of the file (SVR4 only) -c don't create the file if it doesn't already exist -f force the touch, regardless of read/write permissions-m change the modification time of the file (SVR4 only) -t time use the time specified, not the current time (SVR4 only)Example:1. When touch is used without options or expression, both times are set to the current time. The file is created if it doesn't exist : $ touch emp.lst Creates file if it doesn't exist2. When touch is used without options but with expression, it changes both times. The expression consists of an eight-digit number using the format MMDDHHMM (month, day, hour and minute). Optionally, we can suffix a two- or four-digit year string : $ touch 03161430 emp.lst $ ls –l emp.lst -rw-r--r-1 kumar metal 870 Mar 16 14:30 emp.lst 4. Pwd : ‘pwd' stands for 'Print Working Directory. As the name states, command 'pwd' prints the current working directory or simply the directory user is, at present. It prints the current directory name with the complete path starting from root (/). This command is built in shell command and is available on most of the shell - bash, Bourne shell, ksh,zsh, etc. Syntax : $ pwd [option]e.g., /home/frank/src Option: -L (logical) Use PWD from environment, even if it contains symbolic links -P (physical) Avoid all symbolic links -help Display this help and exit --version Output version information and exit If both -L' and'-P options are used, option 'L' is taken into priority. If no option is specified at the prompt pwd will avoid all symlinks, i.e., take option -P into account 5. echo: Displaying a message : This command is often used in shell scripts to display diagnostic messages on the terminal, or to issue prompts for input. So far, we have used it in two ways : (i) To display a message (like echo Sun Solaris). (ii) To evaluate shell variables (like echo (SHELL)). Originally, echo was an external command, but today all shells have echo built-in. Syntax :echo[option] [string] Option : -n do not output the trailing newline-e enable interpretation of backslash escapes-E disable interpretation of backslash escapes (default)--help display this help and exit--version output version information and exit If -e is in effect, the following sequences are recognized :
Note: Your shell may have its own version of echo, which usually supersedes the version described here. Please refer to your shell's documentation for details about the options it supports.6. more: Paging Output: The more command displays its output a page at a time. This is possible because it sends its output to a pager program. UNIX offers the more pager (originally from Berkeley) which has today replaced pg, the original pager of UNIX. Linux also offers more but less is its standard pager. To view the file chap01, enter the command with the filename:$ more chap01 Press q to exitWe'll see the contents of chap01 on the screen, one page at a time. At the bottom of the screen, we'll also see the filename and percentage of the file that has been viewed:--More- (17%)More has a couple of internal commands that don't show up on the screen when we invoke them, the command used to exit more, is an internal command. Navigation : Irrespective of version, more uses the spacebar to scroll forward a page at a time. We can also scroll by small and large increments of lines or screens. To move forward one page, use f or the spacebar and to move back one page, use b.The use of Repeat Factor: As a command prefix simply repeats the command that number of times. This means we can use 10f for scrolling forward by 10 pages and 30b for scrolling back 30 pages. Just ember that the commands themselves are not displayed on the screen-even for a moment.Searching for a Pattern: We can perform a search for a pattern with the / command followed by the string. For instance, to look for the first while loop in our program, we'll have to enter this:/while Press (Enter] alsoWe can repeat this search for viewing the next whileloop section by pressing n, and we can do that repeatedly until we have scanned the entire file. Move back with b (using a repeat factor, if necessary) to arrive at the first page.Internal commands:Spacebar of f one page forward 10f 10 page forwardEnter key one line forwardB one page back 10b 10 page back:n next file:P previous file .(Dot) repeat last commandq Quit 7. chmod: Changing file permissions: The command name chmod stands for "change mode", and it is used to define the way a file can be accessed. Chmod (change mode) is one of the most frequently used commands in unix or linux operating system. The chmod command is used to change the file or directory access permissions.Syntax:chmod [options] permissions filenameThere are three different permissions. They are:Read (4): Permitted to read the contents of the file. In case of directory, you can view all the files and sub-directories in that directory Write (2): Permitted to write to the file. In case of directory, you can create files and sub-directories Execute (1): Execute the file as a program/shell script. In case of directory, You can enter into that directory. Here in the above, the numbers in the brackets represents the numeric values for the corresponding permissions. If you want to have a combination of permissions add the required numbers. For example, for read and execute, it is 4+1= 5. chmod [options]-R: recursively change the permissions of a directory.-v: VerboseChmod Examples in Linux / Unix:1. Give read, write and execute permissions to everyone. Read, write and execute: 4+2+1=7$ chmod 777 sample.shIn the above example, you can see that the permissions are specified with a three digit number. The first digit is for user permissions, second is for group and third is for others permission. This type of representation is called octal representation. Alternatively, you can use the symbolic representation to give the permissions.chmod ugo+rwx sample.shWe will see more details about the symbolic representation later. 2. Give read permission to user, write permission to group and execute permission to others$ chmod 421 sample.sh 3. Recursive permissions to directoryTo give read and write permissions to all the users to a directory (including files and subdirectories) use the recursive option -R.chmod -R 666 /dirSymbolic Representation of Permissions: The following symbols are used to represent the users, groups and others: ● u: User● g: Group● o: Others ● a: All (user, group and others)The following symbols represent the permissions:● r: read● W: write● X: executeThe following symbols represent the permissions grant or revoke: ● + : Additional permissions. Selected permissions are added.● - : Revoke the permissions. Selected permissions are revoked.● = : Specific permissions. Only selected permissions are assigned.Examples1. Remove write permission from group$ chmod g-w sample.shThis will only removes the write permission for the group.2. Add new permission execute to others$ chmod o+x sample.shIn addition to the existing permissions, this will add execute permission to others.3. Give only read permissions to the user$chmod u=w sample.shThis will remove the existing permissions to the user and gives only write permission to the user. 8. passwd: passwd command is used to change the password. First it prompts for the old password then it prompts for the new password and finally asks to reenter the new password. $ passwd passwd: Changing password for Chintamani Enter login password: ****New password: ****Re-enter new password: **** passwd: password successfully changed for Chintamani Q10) What are the features of UNIX file system?A10)Features of UNIX file System:1. Hierarchical structure:(i) The file system is organized as a tree with a single root node called root (written "/"); every non-leaf node of the file system structure is a directory of files, and files at the leaf nodes of the tree are either directories, regular files, or special device files.(ii) The name of a file is given by a path name that describes how to locate the file in the file system hierarchy. A path name is a sequence of component names separated by slash characters; a component is a sequence of characters that designates a file name that is uniquely contained in the previous (directory) component (i) A full path name starts with a slash character and specifies a file that can be found by starting at the file system root and traversing the file tree, following the branches that lead to successive component names of the path name. (ii) Thus, the path names "/etc/passwd", "/bin/who", and "/usr/src/cmd/who.c" designate files in the tree shown in figure but "/bin/passwd" and "/usr/src/date.c" do not. (v) A path name does not have to start from root but can be designated relative to the current directory of an executing process, by omitting the initial slash in the path name. Thus, starting from directory "/dev", the path name "tty01" designates the file whose full path name is "/dev/tty01".2. Consistent treatment of file data UNIX imposes no format what so ever on the contents of a file. For it all files are just streams of bytes. Any format that is imposed is done by the utility that creates these files and not the UNIX operating system. For example, C programs must have a .c extension, this is the requisite of C compiler. A UNIX file does not contain the end-of-file mark or its name.3. The ability to create and delete files: Permission to access a file is controlled by access permissions associated with the file. Access permissions can be set independently to control read, write, and execute permission for three classes of users: the file owner, a file group, and everyone else. Users may create files if directory access permissions allow it. The newly created files are leaf nodes the file system directory structure.4. Dynamic growth of files: The size of a file is only restricted by the amount of disk-storage available. The sizes of the files and the number of files can be dynamically modified.5. The protection of file data: UNIX provides security at different levels. Files are protected using file ownership mechanisms. The users are divided into three groups and each group is granted access or denied access in terms of read, writes and executes permissions for each file separately.6. Treatment of peripheral devices (such as terminals and tape units) as files: As devices and directories are also treated as files in UNIX, user does not need to know the details of device related operations and procedures.
\0NNN | the character whose ASCII code is NNN (octal) |
\\ | Backslash |
\a | alert (BEL) |
\b | Backspace |
\c | suppress trailing newline |
\f | form feed |
\n | new line |
\r | carriage return |
\t | horizontal tab |
\v | vertical tab |
0 matching results found